Cooperative Friendly Jamming Techniques for Drone-Based Mobile Secure Zone
Abstract
:1. Introduction
- A cooperative friendly jamming technique is proposed to flexibly form a secure zone for confidential communication of lightweight mobile devices.
- The effect of the proposed CFJ-DMZ is analyzed through simulation and proved through field test in the implemented test bed.
2. Related Work
2.1. Introduction to Friendly Jamming
2.2. Friendly Jamming Security Model
2.3. Friendly Jamming Security Model for Mobility Environment
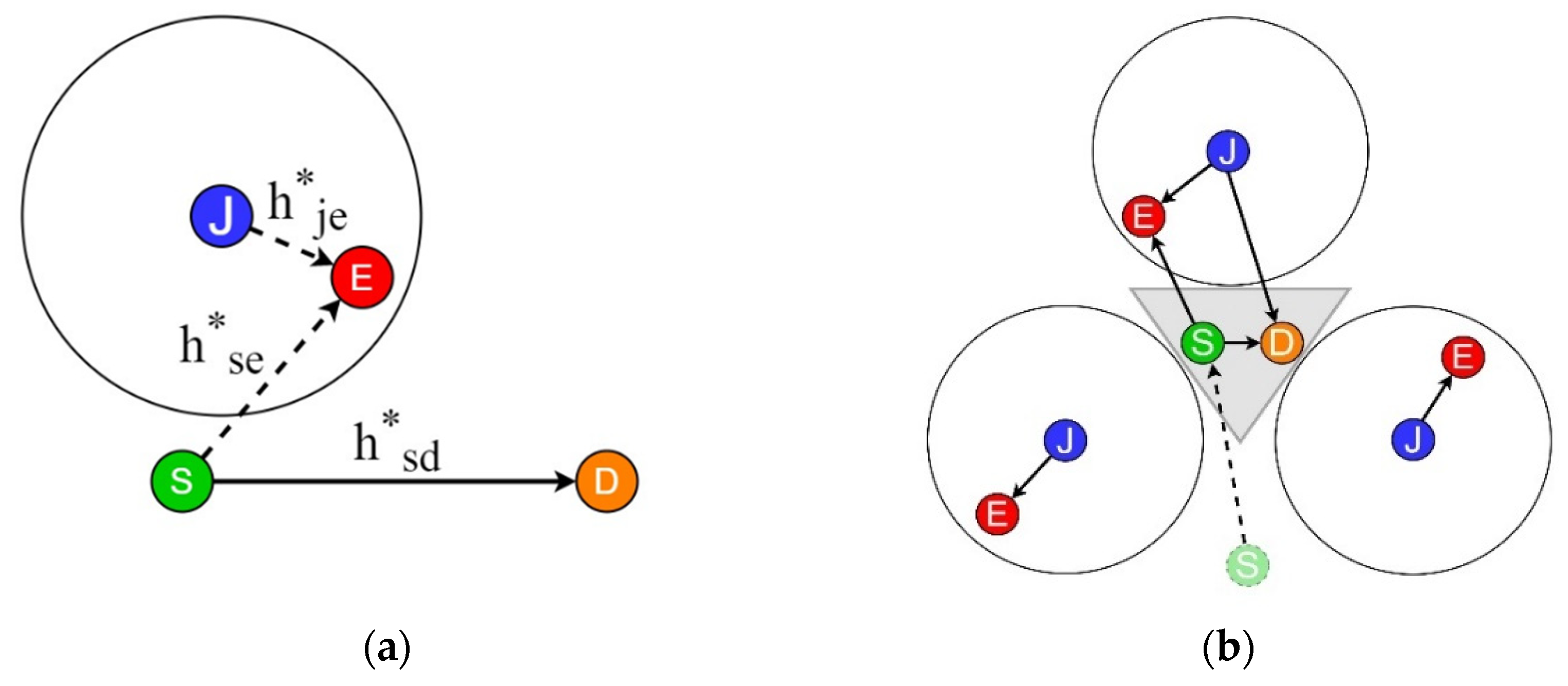
3. Friendly Jamming Technique
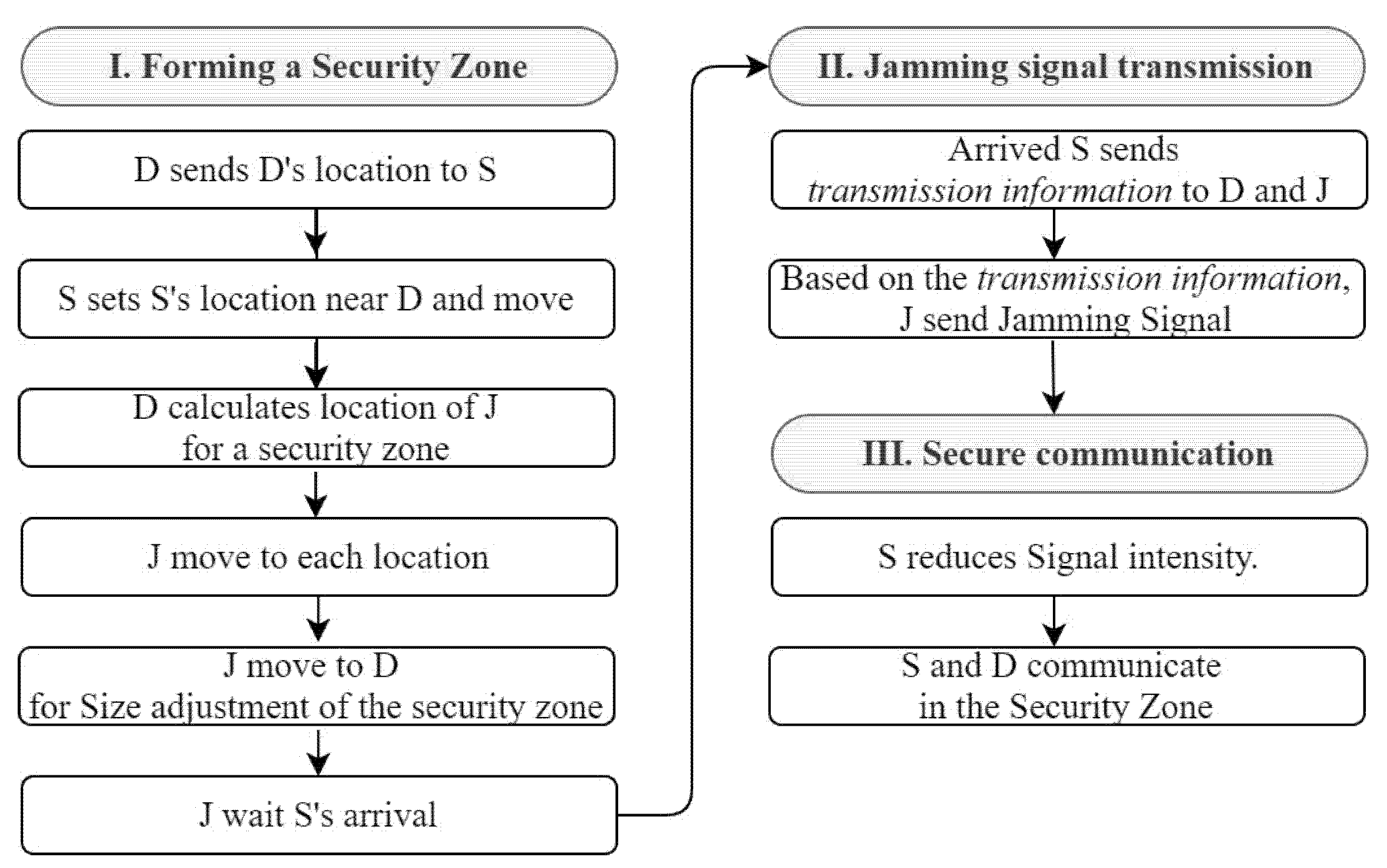
4. CFJ-DMZ Model
5. Experiment
5.1. Simulation
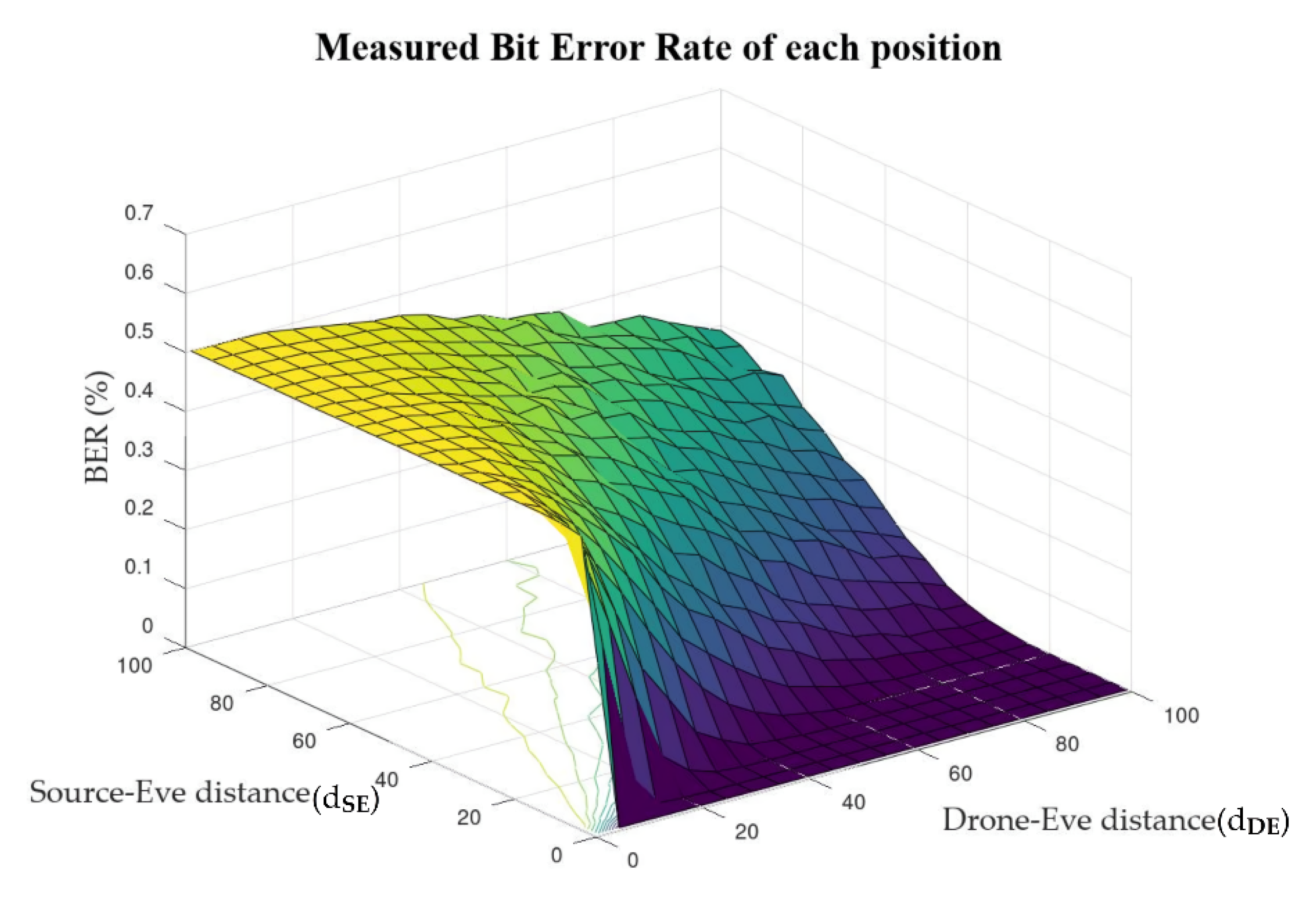
5.1.1. Effect of Friendly Jamming
5.1.2. Evaluation Environments
| Algorithm 1. Pseudo-code for BER measurement of eve. | |
| 1: | |
| 2: | |
| 3: | |
| 4: | |
| 5: | |
| 6: | |
| 7: | |
| 8: | ) |
| 9: | |
| 10: | |
| 11: | |
| 12: | |
| 13: | |
| 14: | |
| 15: | |
| 16: | |
| 17: | |
| 18: | |
| 19 | |
| 20: | |
| 21: | |
| 22: | |
| 23: | |
| 24: | |
5.1.3. Results of Simulation
5.2. Field Experiment
5.2.1. Effect of Friendly Jamming
5.2.2. Experimental Settings
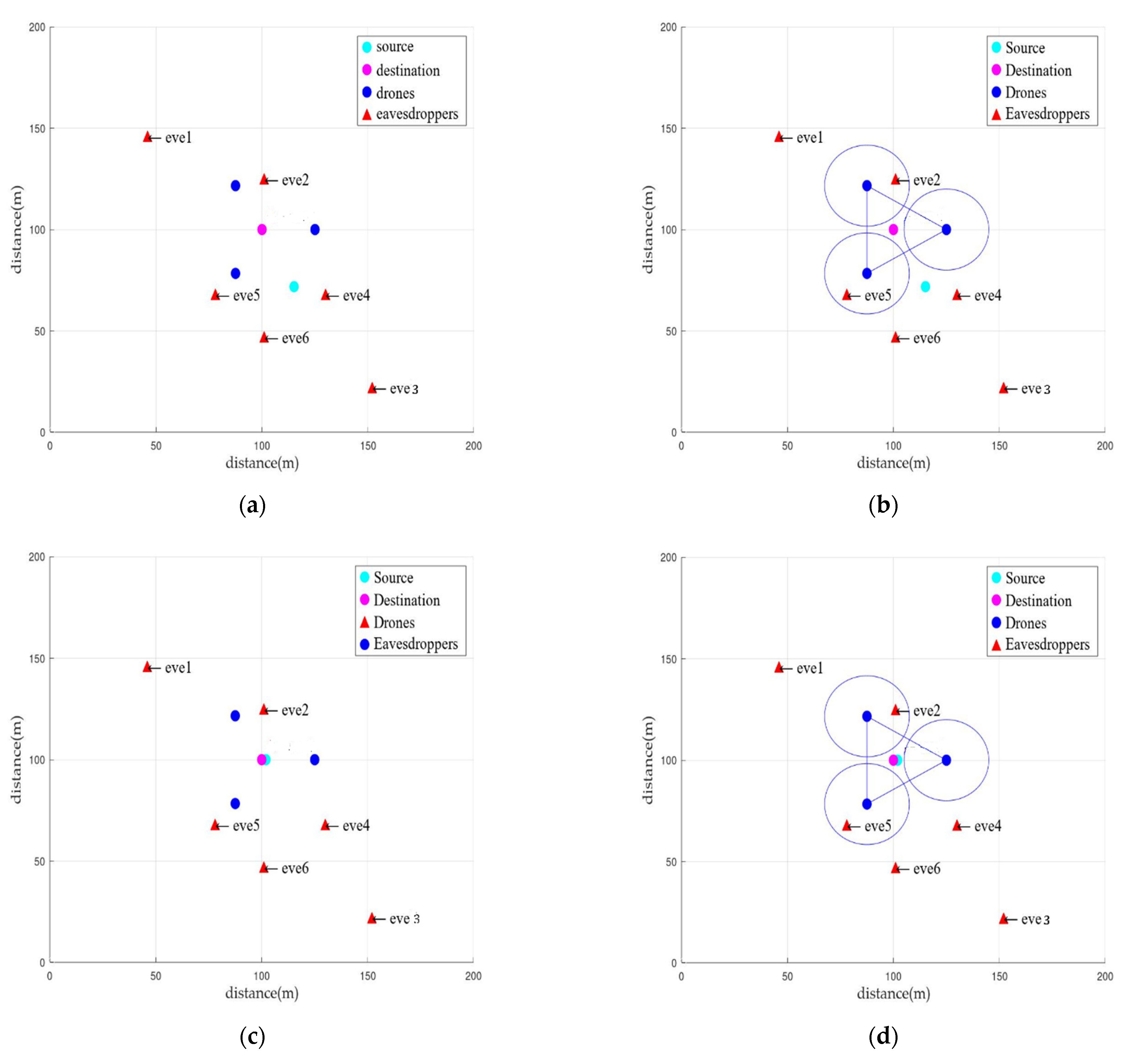
5.2.3. Experiment Results
5.3. Evaluation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Glossary/Nomenclature/Abbreviations
| Nation | Meaning |
