Abstract
A collection of smaller, less expensive sensor nodes called wireless sensor networks (WSNs) use their sensing range to gather environmental data. Data are sent in a multi-hop manner from the sensing node to the base station (BS). The bulk of these sensor nodes run on batteries, which makes replacement and maintenance somewhat difficult. Preserving the network’s energy efficiency is essential to its longevity. In this study, we propose an energy-efficient multi-hop routing protocol called ESO-GJO, which combines the enhanced Snake Optimizer (SO) and Golden Jackal Optimization (GJO). The ESO-GJO method first applies the traditional SO algorithm and then integrates the Brownian motion function in the exploitation stage. The process then integrates multiple parameters, including the energy consumption of the cluster head (CH), node degree of CH, and distance between node and BS to create a fitness function that is used to choose a group of appropriate CHs. Lastly, a multi-hop routing path between CH and BS is created using the GJO optimization technique. According to simulation results, the suggested scheme outperforms LSA, LEACH-IACA, and LEACH-ANT in terms of lowering network energy consumption and extending network lifetime.
1. Introduction
A WSN is a network made up of numerous sensor nodes dispersed within a certain region. To enable data collection, transfer, and analysis, these nodes can be wirelessly connected to one another [1,2]. WSNs are becoming more and more appealing for a wide range of application fields, including military applications, emergency response and security, environmental monitoring, health and medical, automated industrial control, smart cities, transportation and logistics, and entertainment [3,4,5]. WSNs’ low cost and ease of deployment have led to their widespread application in many different industries. But energy is scarce and sensor node batteries are hard to replace. Therefore, it is imperative to address the issue of the energy usage of networks and increase the network’s lifespan [6,7].
Given that the primary cause of node energy consumption is wireless communication [8], energy-efficient communication protocols are essential for drastically reducing network energy consumption and increasing network lifetime. Of these protocols, the clustering routing protocol is a notable example of an essential subset in the field of energy-efficient WSN communication protocols. It has proven to be a very successful method for energy conservation in WSNs with limited energy supplies. Organizing sensor nodes into multiple clusters, each with a CH and additional common nodes, is the core idea behind the cluster-based routing protocol. The common nodes in each cluster gather information and send it to the CH. Following data collection, the regular nodes’ data packets are received, combined, and processed by the CHs, which subsequently forward the processed and combined data to BS. The clustered routing protocol is essential for WSNs’ energy conservation since it reduces energy usage and helps manage overhead traffic [9,10,11,12].
The key idea of network clustering is intimately related to how well the clustered routing protocol affects network energy consumption. As communication distance reduces, so does the amount of energy used for communication inside clusters. Given that CHs use more energy to perform functions like receiving, fusing, and transferring data than normal nodes, choosing the right CHs is essential for enhancing network load balancing. Furthermore, the utilization of a multi-hop communication technique is efficacious in mitigating communication energy consumption, particularly in light of the high energy expenditure linked to long-distance communication. This work employs the SO optimization technique to solve the NP-hard problem [13,14,15,16,17] of optimal CH selection, and the best route between CHs is determined during the data transmission phase using the GJO optimization technique. Below is a summary of this research work’s main contributions:
- (1)
- The ESO-GJO method adds a Brownian motion function to the SO algorithm’s exploitation stage in order to avoid local optima.
- (2)
- The proposed approach uses SO to select the optimal CHs and considers variables such as energy and distance when building the fitness function.
- (3)
- The suggested algorithm uses GJO to determine the route from CH to BS and initializes the GJO population through backward learning.
The structure of the rest of the article is summarized below:
- Section 2: Summarizes previous work in related fields.
- Section 3: Introduces the energy model and network model.
- Section 4: Offers a detailed introduction to the algorithm proposed in this article.
- Section 5: Performance metrics simulation demonstration and comparison.
- Section 6: Summarizes the research work in this paper and suggests future work to be carried out.
2. Related Works
Numerous routing methods have been developed with the goal of increasing energy efficiency and lengthening network lifetime in order to address the problem of limited energy in WSNs. LEACH [18] is one of the most well-known clustering routing methods for WSNs. Each iteration of the LEACH protocol is divided into two stages: clustering and stabilization. During the clustering phase, each node generates a random integer between 0 and 1, which it subsequently compares to the value obtained from a threshold calculation. The node is not elected as CH in the following round if the random number is less than the threshold and it was not elected in the preceding (p is the proportion of nodes that became CH in the current round) rounds. During the stabilization phase, the sensor nodes transmit the information they have collected to the CH. After completing data fusion on the gathered data, CH sends the information in a single hop to the aggregate node. The CH needs more energy to run because it has a higher mission load than other nodes, which is a major drawback of the LEACH algorithm. The energy-efficient multi-hop routing protocol L-LEACH (Energy Balanced) [19] solely takes the distance component into account. Like LEACH, L-LEACH is divided into two phases. Every round, the energy load is split equally among the network nodes and new CHs are chosen. Nonetheless, a noteworthy constraint of the algorithm is its disregard for the algorithm’s intricacy and the corresponding network overhead. This oversight could be considered a negative in assessing the overall performance of L-LEACH. In order to send data from orphan nodes in the network that cannot be fully covered to the BS, Jerbi et al. [20] designed the O-LEACH (orphan-LEACH) protocol. The protocol proposes two solutions. One method is to have a cluster member serve as a gateway, enabling non-clustered nodes to join the cluster by designating that gateway node as the CH, so that the data of the isolated nodes can be sent through the gateway node aggregation to the CH of the cluster where the gateway node is located. Another solution is that cluster members can form subclusters with orphan nodes, and the first orphan node to join will serve as the cluster head for that subcluster. It is important to remember that this approach works only in situations when there is a finite number of cluster members. The Multi-Hop LEACH (MH-LEACH) protocol was created by Neto et al. [21] to find the best pathways to the BS via several intermediate CHs. According to this protocol, each CH broadcasts an advertisement message in order to build its routing table according to the strength of the signal it receives. However, they are forwarded to the CH to be checked for possible looping or an opposite direction before employing these routes. C Long et al. [22] and Tanushree Agarwal et al. [23] propose LEACH-ANT and LEACH-IACA protocols, respectively, both of which are based on LEACH for cluster head selection and utilize an ant colony algorithm to find the optimal path in the inter-cluster transfer phase. However, the algorithm suffers from local optimization and slow convergence speeds.
