Prospect of Internet of Medical Things: A Review on Security Requirements and Solutions
Abstract
:1. Introduction
1.1. On-Body Segment
- Consumer health wearables: MDs that are used for a healthy lifestyle or fitness (e.g., activity trackers, fitness bands, wristbands, smartwatches sports watches, smart shoes, and clothes) are considered consumer health wearables. Companies such as Misfit (Fossil group), Garmin, FitBit, Ava, Withings, Owlet, Samsung Medical, and Apple are operating in this space.
- Clinical-grade wearables: MDs such as a smart belt for detecting falls and providing hip safety for elderly wearers. During physical activity, the Halo Sport headset is used to stimulate brain regions associated with muscle memory, stamina, and endurance. In addition, for identifying sensory nerves and proving relief from chronic pain, a wearable neuromodulation device such as Neurometrix’s Quell is used. Medical-grade devices include any wearable endorsed by one or more health regulators and authorities such as the U.S. Food and Drug Administration (FDA), whereas there is no involvement of health authorities in the segment of consumer health wearables.
1.2. In-Home Segment
- PERS: These MDs are used for senior or dependent members to avoid mobility. This combines wearable devices/relay units with a live medical call-center service to provide prompt medical assistance.
- RPM: It monitors physiological parameters continuously in an effort to slow disease progression, reduce healing time, and avoid re-hospitalization. It comprises all home-monitoring devices and sensors that provide medication reminders and dosing information.
- TVV: Telemedicine and digital tests are an example of TVV. It helps patients obtain treatment and prescriptions or recommended care plans without a hospital visit.
1.3. Community Segment
- Mobility: this service keeps track of health parameters for patients in transit.
- Emergency response intelligence: this is designed to assist primary patients such as first responders, nurses, and hospital emergency-department care providers.
- Kiosks: this includes things such as computer touchscreen displays that may dispense products or provide services such as access to healthcare providers.
- Point-of-care devices: MDs that give services outside of the home or in health-care settings such as medical camps.
- Logistics: devices such as sensors in pharmaceutical shipments that measure pressure, temperature, humidity, shock, and tilt.
1.4. In-Clinic Segment
- MDs that perform administrative or clinical functionalities.
- MDs who are employed in administrative or clinical roles.
- A service provider can be situated in another location while a product is being used by qualified personnel in this segment.
1.5. In-Hospital Segment
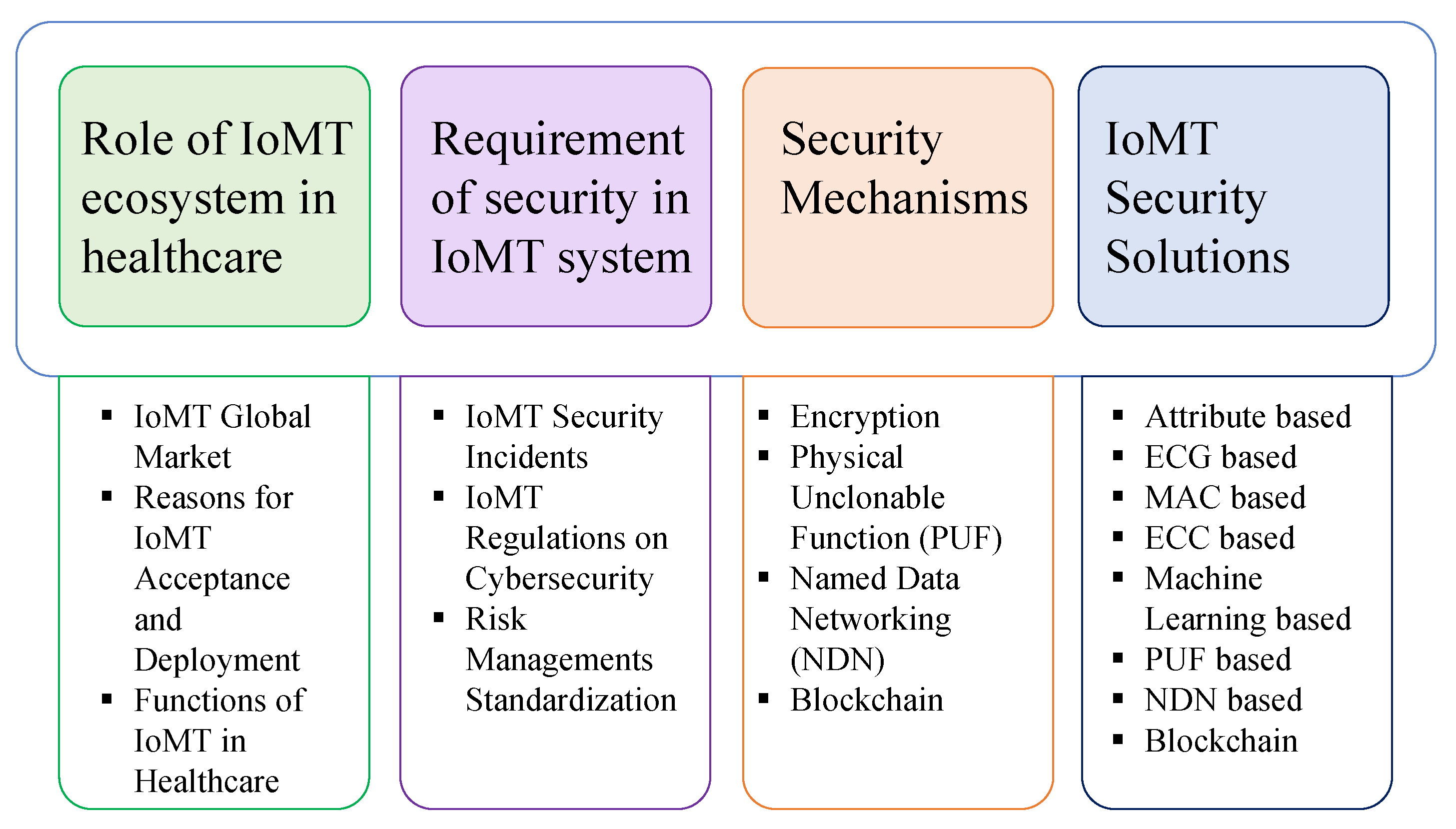
2. Contributions
- Overview of IoMT network, IoMT device segments, and threats to the network;
- The importance of the IoMT ecosystem and role played in the current world is highlighted;
- A review of regulations related to healthcare devices is presented and issues are listed;
- Security mechanisms that are widely used for resource-constrained devices are discussed;
- The pros and cons of the different proposed security frameworks are provided; centralized, decentralized and NDN, as well, are presented.
3. Role of IoMT Ecosystem in Healthcare
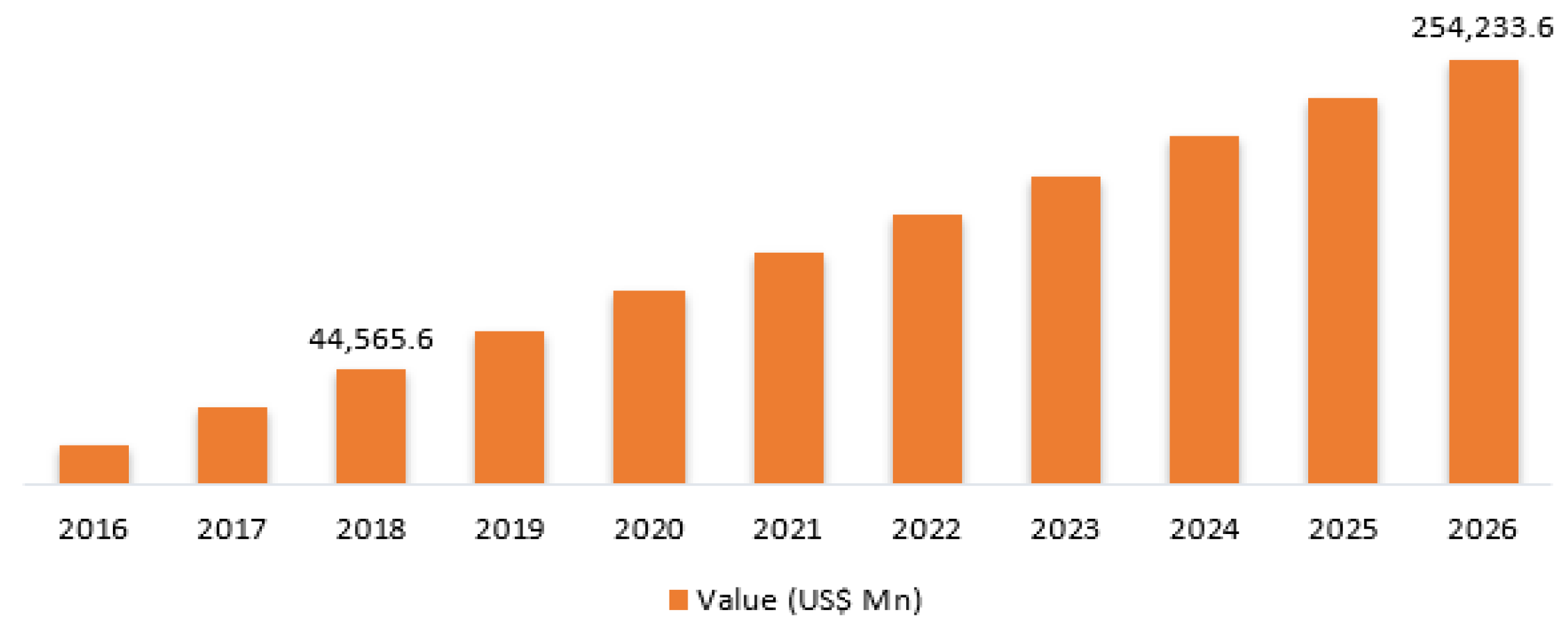
3.1. IoMT Global Market
3.2. Reasons for IoMT Acceptance and Deployment
- Boost and speed up clinician workflows: Small and compact tools, such as Memorial Hermann Health System in Texas, offer significant convenience at the point of care. These tools are used for performing critical duties such as sending SMS, scanning barcodes, and transmitting images.
- Empowers extreme connectivity: Advanced automation and perceptions are at the core of MDs functionality. For instance, smart pills and ultrasound machines can send real-time notifications or alert messages to healthcare organizations.
