Abstract
Wireless sensor networks (WSNs) have been developed recently to support several applications, including environmental monitoring, traffic control, smart battlefield, home automation, etc. WSNs include numerous sensors that can be dispersed around a specific node to achieve the computing process. In WSNs, routing becomes a very significant task that should be managed prudently. The main purpose of a routing algorithm is to send data between sensor nodes (SNs) and base stations (BS) to accomplish communication. A good routing protocol should be adaptive and scalable to the variations in network topologies. Therefore, a scalable protocol has to execute well when the workload increases or the network grows larger. Many complexities in routing involve security, energy consumption, scalability, connectivity, node deployment, and coverage. This article introduces a wavelet mutation with Aquila optimization-based routing (WMAO-EAR) protocol for wireless communication. The presented WMAO-EAR technique aims to accomplish an energy-aware routing process in WSNs. To do this, the WMAO-EAR technique initially derives the WMAO algorithm for the integration of wavelet mutation with the Aquila optimization (AO) algorithm. A fitness function is derived using distinct constraints, such as delay, energy, distance, and security. By setting a mutation probability P, every individual next to the exploitation and exploration phase process has the probability of mutation using the wavelet mutation process. For demonstrating the enhanced performance of the WMAO-EAR technique, a comprehensive simulation analysis is made. The experimental outcomes establish the betterment of the WMAO-EAR method over other recent approaches.
1. Introduction
With the rapid advancement in Future Internet technologies, the mobile Internet, the Internet of Things (IoT), the physical world, and the sensor cloud are regularly getting more connected and moving faster toward the always-connected model [1]. In this model, easily configurable, wirelessly connected, and cheap sensors can sense and gather environmental information anywhere and anytime [2]. Unfortunately, the cheapness and higher availability of sensing techniques could only soften the barrier to truly supporting the level of resilience, scalability, and reliability needed for these models to be global. Efficient software methods and a dearth of accurate simulation models specifically intended for wireless sensor networks (WSNs) result in a lack of reliable algorithms, whose accessibility is crucial for setting up future deployment in better conditions [3]. For instance, systematic consideration of the impacts of network dynamicity, channel interference, and node mobility are key points not sufficiently taken into account yet, preventing or weakening the appropriate operation of the resultant network [4]. Therefore, to smash those barriers, we need fast, accurate, and efficient techniques, particularly to handle communication and judiciously manage the tiny computation, memory, and battery resources of the sensor nodes (SNs) in the network [5]. Figure 1 depicts the overview of a routing protocol for WSNs.
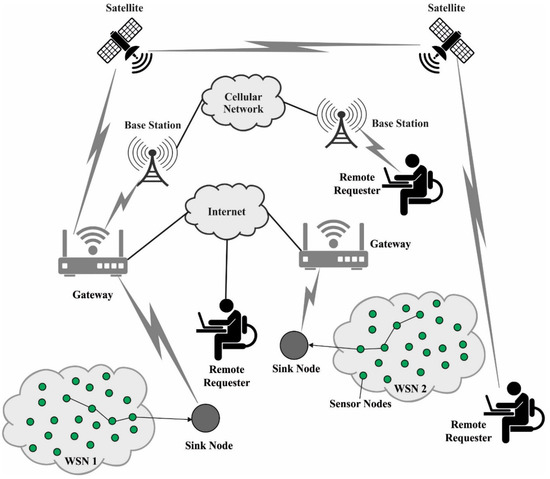
Figure 1.
Routing protocol for WSNs.
In WSNs, numerous types of research have involved routing strategy, corporeal design, procedure for sensing capability, power management, and security issues of SNs. The lifetime of SNs is the major problem for WSNs, since SNs have constrained energy resources. The routing algorithm has played a crucial role in the SN’s lifetime [6]. Routing in WSNs is different from other wireless networks due to unique properties of SNs, such as processing accomplishment, energy constraints, communication of gathered data from more than one node to a single base station, random deployment of SNs, the improbability of global addresses, and so on [7]. To accommodate this, distinct kinds of routing approaches have been designed. The final objective is to maximize the overall network lifetime and accomplish energy efficiency. The lifetime of SNs is based on the battery life that gives power to SNs, where the lifespan of the entire network is dependent. A power resource supplies energy to the transceiver, memory unit, and sensing unit [8]. The memory unit is applied for the storage of application-related data and information on device identification, the sensing unit has a sensor for capturing information from the environment, and the transceiver takes the responsibility for the reception and transmission of information. Fast energy dissipation in SNs making them lifeless is a crucial issue in the arena of WSNs [9]. It is noted that ineffective routing protocol causes fast dissipation of batteries. Therefore, it is a fundamental prerequisite to use and design energy-effective routing algorithms in WSNs that would rise their [10].
