Secure and Robust Demand Response Using Stackelberg Game Model and Energy Blockchain
Abstract
:1. Introduction
- An incentive-based leader–follower stochastic DR model is proposed using blockchain to determine the random energy consumption of customers during peak hours, and effectively control the block mining. This model is a mixed-strategy Stackelberg game designed between the CA and customers, where customers are blockchain nodes and cooperate in block mining.
- For the mixed-strategy Stackelberg game, we prove the existence of the equilibrium point of the game based on the optimal solutions of customers and CA. The optimal solution is achieved by dividing the main Stackelberg game into multiple mixed-strategy subgames and finding a mixed equilibrium in each.
- The blockchain architecture in this work enables a secure, robust, and reliable distributed energy management system, while the processing and computational cost of the crypto algorithm is distributed across the network.
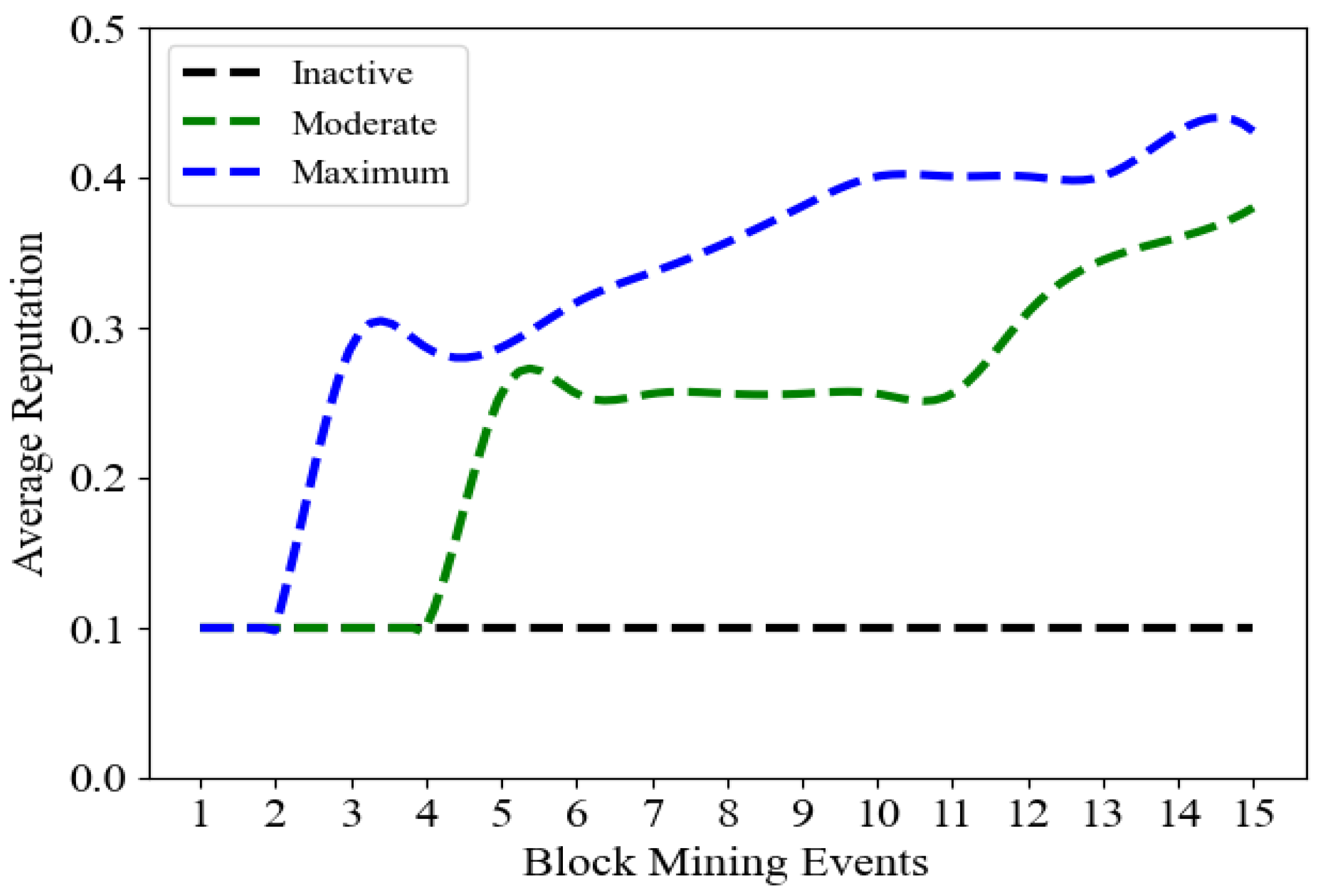
- We propose a novel consensus algorithm based on the proof of energy saving (PoES), where it selects a block miner considering the historical reputation, adequate energy resources (Availability), and DR contribution (Compliance ratio) among participants.