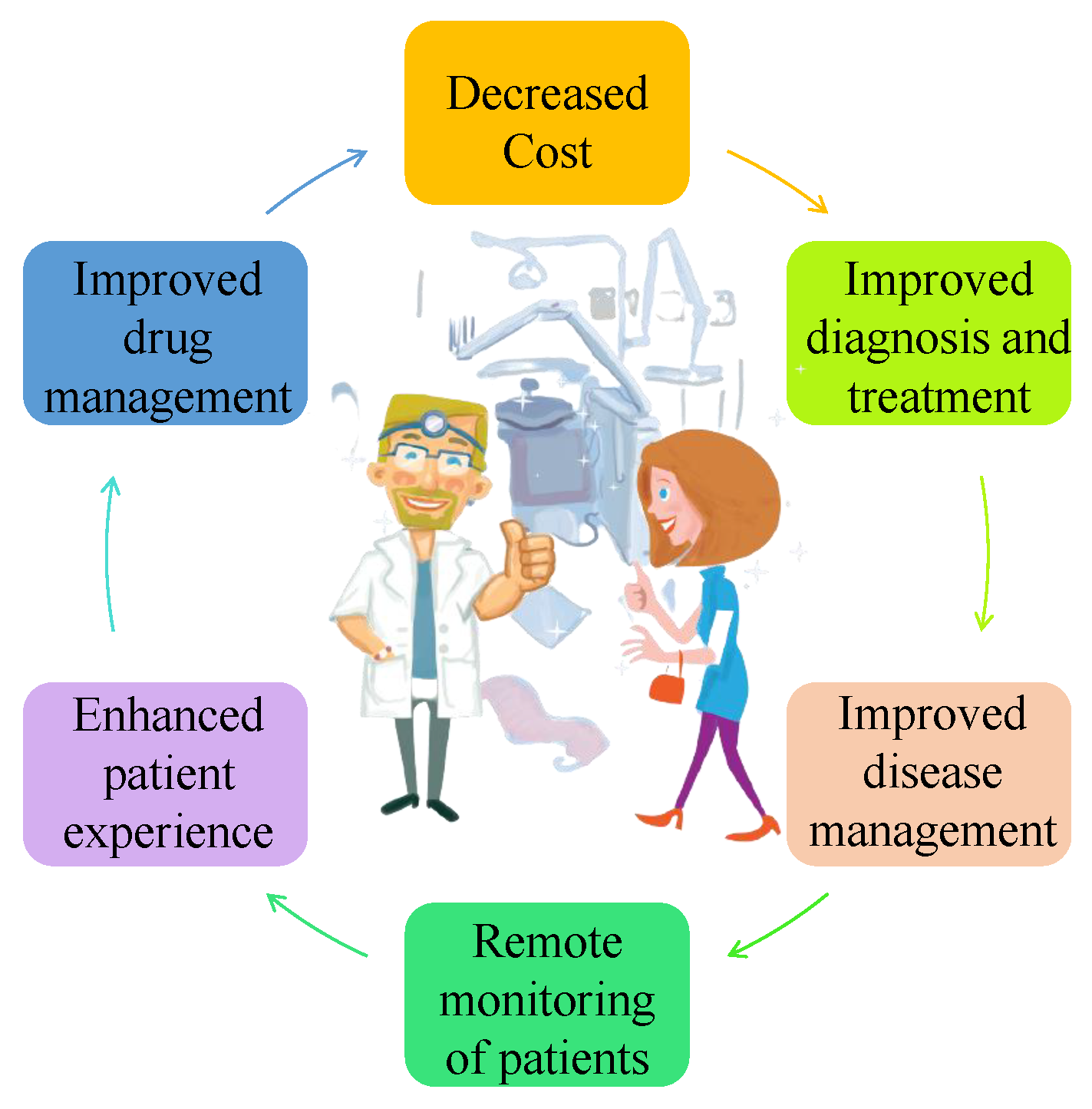
- Remote medical care and services: It allows patients–doctors communication and monitoring from distances. Wi-Fi or Bluetooth-enabled devices such as blood pressure cuffs or glucose monitors or heart-rate checkers collect and transmit data to doctors for evaluating patients’ conditions and prescribing accordingly. For example, improved medication adherence and lowered costs have been achieved by remote patient monitoring (RPM) in different hospitals across Europe such as UCLA Health and Children’s Health in Dallas.
- Proactive approach for sustaining good health: The widespread use of consumer wearable devices allows to aggregate and send patients’ health data to medical personnel for required investigation and treatment. Instead of reactive treatment, it provides proactive care. Wearable devices such as smartwatches and fitness bands are on the market with new types of sensors to keep track of heart rate, measure blood oxygen levels, and provide alerts by forwarding messages.
- Prioritizing the importance of effective security measures: Despite their many benefits, MDs face security issues as a result of device mobility and network requirements, unresolved default passwords, and infrequent (if any) software upgrades. A greater emphasis should be placed on end-to-end security techniques and reliable network monitoring.
