Energy Efficient Consensus Approach of Blockchain for IoT Networks with Edge Computing
(This article belongs to the Section Intelligent Sensors)
Abstract
:1. Introduction
- 1.
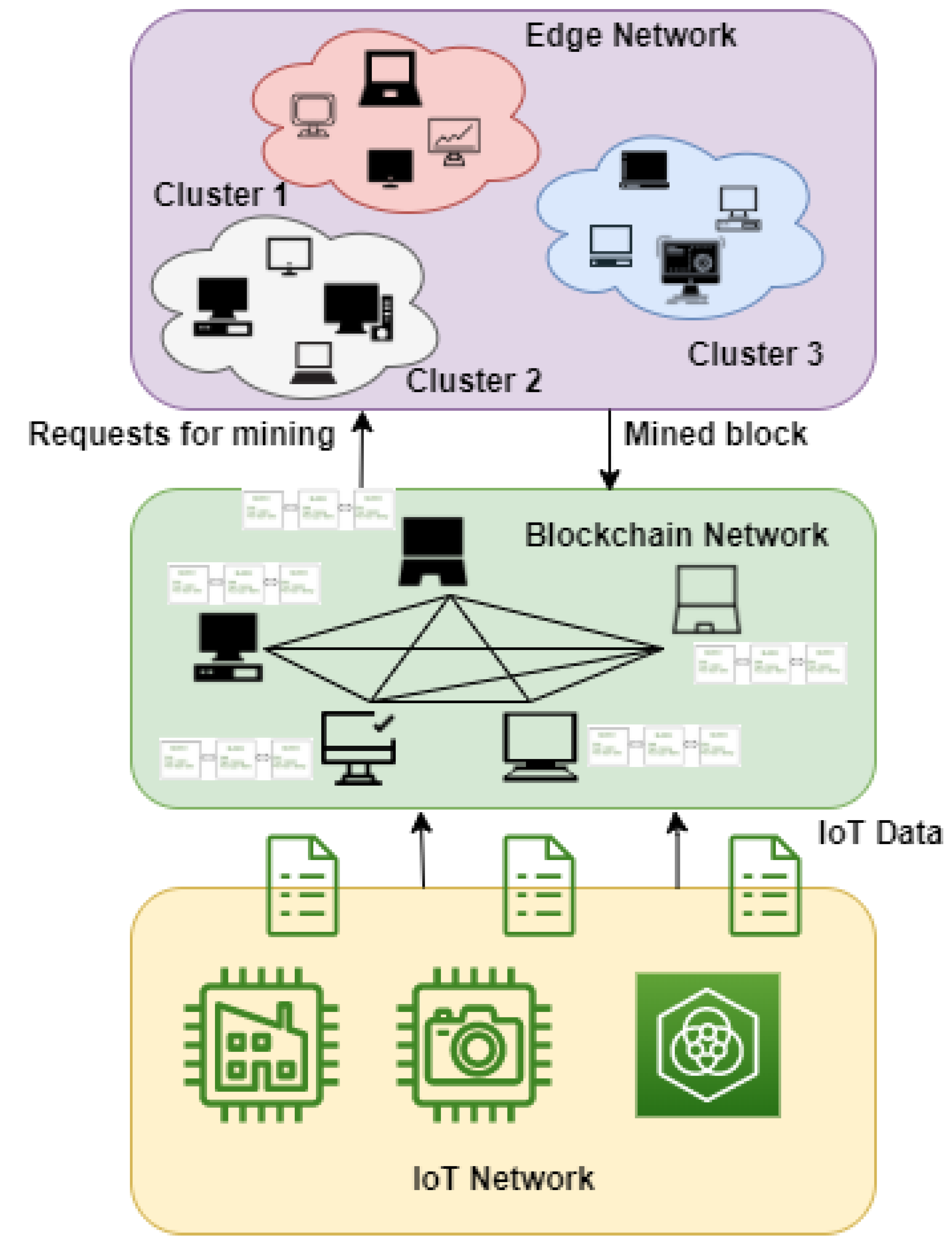
- Data generated by IoT devices is sent to the blockchain network for security purposes. IoT devices are incapable of performing extensive computations required for reaching consensus.
- 2.
- Highly capable devices of the edge network participate in reaching the consensus by becoming miners of the blockchain as computations from the blockchain environment are offloaded to the edge network.
- 3.