This article introduces a wavelet mutation with Aquila optimization-based routing (WMAO-EAR) protocol for wireless communication. The presented technique aims to accomplish energy-aware routing in WSNs. To do this, it initially derives the WMAO algorithm for the integration of wavelet mutation with the Aquila optimization (AO) algorithm. A fitness function (FF) is derived using distinct constraints, such as delay, energy, distance, and security. Once the mutation probability P has been set, every individual next to the exploitation and exploration process has the probability of mutation using the wavelet mutation process. For establishing the enhanced performance of the WMAO-EAR technique, a comprehensive simulation analysis is made.
2. Literature Review
Jagadeesh and Muthulakshmi [11] examined a hybrid metaheuristic (MH) algorithm-based clustering with multihop routing (MHR) (HMA-CMHR) protocol for WSNs. The projected method integrated data transmission, node initialization, clustering, and routing. Initially, the HMA-CMHR algorithm utilized a quantum harmony search algorithm (QHSA)-based clustering procedure for choosing a better subset of CHs. Secondarily, the improved cuckoo search (ICS) technique-based route approach was utilized for a better optimum selection of routes. Gupta and Saha [12] presented a hybrid MH approach where optimum features of ABC and differential evolution (DE) are integrated to measure an optimum group of load-balancing (LB) CHs. Regarding energy efficiency and LB clustering, a new objective function has been developed based on average energy, intracluster distance, and delay parameter. An ABC-based MH technique was presented to the dynamic relocalized mobile sink in a cluster-based network structure.
Al-Otaibi et al. [13] developed a hybridization of the MH cluster-based routing (HMBCR) approach for WSNs. The HMBCR approach primarily contained a brainstorm optimization with levy distribution (BSO-LD)-based clustering employing an FF integrating four parameters: network load, distance to neighbors, energy, and distance to BS. The WWO-HC-based routing method was implemented for optimum route selection. Subramani et al. [14] concentrated on MH-based clustering with routing protocol for UWSNs—MCR-UWSNs. The purpose of the aforementioned system is to choose an effectual group of CHs and route to target. Lakshmanna et al. [15] presented an improved MH-driven energy-aware cluster-based routing (IMD-EACBR) technique for IoT-supported WSNs. The presented IMD-EACBR approach aimed to achieve maximal energy consumption and network lifespan. To attain this, the IMD-EACBR technique used an improved Archimedes optimized algorithm-based clustering (IAOAC) system for CH selective and cluster organization. The TLBO-based MHR (TLBO-MHR) approach has been applied to optimal selective routes to targets.
Srikanth et al. [16] established an MH optimized enabled unequal clustering with MHR protocol (MOUC-MRP) for WSNs. The MOUC-MRP system’s purpose is for selecting CHs and optimum routes to target from WSNs. The harmony search (HS) route-selective manner was developed to an optimum route solution. Mann and Singh [17] examined an improved ABC (iABC) MH with an enhanced searching formula to improve their exploitation abilities and increase the global convergence of the presented MH. An enhanced population-sampling approach was established with Student’s-t distribution that needs only one control parameter for computing and storing, then enhances the efficacy of presented MH.
3. The Proposed Model
In this study, a new WMAO-EAR algorithm is proposed for effectual and energy-aware wireless communication. The presented WMAO-EAR technique aims to accomplish energy-aware routing in WSNs.
3.1. System Model
Approaches utilized to carry out the presented routing protocol were the network model, energy model, and energy-dissipation model [18]. In the following section, a detailed description of all the models is given.
3.1.1. Energy Model
WSNs involve link heterogeneity, energy heterogeneity, and computational heterogeneity. Energy heterogeneity is regarded as the most important to ensure optimal network performance. In the study, we discussed three levels of energy heterogeneity: advanced, normal, and intermediate nodes. Intermediate node initial energy is between advanced and normal node initial energy, given that m and b represent the percentage of advanced nodes and intermediate nodes correspondingly. Advanced node energy is α times more than that of the intermediate and normal node energy is β times more than normal node energy. Now, the is connected with α via . With and signifying the initial energy of normal, intermediate, and advanced nodes, then energy relationships are formulated, using:
3.1.2. Energy-Dissipation Model
Reception and data transmission are two fundamental functions in WSNs. Usually, the data-communication method expends lots of energy when compared to data reception. Now, energy cost during -bit data transmission over distance d is formulated as follows.