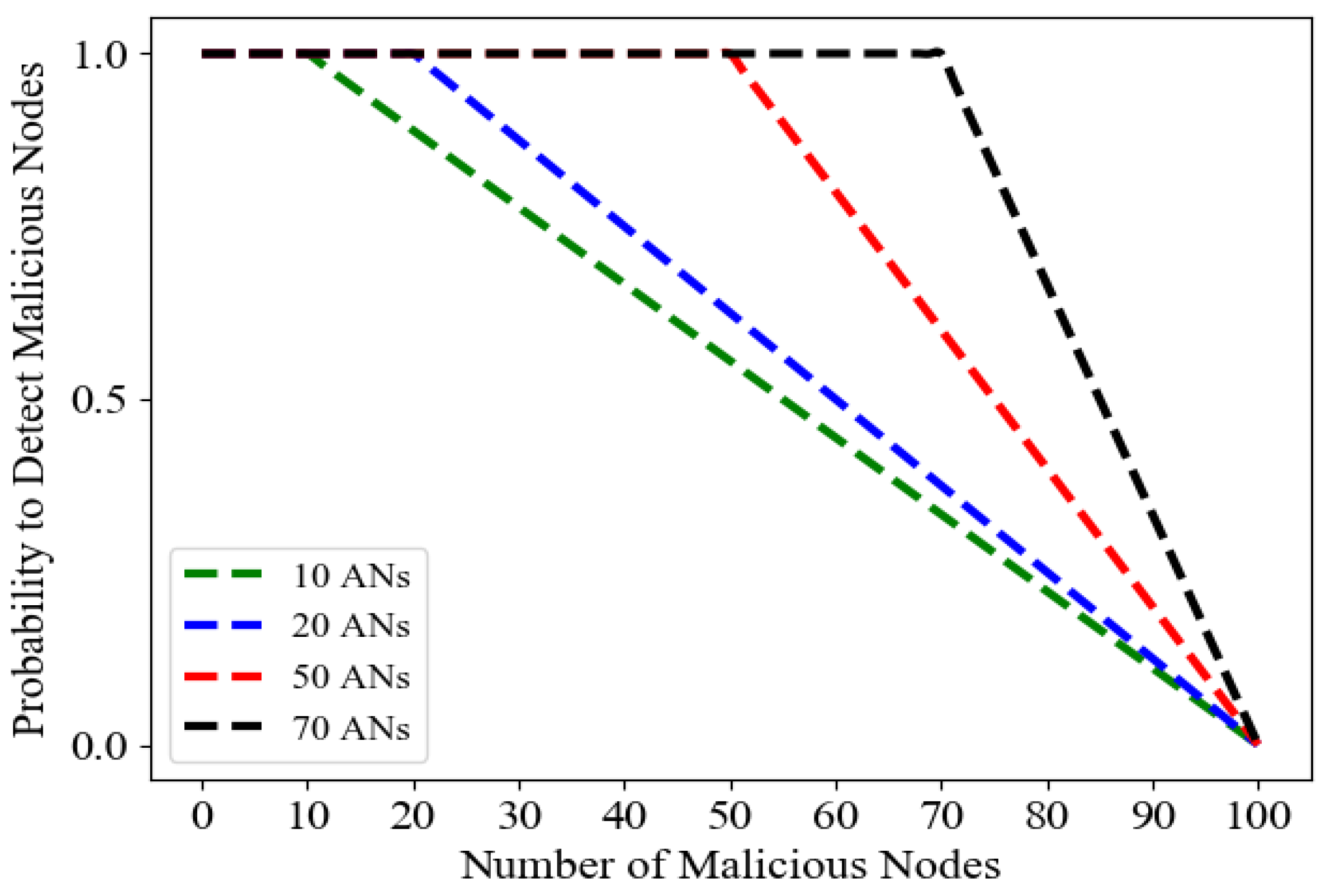
- The simulation results show that the proposed architecture is secure and robust against different cyber security attacks, and it is immune against 51% attack. We illustrate that the malicious nodes can be detected and penalized even in a small network with 10 active nodes.