| CFJ-DMZ | Cooperative Friendly Jamming Techniques for Drone-based Mobile Secure Zone |
| IoT | Internet of Things |
| D2D | Device to Device |
| UAV | Unmanned Aerial Vehicle |
| Fri-UJ | Friendly UAV Jamming |
| SINR | Signal to Interference and Noise Ratio |
| ILR | Information Leakage Rate |
| BER | Bit Error Rate |
| S | Source |
| D | Destination |
| E | Eve |
| J | Jammer |
| dSE | Source-Eve distance |
| dDE | Drone-Eve distance |
References
- Waliullah, M.D.; Gan, D. Wireless LAN security threats & vulnerabilities. Int. J. Adv. Comput. Sci. Appl. 2014, 5, 176–183. [Google Scholar]
- Chen, J.; Jiang, M.; Liu, Y. Wireless LAN security and IEEE 802.11i. IEEE Wirel. Commun. 2005, 12, 27–36. [Google Scholar] [CrossRef]
- Kim, Y.S.; Tague, P.; Lee, H.; Kim, H. Carving Secure Wi-Fi Zones with Defensive Jamming. In Proceedings of the 7th ACM Symposium on Information, Computer and Communications Security, Seoul, Korea, 2–4 May 2012. [Google Scholar]
- Allouche, Y.; Arkin, E.M.; Cassuto, Y.; Efrat, A.; Grebla, G.; Mitchell, J.S.; Sankararaman, S.; Segal, M. Secure communication through jammers jointly optimized in geography and time. Pervasive Mob. Comput. 2017, 41, 83–105. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A survey on security and privacy issues in Internet-of-Things. IEEE Internet Thing 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Bose, T.; Bandyopadhyay, S.; Ukil, A.; Bhattacharyya, A.; Pal, A. Why