Investigating Master–Slave Architecture for Underwater Wireless Sensor Network
Abstract
1. Introduction
- Our proposed master–slave architecture helps to achieve lower energy consumption by limiting the broadcasting of packets to a specific region (set of nodes).
- We avoid packet duplication due to the suppression of nodes and the lack of multiple paths for transmission.
- We perform extensive simulation of our proposed protocol in various scenarios and demonstrate improvements in Packet Delivery Ratio (PDR) and energy tax.
2. Related Work
2.1. Localization-Based Routing Protocols
- VBF: The Vector-Based Forwarding (VBF) [4] protocol uses a virtual pipe core in a virtual vector for data forwarding. The virtual vector extends from source to destination and chooses only the nodes lying in the pipe. The protocol uses redundant and different routes for stability in terms of node movement from source to destination. However, by choosing the forwarders within the pipe repeatedly, the energy usage is not optimized. Furthermore, the network lifetime is high due to imbalanced energy usage.
- HH-VBF: To increase the efficiency of VBF, another protocol called Hop-by-Hop Vector-Based Forwarding (HH-VBF) has been proposed in [5]. In this protocol, every node generates a virtual pipe that changes the vector path by the node position. In contrast to VBF, energy consumption is balanced in this protocol. However, the HH virtual pipe approach creates significant contact overheads compared to VBF and lacks a mechanism to avoid the void space.
- AHH-VBF: The Adaptive Hop-by-Hop Routing Protocol (AHH-VBF) [6] is another attempt to improve the VBF and HH-VBF protocols. It uses variable transmission ranges to save network resources. The transmission range of AHH-VBF varies by distance from the farthest carrier and improves the network lifetime due to the adjustment of the holding time. However, this protocol is limited to select the forwarder by ignoring any residual energy which results in replication packages and unbalanced energy usage.
- ANU-AHH-VBF: In [7], the author suggests another location-based protocol called Avoiding Void Node with Adaptive Hop-by-Hop Vector-Based Forwarding (AVN-AHH-VBF) that uses a virtual routing pipeline with the configured radius for data analysis. In this protocol, when a node receives a packet, the distance from the forwarder is observed in the predefined range. The AVN-AHH-VBF uses the concept of holding time to reduce unwanted broadcasts. The PDR is improved because the packet collision is minimized. However, the performance concerning end-to-end delay is not improved. Therefore, by using residual energy, the technique could not achieve the balancing of energy consumption among nodes.
- ESEVBF: In [8], the authors proposed Energy Scaled and Expanded Vector-Based Forwarding (ESEVBF) protocol to offset energy consumption. The selection is based on the residual energy of the forwarder nodes. It measures and increases the time difference of holding with the residual PFN energy. While lowering the end-to-end delay, the selection process achieves reduced packets’ duplication and network energy consumption. The routing protocol demonstrates little changes in Packet Delivery Rate (PDR), as the forwarding node suppresses vast amounts of nodes with a slight variation in the residual energy, inside the potential forwarding region. If a communication void hole happens, VBF fails to react.
- NEFP: The Novel Efficient Forwarding Protocol (NEFP) [9] is also a localization-based routing protocol. It has three main tasks, i.e., forwarding/routing zones to avoid unimportant forwarding using Markov chain to measure the forwarding probability of the packets in different network topologies and the calculation of holding time to avoid packet duplication and Collison. However, this protocol does not perform well in sparse conditions because of the less probability of finding the next forwarder in the forwarding zone.
- TC-VBF: To address the issue of node’s communication in sparse environment, the Topology Control VBF (TC-VBF) [10] was introduced. It performs the selection of the forwarder similar to the technique of VBF but with the addition of network density consideration. However, eventually, this also faces the same issue of energy holes and void holes such as the VBF in the sparse network due to the death of the forwarder nodes.
- MEES: In this protocol, the two mobile sinks are chosen which are far away from each other [11]. Data collection from the nodes is performed via predefined linear paths. The experimental results demonstrate the improvement of network throughput and lifetime as well as energy consumption.
- DTMR: To reduce energy consumption in terms of signaling power and transmission delay, the authors in [12] proposed the Direction Transmission or Mobile Relay (DTMR) protocol where a source node can send data through a mobile relay node or directly to the destination node; however, there is no guarantee for the reliable communication of data to the destination because of the harsh underwater environment.
- FVBF: The Fuzzy logic-based Vector-based Forwarding protocol (FVBF) [13] is another attempt to improve VBF. It considers the valid distance, projection, and energy of a node for the selection of the next forwarder. Valid distance determines the closeness of a node to sink while projection determines its closeness to the routing pipe.
2.2. Localization-Free Routing Protocols
- DBR: Depth-based Routing (DBR) [14] is the base protocol that played a vital role in the transformation from localization-based to depth-based routing in UWSNs. DBR is an approach based on the greedy algorithm focusing on sending packets from source to sink nodes. It is a single-hop scheme that uses the next node for the data packet transmission. The nodes are randomly deployed and have the characteristic of mobility due to the ocean nature, therefore, resulting in the void hole problem. This protocol uses the depth information to select the next transmission forwarder, and the source node transmits the data in its premises, while every other node within the range of the network receives the packet. Based on the depth difference information, the surrounding nodes are divided into PFNs and suppressed nodes. Next, the nodes occurring in the lower hemisphere drop the packet while the nodes in the upper hemisphere (i.e., PFNs) determine the holding time using the local depth information, and set the timer to hold the data packet. During this holding period, if a node does not obtain a copied version of the captured data packet, it transmits the packet after the timer expiration. On the other hand, the packet is dropped. In this protocol, the sender makes decisions based on one-hop depth and remaining information, resulting in a lower rate of packet delivery as well as lower energy efficiency, and eventually leading to the occurrence of void and energy holes.
- DSRP: Akanksha et al. [15] presented the Distributed Delay-Sensitive Routing Protocol (DSRP) to address the mobility of nodes in a network. In this model, when a node reaches its destination, it stops there for a moment and is then shifted to the new destination by keeping account of the expected traffic, chosen paths, and localization of the nodes. The movement speed of the node is kept between maximum and minimum values. This high mobility results in high PDR with the cost of high energy consumption and end-to-end delay, as compared to low mobility and no mobility models.
- ODBR: The Optimized Depth-Based Routing (ODBR) protocol [16] targets the energy balancing approach where it assigns the energy to nodes based on their depths. To prolong the network lifetime and balance the energy consumption, the nodes with smaller depths are assigned a high amount of energy while the nodes with higher depths get low energy. This approach is not applicable in a deep-water environment because the nodes at the highest depth get low energy and die quickly. However, it works well in shallow water because each node in the network gets the required amount of energy to transmit data due to its less depth.
- EBECRP: To reduce multi-hopping, the authors in [17] presented an Energy-efficient and Balanced Energy Consumption Cluster-based Routing Protocol (EBECRP) which divide the network into sectors where each sector consists of a cluster head capable of collecting data from its neighbor nodes. The nodes first send data either directly to the sink or the cluster head and then the sink collects data from the cluster head. This results in low energy consumption due to optimized routing but high packet loss because of the early death of the cluster head due to energy reuse.
- Hydrocast: The Hydrocast protocol [18] proposed a way to use water pressure as a driving force to forward a data packet to the sink which reduces energy balancing and economize the node energy. To ensure the successful packet delivery to the destination, a dead-end recovery method is proposed where a node hands over its data packet to the neighbor with greater energy. Therefore, it does not perform well in sparse conditions because it cannot find neighbors.
