PyFF: A Fog-Based Flexible Architecture for Enabling Privacy-by-Design IoT-Based Communal Smart Environments †
Abstract
:1. Introduction
- The PyFF architecture is proposed, which is conceived to transform digital environments while increasing energy efficiency, user comfort and maintaining users’ privacy. This architecture is derived from the analysis of two empirical studies (i.e., Smart Sustainable Coffee Machines and GreenSoul project) that are aimed to study user behaviors towards workplace digitization when it comes to automatizing energy-saving actions.
- A multi-faceted qualitative comparison among the proposed PyFF architecture, GreenSoul and the Smart Sustainable Coffee Machines is presented. This comparison enables practitioners to assess the strengths and weaknesses of these three different IoT paradigms discussed in this work. In addition, these results can be taken as reference guidelines on how to convert a digital workplace into an appropriate setting to involve workers in decision making and motivate them towards more sustainable and healthier behaviors while promoting changes.
2. Enabling the Digitization of User Environments by Means of IoT Architectures
- The Smart Sustainable Coffee Machines use-case [26] consists of instrumenting several capsule-based Coffee Machines in ten different work environments to provide them energy sensing and user-interaction capabilities. This scenario is aimed at measuring the importance of preserving user’s privacy when it comes to collecting sensitive data. The conducted experimental tests have led to a better understanding of the importance of user environment digitization and its side-effects. In fact, over-reliance on automation may bring undesired effects to pro-environmental behavior and reduce personal responsibility for action [27].
- The GreenSoul project use-case [28] consists of deploying IoT interactive artifacts to employees of six tertiary buildings across Europe (Austria, Greece, the UK and Spain) to enhance their awareness about energy consumption. The objective was to understand the new dynamics and discussions that these devices may bring in a communal context when they are deployed from scratch (e.g., the interaction with the device in the daily routine, the attachment or the confidence to the information they provide, emotions related to the IoT devices or their role as mediators of conversations among peers).
2.1. Use-Case 1: Smart Sustainable Coffee Machines
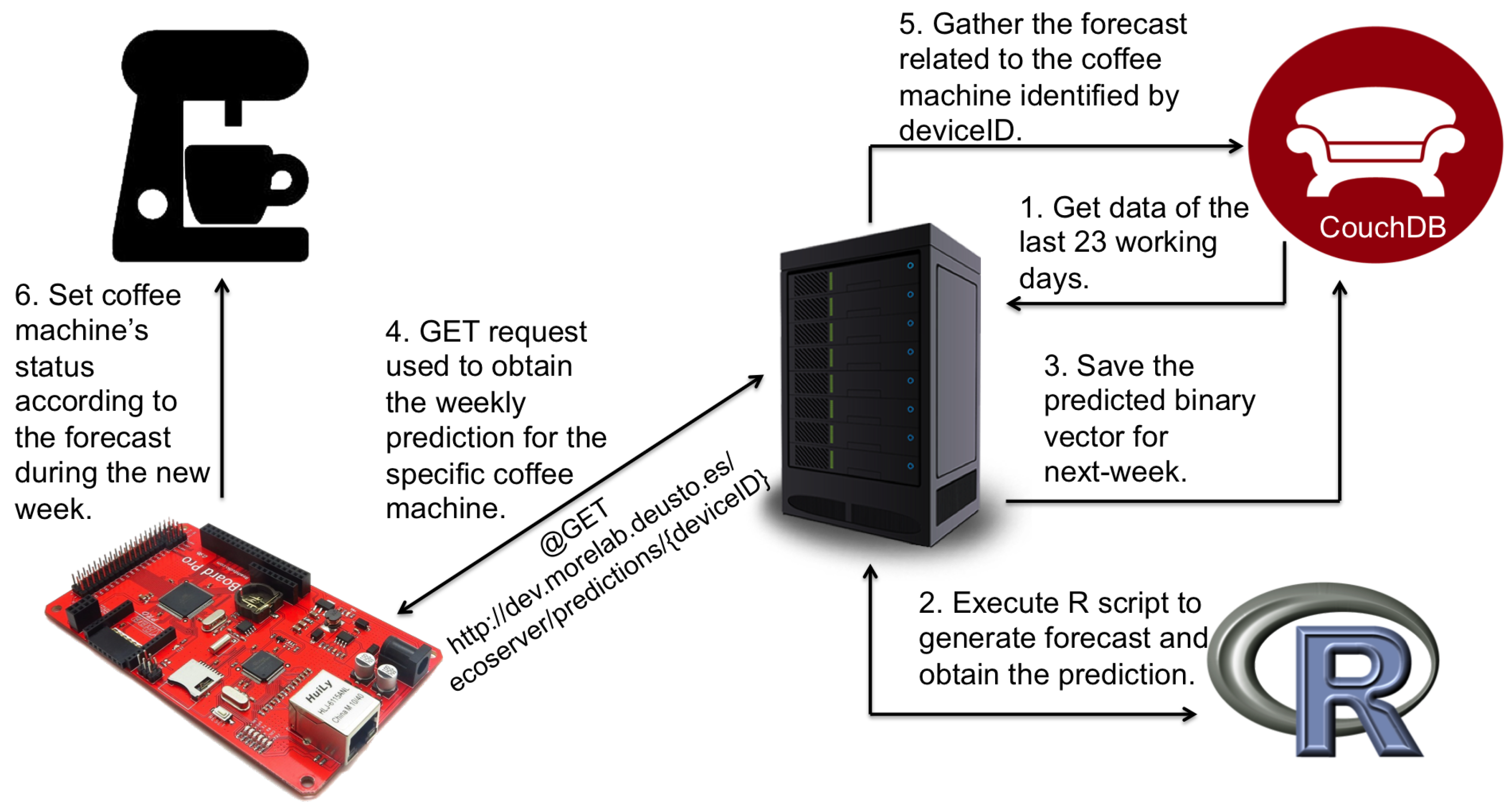
2.1.1. Preparation of the IoT Environment and Experiment Configuration
- Web-based dashboard: In this configuration, a website showing the energy consumption of each user from the coffee machine was developed. This enabled participants to monitor their own consumption and provide rational insights by means of showing historical data.