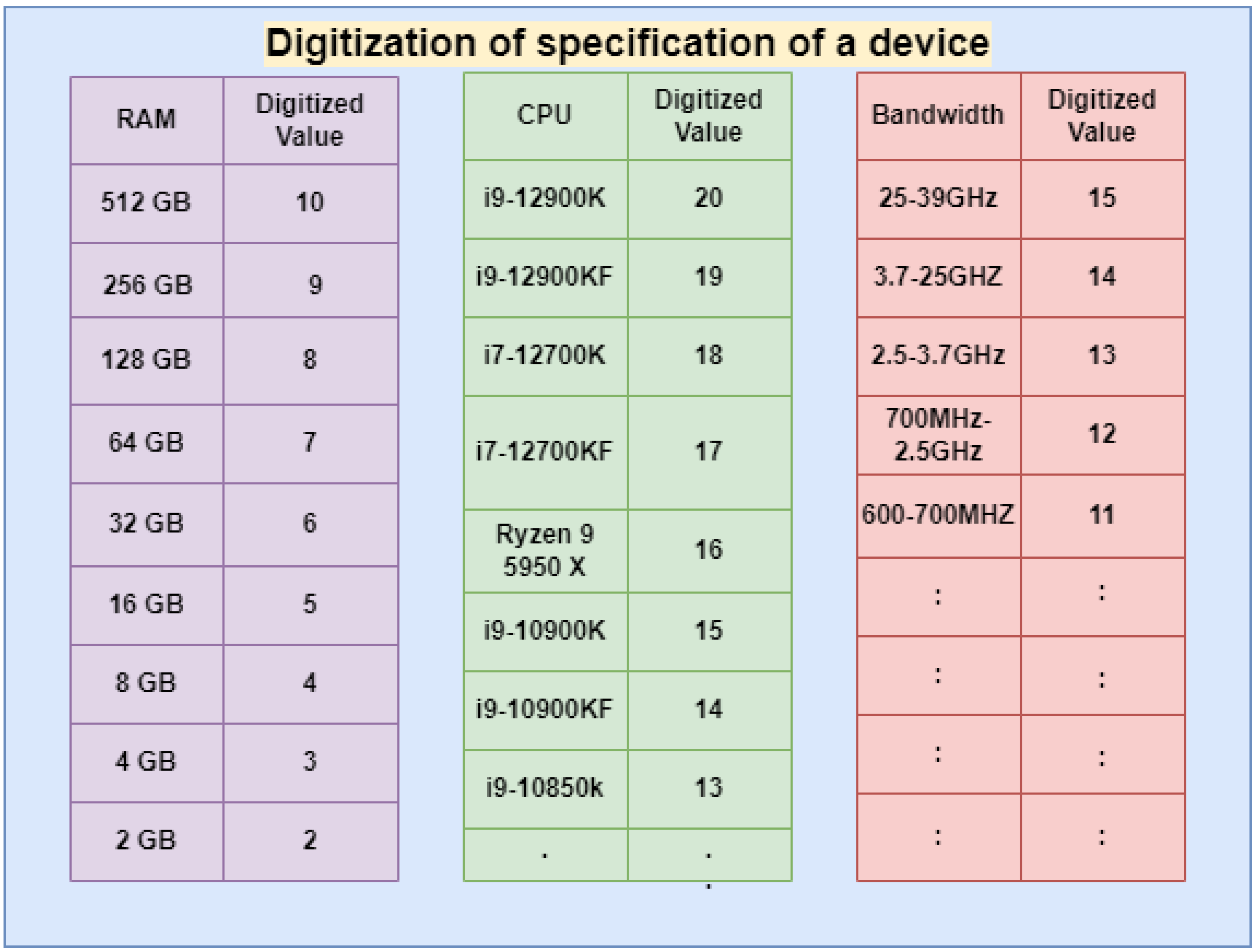
- Specifications of the devices on the basis of RAM, CPU, and the bandwidth of the network are used for the selection of the miner. Formula is also used for finalizing the miner amongst different capable miners.