2. Literature Review
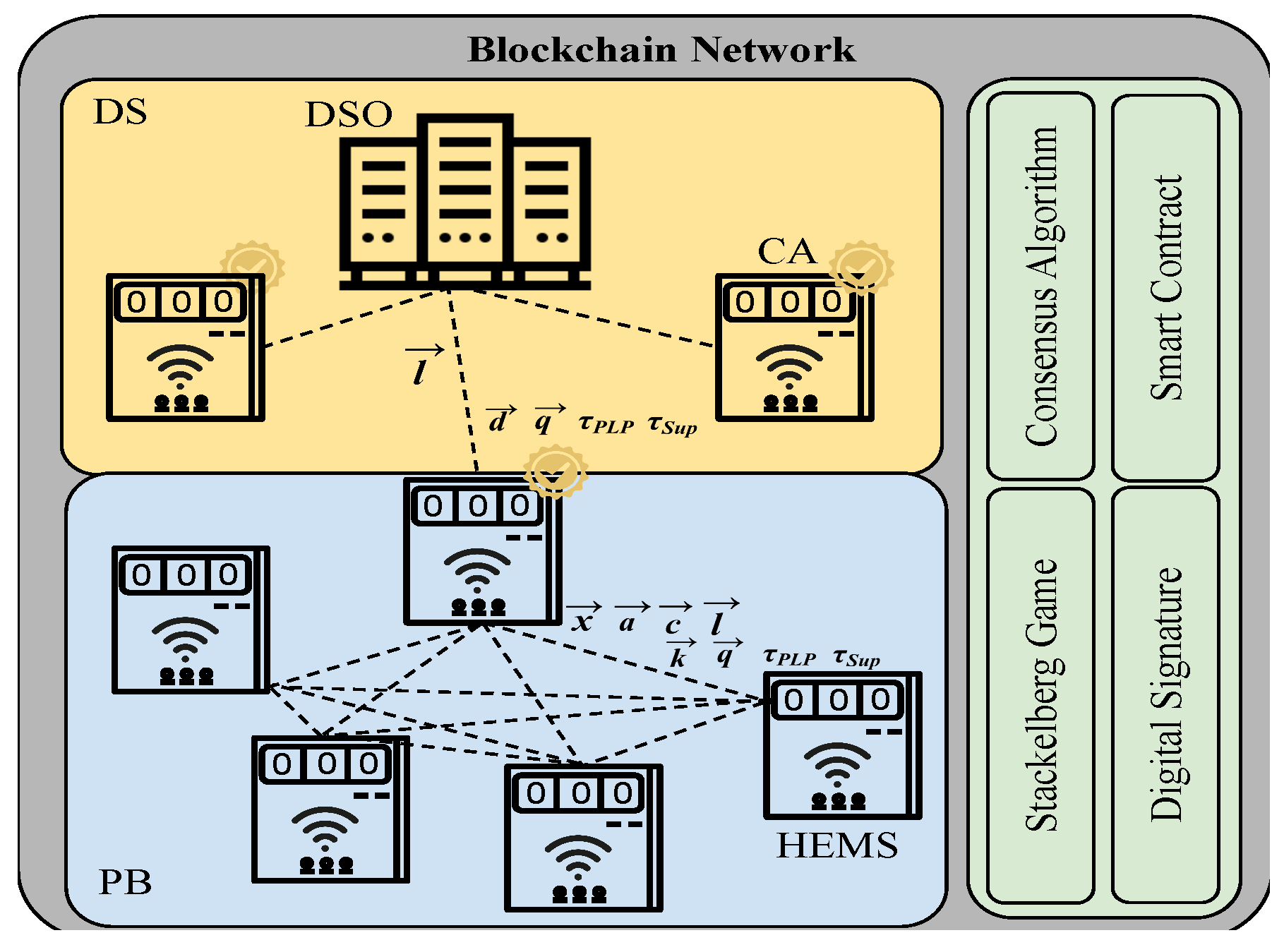
3. System Model
3.1. Network Model
3.2. Authentication Technique
4. Blockchain Design
4.1. Consensus Algorithm—Proof of Energy Saving (PoES)
4.2. Smart Contract
| Algorithm 1 Smart Contract. |
|
5. Stochastic Stackelberg Game
5.1. Game Model
5.2. Mixed-Strategy Stackelberg Game and Equilibrium Analysis
6. Security and Privacy Analysis
7. Simulation Results
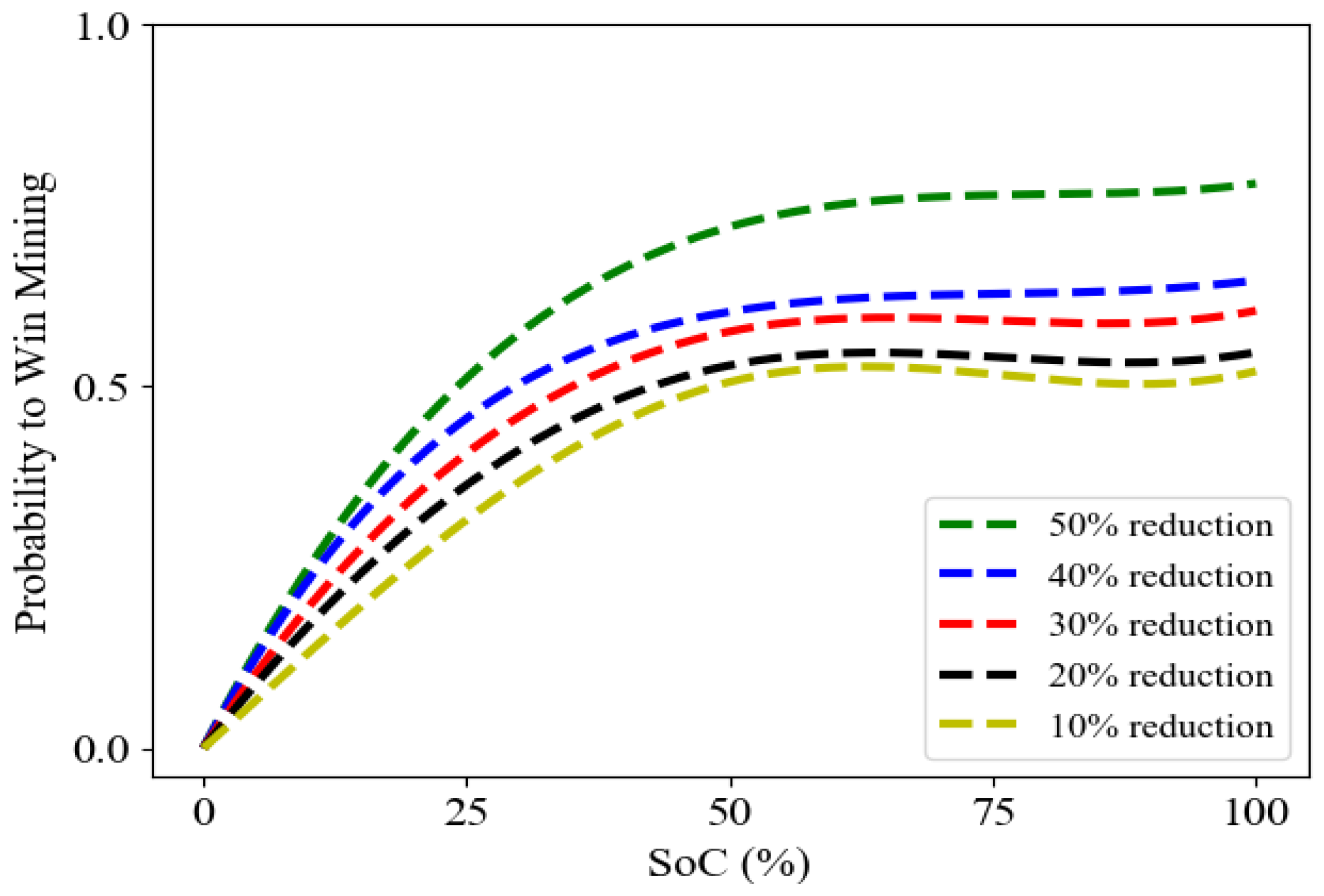
7.1. Effect of EV on Customer Decision
7.2. Blockchain Performance
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AP | Access point |
| AN | Active node |
| CA | Control agent |
| DS | Data synchronization |
| DR | Demand response |
| DSA | Digital signature algorithm |
| DER | Distributed energy resource |
| DSO | Distribution system operator |
| EV | Electric vehicle |
| HEMS | Home energy management systems |
| ID | Identity |
| IoT | Internet of Things |
| LP | Linear programming |
| LSA | Load shed availability |
| NE | Nash equilibrium |
| PLP | Peak load period |
| PV | Photovoltaic |
| PB | Private blockchain |
| PoE | Proof of energy |
| PoEC | Proof of energy consumption |
| PoEG | Proof of energy generation |
| PoEM | Proof of energy market |
| PoES | Proof of energy saving |
| PoS | Proof of stake |
| PoW | Proof of work |
| PK | Public verification key |
| SK | Secret/private signing key |
| SaaS | Software as a service |
| SE | Stackelberg equilibrium |
| SoC | States of charge |
| Sup | Supervision event |
| SVR | Support vector regression |
| VPP | Virtual power plant |
References
- Kumar, P.; Nikolovski, S.; Dong, Z. Internet of Energy Handbook; CRC Press: Boca Raton, FL, USA, 2021. [Google Scholar]
- Zhou, H.; Aral, A.; Brandić, I.; Erol-Kantarci, M. Multiagent Bayesian deep reinforcement learning for microgrid energy management under communication failures. IEEE Internet Things J. 2021, 9, 11685–11698. [Google Scholar] [CrossRef]
- Yang, Q.; Wang, H. Privacy-preserving transactive energy management for IoT-aided smart homes via blockchain. IEEE Internet Things J. 2021, 8, 11463–11475. [Google Scholar] [CrossRef]
- Erol-Kantarci, M.; Mouftah, H. Wireless sensor networks for cost-efficient residential energy management in the smart grid. IEEE Trans. Smart Grid 2011, 2, 314–325. [Google Scholar] [CrossRef]
- Razghandi, M.; Zhou, H.; Erol-Kantarci, M.; Turgut, D. Smart Home Energy Management: VAE-GAN synthetic dataset generator and Q-learning. arXiv 2023, arXiv:2305.08885. [Google Scholar] [CrossRef]
- Di Silvestre, M.; Gallo, P.; Sanseverino, E.; Sciume, G.; Zizzo, G. Aggregation and remuneration in demand response with a blockchain-based framework. IEEE Trans. Ind. Appl. 2020, 56, 4248–4257. [Google Scholar] [CrossRef]