In Equation (4), indicates the reference distance and Elec shows the per bit energy cost for running the receiver or transmitter circuits, and and indicate amplification parameters of the transmitter for free space and multipath fading, correspondingly.
Furthermore, energy costs during -bit data reception are formulated as follows:
3.1.3. Network Model
Consider that the n sensor is positioned in the region of M size and the sensor is static. Every sensor is regarded as being aware of the identification and location of other SNs. Also, consider that the advanced node’s location is predetermined, while the normal and intermediate nodes are placed randomly. All the nodes transmit information to neighboring CH for data aggregation. The distance between the BS and nodes is where d indicates a predetermined range .
3.2. Design of WMAO Algorithm
Abualigah et al. [19] introduced the fundamental formula of the Aquila optimizer (AO). Usually, the AO algorithm mimics the natural behavior of Aquila for catching the prey. Like other metaheuristic (MH) models, AO was a population-based optimization algorithm that takes place by creating an early population that has agents. In Equation (6), the mathematical modeling of the algorithm is given.
and indicate parameters of the searching space, denotes a random number, and shows the dimension of the agent. Next, exploration and exploitation are performed until the optimal solution is found. To perform exploration and exploitation, two strategies are employed. The initial strategy performs the exploration based on the average of agents and the finest agent as follows:
where controls the search in the exploration stage, indicates the maximal amount of iterations, and shows a random number within [0, 1]. Figure 2 showcases the flowchart of the AO method.
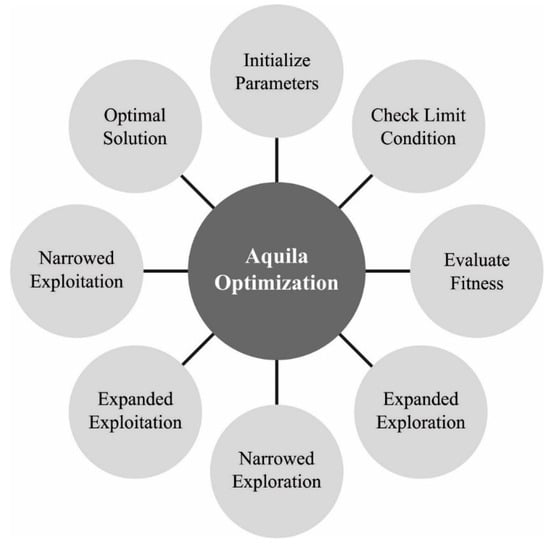
Figure 2.
Flowchart of AO.
The next strategy used to perform the Levy flight distribution and for updating the exploration capability of the solution is:
where and , and denote random numbers, and indicates a constant number. In Equation (9), indicates an arbitrarily selected agent. Furthermore, and imitate the spiral shape, as given below:
where , represents a random number, and indicates integer numbers from 1 to the length of the search domain.
An initial strategy is used to upgrade agents inside the exploitation stage based on and , like exploration as follows:
where and signify the exploitation adjustment parameter and denotes a random number. In the next strategy of exploitation, the agent gets upgraded based on , Levy, and the quality function :
where rand denotes a function that produces a random number and specifies distinct motions that are used to track the best individual solution, as follows:
where rand shows a random number. Given that, specifies reducing value from 2 to , and it is evaluated by Equation (17):
Algorithm 1 illustrates the fundamental steps of the AO.
| Algorithm 1: Aquila optimizer (AO) |
while (The ending criteria are not satisfied) do do based on Equation (7). then then End if End if based on Equation (9) then then End if End if Else based on Equation (13). then then end if end if based on Equation (14). then then end if end if End if end for End while . |
In the WMAO algorithm, the mutation was considered a significant technique to support the technique’s jump from local optimum [20]. In this phase, the wavelet mutating approach for enhancing the execution of the AO method is presented. Once the mutation probability is set, every individual after the exploitation and exploration phase of the method will be getting a mutation chance via wavelet mutation strategy. Where , an individual executes Morlet wavelet mutation. The formula of mutation is:
where denotes the i-th individual location in t-th generation, and LB and UB are the lower and upper bounds of the present search space. Correspondingly, σ represents the wavelet mutating coefficient. Its formula is [21]:
where is the Morlet wavelet function, and 99% of its energy can be concentrated within and 2.5, so φ signifies an arbitrary number within −2.5α and 2.5α. The a is the scaling parameter and its expression is [22]:
where s indicates a given constant. The mutant individual is gained after the wavelet mutation function is completed, and greedy choice can be made among the original individual and mutant individual , i.e.,
This procedure assures that an individual with superior fitness will be entering the next iteration, thereby enhancing the convergence speed and optimization capability of the algorithm.