- WDFAD-DBR: The WDFAD-DBR protocol [19] is an improved version of DBR that aims to make the routing decisions more intelligent by providing two-hop information. Unlike the DBR, this scheme is based on a two-hop model, where the depth information of the next node’s and expected hop is used to calculate the holding time. In addition, the forwarding area is split into three parts, i.e., one main region and two secondary regions for forwarding, so that the high priority nodes can suppress low priority nodes. WDFAD-DBR try to avoid the void hole in advance, as it considers the depth of the expected next-hop neighbor in addition to the current forwarding neighbor. WDFAD-DBR achieves a good packet delivery ratio in a sparse network; however, the forwarding strategy fails to balance network traffic and lower depth nodes are penalized which leads to the early death of the network. Because of the stretching of holding time differences among neighboring nodes, the duplicate packets are not reduced which further results in high energy consumption.
- DOW-PR: The Dolphin and Whale Pod Routing protocol (DOW-PR) is introduced in [20] to achieve better performance for WDFAD-DBR. This protocol adopted the weighting depth difference for the forwarder selection, with some additional selection parameters i.e., PFN number, hop count, and the number of nodes suppressed as well as node residual energy. This hashed out the problem of void holes up to some extent by using the path from the suppressed region in the absence of nodes in the PFN region. The DOW-PR involves two processes i.e., (i) Whale Pod routing (ii) Dolphin Pod routing. In Dolphin Pod routing, all the sink nodes are installed on the water’s surface, whereas only a single sink is placed inside water in the case of Whale Pod routing. Additionally, the power range is divided into power levels for better use of the node power and traffic control using the hop-count mechanism. The experimental results (simulation-based) showed significant performance in terms of higher packet delivery rate, lower APD, smaller energy tax, and better network life.
- EEPDBR: EEPDBR [21] algorithm is used to design an improved probabilistic DBR algorithm for underwater data collection and reporting to the surface receivers by taking node’s residual energy, depth information, and the number of PFNs within the 2-hop neighborhood. This technique outperforms in terms of PDR, energy efficiency, and low average delivery time.
- EBH-DBR: EBH-DBR [22] uses depth, residual energy of the node, and reliability of the link to select the next relay node for data forwarding. In this scheme, the network is divided into slices of the same width to balance energy consumption as well as to control the hop count of the sensor nodes forwarding the data. This technique works well in terms of network prolonging, energy balancing, throughput, and transmission loss.
- EECMR: Energy-Efficient Clustering Multi-hop Routing (EECMR) protocol [23] aims to balance energy consumption of the data transmitting nodes and prolong their life. In this approach, the network is divided into multiple layers concerning the depth level. Data is being forwarded to the sink using a multi-hop mechanism by the cluster head selected based on the depth and residual energy of the node. The cluster head then aggregates the data packets of all cluster members and sends them to the upper layer of the sink node. This protocol is effective in terms of network lifetime and energy consumption.
3. Problem Statement
4. System Model
4.1. Basic Terminologies
- Master nodes: Master nodes are those nodes that fulfill the requirements of the Master Selector function (MSF) and are eligible for the forwarding data packets.
- Slave nodes: Nodes other than masters are slave nodes and are not eligible for forwarding data packets.
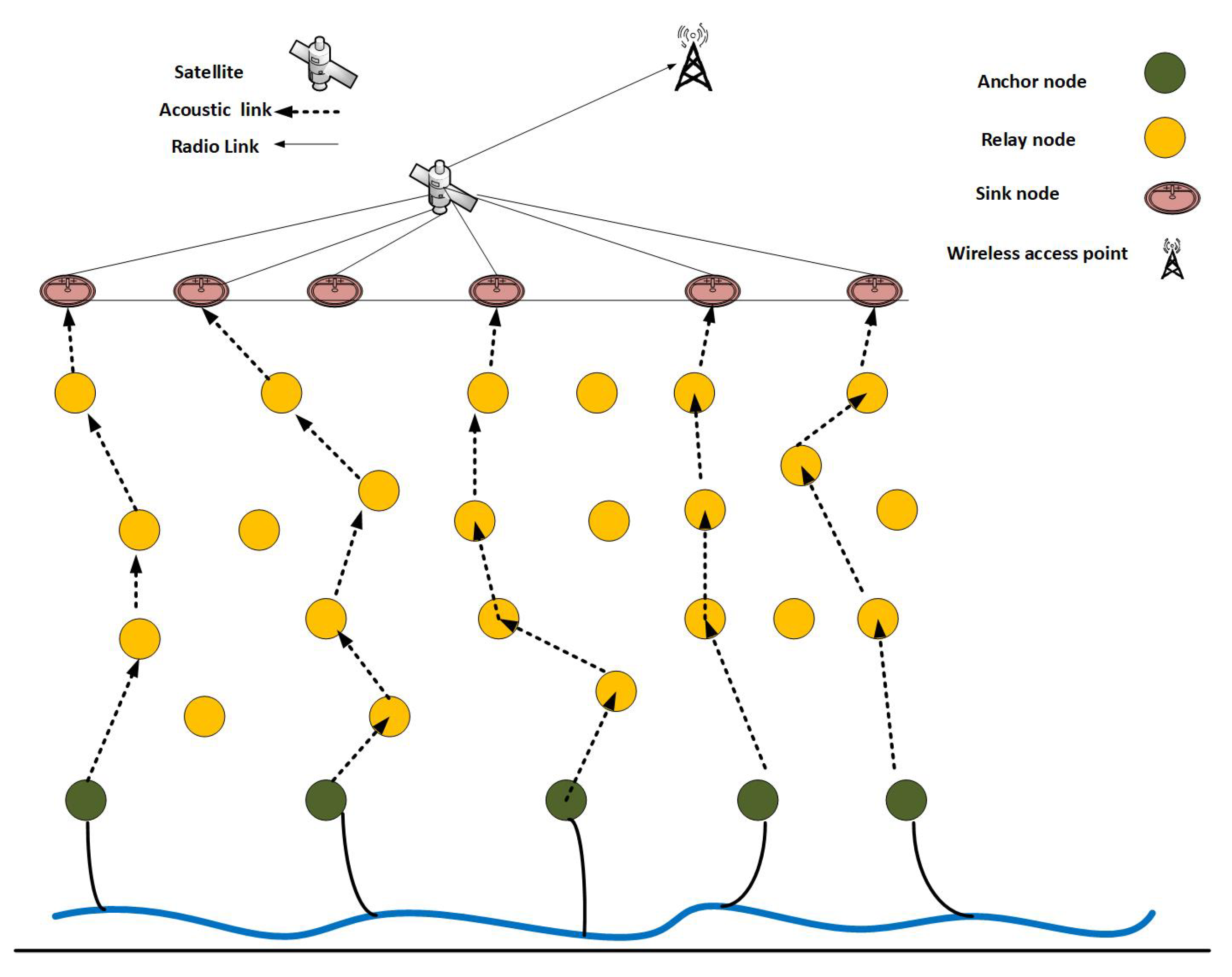
- Anchor nodes: Nodes which are statically bounded at the bottom of the water, also known as data collectors or source nodes.
- Relay nodes: Nodes which are suspended in water and work as 3rd party between anchor nodes and sink nodes.
- Sink nodes: Sink nodes are the receiver/destination nodes and they float on the surface of the water. Their responsibility is to collect data packets from sensor nodes and forward them to base stations through a radio link.