2. Related Work
2.1. Modifying the Consensus Approach of the Blockchain
2.2. Improving Energy Consumption Using Non-Consensus Approach
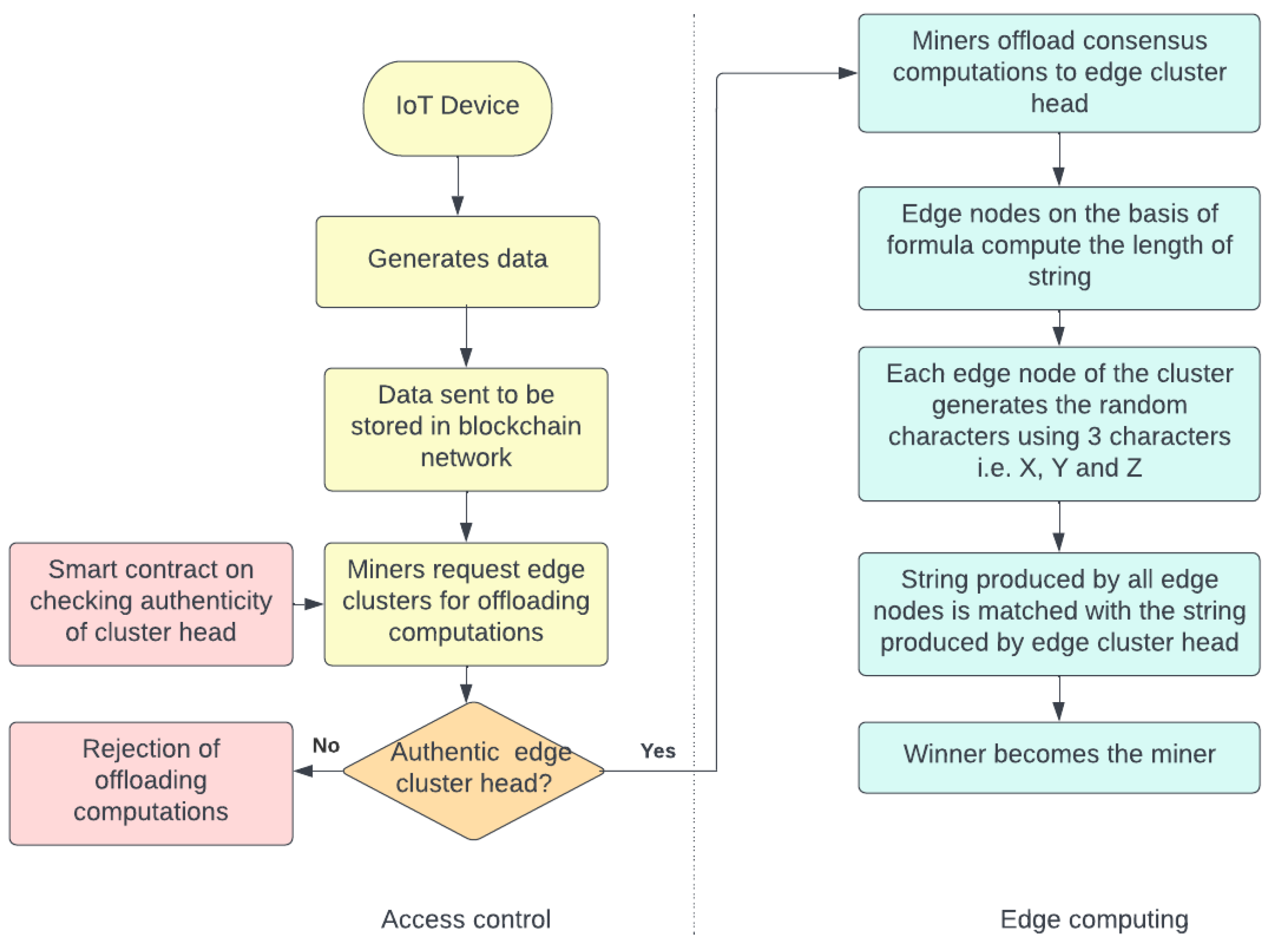
3. System Model
3.1. Components of the System
- IoT devices: the IoT devices mainly consist of sensors, actuators, radio frequency identification system (RFID), etc., for the collection of environmental data. The sensor nodes are used for sensing the data according to their specialization. The IoT devices in the proposed model may consist of devices of smart city, smart agriculture, smart industry, etc.
- Blockchain network: the blockchain network stores the IoT data securely in a distributed and decentralized manner.
- Transaction pool: the data generated by IoT devices are stored in a transaction pool. The miners collect data from the pool for the creation of block.
- Smart contract: the smart contract contains the information of the authenticity of nodes. Smart contracts are referred every time before finalizing the edge cluster head.
- Edge cluster: edge clusters are formed at edge networks. Each edge cluster consists of a cluster head, which is formed randomly on the basis of the formula mentioned in the next section.
- Edge nodes: edge nodes are the part of the edge network. All edge nodes are capable of performing complex computational tasks of reaching consensus in the blockchain.
3.2. Assumptions
- All edge nodes possess high computational power.
- All edge nodes and blockchain nodes are authentic.
- Smart contract stores the information of authenticity of nodes.
- All nodes of the blockchain network possess high storage capacity.
3.3. Workflow of the System Model
4. Proposed Method
- n is the number of miners in the edge cluster;
- s is the sum of the digitized values of a given device.