Not Keep Your Personal Data Secure yet Private in IoT?: Our Lightweight Approach. In Proceedings of the 2015 IEEE Tenth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), Singapore, 7–9 April 2015. [Google Scholar]
- Zhang, X.; He, J.; Wei, Q. Security Considerations on Node Mobility in Wireless Sensor Networks. In Proceedings of the 2009 Fourth International Conference on Computer Sciences and Convergence Information Technology, Seoul, Korea, 24–26 November 2009. [Google Scholar]
- Wyner, A.D.; Aaron, D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1505. [Google Scholar] [CrossRef]
- Bakr, O.; Mudumbai, R. A New Jamming Technique for Secrecy in Multi-Antenna Wireless Networks. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 2513–2517. [Google Scholar]
- Cumanan, K.; Xing, H.; Xu, P.; Zheng, G.; Dai, X.; Nallanathan, A.; Ding, Z.; Karagiannidis, G.K. Physical layer security jamming: Theoretical limits and practical designs in wireless networks. IEEE Access 2016, 5, 3603–3611. [Google Scholar] [CrossRef] [Green Version]
- Vilela, J.P.; Bloch, M.; Barros, J.; McLaughlin, S.W. Wireless secrecy regions with friendly jamming. IEEE Trans. Inf. Forensics Secur. 2011, 6, 256–266. [Google Scholar] [CrossRef]
- Vilela, J.P.; Bloch, M.; Barros, J.; McLaughlin, S.W. Friendly Jamming For Wireless Secrecy. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010. [Google Scholar]