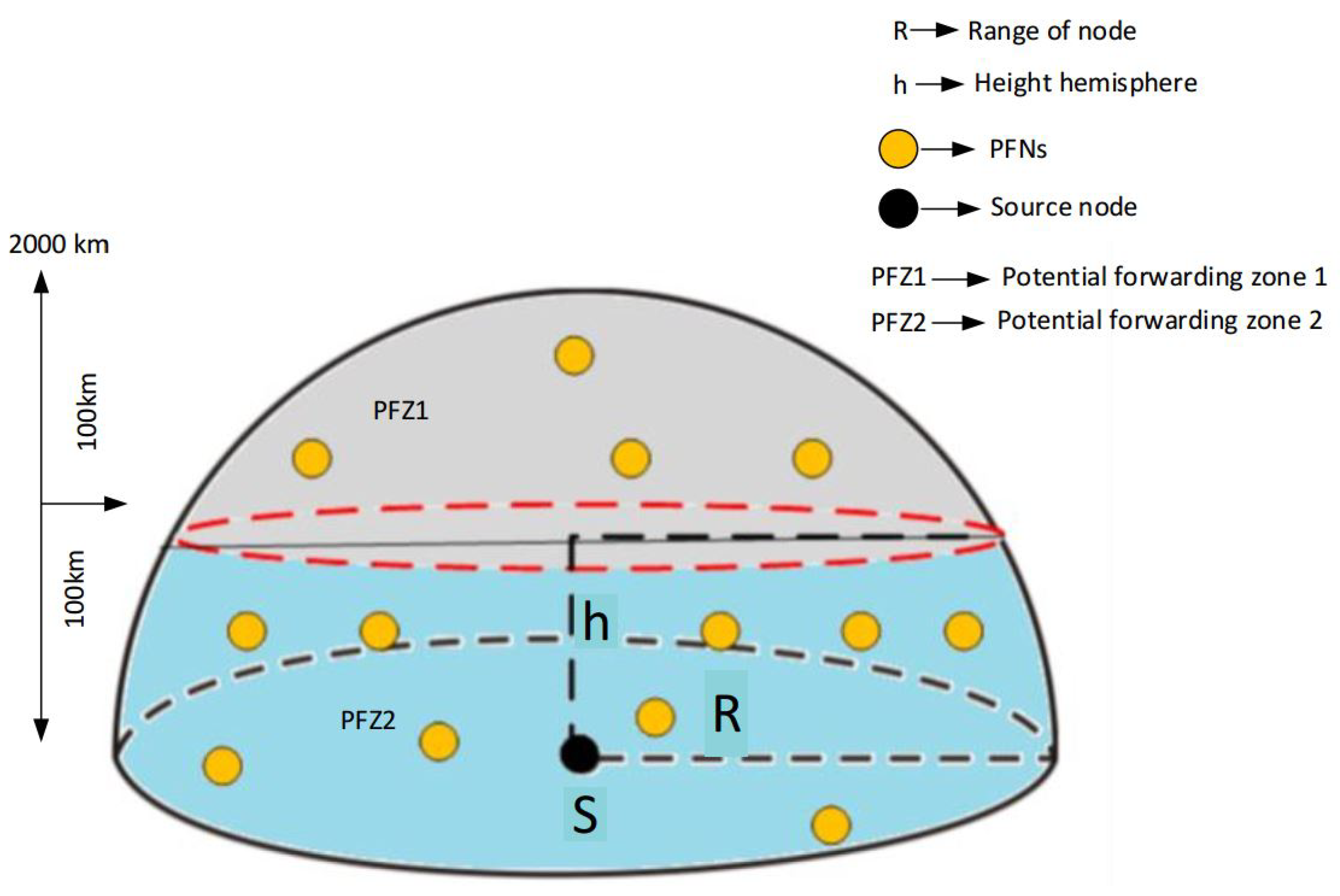
- Transmission range of node S: This refers to the omnidirectional distance from source node S (Xs, Ys, Zs) which currently forwards the packet p until and unless the packet is transmitted.
- Void hole: A state where the forwarding node cannot find any other node to further forward a packet.
- Energy hole: A scenario where the forwarding node lacks the required energy for forwarding a data packet.
- Eligible Neighbors (Eni) of Node i: Nodes spanning within the transmission range of a given node i. Let’s suppose N represents a set of nodes in a networkTherefore, the eligible neighbors of a Node i can be illustrated aswhere (Distji) is the Euclidean distance between node i () and node j () in a 3-dimensional Euclidean space:
- Potential Forwarders (Pfi) for a Node i: Nodes lying in the transmission range Rrs and with their depth (dj) less than the depth (di) form the potential forwarders for a node i, as given below:where
- Potential Forwarding Zone (PFZ): The Potential Forwarding Zone (PFZ) creates a hemispherical zone, where the radius is similar to Rrs and the distance to the sink for each point of PFZ is lower than that of the source node. The PFZ is the sub-region of Rrs for node S and the nodes residing in the zone are Potential Forwarder Nodes (PFNs), i.e., the subsequent forwarders for the packet p.
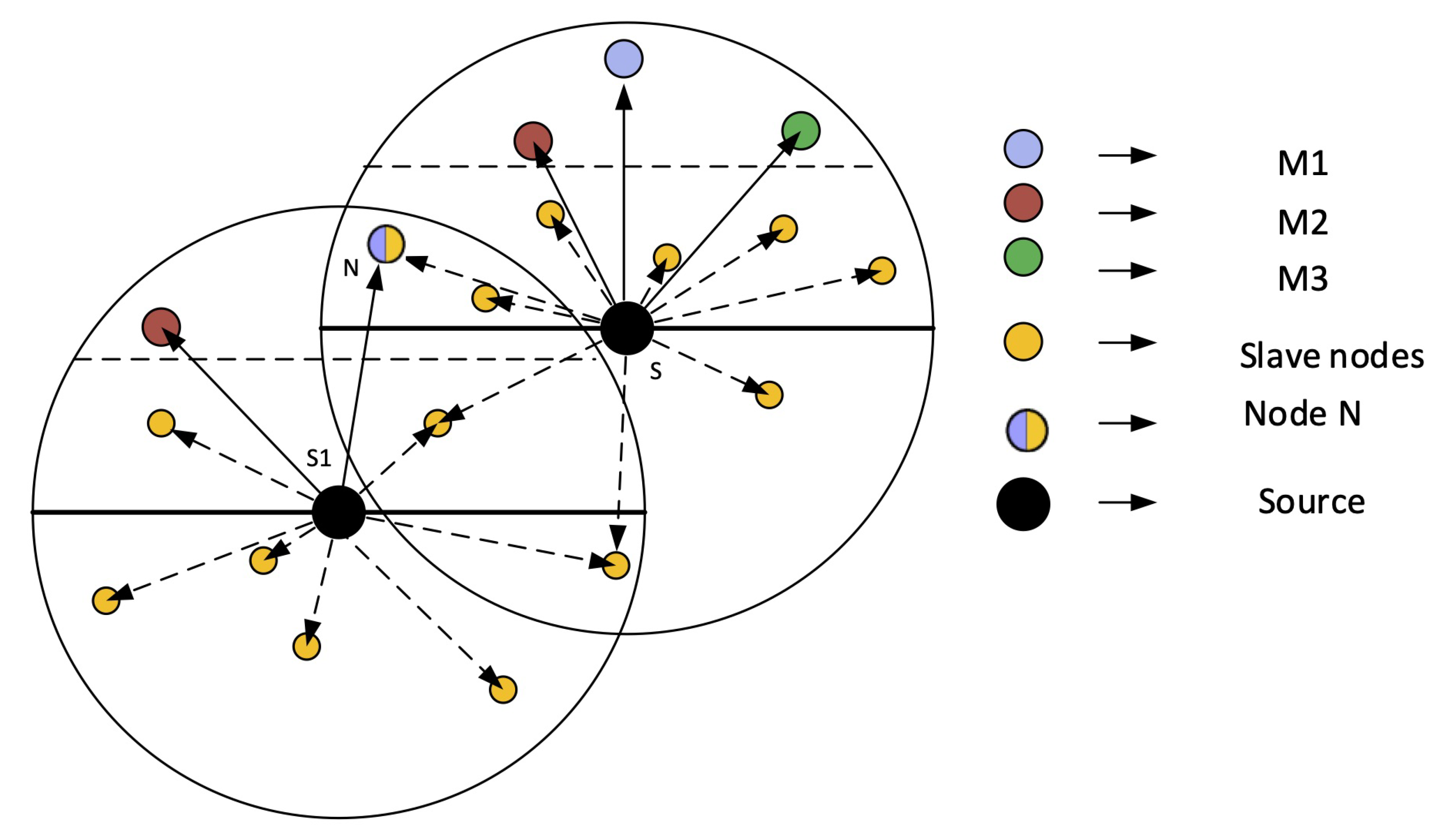
4.2. Network Architecture of ERPMSA-UWSN
4.3. Impact of Acoustic Signal Velocity in the Underwater Environment
4.4. The Energy Propagation Model
4.5. Influence of Voice Signal Reflection/Refraction in an Underwater Environment
4.6. Packet Types in ERPMSA-UWSN
- Neighbor Request Packet (NR): The source node uses NR to get information about the neighbor forwarders. The format of the NR packet is NR (TYPO, SID, D, VA), where TYPO is the two-bit number indicating the type of the packet. For NR, the value of TYPO = 00. SID is the ID of the source node and D is the depth of the source node.
