Availability of an RFID Object-Identification System in IoT Environments
Abstract
:1. Introduction
2. RFID Collision Analysis
2.1. RFID Collision Analysis through Stochastic Petri Nets
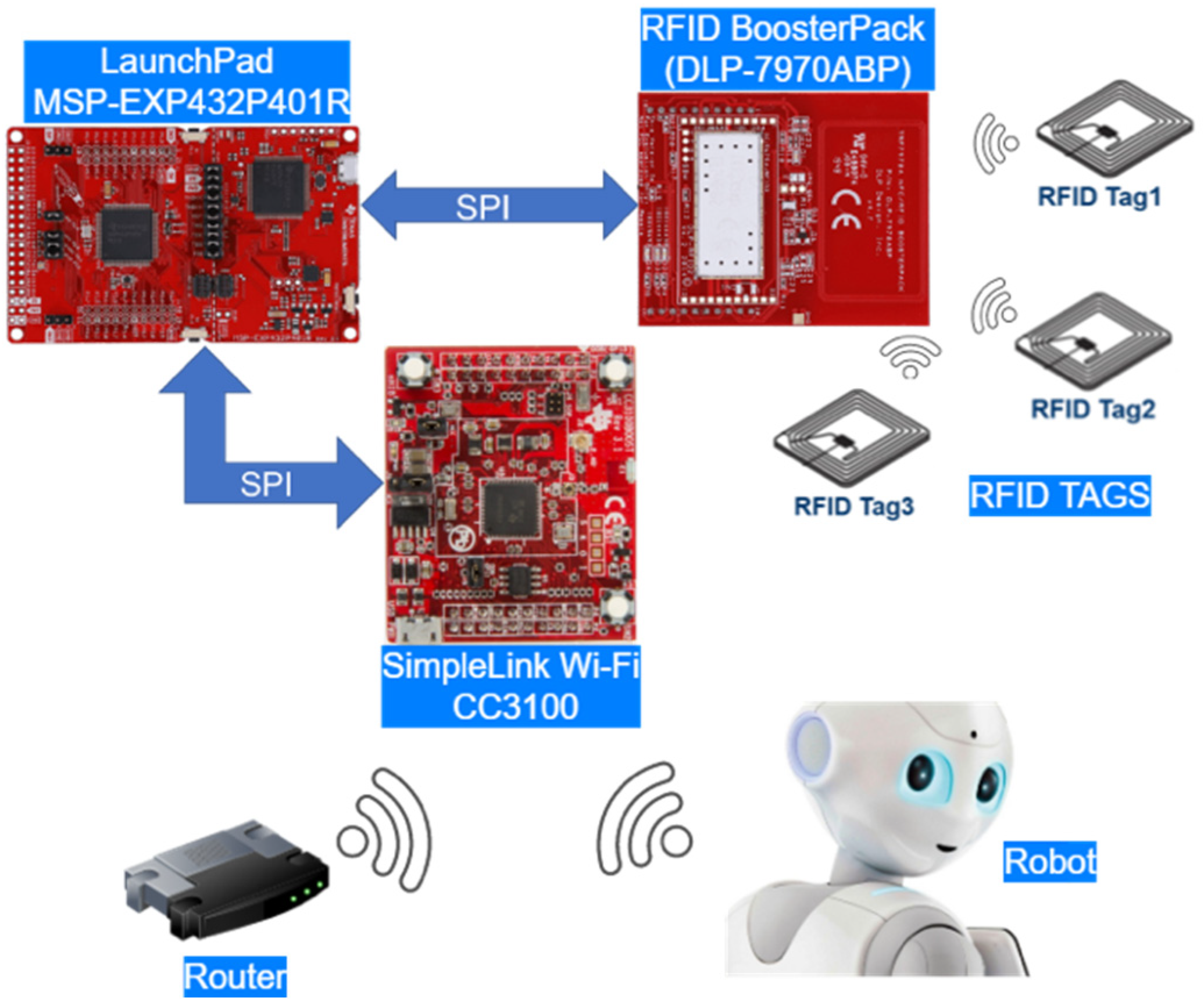
- LaunchPad MSP-EXP432P401R—developing board based on microcontroller MSP432 (ARM Cortex M4).