Swarm intelligence has a lot of potential for WSN routing optimization. In order to extend the network life cycle, Gobi Natesan et al. [24] proposed a clustering algorithm combining Mayfly and Aquila called MFA-AOA. The algorithm uses MFA for CH selection using variables like energy and distance, among others, to build the fitness function and choose CHs. The algorithm uses AOA to select the optimal route between CH and BS. But the algorithm does not adequately consider the complexity. Y. Yao et al. [25] presented the IAOAR routing protocol, which is based on the Archimedean optimization technique and can reduce energy efficiency. The algorithm selects the optimal CH based on AOA. Based on variables such the CH’s residual energy, the distance between clusters, and the CH’s distance from the BS, IAOAR builds the fitness function for choosing the best CHs.To determine the shortest path between CHs, the algorithm employs an ant colony optimization technique. However, it is important to remember that this approach does not handle network heterogeneity, which could be considered in future enhancements. An energy-efficient clustering technique, called EPOA-CHS (Enhanced Pelican Optimization Algorithm for Selecting Optimal CH Set), was proposed by Wang, Z. et al. [26]. The algorithm uses POA for optimal CH selection. EPOA-CHS builds the fitness function for choosing the CH set using characteristics like node energy and inter-cluster distance. However, EPOA-CHS is designed as a single-hop clustering protocol, which means that it can only operate within single-hop communication. This characteristic may affect its applicability in specific network scenarios where multi-hop communication is more advantageous. Punithavathi et al. [27] introduced BWO-IACO, an energy-efficient clustering approach based on the combination of Ant Colony Optimization and Black Widow Optimization. Using BWO, the algorithm chooses a suitable set of CHs. The fitness function used to choose CHs is composed of several criteria, including node centrality, node degree, and intra-cluster. The algorithm uses improved ACO for inter-cluster routing. However, the technique does not account for how data aggregation affects data transmission energy. Vinitha et al. [28] suggested a multi-hop routing protocol with Cat Swarm Optimization (CSO) and Salp Swarm Optimization (SSA) to lower the energy consumption and latency of wireless sensor networks. The algorithm uses LEACH to select CHs and C-SSA to select the optimal hops. Energy, distance, and latency are among the elements that make up the fitness function used to choose the best hops. However, the applicability of the algorithm to large-scale networks has not been fully considered, which may be a topic for development or further research. To minimize network power consumption, Senthil, G.A. et al. [29] proposed a routing protocol capable of efficient cluster head election and path optimization. The protocol combines Lightning Search Algorithm and Particle Swarm Optimization and is called PSO-LSA. However, the protocol focuses too much on orphan nodes, which may lead to degradation of the performance of the protocol.
3. Preliminaries
This section furnishes details regarding the network model and energy model.
3.1. Network Model
Figure 1 illustrates the structure of the WSNs.
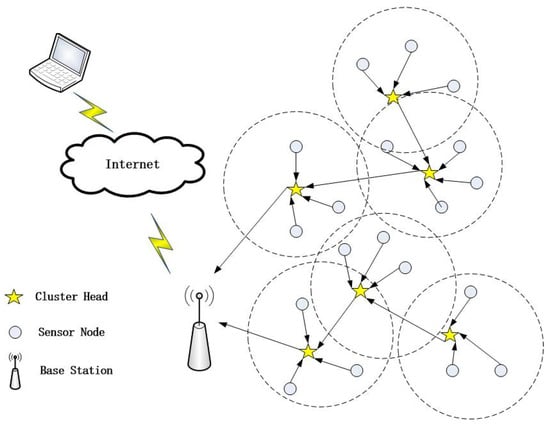
Figure 1.
Cluster-based WSN with CHs.
The following factors are taken into account when creating the network model:
- In WSNs, every sensor node has the same initial energy.
- Distances between nodes are calculated using Euclidean distance.
- Within the sensing area, sensor nodes are haphazardly placed and maintain a fixed location once deployed.
- The BS can be positioned either within or outside the screening region, and it remains stationary.
- The sensor node as a cluster member transmits the collected environmental data to the CH.
- The aggregated data are transferred to the BS via CH.
3.2. Energy Model
The standard first-order radio model, as described in [30,31], is the foundation for this article’s estimation of the nodes’ energy consumption. Equation (1) gives the transmitting node’s energy usage, which is referred to as . This computation is useful when a node sends l bits of data to a receiving node that is located d away. Furthermore, Equation (2) establishes the receiving node’s energy consumption, which is represented by the symbol .
Here, and , respectively, represent the energy consumption coefficients of the amplifier circuit for the free-space fading model and the multipath fading model. Furthermore, the transmission and receiving circuits’ energy consumption coefficient is denoted by . Equation (3) establishes the threshold, which is represented as and acts as the border between the two attenuation models. The transmission uses the free-space fading model if the distance d is less than , which results in an energy consumption of for the amplifier circuit. On the other hand, the multipath fading model is applied where d > , resulting in an energy consumption of for the amplifier circuit.
Data are received by the CH from the cluster, and it uses some energy to transfer the aggregated data to the BS. Consequently, it becomes imperative for the CH to possess a sufficient reservoir of energy to effectively relay data to the BS. The energy level of the CH is represented by the letter ,
where is the energy used by the transmitter. is the energy necessary for data aggregating, and a data packet is represented by the symbol l. When transmitting over long distances to a base station, as shown by , the transmitter amplifier’s energy usage is represented by . The energy consumption of non-cluster heads is shown by .
Within a specific context, the symbol l denotes a data packet, denotes the transmitter’s energy consumption, denotes a transmitter amplifier in a free condition, denotes the CH’s short distance, and denotes the BS’s long distance.
4. Proposed Method
We will provide a detailed introduction to the proposed ESO-GJO protocol in this section. Each iteration of the ESO-GJO protocol encapsulates both the CH selection phase and the subsequent data transmission stage, amalgamating these crucial processes within every round. In the cluster head selection phase, we use the SO optimization algorithm for cluster head selection and in the data transmission phase, we use the GJO optimization algorithm for optimal path selection. In addition, the fitness function plays a crucial role in the SO algorithm and GJO, which is an indicator of the degree of superiority of a solution, and provides a search direction for the algorithm. Through the rational design of the fitness function, we can help the algorithm to find the optimal solution of the problem faster. The choice of fitness function should be determined according to the needs of the specific problem, and it can be defined based on the constraints of the problem and the objective function. Figure 2 shows the flow block diagram of the ESO-GJO algorithm.