- Acknowledgment Packet (ACK): ACK packet is a reply from the neighbor node in the response of NR, containing full information of its sender. The format of the ACK is ACK (TYPO, SID, D, E), where the value of TYPO for ACK is “01”, SID is the ID of that neighbor node, D is the depth and E is the energy of the ACK packet’s sender node. We store these values in a separate table called MTAB, in descending order corresponding to their IDs. In the table, the MSF value of the first index node is highest among all nodes and other indices are occupied accordingly.
- Control Packet (CTRL): CTRL packet is used to invoke the masters for the forwarding procedure. By awakening the masters, it automatically turns slave nodes into the indolent state. The format is CTRL (TYPO, SID, PTR1, PTR2, D) where TYPO for this packet is “10”, SID is the ID of the sender node, PTR1 and PTR2 are pointers to the array that contain IDs of the three descending indexed Masters of PFZ1 and PFZ2 respectively, while D is the depth of the sender node.
- Data Packet (DATA): DATA packet contains the real data with the payload and header. The format of the DATA packet is DATA (TYPO, SID, DID, D), where TYPO value is “11”, SID represents the source node ID, DID indicates the destination node, while D represents the depth of the sender node.
4.6.1. Division of Potential Forwarding Zone (PFZ) into PFN levels
4.6.2. Node Density in PFZ Levels
4.7. Distance-Based Adaptive Transmission Methods
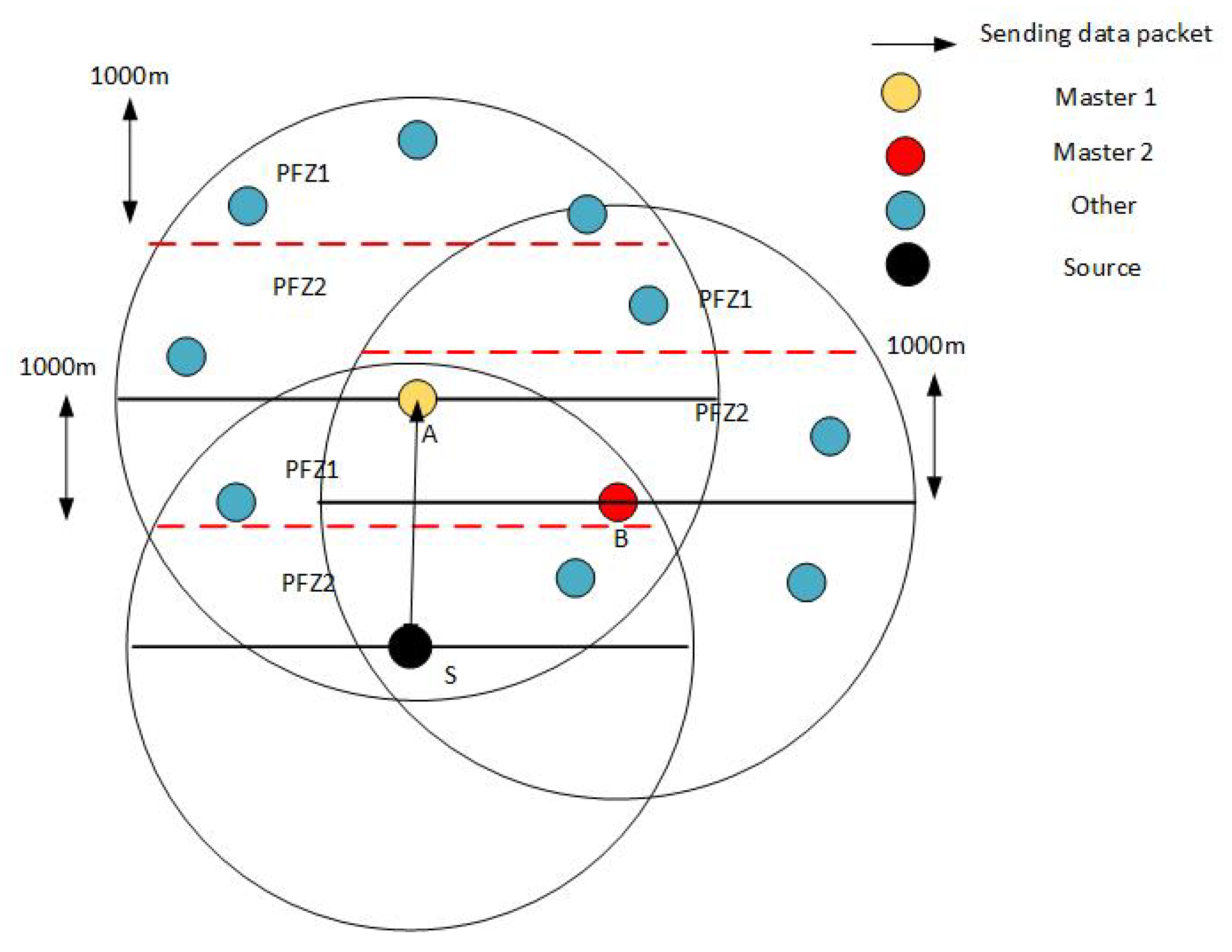
4.8. Distribution of PFNs into Masters and Slaves
| Algorithm 1: Masters selection algorithm |
 |
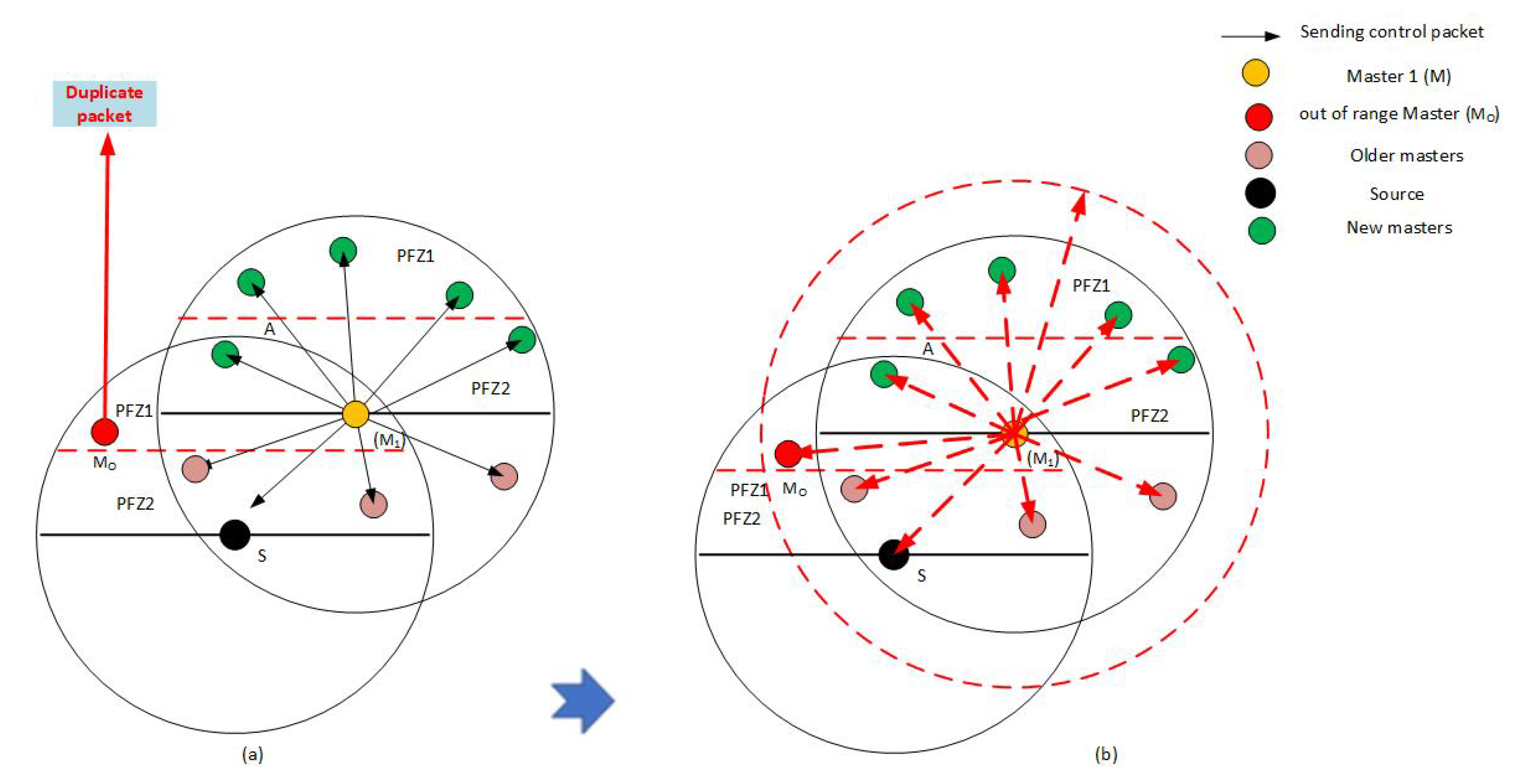
4.9. Master-Range Extension to End Data Packet Duplication
4.10. Data Packet Forwarding Mechanism in ERPMSA-UWSN
- After receiving the ACK packet, the source node updates its neighbor table and sorts out the master and slaves.
- The source node sends a Control packet in its surroundings, containing the IDs of Masters of each PFN region, which turn the slave nodes to the idle state while keeping the masters active.
- The data packet is sent which is only received by the master nodes while the holding time is assigned based on their priority. In this way, masters nodes of the region PFZ1 get a higher priority than the region PFZ2.
- Before forwarding data, master must check for the energy hole scenario. In case of an energy hole, the 2nd Master takes charge and forwards the data packet. If the 2nd Master also encounters the same situation, it hands over the responsibility to its subordinate master, i.e., the 3rd master. If it does not find a way out, the packet is dropped. This increases the chances of the data packet getting its destination most probably.
- If there is no energy hole then the master beating the clock first will forward the data to the forwarder in its range in the same fashion, while the other master drops the packet after hearing the control packet from the forwarding master.The whole procedure is well elaborated in the sequence diagram in Figure 7.
4.11. Holding Time and Activation Time Calculation
4.11.1. Activation Time (AT) calculation
4.11.2. Holding Time (HT) Calculation
4.12. Data Delivery Scheme
4.13. Restricting Extra Reception of Packets
| Algorithm 2: Packet’s transmission Algorithm |
 |
5. Simulation
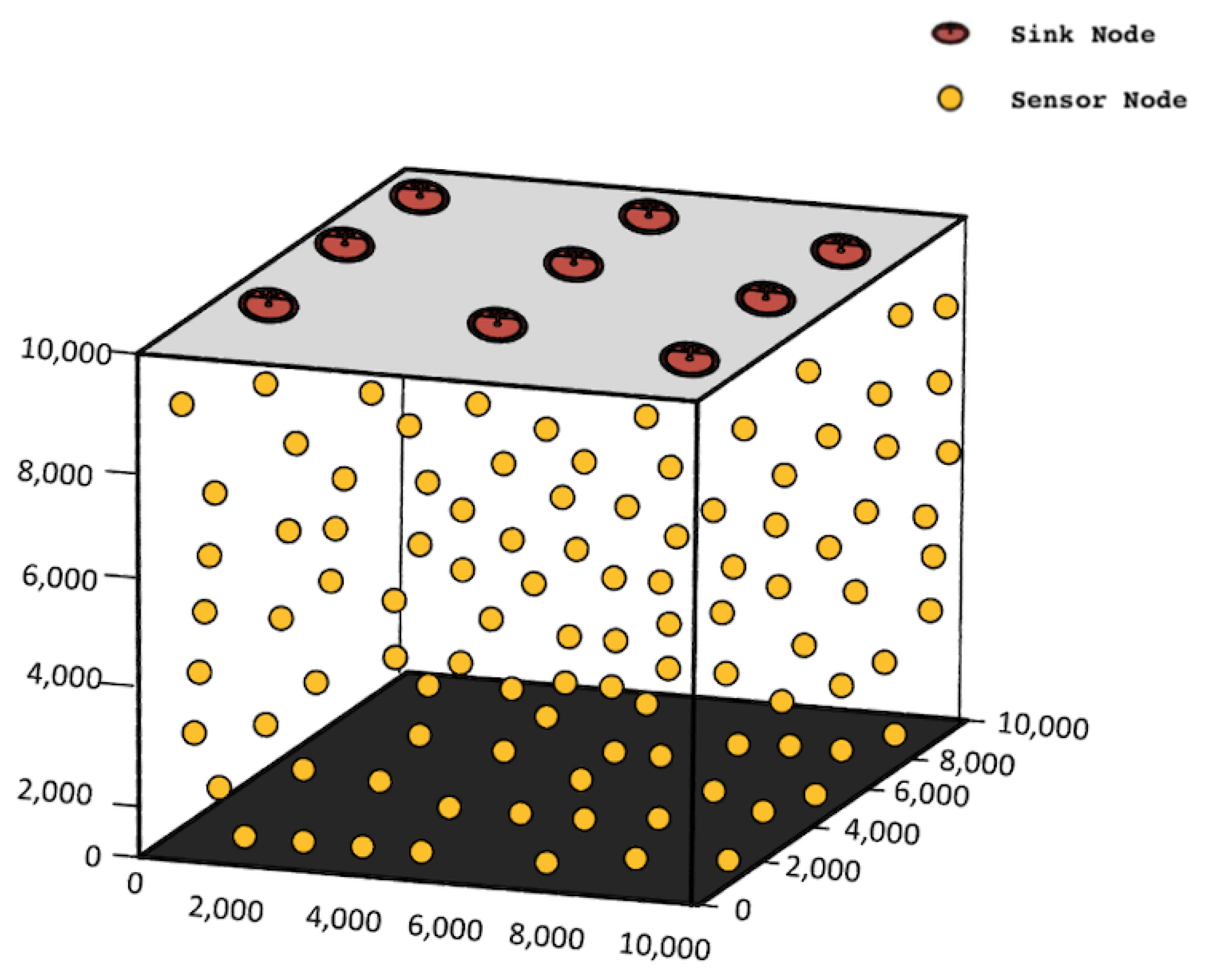
5.1. Simulation Setup
5.2. Performance Breakdown and Comparison
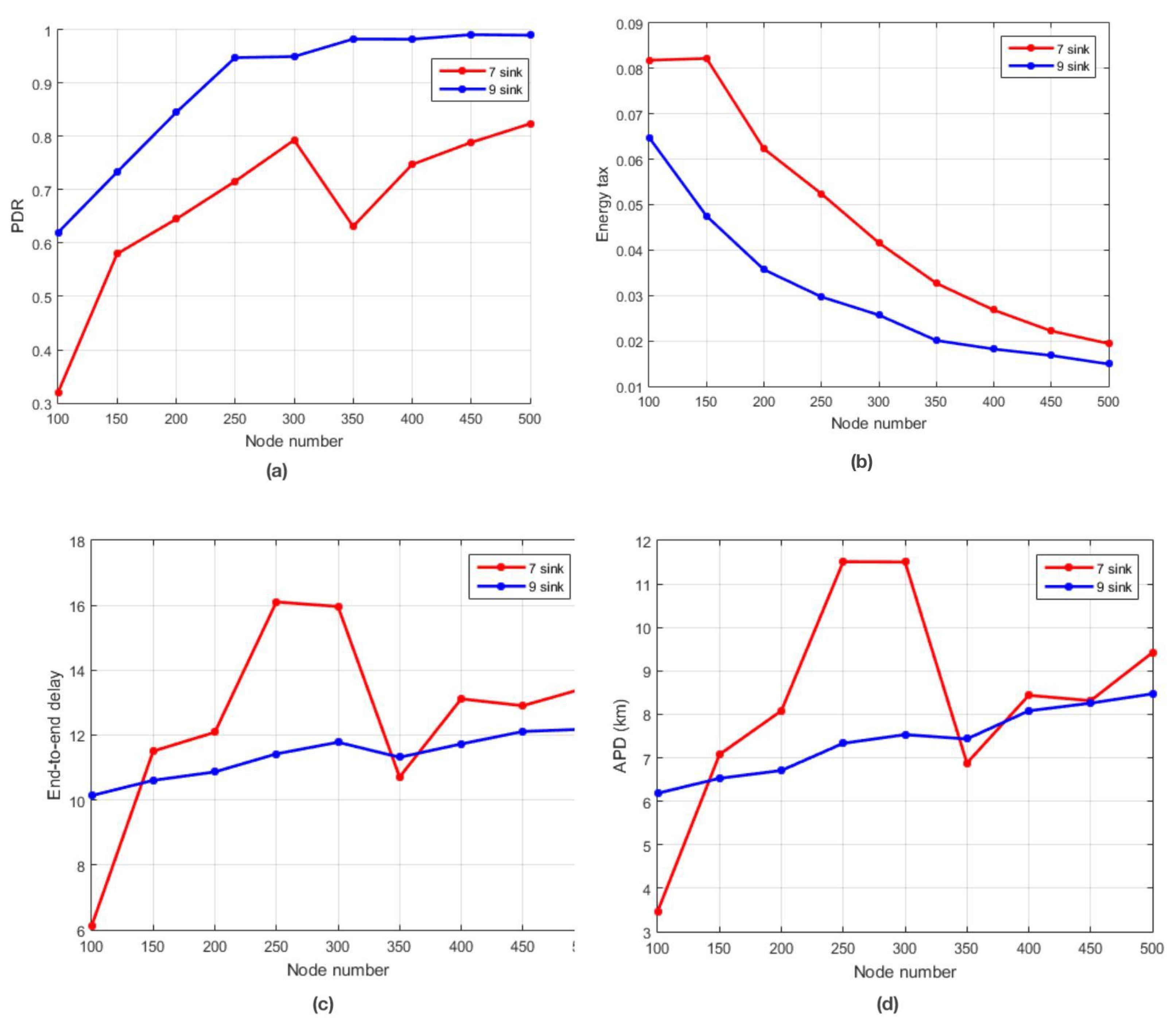
5.2.1. Packet Delivery Ratio (PDR)
5.2.2. Energy Tax
5.2.3. End-to-End Delay (E2ED)
5.2.4. Accumulated Propagation Distance (APD)
5.3. Simulation Results
5.3.1. Simulation of ERPMSA-UWSN in Comparison with WDFAD
5.3.2. Simulation Results Based on Sink Variation
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Felemban, E.; Shaikh, F.K.; Qureshi, U.M.; Sheikh, A.A.; Qaisar, S.B. Underwater Sensor Network Applications: A Comprehensive Survey. Int. J. Distrib. Sens. Netw. 2015. [Google Scholar] [CrossRef]
