BiRep: A Reputation Scheme to Mitigate the Effects of Black-Hole Nodes in Delay-Tolerant Internet of Vehicles
Abstract
:1. Introduction
- BiRep is proposed as a new and completely distributed reputation scheme designed to provide an effective and robust identification and punishment of black-hole nodes in a DT-IoV network to diminish their impact on network performance. BiRep can work with any underlying routing protocol.
- The BiRep design is thoroughly described, comprising the evaluation of mechanisms for detecting black-hole nodes, based on message forwarding proofs stored in exchanged messages, the gains achieved by exchanging reputation information with other nodes, and the effect of different punishment actions over black-hole nodes.
- BiRep performance is studied in different scenarios and compared with other related work.
2. Background and Related Work
2.1. Delay-Tolerant Internet of Vehicles
2.2. Attacks in DT-IoV
2.3. Black-Hole Solutions in DT-IoV
3. Preliminaries
3.1. Assumptions
3.2. Reputation System Performance Metrics
3.2.1. Routing Protocol Metrics
3.2.2. Node Classification Metrics
4. Building the Reputation System
4.1. Approach to Building the Reputation System
4.2. Simulation Scenario
4.3. Detection Phase
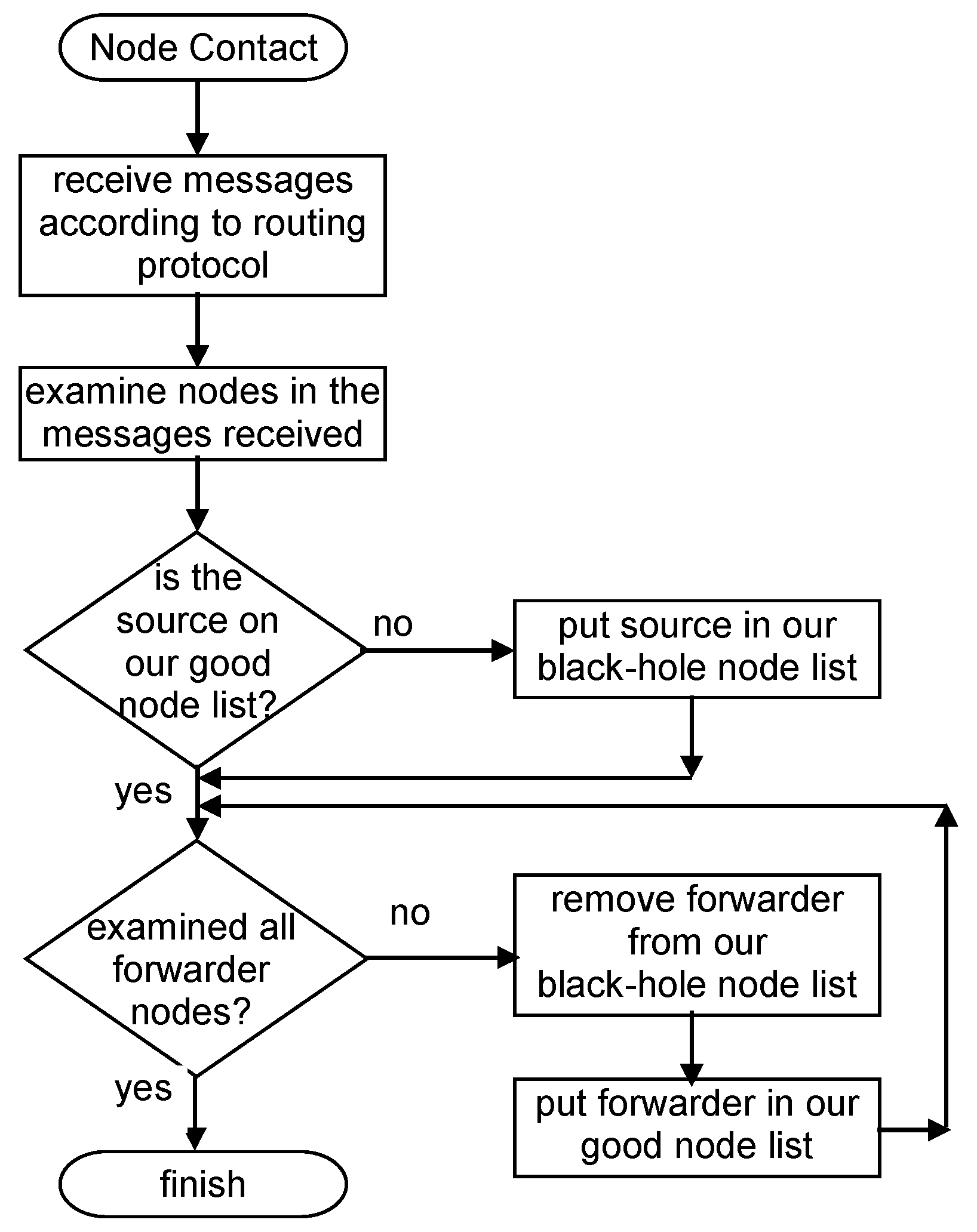
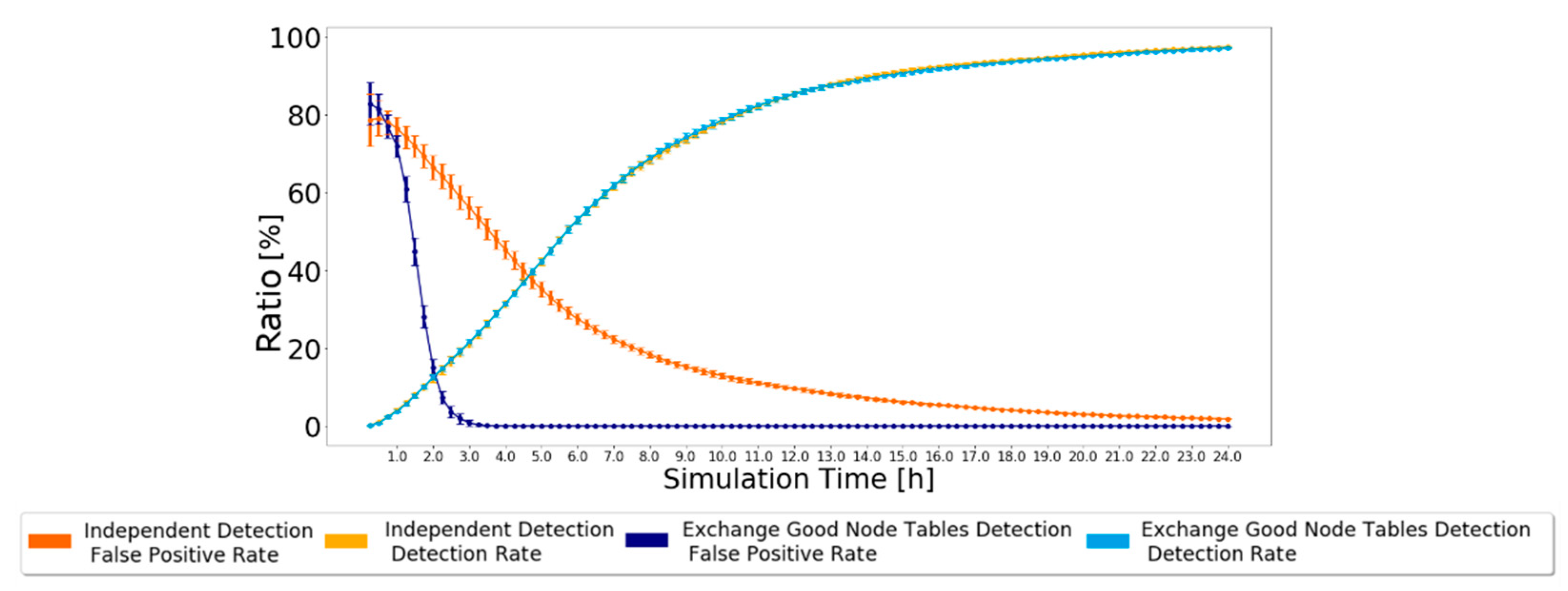
4.3.1. Independent Detection Scheme: Scheme Description
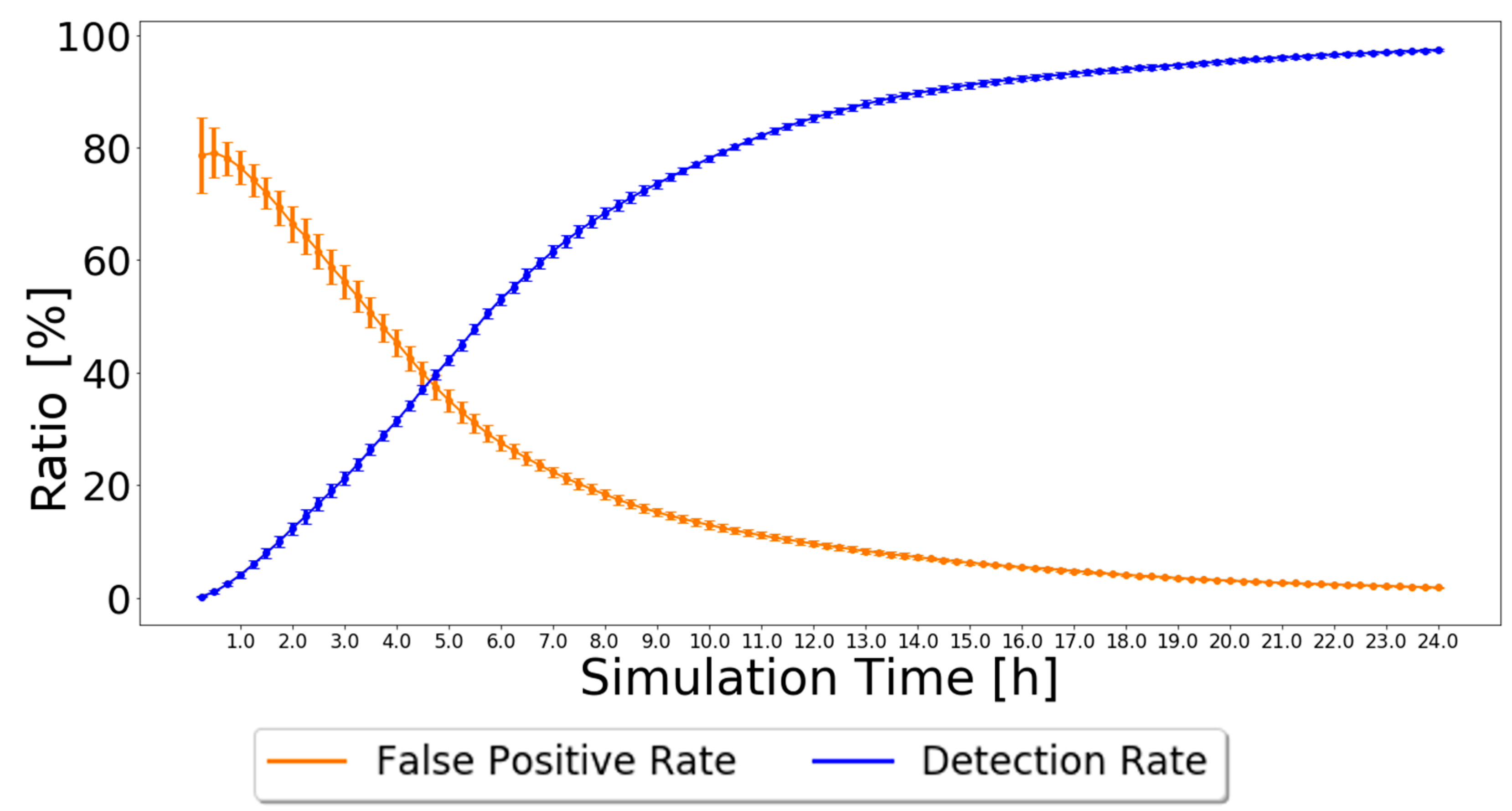
4.3.2. Independent Detection Scheme: Analysis and Discussion