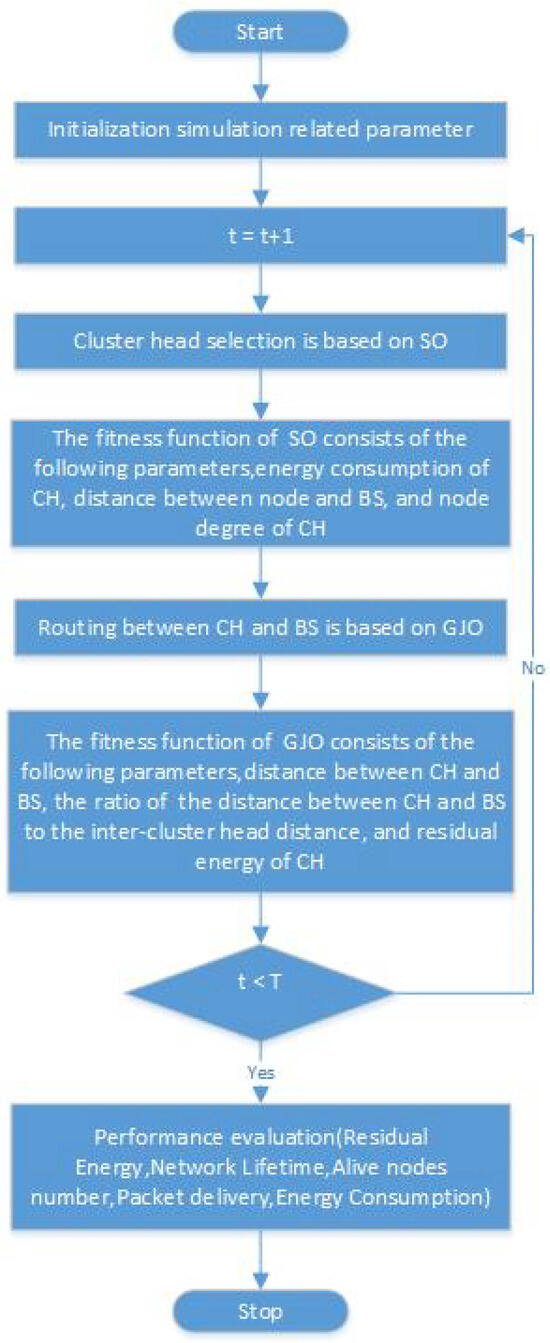
Figure 2.
ESO-GJO flowchart.
4.1. CH Selection Stage
4.1.1. CH Selection Using SO
In this section, we describe how to use the SO [32] optimization algorithm for optimal cluster head set selection for wireless sensor networks. The suggested algorithm’s main goal is to carefully choose CHs from the pool of regular sensor nodes, strategically integrating considerations for energy conservation. This overarching aim is geared towards proactively elongating the network’s operational lifetime.
An individual in SO symbolizes a whole solution. It represents the ideal locations of the CHs for the proposed algorithm’s CH selection. Let represent the ith member of the population, and let represent each component’s coordinates for the sensor nodes chosen to serve as CH. Every single person has the same number of dimensions represented by the letter D; this corresponds to the quantity of CH.
The snakes choose a random position during the exploration phase and adjust their position in relation to it if . The following steps are followed to mimic the exploration phase:
The ith male position is shown by , the random male position is indicated by , and the male’s ability to find food is indicated by . The calculation for this is as follows:
where is defined, the fitness of is denoted by , and the ith member of the male group’s fitness is denoted by .
where is the female’s capacity to locate food and may be computed as follows; a random female’s position is indicated by ; and position of the ith female is indicated by .
In this case, the fitness of is represented by , and the ith member of the female group’s fitness is denoted by .
The constant coefficient is utilized to update the snake’s position throughout the exploiting phase. In this study, instead of using the constant coefficient , we use the Brownian motion function to keep the algorithm from reaching a local optimum. One of many physical processes in which a quantity continuously fluctuates between tiny, random fluctuations is called Brownian motion. It is believed that Brownian motion is a Markov process coupled with a Gaussian process. The normal (Gaussian) equation was altered by the algorithm’s changes to the size and number of agents, which are used to determine the Brownian motion steps, and the Brownian motion was finalized (Equation (10))
The following formula can be used to define the temperature Temp.
Here, t represents the current iteration, and T signifies the maximum number of iterations.
The definition of the quantity of food is Q. The following formula can be used to determine how much food is consumed.
where . If the , snakes only travel in the direction of food.
where represents the best individual’s position and represents the individual’s position. The snake will go into either the fighting or mating mode if the temperature is less than 0.6.
In Fight Mode,
where represents the male position, denotes the fighting prowess of the male agent, and represents the best individual’s position within the female group.
where denotes the female agent’s combat prowess, indicates that she is the top member of the male group, and represents her position.
is represented by Equation (16) and is represented by Equation (17):
where is the agent fitness, is the best agent of the male group, and is the best agent of the female group. In Mating Mode,
where denotes the ability of the male and female to mate, respectively; and , respectively, denote the positions of the ith agents within the female and male groups. These values can be calculated as follows:
Replacement of worst males and females selected from hatched eggs:
where is the worst individual in the male group; is the worst individual in the female group.
Finally, the globally optimal individual vector is used as the optimal CH set.
4.1.2. Fitness Function of SO
The fitness function used by the SO algorithm to determine the ideal set of CHs is made up of the following variables and formulas.
- (1)
- Energy consumption of CH:This is the first parameter of the fitness function. Our goal is to prioritize nodes with low energy consumption as CH. Let represent the ’s energy consumption, and assume that , K is the number of CHs.Consequently, minimizing the objective function is our aim:
- (2)
- Distance between node and BS:This is the second parameter of the fitness function. Our goal is to prioritize the node with the shortest distance to the common node and BS as the CH. Let be the distance from intra-cluster node to cluster head node . Let be the distance from to BS where , K represents the quantity of CHs and , M represents the quantity of cluster members. Consequently, minimizing the objective function is our aim:
- (3)
- Node Degree of CH: This is the third parameter of the fitness function. High-degree nodes are given preference to become CH in the ESO-GJO CH selection process. Consequently, our goal is to maximize the objective function as follows
Our suggested SO algorithm’s fitness function is to minimize the aforementioned , , and functions. As a result, the following is the fitness function for our algorithm:
where the weights for the goal function are provided by the constants , , and . The total of these constants ought to equal one. Minimizing the cumulative objective function is our aim.
4.2. Data Routing Stage
4.2.1. Routing Algorithm Using GJO
The goal of the routing problem we will now solve is to reduce the maximum possible transmission distance between CHs in a routing path. The goal of the routing problem we will now solve is to reduce the maximum possible transmission distance between CHs in the routing path. This section describes how to use the GJO [33] optimization algorithm for optimal path selection for wireless sensor networks.