- Akyildiz, F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Khan, A.; Ali, I.; Ghani, A.; Khan, N.; Alsaqer, M.; Rahman, A.U.; Mahmood, H. Routing Protocols for Underwater Wireless Sensor Networks: Taxonomy, Research Challenges, Routing Strategies and Future Directions. Sensors 2018, 18, 1619. [Google Scholar] [CrossRef]
- Xie, P.; Cui, J.H.; Lao, L. VBF: Vector-based forwarding protocol for underwater sensor networks. In Proceedings of the 5th International IFIP-TC6 Conference, Coimbra, Portugal, 15–19 May 2006. [Google Scholar]
- Nicolaou, N.; See, A.; Xie, P.; Cui, J.-H.; Maggiorini, D. Improving the robustness of location-based routing for underwater sensor networks. In Proceedings of the OCEANS 2007-Europe, Aberdeen, UK, 18–21 June 2007. [Google Scholar]
- Yu, H.; Yao, N.; Liu, J. An adaptive routing protocol in underwater sparse acoustic sensor networks. Ad Hoc Netw. 2015, 34, 121–143. [Google Scholar] [CrossRef]
- Hafeez, T.; Javaid, N.; Hameed, A.R.; Sher, A.; Khan, Z.A.; Qasim, U. AVN-AHH-VBF: Avoiding void node with adaptive hop-by-hop vector based forwarding for underwater wireless sensor networks. In Proceedings of the 2016 10th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), Fukuoka, Japan, 6–8 July 2016; pp. 49–55. [Google Scholar]
- Wadud, Z.; Hussain, S.; Javaid, N.; Bouk, S.H.; Alrajeh, N.; Alabed, M.S.; Guizani, N. An energy scaled and expanded vector-based forwarding scheme for industrial underwater acoustic sensor networks with sink mobility. Sensors 2017, 7, 2251. [Google Scholar] [CrossRef] [PubMed]
- Qingwen, W.; Fei, C.; Zhi, L.; Qian, Q. A novel efficient forwarding protocol for 3-D underwater wireless sensor networks. In Proceedings of the IEEE 11th International Conference on Industrial Electronics and Applications, Hefei, China, 5–7 June 2016. [Google Scholar]
- IYazgi; Baykal, B. IYazgi; Baykal, B. Topology control vector based forwarding algorithm for underwater acoustic networks. In Proceedings of the IEEE 24th International Conference on Signal Processing and Communication Application, Zonguldak, Turkey, 16–19 May 2017. [Google Scholar]
- Walayat, A.; Javaid, N.; Akbar, M.; Khan, Z.A. MEES: Mobile energy efficient square routing for underwater wireless sensor networks. In Proceedings of the IEEE 31st International Conference on Advanced Information Networking and Applications, Taipei, Taiwan, 26–29 March 2017. [Google Scholar]
- Zhong, X.; Chen, F.; Fan, J.; Guan, Q.; Ji, F.; Yu, H. Throughput analysis on 3-dimensional underwater acoustic network with one-hop mobile relay. Sensors 2018, 18, 252. [Google Scholar] [CrossRef]
- Bu, R.; Wang, S.; Wang, H. Fuzzy logic vector–based forwarding routing protocol for underwater acoustic sensor networks. Trans. Emerg. Telecommun. Technol. 2018, 29, 1–18. [Google Scholar] [CrossRef]
- Yan, H.; Shi, Z.J.; Cui, J.H. DBR: Depth-based routing for underwater sensor networks. In Proceedings of the IFIP International Conference on Networking, Singapore, 5–9 May 2008. [Google Scholar]
- Dubey, A.; Rajawat, A. Impulse effect of node mobility on delay sensitive routing algorithm in underwater sensor network. In Proceedings of the IEEE 10th International Conference on Internet of Things and Applications, Pune, India, 22–24 January 2016. [Google Scholar]
- Ahmed, T.; Chaudhary, M.; Kaleem, M.; Nazir, S. Optimized depth-based routing protocol for underwater wireless sensor networks. In Proceedings of the IEEE 10th International Conference on Open Source Systems and Technologies, Lahore, Pakistan, 15–17 December 2016; pp. 147–150. [Google Scholar]
- Majid, A.; Azam, I.; Waheed, A.; Abidin, M.Z.; Hafeez, T.; Khan, Z.A.; Qasim, U.; Javaid, N. An energy efficient and balanced energy consumption cluster based routing protocol for underwater wireless sensor networks. In Proceedings of the IEEE 30th International Conference on Advanced Information Networking and Applications, Crans-Montana, Switzerland, 23–25 March 2016. [Google Scholar]