- TRF7970A NFC transceiver BoosterPack (DLP-7970ABP)—NFC/RFID transceiver with 16-slot RFID frame inventory.
- CC3100BOOST—SimpleLink Wi-Fi CC3100 wireless network processor BoosterPack.
- idle slot—a slot in the inventory frame without a response.
- single tag per slot—a slot with a single RFID tag response, the tag’s UID was received.
- collision slot—a slot in which multiple RFID tags responded. The anticollision algorithm needs to be run with a new set of values for the M and Lm parameters.
- Start—a place containing the number of slots that are analyzed during a frame inquiry.
- Current_Slot—the current slot indicated by the slot counter that is waiting to receive a response from the RFID tags.
- TI_0—an immediate transition that guaranties that each slot is processed one at a time. The purpose of the transition is to remove one token from Start and produce a new token in Current_Slot.
- Tag_per_slot—an immediate transition that is fired in the case that only one tag responds for the analyzed slot. This transition being fired removes the token from Current_Slot and produces one in Tag. As a result, one tag was detected from Nt tags present in the system.
- Idle_slot—an immediate transition that models not receiving a response during the interrogated slot.
- Collision_2Tags—an immediate transition that models a scenario in which two tags responded for the current slot. In this case, a new inquiry is needed to identify each RFID tag.
2.2. SPN Submodels to Analyze Collision between RFID Tags
- the main model populates Idle_Slots with 15 tokens, plus one collision slot;
- the submodel dealing with the collision among three tags populates Tag with one token and Idle_Slots with 14 tokens (i.e., one inquiry frame), plus one collision slot;
- the submodel dealing with the collision between two tags populates Tag with two token and Idle_Slots with 14 tokens.
2.3. RFID Collision Analysis through MATLAB
- —number of frames needed to solve the collision between tags and obtain their UID;
- —time length of a frame inventory (implementation-dependent);
- Nt—number of tags in the RFID reader vicinity.
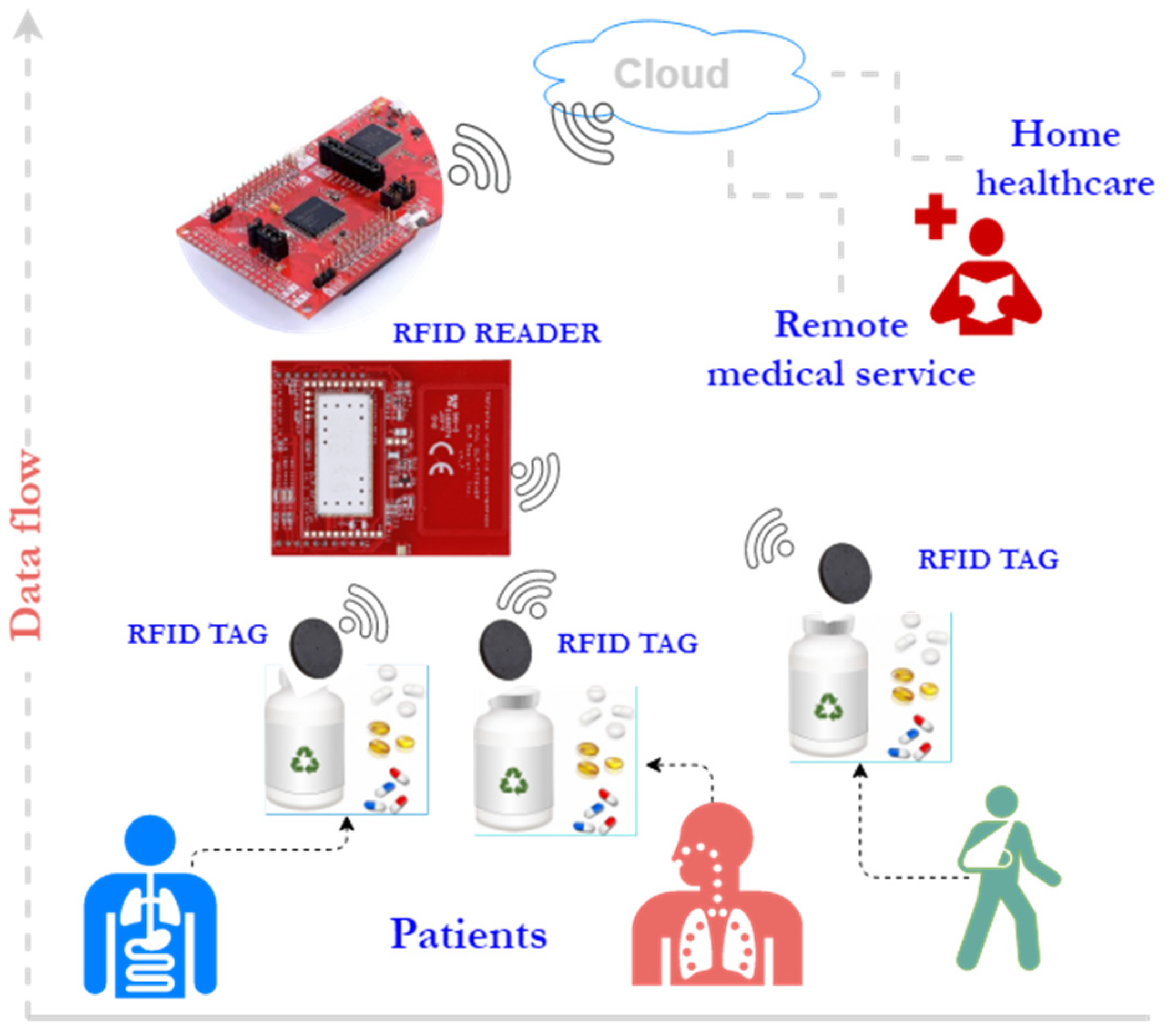
2.4. RFID Object Identification at the Edge—Availability
- modeling the erroneous reception of associated bits with the UID of a tag by Tag_E (tags whose UID was incorrectly received) and Tag_R (tags whose UID was correctly received);
- modeling the operation of RFID tags through Tag_Up and Tag_Down locations;