- Thukral, M. Emergence of blockchain-technology application in peer-to-peer electrical-energy trading: A review. Clean Energy 2021, 5, 104–123. [Google Scholar] [CrossRef]
- Saxena, S.; Farag, H.; Brookson, A.; Turesson, H.; Kim, H. A Permissioned Blockchain System to Reduce Peak Demand in Residential Communities via Energy Trading: A Real-World Case Study. IEEE Access 2020, 9, 5517–5530. [Google Scholar] [CrossRef]
- Johnson, E. Insight into the World of Blockchain by Cybrosys Technologies—Cryptocurrency—Bitcoin; Scribd: San Francisco, CA, USA, 2020. [Google Scholar]
- Samadi, M.; Fattahi, J. EVSE Effectiveness in Multi-Unit Residential Buildings using Composite Optimization and Heuristic Search. IEEE Trans. Power Syst. 2023, early access, 1–13. [Google Scholar] [CrossRef]
- Fattahi, J.; Samadi, M. Effective Self-Committed V2G for Residential Complexes. Sustain. Energy Grids Netw. 2023, 35, 101114. [Google Scholar] [CrossRef]
- Almunawar, M.; Anshari, M. Empowering customers in electronic health (e–health) through social customer relationship management. Int. J. Electron. Cust. Relatsh. Manag. 2014, 8, 87–100. [Google Scholar] [CrossRef]
- Jiang, T.; Fang, H.; Wang, H. Blockchain-based internet of vehicles: Distributed network architecture and performance analysis. IEEE Internet Things J. 2018, 6, 4640–4649. [Google Scholar] [CrossRef]
- Siano, P.; De Marco, G.; Rolán, A.; Loia, V. A survey and evaluation of the potentials of distributed ledger technology for peer-to-peer transactive energy exchanges in local energy markets. IEEE Syst. J. 2019, 13, 3454–3466. [Google Scholar] [CrossRef]
- Ghorbanian, M.; Dolatabadi, S.; Siano, P.; Kouveliotis-Lysikatos, I.; Hatziargyriou, N. Methods for flexible management of blockchain-based cryptocurrencies in electricity markets and smart grids. IEEE Trans. Smart Grid 2020, 11, 4227–4235. [Google Scholar] [CrossRef]
- Asgaonkar, A.; Krishnamachari, B. Solving the buyer and seller’s dilemma: A dual-deposit escrow smart contract for provably cheat-proof delivery and payment for a digital good without a trusted mediator. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Republic of Korea, 14–17 May 2019; pp. 262–267. [Google Scholar]
- Julie, E.; Nayahi, J.; Jhanjhi, N. Blockchain Technology: Fundamentals, Applications, and Case Studies; CRC Press: Boca Raton, FL, USA, 2020. [Google Scholar]
- Dedeoglu, V.; Jurdak, R.; Putra, G.D.; Dorri, A.; Kanhere, S. A trust architecture for blockchain in IoT. In Proceedings of the 16th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Houston, TX, USA, 12–14 November 2019; pp. 190–199. [Google Scholar]