3.3. Process Involved in the WMAO-EAR Technique
In the presented WMAO-EAR technique, an FF is derived using distinct constraints, such as delay, energy, distance, and security. The main concept of the proposed algorithm is to decrease the communication distance between the selected nodes and CH [23]. It also focuses on decreasing the delay to transmit the information from one node to another. In contrast, network energy has to be higher, i.e., during data transmission, it needs to employ a small amount of energy. Finally, the node must tolerate the risk attained in the network. The objective function of the adapted CH demonstrated in Equation (22), while the value of needs to depend on . Now, and indicate the operation, as demonstrated in Equations (23) and (24). The constraints on delay, energy, distance, and security are indicated as and . The condition of this constraint is indicated as . In Equation (24), denotes the distance between the normal and sink nodes.
Equation (25) illustrates the FF for distance, where is related to packet transmission from the normal nodes to CH and CH to . Generally, lies amongst and the value goes high when the distance between the normal node and CH is higher. Equations (26) and (27) demonstrate and , where indicates the normal node in cluster, represents the CH of th cluster, the distance between the BS and CH is stated as symbolizes the distance between the normal node and CH, indicates the distance between two normal nodes, and and represent the node amount that eliminates the th and clusters.
Equation (28) illustrates the FF of energy. The value is greater than 1 and the whole CH cumulative and concern the maximum energy value and the greater amount of CH.
Equation (29) shows the FF of delay that ranges within is directly proportional to each node inherent in the cluster. Consequently, the delay gets minimalized when the CH has a decreased number of nodes. The numerator indicates the high amount of CH and the denominator indicates the total amount of nodes in the WSN.
4. Results and Discussion
This section inspects the routing performance of the WMAO-EAR method on WSNs. The presented WMAO-EAR model is tested under two node counts (NC) of 100 and 300. Table 1 provides a lifetime inspection of the WMAO-EAR model with existing methods in terms of FND, HND, and LND [24]. Figure 3 exhibits a brief lifetime assessment of the WMAO-EAR method under NC of 100. The results implied that the WMAO-EAR model attained an extended lifetime. For example, concerning FND, the WMAO-EAR model offered an increased FND of 1500 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC models reached reduced FND of 466, 1000, 990, 780, and 2563 rounds, respectively. In terms of HND, the WMAO-EAR technique presented an increased HND of 4750 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC techniques reached a reduced HND of 531, 4328, 3269, 2251, and 4525 rounds, respectively. Finally, in terms of LND, the WMAO-EAR algorithm provided an increased LND of 5432 rounds, while the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC techniques achieved reduced LND of 275, 5230, 5072, 4500, and 5140 rounds, respectively.

Table 1.
Lifetime analysis of WMAO-EAR approach with existing algorithms under NC of 100 and 300.
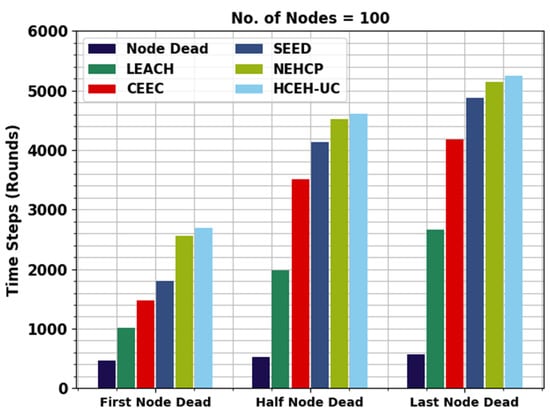
Figure 3.
Lifetime analysis of WMAO-EAR approach under NC of 100.
Figure 4 displays the detailed lifetime assessment of the WMAO-EAR approach under NC of 300. The results denote the WMAO-EAR method obtained an extended lifetime. For example, in terms of FND, the WMAO-EAR approach has rendered an increased FND of 2786 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC approaches attained reduced FND of 528, 1091, 1610, 1814, and 2651 rounds, respectively. For HND, the WMAO-EAR method and HCEHUC models reached reduced HND of 616, 2088, 3566, 4221, and 4562 rounds, respectively. Finally, in terms of LND, the WMAO-EAR approach gave an increased LND of 5387 rounds, where the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC methods reached reduced LND of 715, 2736, 5072, 4327, and 5017 rounds, respectively.