3.3. Functions of IoMT in Healthcare
4. Requirement of Security in IoMT System
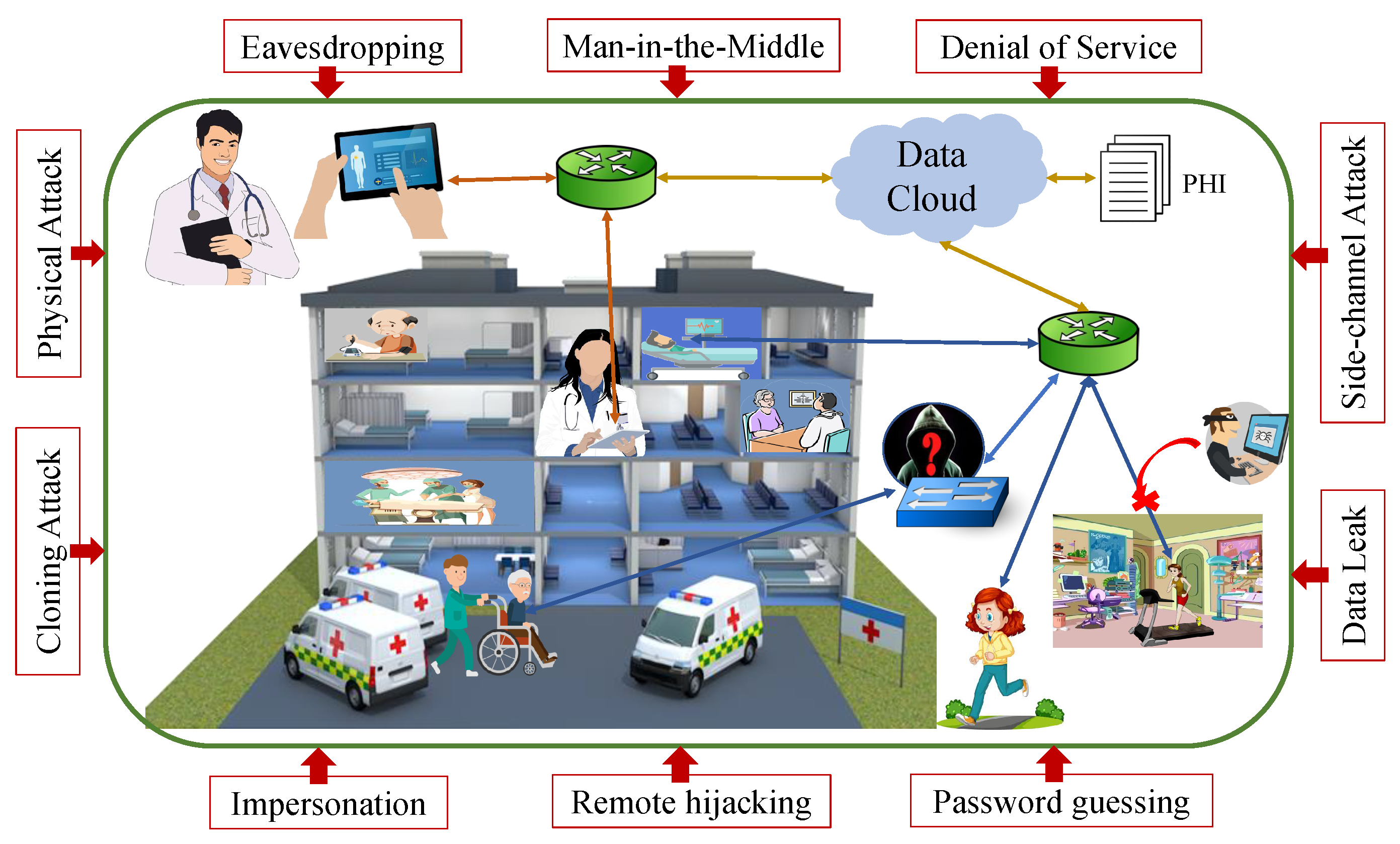
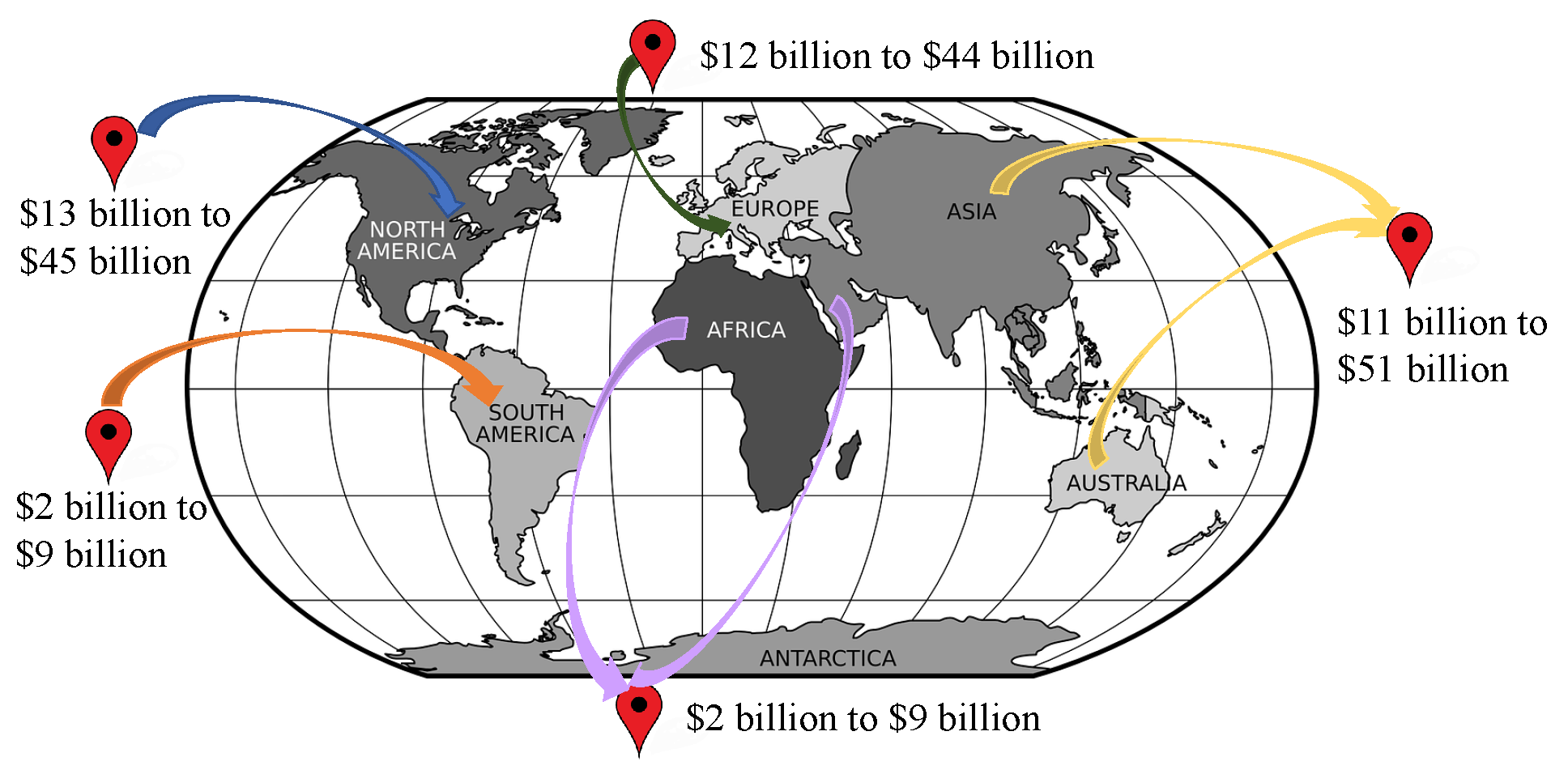
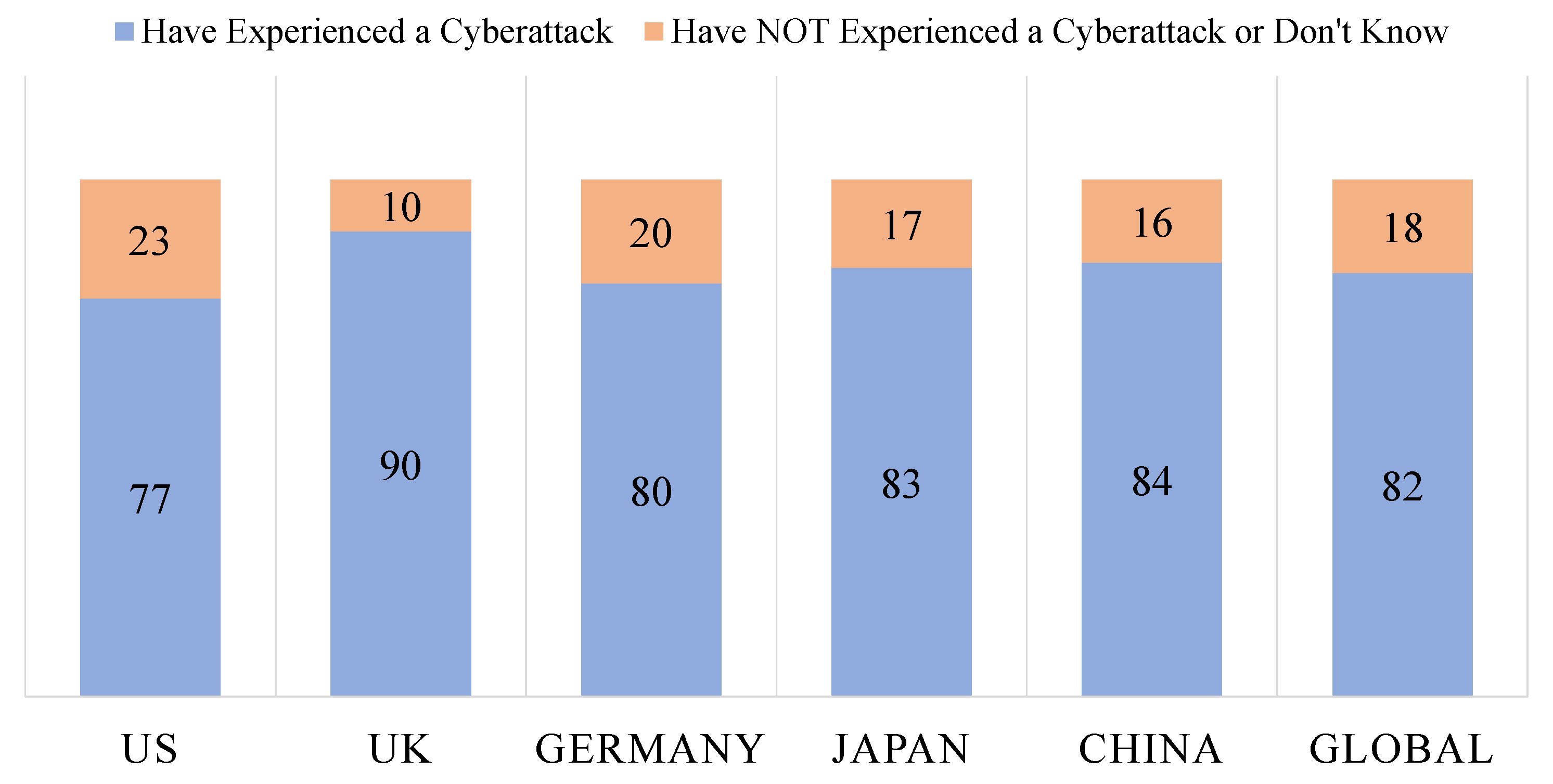
4.1. IoMT Security Incidents
4.2. IoMT Regulations on Cybersecurity
- Are reasonably secure from cybersecurity invasion and compromise.
- Provide a standard level of availability, reliability, and correct operation.
- Are reasonably suited to performing their desired functions.
- Adhere to generally accepted security procedures throughout.
4.3. Risk-Management Standardization
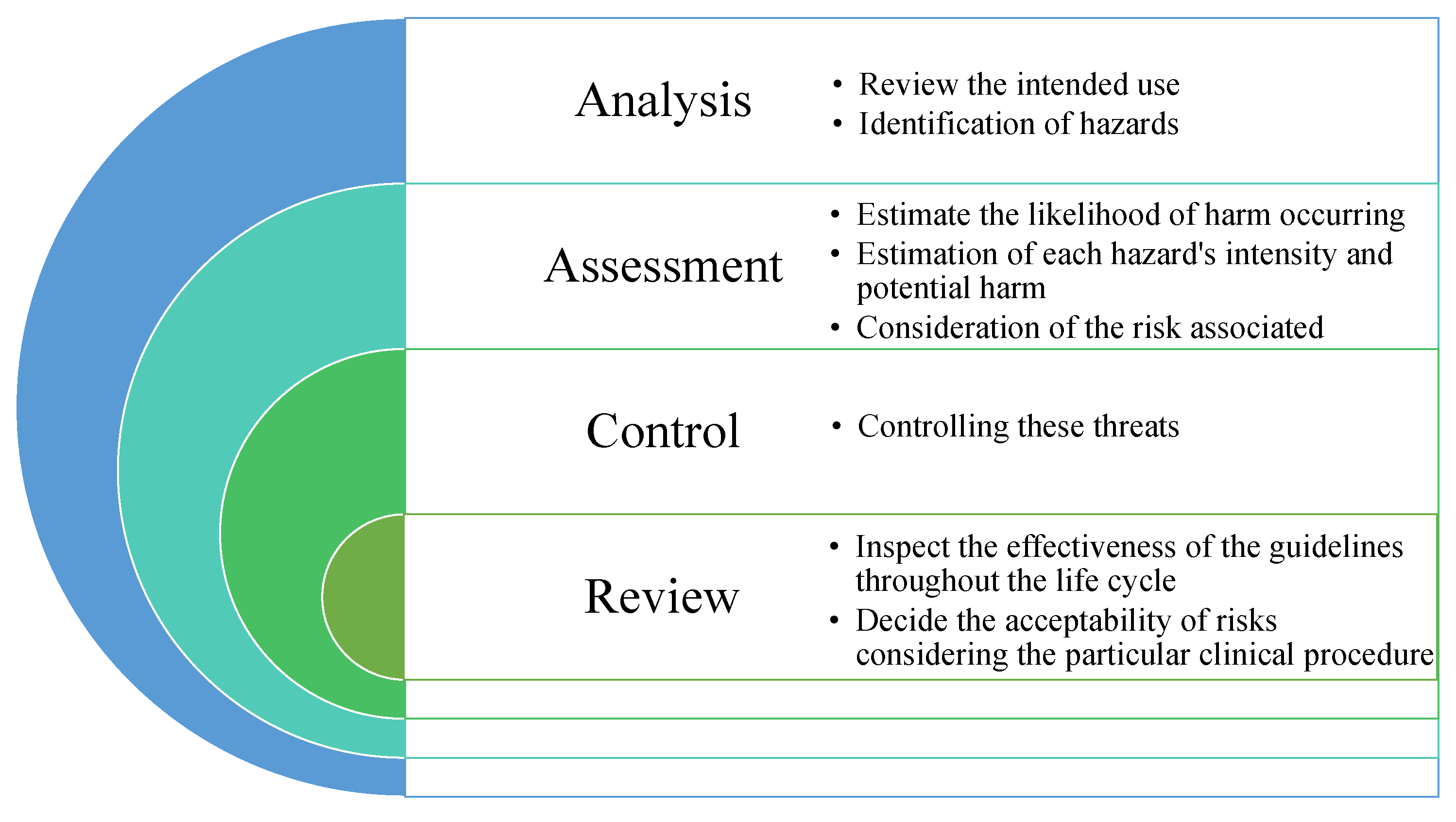
4.3.1. ISO 14971 Medical Devices—Application of Risk Management
- Defining the scope, bounds of risk management, and intended use.
- Need for proper correlation between hierarchical system architectures and terms such as hazards; need for clear definition of root causes and effects.
- Avoiding robust approaches to ensure safety and security.
- Lack of “safety class” with respect to reliability and trustworthiness which exists in ISO 62304.
- Risk control while multiple items are involved; reliable risk controls.
- Verify each safety component, test items in different systems or configurations.
- Disclosures are required for development users and operational users, Balancing the necessity of external stakeholders with proper communication.