- Dorri, A.; Kanhere, S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Ye, D.; Kim, D.; Zhao, J. Toward secure blockchain-enabled internet of vehicles: Optimizing consensus management using reputation and contract theory. IEEE Trans. Veh. Technol. 2019, 68, 2906–2920. [Google Scholar] [CrossRef]
- Rouhani, S.; Deters, R. Data Trust Framework Using Blockchain Technology and Adaptive Transaction Validation. IEEE Access 2021, 9, 90379–90391. [Google Scholar] [CrossRef]
- Liu, Z.; Luong, N.; Wang, W.; Niyato, D.; Wang, P.; Liang, Y.; Kim, D. A survey on blockchain: A game theoretical perspective. IEEE Access 2019, 7, 47615–47643. [Google Scholar] [CrossRef]
- Hassan, M.; Rehmani, M.; Chen, J. VPT: Privacy Preserving Energy Trading and Block Mining Mechanism for Blockchain based Virtual Power Plants. arXiv 2021, arXiv:2102.01480. [Google Scholar]
- Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain-based mechanisms for local energy trading in smart grids. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019 ; pp. 110–114. [Google Scholar]
- Jindal, A.; Aujla, G.; Kumar, N.; Villari, M. GUARDIAN: Blockchain-based secure demand response management in smart grid system. IEEE Trans. Serv. Comput. 2019, 13, 613–624. [Google Scholar] [CrossRef]
- Chatterjee, K.; Goharshady, A.; Ibsen-Jensen, R.; Velner, Y. Ergodic mean-payoff games for the analysis of attacks in crypto-currencies. arXiv 2018, arXiv:1806.03108. [Google Scholar]
- Sapirshtein, A.; Sompolinsky, Y.; Zohar, A. Optimal selfish mining strategies in bitcoin. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 22–26 February 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 515–532. [Google Scholar]
- Cheng, L.; Yu, T. Game-theoretic approaches applied to transactions in the open and ever-growing electricity markets from the perspective of power demand response: An overview. IEEE Access 2019, 7, 25727–25762. [Google Scholar] [CrossRef]
- Ben Abdelaziz, F.; Mrad, F. Multiagent systems for modeling the information game in a financial market. Int. Trans. Oper. Res. 2023, 30, 2210–2223. [Google Scholar] [CrossRef]
- Dong, C.; Wang, Y.; Aldweesh, A.; McCorry, P.; van Moorsel, A. Betrayal, distrust, and rationality: Smart counter-collusion contracts for verifiable cloud computing. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 211–227. [Google Scholar]
- Bigi, G.; Bracciali, A.; Meacci, G.; Tuosto, E. Validation of decentralised smart contracts through game theory and formal methods. In Programming Languages with Applications to Biology and Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 142–161. [Google Scholar]