The starting population is generated by random initialization in the GJO methodology, yet this approach is vulnerable to the issue of an excessively dispersed or locally concentrated population.
Due to this circumstance, the population diversity of the classic GJO algorithm is inadequate, which significantly impairs the ensuing iterative optimization search.
Thus, in order to broaden the algorithm’s search space and boost population variety, we chose to initiate the population in this study using a backward learning technique.
The following is the definition of the reverse learning strategy:
Let be the ith individual of the current population. The general inverse learning strategy produces a general inverse solution of as .
M is an enormous positive number, a is the multiplier of the interval , and c is incremental. is the seed of the random number. approximately obeys a uniform distribution in the interval ; its maximum period is M, and approximately obeys a uniform distribution in the interval .
The two primary steps of the GJO algorithm are finding prey and encircling and attacking it. These processes represent the exploration and exploitation of populations, respectively.
- (1)
- The stage of exploration or hunting for preyThis section proposes GJO’s exploration plan. Jackals can sense and follow their prey due to their innate instincts, yet sometimes the prey escapes and is hard to catch. As a result, the females follow the males and lead the pack in search of additional prey.where t is the current iteration. represents the prey’s position vector, while and represent the locations of the male and female jackals. The updated positions of the male and female jackals with respect to the prey are shown by and .The prey’s initial energy level is represented by , while its decreasing energy is represented by .where r can be any integer between 0 and 1.where ; the rounds of iteration are denoted by T and is calculated by Equation (36):
- (2)
- The stage of exploitation or encircling and leaping for preyThe mathematical model of joint roundup of male and female jackals is shown in Equations (39) and (40):
Finally, the position vector is used as the optimal path.
4.2.2. Fitness Function of GJO
The GJO method builds the fitness function using the following parameters in order to find the optimal route between CH and BS:
- (1)
- Distance between CH and BS: The further the distance between the CH and the BS, the more energy is required to transmit the data. Therefore, the CH close to the BS is selected to form the best path. Consequently, minimizing the objective function is our aim:
- (2)
- The ratio of the distance between CH and BS to the inter-cluster head distance:The fitness function’s second parameter will be this ratio. Here, maximizing the inter-cluster distance and minimizing the distance between and BS are the main objectives. Consequently, minimizing the objective function is our aim:
- (3)
- Residual energy of CH: This is the fitness function’s third parameter. Our goal is to prioritize the CH with more remaining energy as the next hop. Let denote the residual energy of CH; K denotes the number of CHs. Consequently, our goal is to maximize the objective function as follows:The following three functions , , and , are to be minimized as the fitness function for our suggested GJO method. As a result, the following is the fitness function for our algorithm:where , , and are constants that give the objective functions weights. The total of these constants ought to equal 1. Minimizing the objective function is our aim.
4.3. The Pseudo-Code of the Proposed Algorithm
Algorithm 1 is a pseudo-code that uses the SO algorithm to select the best set of CHs and Algorithm 2 is a pseudo-code that uses the GJO method to find the best route between CH and BS.
| Algorithm 1 SO-Clustering |
|
| Algorithm 2 GJO-Routing |
|
5. Simulation Results
5.1. Simulation Settings
Using the 100 × 100, 200 × 200, 300 × 300 (m2) setup area range for the experiment, compare the clustering impact of the technique proposed with the other three comparative algorithms. The following algorithms are compared with the suggested approaches: PSO-LSA [29], LEACH-IACA [22], and LEACH-ANT [23]. Identical sets of network input setup parameters are used by all methods. The simulation related parameters are shown in Table 1.

Table 1.
Simulation-related parameter.
5.2. Residual Energy
This performance metric is the sum of the remaining energy of the surviving nodes in each round. For the length of the simulation, a fixed initial energy of 0.5 J has been used. The ESO-GJO technique presented in this research is compared with PSO-LSA, EPOA-CHS, LEACH-IACA, and LEACH-ANT residual energy for a scenario with 100 nodes. The results are displayed in Figure 3a. It is noted that LEACH-IACA and LEACH-ANT lost their remaining energy after 1500 cycles. On the other hand, PSO-LSA,EPOA-CHS, and ESO-GJO managed to live with 15.29 J, 16.41 J, and 18.13 J, respectively. All nodes of PSO-LSA and EPOA-CHS die after the 2400th round. However, the proposed ESO-GJO still has 0.08 J of energy remaining. Figure 3b shows the results of comparing the residual energy of ESO-GJO with other protocols for the scenario of 200 nodes. It is observed that at the end of 1000 rounds, all the energies of LEACH-IACA and LEACH-ANT are exhausted. However, PSO-LSA, EPOA-CHS, and ESO-GJO have 55.30 J, 55.01 J, and 56.79 J remaining, respectively. With PSO-LSA, all nodes die at round 2500. However, the proposed ESO-GJO still has 2.67 J of energy remaining. Figure 3c shows the results of comparing the residual energy of ESO-GJO with other protocols for the scenario of 300 nodes. It is observed that at the end of 800 rounds, all the energies of LEACH-IACA and LEACH-ANT are exhausted. However, PSO-LSA,EPOA-CHS, and ESO-GJO have 94.14 J, 94.95 J, and 95.40 J remaining, respectively. With PSO-LSA and EPOA-CHS, all nodes die at round 2350. However, the proposed ESO-GJO still has 0.05 J of energy remaining. Figure 3a–c show that the proposed ESO-GJO increases network residual energy over the compared LSA, LEACH-IACA, and LEACH-ANT protocols.