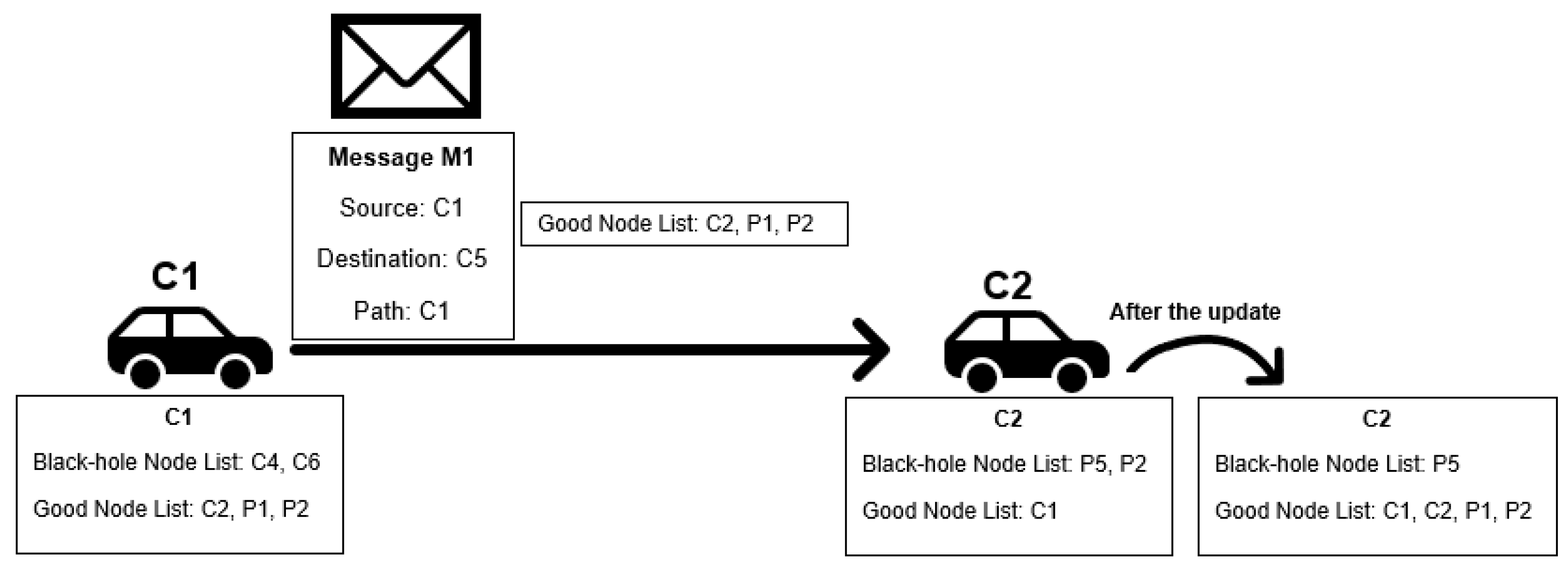
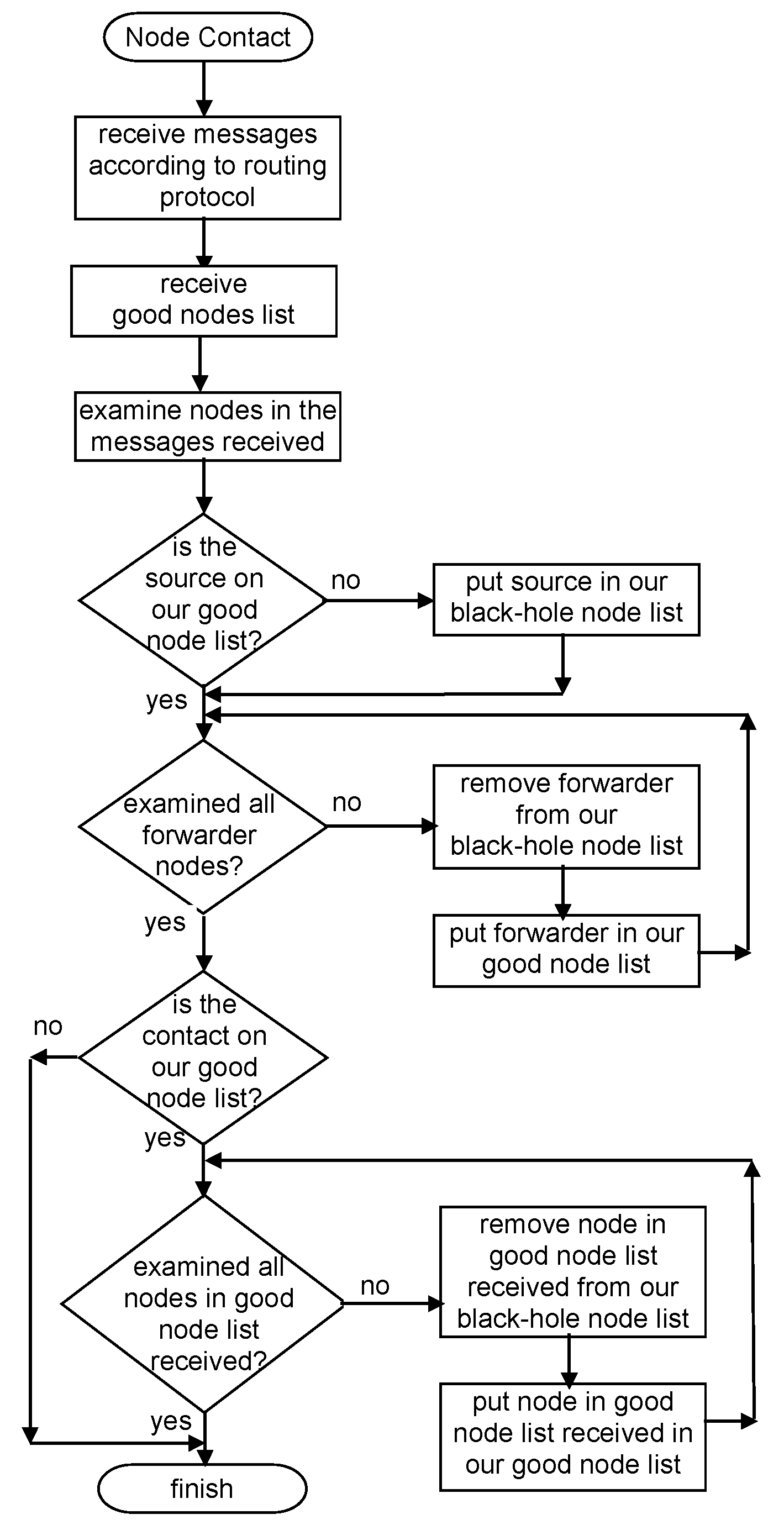
4.3.3. Exchange Good Nodes Tables Detection Scheme: Scheme Description
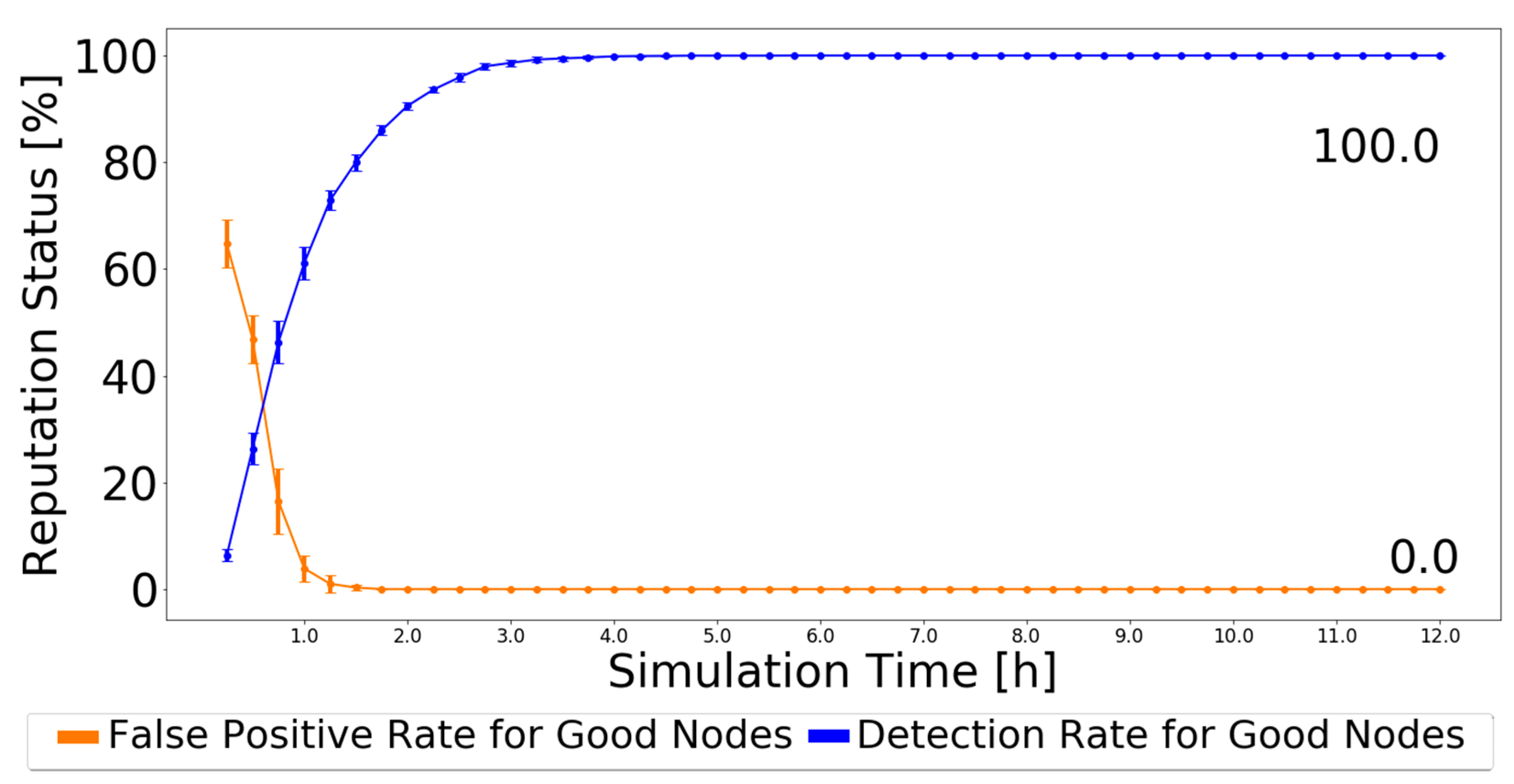
4.3.4. Exchange Good Nodes Tables Detection Scheme: Analysis and Discussion
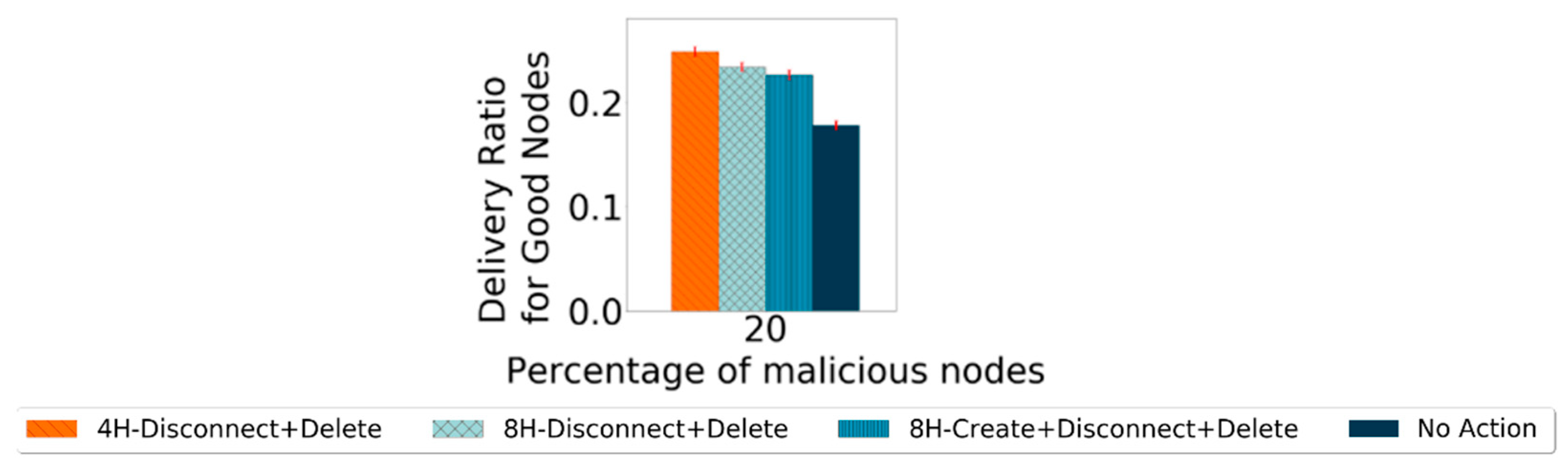
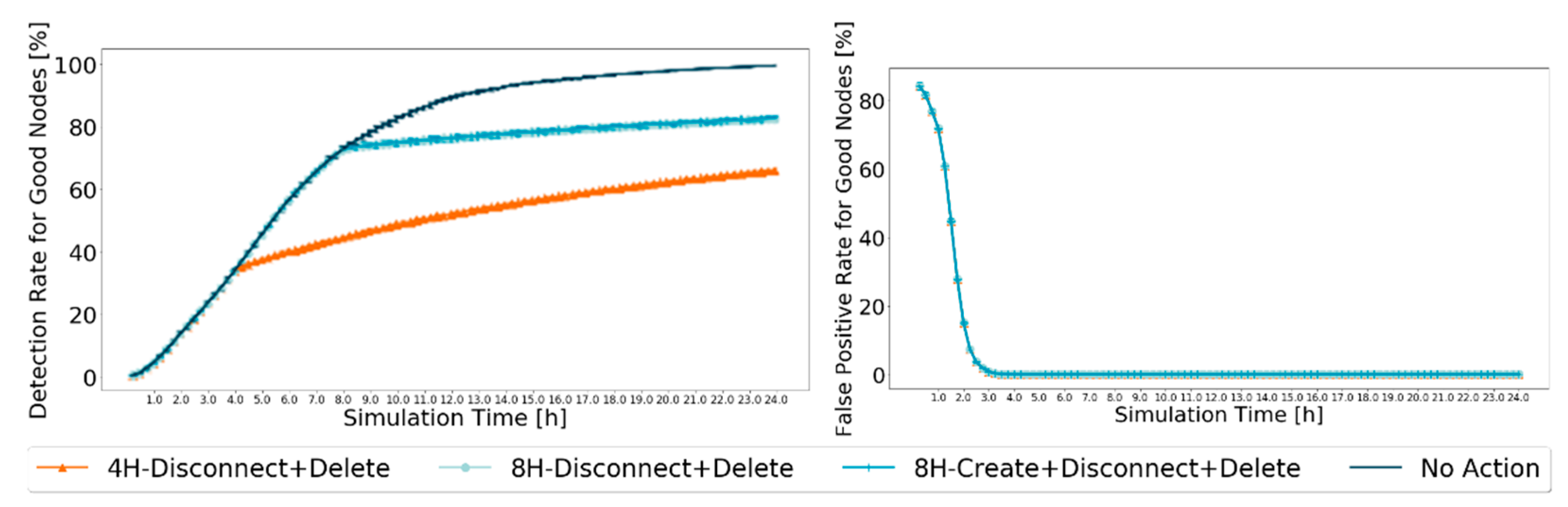
4.4. Action Phase
- Creation Action: Nodes do not create messages for nodes that they have in the black-hole node list.