- modeling the operation of the RFID antenna through the Antenna_Up and Antenna_Down locations;
- modeling the operation of the RFID reader through the Reader_Up and Reader_Down locations;
- modeling the operation of the microcontroller through the Microcontroller_Up and Microcontroller_Down locations;
- modeling the operation of the network card through the Networkcard_Up and Networkcard_Down locations;
- modeling the operation of the router through the Router_Up and Router_Down locations; and
- modeling the operation of the Pepper robot through the Pepper_Up and Pepper_Down locations.
- determining the availability when all the tags are correctly identified, there are no errors in receiving UIDs:
- determining the availability when, at most, one UID code is received erroneously:
- determining the availability when, at most, two UIDs are erroneous:
- Pepper, multiple (Wi-Fi + RFID reader) modules scenario in which the Pepper robot communicates with multiple Wi-Fi + RFID reader modules (Figure 12). Each module is responsible for monitoring the RFID tags.
- Pepper, Wi-Fi, multiple RFID reader: In this scenario, there was a single microcontroller with Wi-Fi capabilities that acted as an intermediate point between the Pepper robot and RFID readers (Figure 13). The microcontroller stored the UID of each tag found near the RFID readers.
- Scenario I: Nt tags are in the system;
- Scenario II: Nt tags are in the system, the first pair of Wi-Fi + RFID reader deals with Nt/2 tags, and the other half is read by the second pair of Wi-Fi + RFID reader;
- Scenario III: Nt tags are in the system; the first RFID reader deals with Nt/2 tags, the other half is read by the second RFID reader.
- determining the availability when all tags are correctly identified, there are no errors in receiving UIDs:
- determining the availability when one UID code at most is received erroneously:
- determining the availability when two UIDs at most are erroneous:
3. Results
3.1. RFID Tag Detection as a Function of Cost
- confidence level of 95%;
- maximal relative error of 3%;
- batch size of 10,000;
3.2. RFID Object-Detection System Availability
- 11 events in which, out of four tags, only three were read;
- Three events required resetting the system, and there were problems in transmitting messages that led to the system being blocked;
- Three events occurred in which the sockets were not closed correctly, resulting in the loss of messages with the server.