5. Results and Discussions
5.1. Experimental Setup
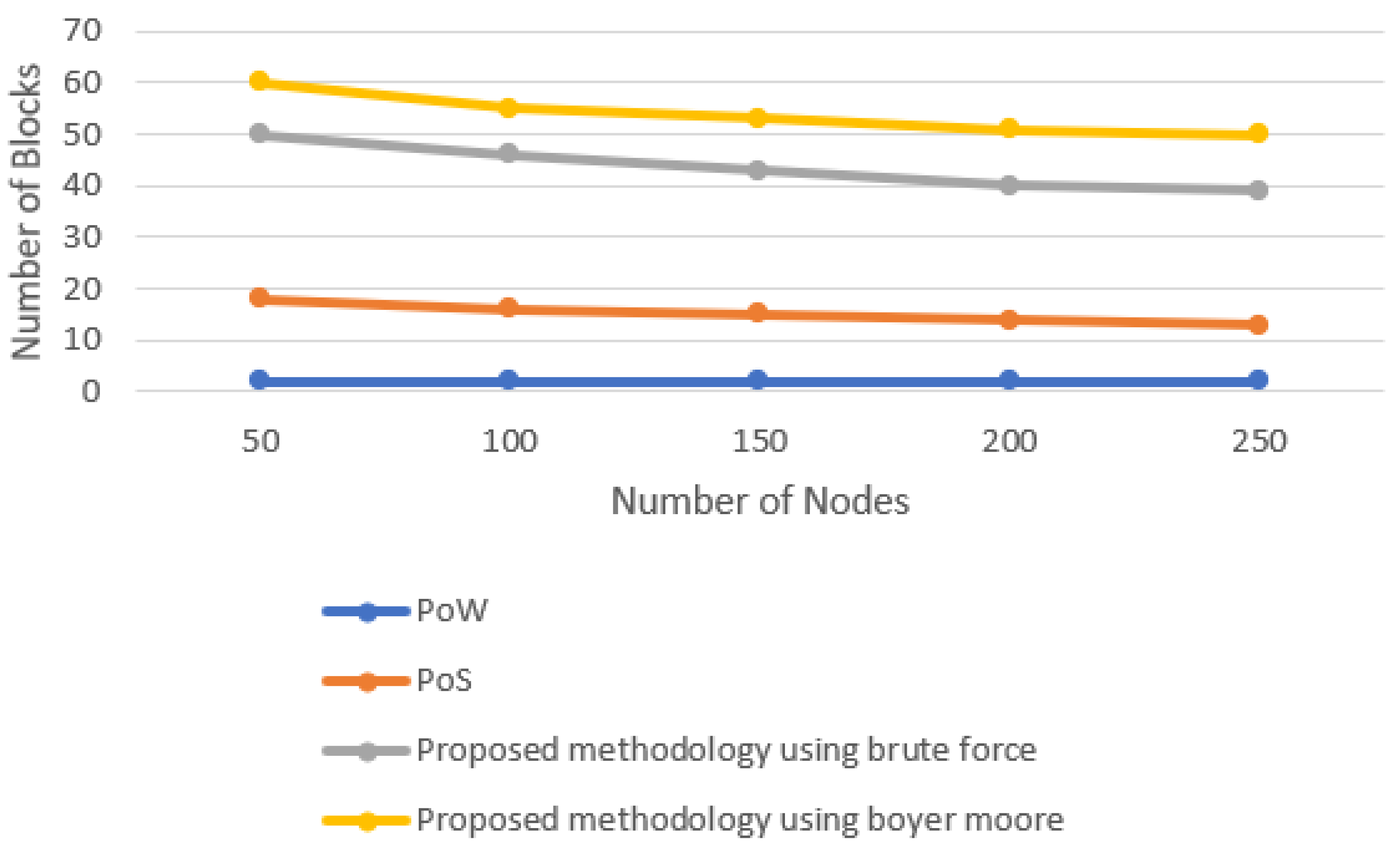
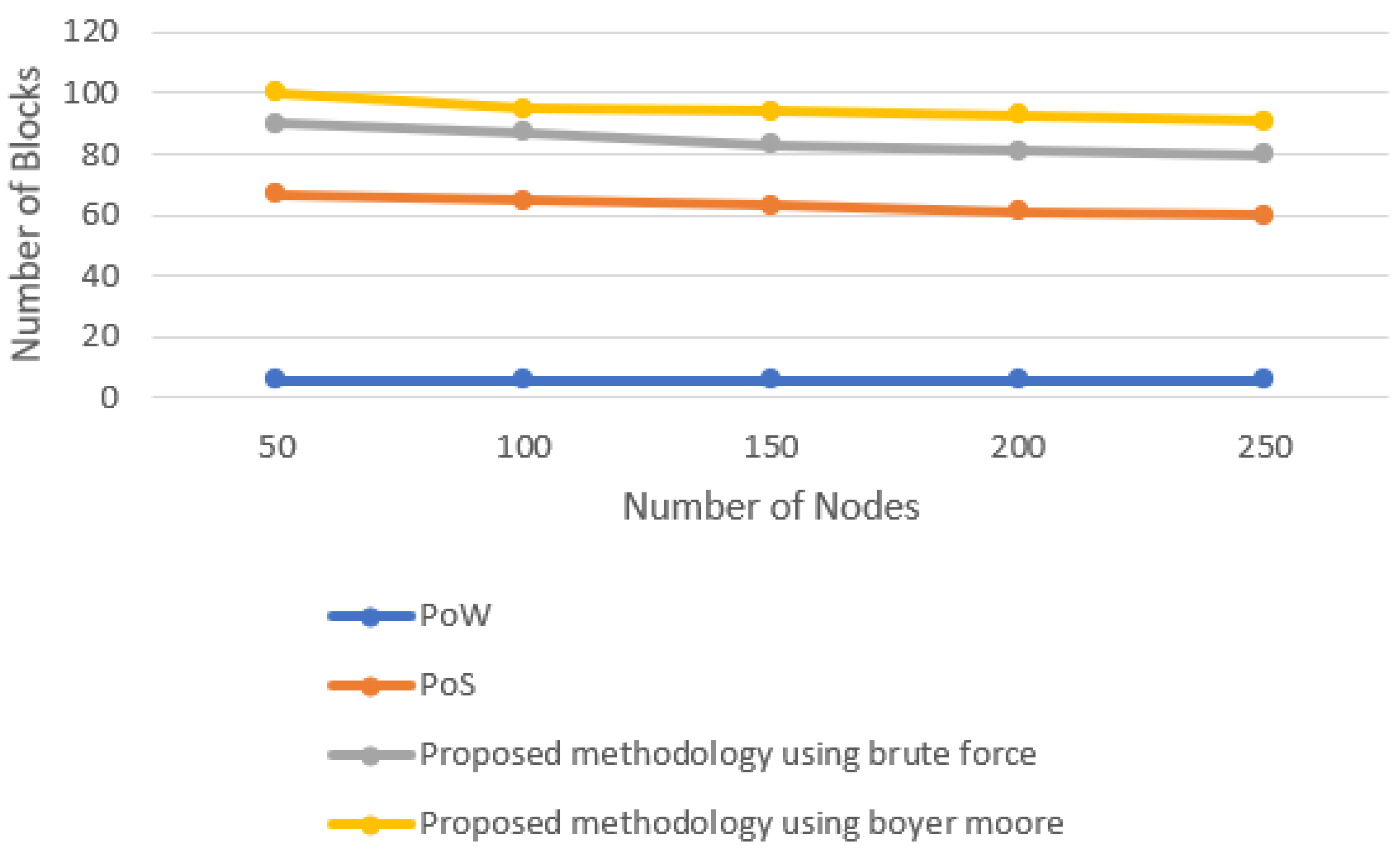
5.2. Efficiency of Block Generation
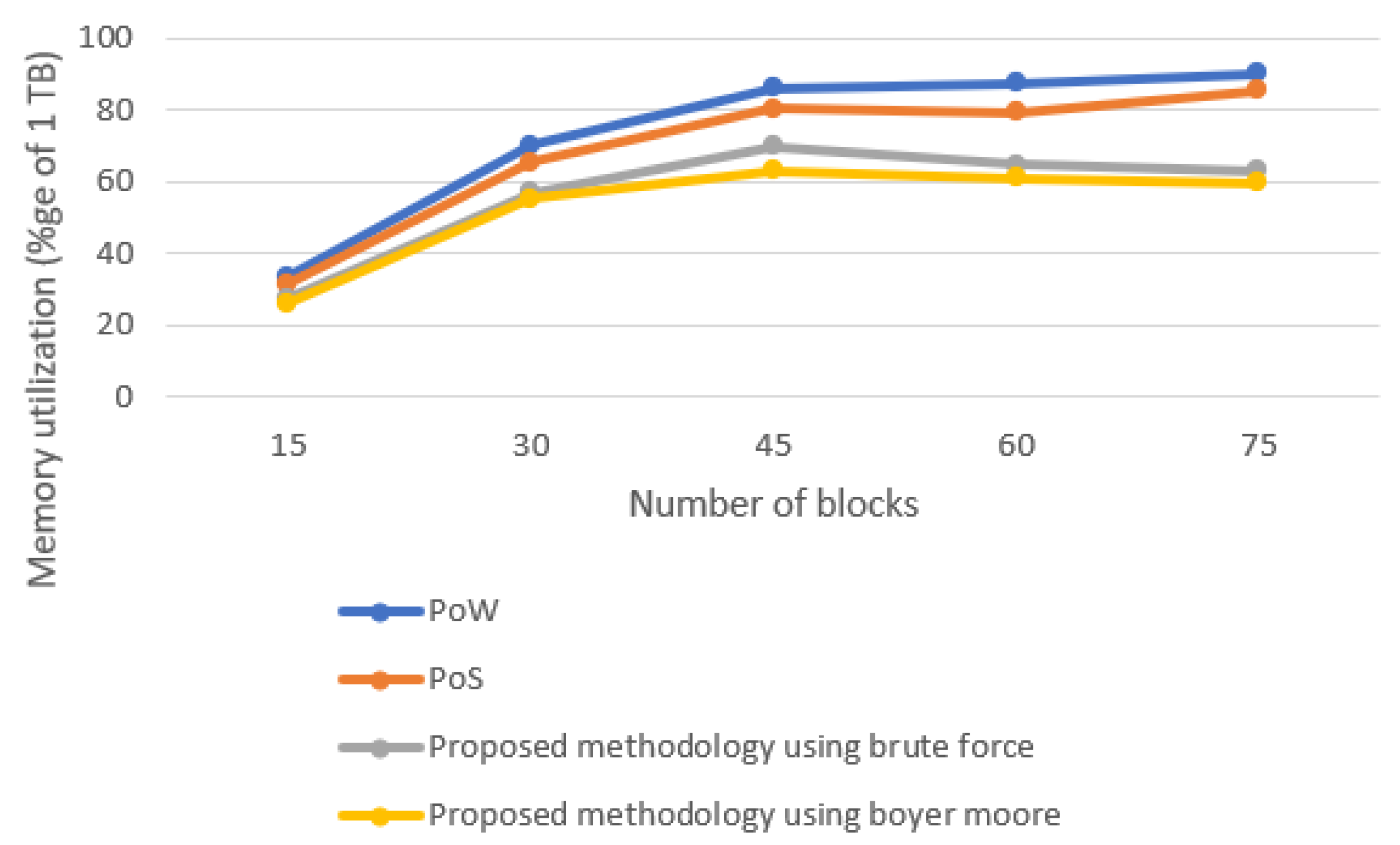
5.3. Memory Utilization
5.4. Energy Consumption
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Liu, Y.; Su, Z.; Wang, Y. Energy-Efficient and Physical Layer Secure Computation Offloading in Blockchain-Empowered Internet of Things. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Rani, S.; Kataria, A.; Sharma, V.; Ghosh, S.; Karar, V.; Lee, K.; Choi, C. Threats and corrective measures for IoT security with observance of cybercrime: A survey. Wirel. Commun. Mob. Comput. 2021, 2021, 5579148. [Google Scholar] [CrossRef]
- Wang, Y.; Su, Z.; Zhang, N.; Chen, J.; Sun, X.; Ye, Z.; Zhou, Z. SPDS: A Secure and Auditable Private Data Sharing Scheme for Smart Grid Based on Blockchain. IEEE Trans. Ind. Informatics 2020, 17, 7688–7699. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Xu, Q.; Zhang, N. LVBS: Lightweight vehicular blockchain for secure data sharing in disaster rescue. IEEE Trans. Dependable Secur. Comput. 2020, 19, 19–32. [Google Scholar] [CrossRef]
- Nair, R.; Gupta, S.; Soni, M.; Shukla, P.K.; Dhiman, G. An approach to minimize the energy consumption during blockchain transaction. Mater. Today Proc. 2020. [Google Scholar] [CrossRef]
- Wright, C.S. Bitcoin: A Peer-to-Peer Electronic Cash System. (21 August 2008). Available online: https://ssrn.com/abstract=3440802 (accessed on 27 March 2022).
- Available online: https://www.blockchain.com/charts/hash-rate (accessed on 27 March 2022).