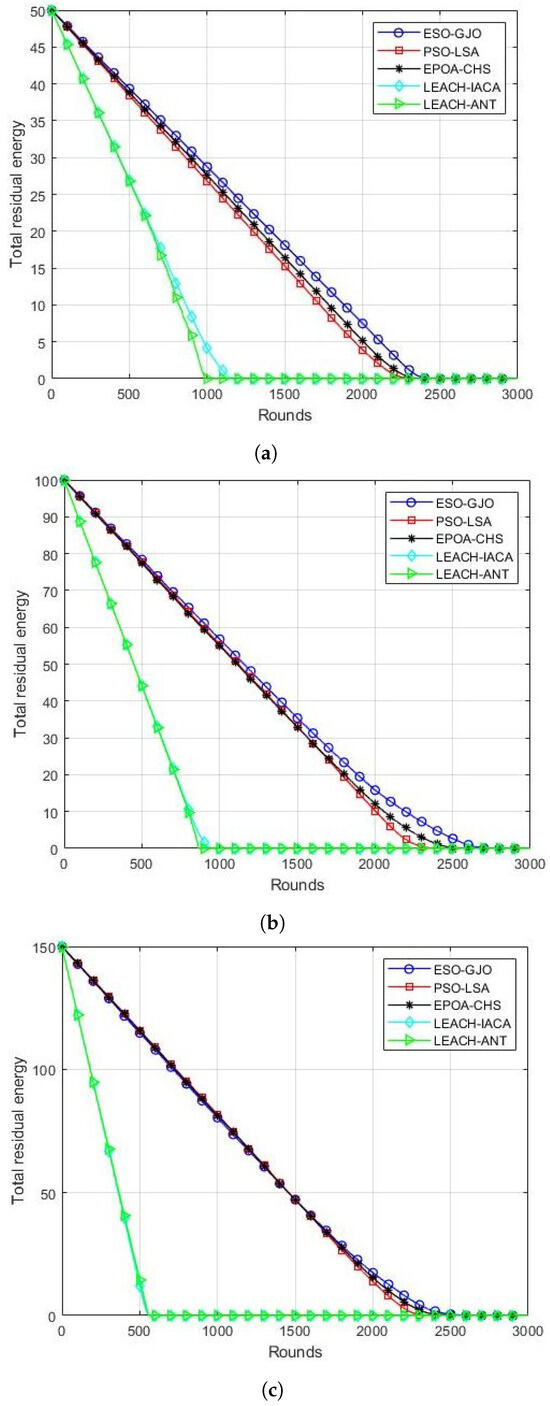
Figure 3.
Residual energy in each round. Scenarios with (a) 100 nodes; (b) 200 nodes; (c) 300 nodes.
5.3. Network Lifetime
This section compares the network lifetimes of the PSO-LSA,EPOA-CHS, LEACH-IACA, and LEACH-ANT algorithms with the suggested ESO-GJO algorithm. The time span from the sensor network’s inception to the death of the final node is referred to in this study as the network lifetime. Four different metrics, FND (First Node Death), HND (Half Nodes Death), MND (Most Nodes Death), and LND (Last Node Death), are analyzed for different protocols. Table 2 records the number of rounds in which each indicator occurs in different scenarios for ESO-GJO, PSO-LSA, EPOA-CHS, LEACH-IACA, and LEACH-ANT. Figure 4a–c shows more visually the results of ESO-GJO compared to other protocols for the four metrics in the section above for scenarios with 100 nodes, 200 nodes, and 300 nodes. Consequently, our suggested ESO-GJO can more effectively increase the network lifetime.

Table 2.
Round and lifetime.
5.4. Live Nodes Number
The total lifespan of a WSN is indicated by the number of live nodes in the network. The proposed ESO-GJO protocol and the other three protocols are compared for the number of surviving nodes every round for the scenarios of 100, 200, and 300 nodes during the course of the network lifetime in Figure 5a–c. In the case of 100 sensors, the proposed ESO-GJO algorithm extends the network lifetime by about 8.14%, 5.24%, 119.87%, and 135.76%, respectively, compared to other routing protocols. In the case of 200 sensors, the proposed ESO-GJO algorithm extends the network lifetime by about 22.3%, 8.46%, 192.2%, and 180.6%, respectively, compared to other routing protocols. In the case of 300 sensors, the proposed ESO-GJO algorithm extends the network lifetime by about 16.9%, 4.97%, 181.5%, and 363.5%, respectively, compared to the other three protocols. As a result, the ESO-GJO protocol’s suggested approach can successfully lower energy dissipation and increase the network’s lifespan.
5.5. Packet Delivery
The total number of packets that the BS has received is the definition of this network performance indicator. Regarding network throughput, the ESO-GJO approach performs better than the LSA, LEACH-IACA, and LEACH-ANT algorithms in Figure 6a (100 nodes). Specifically, ESO-GJO’s network throughput outperformed PSO-LSA,EPOA-CHS, LEACH-IACA, and LEACH-ANT by 7.89%, 5.44%, 119.3%, and 133.1%, respectively. The ESO-GJO algorithm outperforms PSO-LSA,EPOA-CHS, LEACH-IACA, and LEACH-ANT in terms of network throughput when Figure 6b (200 nodes) is considered. Specifically, ESO-GJO’s network throughput outperformed PSO-LSA,EPOA-CHS, LEACH-IACA, and LEACH-ANT by 6.62%, 4.70%, 167.36%, and 156.22%, respectively. Finally, the ESO-GJO algorithm outperforms PSO-LSA, EPOA-CHS, LEACH-IACA, and LEACH-ANT in terms of network throughput when Figure 6c (300 nodes) is considered. Specifically, ESO-GJO’s network throughput outperformed PSO-LSA, EPOA-CHS, LEACH-IACA, and LEACH-ANT by 1.02%, 0.58%, 308.26%, and 149.70%, respectively. These outcomes unequivocally demonstrate the improved network throughput that the ESO-GJO algorithm achieves in many contexts as well as its superiority over the other protocols.