- Disconnect Action: When a node is within range of another node that is in the black-hole node list, no connection is established, and no messages are exchanged.
- Delete Action: All messages from nodes in the black-hole list are deleted from buffers.
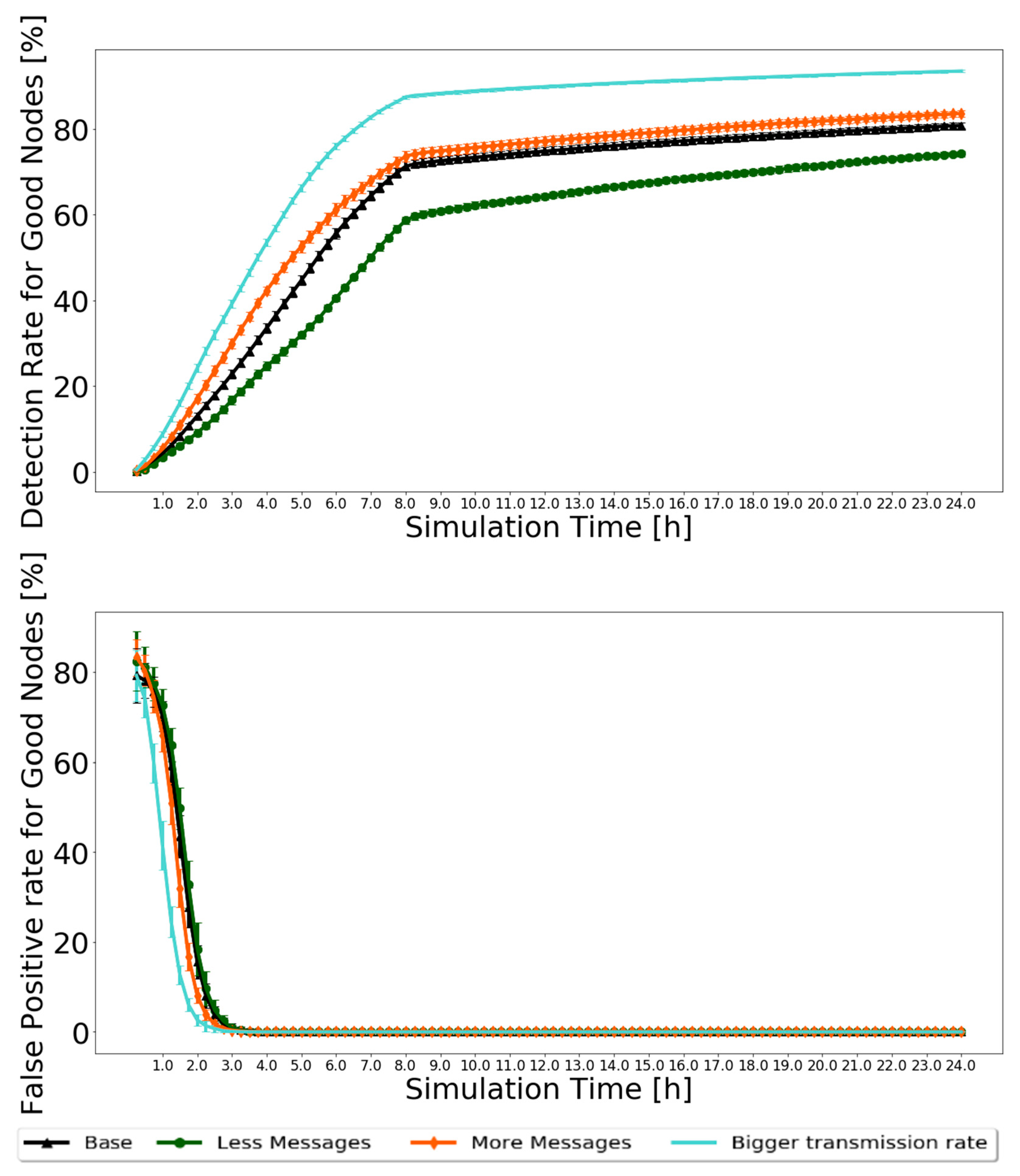
5. Robustness Results and Analysis
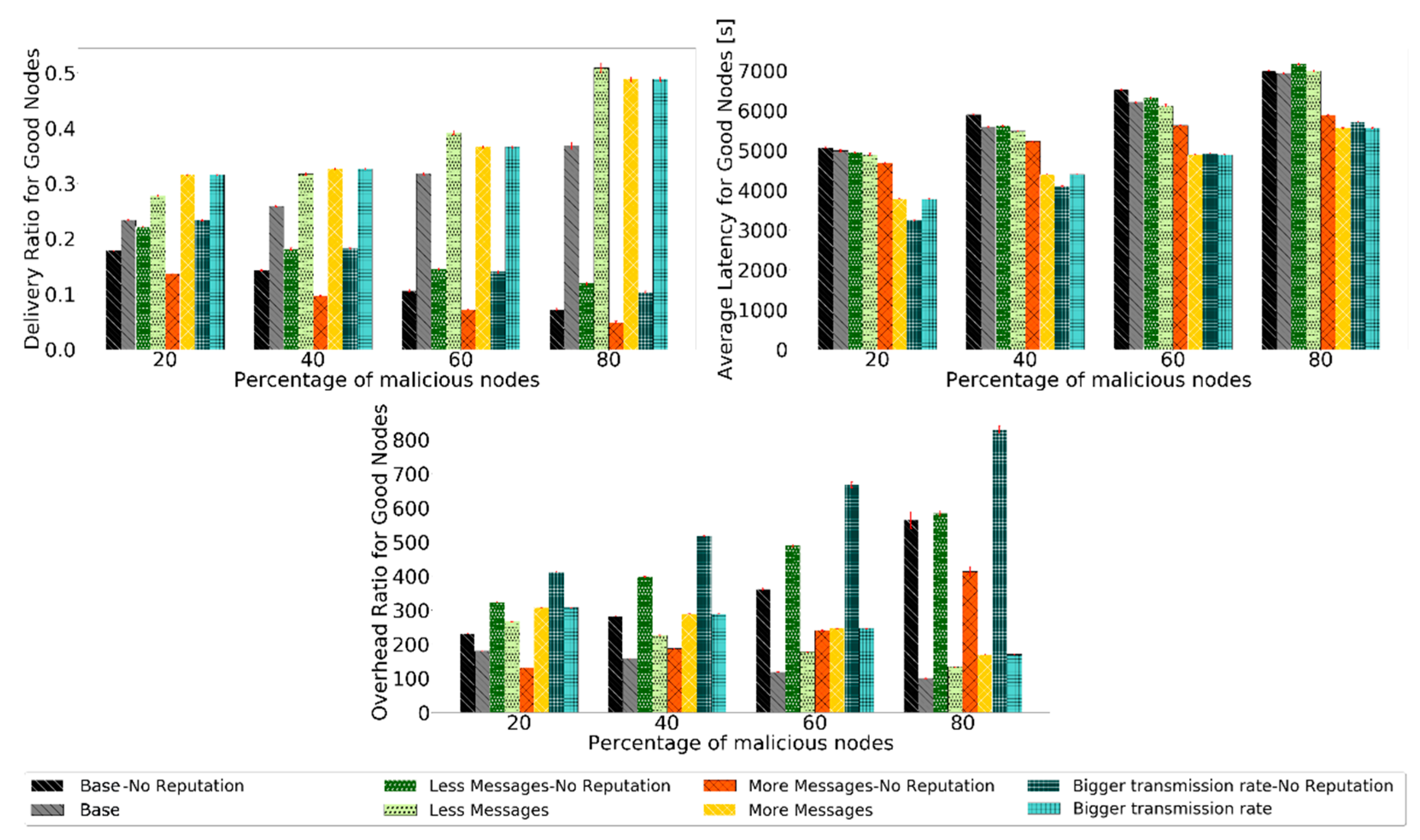
5.1. Varying the Message Generation Rate
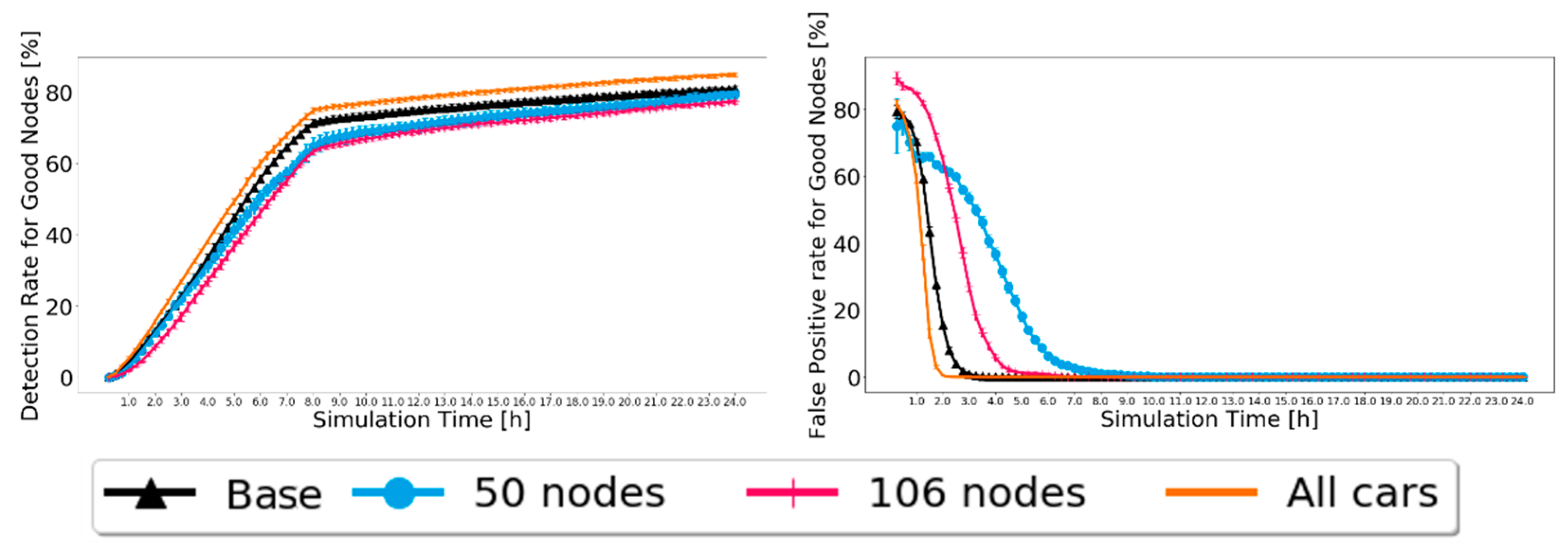
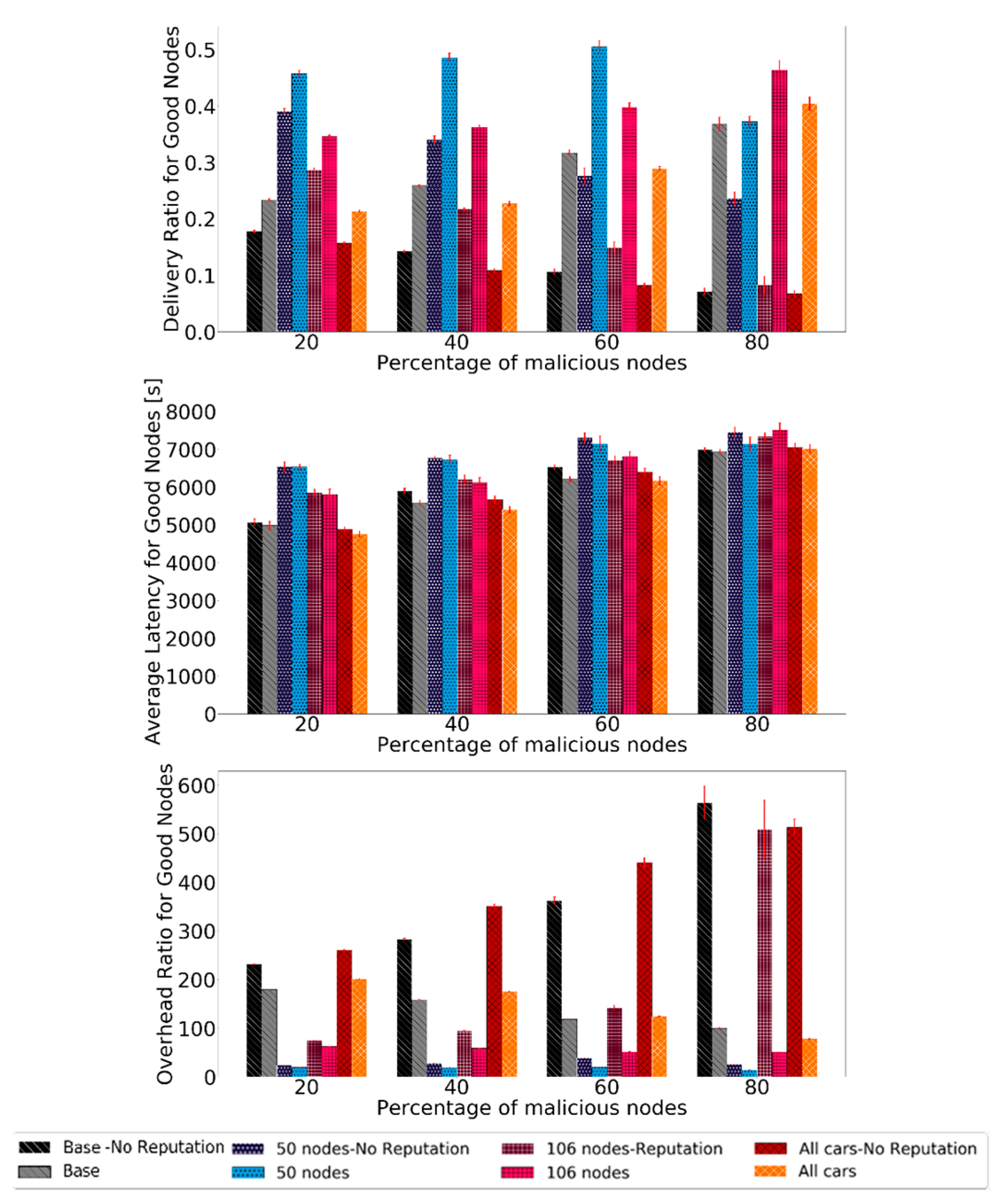
5.2. Varying the Node Density
5.3. Comparing BiRep with the State-of-the-Art
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Warthman, F. The InterPlaNetary (IPN) Internet Project, Version 3.2.; Delay- and Disruption-Tolerant Networks (DTNs)—A Tutorial; InterPlanetary Networking Special Interest Group (IPNSIG); Available online: http://ipnsig.org/wp-content/uploads/2015/09/DTN_Tutorial_v3.2.pdf (accessed on 14 September 2015).
- Silva, L.; Magaia, N.; Sousa, B.; Kobusińska, A.; Casimiro, A.; Mavromoustakis, C.X.; Mastorakis, G.; Albuquerque, V.H.C. Computing Paradigms in Emerging Vehicular Environments: A Review. IEEE/CAA J. Autom. Sin. 2021, 8, 491–511. [Google Scholar] [CrossRef]
- Pereira, P.R.; Casaca, A.; Rodrigues, J.J.P.C.; Soares, V.N.G.J.; Triay, J.; Cervelló-Pastor, C. From Delay-Tolerant Networks to Vehicular Delay-Tolerant Networks. IEEE Commun. Surv. Tutor. 2012, 14, 1166–1182. [Google Scholar] [CrossRef]
- Magaia, N.; Pereira, P.; Correia, M.P.; Rawat, D.B.; Rodrigues, J.J.P.C.; Stojmenovic, I. Security in delay-tolerant mobile cyber physical applications. Cyber Phys. Syst. Theory Pract. 2015, 373–394. [Google Scholar] [CrossRef]
- Fall, K. A delay-tolerant network architecture for challenged Internets. In Proceedings of the SIGCOMM’03 2003 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Karlsruhe, Germany, 25–29 August 2003; pp. 27–34. [Google Scholar] [CrossRef] [Green Version]
- Veniam. The Internet of Moving Things. Available online: https://veniam.com/ (accessed on 26 January 2021).
- Dini, G.; Duca, A.L. A reputation-based approach to tolerate misbehaving carriers in delay tolerant networks. In Proceedings of the 2010 IEEE Symposium on Computers and Communications (ISCC), Riccione, Italy, 22–25 June 2010; pp. 772–777. [Google Scholar] [CrossRef]
- Magaia, N.; Pereira, P.R.; Correia, M.P. Nodes’ Misbehavior in Vehicular Delay-Tolerant Networks. In Proceedings of the Conference on Future Internet Communications (CFIC 2013), Coimbra, Portugal, 15–16 May 2013. [Google Scholar] [CrossRef]