- Noh, Y.; Lee, U.; Wang, P.; Vieira, L.F.M.; Gerla, J.H.C.M.; Kim, K. Hydrocast: Pressure routing for underwater sensor networks. IEEE Trans. Veh. Technol. 2016, 65, 333–347. [Google Scholar] [CrossRef]
- Yu, H.; Yao, N.; Wang, T.; Li, G.; Gao, Z.; Tan, G. WDFAD-DBR: Weighting depth and forwarding area division DBR routing protocol for UASNs. Ad Hoc Netw. 2016, 7, 256–282. [Google Scholar] [CrossRef]
- Wadud, Z.; Ullah, K.; Hussain, S.; Yang, X.; Qazi, A.B. Dow-pr DOlphin and whale pods routing protocol for underwater wireless sensor networks (UWSNs). Sensors 2018, 18, 1529. [Google Scholar] [CrossRef]
- Zhang, M.; Cai, W. Energy-Efficient Depth Based Probabilistic Routing Within 2-Hop Neighborhood for Underwater Sensor Networks. IEEE Sens. Lett. 2020, 4. [Google Scholar] [CrossRef]
- Kumar, R.; Bhardwaj, D.; Mishra, M. EBH-DBR: Energy-balanced hybrid depth-based routing protocol for underwater wireless sensor networks. Mod. Phys. Lett. B 2021, 35, 2150061. [Google Scholar] [CrossRef]
- Nguyen, N.-T.; Le, T.T.T.; Nguyen, H.-H.; Voznak, M. Energy-Efficient Clustering Multi-Hop Routing Protocol in a UWSN. Sensors 2021, 21, 627. [Google Scholar] [CrossRef] [PubMed]
- Diamant, R.; Casari, P.; Compagnro, F.; Kebkal, O.K.V.; Zorozi, M. Fair and throughput-optimal routing in multimodal underwater networks. IEEE Trans. Wirel. Commun. 2018, 17, 1738–1754. [Google Scholar] [CrossRef]
- Faheem, M.; Tuna, G.; Gungor, V.C. QERP: Quality-of-service (QOS) aware evolutionary routing protocol for underwater wireless sensor networks. IEEE Syst. J. 2017, 12, 2066–2073. [Google Scholar] [CrossRef]
- Rehman, M.A.; Lee, Y.; Koo, I. EECOR: An energy-efficient cooperative opportunistic routing protocol for Underwater acoustic sensor networks. IEEE Access 2017, 5, 14119–14132. [Google Scholar] [CrossRef]
- Li, M.; Du, X.; Huang, K.; Hou, S.; Liu, X. A routing protocol based on received signal strength for underwater wireless sensor networks (UWSNs). Information 2017, 8, 153. [Google Scholar] [CrossRef]
- Yang, J.; Liu, S.; Liu, Q.; Qiaoi, Q.G. UMDR: Multi-path routing protocol for underwater ad hoc networks with directional antenna. J. Phys. Conf. Ser. 2018, 960, 1–7. [Google Scholar] [CrossRef]
- Patil, K.; Jafri, M.R.; Fiems, D.; Marin, A. Stochastic modeling of depth based routing in underwater sensor networks. Ad Hoc Netw. 2019, 89, 132–141. [Google Scholar] [CrossRef]
- Coutinho, R.W.L.; Boukerche, A.; Loureiro, A.A.F. PCR: A Power Control-based Opportunistic Routing for Underwater Sensor Networks. In Proceedings of the 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Montreal, QC, Canada, 28 October–2 November 2018; pp. 173–180. [Google Scholar]
- Gola, K.K.; Gupta, B. Underwater Acoustic Sensor Networks: An Energy Efficient and Void Avoidance Routing Based on Grey Wolf Optimization Algorithm. Arab. J. Sci. Eng. 2021, 46, 3939–3954. [Google Scholar] [CrossRef]
- Alfouzan, F.A.; Ghoreyshi, S.Y.; Shahrabi, A.; Ghahroudi, M.S. An AUV-Aided Cross-Layer Mobile Data Gathering Protocol for Underwater Sensor Networks. Sensors 2020, 20, 4813. [Google Scholar] [CrossRef]
- Gul, H.; Ullah, G.; Khan, M.K.M.Y. EERBCR: Energy-efficient regional based cooperative routing protocol for underwater sensor networks with sink mobility. J. Ambient. Intell. Humaniz. Comput. 2021, 1–13. [Google Scholar] [CrossRef]
- Fattah, S.; Gani, A.; Ahmedy, I.; Idris, M.Y.I.; Hashem, I.A.T. A Survey on Underwater Wireless Sensor Networks: Requirements, Taxonomy, Recent Advances, and Open Research Challenges. Sensors 2020, 20, 5393. [Google Scholar] [CrossRef] [PubMed]
- Lu, Y.; He, R.; Chen, X.; Lin, B.; Yu, C. Energy-Efficient Depth-Based Opportunistic Routing with Q-Learning for Underwater Wireless Sensor Networks. Sensors 2020, 20, 1025. [Google Scholar] [CrossRef] [PubMed]