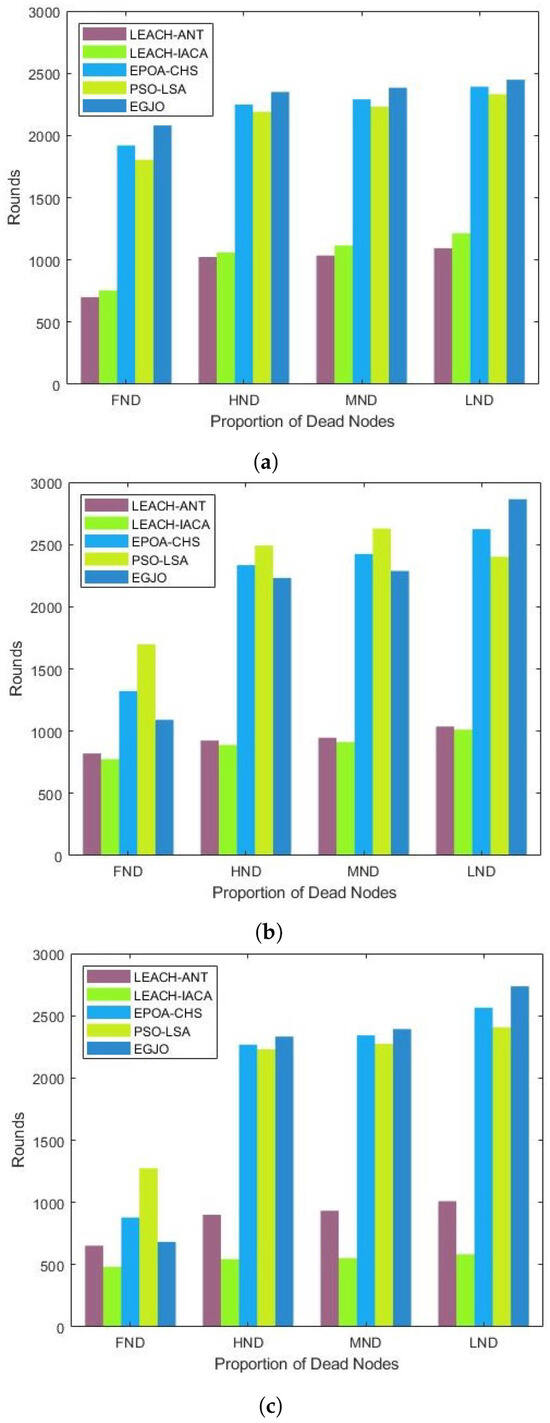
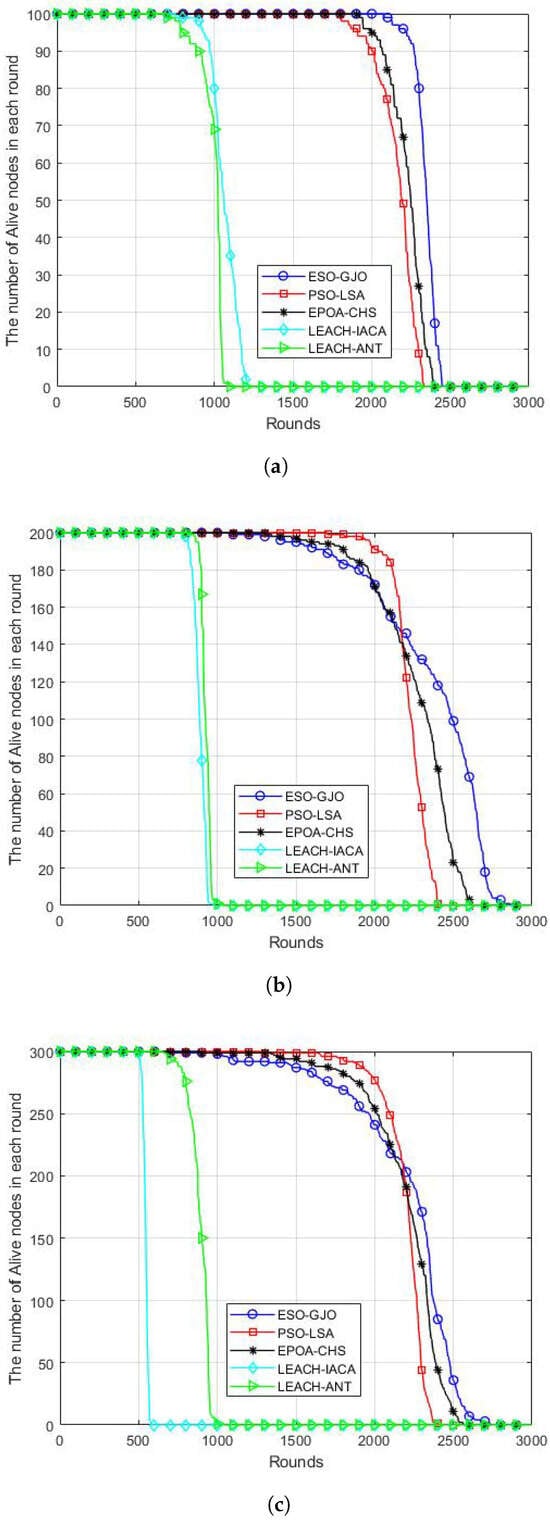
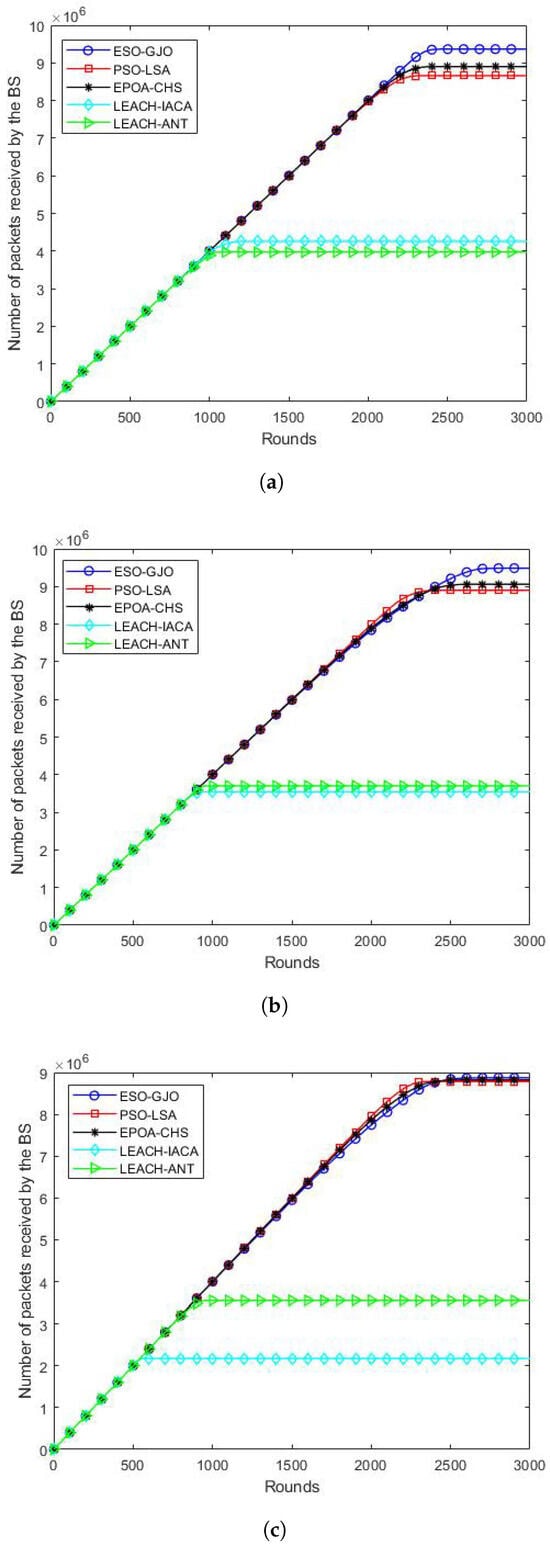

Figure 4.
