3.1. Preliminaries—Basics of Supersingular Iosgency Curve
Initially, we briefly introduce the supersingular isogeny curve that has been used to design the proposed signature scheme and its problems to prove its resistance against cyberattacks. We consider two elliptic curves
over a finite field
also used in [
36,
37]. An isogeny φ:
is a nonconstant morphism that preserves the group structure [
38]. The degree of an isogeny φ is equal to the degree of φ as a morphism. An isogeny of degree ℓ is called a ℓ-isogeny [
39,
40]. If φ is separable, then deg φ = #ker φ. If isogeny is separable between two curves, we say that they are isogenous [
41]. Tate’s theorem [
42,
43] is that two curves
over
are isogenous if and only if
. An isogeny can be identified by its kernel in such a way that for every finite subgroup G of
, there is a unique
and a separable isogeny φ:
with kernel G such that φ:
. To obtain subgroup G we can use Vélu’s formulae.
Isogenies with the same domain and range are called as endomorphisms. The set of endomorphisms is maximal order either to quaternion algebra or to an imaginary quadratic field. The curve is supersingular for the first case; otherwise, the curve is ordinary. In the case of a supersingular elliptic curve, there is always a curve in the isomorphism class defined over , thus its j-invariant is over . One can construct a so-called isogeny graph for any prime , where an edge and vertex are associated with an l-isogeny and j-invariant, respectively. Next, we present a few hard problems related to supersingular elliptic curves over .
Problem 1 (computational supersingular isogeny () problem): suppose to be an isogeny with kernel () where chose at random from ᴢ/ and not divisible by . Find a generator of () where is given.
Problem 2 (computational supersingular isogeny () problem): suppose to be an isogeny with kernel () where chose at random from ᴢ/ and not divisible by . Find a generator of () where is given.
Problem 3 (supersingular isogeny Diffie–Hellman (SIDH) problem): let be an isogeny with kernel and be an isogeny with kernel , where are chosen at random from ᴢ/ and ᴢ/, respectively. {,} be given, find j-invariant of 〈)〉.
Problem 4 (supersingular isogeny auxiliary point ccomputation ()): suppose to be an isogeny with kernel () where chose at random from ᴢ/ and is not divisible by . The supersingular isogeny auxiliary point computation problem is to find the auxiliary point and , where } are given.
Problem 5 (supersingular isogeny auxiliary point computation ()): suppose to be an isogeny with kernel () where is chosen at random from ᴢ/ and is not divisible by . The supersingular isogeny auxiliary point computation problem is to find the auxiliary point and , where {} are given.
A signature scheme consists of three polynomial time algorithms: key generation, registration, and validation. We prove the security of the scheme using the existential unforgeable under an adaptively chosen message attack (EU-ACMA) (32). A forger and a challenger play a game where the forger uses the public key and signing oracle model. The forger issues signature queries to the sign oracle to generate a signature of message and the oracle sends to the forger. The attack is considered successful when the forger produces a valid signature and message pair different from those generated from the query oracle.
Definition 1. A digital signature scheme is existentially unforgeable under an adaptively chosen message attack (EU-ACMA) if any adversary à cannot produce a valid message–signature pair in polynomial time with access to the signing oracle.
Setup: Suppose we have a function KeyGen to output key pair (pk, sk), and challenger give the pk to the adversary Ã.
Queries: The adversary à issues signature queries to sign oracle Ś to generate valid signature corresponding to messages .
Output: Finally, adversary à generates a valid message signature pair () and wins the game if .
The signature scheme is secure if probability to distinguish between simulated signature and real signature is negligible for adversary à with access to signing oracle
i.e.,
3.2. System Model
We consider an IoE environment in which several heterogeneous smart nodes such as an individual human, an organization, sensors, vehicles, smart watches, smart phones are deployed as shown in
Figure 1. We classify these smart nodes into two main categories: service provider and client. In the IoE environment, a client can be an organization, an individual human or any device that wants to access services such as health reports collection, banking, e-commerce. The client encrypts the data with its signature and sends it to the service provider. The service provider allows authentic clients to access the service. A service provider provides an organization with three servers: the key generation server, the database server, and the validation server. For individual clients, the key generation server generates the global parameters and public–private keys. The database server maintains the data and the validation server helps in authenticating the clients. The service provider generates appropriate rights using a tag machine and performs key generation, encryption/decryption using the supersingular isogeny curves. It issues the rights to clients based on the service such as a client can view only his/her data for a particular period. The Internet of Everything (IoE) is considered as superset of Internet of Things (IoT). IoE covers the wider concept of connectivity where network intelligence at the edge devices makes it a more complex network tha then IoT. So, basically, it can be considered as an extension of the IoT in terms of network management and network intelligence.