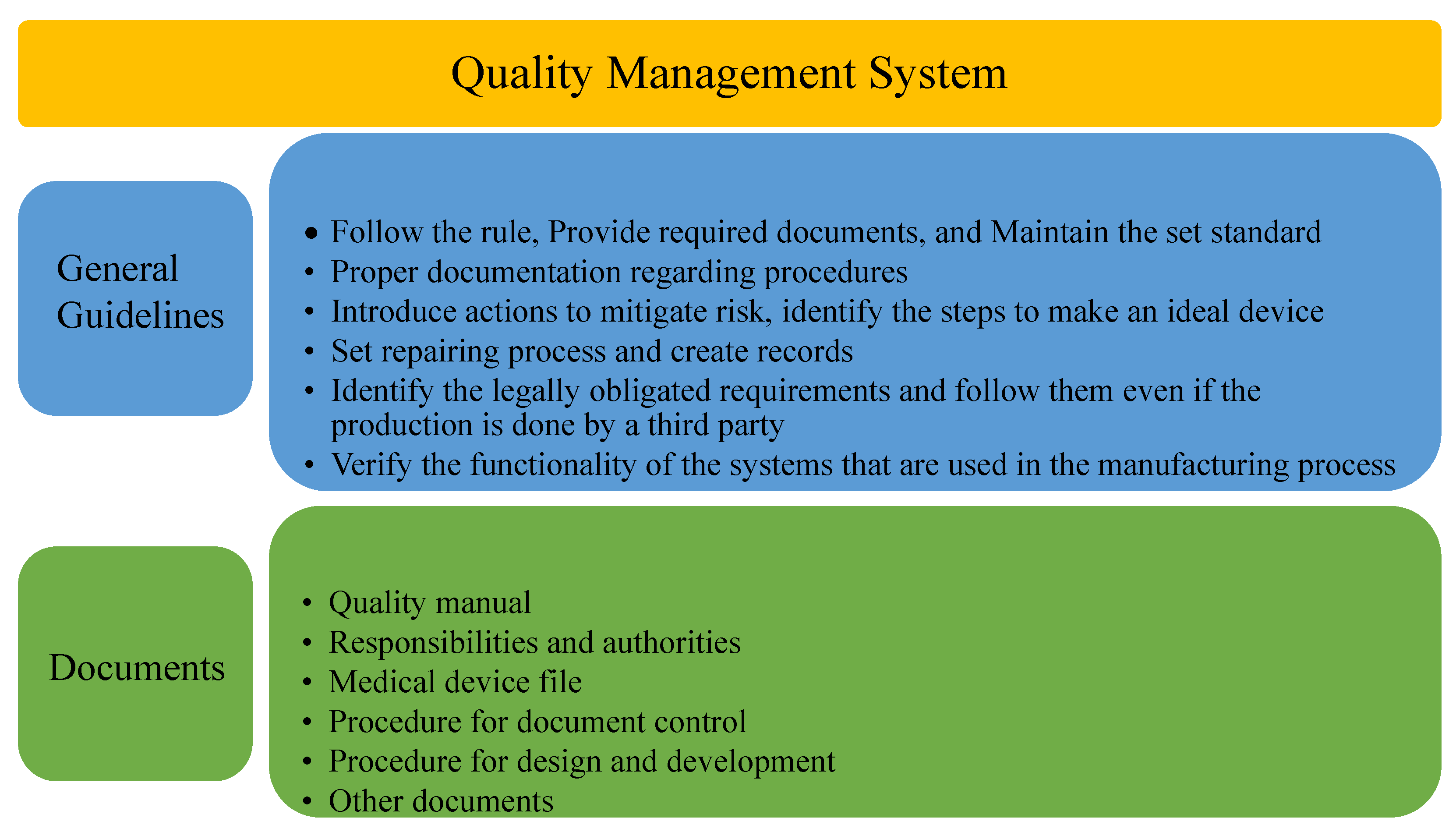
4.3.2. ISO 13485 Medical Devices—Quality Management System (QMS)
4.3.3. IEC 60601-1—Medical Electrical Equipment
- Sharp edges.
- Pinch points.
- Stability under various conditions.
- Movement over a threshold.
- Rough handling.
- Strain on the user.
- Durability of marking.
- Tensile safety factor.
- Correct labeling.
4.3.4. ISO/IEC 80001—Risk Management of Medical Devices on a Network
- ISO/IEC 80001 [58]: Application of risk management for IT-networks incorporating medical devices—Part 1: Roles, responsibilities, and activities in ten sub-parts, dealing with risk-management techniques, guidelines, and processes.
- ISO/IEC 80001: Application of risk management for IT-networks incorporating medical devices—Part 2—1: Roles, responsibilities, and activities in ten sub-parts, dealing with risk-management techniques, guidelines, and processes; Practical Applications and Examples in nine subparts dealing with technical controls and requirements to enable the implementation of ISO/IEC 80001-1.
4.3.5. EU MDR 2017/745
- diagnosis, prevention, monitoring, prediction, prognosis, treatment or alleviation of disease
4.3.6. FDA-2020-D-0957—Guidance for the Content of Premarket Submissions for Software Contained in Medical Devices
4.3.7. FDA-2013-D-0616—Content of Premarket Submissions for Management of Cybersecurity in Medical Devices
- Identification of assets, threats, and vulnerabilities.
- Evaluation of the effects of risks and attacks on device features and functions and end consumers.
- Evaluation of the propensity for a threat and a weakness to be addressed.
- Determining risk exposure levels and effective mitigation tactics.
- Evaluation of overall risk standards and residual risk.
4.3.8. FDA-2015-D-5105—Postmarket Management of Cybersecurity in Medical Devices
- Monitor to identify and detect sources of security vulnerabilities and threats.
- Preserving a robust software lifecycle that includes software update design, verification, third-party software monitoring.
- Understand, assess, and detect the presence and effect of a hazard.
- Establishing and sharing procedures for identifying and handling vulnerabilities.
- Clear definition of a threat model to maintain protection, response, and recovery.
- Establishing a unified policy and procedure for vulnerability disclosure.
- Enacting mitigations that deal with cybersecurity risk before it is exploited.
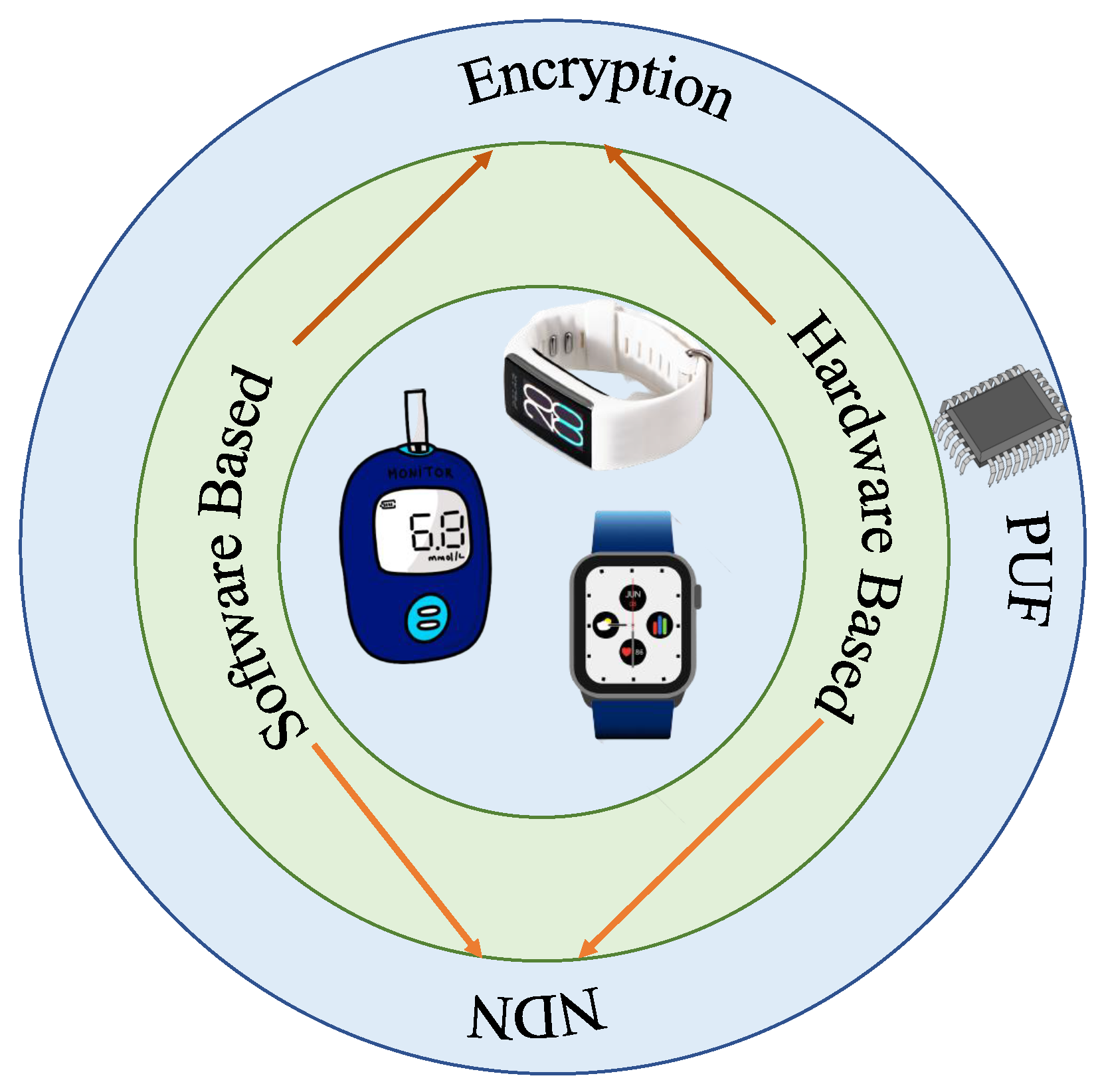
5. Security Mechanisms
- Uniqueness: Each challenge–response pair (CRP) of PUF is required to be different from one chip to another chip. Different PUFs should not generate the same CRP set. The ideal value of uniqueness is 50%. It is measured by hamming distance (HD). Hamming distance is measured by the difference in bits of responses.
- Reliability: A PUF should have to be reliable and have the capability to produce the same response for a particular challenge. The ideal value of the reliability of a PUF is 100%.
- Randomness: Bits (1’s and 0’s) of a response should have to be random. It is expected that, in a response, the presence of 1’s and 0’s will be the same. If a PUF follows this rule, then the randomness of the PUF will be 100%.