- He, B.; She, Y.; Lau, V.K.N. Artificial noise injection for securing single-antenna system. IEEE Trans. Veh. Technol. 2017, 66, 9577–9581. [Google Scholar] [CrossRef] [Green Version]
- Giti, J.E.; Sakzad, A.; Srinivasan, B.; Kamruzzaman, J.; Gaire, R. Friendly Jammer Against an Adaptive Eavesdropper in a Relay-Aided Network. In Proceedings of the 2020 International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020. [Google Scholar]
- Kishk, M.A.; Dhillon, H.S. Stochastic geometry-based comparison of secrecy enhancement techniques in D2D networks. IEEE Wirel. Commun. Lett. 2017, 6, 394–397. [Google Scholar] [CrossRef]
- Kim, Y.S.; Tague, P.; Lee, H.; Kim, H. A jamming approach to enhance enterprise Wi-Fi secrecy through spatial access control. Wirel. Netw. 2015, 21, 2631–2647. [Google Scholar] [CrossRef]
- Yaacoub, E.; Husseini, M.A. Achieving Physical Layer Security with Massive MIMO Beamforming. In Proceedings of the 2017 11th European Conference on Antennas and Propagation (EUCAP), Paris, France, 19–24 March 2017. [Google Scholar]
- Sharma, V.; You, I.S.; Andersson, K.; Palmieri, F.; Rehmani, M.H.; Lim, J.D. Security, privacy and trust for smart mobile-Internet of Things (M-IoT). IEEE Access 2020, 8, 167123–167163. [Google Scholar] [CrossRef]
- Wang, Q.; Dai, H.; Wang, H.; Xu, G.; Sangaiahs, A.K. UAV-enabled friendly jamming scheme to secure industrial Internet of Things. J. Commun. Netw. 2019, 21, 481–490. [Google Scholar] [CrossRef]