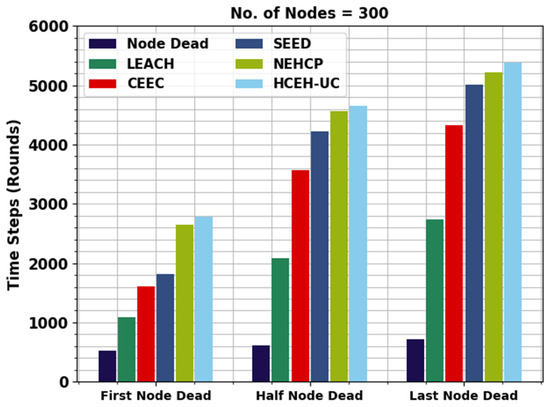
Figure 4.
Lifetime analysis of WMAO-EAR approach under NC of 300.
Table 2 presents a detailed energy utilization (EU) examination of the WMAO-EAR method with other approaches. Figure 5 provides the initial EU inspection of the WMAO-EAR model with compared methods on NC of 100. The figure shows that the WMAO-EAR model achieved EU in the latter rounds of execution. For example, with 0.25 J energy, the WMAO-EAR method ran to 2722 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC models executed for 340, 1436, 2067, 2445, and 2649 rounds, respectively. Concurrently, with 0.5 J energy, the WMAO-EAR approach ran to 5213 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC approaches executed for 702, 2748, 4287, 4985, and 5211 rounds, respectively.

Table 2.
EU analysis of WMAO-EAR approach with existing algorithms under NC of 100 and 300.

Figure 5.
EU analysis of WMAO-EAR approach under NC of 100.
Figure 6 offers the initial EU review of the WMAO-EAR technique with compared methods on NC of 300. The figure shoes that the WMAO-EAR approach obtained EU in the latter rounds of execution. For example, with 0.25 J energy, the WMAO-EAR algorithm runs to 2837 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC approaches execute 558, 1656, 2161, 2676, and 2661 rounds, respectively. Concurrently, with 0.5 J energy, the WMAO-EAR methodology runs to 5423 rounds, whereas the LEACH, CE-EC, SEED, NEH-CP, and HCEHUC techniques execute 846, 2815, 4390, 4997, and 5259 rounds, respectively.
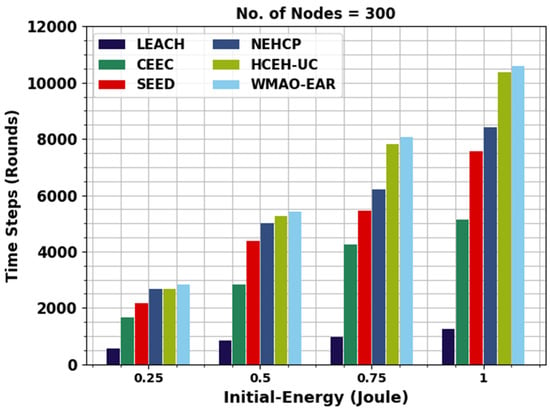
Figure 6.
EU analysis of WMAO-EAR approach under NC of 300.
Table 3 provides a detailed NOAN evaluation of the WMAO-EAR model with other existing models. Figure 7 highlights the comparative NOAN inspection of the WMAO-EAR model. With 2000 rounds, the NOAN offered by the WMAO-EAR model is 99, whereas the CE-EC, SEED, NEH-CP, and HCEHUC models obtained reduced NOAN of 98, 93, 79, and 56, respectively. Likewise, with 2500 rounds, the NOAN presented by the WMAO-EAR approach is 98, whereas the CE-EC, SEED, NEH-CP, and HCEHUC techniques attained reduced NOAN of 97, 78, 46, and 19, respectively. With 3000 rounds, the NOAN presented by the WMAO-EAR algorithm is 95, whereas the CE-EC, SEED, NEH-CP, and HCEHUC methodologies attained reduced NOAN of 92, 59, 29, and 0, respectively.

Table 3.
NOAN analysis of WMAO-EAR approach with existing algorithms under NC of 100 and 300.
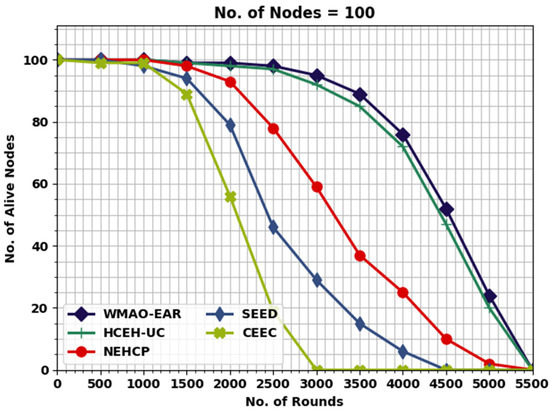
Figure 7.