6. IoMT Security Solutions
6.1. Attribute Based
6.2. ECG Based
6.3. MAC Based
6.4. ECC-Based
6.5. Machine-Learning-Based
6.6. PUF Based
6.7. Blockchain Based
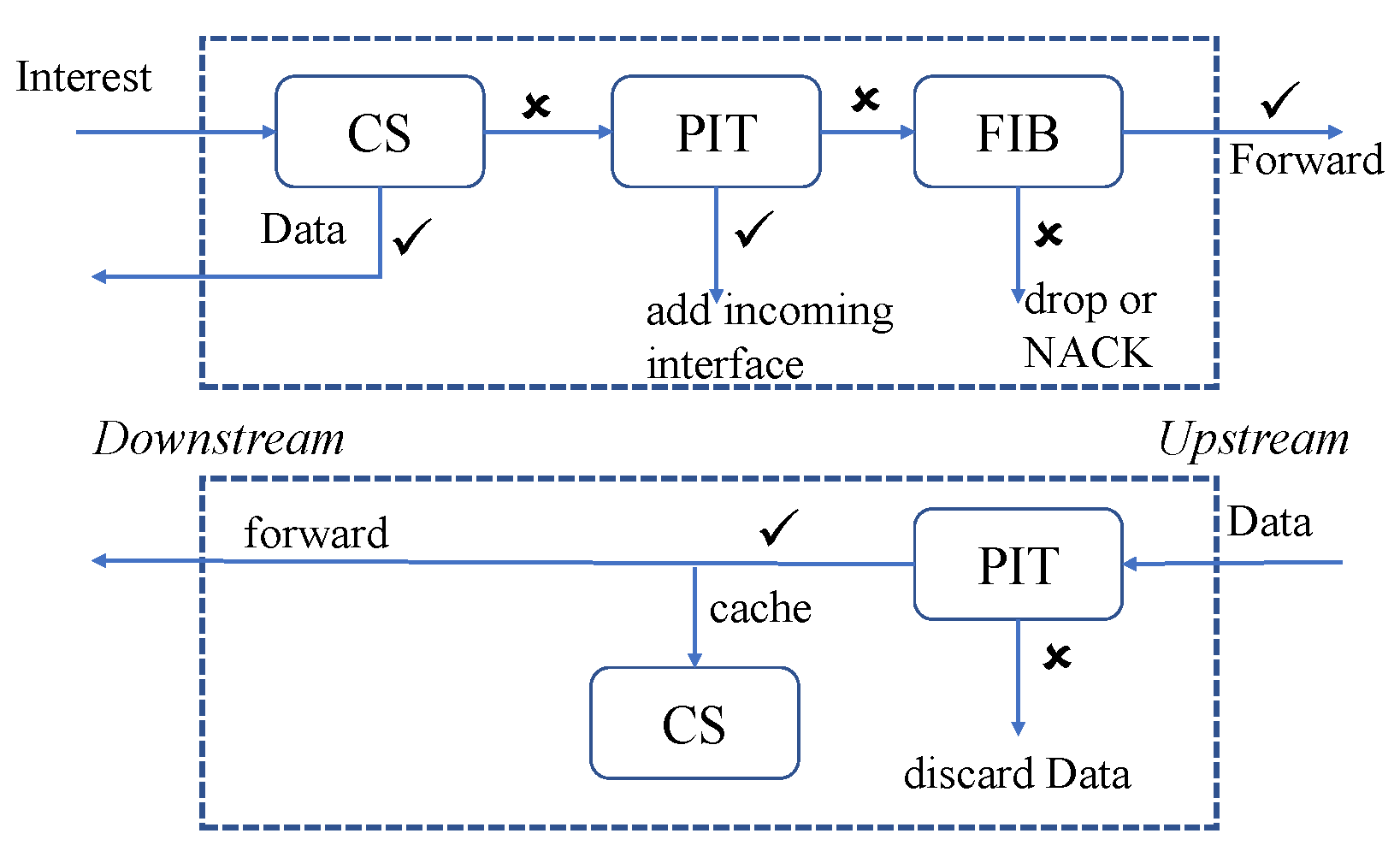
6.8. NDN Based
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Tran-Dang, H.; Krommenacker, N.; Charpentier, P.; Kim, D.S. Toward the Internet of Things for Physical Internet: Perspectives and Challenges. IEEE Internet Things J. 2020, 7, 4711–4736. [Google Scholar] [CrossRef]
- Wazid, M.; Singh, J.; Das, A.K.; Shetty, S.; Khan, M.K.; Rodrigues, J.J.P.C. ASCP-IoMT: AI-Enabled Lightweight Secure Communication Protocol for Internet of Medical Things. IEEE Access 2022, 10, 57990–58004. [Google Scholar] [CrossRef]
- Amin, F.; Majeed, A.; Mateen, A.; Abbasi, R.; Hwang, S.O. A Systematic Survey on the Recent Advancements in the Social Internet of Things. IEEE Access 2022, 10, 63867–63884. [Google Scholar] [CrossRef]
- Sadhu, P.; Yanambaka, V.P.; Abdelgawad, A.; Yelamarthi, K. NAHAP: PUF-Based Three Factor Authentication System for Internet of Medical Things. IEEE Consum. Electron. Mag. 2022. [Google Scholar] [CrossRef]
- Internet of Medical Things Market. Available online: https://www2.deloitte.com/ie/en/pages/life-sciences-and-healthcare/articles/internet-of-medical-things.html (accessed on 3 March 2022).
- Internet of Medical Things Revolutionizing Healthcare. Available online: https://aabme.asme.org/posts/internet-of-medical-things-revolutionizing-healthcare/ (accessed on 1 April 2021).
- Alamri, B.; Crowley, K.; Richardson, I. Blockchain-Based Identity Management Systems in Health IoT: A Systematic Review. IEEE Access 2022, 10, 59612–59629. [Google Scholar] [CrossRef]
- Aledhari, M.; Razzak, R.; Qolomany, B.; Al-Fuqaha, A.; Saeed, F. Biomedical IoT: Enabling Technologies, Architectural Elements, Challenges, and Future Directions. IEEE Access 2022, 10, 31306–31339. [Google Scholar] [CrossRef]
- Xu, C.; Wang, N.; Zhu, L.; Sharif, K.; Zhang, C. Achieving Searchable and Privacy-preserving Data Sharing for Cloud-assisted E-healthcare System. IEEE Internet Things J. 2019, 6, 8345–8356. [Google Scholar] [CrossRef]
- Hernandez, S.; Raison, M.; Torres, A.; Gaudet, G.; Achiche, S. From on-body Sensors to in-body Data for Health Monitoring and Medical Robotics: A Survey. In Proceedings of the Global Information Infrastructure and Networking Symposium (GIIS), Montreal, QC, Canada, 15–19 September 2014; pp. 1–5. [Google Scholar] [CrossRef]
- Noguchi, H.; Mori, T.; Sato, T. Framework for Search Application based on Time Segment of Sensor Data in Home Environment. In Proceedings of the Seventh International Conference on Networked Sensing Systems (INSS), Kassel, Germany, 15–18 June 2010; pp. 261–264. [Google Scholar] [CrossRef]
- Internet of Medical Things (IoMT) Market By Component, Platform, Connectivity Devices, Application and Is Expected to Reach USD 1,84,592.31 Million by 2028. Available online: https://www.marketwatch.com/press-release/internet-of-medical-things-iomt-market-by-component-platform-connectivity-devices-application-and-is-expected-to-reach-usd-18459231-million-by-2028-2022-04-26 (accessed on 22 June 2022).
- What Is the Internet of Medical Things (IoMT)? Available online: https://mobius.md/2019/03/06/what-is-the-iomt/ (accessed on 22 June 2022).
- Masud, M.; Gaba, G.S.; Alqahtani, S.; Muhammad, G.; Gupta, B.B.; Kumar, P.; Ghoneim, A. A Lightweight and Robust Secure Key Establishment Protocol for Internet of Medical Things in COVID-19 Patients Care. IEEE Internet Things J. 2021, 8, 15694–15703. [Google Scholar] [CrossRef]
- Saheed, Y.K.; Arowolo, M.O. Efficient Cyber Attack Detection on the Internet of Medical Things-Smart Environment Based on Deep Recurrent Neural Network and Machine Learning Algorithms. IEEE Access 2021, 9, 161546–161554. [Google Scholar] [CrossRef]
- Hameed, K.; Garg, S.; Amin, M.B.; Kang, B.; Khan, A. A Context-aware Information-based Clone Node Attack Detection Scheme in Internet of Things. J. Netw. Comput. Appl. 2022, 197, 103271. [Google Scholar] [CrossRef]
- Sengupta, J.; Ruj, S.; Bit, S.D. A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT. J. Netw. Comput. Appl. 2020, 149, 102481. [Google Scholar] [CrossRef]
- Shamsoshoara, A.; Korenda, A.; Afghah, F.; Zeadally, S. A Survey on Physical Unclonable Function (PUF)-based Security Solutions for Internet of Things. Comput. Netw. 2020, 183, 107593. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M. From Pre-Quantum to Post-Quantum IoT Security: A Survey on Quantum-Resistant Cryptosystems for the Internet of Things. IEEE Internet Things J. 2020, 7, 6457–6480. [Google Scholar] [CrossRef]
- Alwarafy, A.; Al-Thelaya, K.A.; Abdallah, M.; Schneider, J.; Hamdi, M. A Survey on Security and Privacy Issues in Edge-Computing-Assisted Internet of Things. IEEE Internet Things J. 2021, 8, 4004–4022. [Google Scholar] [CrossRef]
- Shakeel, T.; Habib, S.; Boulila, W.; Koubaa, A.; Javed, A.R.; Rizwan, M.; Gadekallu, T.R.; Sufiyan, M. A Survey on COVID-19 Impact in the Healthcare Domain: Worldwide Market Implementation, Applications, Security and Privacy Issues, Challenges and Future Prospects. Complex Intell. Syst. 2022, 1–32. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef] [Green Version]
- Arora, P.; Kaur, B.; Teixeira, M.A. Machine Learning-Based Security Solutions for Healthcare: An Overview. Emerg. Technol. Comput. Commun. Smart Cities 2022, 649–659. [Google Scholar]
- Rbah, Y.; Mahfoudi, M.; Balboul, Y.; Fattah, M.; Mazer, S.; Elbekkali, M.; Bernoussi, B. Machine Learning and Deep Learning Methods for Intrusion Detection Systems in IoMT: A survey. In Proceedings of the 2nd International Conference on Innovative Research in Applied Science, Engineering and Technology (IRASET), Meknes, Morocco, 3–4 March 2022; pp. 1–9. [Google Scholar] [CrossRef]
- Sadawi, A.A.; Hassan, M.S.; Ndiaye, M. A Survey on the Integration of Blockchain With IoT to Enhance Performance and Eliminate Challenges. IEEE Access 2021, 9, 54478–54497. [Google Scholar] [CrossRef]
- Khor, J.H.; Sidorov, M.; Woon, P.Y. Public Blockchains for Resource-Constrained IoT Devices—A State-of-the-Art Survey. IEEE Internet Things J. 2021, 8, 11960–11982. [Google Scholar] [CrossRef]
- Awad, A.; Fouda, M.M.; Khashaba, M.M.; Mohamed, E.R.; Hosny, K.M. Utilization of mobile edge computing on the Internet of Medical Things: A survey. ICT Express 2022. [Google Scholar] [CrossRef]
- Global Internet of Medical Things (IoMT) Market. Available online: https://www.alltheresearch.com/report/166/internet-of-medical-things-market (accessed on 6 June 2021).