- Li, X.; Dai, H.N.; Wang, Q.; Imran, M.; Li, D.; Imran, M.A. Securing Internet of Medical Things with Friendly-jamming schemes. ELSEVIER Comput. Commun. 2020, 160, 431–442. [Google Scholar] [CrossRef] [PubMed]
- Zhang, S.; Ansari, N. Latency Aware 3D Placement and User Association in Drone-Assisted Heterogeneous Networks with FSO-Based Backhaul. IEEE Trans. Veh. Technol. 2021, 70, 11991–12000. [Google Scholar] [CrossRef]
- Duo, B.; Hua, H.; Li, Y.; Hua, Y.; Zhu, X. Robust 3D trajectory and power design in probabilistic LoS channel for UAV-enabled cooperative jamming. ELSEVIER Veh. Commun. 2021, 32, 100387. [Google Scholar] [CrossRef]
- Lohanan, P.; Mishrab, D.; Nguyen, J.; Gupta, V. Secrecy-aware UAV position-aided jamming for practical eavesdropper localization models. ELSEVIER Veh. Commun. 2021, 33, 100430. [Google Scholar]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and applications of physical layer security techniques for confidentiality: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 1173–1828. [Google Scholar] [CrossRef]
- Leung-Yan-Cheong, S.K.; Hellman, M.E. The Gaussian wiretap channel. IEEE Trans. Inf. Theory 1978, IT-24, 451–456. [Google Scholar] [CrossRef]
- Demijan, K.; Jeongseok, H.; Steven, W.M.; Joao, B.; Byungjae, K. LDPC Codes for the Gaussian Wiretap Channel. IEEE Trans. Inf. Forensics Secur. 2011, 6, 532–540. [Google Scholar]
