Towards a Machine Learning Based Situational Awareness Framework for Cybersecurity: An SDN Implementation
Abstract
:1. Introduction
2. State of the Art
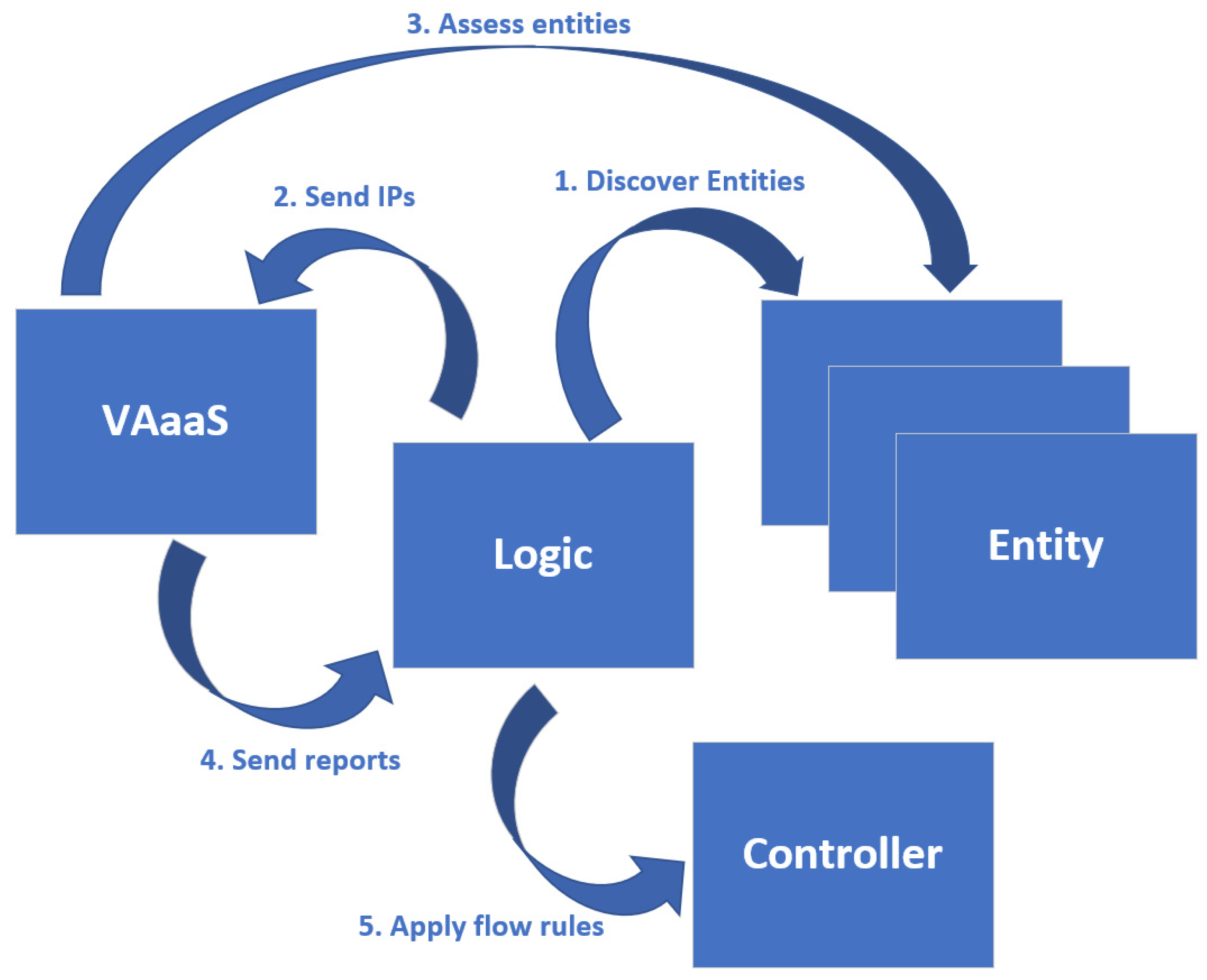
- Discover existing and newly introduced network-enabled entities in real-time by utilizing the SDN paradigm.