- Rizzardi, A.; Sicari, S.; Miorandi, D.; Coen-Porisini, A. Securing the access control policies to the Internet of Things resources through permissioned blockchain. Concurr. Comput. Pract. Exp. 2022, e6934. [Google Scholar] [CrossRef]
- Billah, M.; Mehedi, S.; Anwar, A.; Rahman, Z.; Islam, R. A Systematic Literature Review on Blockchain Enabled Federated Learning Framework for Internet of Vehicles. arXiv 2022, arXiv:2203.05192. [Google Scholar]
- Chen, X.; Li, M.; Zhong, H.; Ma, Y.; Hsu, C.H. DNNOff: Offloading DNN-based intelligent IoT applications in mobile edge computing. IEEE Trans. Ind. Informat. 2021, 18, 2820–2829. [Google Scholar] [CrossRef]
- Fan, Y.; Wu, H.; Paik, H.Y. DR-BFT: A consensus algorithm for blockchain-based multi-layer data integrity framework in dynamic edge computing system. Future Gener. Comput. Syst. 2021, 124, 33–48. [Google Scholar] [CrossRef]
- Xu, J.; Wang, S.; Zhou, A.; Yang, F. Edgence: A blockchain-enabled edge-computing platform for intelligent IoT-based dApps. China Commun. 2020, 17, 78–87. [Google Scholar] [CrossRef]
- Sharma, A.; Tomar, R.; Chilamkurti, N.; Kim, B.G. Blockchain based smart contracts for internet of medical things in e-healthcare. Electronics 2020, 9, 1609. [Google Scholar] [CrossRef]
- Hîrţan, L.A.; Dobre, C.; González-Vélez, H. Blockchain-based reputation for intelligent transportation systems. Sensors 2020, 20, 791. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Manogaran, G.; Alazab, M.; Shakeel, P.M.; Hsu, C.H. Blockchain assisted secure data sharing model for Internet of Things based smart industries. IEEE Trans. Reliab. 2021, 71, 348–358. [Google Scholar] [CrossRef]
- Liu, C.M.; Badigineni, M.; Lu, S.W. Adaptive Blocksize for IoT Payload Data on Fabric Blockchain. In Proceedings of the 2021 30th Wireless and Optical Communications Conference (WOCC), Taipei, Taiwan, 7–8 October 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 92–96. [Google Scholar]
- Zhaofeng, M.; Jialin, M.; Jihui, W.; Zhiguang, S. Blockchain-based decentralized authentication modeling scheme in edge and IoT environment. IEEE Internet Things J. 2020, 8, 2116–2123. [Google Scholar] [CrossRef]
- Luo, X.; Yang, P.; Wang, W.; Gao, Y.; Yuan, M. S-PoDL: A two-stage computational-efficient consensus mechanism for blockchain-enabled multi-access edge computing. Phys. Commun. 2021, 46, 101338. [Google Scholar] [CrossRef]
- Ayaz, F.; Sheng, Z.; Tian, D.; Guan, Y.L. A Proof-of-Quality-Factor (PoQF)-Based Blockchain and Edge Computing for Vehicular Message Dissemination. IEEE Internet Things J. 2020, 8, 2468–2482. [Google Scholar] [CrossRef]
- Wang, D.; Wang, Z.; Lian, X. Research on Distributed Energy Consensus Mechanism Based on Blockchain in Virtual Power Plant. Sensors 2022, 22, 1783. [Google Scholar] [CrossRef]
- Sheikh, A.; Kamuni, V.; Urooj, A.; Wagh, S.; Singh, N.; Patel, D. Secured energy trading using byzantine-based blockchain consensus. IEEE Access 2019, 8, 8554–8571. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Rai, M.K.; Thomas, R.; Kim, T.H. Proof-of-work consensus approach in blockchain technology for cloud and fog computing using maximization-factorization statistics. IEEE Internet Things J. 2019, 6, 6835–6842. [Google Scholar] [CrossRef]
- Maitra, S.; Yanambaka, V.P.; Abdelgawad, A.; Puthal, D.; Yelamarthi, K. Proof-of-authentication consensus algorithm: Blockchain-based IoT implementation. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–2. [Google Scholar]
- Sun, G.; Dai, M.; Sun, J.; Yu, H. Voting-based decentralized consensus design for improving the efficiency and security of consortium blockchain. IEEE Internet Things J. 2020, 8, 6257–6272. [Google Scholar] [CrossRef]
- Wu, J.; Dong, M.; Ota, K.; Li, J.; Yang, W. Application-aware consensus management for software-defined intelligent blockchain in IoT. IEEE Netw. 2020, 34, 69–75. [Google Scholar] [CrossRef]
- Ravindran, R. Circle of trust: A high volume, energy efficient, stake blind and high attack tolerant blockchain consensus protocol. In Proceedings of the 2019 IEEE 12th International Conference on Global Security, Safety and Sustainability (ICGS3), London, UK, 16–18 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–4. [Google Scholar]
- Yang, L.; Li, M.; Si, P.; Yang, R.; Sun, E.; Zhang, Y. Energy-efficient resource allocation for blockchain-enabled industrial Internet of Things with deep reinforcement learning. IEEE Internet Things J. 2020, 8, 2318–2329. [Google Scholar] [CrossRef]