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Costa, F.; Genovesi, S.; Borgese, M.; Michel, A.; Dicandia, F.A.; Manara, G. A Review of RFID Sensors, the New Frontier of Internet of Things. Sensors 2021, 21, 3138. [Google Scholar] [CrossRef]
- Li, C.Z.; Zhong, R.Y.; Xue, F.; Xu, G.; Chen, K.; Huang, G.G.; Shen, G.Q. Integrating RFID and BIM Technologies for Mitigating Risks and Improving Schedule Performance of Prefabricated House Construction. J. Clean. Prod. 2017, 165, 1048–1062. [Google Scholar] [CrossRef]
- Luvisi, A.; Lorenzini, G. RFID-Plants in the Smart City: Applications and Outlook for Urban Green Management. Urban For. Urban Green 2014, 13, 630–637. [Google Scholar] [CrossRef]
- Ji, Y.; Xu, Z.; Feng, Q.; Sang, Y. Concurrent Collision Probability of RFID Tags in Underground Mine Personnel Position Systems. Min. Sci. Technol. China 2010, 20, 734–737. [Google Scholar] [CrossRef]
- Chanchaichujit, J.; Balasubramanian, S.; Charmaine, N.S.M. A Systematic Literature Review on the Benefit-Drivers of RFID Implementation in Supply Chains and Its Impact on Organizational Competitive Advantage. Cogent Bus. Manag. 2020, 7, 1–20. [Google Scholar] [CrossRef]
- Smith, A.D. RFID Applications in Healthcare Systems From an Operational Perspective. Int. J. Syst. Soc. IJSS 2019, 6, 1–28. [Google Scholar] [CrossRef]
- Kim Geok, T.; Zar Aung, K.; Sandar Aung, M.; Thu Soe, M.; Abdaziz, A.; Pao Liew, C.; Hossain, F.; Tso, C.P.; Yong, W.H. Review of Indoor Positioning: Radio Wave Technology. Appl. Sci. 2021, 11, 279. [Google Scholar] [CrossRef]
- Michalski, A.; Watral, Z. Problems of Powering End Devices in Wireless Networks of the Internet of Things. Energies 2021, 14, 2417. [Google Scholar] [CrossRef]
- Khalid, N.; Mirzavand, R.; Iyer, A.K. A Survey on Battery-Less RFID-Based Wireless Sensors. Micromachines 2021, 12, 819. [Google Scholar] [CrossRef]
- Yusoff, Z.Y.M.; Ishak, M.K.; Alezabi, K.A. The Role of RFID in Green IoT: A Survey on Technologies, Challenges and a Way Forward. Adv. Sci. Technol. Eng. Syst. J. 2021, 6, 17–35. [Google Scholar] [CrossRef]
- Javed, N.; Azam, M.A.; Qazi, I.; Amin, Y.; Tenhunen, H. A Novel Multi-Parameter Chipless RFID Sensor for Green Networks. AEU-Int. J. Electron. Commun. 2021, 128, 153512. [Google Scholar] [CrossRef]
- Campioni, F.; Choudhury, S.; Al- Turjman, F. Scheduling RFID Networks in the IoT and Smart Health Era. J. Ambient Intell. Humaniz. Comput. 2019, 10, 4043–4057. [Google Scholar] [CrossRef]
- Munoz-Ausecha, C.; Ruiz-Rosero, J.; Ramirez-Gonzalez, G. RFID Applications and Security Review. Computation 2021, 9, 69. [Google Scholar] [CrossRef]
- Pal, K. RFID Tag Collision Problem in Supply Chain Management. Int. J. Adv. Pervasive Ubiquitous Comput. 2019, 11, 1–12. [Google Scholar] [CrossRef]
- Hasanuzzaman, F.M.; Yang, X.; Tian, Y.; Liu, Q.; Capezuti, E. Monitoring Activity of Taking Medicine by Incorporating RFID and Video Analysis. Netw. Model. Anal. Health Inform. Bioinforma. 2013, 2, 61–70. [Google Scholar] [CrossRef]
- Choi, J.; Ahn, S. Optimal Service Provisioning for the Scalable Fog/Edge Computing Environment. Sensors 2021, 21, 1506. [Google Scholar] [CrossRef]
- Rao, S. Implementation of the ISO15693 Protocol in the TI TRF796x 2009. 2009. Available online: https://www.ti.com/lit/an/sloa138/sloa138.pdf?ts=1631842962864&ref_url=https%253A%252F%252Fwww.google.com%252F (accessed on 13 August 2021).