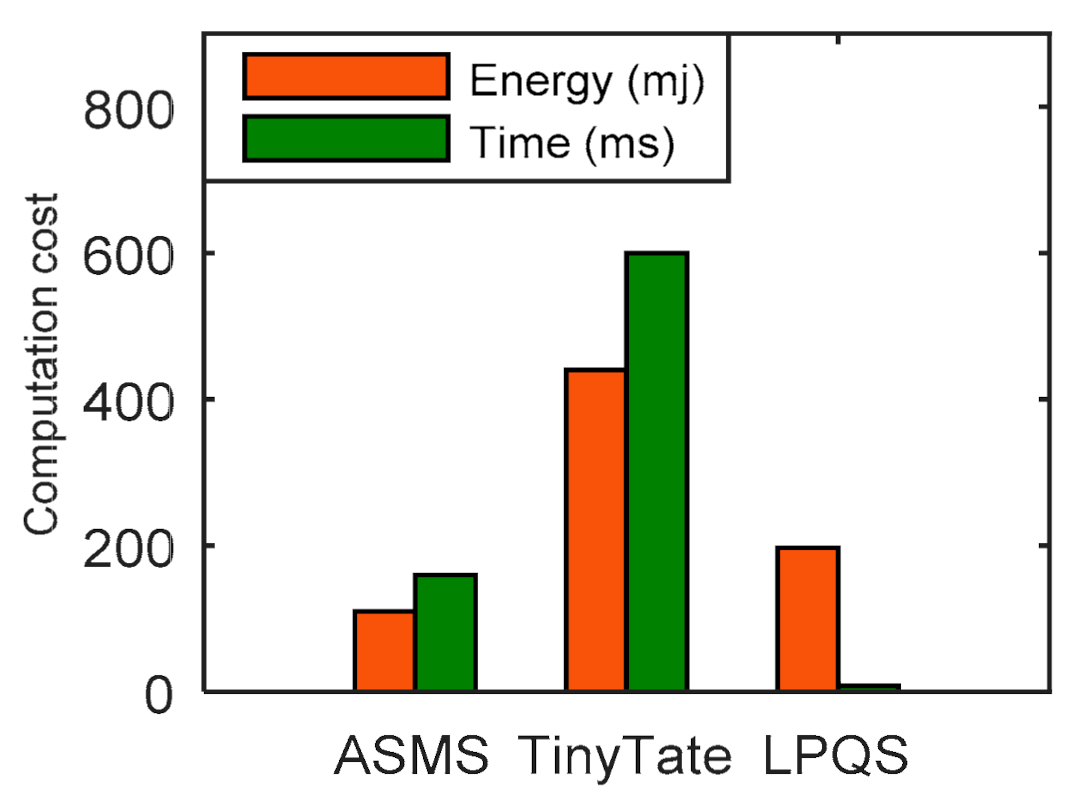
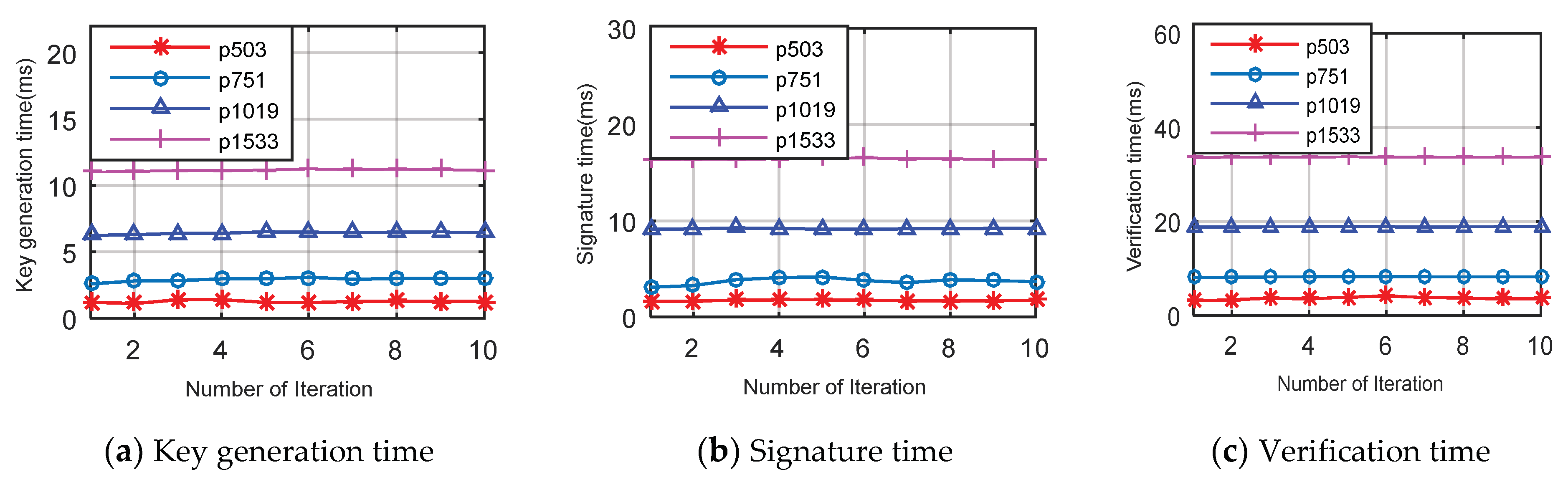
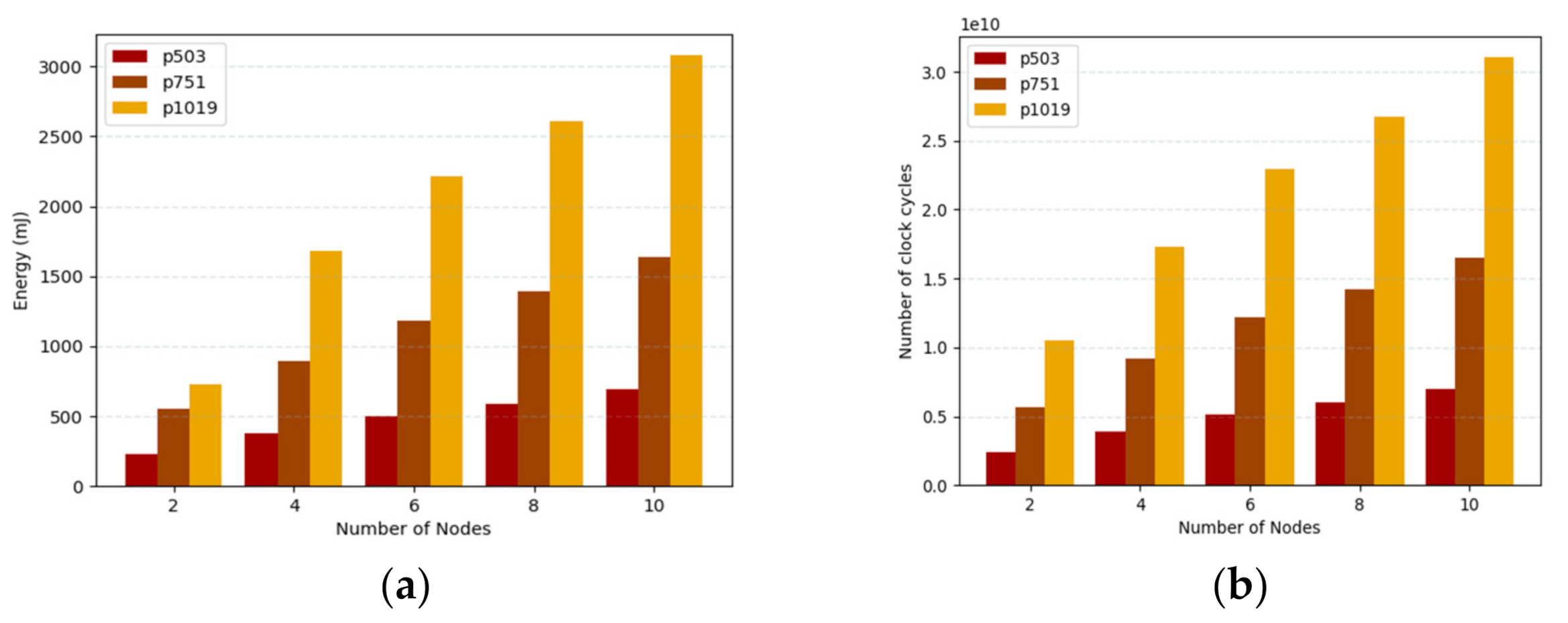
To ensure secure data transmission between a service provider and clients, and to reduce the complexity of the system with less consumption of the system resources, we present a LPQS scheme for secure data transmission for an IoE environment. The scheme uses supersingular isogeny curves for the postquantum cryptography signature. The proposed scheme consists of four phases: initialization, registration, signature, and validation. In the first phase, the service provider initializes all the parameters for global access. In the second phase, the service provider calculates the basis points for the clients using the ID of an individual client. The client performs the signature on the data with the help of the service provider in the signature phase. In the validation phase, the clients and service providers validate each other using the two isogeny curves. We want to clarify that “green” means a reduction in the computing requirement for providing