- Yu, W.; Chen, Y.; Wan, L.; Zhang, X.; Zhu, P.; Xu, X. An Energy Optimization Clustering Scheme for Multi-Hop Underwater Acoustic Cooperative Sensor Networks. IEEE Access 2020, 8, 89171–89184. [Google Scholar] [CrossRef]
- Hu, T.; Fei, Y. QELAR: A machine-learning-based adaptive routing protocol for energy-efficient and lifetime-extended underwater sensor networks. IEEE Trans. Mob. Comput. 2010, 9, 796–809. [Google Scholar]
- Park, S.H.; Mitchell, P.D.; Grace, D. Reinforcement Learning Based MAC Protocol (UW-ALOHA-Q) for Underwater Acoustic Sensor Networks. IEEE Access 2019, 7, 165531–165542. [Google Scholar] [CrossRef]
- Gola, K.K.; Gupta, B. Underwater sensor networks: Comparative analysis on applications, deployment and routing techniques. IET Commun. 2020, 14, 2859–2870. [Google Scholar] [CrossRef]
- Climent, S.; Sanchez, A.; Capella, J.V.; Meratnia, N.; Serrano, J.J. Underwater acoustic wireless sensor networks: Advances and future trends in physical, MAC and routing layers. Sensors 2014, 14, 795–833. [Google Scholar] [CrossRef]
- Mackenzie, K.V. Nine-term equation for sound speed in the oceans. J. Acoust. Soc. Am. 1981, 70, 807–812. [Google Scholar] [CrossRef]
- Pottie, G.J.; Kaiser, W.J. Wireless integrated network sensors. Commun. ACM 2000, 43, 51–58. [Google Scholar] [CrossRef]
- Jafri, M.; Marin, A.; Torsello, A.; Ghaderi, M. On the optimality of opportunistic routing protocols for underwater sensor networks. In Proceedings of the 21st ACM International Conference on Modeling, Analysis and Simulation of Wireless and Mobile Systems, Montreal, QC, Canada, 28 October–2 November 2018; pp. 207–215. [Google Scholar]
- Chiang, K.H.; Shenoy, N. A 2-D random-walk mobility model for location-management studies in wireless networks. IEEE Trans. Veh. Technol. 2004, 53, 413–424. [Google Scholar] [CrossRef]
- Raghunathan, V.; Schurgers, C.; Park, S.; Srivastava, M.R. Energy-aware wireless microsensor networks. IEEE Signal Proc. Mag. 2002, 19, 40–50. [Google Scholar] [CrossRef]
- Stojanovic, M.; Preisig, J. Underwater acoustic communication channels: Propagation models and statistical characterization. IEEE Commun. Mag. 2009, 47, 84–89. [Google Scholar] [CrossRef]






| Protocol Category | Protocol | Advantages | Drawbacks |
|---|---|---|---|
| Localization-Based Routing | VBF [4] | Limiting the direction and forwarding range | Cause duplicate packets in dense and void holes in sparse network |
| HH-VBF [5] | Improved PDR | Fails to provide energy fairness and void holes avoidance | |
| AHH-VBF [6] | Energy efficiency is achieved due to power adjustment | Imbalanced energy consumption | |
| AVN-AHHVBF [7] | Energy efficiency | High packet loss | |
| ESEVBF [8] | PDR and energy optimization | Fails in sparse network | |
| NEFP [9] | Energy efficiency | does not perform well in sparse network | |
| TC-VBF [10] | Energy efficiency | Network throughput is lower for fewer nodes | |
| MEES [11] | Energy optimization, energy balancing | packets are dropped by nodes for out-of-range sinks | |
| DTMR [12] | Network throughput is higher, lower delay | Unreliable for direct transmission | |
| FVBF [13] | Energy optimization, delay tolerant and higher throughput | Lower network lifetime due to rapid dying of nodes in the pipe | |
| Localization-Free Routing | DBR [14] | Increase in PDR in dense network | Bad performance in sparse network |
| DSRP [15] | High throughput | High energy consumption and end-to-end delay | |
| ODBR [16] | prolong network life, energy balancing | Not good for in-depth water regions as the nodes located at the bottom needs higher energy for sending attributes | |
| EBECRP [17] | Energy efficiency and network balancing | Higher packet drop ratio because of the cluster heads mobility or death | |
| Hydrocast [18] | Energy efficiency | Does not perform well in sparse network, increased load because of using opportunistic routing | |