- Performs vulnerability assessment on discovered network-enabled entities using a Vulnerability Assessment as a Service (VAaaS) component.
- Assigns the assessed entities to a connectivity-appropriate network slice through an SDN controller application, depending on their risk level (vulnerability assessment).
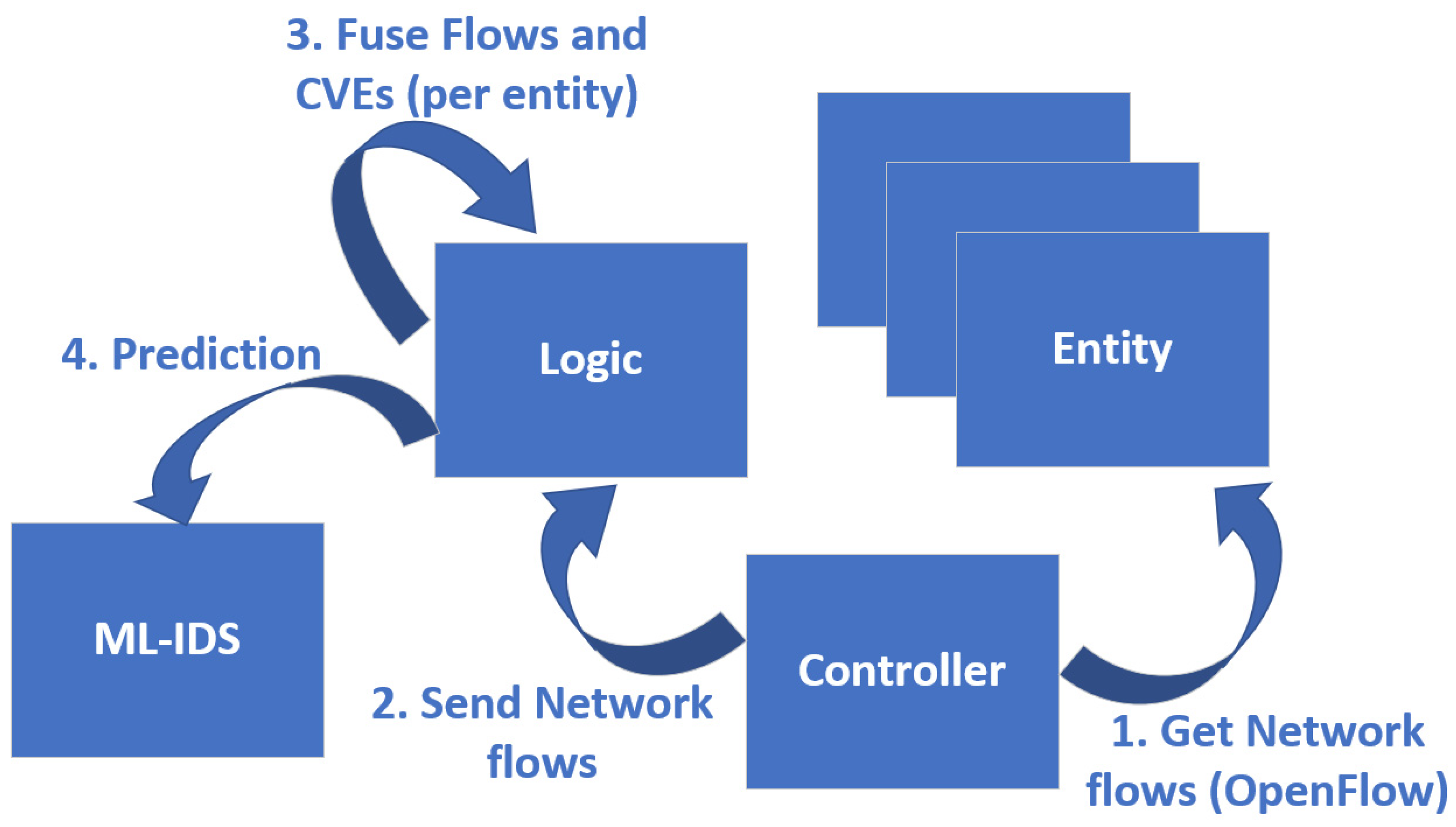
- Leverages an enhanced dataset, which combines heterogeneous data to train an ML-based IDS, thus achieving more fine-grained classification, and therefore more robust training results.