Network life cycle. Scenarios with (a) 100 nodes; (b) 200 nodes; (c) 300 nodes.

Figure 5.
Live nodes number in each round. Scenarios with (a) 100 nodes; (b) 200 nodes; (c) 300 nodes.

Figure 6.
Packet delivery in each round. Scenarios with (a) 100 nodes; (b) 200 nodes; (c) 300 nodes.
5.6. Energy Consumption
This network performance metric displays the total energy utilized by all of the active nodes in the network throughout each cycle. Based on simulation results, Figure 7a–c illustrate that the suggested ESO-GJO model outperforms PSO-LSA,EPOA-CHS, LEACH-IACA, and LEACH-ANT. By taking the objective function’s energy impact into account, the ESO-GJO algorithm reduces network energy consumption and lengthens the network’s lifespan.
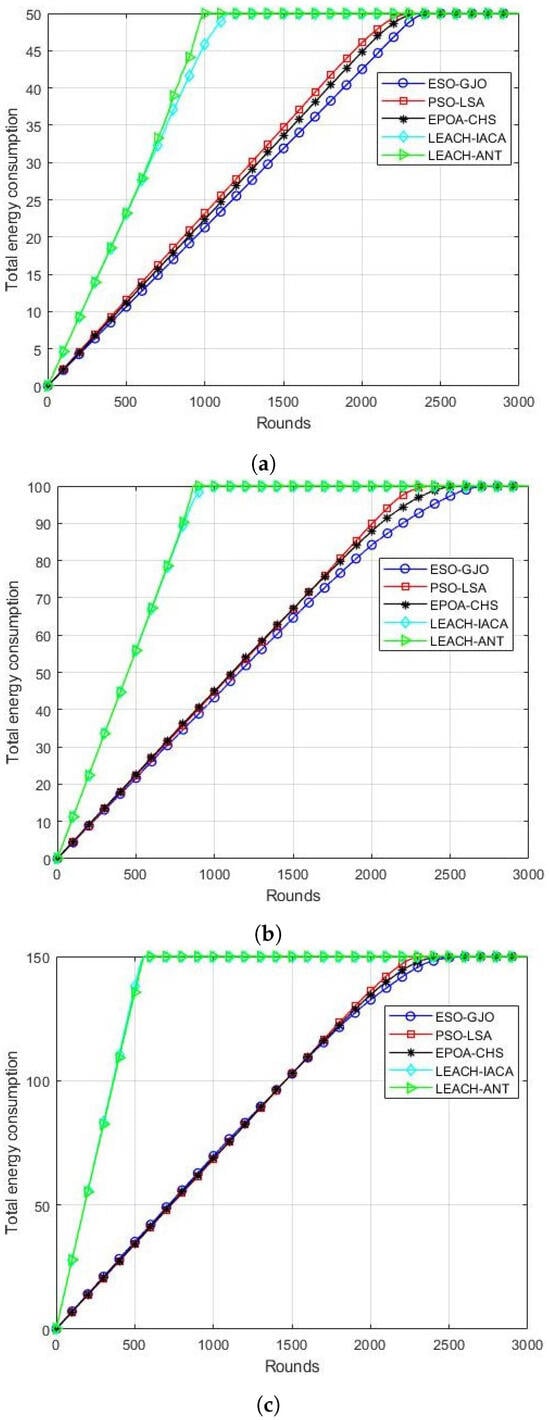
Figure 7.
Energy consumption in each round. Scenarios with (a) 100 nodes; (b) 200 nodes; (c) 300 nodes.
6. Conclusions
We have created a novel ESO-GJO method for energy-constrained WSNs in this study. In order to minimize energy usage, we construct an objective function and select the set of optimal CHs. The experimental results have been published together with a comparison of the LSA, LEACH-IACA, and LEACH-ANT algorithms that are currently in use. In the test scenarios with 100, 200, and 300 sensor nodes, respectively, the algorithm is run. The results indicate that, in comparison to alternative protocols, the strategy outlined in this study is successful in reducing network energy consumption and improving network lifetime. However, the algorithm still has limitations; the performance metric FND falls short in large-scale networks. With the aforementioned restrictions in mind, future research can build on these findings to prolong the FND emergence period for large-scale WSNs.
Author Contributions
Conceptualization, Z.W.; Methodology, Z.W.; Software, Z.W.; Validation, Z.W.; Formal analysis, Z.W. and P.X.; Investigation, Z.W.; Resources, P.X.; Data curation, Z.W.; Writing—original draft, Z.W.; Writing—review & editing, Z.W. and P.X.; Visualization, Z.W.; Supervision, Z.W.; Project administration, Z.W.; Funding acquisition, J.D. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Project of Industrial Technology Research and Development in Jilin Province (2023C031-3), Science and Technology Development Program of Jilin Province (20220508152RC).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data is contained within the article.