- Qu, Z.; Sun, X.; Chen, X.; Yuan, S. A Novel RFID Multi-Tag Anti-Collision Protocol for Dynamic Vehicle Identification. PLoS ONE 2019, 14, e0219344. [Google Scholar] [CrossRef] [PubMed]
- Alma’aitah, A.; Hassanein, H.S.; Ibnkahla, M. Tag Modulation Silencing: Design and Application in RFID Anti-Collision Protocols. IEEE Trans. Commun. 2014, 62, 4068–4079. [Google Scholar] [CrossRef]
- Cha, J.-R.; Kim, J.-H. Novel Anti-Collision Algorithms for Fast Object Identification in RFID System. In Proceedings of the 11th International Conference on Parallel and Distributed Systems (ICPADS’05), Fukuoka, Japan, 20–22 July 2005; Volume 2, pp. 63–67. [Google Scholar]
- Birari, S.M.; Iyer, S. Mitigating the Reader Collision Problem in RFID Networks with Mobile Readers. In Proceedings of the 2005 13th IEEE International Conference on Networks Jointly Held with the 2005 IEEE 7th Malaysia International Conf on Communic, Kuala Lumpur, Malaysia, 16–18 November 2005; Volume 1, p. 6. [Google Scholar]
- Corches, C.; Donca, I.C.; Stan, O.; Miclea, L.; Daraban, M. Analyzing the RFID Failure Impact on Availability of IoT Services. In Proceedings of the 2020 IEEE 26th International Symposium for Design and Technology in Electronic Packaging (SIITME), Pitesti, Románia, 21–24 October 2020; pp. 163–168. [Google Scholar]
- O’Connor, P.P.; Kleyner, A. Practical Reliability Engineering, 5th ed.; Wiley Publishing: Hoboken, NJ, USA, 2012; ISBN 978-0-470-97981-5. [Google Scholar]
- Silva, B.; Matos, R.; Callou, G.; Figueiredo, J.; Oliveira, D.; Ferreira, J.; Dantas, J.; Lobo, A.; Alves, V.; Maciel, P. Mercury: An Integrated Environment for Performance and Dependability Evaluation of General Systems. In Proceedings of the 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN 2015), Rio de Janeiro, Brazil, 1 January 2015. [Google Scholar]
- Lira, V.; Tavares, E.; Fernandes, S.; Maciel, P.; Silva, R.M.A. Virtual Network Resource Allocation Considering Dependability Issues. In Proceedings of the 2013 IEEE 16th International Conference on Computational Science and Engineering, Sydney, Australia, 3–5 December 2013; pp. 330–337. [Google Scholar]
- Cmiljanic, N.; Landaluce, H.; Perallos, A. A Comparison of RFID Anti-Collision Protocols for Tag Identification. Appl. Sci. 2018, 8, 1282. [Google Scholar] [CrossRef] [Green Version]
- Khadka, G.; Hwang, S.-S. Tag-to-Tag Interference Suppression Technique Based on Time Division for RFID. Sensors 2017, 17, 78. [Google Scholar] [CrossRef] [Green Version]
- Park, J.; Chung, M.Y.; Lee, T. Identification of RFID Tags in Framed-Slotted ALOHA with Robust Estimation and Binary Selection. IEEE Commun. Lett. 2007, 11, 452–454. [Google Scholar] [CrossRef]
- Marsan, M.A.; Balbo, G.; Conte, G.; Donatelli, S.; Franceschinis, G. Modelling with Generalized Stochastic Petri Nets, 1st ed.; John Wiley & Sons, Inc.: Hoboken, NJ, USA, 1994; ISBN 978-0-471-93059-4. [Google Scholar]
- Su, W.; Beilke, K.M.; Ha, T.T. A Reliability Study of RFID Technology in a Fading Channel. In Proceedings of the 2007 Conference Record of the Forty-First Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 4–7 November 2007; pp. 2124–2127. [Google Scholar]
- Goulbourne, J.A. TRF7960 Evaluation Module ISO15693 Host Commands 2008. 2008. Available online: https://docplayer.net/13303499-Trf7960-evaluation-module-iso-15693-host-commands.html (accessed on 13 August 2021).