NOAN analysis of WMAO-EAR approach under NC of 100.
Figure 8 illustrates the comparative NOAN study of the WMAO-EAR approach. With 2000 rounds, the NOAN 300 rendered by the WMAO-EAR technique is 300, whereas the CE-EC, SEED, NEH-CP, and HCEHUC methods attained reduced NOAN of 295, 277, 257, and 216, respectively. With 2500 rounds, the NOAN granted by the WMAO-EAR model is 298, whereas the CE-EC, SEED, NEH-CP, and HCEHUC approaches achieved reduced NOAN of 282, 256, 203, and 142, respectively. With 3000 rounds, the NOAN offered by the WMAO-EAR method is 281, whereas the CE-EC, SEED, NEH-CP, and HCEHUC models attained reduced NOAN of 259, 240, 142, and 69, respectively.
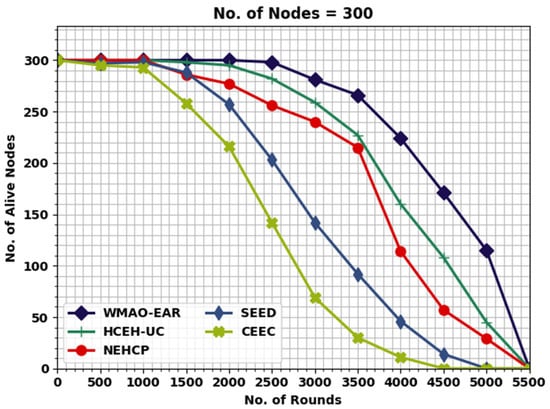
Figure 8.
NOAN analysis of WMAO-EAR approach under NC of 300.
A comparative NODN assessment of the WMAO-EAR model with other models is provided in Table 4. Figure 9 illustrates a detailed NODN investigation of the WMAO-EAR model with other approaches. The outcomes indicated that the WMAO-EAR method reached maximum outcome with minimal NODN values. For example, with 2000 rounds, the WMAO-EAR model gained a lower NODN of 1, whereas the CE-EC, SEED, NEH-CP, and HCEHUC models attained higher NODN of 2, 7, 21, and 44, respectively. Finally, with 3000 rounds, the WMAO-EAR method gained a lower NODN of 5, whereas the CE-EC, SEED, NEH-CP, and HCEHUC approaches attained higher NODN of 8, 41, 71, and 100, respectively.

Table 4.
NODN analysis of WMAO-EAR approach with existing algorithms under NC of 100 and 300.
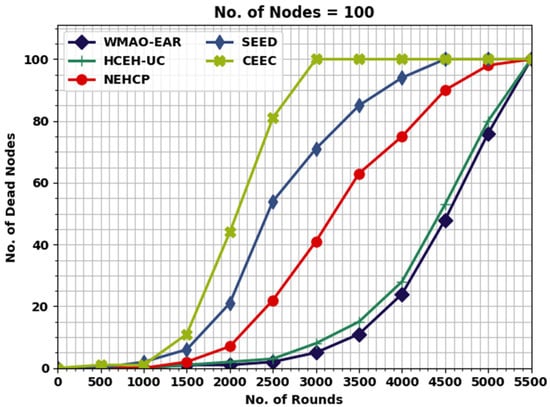
Figure 9.
NODN analysis of WMAO-EAR approach under NC of 100.
Figure 10 illustrates a comprehensive NODN investigation of the WMAO-EAR technique with other models. The outcomes show that the WMAO-EAR approach attained maximum outcome with minimal NODN values. For instance, with 2000 rounds, the WMAO-EAR approach gained a lower NODN of 0, whereas the CE-EC, SEED, NEH-CP, and HCEHUC approaches attained higher NODN of 5, 23, 43, and 84, respectively.
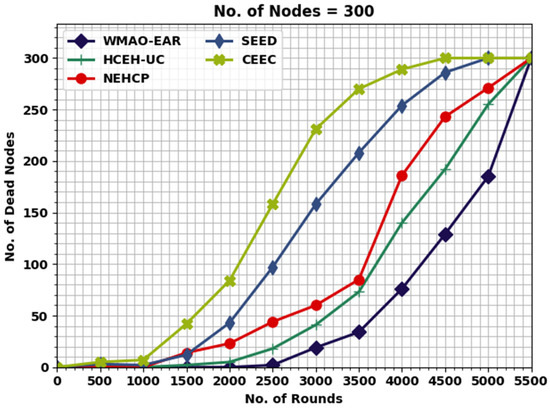
Figure 10.