- Produce intrusion detection predictions, by utilizing real-time data (Netflow data and system vulnerabilities—CVEs).
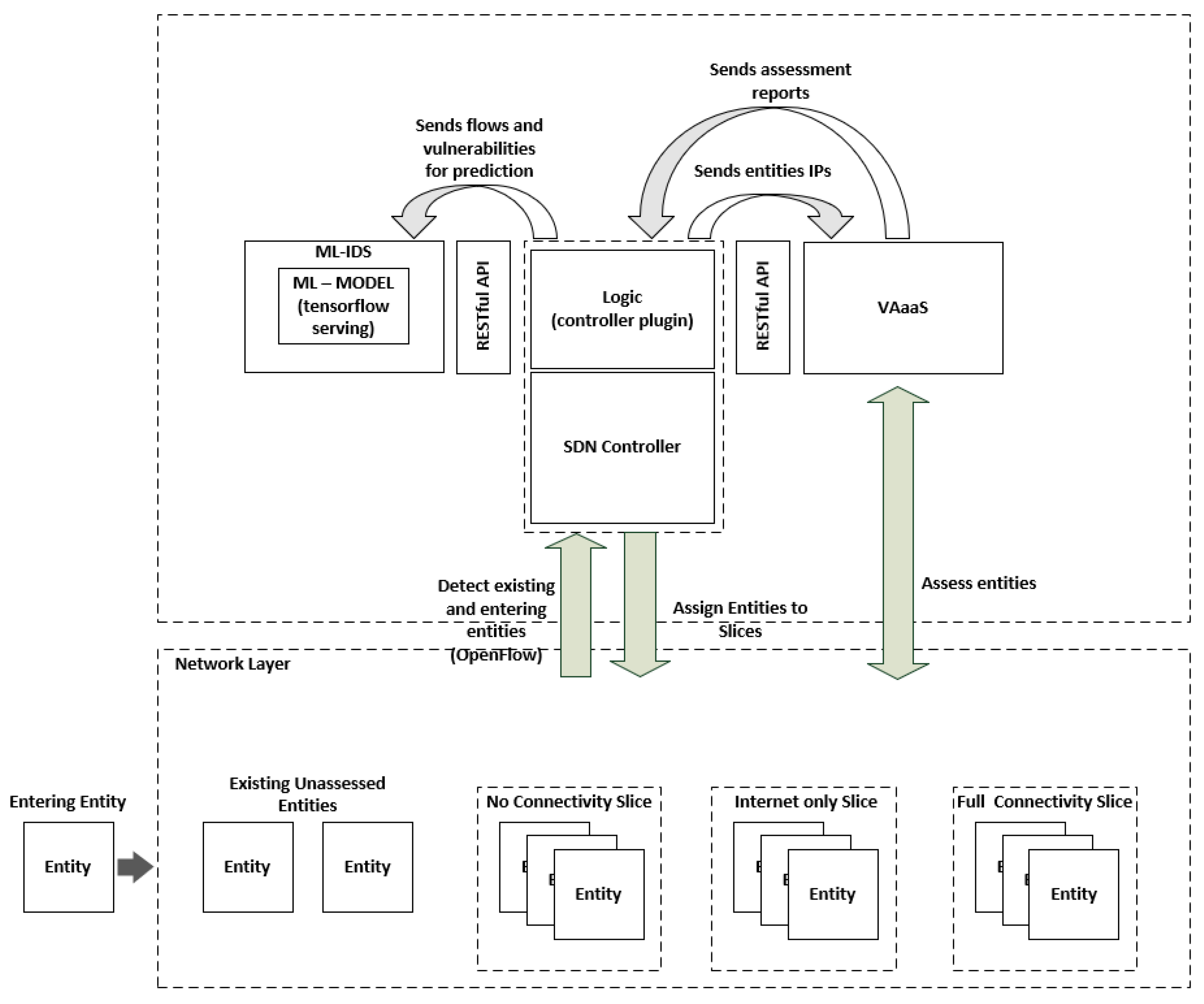
3. System Architecture
3.1. Logic Component
3.2. Vulnerability Assessment as a Service (VAaaS) Component
3.3. ML-IDS
3.3.1. Dataset
3.3.2. ML-Model
3.4. Use Cases
3.4.1. Identification and Protection Use Case
3.4.2. Detection Use Case
4. Evaluation