- D’Oro, S.; Ekici, E.; Palazzo, S. Optimal power allocation and scheduling under jamming attacks. IEEE/ACM Trans. Netw. 2017, 25, 1310–1323. [Google Scholar] [CrossRef]
- Abdullah, Z.; Chen, G.; Abdullah, M.A.M.; Chambers, J.A. Enhanced secrecy performance of multihop IoT networks with cooperative hybrid-duplex jamming. IEEE Trans. Inf. Forensics Secur. 2020, 16, 161–172. [Google Scholar] [CrossRef]


| Paper Title | Research Topic | Number of Jammers | Main Idea | Limitation |
|---|---|---|---|---|
| UAV-enabled friendly jamming scheme to secure industrial Internet of Things [19] | Eavesdropping, Internet of Things, unmanned aerial vehicles | Multiple | Unmanned aerial vehicles (UAV)-enabled friendly jamming scheme | Need to study the optimal number of jammers |
| A jamming approach to enhance enterprise Wi-Fi secrecy through spatial access control [16] | Eavesdropping, Wi-Fi networks | Multiple | Defensive jamming approach in Wi-Fi networks secured by the WPA2 enterprise mode | Need to study friendly jamming techniques in a mobile environment |
| Achieving physical layer security with massive MIMO beamforming [17] | Antenna arrays, beamforming, cylindrical arrays, massive MIMO | Single | Beamforming with large cylindrical antenna arrays | Need to study appropriate node placement |