NODN analysis of WMAO-EAR approach under NC of 300.
Eventually, with 2500 rounds, the WMAO-EAR method attained a lower NODN of 2, whereas the CE-EC, SEED, NEH-CP, and HCEHUC approaches attained higher NODN of 18, 44, 97, and 158, respectively. These experimental values show the enhancements of the WMAO-EAR technique over other existing models.
5. Conclusions
In this study, a new WMAO-EAR approach was devised for effective and energy-aware wireless communication. The presented WMAO-EAR technique aims to accomplish an energy-aware routing process in WSNs. To do this, the WMAO-EAR technique initially derives the WMAO algorithm for the integration of wavelet mutation with the AO algorithm. An FF is derived using distinct constraints, such as delay, energy, distance, and security. Once the mutation probability P is set, every individual next to the exploitation and exploration stage process has a probability of mutation using the wavelet mutation process. To demonstrate the enhanced performance of the WMAO-EAR technique, a comprehensive simulation analysis has been presented. The experimental results establish the superiority of the WMAO-EAR method over other recent approaches. In the future, lightweight cryptographic solutions can be applied to boost secure communication.
Author Contributions
Conceptualization, S.A.; Data curation, M.O.; Formal analysis, M.O.; Funding acquisition, A.M.; Investigation, A.G.; Methodology, S.A., A.G. and A.Y.; Project administration, A.Y. and A.M.; Software, R.A. and O.A.; Supervision, R.A. and O.A.; Validation, A.A.; Visualization, A.A.; Writing—original draft, S.A.; Writing—review & editing, A.M. All authors have read and agreed to the published version of the manuscript.
Funding
Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R203), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4320484DSR03). The author would like to thank the Deanship of Scientific Research at Shaqra University for supporting this work.
Institutional Review Board Statement
This article does not contain any studies with human participants performed by any of the authors.
Informed Consent Statement
Not applicable.
Data Availability Statement
Data sharing does not apply to this article as no datasets were generated.
Conflicts of Interest
The authors declare that they have no conflicts of interest. The manuscript was written with the contributions of all authors. All authors have approved the final version of the manuscript.
References
- Mohan, P.; Subramani, N.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I.; Ulaganathan, S. Improved metaheuristics-based clustering with multihop routing protocol for underwater wireless sensor networks. Sensors 2022, 22, 1618. [Google Scholar] [CrossRef] [PubMed]
- Srivastava, A.; Mishra, P.K. A survey on WSN issues with its heuristics and meta-heuristics solutions. Wirel. Pers. Commun. 2021, 121, 745–814. [Google Scholar] [CrossRef]
- Sharma, R.; Vashisht, V.; Singh, U. Metaheuristics-based energy efficient clustering in WSNs: Challenges and research contributions. IET Wirel. Sens. Syst. 2020, 10, 253–264. [Google Scholar] [CrossRef]
- Yadav, R.K.; Mahapatra, R.P. Hybrid metaheuristic algorithm for optimal cluster head selection in wireless sensor network. Pervasive Mob. Comput. 2022, 79, 101504. [Google Scholar] [CrossRef]
- Revanesh, M.; Sridhar, V. A trusted distributed routing scheme for wireless sensor networks using blockchain and meta-heuristics-based deep learning technique. Trans. Emerg. Telecommun. Technol. 2021, 32, e4259. [Google Scholar] [CrossRef]
- Wang, H.; Li, K.; Pedrycz, W. An elite hybrid metaheuristic optimization algorithm for maximizing wireless sensor networks lifetime with a sink node. IEEE Sens. J. 2020, 20, 5634–5649. [Google Scholar] [CrossRef]
- Esmaeili, H.; Bidgoli, B.M.; Hakami, V. CMML: Combined metaheuristic-machine learning for adaptable routing in clustered wireless sensor networks. Appl. Soft Comput. 2022, 118, 108477. [Google Scholar] [CrossRef]