4.1. Aim
4.2. Method
4.3. Variables
4.3.1. Dependent
4.3.2. Independent
4.3.3. Fixed
4.4. Prediction
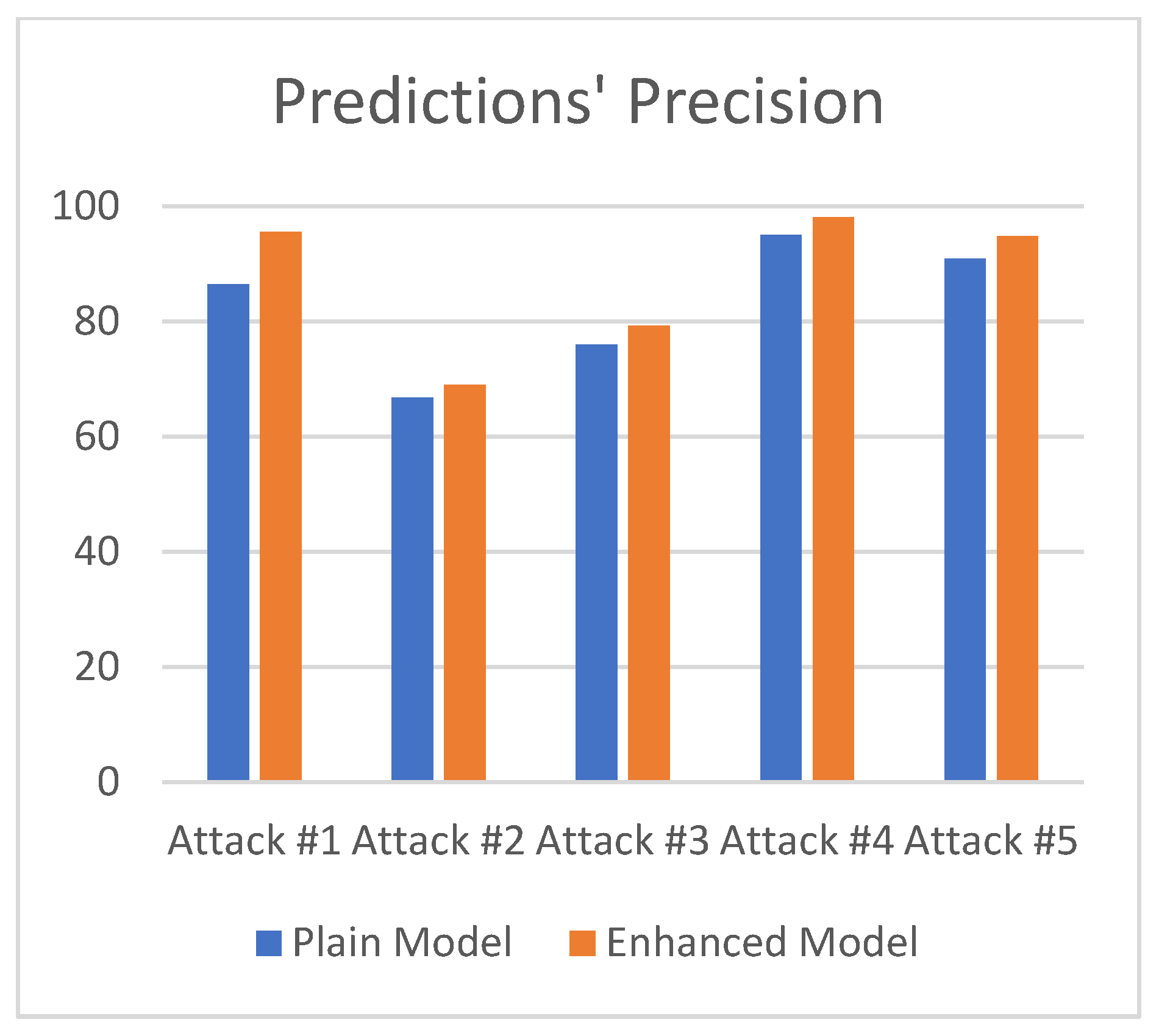
4.5. Results
4.6. Discussion
4.7. Evaluation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- ENISA Threat Landscape 2020—Data Breach. Available online: https://www.enisa.europa.eu/publications/enisa-threat-landscape-2020-data-breach (accessed on 16 July 2021).