| Friendly jammer against an adaptive eavesdropper in a relay-aided network [14] | Relay-aided single-input single-output network, adaptive eavesdropping, outage probability | Single | Simulations for improvement in the secrecy capacity and SOP performances owing to the presence of friendly jamming | Need to study improved security for confident communication of nodes that want protection, and optimal number of jammers |
| Friendly jamming for wireless secrecy [12] | Cooperative jamming, jamming coverage, jamming efficiency, eavesdropping | Single | Cooperative/friendly jamming on the secrecy outage probability of a quasi-static wiretap fading channel | Need to study friendly jamming techniques in a mobile environment, and the optimal number of jammers |
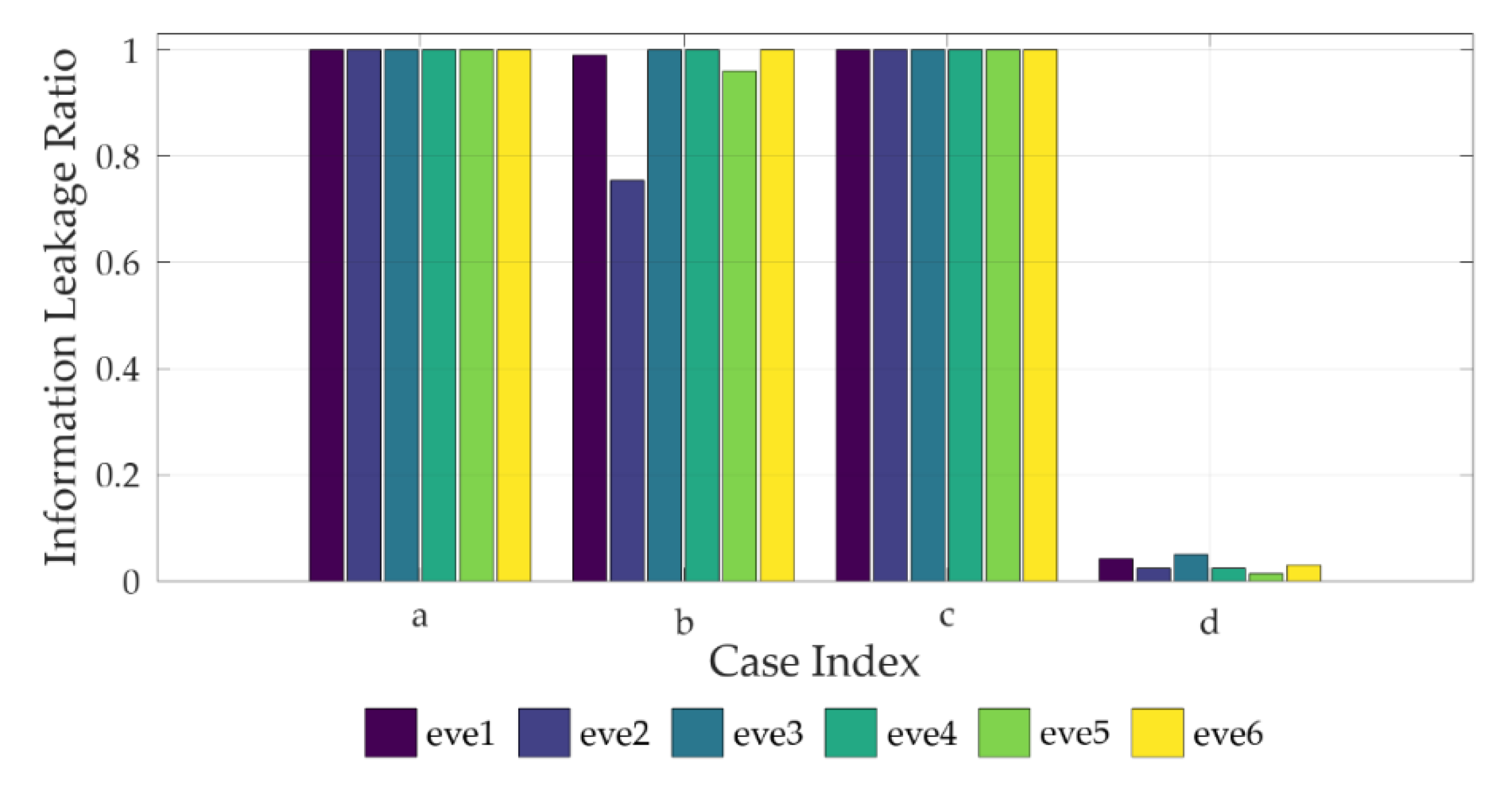
| Node | Source in Figure 4a,b | Source in Figure 4c,d | Destiantion | eve1 | eve2 | eve3 | eve4 | eve5 | eve6 |
|---|---|---|---|---|---|---|---|---|---|
| Location | (127.42, 60.1) | (102, 100) | (100, 100) | (23, 146) | (101, 125) | (155, 22) | (149, 89) | (73,71) | (101, 47) |
| Case | Figure 4a | Figure 4b | Figure 4c | Figure 4d |
|---|---|---|---|---|
| Mobility | X | X | O | O |
| friendly jamming | X | O | X | O |
| Source-Destination distance (m) | 48.413 | 48.413 | 2 | 2 |
| Notation | Remark |
|---|---|
| Channel coefficient for free-space path loss | |
| Randomized complex number | |
| Channel coefficient for free-space path loss of distance between source and eve | |