- Dimitri, N. Bitcoin mining as a contest. Ledger 2017, 2, 31–37. [Google Scholar] [CrossRef]
- Guo, Y.; Wan, Z.; Cheng, X. When blockchain meets smart grids: A comprehensive survey. High-Confid. Comput. 2022, 2, 100059. [Google Scholar] [CrossRef]
- Yu, M.; Hong, S. A real-time demand-response algorithm for smart grids: A stackelberg game approach. IEEE Trans. Smart Grid 2015, 7, 879–888. [Google Scholar] [CrossRef]
- Nekouei, E.; Alpcan, T.; Chattopadhyay, D. Game-theoretic frameworks for demand response in electricity markets. IEEE Trans. Smart Grid 2014, 6, 748–758. [Google Scholar] [CrossRef]
- Başar, T.; Jan Olsder, G. Chapter 3. Non-cooperative Finite Games: N-Person Nonzero-Sum. In Dynamic Non-Cooperative Game Theory, 2nd ed.; Society for Industrial and Applied Mathematics: Philadelphia, PA, USA, 1998; pp. 77–160. [Google Scholar]
- Jiang, Y.; Zhou, K.; Lu, X.; Yang, S. Electricity trading pricing among prosumers with game theory-based model in energy blockchain environment. Appl. Energy 2020, 271, 115239–115252. [Google Scholar] [CrossRef]
- Wang, H.; Feng, T.; Xiong, W. How can the dynamic game be integrated into blockchain-based distributed energy resources multi-agent transactions for decision-making? Energy 2022, 254, 124318. [Google Scholar] [CrossRef]
- Bai, F.; Zhang, C.; Zhang, X. Intelligent optimal demand response implemented by blockchain and cooperative game in microgrids. Int. Trans. Oper. Res. 2023. early view. [Google Scholar] [CrossRef]
- Pradhan, N.; Singh, A.; Sudha, S.; Reddy, K.; Roy, D. Performance Evaluation and Cyberattack Mitigation in a Blockchain-Enabled Peer-to-Peer Energy Trading Framework. Sensors 2023, 23, 670. [Google Scholar] [CrossRef]
- Mitrea, D.; Cioara, T.; Anghel, I. Privacy-Preserving Computation for Peer-to-Peer Energy Trading on a Public Blockchain. Sensors 2023, 23, 4640. [Google Scholar] [CrossRef] [PubMed]
- Tsao, Y.; Thanh, V. Toward blockchain-based renewable energy microgrid design considering default risk and demand uncertainty. Renew. Energy 2021, 163, 870–881. [Google Scholar] [CrossRef]
- Samadi, M.; Schriemer, H.; Ruj, S.; Erol-Kantarci, M. Energy Blockchain for Demand Response and Distributed Energy Resource Management. In Proceedings of the 2021 IEEE 12th International Conference on Communications, Control, and Computing Technologies for Smart Grids (IEEESmartGridComm), Aachen, Germany, 25–28 October 2021. [Google Scholar]
- Danish, S.; Zhang, K.; Jacobsen, H.; Ashraf, N.; Qureshi, H. Blockev: Efficient and secure charging station selection for electric vehicles. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4194–4211. [Google Scholar] [CrossRef]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Asheralieva, A.; Niyato, D. Reputation-Based Coalition Formation for Secure Self-Organized and Scalable Sharding in IoT Blockchains With Mobile-Edge Computing. IEEE Internet Things J. 2020, 7, 11830–11850. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Wu, M.; Maharjan, S.; Xie, S.; Zhang, Y. Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet Things J. 2019, 6, 4660–4670. [Google Scholar] [CrossRef]
- Chatterjee, B. An optimization formulation to compute Nash equilibrium in finite games. In Proceedings of the 2009 Proceeding of International Conference on Methods and Models in Computer Science (ICM2CS), New Delhi, India, 14–15 December 2009; pp. 1–5. [Google Scholar]
- Cunningham, L.; Baldick, R.; Baughman, M. An empirical study of applied game theory: Transmission constrained Cournot behavior. IEEE Trans. Power Syst. 2002, 17, 166–172. [Google Scholar] [CrossRef]
- Korzhyk, D.; Conitzer, V.; Parr, R. Solving Stackelberg games with uncertain observability. In Proceedings of the International Conference on Autonomous Agents and Multi-Agent Systems (AAMAS), Taipei, Taiwan, 2–6 May 2011; pp. 1013–1020. [Google Scholar]
- Marecki, J.; Tesauro, G.; Segal, R. Playing repeated stackelberg games with unknown opponents. In Proceedings of the 11th International Conference on Autonomous Agents and Multiagent Systems, Valencia, Spain, 4–8 June 2012; Volume 2, pp. 821–828. [Google Scholar]
- Conitzer, V. On Stackelberg mixed strategies. Synthese 2016, 193, 689–703. [Google Scholar] [CrossRef]
- Fattahi, J.; Wright, D.; Schriemer, H. An Energy Internet DERMS Platform using a Multi-level Stackelberg Game. Sustain. Cities Soc. 2020, 60, 102262–102288. [Google Scholar] [CrossRef]
- Watson, J. Chapter 15. Sequential Rationality and Subgame Perfection. In Strategy: An Introduction to Game Theory; Norton, W.W., Ed.; Numerade: Santa Monica, CA, USA, 2008; pp. 183–199. [Google Scholar]
- Kakutani, S. A generalization of Brouwer’s fixed point theorem. Duke Math. J. 1941, 8, 457–459. [Google Scholar] [CrossRef]
- Arora, R. Optimization: Algorithms and Applications; CRC Press: Boca Raton, FL, USA, 2015; pp. 93–133. [Google Scholar]
- Samadi, M.; Kebriaei, H.; Schriemer, H.; Erol-Kantarci, M. Stochastic Demand Response Management Using Mixed-Strategy Stackelberg Game. IEEE Syst. J. 2022, 16, 4708–4718. [Google Scholar] [CrossRef]
- Tadelis, S. Game Theory: An Introduction; Princeton University Press: Princeton, NJ, USA, 2013; pp. 101–123. [Google Scholar]
- Douceur, J. The sybil attack. In Proceedings of the International Workshop on Peer-To-Peer Systems, Cambridge, MA, USA, 7–8 March 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 251–260. [Google Scholar]
- Conti, M.; Dragoni, N.; Lesyk, V. A survey of man in the middle attacks. IEEE Commun. Surv. Tutor. 2016, 18, 2027–2051. [Google Scholar] [CrossRef]
- Chaganti, R.; Boppana, R.; Ravi, V.; Munir, K.; Almutairi, M.; Rustam, F.; Lee, E.; Ashraf, I. A comprehensive review of denial of service attacks in blockchain ecosystem and open challenges. IEEE Access 2022, 10, 96538–96555. [Google Scholar] [CrossRef]
- De Maio, V.; Uriarte, R.; Brandic, I. Energy and profit-aware proof-of-stake offloading in blockchain-based vanets. In Proceedings of the 12th IEEE/ACM International Conference on Utility and Cloud Computing, Auckland, New Zealand, 2–5 December 2019; pp. 177–186. [Google Scholar]
- O’Dwyer, K.; Malone, D. Bitcoin mining and its energy footprint. In Proceedings of the 25th IET Irish Signals & Systems Conference (ISSC’14), Limerick, Ireland, 26–27 June 2014; pp. 280–285. [Google Scholar]
- Yang, J.; Paudel, A.; Gooi, H. Compensation for power loss by a Proof-of-Stake consortium blockchain microgrid. IEEE Trans. Ind. Inform. 2020, 17, 3253–3262. [Google Scholar] [CrossRef]
- Sedlmeir, J.; Buhl, H.; Fridgen, G.; Keller, R. Recent Developments in Blockchain Technology and their Impact on Energy Consumption. arXiv 2021, arXiv:2102.07886. [Google Scholar]
- SUNLAB Group at University of Ottawa Photovoltaic Testing at Ottawa Region. 2018. Available online: http://sunlab.eecs.uottawa.ca/facilities/solar-test-sites/ (accessed on 26 July 2023).



| Component | Communication | Computational | Storage |
|---|---|---|---|
| Mixed-Strategy Stochastic Game | 10 s | 50 s | 0.011 MB |
| Smart Contract (per validation) | 5 s | 500 ns | 0.1 MB |
| Consensus (PoES) (per block validation) | 50 s | 0.5 ms | 1.5 MB |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Samadi, M.; Ruj, S.; Schriemer, H.; Erol-Kantarci, M. Secure and Robust Demand Response Using Stackelberg Game Model and Energy Blockchain. Sensors 2023, 23, 8352. https://doi.org/10.3390/s23208352
Samadi M, Ruj S, Schriemer H, Erol-Kantarci M. Secure and Robust Demand Response Using Stackelberg Game Model and Energy Blockchain. Sensors. 2023; 23(20):8352. https://doi.org/10.3390/s23208352
Chicago/Turabian StyleSamadi, Mikhak, Sushmita Ruj, Henry Schriemer, and Melike Erol-Kantarci. 2023. "Secure and Robust Demand Response Using Stackelberg Game Model and Energy Blockchain" Sensors 23, no. 20: 8352. https://doi.org/10.3390/s23208352
APA StyleSamadi, M., Ruj, S., Schriemer, H., & Erol-Kantarci, M. (2023). Secure and Robust Demand Response Using Stackelberg Game Model and Energy Blockchain. Sensors, 23(20), 8352. https://doi.org/10.3390/s23208352