- Du, X.; Wang, T.; Wang, L.; Pan, W.; Chai, C.; Xu, X.; Jiang, B.; Wang, J. CoreBug: Improving effort-aware bug prediction in software systems using generalized k-core decomposition in class dependency networks. Axioms 2022, 11, 205. [Google Scholar] [CrossRef]
- Singh, S.; Nandan, A.S.; Malik, A.; Kumar, N.; Barnawi, A. An energy-efficient modified metaheuristic inspired algorithm for disaster management system using WSNs. IEEE Sens. J. 2021, 21, 15398–15408. [Google Scholar] [CrossRef]
- Moharamkhani, E.; Zadmehr, B.; Memarian, S.; Saber, M.J.; Shokouhifar, M. Multiobjective fuzzy knowledge-based bacterial foraging optimization for congestion control in clustered wireless sensor networks. Int. J. Commun. Syst. 2021, 34, e4949. [Google Scholar] [CrossRef]
- Jagadeesh, S.; Muthulakshmi, I. Hybrid Metaheuristic Algorithm-Based Clustering with Multi-Hop Routing Protocol for Wireless Sensor Networks. In Proceedings of Data Analytics and Management; Springer: Singapore, 2022; pp. 843–855. [Google Scholar]
- Gupta, G.P.; Saha, B. Load balanced clustering scheme using hybrid metaheuristic technique for mobile sink based wireless sensor networks. J. Ambient. Intell. Humaniz. Comput. 2020, 1–12. [Google Scholar] [CrossRef]
- Al-Otaibi, S.; Al-Rasheed, A.; Mansour, R.F.; Yang, E.; Joshi, G.P.; Cho, W. Hybridization of metaheuristic algorithm for dynamic cluster-based routing protocol in wireless sensor Networksx. IEEE Access 2021, 9, 83751–83761. [Google Scholar] [CrossRef]
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An efficient metaheuristic-based clustering with routing protocol for underwater wireless sensor networks. Sensors 2022, 22, 415. [Google Scholar] [CrossRef] [PubMed]
- Lakshmanna, K.; Subramani, N.; Alotaibi, Y.; Alghamdi, S.; Khalafand, O.I.; Nanda, A.K. Improved metaheuristic-driven energy-aware cluster-based routing scheme for IoT-assisted wireless sensor networks. Sustainability 2022, 14, 7712. [Google Scholar] [CrossRef]
- Srikanth, V.; Vanitha, M.; Maragatharajan, M.; Marappan, P.; Jegajothi, B. Metaheuristic Optimization Enabled Unequal Clustering with Routing Technique. In Proceedings of the 2022 International Conference on Electronics and Renewable Systems (ICEARS), Tuticorin, India, 16–18 March 2022; pp. 800–806. [Google Scholar]
- Mann, P.S.; Singh, S. Improved metaheuristic-based energy-efficient clustering protocol with optimal base station location in wireless sensor networks. Soft Comput. 2019, 23, 1021–1037. [Google Scholar] [CrossRef]
- Sheikhpour, R.; Jabbehdari, S.; Khadem-Zadeh, A. Comparison of energy efficient clustering protocols in heterogeneous wireless sensor networks. Int. J. Adv. Sci. Technol. 2011, 36, 27–40. [Google Scholar]
- Abualigah, L.; Yousri, D.; Abd Elaziz, M.; Ewees, A.A.; Al-Qaness, M.A.; Gandomi, A.H. Aquila optimizer: A novel meta-heuristic optimization algorithm. Comput. Ind. Eng. 2021, 157, 107250. [Google Scholar] [CrossRef]
- Hu, G.; Du, B.; Li, H.; Wang, X. Quadratic interpolation boosted black widow spider-inspired optimization algorithm with wavelet mutation. Math. Comput. Simul. 2022, 200, 428–467. [Google Scholar] [CrossRef]
- Mukherjee, V.; Mukherjee, A.; Prasad, D. Whale optimization algorithm with wavelet mutation for the solution of optimal power flow problem. In Handbook of Research on Predictive Modeling and Optimization Methods in Science and Engineering; IGI Global: Hershey, PA, USA, 2018; pp. 500–553. [Google Scholar]
- Ma, L.; Li, J.; Zhao, Y. Population Forecast of China’s Rural Community Based on CFANGBM and Improved Aquila Optimizer Algorithm. Fractal Fract. 2021, 5, 190. [Google Scholar] [CrossRef]
- Roy, S.; Mazumdar, N.; Pamula, R. An energy optimized and QoS concerned data gathering protocol for wireless sensor network using variable dimensional PSO. Ad Hoc Netw. 2021, 123, 102669. [Google Scholar] [CrossRef]
- Han, B.; Ran, F.; Li, J.; Yan, L.; Shen, H.; Li, A. A Novel Adaptive Cluster Based Routing Protocol for Energy-Harvesting Wireless Sensor Networks. Sensors 2022, 22, 1564. [Google Scholar] [CrossRef] [PubMed]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).