| Channel coefficient for free-space path loss of distance between source and destination | |
| Channel coefficient for free-space path loss of distance between jammer and eve | |
| Scaling factor of amplification based on the distance source and destination |
| Node | Destination Node | eve1 | eve2 | eve3 | eve4 | eve5 | eve6 |
|---|---|---|---|---|---|---|---|
| BER metric | 0 | 0.389 | 0.012 | 0.975 | 0.992 | 0.938 | 0.562 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jeon, G.-H.; Lee, J.-H.; Sung, Y.-S.; Park, H.-J.; Lee, Y.-J.; Yun, S.-W.; Lee, I.-G. Cooperative Friendly Jamming Techniques for Drone-Based Mobile Secure Zone. Sensors 2022, 22, 865. https://doi.org/10.3390/s22030865
Jeon G-H, Lee J-H, Sung Y-S, Park H-J, Lee Y-J, Yun S-W, Lee I-G. Cooperative Friendly Jamming Techniques for Drone-Based Mobile Secure Zone. Sensors. 2022; 22(3):865. https://doi.org/10.3390/s22030865
Chicago/Turabian StyleJeon, Ga-Hye, Ji-Hyun Lee, Yeon-Su Sung, Hyun-Ju Park, You-Jin Lee, Sun-Woo Yun, and Il-Gu Lee. 2022. "Cooperative Friendly Jamming Techniques for Drone-Based Mobile Secure Zone" Sensors 22, no. 3: 865. https://doi.org/10.3390/s22030865
APA StyleJeon, G.-H., Lee, J.-H., Sung, Y.-S., Park, H.-J., Lee, Y.-J., Yun, S.-W., & Lee, I.-G. (2022). Cooperative Friendly Jamming Techniques for Drone-Based Mobile Secure Zone. Sensors, 22(3), 865. https://doi.org/10.3390/s22030865