security in the IoE environment. The proposed framework LPQS reduces the size of keys and signature for enabling security in the IoE. It also uses keys which can be used for longer period and are flexible in use, further reducing computation at the IoE nodes. Thus, green design means it is energy-efficient for the IoE nodes, as well as computing power efficient for the coordinator nodes at the edge.
3.3. Lightweight Post Quantum Signature
Firstly, in the initialization phase, the service provider initializes the system by setting all the global parameters as a set
, where the description and use of every parameter is given in
Table 1. Isogeny-based cryptosystem uses supersingular elliptic curves over characteristic
, where
is a prime of the form
. Here,
are positive integers such that
and
is a small cofactor to ensure
as a prime. This special form of
allows us to efficiently compute isogenies, as given in the next sections. The global parameters generated by service provider include
over the curve
of finite field
of characteristics
with
element. The service provider selects a random integer α, such that
. The random number α is kept secret as the service provider’s secret key. The service provider uses an ephemeral secret key, which changes in every session to support nontraceability. Fix points
such that group
generated by
and
in the whole group
. The elliptic curve points
are the global parameters of the supersingular isogeny-based cryptosystem.
, where
is the generator of a kernel of service provider which creates a secret subgroup of
E[
].
is the elliptic curve that is the image curve under the isogeny {
}.
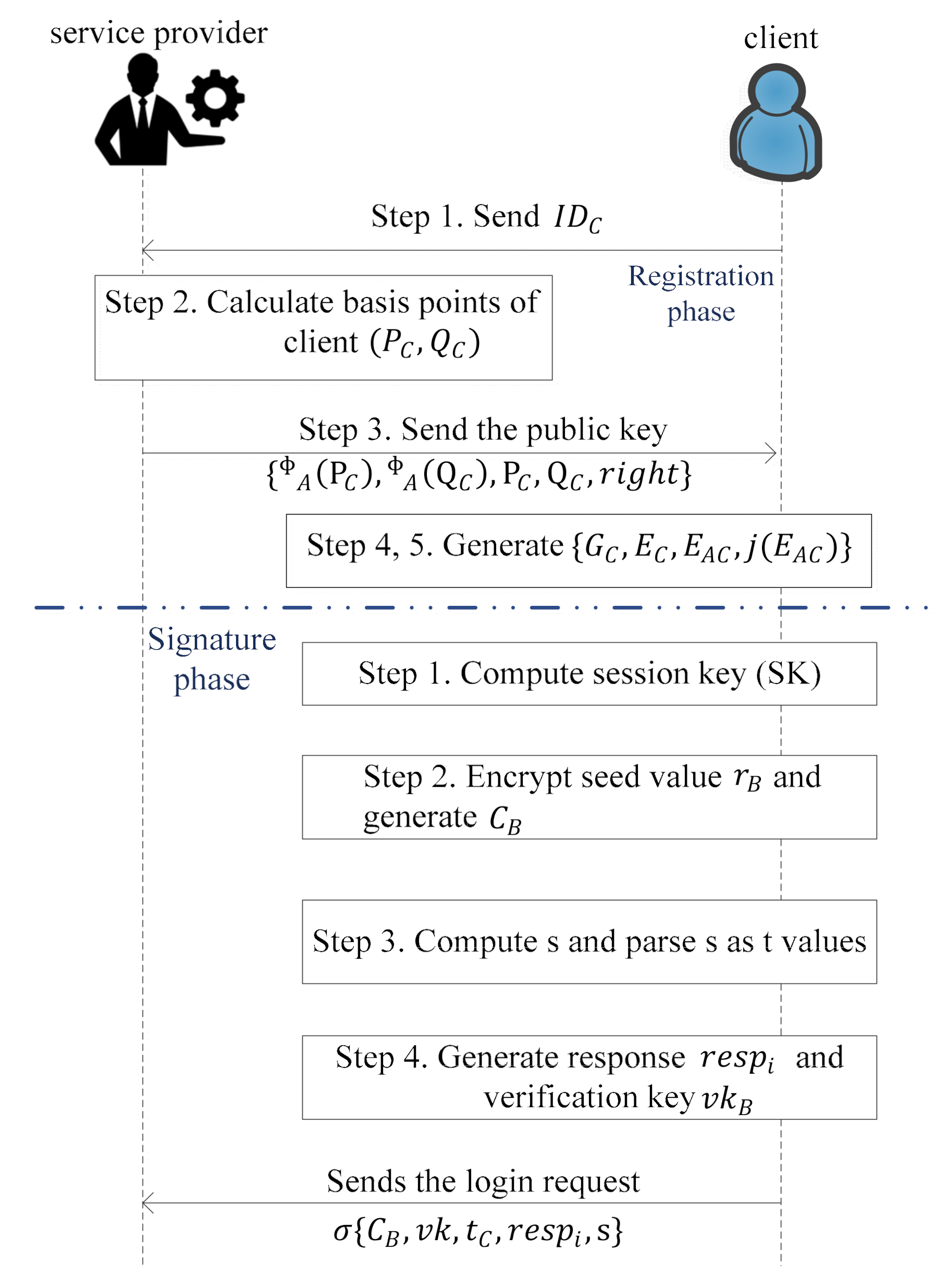
Secondly, the in registration phase, service provider performs the registration with the help of the client (C) to provide access to the facility/services of the service provider in the IoE environment as shown in
Figure 2 and the steps are:
- Step 1.
The client sends its identity generated randomly to the service provider through a public channel.
- Step 2.
After receiving the
, the service provider calculates basis points of client i.e.,
and
using the
and
, which are assigned by service provider as expressed by Equations (1) and (2).
where,
is a fixed hash function, and rights are the authority assigned to the client. The notation
is the xor function, and
is a concatenation operation.
- Step 3.
The service provider generates the public key of client as and sends it to the .
- Step 4.
Upon receiving
, the client selects a random number as a secret key from
. The generator
for the kernel of the client is expressed as given by Equation (3).
where
and
are the basis for
and
.
- Step 5.
The client computes the image curve and also computes the shared secret value , where is the j-invariant of the image curve .
Thirdly, in the signature phase, the client does the following four steps to sign message
which is shown in
Figure 2.
- Step 1.
The client calculates the , where and is the timestamp.
- Step 2.
Further, encrypt the seed value
as expressed by Equation (4).
- Step 3.
Compute . Parse as t values .
- Step 4.
If then response else . is only calculated by the service provider and verification key for . The client sends the login request to the service provider.