- Texas Instruments RI-I17-112A-03 Tag-ItTM HF-I Plus Transponder Inlays 2014. 2014. Available online: https://www.ti.com/lit/ds/scbs827b/scbs827b.pdf (accessed on 13 August 2021).

















| Slot Type | Probability of Occurrence | |
|---|---|---|
| One tag per slot | 20.5993652% | |
| Idle slot | 77.2476196% | |
| Slot with collision | 2.1530151% | |
| Slot with 2-tag collision | 2.0599365% | |
| Slot with 3-tag collision | 0.0915527% | |
| Slot with 4-tag collision | 0.0015259% |
| No. of Tags | Scenario 1 | Scenario 2 | Scenario 3 | ||||||
|---|---|---|---|---|---|---|---|---|---|
| No Errors | One Erroneous Tag | Two Erroneous Tags | No Errors | One Erroneous Tag | Two Erroneous Tags | No Errors | One Erroneous Tag | Two Erroneous Tags | |
| 2 | 87.9900% | 99.6062% | N/A | 87.9569% | 99.6212% | N/A | 88.0242% | 99.6423% | N/A |
| 4 | 77.5855% | 97.9709% | 99.9000% | 77.3842% | 97.8143% | 99.8960% | 77.1889% | 97.8651% | 99.8988% |
| 6 | 68.1615% | 95.1877% | 99.5746% | 68.0436% | 94.9642% | 99.5199% | 67.9565% | 95.1738% | 99.5216% |
| 8 | 60.5690% | 91.8783% | 98.8528% | 59.8911% | 91.3952% | 98.9691% | 59.7986% | 91.5098% | 98.9798% |
| 10 | 52.3894% | 87.4789% | 97.7052% | 52.3087% | 87.3695% | 97.9219% | 52.9554% | 87.6973% | 97.9450% |
| 12 | 45.7768% | 82.9385% | 96.4815% | 46.3120% | 83.2289% | 96.5695% | 46.3120% | 83.2031% | 96.5885% |
| 14 | 41.0236% | 78.6182% | 95.0974% | 40.8684% | 78.5720% | 94.8635% | 40.7682% | 78.5771% | 94.9531% |
| 16 | 35.5921% | 73.6819% | 92.5009% | 36.1016% | 73.6395% | 92.6258% | 35.7017% | 73.6912% | 92.5994% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Corches, C.; Daraban, M.; Miclea, L. Availability of an RFID Object-Identification System in IoT Environments. Sensors 2021, 21, 6220. https://doi.org/10.3390/s21186220
Corches C, Daraban M, Miclea L. Availability of an RFID Object-Identification System in IoT Environments. Sensors. 2021; 21(18):6220. https://doi.org/10.3390/s21186220
Chicago/Turabian StyleCorches, Cosmina, Mihai Daraban, and Liviu Miclea. 2021. "Availability of an RFID Object-Identification System in IoT Environments" Sensors 21, no. 18: 6220. https://doi.org/10.3390/s21186220
APA StyleCorches, C., Daraban, M., & Miclea, L. (2021). Availability of an RFID Object-Identification System in IoT Environments. Sensors, 21(18), 6220. https://doi.org/10.3390/s21186220