- ENISA Threat Landscape 2020—Information Leakage. Available online: https://www.enisa.europa.eu/publications/information-leakage (accessed on 16 July 2021).
- Staffa, M.; Sgaglione, L.; Mazzeo, G.; Coppolino, L.; D’Antonio, S.; Romano, L.; Gelenbe, E.; Stan, O.; Carpov, S.; Grivas, E.; et al. An openNCP-based solution for secure ehealth data exchange. J. Netw. Comput. Appl. 2018, 116, 65–85. [Google Scholar] [CrossRef]
- Spanos, G.; Giannoutakis, K.M.; Votis, K.; Viano, B.; Augusto-Gonzalez, J.; Aivatoglou, G.; Tzovaras, D. A Lightweight Cyber-Security Defense Framework for Smart Homes. In Proceedings of the 2020 International Conference on INnovations in Intelligent SysTems and Applications (INISTA), Novi Sad, Serbia, 24–26 August 2020; p. 120137. [Google Scholar]
- Markakis, E.; Nikoloudakis, Y.; Mastorakis, G.; Mavromoustakis, C.X.; Pallis, E.; Sideris, A.; Zotos, N.; Antic, J.; Cernivec, A.; Fejzic, D.; et al. Acceleration at the edge for supporting smes security: The FORTIKA paradigm. IEEE Commun. Mag. 2019, 57, 41–47. [Google Scholar] [CrossRef]
- Sutton, R.; Ludwiniak, R.; Pitropakis, N.; Chrysoulas, N.; Dagiuklas, T. Towards an SDN Assisted IDS. In Proceedings of the 2021 11th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 19–21 April 2021. [Google Scholar]
- Endsley, M.R. Toward a theory of situation awareness in dynamic systems. Hum. Factors 1995, 37, 32–64. [Google Scholar] [CrossRef]
- Bass, T. Multisensor Data Fusion for Next Generation Distributed Intrusion Detection Systems. Irish Natl. Symp. 1999, 28, 24–27. [Google Scholar] [CrossRef]
- Bass, T. Intrusion detection systems and multisensor data fusion. Commun. ACM 2000, 43, 99–105. [Google Scholar] [CrossRef]
- Tsolakis, A.; Moschos, I.; Votis, K.; Ioannidis, D.; Dimitrios, T.; Pandey, P.; Katsikas, S.; Kotsakis, E.; Garcia-Castro, R. A secured and trusted demand response system based on blockchain technologies. In Proceedings of the 2018 Innovations in Intelligent Systems and Applications (INISTA), Thessaloniki, Greece, 3–5 July 2018. [Google Scholar]
- Pitropakis, N.; Panaousis, E.; Giannakoulias, A.; Kalpakis, G.; Rodriguez, R.D.; Sarigiannidis, P. An Enhanced Cyber Attack Attribution Framework. In International Conference on Trust and Privacy in Digital Business; Springer: Cham, Switzerland, 2018; pp. 213–228. [Google Scholar]
- Markakis, E.; Nikoloudakis, Y.; Pallis, E.; Manso, M. Security assessment as a service cross-layered system for the adoption of digital, personalised and trusted healthcare. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 91–94. [Google Scholar]
- First.org. CVSS V3.1. Available online: https://www.first.org/cvss/ (accessed on 16 July 2021).