- Indumathi, J.; Shankar, A.; Ghalib, M.R.; Gitanjali, J.; Hua, Q.; Wen, Z.; Qi, X. Block Chain Based Internet of Medical Things for Uninterrupted, Ubiquitous, User-Friendly, Unflappable, Unblemished, Unlimited Health Care Services (BC IoMT U 6 HCS). IEEE Access 2020, 8, 216856–216872. [Google Scholar] [CrossRef]
- How Connected Medical Devices Are Transforming Health Care. Available online: https://www2.deloitte.com/global/en/pages/life-sciences-and-healthcare/articles/medtech-internet-of-medical-things.html. (accessed on 3 March 2022).
- 5 Reasons IoMT Devices Make Sense for Healthcare Organizations. Available online: https://healthtechmagazine.net/article/2020/04/5-reasons-iomt-devices-make-sense-healthcare-organizations/ (accessed on 1 April 2021).
- Aman, A.H.M.; Hassan, W.H.; Sameen, S.; Attarbashi, Z.S.; Alizadeh, M.; Latiff, L.A. IoMT Amid COVID-19 Pandemic: Application, Architecture, Technology, and Security. J. Netw. Comput. Appl. 2020, 174, 102886. [Google Scholar] [CrossRef] [PubMed]
- Jahankhani, H.; Ibarra, J. Digital Forensic Investigation for the Internet of Medical Things (IoMT). Forensic Leg. Investig. Sci. 2019, 5, 29. [Google Scholar] [CrossRef]
- Alsubaei, F.; Abuhussein, A.; Shandilya, V.; Shiva, S. IoMT-SAF: Internet of Medical Things Security Assessment Framework. Internet Things 2019, 8, 100123. [Google Scholar] [CrossRef]
- Medical Device Security. Available online: https://healthitsecurity.com/tag/medical-device-security/ (accessed on 2 April 2021).
- Medical Device Cybersecurity in the Age of IoMT. Available online: https://www.medtechintelligence.com/column/medical-device-cybersecurity-in-the-age-of-iomt/ (accessed on 6 June 2021).
- Wu, L.; Du, X.; Guizani, M.; Mohamed, A. Access Control Schemes for Implantable Medical Devices: A Survey. IEEE Internet Things J. 2017, 4, 1272–1283. [Google Scholar] [CrossRef]
- Iwaya, L.H.; Ahmad, A.; Babar, M.A. Security and Privacy for mHealth and uHealth Systems: A Systematic Mapping Study. IEEE Access 2020, 8, 150081–150112. [Google Scholar] [CrossRef]
- ISO 14971—Risk Management. Available online: https://en.wikipedia.org/wiki/ISO_14971 (accessed on 21 June 2022).
- ISO 14971—Medical Devices—Application of Risk Management to Medical Devices. Available online: https://www.iso.org/standard/72704.html (accessed on 21 June 2022).
- Thiagarajan, H. Supporting Model based Safety and Security Assessment of High Assurance Systems. Ph.D. Thesis, Kansas State University, Manhattan, KS, USA, 2022. [Google Scholar]
- Sampath, T.; Thamizharasan, S.; Vijay Kumar Shetty, K.; Timiri Shanmugam, P.S. ISO 14971 and ISO 24971: Medical Device Risk Management. In Medical Device Guidelines and Regulations Handbook; Springer: Berlin, Germany, 2022; pp. 31–56. [Google Scholar]
- Lankinen, V. Risk Management in Academic Medical Device Research ENVI-RONMENT. 2022. [Google Scholar]
- Franconi, F. European Certification Procedures for Medical Devices: Technical Documentation for Annex XVI Medical Devices in Relation to the New Medical Device Regulation 2017/745. 2022. [Google Scholar]
- Hatcliff, J.; Vasserman, E.Y.; Carpenter, T.; Whillock, R. Challenges of Distributed Risk Management for Medical Application Platforms. In Proceedings of the Prpceeding of IEEE Symposium on Product Compliance Engineering (ISPCE), Hong Kong, 5–7 December 2018; pp. 1–14. [Google Scholar] [CrossRef]
- ISO 14971 Risk Management for Medical Devices: The Definitive Guide. Available online: https://www.greenlight.guru/blog/iso-14971-risk-management (accessed on 22 June 2022).
- What Is ISO 13485? Overview of the Standard. Available online: https://advisera.com/13485academy/what-is-iso-13485/ (accessed on 21 June 2022).
- EN ISO 13485:2016+A11:2021. Why This Amendment Is Important? Available online: https://www.qservegroup.com/eu/en/i1051/en-iso-13485-2016plusa11-2021–ennbsp-span-styleistext-align–justify-it-has-been-publishedspan (accessed on 21 June 2022).
- ISO 13485 Requirements: FAQ about the Top Medical Device Quality Management Standard. Available online: https://www.mastercontrol.com/gxp-lifeline/iso-13485-requirements-medical-devices/ (accessed on 21 June 2022).
- US FDA Formally Proposes Aligning Quality System Regulations with ISO 13485. Available online: https://www.emergobyul.com/blog/2022/02/us-fda-formally-proposes-aligning-quality-system-regulations-iso-13485 (accessed on 21 June 2022).
- ISO 13485:2016(en) Medical Devices—Quality Management Systems. Available online: https://www.iso.org/obp/ui#iso:std:iso:13485:ed-3:v1:en (accessed on 22 June 2022).
- IEC 60601-1-11:2015 Medical Electrical Equipment. Available online: https://www.iso.org/standard/65529.html#:~:text=IEC%2060601%2D1%2D11%3A2015%20applies%20to%20the%20basic,in%20the%20home%20healthcare%20environment. (accessed on 21 June 2022).
- A Practical Guide to IEC 60601-1. Available online: https://www.rigelmedical.com/gb/downloads/Rigel-Medical-A-Practical-guide-to-IEC-60601-1.pdf (accessed on 21 June 2022).
- Workshop on Risk Based EMC initiative in Europe. Available online: https://research.tue.nl/en/publications/workshop-on-risk-based-emc-initiative-in-europe (accessed on 21 June 2022).
- IEC 60601. Available online: https://en.wikipedia.org/wiki/IEC_60601 (accessed on 21 June 2022).
- ISO/IEC 80001 (Risk Management of Medical Devices on a Network). Available online: https://journals.lww.com/jcejournal/Citation/2016/07000/ISO_IEC_80001__Risk_Management_of_Medical_Devices.4.aspx (accessed on 21 June 2022).
- Anderson, S.; Williams, T. Cybersecurity and Medical Devices: Are the ISO/IEC 80001-2-2 Technical Controls up to the Challenge? Comput. Stand. Interfaces 2018, 56, 134–143. [Google Scholar] [CrossRef]
- IEC 80001-1:2010 Application of Risk Management for IT-Networks Incorporating Medical Devices—Part 1: Roles, Responsibilities and Activities. Available online: https://www.iso.org/standard/44863.html (accessed on 21 June 2022).
- IEC/TR 80001-2-2:2012 Application of Risk Management for IT-Networks Incorporating Medical Devices—Part 2-2: Guidance for the Communication of Medical Device Security Needs, Risks and Controls. Available online: https://www.iso.org/standard/57939.html (accessed on 21 June 2022).
- Regulation (EU) 2017/745. Available online: https://en.wikipedia.org/wiki/Regulation_(EU)_2017/745 (accessed on 22 June 2022).
- Clemens, N. The European Medical Device Regulation 2017/745/EU: Changes and Impact on Stakeholders. J. Clin. Res. Best Pract. 2018, 14, 1–7. [Google Scholar]
- Lang, M. Heart Rate Monitoring Apps: Information for Engineers and Researchers about the New European Medical Devices Regulation 2017/745. JMIR Biomed. Eng. 2017, 2, e8179. [Google Scholar] [CrossRef]
- Germundsson, F.; Kvist, N. MDR 2017/745-New EU Regulation for Medical Devices: A Process Description for EHR Manufacturers on How to Fulfill the Regulation. 2020. [Google Scholar]
- Ivanovska, E.; Ribarska, J.T.; Lazova, J.; Popstefanova, N.; Jovanoska, M.D.; Jolevska, S.T. Providing Clinical Evidence under the MDR 2017/745–New Challenges for Manufacturers in Medical Device Industry. Arh. Farm. 2019, 69, 39–49. [Google Scholar] [CrossRef]
- Kelso, K. EU Medical Device Regulation 2017/745 versus US Food and Drug Administration Approval of Dermal Filler Products. J. Aesthetic Nurs. 2020, 9, 320–324. [Google Scholar] [CrossRef]
- Guidance for the Content of Premarket Submissions for Software Contained in Medical Devices. Available online: https://www.fda.gov/regulatory-information/search-fda-guidance-documents/guidance-content-premarket-submissions-software-contained-medical-devices (accessed on 22 June 2022).
- FDA Issues Draft Guidance on Cybersecurity Considerations in Premarket Submissions for Medical Devices. Available online: https://www.wilmerhale.com/insights/client-alerts/fda-issues-draft-guidance-on-cybersecurity-considerations-in-premarket-submissions-for-medical-devices (accessed on 22 June 2022).
- Content of Premarket Submissions for Management of Cybersecurity in Medical Devices. Available online: https://www.fda.gov/media/86174/download (accessed on 22 June 2022).
- Content of Premarket Submissions for Management of Cybersecurity in Medical Devices. Draft Guidance for Industry and Food and Drug Administration Staff. Available online: https://www.regulations.gov/document/FDA-2013-D-0616-0002 (accessed on 22 June 2022).
- FDA Issues Guidance on Management of Cybersecurity in Medical Devices. Available online: https://chemical-facility-security-news.blogspot.com/2014/10/fda-issues-guidance-on-management-of.html (accessed on 22 June 2022).
- Postmarket Management of Cybersecurity in Medical Devices; Guidance for Industry and Food and Drug Administration. Available online: https://www.govinfo.gov/content/pkg/FR-2016-12-28/pdf/2016-31406.pdf (accessed on 22 June 2022).
- Postmarket Management of Cybersecurity in Medical Devices. Available online: https://www.fda.gov/regulatory-information/search-fda-guidance-documents/postmarket-management-cybersecurity-medical-devices (accessed on 22 June 2022).
- Postmarket Management of Cybersecurity in Medical Devices; Guidance for Industry and Food and Drug Administration. Available online: https://www.federalregister.gov/documents/2016/12/28/2016-31406/postmarket-management-of-cybersecurity-in-medical-devices-guidance-for-industry-and-food-and-drug (accessed on 22 June 2022).
- Comments to FDA’s Draft Guidance for Postmarket Management of Cybersecurity in Medical Devices. Available online: https://www.rapid7.com/globalassets/_pdfs/rapid7-comments/rapid7-comments-to-fda-draft-guidance-for-postmarket-management-of-cybersecurity-in-medical-devices—docket-no.-fda-2015-d-5105—apr.-19-2016.pdf (accessed on 22 June 2022).