- Persuasive feedback: This configuration combined subtle visual hints with ambient feedback provided in real-time to persuade the user to decide when the coffee machine should be turned off.
- Automation: This configuration required no intervention from the user. In this way, the coffee machines decided themselves when was the best moment to shut down and did so accordingly. This was aimed at providing a notion of comfort for the users since they did not have to worry about switching the coffee machine off and on to save energy.
2.1.2. Evaluation Procedure and Obtained Results
- Energy Consumption: After running the experiment with the IoT coffee machines, the energy consumption for the Persuasive feedback and Automation experimental conditions dropped by 44% and 14%, respectively. Surprisingly, no energy consumption reduction was observed in the Web-based dashboard experimental condition. Therefore, the following remarks can be inferred. First, it is possible to improve energy consumption of daily appliances. Second, human supervision can mitigate bias in statistical models (i.e., the Persuasive feedback condition saved more energy than the Automation one). Finally, persuasion is key to involving users (i.e., no changes where observed in the Web-based dashboard experimental condition)
- Questionnaires: After analyzing all the questionnaire data, it was found that the users of the Automation experimental condition were the ones who most distrusted the autonomous behavior of the coffee machine and, thus, felt skeptical that technology could be a driver for pro-environmental change. Additionally, after the experiment, this experimental group proved to be less likely to adopt attitudes to favor the environment. These findings are fairly well correlated with the work of Murtagh et al. [27], who found that automation impairs pro-environmental attitudes and undermines actions for personal responsibility. To sum up, the following remark can be inferred from the evidence above: autonomous appliances (e.g., the coffee machine in this use-case) may contribute to reduce the confidence and trust in technology. Therefore, user idiosyncrasy cannot be neglected when implementing automation in an IoT domain.
- Focus Groups: To further capture user feedback on this experiment, a set of focus groups was conducted. From them, the most relevant observation came from the users of the Automation experimental condition. Specifically, they complained about the fact that users were kept out the loop of the coffee machine operation. That is, it was not possible to intervene on the decision process that the coffee machine did to self shutdown. Users reported feelings of frustration when being unable to use the appliance at will—although they were aware that this was done to improve energy consumption.The main lesson learned from this situation is that users need to understand the behavior of an autonomous device in order to ensure a long-term effective coexistence.