- NIST. Cybersecurity Framework. Available online: https://www.nist.gov/news-events/news/2018/04/nist-releases-version-11-its-popular-cybersecurity-framework (accessed on 13 February 2021).
- Lee, S.; Yoon, C.; Lee, C.; Shin, S.; Yegneswaran, V.; Porras, P. DELTA: A security assessment framework for software-defined networks. In Proceedings of the 2014 Network and Distributed System Security Symposium 2017, San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Nikoloudakis, Y.; Pallis, E.; Mastorakis, G.; Mavromoustakis, C.X.; Skianis, C.; Markakis, E.K. Vulnerability assessment as a service for fog-centric ICT ecosystems: A healthcare use case. Peer Peer Netw. Appl. 2019, 12, 1216–1224. [Google Scholar] [CrossRef]
- Loi, F.; Sivanathan, A.; Gharakheili, H.H.; Radford, A.; Sivaraman, V. Systematically evaluating security and privacy for consumer iot devices. In Proceedings of the 2017 Workshop on Computing Within Limits 2017, Santa Barbara, CA, USA, 22–24 June 2017; Volume 1, pp. 1–6. [Google Scholar]
- Tchao, E.T.; Ansah, R.Y.; Djane, S.D. Barrier free internet access: Evaluating the cyber security risk posed by the adoption of bring your own devices to e-learning network infrastructure. Int. J. Comput. Appl. 2017, 176, 53–62. [Google Scholar]
- Miettinen, M.; Marchal, S.; Hafeez, I.; Frassetto, T.; Asokan, N.; Sadeghi, A.-R.; Tarkoma, S. IoT sentinel demo: Automated device-type identification for security enforcement in IoT. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2511–2514. [Google Scholar]
- Li, H.; Wei, F.; Hu, H. Enabling dynamic network access control with anomaly-based IDS and SDN. In Proceedings of the 2019 ACM International Workshop on Security in Software Defined Networks & Network Function Virtualization—SDN-NFVSec ’19, Richardson, TX, USA, 27 March 2019; pp. 13–16. [Google Scholar]
- Liu, X.-W.; Wang, H.-Q.; Liang, Y.; Lai, J.-B. Heterogeneous multi-sensor data fusion with multi-class support vector machines: Creating network security situation awareness. In Proceedings of the 2007 International Conference on Machine Learning and Cybernetics, Hong Kong, China, 19–22 August 2007; pp. 2689–2694. [Google Scholar]
- Liu, X.; Wang, H.; Lai, J.; Liang, Y.; Yang, C. Multiclass support vector machines theory and its data fusion application in network security situation awareness. In Proceedings of the 2007 International Conference on Wireless Communications, Networking and Mobile Computing, Shanghai, China, 21–25 September 2007; pp. 6343–6346. [Google Scholar]
- Thaseen, S.; Kumar, C.A. An analysis of supervised tree based classifiers for intrusion detection system. In Proceedings of the 2013 International Conference on Pattern Recognition, Informatics and Mobile Engineering, Salem, India, 21–22 February 2013; pp. 294–299. [Google Scholar]
- Zhang, H.; Yu, X.; Ren, P.; Luo, C.; Min, G. Deep adversarial learning in intrusion detection: A data augmentation enhanced framework. arXiv 2019, arXiv:1901.07949. [Google Scholar]
- Srivastava, S.K.; Sharma, Y.K.; Kumar, S. Characteristics categorization dataset KDD Cup’99. AIP Conf. Proc. 2019, 2142, 110034. [Google Scholar] [CrossRef]
- Mathews, M.; Halvorsen, P.; Joshi, A.; Finin, T. A collaborative approach to situational awareness for cybersecurity. In Proceedings of the 8th International Conference on Collaborative Computing: Networking, Applications and Worksharing 2012, Pittsburgh, PA, USA, 14–17 October 2012; pp. 216–222. [Google Scholar]
- Zhang, Y.; Zhang, J.; Zhang, B. Visual analysis of cybersecurity situational awareness. In Proceedings of the 2019 IEEE 10th International Conference on Software Engineering and Service Science (ICSESS), Beijing, China, 18–20 October 2019; pp. 685–688. [Google Scholar]