- Magaia, N.; Sheng, Z. ReFIoV: A novel reputation framework for information-centric vehicular applications. IEEE Trans. Veh. Technol. 2019, 68, 1810–1823. [Google Scholar] [CrossRef] [Green Version]
- Chuah, M.; Yang, P.; Han, J. A ferry-based intrusion detection scheme for sparsely connected ad hoc networks. In Proceedings of the 2007 Fourth Annual International Conference on Mobile and Ubiquitous Systems: Networking Services, (MobiQuitous), Philadelphia, PA, USA, 6–10 August 2007; pp. 1–8. [Google Scholar] [CrossRef]
- Lindgren, A.; Doria, A.; Davies, E.; Grasic, S. Probabilistic routing protocol for intermittently connected networks. RFC 6693 2012. [Google Scholar] [CrossRef] [Green Version]
- Burgess, J.; Gallagher, B.; Jensen, D.; Levine, B.N. MaxProp: Routing for vehicle-based disruption-tolerant network. In Proceedings of the 25th IEEE Infocom Conference, Barcelona, Spain, 23–29 April 2006; pp. 1688–1698. [Google Scholar] [CrossRef]
- Ren, Y.; Chuah, M.; Yang, J.; Chen, Y. MUTON: Detecting malicious nodes in disrupt-tolerant networks. In Proceedings of the 2010 IEEE Wireless Communication and Networking Conference, Sydney, Australia, 18–21 April 2010; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Guo, Y.; Schildt, S.; Wolf, L. Detecting black-hole and greyhole attacks in vehicular delay tolerant networks. In Proceedings of the 2013 Fifth International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 7–10 January 2013; pp. 1–7. [Google Scholar] [CrossRef]
- Guo, Y.; Schildt, S.; Pögel, T.; Wolf, L.C. Detecting Malicious behavior in a Vehicular DTN for Public Transportation. In Proceedings of the Global Information Infrastructure and Networking Symposium 2013 (GIIS’13), Trento, Italy, 28–31 October 2013; pp. 1–8. [Google Scholar] [CrossRef]
- Ren, Y.; Chuah, M.C.; Yang, J.; Chen, T. Detecting black-hole attacks in Disruption-Tolerant Networks through packet exchange recording. In Proceedings of the 2010 IEEE International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Montreal, QC, Canada, 14–17 June 2010; pp. 1–6. [Google Scholar] [CrossRef] [Green Version]
- Dini, G.; Duca, A.L. Towards a reputation-based routing protocol to contrast black-holes in a delay tolerant network. Ad Hoc Netw. 2012, 10, 1167–1178. [Google Scholar] [CrossRef]
- Dias, J.A.F.F.; Rodrigues, J.J.P.C.; Xia, F.; Mavromoustakis, C.X. A Cooperative Watchdog System to Detect Misbehavior Nodes in Vehicular Delay-Tolerant Networks. IEEE Trans. Ind. Electron. 2015, 62, 7929–7937. [Google Scholar] [CrossRef]