- Otoum, S.; Al Ridhawi, I.; Mouftah, H.T. Blockchain-supported federated learning for trustworthy vehicular networks. In Proceedings of the GLOBECOM 2020-2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 1–6. [Google Scholar]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Zhang, Q.; Choo, K.K.R. An energy-efficient SDN controller architecture for IoT networks with blockchain-based security. IEEE Trans. Serv. Comput. 2020, 13, 625–638. [Google Scholar] [CrossRef]
- Wu, H.; Wolter, K.; Jiao, P.; Deng, Y.; Zhao, Y.; Xu, M. EEDTO: An energy-efficient dynamic task offloading algorithm for blockchain-enabled IoT-edge-cloud orchestrated computing. IEEE Internet Things J. 2020, 8, 2163–2176. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Secure computation offloading in blockchain based IoT networks with deep reinforcement learning. IEEE Trans. Netw. Sci. Eng. 2021, 8, 3192–3208. [Google Scholar] [CrossRef]
- Xu, X.; Zhao, H.; Yao, H.; Wang, S. A Blockchain-Enabled Energy-Efficient Data Collection System for UAV-Assisted IoT. IEEE Internet Things J. 2020, 8, 2431–2443. [Google Scholar] [CrossRef]



| Reference No. | Consensus Approach Used | Contributions | Validation Parameters | Future Scope |
|---|---|---|---|---|
| [20] | Practical Byzantine fault tolerance | Proposed blockchain network collaboration mechanism | Time and fault tolerance | Use of multichain and sidechain to improve the performance of model |
| [21] | Framework based on the Byzantine approach | Energy trading process is formulated by using the Byzantine general approach | Success probability of attack | Refining the consensus approach |
| [22] | Modified proof of work | Proposed novel algorithm for reaching consensus by using polynomial matrix factorization and statistical likelihood maximization | memory usage, energy, convergence time, and energy consumption | Using smart contract for its adaptability |
| [23] | Proof-of-authentication | Consensus designed for resource-constrained IoT devices | Energy and latency | Consideration of transparency and security of IoT architecture |
| [24] | Proof of reputation, proof of assets | Decentralized consensus approach is designed on the basis of voting | Time and energy | Suitable for complex scenarios |
| [25] | Application aware consensus | Virtualized consensus approach using transfer learning | Throughput, energy, and time | Adapting edge artificial intelligence for blockchain |
| [26] | Circle of trust–consensus | Use of trust scores | Throughput and energy |
| Reference No. | Technique Used | Contributions | Validation Parameters | Future Scope |
|---|---|---|---|---|
| [27] | Practical Byzantine fault tolerance | Energy-efficient technique for industrial IoT by jointly optimizing the device allocation and weighted cost | Energy consumption, total time, and computation overhead | Considering other consensus approaches |
| [28] | Consensus based on federated learning (FL) | Achieved fog consensus using FL for vehicular networks | Accuracy, energy consumption, throughput, and latency | Adopting different FL techniques |
| [29] | Use of SDN controllers | Cluster techniques for IoT networks by using blockchain and SDN | Energy, throughput, and time | High-level blockchain architecture |
| [30] | Offloading computations to mobile edge computing servers | Framework based on the Lyapunov optimization is framed | Response time and energy consumption | Implementation on real-world networks based on blockchain |
| [31] | Offloading computations to mobile edge computing servers | Deep reinforcement learning technique is used to finalize the offloading policy | Processing delay and energy consumption | Considering offloading requirements of various IoT devices due to the increase in network traffic |
| [32] | Adaptive linear prediction technique | Charging coins are obtained by unmanned aerial vehicles | Accuracy and energy consumption |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wadhwa, S.; Rani, S.; Kavita; Verma, S.; Shafi, J.; Wozniak, M. Energy Efficient Consensus Approach of Blockchain for IoT Networks with Edge Computing. Sensors 2022, 22, 3733. https://doi.org/10.3390/s22103733
Wadhwa S, Rani S, Kavita, Verma S, Shafi J, Wozniak M. Energy Efficient Consensus Approach of Blockchain for IoT Networks with Edge Computing. Sensors. 2022; 22(10):3733. https://doi.org/10.3390/s22103733
Chicago/Turabian StyleWadhwa, Shivani, Shalli Rani, Kavita, Sahil Verma, Jana Shafi, and Marcin Wozniak. 2022. "Energy Efficient Consensus Approach of Blockchain for IoT Networks with Edge Computing" Sensors 22, no. 10: 3733. https://doi.org/10.3390/s22103733
APA StyleWadhwa, S., Rani, S., Kavita, Verma, S., Shafi, J., & Wozniak, M. (2022). Energy Efficient Consensus Approach of Blockchain for IoT Networks with Edge Computing. Sensors, 22(10), 3733. https://doi.org/10.3390/s22103733