- Comments of the Telecommunications Industry Association to the Food and Drug Administration’s Draft Guidance for Industry and Food and Drug Administration Staff; Content of Premarket Submissions for Management of Cybersecurity in Medical Devices. Available online: https://www.tiaonline.org/wp-content/uploads/2018/02/TIA_Comments-FDA_Guidance_re_Premarket_Submissions_for_Management_of_Cybersecurity_in_Medical_Devices_091213.pdf (accessed on 22 June 2022).
- Li, S.; Zhang, T.; Yu, B.; He, K. A Provably Secure and Practical PUF-based End-to-End Mutual Authentication and Key Exchange Protocol for IoT. IEEE Sensors J. 2020, 21, 5487–5501. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A Privacy-preserving and Scalable Authentication Protocol for the Internet of Vehicles. IEEE Internet Things J. 2020, 8, 1123–1139. [Google Scholar] [CrossRef]
- Alladi, T.; Chamola, V. HARCI: A Two-way Authentication Protocol for Three Entity Healthcare IoT Networks. IEEE J. Sel. Areas Commun. 2020, 39, 361–369. [Google Scholar] [CrossRef]
- Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A.; Yelamarthi, K. Performance Analysis of Ring Oscillator PUF for Robust Security in Smart Transportation. In Proceedings of the Proceedings of IEEE 7th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 14 June–31 July 2021; pp. 301–302. [Google Scholar]
- Sadhu, P.K.; Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E. Easy-Sec: PUF-Based Rapid and Robust Authentication Framework for the Internet of Vehicles. arXiv 2022, arXiv:2204.07709. [Google Scholar]
- Afanasyev, A.; Burke, J.; Refaei, T.; Wang, L.; Zhang, B.; Zhang, L. A Brief Introduction to Named Data Networking. In Proceedings of the IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 1–6. [Google Scholar]
- Saxena, D.; Raychoudhury, V.; Suri, N.; Becker, C.; Cao, J. Named Data Networking: A Survey. Comput. Sci. Rev. 2016, 19, 15–55. [Google Scholar] [CrossRef] [Green Version]
- Chiou, S.Y.; Ying, Z.; Liu, J. Improvement of a Privacy Authentication Scheme Based on Cloud for Medical Environment. J. Med. Syst. 2016, 40, 101. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. Smart Mutual Authentication Protocol for Cloud Based Medical Healthcare Systems using Internet of Medical Things. IEEE J. Sel. Areas Commun. 2020, 39, 346–360. [Google Scholar] [CrossRef]
- Park, K.; Noh, S.; Lee, H.; Das, A.K.; Kim, M.; Park, Y.; Wazid, M. LAKS-NVT: Provably Secure and Lightweight Authentication and Key Agreement Scheme without Verification Table in Medical Internet of Things. IEEE Access 2020, 8, 119387–119404. [Google Scholar] [CrossRef]
- Xu, Z.; Xu, C.; Liang, W.; Xu, J.; Chen, H. A Lightweight Mutual Authentication and Key Agreement Scheme for Medical Internet of Things. IEEE Access 2019, 7, 53922–53931. [Google Scholar] [CrossRef]
- Kumar, M.; Chand, S. A Secure and Efficient Cloud-Centric Internet-of-Medical-Things-Enabled Smart Healthcare System With Public Verifiability. IEEE Internet Things J. 2020, 7, 10650–10659. [Google Scholar] [CrossRef]
- Limaye, A.; Adegbija, T. HERMIT: A Benchmark Suite for the Internet of Medical Things. IEEE Internet Things J. 2018, 5, 4212–4222. [Google Scholar] [CrossRef]
- Lu, D.; Han, R.; Shen, Y.; Dong, X.; Ma, J.; Du, X.; Guizani, M. xTSeH: A Trusted Platform Module Sharing Scheme Towards Smart IoT-eHealth Devices. IEEE J. Sel. Areas Commun. 2020, 39, 370–383. [Google Scholar] [CrossRef]
- Hsu, C.L.; Le, T.V.; Hsieh, M.C.; Tsai, K.Y.; Lu, C.F.; Lin, T.W. Three-Factor UCSSO Scheme With Fast Authentication and Privacy Protection for Telecare Medicine Information Systems. IEEE Access 2020, 8, 196553–196566. [Google Scholar] [CrossRef]
- Chen, M.; Lee, T.F. Anonymous Group-oriented Time-bound Key Agreement for Internet of Medical Things in Telemonitoring Using Chaotic-maps. IEEE Internet Things J. 2021, 8, 13939–13949. [Google Scholar] [CrossRef]
- Dharminder, D.; Gupta, P. Security Analysis and Application of Chebyshev Chaotic Map in the Authentication Protocols. Int. J. Comput. Appl. 2019, 43, 1095–1103. [Google Scholar] [CrossRef]
- Li, J.; Su, Z.; Guo, D.; Choo, K.K.R.; Ji, Y. PSL-MAAKA: Provably-Secure and Lightweight Mutual Authentication and Key Agreement Protocol for Fully Public Channels in Internet of Medical Things. IEEE Internet Things J. 2021, 8, 13183–13195. [Google Scholar] [CrossRef]
- Zhang, L.; Ye, Y.; Mu, Y. Multiauthority Access Control With Anonymous Authentication for Personal Health Record. IEEE Internet Things J. 2020, 8, 156–167. [Google Scholar] [CrossRef]
- Hwang, Y.W.; Lee, I.Y. A Study on CP-ABE-Based Medical Data Sharing System with Key Abuse Prevention and Verifiable Outsourcing in the IoMT Environment. Sensors 2020, 20, 4934. [Google Scholar] [CrossRef]
- Hahn, C.; Kwon, H.; Hur, J. Trustworthy Delegation Toward Securing Mobile Healthcare Cyber-physical Systems. IEEE Internet Things J. 2018, 6, 6301–6309. [Google Scholar] [CrossRef]
- Liu, H.; Yao, X.; Yang, T.; Ning, H. Cooperative Privacy Preservation for Wearable Devices in Hybrid Computing-based Smart Health. IEEE Internet Things J. 2018, 6, 1352–1362. [Google Scholar] [CrossRef]
- Huang, P.; Guo, L.; Li, M.; Fang, Y. Practical Privacy-preserving ECG-based Authentication for IoT-based Healthcare. IEEE Internet Things J. 2019, 6, 9200–9210. [Google Scholar] [CrossRef]
- Siddiqi, M.A.; Doerr, C.; Strydis, C. IMDfence: Architecting a Secure Protocol for Implantable Medical Devices. IEEE Access 2020, 8, 147948–147964. [Google Scholar] [CrossRef]
- Kumar, P.; Lee, S.G.; Lee, H.J. E-SAP: Efficient-strong Authentication Protocol for Healthcare Applications using Wireless Medical Sensor Networks. Sensors 2012, 12, 1625–1647. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- He, D.; Kumar, N.; Chen, J.; Lee, C.C.; Chilamkurti, N.; Yeo, S.S. Robust Anonymous Authentication Protocol for Health-care Applications using Wireless Medical Sensor Networks. Multimed. Syst. 2015, 21, 49–60. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Liao, J.; Liang, W.; Khan, M.K. A New Authentication Protocol for Healthcare Applications using Wireless Medical Sensor Networks with User Anonymity. Secur. Commun. Netw. 2016, 9, 2643–2655. [Google Scholar] [CrossRef]
- Li, X.; Peng, J.; Obaidat, M.S.; Wu, F.; Khan, M.K.; Chen, C. A Secure Three-factor User Authentication Protocol with Forward Secrecy for Wireless Medical Sensor Network Systems. IEEE Syst. J. 2019, 14, 39–50. [Google Scholar] [CrossRef]
- Almogren, A.; Mohiuddin, I.; Din, I.U.; Almajed, H.; Guizani, N. FTM-IoMT: Fuzzy-Based Trust Management for Preventing Sybil Attacks in Internet of Medical Things. IEEE Internet Things J. 2020, 8, 4485–4497. [Google Scholar] [CrossRef]
- Ying, B.; Mohsen, N.R.; Nayak, A.A. Efficient Authentication Protocol for Continuous Monitoring in Medical Sensor Networks. IEEE Open J. Comput. Soc. 2021, 2, 130–138. [Google Scholar] [CrossRef]
- Liu, X.; Yang, X.; Luo, Y.; Zhang, Q. Verifiable Multi-keyword Search Encryption Scheme with Anonymous Key Generation for Medical Internet of Things. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Wang, J.; Wu, L.; Wang, H.; Choo, K.K.R.; He, D. An Efficient and Privacy-Preserving Outsourced Support Vector Machine Training for Internet of Medical Things. IEEE Internet Things J. 2020, 8, 458–473. [Google Scholar] [CrossRef]
- Awan, K.A.; Din, I.U.; Almogren, A.; Almajed, H.; Mohiuddin, I.; Guizani, M. NeuroTrust—Artificial-Neural-Network-Based Intelligent Trust Management Mechanism for Large-Scale Internet of Medical Things. IEEE Internet Things J. 2020, 8, 15672–15682. [Google Scholar] [CrossRef]
- Ding, Y.; Wu, G.; Chen, D.; Zhang, N.; Gong, L.; Cao, M.; Qin, Z. DeepEDN: A Deep-Learning-Based Image Encryption and Decryption Network for Internet of Medical Things. IEEE Internet Things J. 2020, 8, 1504–1518. [Google Scholar] [CrossRef]
- Li, J.; Ji, Y.; Choo, K.K.R.; Hogrefe, D. CL-CPPA: Certificate-Less Conditional Privacy-Preserving Authentication Protocol for the Internet of Vehicles. IEEE Internet Things J. 2019, 6, 10332–10343. [Google Scholar] [CrossRef]
- Yanambaka, V.P.; Mohanty, S.P.; Kougianos, E.; Puthal, D. PMsec: Physical Unclonable Function-Based Robust and Lightweight Authentication in the Internet of Medical Things. IEEE Trans. Consum. Electron. 2019, 65, 388–397. [Google Scholar] [CrossRef]
- Gope, P.; Gheraibia, Y.; Kabir, S.; Sikdar, B. A secure IoT-based modern healthcare system with fault-tolerant decision making process. IEEE J. Biomed. Health Inform. 2020, 25, 862–873. [Google Scholar] [CrossRef] [PubMed]
- Abdellatif, A.A.; Samara, L.; Mohamed, A.; Erbad, A.; Chiasserini, C.F.; Guizani, M.; O’Connor, M.D.; Laughton, J. Medge-chain: Leveraging edge computing and blockchain for efficient medical data exchange. IEEE Internet Things J. 2021, 8, 15762–15775. [Google Scholar] [CrossRef]
- Xu, J.; Xue, K.; Li, S.; Tian, H.; Hong, J.; Hong, P.; Yu, N. Healthchain: A Blockchain-Based Privacy Preserving Scheme for Large-Scale Health Data. IEEE Internet Things J. 2019, 6, 8770–8781. [Google Scholar] [CrossRef]
- Liu, X.; Wang, Z.; Jin, C.; Li, F.; Li, G. A Blockchain-based Medical Data Sharing and Protection Scheme. IEEE Access 2019, 7, 118943–118953. [Google Scholar] [CrossRef]
- Lin, P.; Song, Q.; Yu, F.R.; Wang, D.; Guo, L. Task Offloading for Wireless VR-Enabled Medical Treatment With Blockchain Security Using Collective Reinforcement Learning. IEEE Internet Things J. 2021, 8, 15749–15761. [Google Scholar] [CrossRef]
- Garg, N.; Wazid, M.; Das, A.K.; Singh, D.P.; Rodrigues, J.J.; Park, Y. BAKMP-IoMT: Design of blockchain enabled authenticated key management protocol for internet of medical things deployment. IEEE Access 2020, 8, 95956–95977. [Google Scholar] [CrossRef]