- Mantas, N.; Louta, M.; Karapistoli, E.; Karetsos, G.T.; Kraounakis, S.; Obaidat, M.S. Towards an incentive-compatible, reputation based framework for stimulating cooperation in opportunistic networks: A survey. IET Netw. 2017, 6, 169–178. [Google Scholar] [CrossRef]
- Rehman, G.; Ghani, A.; Muhammad, S.; Singh, M.; Singh, D. Selfishness in Vehicular Delay-Tolerant Networks: A Review. Sensors 2020, 20, 3000. [Google Scholar] [CrossRef] [PubMed]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Guo, J.; Li, X.; Liu, Z.; Ma, J.; Yang, C.; Zhang, J.; Wu, D. TROVE: A Context-Awareness Trust Model for VANETs Using Reinforcement Learning. IEEE Internet Things J. 2020, 7, 6647–6662. [Google Scholar] [CrossRef]
- The ONE. The Opportunistic Network Environment Simulator. Available online: https://akeranen.github.io/the-one/ (accessed on 26 January 2021).
- Magaia, N.; Borrego, C.; Pereira, P.R.; Correia, M. ePRIVO: An enhanced privacy-preserving opportunistic routing protocol for vehicular delay-tolerant networks. IEEE Trans. Veh. Technol. 2018, 67, 11154–11168. [Google Scholar] [CrossRef] [Green Version]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Single-copy Routing in Intermittently Connected Mobile Networks. In Proceedings of the First IEEE Conference on Sensor and Ad Hoc Communications and Networks (IEEE SECON 2004), Santa Clara, CA, USA, 4–7 October 2004; pp. 235–244. [Google Scholar] [CrossRef]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and wait: An efficient routing scheme for intermittently connected mobile networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking, ACM, Philadelphia, PA, USA, 22–26 August 2005; pp. 252–259. [Google Scholar] [CrossRef]
- Luo, B.; Li, X.; Weng, J.; Guo, J.; Ma, J. Blockchain Enabled Trust-Based Location Privacy Protection Scheme in VANET. IEEE Trans. Veh. Technol. 2020, 69, 2034–2048. [Google Scholar] [CrossRef]

| Scheme | Information Used | Detection | Action | Limitations |
|---|---|---|---|---|
| FBIDM [10] | past meetings, past delivery probability | suspicious multiple times | exclude black-holes | requires ferry nodes |
| MUTON [13] | past meetings, past delivery probability, transitivity | suspicious multiple times | exclude black-holes | requires ferry nodes |
| MDS [14] | encounter records | forwards less than a threshold | exclude black-holes | no exchange of trust information |
| MDS extension [15] | encounter records, cluster analysis | forwards less than a threshold | exclude black-holes | no exchange of trust information |