- Park, H.K.; Kim, M.S.; Park, M.; Lee, K. Cyber situational awareness enhancement with regular expressions and an evaluation methodology. In Proceedings of the MILCOM 2017–2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 23–25 October 2017; pp. 406–411. [Google Scholar]
- Doynikova, E.; Kotenko, I. CVSS-based probabilistic risk assessment for cyber situational awareness and countermeasure selection. In Proceedings of the 2017 25th Euromicro International Conference on Parallel, Distributed and Network-based Processing (PDP), St. Petersburg, Russia, 6–8 March 2017; pp. 346–353. [Google Scholar]
- Wang, H.; Chen, Z.; Feng, X.; Di, X.; Liu, D.; Zhao, J.; Sui, X. Research on network security situation assessment and quantification method based on analytic hierarchy process. Wirel. Pers. Commun. 2018, 102, 1401–1420. [Google Scholar] [CrossRef]
- Saaty, T.L. What is the analytic hierarchy process? In Mathematical Models for Decision Support; Springer: Berlin/Heidelberg, Germany, 1988; Volume 15, pp. 109–121. [Google Scholar]
- Saaty, T.L. Decision making with the analytic hierarchy process. Int. J. Serv. Sci. 2008, 1, 83. [Google Scholar] [CrossRef] [Green Version]
- Zadeh, L.A. Simple view of the dempster-shafer theory of evidence and its implication for the rule of combination. AI Mag. 1986, 7, 85–90. [Google Scholar]
- Irsik, T.; Celeda, P. Cyber situation awareness via IP flow monitoring. In Proceedings of the NOMS 2020—2020 IEEE/IFIP Network Operations and Management Symposium, Budapest, Hungary, 20–24 April 2020; pp. 1–6. [Google Scholar]
- Jirsik, T.; Celeda, P. Toward real-time network-wide cyber situational awareness. In Proceedings of the NOMS 2018—2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018; pp. 1–7. [Google Scholar]
- Specification of the IP Flow Information Export (IPFIX) Protocol for the Exchange of Flow Information. Available online: http://www.ietf.org/rfc/rfc7011.txt (accessed on 16 July 2021).
- NIST’s Cybersecurity Lifecycle. Available online: https://www.nist.gov/cyberframework/online-learning/five-functions (accessed on 16 July 2021).
- Common Vulnerability Scoring System version 3.1: Specification Document. Available online: https://www.first.org/cvss/specification-document (accessed on 16 July 2021).
- CVSS v3.0 Calculator. Available online: https://www.first.org/cvss/calculator/3.0 (accessed on 16 July 2021).
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. In Proceedings of the ICISSP 2018, Madeira, Portugal, 22–24 January 2018; pp. 108–116. [Google Scholar]
- Brownlee, J. Better deep learning: Train faster, reduce overfitting, and make better predictions. In Machine Learning Mastery; Packt: Birmingham, UK; O’Reilly: Sebastopol, CA, USA, 2018. [Google Scholar]
- Brownlee, J. Master machine learning algorithms: Discover How They Work and Implement Them from Scratch. In Machine Learning Mastery; Packt: Birmingham, UK; O’Reilly: Sebastopol, CA, USA, 2018. [Google Scholar]
- Brownlee, J. Supervised and unsupervised machine learning algorithms. In Machine Learning Mastery; Packt: Birmingham, UK; O’Reilly: Sebastopol, CA, USA, 2018. [Google Scholar]
- Brownlee, J. Deep learning with python: Develop deep learning models on theano and tensorflow using keras. In Machine Learning Mastery; Packt: Birmingham, UK; O’Reilly: Sebastopol, CA, USA, 2018. [Google Scholar]
- TensorFlow Serving Models. Available online: https://www.tensorflow.org/tfx/guide/serving (accessed on 16 July 2021).