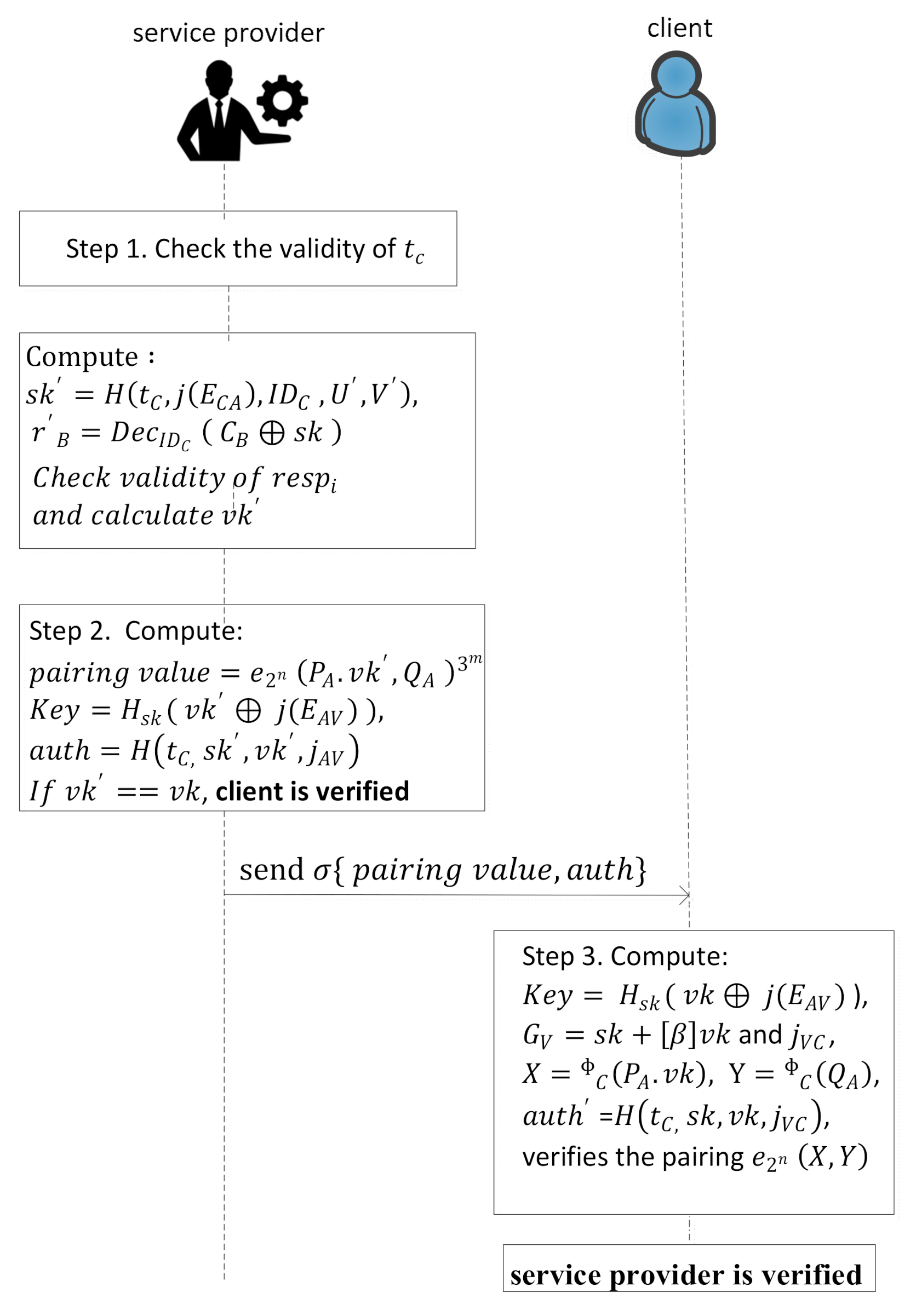
In this last validation phase the service provider and the client validate each other, which is shown in
Figure 3 with stepwise description as follows.
- Step 1.
The service provider checks the validity of
of received signature
and if it is valid then proceeds further; otherwise the service provider rejects the request. After checking the
validity, the service provider calculates the image of the client with the help of its basis as,
,
and also computes
and
as expressed by Equation (5).
for
i = 1 to
t, parse
s as
t values and check if
then parse
. Check if
has order
and if
generates
and
generates
. If
then check if
has order
and generates
and
If
is equal to
then
is authenticated.
- Step 2.
The service provider computes
and develops the key and authentication using
and
as expressed in Equations (6) and (7), and computes the value of
and
(as shown in
Figure 3) and send
to the client.
- Step 3.
After receiving the signature, the client verifies the authenticity of the service provider and computes
) and
and
as shown in
Figure 3. Further, it calculates
,
=
and also verifies the pairing
Now the service provider is also verified.