| Packet Exchange Recordings [16] | delivery records | forwards less than a threshold multiple times | none described | no exchange of trust information |
| RCAR [17] | messages carry forwarders, ACK messages | aging decreases reputation | prefer nodes with a higher reputation | no exchange of trust information, requires ACK |
| CWS [18] | messages delivered, relayed, dropped | exchange of reputation, thresholds | few resources used for nodes with low reputation | does not assess classification performance |
| BiRep | messages carry forwarders | exchange of reputation, node has no forwarding record | warmup, disconnect from black-holes, delete messages from black-holes |
| Simulation Time | 24 h |
|---|---|
| Map | Helsinki downtown (4500 m × 3500 m) |
| Movement Model | Shortest Path Map-Based Movement Model |
| Nodes’ speed | Pedestrians 1.8–5.4 km/h; Cars 10–50 km/h; Trams 25–36 km/h |
| Number of nodes | 206 (Pedestrians: 100; Cars: 100; Trams: 6) |
| Nodes’ buffer size | 5 MB |
| Nodes’ wait time | 0–120 s |
| Message size | 500 kb–1 MB |
| Message generation interval | 25–35 s |
| Message TTL (Time to Live) | 5 h |
| Interfaces’ data rate | 250 kBps = 2 Mbps |
| Interfaces’ transmission range | 10 m |
| Scenario Name | Base | Less Messages | More Messages | Bigger Transmission Rate |
|---|---|---|---|---|
| Message generation interval | 25–35 s | 35–70 s | 9–18 s | 25–35 s |
| Interfaces’ data rate | 2 Mbps | 2 Mbps | 2 Mbps | 4 Mbps |
| Reputation Schemes | False Positive Ratio | Detection Ratio |
|---|---|---|
| FBIDM | 5% | 80% |
| MUTON | 2% | 95% |
| BiRep | 0% | 80% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nabais, C.; Pereira, P.R.; Magaia, N. BiRep: A Reputation Scheme to Mitigate the Effects of Black-Hole Nodes in Delay-Tolerant Internet of Vehicles. Sensors 2021, 21, 835. https://doi.org/10.3390/s21030835
Nabais C, Pereira PR, Magaia N. BiRep: A Reputation Scheme to Mitigate the Effects of Black-Hole Nodes in Delay-Tolerant Internet of Vehicles. Sensors. 2021; 21(3):835. https://doi.org/10.3390/s21030835
Chicago/Turabian StyleNabais, Catarina, Paulo Rogério Pereira, and Naercio Magaia. 2021. "BiRep: A Reputation Scheme to Mitigate the Effects of Black-Hole Nodes in Delay-Tolerant Internet of Vehicles" Sensors 21, no. 3: 835. https://doi.org/10.3390/s21030835
APA StyleNabais, C., Pereira, P. R., & Magaia, N. (2021). BiRep: A Reputation Scheme to Mitigate the Effects of Black-Hole Nodes in Delay-Tolerant Internet of Vehicles. Sensors, 21(3), 835. https://doi.org/10.3390/s21030835