- Egala, B.S.; Pradhan, A.K.; Badarla, V.R.; Mohanty, S.P. Fortified-chain: A blockchain-based framework for security and privacy-assured internet of medical things with effective access control. IEEE Internet Things J. 2021, 8, 11717–11731. [Google Scholar] [CrossRef]
- Ullah, S.S.; Hussain, S.; Alroobaea, R.; Ali, I. Securing NDN-Based Internet of Health Things through Cost-Effective Signcryption Scheme. Wirel. Commun. Mob. Comput. 2021, 2021, 5569365. [Google Scholar]
- Wang, X.; Cai, S. Secure healthcare monitoring framework integrating NDN-based IoT with edge cloud. Future Gener. Comput. Syst. 2020, 112, 320–329. [Google Scholar] [CrossRef]
- Ullah, S.S.; Hussain, S.; Gumaei, A.; Alhilal, M.S.; Alkhamees, B.F.; Uddin, M.; Al-Rakhami, M. A Cost-Effective Approach for NDN-Based Internet of Medical Things Deployment. Comput. Mater. Contin. 2022, 70, 233–249. [Google Scholar]


| Survey | Citation | Year | Objective |
|---|---|---|---|
| A Comprehensive Survey on Attacks, Security Issues and Blockchain Solutions for IoT and IIoT | Sengupta et al. [17] | 2019 | Develop blockchain-based application-specific solutions for IoT and IIoT, and classify IoT attacks and responses. |
| From Pre-Quantum to Post-Quantum IoT Security: A Survey on Quantum-Resistant Cryptosystems for the Internet of Things | Fernández-Caramés et al. [19] | 2020 | Impacts and vulnerabilities of conventional and quantum security. |
| A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security | Al-Garadi et al. [22] | 2020 | Hazards to IoT security and related solutions utilizing deep learning and machine learning. |
| A Survey on Physical Unclonable Function (PUF)-based Security Solutions for Internet of Things | Shamsoshoara et al. [18] | 2020 | PUF-based security mechanisms for IoT technology. |
| A Survey on the Integration of Blockchain With IoT to Enhance Performance and Eliminate Challenges | Sawadi et al. [25] | 2021 | Using blockchain technology, threats and risks are repelled. |
| A Survey on Security and Privacy Issues in Edge- Computing-Assisted Internet of Things | Alwarafy et al. [20] | 2021 | Utilizing edge computing to enhance data processing and intrusion resistance. |
| Public Blockchains for Resource-Constrained IoT Devices—A State-of-the-Art Survey | Khor et al. [26] | 2021 | Describe the benefits of blockchain technology and how resource-constrained devices could use it. |
| Machine Learning-Based Security Solutions for Healthcare: An Overview | Arora et al. [23] | 2022 | Healthcare security solutions using machine learning. |
| Utilization of mobile edge computing on the Internet of Medical Things: A survey | Awad et al. [27] | 2022 | Analyze the way to enhance quality and performance of IoMT using edge computing. |
| Machine Learning and Deep Learning Methods for Intrusion Detection Systems in IoMT: A survey | Rbah et al. [24] | 2022 | To make a defense system in IoMT using machine learning. |
| A survey on COVID-19 impact in the healthcare domain: worldwide market implementation, applications, security and privacy issues, challenges and future prospects | Shakeel et al. [21] | 2022 | Focused on healthcare systems, devices and different communication protocol rather than security systems. |
| This Paper | - | - | Ecosystem of healthcare, importance of IoMT in healthcare, EU and FDA regulations for healthcare with security issues, established security mechanisms and detailed discussion of different proposed security protocols. |
| Author | Year | Objective | Technique Used | Type of Data | Framework | Pros | Cons |
|---|---|---|---|---|---|---|---|
| Deebak et al. [84] | 2020 | Data security and anonymity | PKI | Medical records | SSA | Solves Chiou et al.’s work [83] | Computational cost is high |
| Park et al. [85] | 2020 | To solve issues of MAKA scheme | PKI | Medical IoT data | LAKS-NVT | Does not require a server verification table | Traceable |
| Kumar et al. [87] | 2020 | Secure and efficient cloud-centric IoMT-enabled smart healthcare system | PKI | PHI file | EF-IDASC | Low energy consumption | DoS, reply attack |
| Limaye et al. [88] | 2018 | Facilitate research into new microarchitectures and optimizations | PKI | Healthcare data | HERMIT | Efficient processors for IoMT applications | Basic security |
| Lu et al. [89] | 2020 | TPM deployed in non-TPM protected embedded device via network | PKI | Sensor data | xTSeH | Does not discard request due to increased traffic | Security improvement required |
| Hsu et al. [90] | 2020 | Remove storing credentials and secure communication | PKI | eHealth data | UCSSO | No storage and central authority | Service could be interrupted |
| Chen et al. [91] | 2021 | Reduce energy consumption, achieve privacy and security | PKI & Chaotic map | Health data | - | Group authentication | Server impersonation |
| Li et al. [93] | 2021 | Reduce complexity and secure communication | PKI | Medical data | PSL-MAAKA | Lightweight scheme | Much time and storage required |
| Zhang et al. [94] | 2020 | Protect personal health records | ABE | PHR file | PHR sharing framework | Support offline and online | MITM, DoS, etc., security |
| Liu et al. [97] | 2018 | Enhance privacy preserving and efficient data structure | CP-ABE | Biomedical data | - | Server impersonation attack | Lot of storage and computation |
| Hwang et al. [95] | 2020 | Improve CP-ABE based scheme | CP-ABE | PHI file | - | Resolves key abuse problem | PHI leakage |
| Huang et al. [98] | 2019 | Protection from unauthorized entity | ECG | PHR file | - | Remove noise, light algorithm | No anonymous identity |
| Xu et al. [9] | 2019 | Secure data sharing | MAC | PHI file | - | Multi-keyword search | Device to gateway security |
| Siddiqi et al. [99] | 2020 | Security protocol for IMD ecosystem | MAC | Medical data | IMDfence | 7% energy consumption | No user anonymity |
| Hahn et al. [96] | 2020 | Attack MAC-based scheme and countermeasure | Commitment (MAC) | Medical data | - | Low verification time | DoS, server impersonation |
| Li et al. [103] | 2019 | Enhance security of previous work | ECC | Medical data | 3FUAP | Vulnerability and countermeasure | Computational cost |
| Almog- ren et al. [104] | 2020 | Fake node detection and deactivation | ECC | eHealth data | FTM | Double filter | Mainly focused on Sybil attack |
| Ying et al. [105] | 2021 | Secure communication | ECC | Medical data | - | Low computational time | High communication overhead |
| Liu et al. [106] | 2021 | Achieve data SNP preservation | ECC | EHR file | - | Major decryption on server side | Complex |
| Wang et al. [107] | 2020 | Ensure data privacy | Machine learning | Medical data | EPoSVM | Efficiency | Significant time required |
| Awan et al. [108] | 2020 | Maintains a robust network by predicting and eliminating malicious nodes | Supervised learning and ECC | Health data | NeuroTrust | Lightweight encryption | Needs focus on attacks |
| Ding et al. [109] | 2020 | To preserve the privacy or security of the patient | Deep learning | DeepEDN | Image | Fast | Needs robustness and server verification |
| Yanambaka et al. [111] | 2019 | Secure communication | PUF | Medical data | Pmsec | Lightweight | ML attack |
| Gope et al. [112] | 2020 | Secure and efficient authentication | PUF | Healthcare monitoring | - | Less computation at server | Two CRPs per transaction |
| Alladi et al. [78] | 2020 | To achieve physical security | PUF | Health data | HARCI | Low time in computation | Unstable CRP can cause failure |
| Author | Year | Objective | Technique Used | Type of Data | Framework | Pros | Cons |
|---|---|---|---|---|---|---|---|
| Abdellatif et al. [113] | 2021 | Process large amounts of medical data | Blockchain | Medical data | MEdge-Chain | Remote monitoring, different actions for different data | Security is not focused |
| Xu et al. [114] | 2019 | Fine-grained access control | Blockchain (PoW) | Health data | Healthchain | User can update key if suspicious | Not suitable for high adversary |
| Liu et al. [115] | 2019 | Data sharing and privacy preservation | Blockchain (DPoS) | EHR file | - | Symptom matching communication | High overhead |
| Lin et al. [116] | 2021 | Task offloading and data processing to resist malicious attacks | Blockchain & MAC | VR video and feedback | - | Common view of similar patients | High computing capacity required |
| Garg et al. [117] | 2020 | Secure exchange of health-related confidential and private information | Blockchain & ECC | Health data | BAKMP | Dynamic node addition | Expensive computation |
| Egala et al. [118] | 2021 | Efficient secure exchange for decentralized network | Blockchain & ECC | EHR file | Fortified-Chain | Low energy, fast response | Ring tamper resistance instead of device |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A.; Yelamarthi, K. Prospect of Internet of Medical Things: A Review on Security Requirements and Solutions. Sensors 2022, 22, 5517. https://doi.org/10.3390/s22155517
Sadhu PK, Yanambaka VP, Abdelgawad A, Yelamarthi K. Prospect of Internet of Medical Things: A Review on Security Requirements and Solutions. Sensors. 2022; 22(15):5517. https://doi.org/10.3390/s22155517
Chicago/Turabian StyleSadhu, Pintu Kumar, Venkata P. Yanambaka, Ahmed Abdelgawad, and Kumar Yelamarthi. 2022. "Prospect of Internet of Medical Things: A Review on Security Requirements and Solutions" Sensors 22, no. 15: 5517. https://doi.org/10.3390/s22155517
APA StyleSadhu, P. K., Yanambaka, V. P., Abdelgawad, A., & Yelamarthi, K. (2022). Prospect of Internet of Medical Things: A Review on Security Requirements and Solutions. Sensors, 22(15), 5517. https://doi.org/10.3390/s22155517