- CVE-2014-3120. Available online: https://nvd.nist.gov/vuln/detail/CVE-2014-3120 (accessed on 16 July 2021).
- CVE-2015-8249. Available online: https://nvd.nist.gov/vuln/detail/CVE-2015-8249 (accessed on 16 July 2021).
- CVE-2016-1209. Available online: https://nvd.nist.gov/vuln/detail/CVE-2016-1209 (accessed on 16 July 2021).
- CVE-2001-0553. Available online: https://nvd.nist.gov/vuln/detail/CVE-2001-0553 (accessed on 16 July 2021).
- CVE-2007-6750. Available online: https://nvd.nist.gov/vuln/detail/CVE-2007-6750 (accessed on 16 July 2021).
| Attack | Attack Number |
|---|---|
| Remote File Inclusion (RFI) attack | Attack #1 |
| ManageEngine Desktop Central 9-specific RFI attack | Attack #2 |
| WordPress-specific RFI attack | Attack #3 |
| SSH Brute-Force attack | Attack #4 |
| Slow Loris DoS attack | Attack #5 |
| Precision | Attack #1 | Attack #2 | Attack #3 | Attack #4 | Attack #5 | Standard Deviation | Mean |
|---|---|---|---|---|---|---|---|
| Plain model | 86.42 | 66.80 | 75.92 | 95.01 | 90.86 | 10.29 | 83.00 |
| Enhanced Model | 95.55 | 68.96 | 79.19 | 98.06 | 94.82 | 11.33 | 87.32 |
| Delta | 9.13 | 2.15 | 3.27 | 3.05 | 3.96 | 1.04 | 4.31 |
| True/Predicted | Elastic | Manage Engine | Wordpress | SSH | Slowloris |
|---|---|---|---|---|---|
| Elastic | 387 | 0 | 0 | 0 | 18 |
| ManageEngine | 0 | 164 | 0 | 0 | 20 |
| Wordpress | 0 | 0 | 288 | 34 | 0 |
| SSH | 0 | 0 | 4 | 1819 | 10 |
| Slowloris | 18 | 74 | 72 | 2 | 877 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nikoloudakis, Y.; Kefaloukos, I.; Klados, S.; Panagiotakis, S.; Pallis, E.; Skianis, C.; Markakis, E.K. Towards a Machine Learning Based Situational Awareness Framework for Cybersecurity: An SDN Implementation. Sensors 2021, 21, 4939. https://doi.org/10.3390/s21144939
Nikoloudakis Y, Kefaloukos I, Klados S, Panagiotakis S, Pallis E, Skianis C, Markakis EK. Towards a Machine Learning Based Situational Awareness Framework for Cybersecurity: An SDN Implementation. Sensors. 2021; 21(14):4939. https://doi.org/10.3390/s21144939
Chicago/Turabian StyleNikoloudakis, Yannis, Ioannis Kefaloukos, Stylianos Klados, Spyros Panagiotakis, Evangelos Pallis, Charalabos Skianis, and Evangelos K. Markakis. 2021. "Towards a Machine Learning Based Situational Awareness Framework for Cybersecurity: An SDN Implementation" Sensors 21, no. 14: 4939. https://doi.org/10.3390/s21144939
APA StyleNikoloudakis, Y., Kefaloukos, I., Klados, S., Panagiotakis, S., Pallis, E., Skianis, C., & Markakis, E. K. (2021). Towards a Machine Learning Based Situational Awareness Framework for Cybersecurity: An SDN Implementation. Sensors, 21(14), 4939. https://doi.org/10.3390/s21144939