Conflicts of Interest
Authors Zhen Wang and Pengzhan Xing were employed by the company Changchun Guanghua Micro-Electronics Equipment Engineering Center Co., Ltd. The remaining author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Fischione, C. An Introduction to Wireless Sensor Networks; KTH Royal Institute of Technology: Stockholm, Sweden, 2014. [Google Scholar]
- BenSaleh, M.S.; Saida, R.; Kacem, Y.H.; Abid, M. Wireless Sensor Network Design Methodologies: A Survey. J. Sens. 2020, 2020, 9592836. [Google Scholar] [CrossRef]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of wireless sensor networks: An up-to-date survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef]
- Aranda, J.; Mendez, D.; Carrillo, H. Multimodal wireless sensor networks for monitoring applications: A review. J. Circuits, Syst. Comput. 2020, 29, 2030003. [Google Scholar] [CrossRef]
- Mohamed, R.E.; Saleh, A.I.; Abdelrazzak, M.; Samra, A.S. Survey on wireless sensor network applications and energy efficient routing protocols. Wirel. Pers. Commun. 2018, 101, 1019–1055. [Google Scholar] [CrossRef]
- Priyadarshi, R.; Gupta, B.; Anurag, A. Deployment techniques in wireless sensor networks: A survey, classification, challenges, and future research issues. J. Supercomput. 2020, 76, 7333–7373. [Google Scholar] [CrossRef]
- Amutha, J.; Sharma, S.; Nagar, J. WSN strategies based on sensors, deployment, sensing models, coverage and energy efficiency: Review, approaches and open issues. Wirel. Pers. Commun. 2020, 111, 1089–1115. [Google Scholar] [CrossRef]
- Croce, S.; Marcelloni, F.; Vecchio, M. Reducing power consumption in wireless sensor networks using a novel approach to data aggregation. Comput. J. 2008, 51, 227–239. [Google Scholar] [CrossRef]
- Fanian, F.; Rafsanjani, M.K. Cluster-based routing protocols in wireless sensor networks: A survey based on methodology. J. Netw. Comput. Appl. 2019, 142, 111–142. [Google Scholar] [CrossRef]
- Wang, Q.; Lin, D.; Yang, P.; Zhang, Z. An energy-efficient compressive sensing-based clustering routing protocol for WSNs. IEEE Sens. J. 2019, 19, 3950–3960. [Google Scholar] [CrossRef]
- Shafiq, M.; Ashraf, H.; Ullah, A.; Tahira, S. Systematic Literature Review on Energy Efficient Routing Schemes in WSN—A Survey. Mob. Netw. Appl. 2020, 25, 882–895. [Google Scholar] [CrossRef]
- Nakas, C.; Kandris, D.; Visvardis, G. Energy efficient routing in wireless sensor networks: A comprehensive survey. Algorithms 2020, 13, 72. [Google Scholar] [CrossRef]
- Daniel, A.; Balamurugan, K.M.; Vijay, R.; Arjun, K. Energy aware clustering with multihop routing algorithm for wireless sensor networks. Intell. Autom. Soft Comput. 2021, 29, 233–246. [Google Scholar] [CrossRef]
- Saleem, M.M.; Alabady, S.A. Improvement of the WMSNs lifetime using multi-hop clustering routing protocol. Wirel. Netw. 2022, 28, 3173–3183. [Google Scholar] [CrossRef]
- Pantazis, N.A.; Nikolidakis, S.A.; Vergados, D. Energy-efcient routing protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2013, 15, 551–591. [Google Scholar] [CrossRef]
- Behera, T.M.; Samal, U.C.; Mohapatra, S.K.; Khan, M.S.; Appasani, B.; Bizon, N.; Thounthong, P. Energy-Efficient Routing Protocols for Wireless Sensor Networks: Architectures, Strategies, and Performance. Electronics 2022, 11, 2282. [Google Scholar] [CrossRef]
- Al Aghbari, Z.; Khedr, A.M.; Osamy, W.; Arif, I.; Agrawal, D.P. Routing in wireless sensor networks using optimization techniques: A survey. Wirel. Pers. Commun. 2020, 111, 2407–2434. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-efficient commu nication protocol for wireless microsensor networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000; Volume 1, p. 10. [Google Scholar]
- Liao, Q.; Zhu, H. An Energy Balanced Clustering Algorithm Based on LEACH Protocol. Appl. Mech. Mater. 2013, 341–342, 1138–1143. [Google Scholar] [CrossRef]
- Jerbi, W.; Guermazi, A.; Trabelsi, H. O-LEACH of routing protocol for wireless sensor networks. In Proceedings of the 13th International Conference Computer Vision Graphics and Image Processing (CGiV), Beni Mellal, Morocco, 29 March–1 April 2016; pp. 399–404. [Google Scholar]
- Neto, J.H.B.; Cardoso, A.R.; Celestino, J., Jr. MH-LEACH: A Distributed Algorithm for Multi-Hop Communication. Wirel. Sens. Netw. 2014, 2014, 55–61. [Google Scholar]
- Long, C.; Liao, S.; Zou, X.; Zhou, X.; Zhang, N. An improved LEACH multi-hop routing protocol based on intelligent ant colony algorithm for wireless sensor networks. J. Inf. Comput. Sci. 2014, 11, 2747–2757. [Google Scholar] [CrossRef]
- Agarwal, T.; Kumar, D.; Prakash, N.R. Prolonging Network Lifetime Using Ant Colony Optimization Algorithm on LEACH Protocol for Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2010; pp. 634–641. [Google Scholar]
- Natesan, G.; Konda, S.; de Prado, R.P.; Wozniak, M. A Hybrid Mayfly-Aquila Optimization Algorithm Based Energy-Efficient Clustering Routing Protocol for Wireless Sensor Networks. Sensors 2022, 22, 6405. [Google Scholar] [CrossRef]
- Yao, Y.; Xie, D.; Li, Y.; Wang, C.; Li, Y. Routing Protocol for Wireless Sensor Networks Based on Archimedes Optimization Algorithm. IEEE Sens. J. 2022, 22, 15561–15573. [Google Scholar] [CrossRef]
- Wang, Z.; Duan, J.; Xu, H.; Song, X.; Yang, Y. Enhanced Pelican Optimization Algorithm for Cluster Head Selection in Heterogeneous Wireless Sensor Networks. Sensors 2023, 23, 7711. [Google Scholar] [CrossRef] [PubMed]
- Punithavathi, R.; Kurangi, C.; Balamurugan, S.P.; Pustokhina, I.V.; Pustokhin, D.A.; Shankar, K. Hybrid BWO-IACO algorithm for cluster based routing in wireless sensor networks. Comput. Mater. Contin. 2021, 69, 433–449. [Google Scholar] [CrossRef]
- Vinitha, A.; Rukmini, M.S.S.; Sunehra, D. Energy-efficient multihop routing in WSN using the hybrid optimization algorithm. Int. J. Commun. Syst. 2020, 33, e4440. [Google Scholar] [CrossRef]
- Senthil, G.A.; Raaza, A.; Kumar, N. Internet of Things Energy Efficient Cluster-Based Routing Using Hybrid Particle Swarm Optimization for Wireless Sensor Network. Wirel. Pers. Commun. 2021, 122, 2603–2619. [Google Scholar] [CrossRef]
- Mantri, D.; Prasad, N.R.; Prasad, R. Grouping of clusters for efficient data aggregation (GCEDA) in wireless sensor network. In Proceedings of the 2013 3rd IEEE International Advance Computing Conference (IACC), Ghaziabad, India, 22–23 February 2013; pp. 132–137. [Google Scholar]
- Sajwan, M.; Gosain, D.; Sharma, A.K. CAMP: Cluster aided multi-path routing protocol for wireless sensor networks. Wirel. Netw. 2019, 25, 2603–2620. [Google Scholar] [CrossRef]
- Hashim, F.A.; Hussien, A.G. Snake Optimizer: A novel meta-heuristic optimization algorithm. Knowl.-Based Syst. 2022, 242, 108320. [Google Scholar] [CrossRef]
- Chopra, N.; Ansari, M.M. Golden jackal optimization: A novel nature-inspired optimizer for engineering applications. Expert Syst. Appl. 2022, 198, 116924. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).