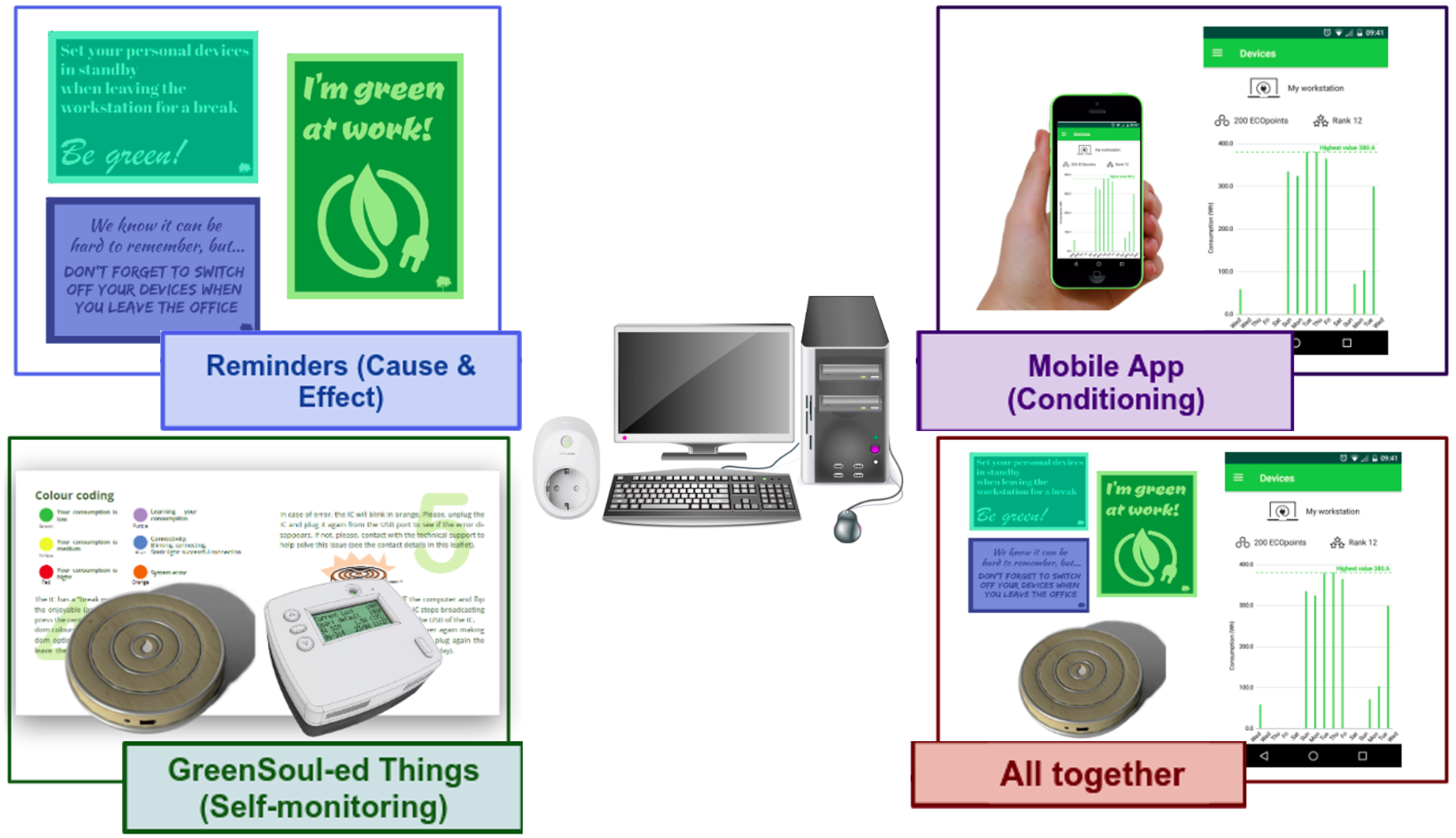
2.2. Use-Case 2: GreenSoul Project
2.2.1. Preparation of the IoT Environment and Experiment Configuration
2.2.2. Evaluation Procedure and Obtained Results
2.3. Architecture Requirements for Enabling a Privacy-by-Design with Human-in-the-Loop IoT Environment
- A fully-automated management system focused on energy efficiency seems to cause passivity among people to act in favor of the environment. In fact, users are not involved in actions which are automatically taken by the systems, and thus can hardly be influenced to adopt a good habit to help to reduce energy consumption.
- The automated system can also generate widespread distrust in the technology since it will discourage humans from taking the lead on their own actions.
- Users are often sensitive to sharing their data, resulting in users’ reluctance if the desired level of privacy is not respected. However, it is of paramount importance to sense as many data and monitor as many devices as possible to provide accurate recommendations (e.g., in health or energy-related scenarios) in order to increase end-users confidence.
- Since involving users to take actions in the smart environment is recommended, it is important to study their profiles in both socioeconomic and behavioral terms. This will help in defining the ICT intervention campaigns to communicate with each one accordingly and promote sustainable practices among users.
- Flexibility: The system must be able to provide different degrees of service at the same time according to the user profile and service to be delivered.
- Privacy: The system must take into account the sensitivity of the data originated in the IoT environment, the service properties and user willingness to expose her/his associated data when exchanging and computing data over the IoT environment. Therefore, service performance shall be reduced, if necessary, to keep the desired privacy level.
- Scalability: The system must provide for an ever-growing number of devices (and users) cohabiting and communicating among each others in the same IoT environment.
- