Searchable Blockchain-Based Healthcare Information Exchange System to Enhance Privacy Preserving and Data Usability
Abstract
1. Introduction
- We present the trade-off issue in HIE systems, where the robust security measures implemented for privacy preserving diminished data usability.
- We propose a blockchain-based HIE system to solve the trade-off issue in HIE, allowing for the searching of encrypted EHR information.
- We present direct examples of utilizing healthcare information stored in a blockchain-based HIE system.
2. Related Work
3. Problem Definition
3.1. System Model
3.1.1. Searchable Blockchain
3.1.2. Internet of Medical Things (IoMT)
3.1.3. EHR Owner
3.1.4. EHR Searcher
3.2. Threat Model
- Inference Attacks: Inference attacks occur when adversaries employ data analysis on anonymized data to deduce sensitive information not intended for disclosure. These attacks can disclose private information about EHR owners by exploiting correlations between various data elements.
- Linkage Attacks: More sophisticated than simple data association, linkage attacks combine multiple pieces of information to deduce additional personal details. Attackers can re-identify individuals within a dataset by linking anonymized data with external information. Such threats are particularly relevant to blockchain-based HIE systems, where anonymized EHRs can be re-identified when combined with public datasets.
- Intersection Attacks: Intersection attacks involve deducing the presence of specific individuals within a dataset by intersecting multiple datasets. For instance, the intersection of known patient hospital visit times with blockchain access logs could potentially reveal patient identity.
- Sybil Attacks: In the context of blockchain networks, Sybil attacks involve the creation of multiple fake identities by an attacker to gain disproportionate influence within the network. This can compromise the integrity of the consensus mechanism and lead to unauthorized access or manipulation of sensitive medical data.
- Replay Attacks: Replay attacks capture and replay data transmissions to create unauthorized transactions or data entries on the blockchain. This can lead to the sharing of incorrect health information or compromise the integrity of healthcare information on the blockchain.
- Man-in-the-Middle (MitM) Attacks: Blockchain technology inherently protects data in transit through encryption and digital signatures. However, MitM attacks can occur during the block propagation process before the data is recorded on the blockchain. Attackers can intercept and potentially alter propagating blocks, leading to the dissemination of incorrect information.
- Identity disclosure: Identity disclosure involves leaking information that can specifically identify an individual, such as their name, date of birth, or address. Exposing identity information can be exploited for criminality, such as credit card fraud or creating fake accounts.
- Attribute disclosure: Attribute disclosure concerns exposing sensitive attribute information like a person’s health status, religion, ethnicity, or political beliefs. Leaking attribute information can lead to discrimination or hate crimes.
- Association disclosure: Association disclosure occurs when combining two or more pieces of information reveals additional private information. For example, combining a person’s location data with their social media posts could expose details about their daily life.
- Context disclosure: Context disclosure involves leaking the context in which personal information was collected or used. For example, disclosing a person’s search history could reveal their interests or behavior patterns.
3.3. Design Goal
- Strong Data Privacy Protection: Protecting personal information is crucial for secure EHR exchange. Patient privacy must be securely guaranteed, meaning that users participating in the blockchain network should not be able to infer the identity or information of other users from the shared data. Consequently, EHR information must be stored on the blockchain in an anonymized form using secure data protection techniques.
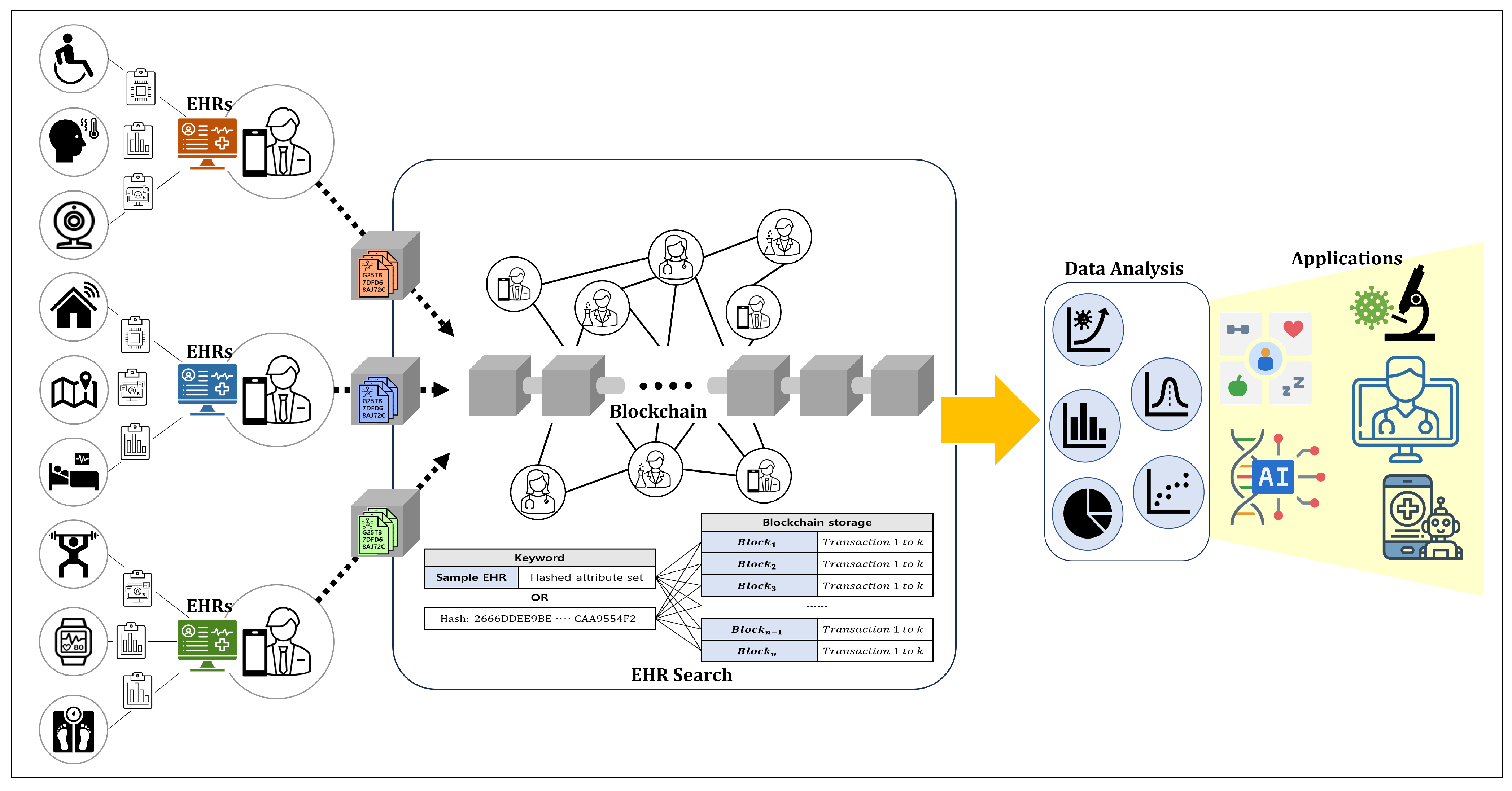
- High Data Usability: The blockchain-based HIE system requires scalability to utilize the diverse EHRs collected through a shared ledger efficiently. It should provide functionalities to utilize and process information, such as querying specific healthcare information or conducting statistical analysis from EHRs. Furthermore, it should allow independent processing of healthcare information within EHRs, enabling access to granular information. Therefore, the information in EHRs should be processed as individual transactions and stored in the blockchain.
4. Proposed Scheme
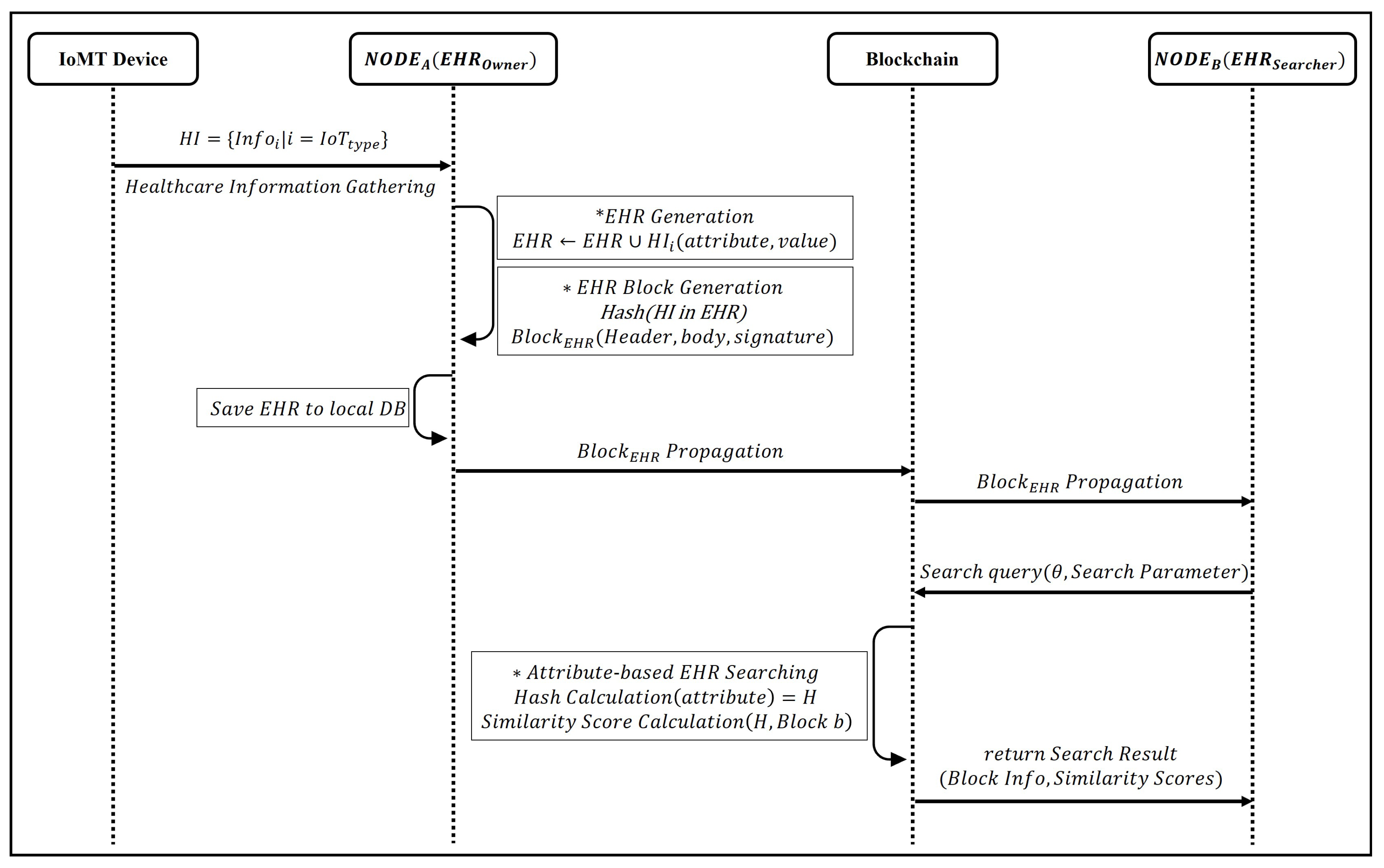
4.1. Overall Procedure of the Searchable Blockchain-Based HIE System
- EHR Sharing Process
- Users collect healthcare information generated from various IoMT devices. Each IoMT device produces different kinds of healthcare information.
- Users generate EHRs using the collected healthcare information. The composition of EHRs varies based on the sensing cycle and type of IoT devices. EHRs are used to create blocks to share healthcare information on the blockchain network or to prove ownership of healthcare information stored on the blockchain.
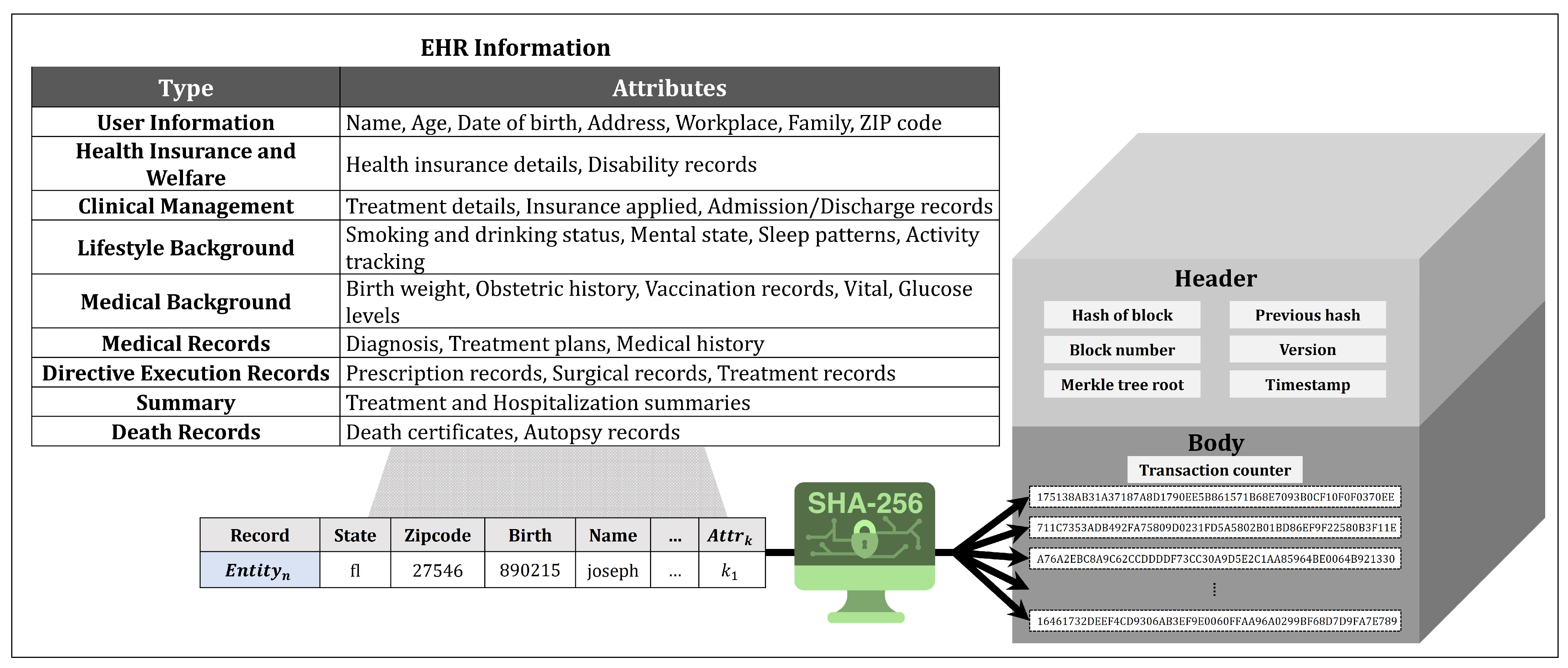
- Users generate transactions by hashing the healthcare information in the EHR. The transactions consist of hashed attributes and their hashed values. Users create transactions and sign them using their secret keys. The transactions are compiled to form EHR blocks and then shared on the blockchain network.
- The propagated EHR blocks are connected and stored in the blockchain. Users can access and utilize the healthcare information stored in the blockchain using its search functionality.
- EHR Searching Process
- Participants in the blockchain network use search parameters to search for healthcare information. Three types of parameters can be used: records, hashes of attributes, and hashes of values. The quantity of information provided as search results varies depending on the search parameter. Therefore, users must choose parameters appropriate to their desired level of results.
- The search procedure is executed based on the input search parameters. If records are input, EHR blocks with attributes and values similar to the given record are searched. The hashes of attributes and values in the record are compared with the information in EHR blocks stored in the blockchain to calculate similarity. Blocks with a similarity exceeding a user-defined threshold are returned as search results. If hashes of attributes or values are used as input, transactions matching the values are returned as search results. When searching using multiple attributes or values, similarity is calculated similarly to when using records and only results exceeding the threshold are returned.
- Users utilize the healthcare information from the search results according to their purposes. Blockchain-based HIE systems securely manage healthcare data, providing users with reliable information. The information can be employed for patient care, research, and policy-making, among other multifaceted applications.
4.2. Initialization of the Blockchain-Based HIE System
4.3. Healthcare Information Gathering
4.4. EHR and Block Generation
| Algorithm 1 EHR Generation |
|
| Algorithm 2 Block Validation |
|
4.5. EHR Searching Algorithm
| Algorithm 3 Attribute-based EHR Searching Algorithm |
|
| Algorithm 4 Hash Calculation |
|
| Algorithm 5 Similarity Score Calculation |
|
4.6. Search Result
5. Experiment and Results
5.1. Experimental Setup
5.2. Synthetic EHR
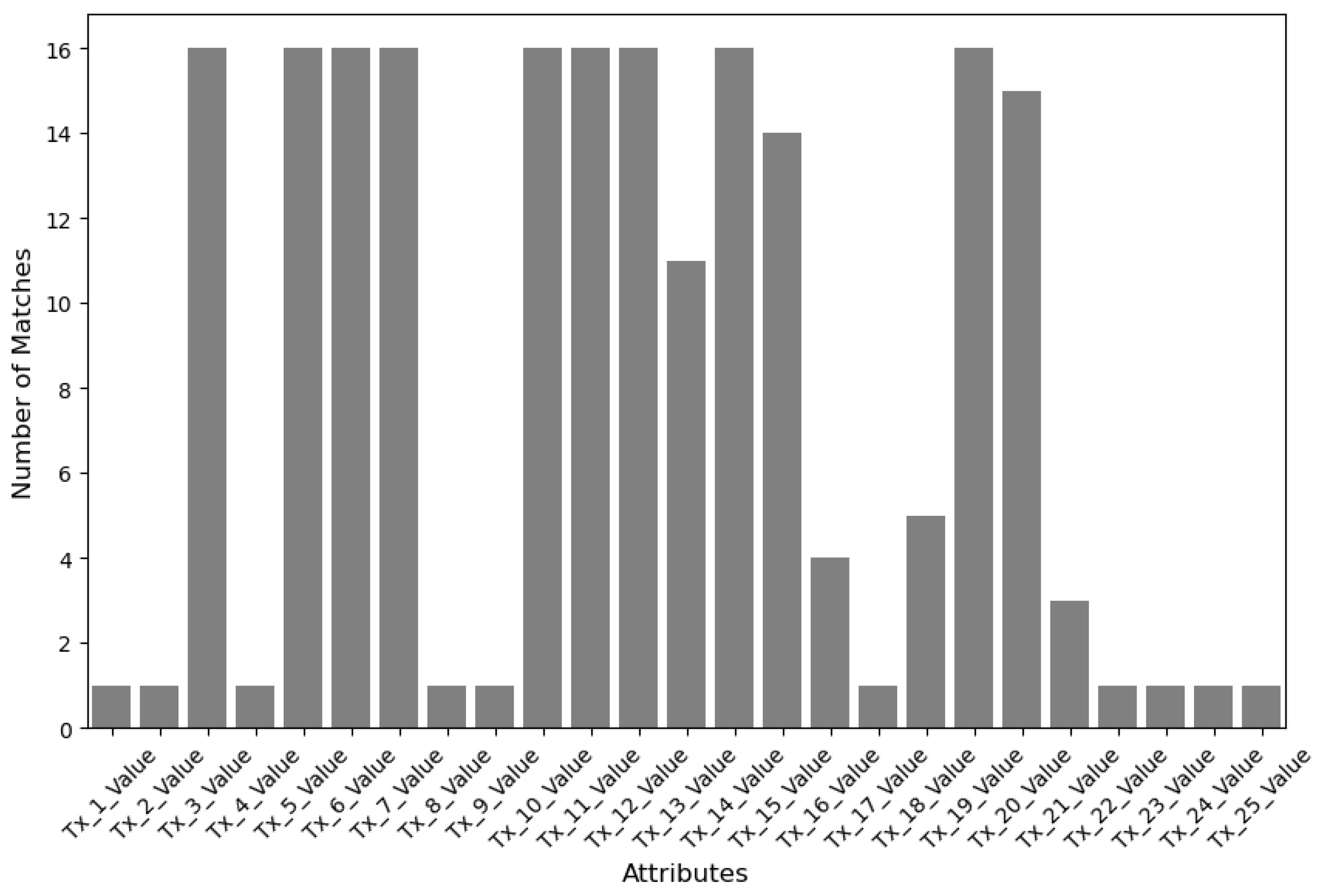
5.3. Performance Analysis
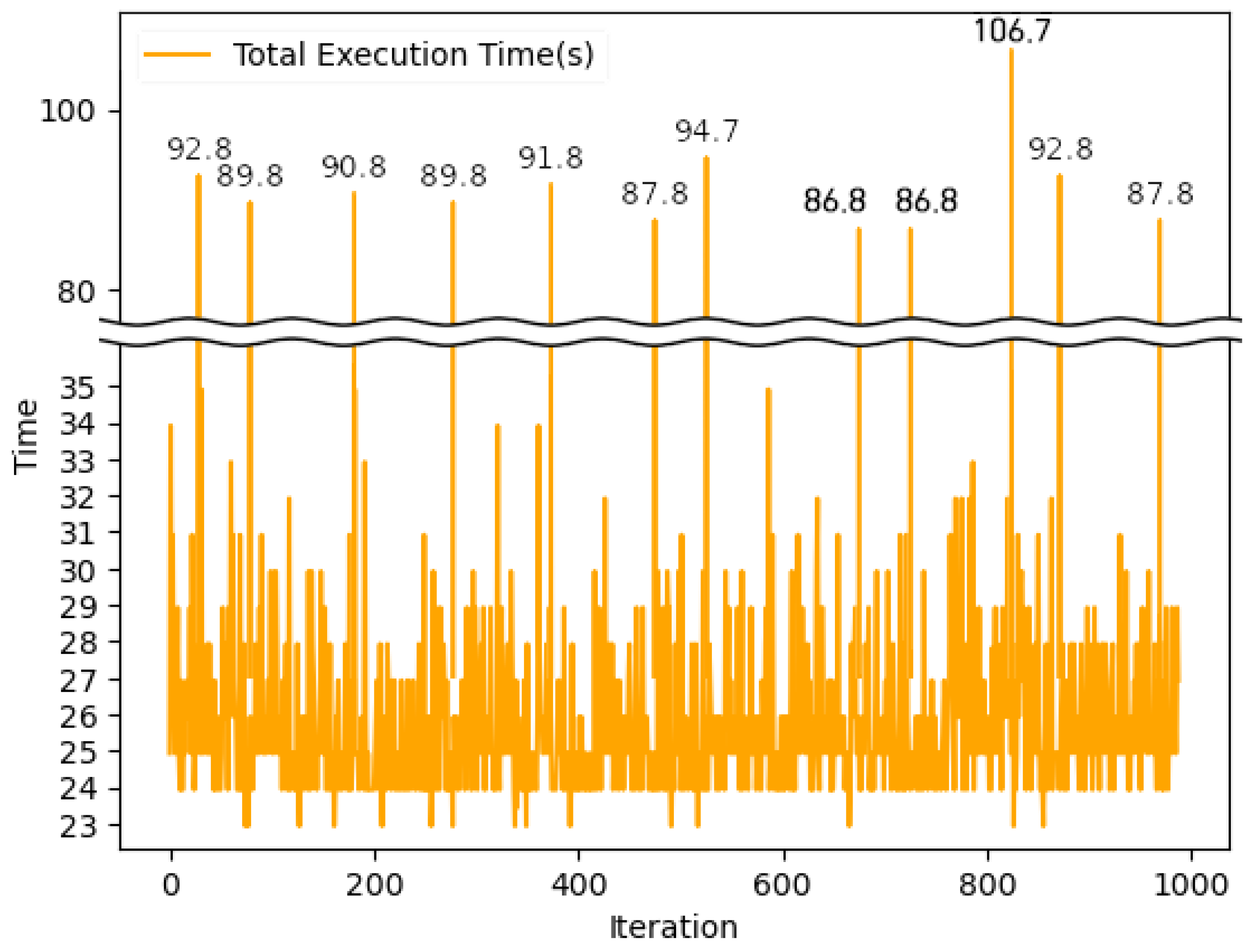
5.4. EHR Sharing Simulation
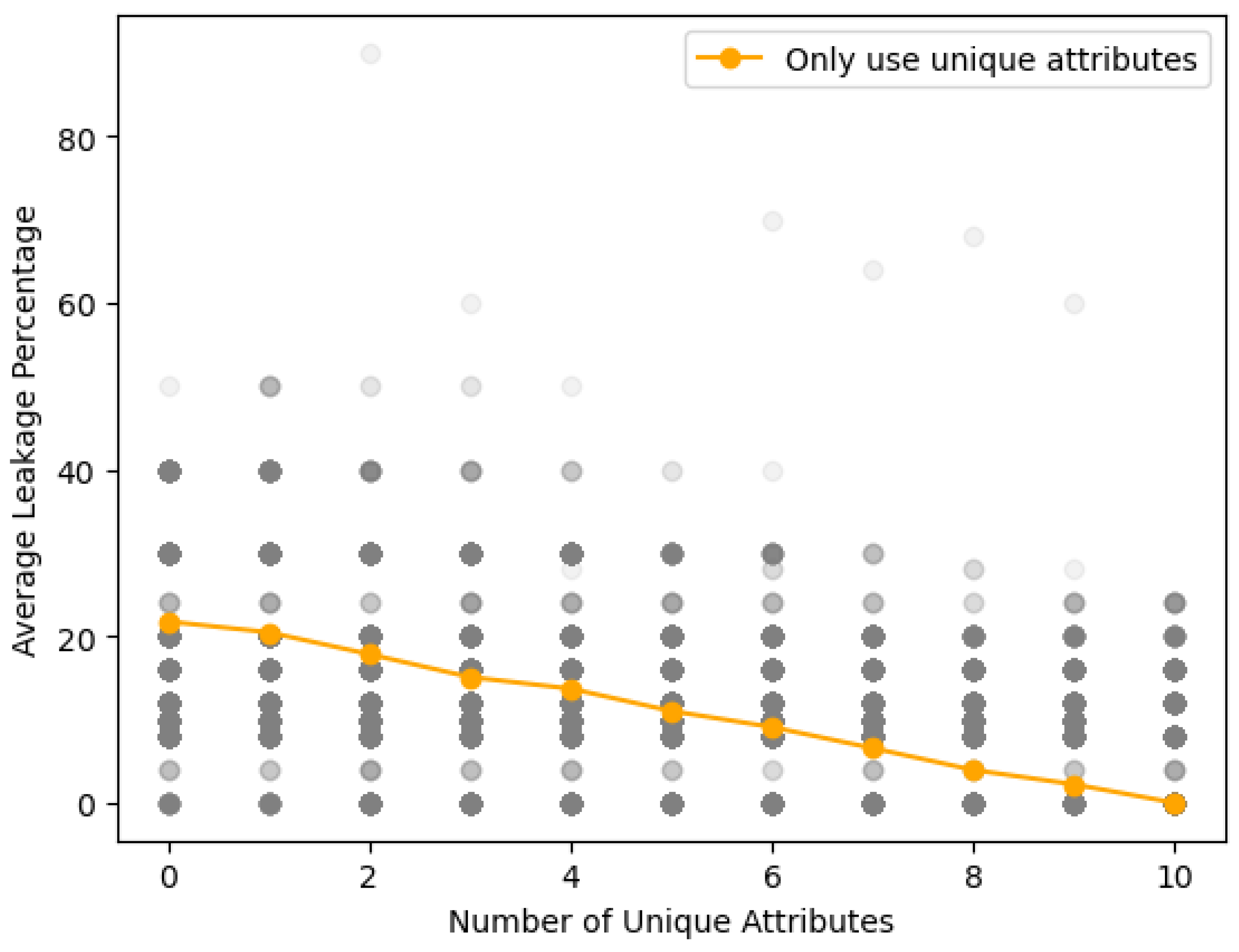
5.5. Security Performance Simulation
5.6. Security Analysis
- Inference Attacks: Blockchain technology’s transparency allows all network participants to access the stored data, posing a risk of inference attacks by malicious nodes or users with honest curiosity. In such attacks, sensitive details can be deduced from anonymized data, breaching the confidentiality of EHR. Our proposed HIE system counters this by processing EHR data attribute-wise, treating each as a separate transaction. This method minimizes the amount of that can be leakage. Consequently, even in a breach, the exposed is fragmented, offering attackers only partial information about the EHR. This strategy makes it difficult for malicious users to identify the EHR owner through inferred information or to use it for criminal purposes. The proposed system does not employ advanced encryption techniques requiring high computational complexity to improve data usability. It is also based on a public blockchain model to increase accessibility to . Therefore, security may be relatively weak compared to an HIE system based on a private blockchain model using advanced encryption technology such as homomorphic encryption. To supplement the security of the proposed system, you can consider applying data masking technology to the information to be shared or using categorized values. Alternatively, you can consider applying access control technology through a private blockchain so that only verified users can participate in the network.
- Linkage Attacks: Linkage attacks threaten patient anonymity by potentially re-identifying individuals through correlating anonymized with external data sources, risking unauthorized privacy disclosure. The proposed system refrains from storing combined or linked data that may expose personal information to prevent linkage attacks. For example, it does not aggregate location data and social media posts with blockchain-stored information, treating each data piece separately and securely to avoid unintended comprehensive disclosures about an individual’s daily activities. In combating linkage attacks, the proposed HIE system employs SHA-256, a robust anonymization technique, to hash all shared within the blockchain network. This approach effectively deals with identifiable features in the original data, ensuring anonymized does not contain direct identifiers. The unidirectional nature of SHA-256 makes it virtually impossible for attackers to reconstruct the original data from the hash value, significantly hindering their ability to infer the original . SHA-256’s high collision resistance and sensitivity mean even minor changes in input data cause drastic alterations in the hash output, further deterring the re-creation of original data. Consequently, applying SHA-256 for anonymization of in the proposed HIE system enhances the reliability and integrity of the shared data and provides a solid foundation for safeguarding user privacy.
- Intersection Attacks: Intersection attacks exploit the overlapping information among different datasets to identify individuals within the blockchain network, breaching user anonymity and privacy. Adopting privacy-preserving data aggregation methods, like secure multi-party computation (SMPC), is recommended to mitigate the risks associated with intersection attacks. We propose an HIE system that leverages blockchain technology to preserve user privacy. Before storing data, this system applies a robust anonymization or pseudonymization process using cryptographic algorithms to strip or alter personally identifiable information. This approach maintains the data’s integrity while concealing any direct identifiers. Additionally, the system employs an attribute-based approach to handle , fragmenting sensitive EHR information into multiple parts. Therefore, even if some is exposed to an attacker, it is impossible to specify the actual identity of the EHR owner because the attacker cannot reconstruct all the EHR information.
- Sybil Attacks: In the proposed HIE system, participants in the blockchain network directly create and propagate EHR blocks. As such, the system does not utilize consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) but instead employs a Practical Byzantine Fault Tolerance (PBFT)-based process to maintain the integrity of the blockchain ledger. The proposed HIE system adopts a method to limit users’ issuance and use of multiple keys as a countermeasure against Sybil attacks. It is assumed that users must authenticate their identity using their passport number or driver’s license information and a unique identifier from a country or authority to participate in the network and generate keys. Each participant, having undergone verification, is allocated a single , ensuring they possess only one vote in any PBFT consensus activity. This limitation prevents users from gaining undue influence over the ledger, protecting the network from unauthorized alterations or deletions.
- Replay Attacks and Man-in-the-Middle (MitM) Attacks: During the propagation of blocks within the blockchain network, attackers could intercept blocks, alter their data, or substitute them with incorrect information, thereby compromising the integrity and consistency of health data within the HIE system. Implementing nonce and timestamp mechanisms in blockchain transactions is essential to prevent such attacks. In the proposed HIE system, users generate blocks using their EHR data, eliminating the need for a consensus process for block creation. As a result, there is no nonce value associated with block creation. Instead, each EHR block records the creation time in its block header during the generation process. Furthermore, all transactions within the block body are digitally signed with the private key of the EHR owner who generated the block. This signature safeguards against attackers intercepting the block during propagation, modifying its content, or regenerating blocks with incorrect information. Before appending a block to the chain, participants verify the block’s information and the transaction signatures they receive, ensuring the integrity and authenticity of the data. These mechanisms provide the uniqueness of each transaction and confine its validity to a specific timeframe, safeguarding the system against unauthorized or duplicate transactions.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| HIE | Healthcare Information Exchange |
| IoMT | Internet of Medical Things |
| EHR | Electronic Health Records |
| ABAC | Attribute-Based Access Control |
| PK | Public Key |
| SK | Secret Key |
| ECC | Elliptic Curve Cryptography |
References
- Heart, T.; Ben-Assuli, O.; Shabtai, I. A review of PHR, EMR and EHR integration: A more personalized healthcare and public health policy. Health Policy Technol. 2017, 6, 20–25. [Google Scholar] [CrossRef]
- Pedersen, C.A.; Schneider, P.J.; Santell, J.P. ASHP national survey of pharmacy practice in hospital settings: Prescribing and transcribing—2001. Am. J. Health-Syst. Pharm. 2001, 58, 2251–2266. [Google Scholar] [CrossRef] [PubMed]
- Rajpurkar, P.; Chen, E.; Banerjee, O.; Topol, E.J. AI in health and medicine. Nat. Med. 2022, 28, 31–38. [Google Scholar] [CrossRef] [PubMed]
- Vishnu, S.; Ramson, S.J.; Jegan, R. Internet of medical things (IoMT)—An overview. In Proceedings of the 2020 5th International Conference on Devices, Circuits and Systems (ICDCS), Coimbatore, India, 5–6 March 2020; pp. 101–104. [Google Scholar]
- Fernández-Alemán, J.L.; Señor, I.C.; Lozoya, P.Á.O.; Toval, A. Security and privacy in electronic health records: A systematic literature review. J. Biomed. Inform. 2013, 46, 541–562. [Google Scholar] [CrossRef] [PubMed]
- Tian, S.; Yang, W.; Le Grange, J.M.; Wang, P.; Huang, W.; Ye, Z. Smart healthcare: Making medical care more intelligent. Glob. Health J. 2019, 3, 62–65. [Google Scholar] [CrossRef]
- Price, W.N.; Cohen, I.G. Privacy in the age of medical big data. Nat. Med. 2019, 25, 37–43. [Google Scholar] [CrossRef] [PubMed]
- Menachemi, N.; Rahurkar, S.; Harle, C.A.; Vest, J.R. The benefits of health information exchange: An updated systematic review. J. Am. Med. Inform. Assoc. 2018, 25, 1259–1265. [Google Scholar] [CrossRef] [PubMed]
- Dixon, B.E.; Cusack, C.M. Measuring the value of health information exchange. In Health Information Exchange; Elsevier: Amsterdam, The Netherlands, 2023; pp. 379–398. [Google Scholar]
- Hatzivasilis, G.; Soultatos, O.; Ioannidis, S.; Verikoukis, C.; Demetriou, G.; Tsatsoulis, C. Review of Security and Privacy for the Internet of Medical Things (IoMT). In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini, Greece, 29–31 May 2019; pp. 457–464. [Google Scholar] [CrossRef]
- Gong, T.; Huang, H.; Li, P.; Zhang, K.; Jiang, H. A Medical Healthcare System for Privacy Protection Based on IoT. In Proceedings of the 2015 Seventh International Symposium on Parallel Architectures, Algorithms and Programming (PAAP), Nanjing, China, 12–14 December 2015; pp. 217–222. [Google Scholar] [CrossRef]
- Zhuang, Y.; Sheets, L.R.; Chen, Y.W.; Shae, Z.Y.; Tsai, J.J.; Shyu, C.R. A Patient-Centric Health Information Exchange Framework Using Blockchain Technology. IEEE J. Biomed. Health Inform. 2020, 24, 2169–2176. [Google Scholar] [CrossRef] [PubMed]
- Chandrasekhar, S.; Ibrahim, A.; Singhal, M. A novel access control protocol using proxy signatures for cloud-based health information exchange. Comput. Secur. 2017, 67, 73–88. [Google Scholar] [CrossRef]
- Srivastava, G.; Parizi, R.M.; Dehghantanha, A.; Choo, K.K.R. Data sharing and privacy for patient iot devices using blockchain. In Proceedings of the International Conference on Smart City and Informatization, Guangzhou, China, 12–15 November 2019; pp. 334–348. [Google Scholar]
- Esmaeilzadeh, P.; Mirzaei, T. The Potential of Blockchain Technology for Health Information Exchange: Experimental Study from Patients’ Perspectives. J. Med. Internet Res. 2019, 21, e14184. [Google Scholar] [CrossRef] [PubMed]
- Bernal Bernabe, J.; Canovas, J.L.; Hernandez-Ramos, J.L.; Torres Moreno, R.; Skarmeta, A. Privacy-Preserving Solutions for Blockchain: Review and Challenges. IEEE Access 2019, 7, 164908–164940. [Google Scholar] [CrossRef]
- Chen, L.; Lee, W.K.; Chang, C.C.; Choo, K.K.R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Niu, S.; Chen, L.; Wang, J.; Yu, F. Electronic Health Record Sharing Scheme with Searchable Attribute-Based Encryption on Blockchain. IEEE Access 2020, 8, 7195–7204. [Google Scholar] [CrossRef]
- Li, F.; Liu, K.; Zhang, L.; Huang, S.; Wu, Q. EHRChain: A Blockchain-Based EHR System Using Attribute-Based and Homomorphic Cryptosystem. IEEE Trans. Serv. Comput. 2022, 15, 2755–2765. [Google Scholar] [CrossRef]
- Han, J.; Li, Z.; Liu, J.; Wang, H.; Xian, M.; Zhang, Y.; Chen, Y. Attribute-Based Access Control Meets Blockchain-Enabled Searchable Encryption: A Flexible and Privacy-Preserving Framework for Multi-User Search. Electronics 2022, 11, 2536. [Google Scholar] [CrossRef]
- Ali, A.; Al-rimy, B.A.S.; Alsubaei, F.S.; Almazroi, A.A.; Almazroi, A.A. HealthLock: Blockchain-Based Privacy Preservation Using Homomorphic Encryption in Internet of Things Healthcare Applications. Sensors 2023, 23, 6762. [Google Scholar] [CrossRef] [PubMed]
- Thantharate, P.; Thantharate, A. ZeroTrustBlock: Enhancing Security, Privacy, and Interoperability of Sensitive Data through ZeroTrust Permissioned Blockchain. Big Data Cogn. Comput. 2023, 7, 165. [Google Scholar] [CrossRef]
- Heng, Y.; Armknecht, F.; Chen, Y.; Schnell, R. On the effectiveness of graph matching attacks against privacy-preserving record linkage. PLoS ONE 2022, 17, e0267893. [Google Scholar] [CrossRef] [PubMed]
- Vidanage, A.; Ranbaduge, T.; Christen, P.; Schnell, R. Efficient pattern mining based cryptanalysis for privacy-preserving record linkage. In Proceedings of the 2019 IEEE 35th International Conference on Data Engineering (ICDE), Macao, China, 8–11 April 2019; pp. 1698–1701. [Google Scholar]
- Vidanage, A.; Christen, P.; Ranbaduge, T.; Schnell, R. A graph matching attack on privacy-preserving record linkage. In Proceedings of the 29th ACM International Conference on Information & Knowledge Management, Virtual Event, Ireland, 19–23 October 2020; pp. 1485–1494. [Google Scholar]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
- Hussien, H.M.; Yasin, S.M.; Udzir, N.I.; Ninggal, M.I.H. Blockchain-based access control scheme for secure shared personal health records over decentralised storage. Sensors 2021, 21, 2462. [Google Scholar] [CrossRef] [PubMed]
- Lee, S.; Kim, J.; Kwon, Y.; Kim, T.; Cho, S. Privacy Preservation in Patient Information Exchange Systems Based on Blockchain: System Design Study. J. Med. Internet Res. 2022, 24, e29108. [Google Scholar] [CrossRef] [PubMed]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25 July 2016; Volume 310, pp. 1–4. [Google Scholar]
- Apache CouchDB. 2019. Available online: http://couchdb.apache.org/ (accessed on 17 February 2022).
- Synthea’s COVID-19 Patient Synthetic Data. 2020. Available online: https://synthea.mitre.org/ (accessed on 12 July 2023).


| Category | Fields | Description |
|---|---|---|
| Identification | ID | Unique identifiers for patients. |
| SSN | Social Security Numbers. | |
| Drivers | Driver’s license numbers. | |
| Passport | Passport numbers. | |
| Personal Information | Birthdate | The birth dates of patients. |
| Deathdate | Dates of death, if applicable. | |
| Prefix, First, Last, Suffix | Parts of the patient’s name. | |
| Maiden | Maiden names, if applicable. | |
| Marital | Marital status. | |
| Demographics | Race, Ethnicity, Gender, Birthplace | Demographic details. |
| Address | Address, City, State, County, ZIP | Address details. |
| Latitude, Longitude | Geographical coordinates. | |
| Healthcare Details | Healthcare Expenses and Coverage | Financial details related to healthcare. |
| Number of Attributes | Shortest Elapsed Time (ms) | Longest Elapsed Time (ms) | Average Elapsed Time (ms) | Average Found Records |
|---|---|---|---|---|
| 1 | 8.09 ms | 2632.05 ms | 98.65 ms | 1 |
| 2 | 8.21 ms | 2693.75 ms | 105.96 ms | 2.4 |
| 3 | 9.19 ms | 1957.81 ms | 115.41 ms | 1.26 |
| 4 | 10.52 ms | 2200.12 ms | 123.65 ms | 1.27 |
| 5 | 12.46 ms | 2018.36 ms | 140.73 ms | 266.41 |
| 6 | 13 ms | 3101.46 ms | 145.6 ms | 266.13 |
| 7 | 13.5 ms | 2623.53 ms | 157.53 ms | 402.94 |
| 8 | 15.53 ms | 1919.72 ms | 168.18 ms | 266.16 |
| 9 | 16.76 ms | 2475.46 ms | 180.43 ms | 266.44 |
| 10 | 17.96 ms | 2567.42 ms | 187.7 ms | 407.75 |
| 11 | 18.57 ms | 1862.05 ms | 200.53 ms | 406.39 |
| 12 | 20.27 ms | 2702.53 ms | 217.24 ms | 1151.62 |
| 13 | 20.84 ms | 2960.34 ms | 224.84 ms | 925.76 |
| 14 | 22.15 ms | 2311.72 ms | 235.41 ms | 2380.34 |
| 15 | 23.4 ms | 3361.02 ms | 245.36 ms | 3974.07 |
| 16 | 24.07 ms | 2362.89 ms | 248.45 ms | 2218.18 |
| 17 | 24.96 ms | 3082.44 ms | 266.1 ms | 2218.18 |
| 18 | 25.38 ms | 2451.37 ms | 266.68 ms | 801.86 |
| 19 | 26.35 ms | 2559.06 ms | 275.97 ms | 2247.65 |
| 20 | 27.16 ms | 2994.91 ms | 285.51 ms | 2483.63 |
| 21 | 28.03 ms | 3036.52 ms | 295.47 ms | 1308.84 |
| 22 | 28.51 ms | 2482.71 ms | 299 ms | 1308.84 |
| 23 | 30.61 ms | 2290.12 ms | 311.63 ms | 484.46 |
| 24 | 30.99 ms | 3518.19 ms | 324.51 ms | 484.47 |
| 25 | 32.53 ms | 2759.03 ms | 331.23 ms | 485.78 |
| Unique Attributes | Normal Attributes |
|---|---|
| ‘DRIVERS’, ‘ADDRESS’, ‘PASSPORT’, ‘LAT’, ‘LON’, ‘MAIDEN’, ‘SSN’, ‘HEALTHCARE COVERAGE’, ‘ID’, ‘HEALTHCARE EXPENSES’ | ‘MARITAL’, ‘COUNTY’, ‘CITY’, ‘BIRTHDATE’, ‘STATE’, ‘LAST’, ‘ETHNICITY’, ‘FIRST’, ‘RACE’, ‘BIRTHPLACE’, ‘ZIP’, ‘GENDER’, ‘PREFIX’, ‘SUFFIX’, ‘DEATHDATE’ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.; Kim, Y.; Cho, S. Searchable Blockchain-Based Healthcare Information Exchange System to Enhance Privacy Preserving and Data Usability. Sensors 2024, 24, 1582. https://doi.org/10.3390/s24051582
Lee S, Kim Y, Cho S. Searchable Blockchain-Based Healthcare Information Exchange System to Enhance Privacy Preserving and Data Usability. Sensors. 2024; 24(5):1582. https://doi.org/10.3390/s24051582
Chicago/Turabian StyleLee, Sejong, Yushin Kim, and Sunghyun Cho. 2024. "Searchable Blockchain-Based Healthcare Information Exchange System to Enhance Privacy Preserving and Data Usability" Sensors 24, no. 5: 1582. https://doi.org/10.3390/s24051582
APA StyleLee, S., Kim, Y., & Cho, S. (2024). Searchable Blockchain-Based Healthcare Information Exchange System to Enhance Privacy Preserving and Data Usability. Sensors, 24(5), 1582. https://doi.org/10.3390/s24051582