| WDFAD-DBR [19] | Increase in network lifetime and decreased | energy consumption E2ED is increased | |
| DOW-PR [20] | Increase in PDR and Decreased in Energy in energy consumption | Increase in E2ED | |
| OMR [24] | Higher network throughput, lower E2ED, energy optimization | Does not perform well for long-range communication because of the fading issue of RF waves | |
| QERP [25] | Increase in PDR and Decreased in Energy in energy consumption and low packet latency | Earlier death of cluster heads because of overloading leading to the creation of energy holes | |
| EECOR [26] | Energy efficiency, high throughput | Increased delay due to the communication among various nodes in forwarding region | |
| RRSS [27] | Energy efficiency | Overloaded nodes because of more data in the vector | |
| UMDR [28] | Energy optimization, higher throughput, and lower E2ED | complications due to the frequent calculations of the next hop and information about antenna |
| Symbols/Abbreviations | Description |
|---|---|
| UWSN | Underwater Sensor Network |
| TWSN | Terrestrial Wireless sensor network |
| MSF | Master Selector Function |
| NR | Packet for Neighbor request |
| DATA | Data packet |
| ACK | Acknowledgment |
| CTRL | Control Packet |
| NTAB | Neighbor Table |
| MTAB | Table for the master nodes |
| PFZ | Potential Forwarding Zone |
| PFZ1 | cap of the upper hemisphere |
| PFZ2 | lower Part of upper hemisphere |
| PFN | Potential Forwarding Node |
| ATMi | activation time for Mi i = 1,2,3. |
| HTMi | Holding time for Mi i = 1,2,3. |
| PDC | Propagation delay for control packet |
| APD | Accumulated Propagation Distance |
| PDR | Packet Delivery Ratio |
| En | Eligible Neighbor |
| Eth | Threshold energy for data transmission |
| Ni.E | Energy of node i (i = 1,2,3,4...) |
| Parameters | Values |
|---|---|
| Node count | 100:50:500 |
| Aggregate of sinks | 9 |
| Maximum range of transmission per node | 2 Km |
| Deployment region: 3D area of 10 Km | 10 Km2 |
| DATA Header size | 11 Bytes |
| DATA Payload size | 72 Bytes |
| Size of ACK Packet | 50 bits |
| Size of neighbor request | 50 bit |
| Data rate | 16 Kbps |
| Initial energy per node | 100 J |
| Maximum Transmission Power | 90 dB re |
| Power threshold for receiving | 10 dB re |
| Sending energy | 50 W |
| Receiving energy | 158 mW |
| Idle Energy | 158 mW |
| Center Frequency | 12 KHz |
| Acoustic Propagation | 1500 m/s |
| 2 Km | |
| Bandwidth | 4 KHz |
| Random Walk | 2 m/s |
| Probability of moving left | 0.5 |
| Probability of moving right | 0.5 |
| Alive node threshold energy | 5 J |
| P1 | 1 |
| P2 | 0.5 |
| Number of Nodes | % Improvement in PDR | % Improvement in Energy Tax |
|---|---|---|
| 100 | 26 | 47 |
| 150 | 9 | 43 |
| 200 | 2 | 6 |
| 250 | 1 | 2 |
| 300 | 1.5 | 3 |
| 350 | 1.4 | 4.1 |
| 400 | 1.1 | 3.5 |
| 450 | 0.98 | 4.2 |
| 500 | 0.9 | 4.6 |
| Total Avg | 4.8 | 13 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jan, S.; Yafi, E.; Hafeez, A.; Khatana, H.W.; Hussain, S.; Akhtar, R.; Wadud, Z. Investigating Master–Slave Architecture for Underwater Wireless Sensor Network. Sensors 2021, 21, 3000. https://doi.org/10.3390/s21093000
Jan S, Yafi E, Hafeez A, Khatana HW, Hussain S, Akhtar R, Wadud Z. Investigating Master–Slave Architecture for Underwater Wireless Sensor Network. Sensors. 2021; 21(9):3000. https://doi.org/10.3390/s21093000
Chicago/Turabian StyleJan, Sadeeq, Eiad Yafi, Abdul Hafeez, Hamza Waheed Khatana, Sajid Hussain, Rohail Akhtar, and Zahid Wadud. 2021. "Investigating Master–Slave Architecture for Underwater Wireless Sensor Network" Sensors 21, no. 9: 3000. https://doi.org/10.3390/s21093000
APA StyleJan, S., Yafi, E., Hafeez, A., Khatana, H. W., Hussain, S., Akhtar, R., & Wadud, Z. (2021). Investigating Master–Slave Architecture for Underwater Wireless Sensor Network. Sensors, 21(9), 3000. https://doi.org/10.3390/s21093000







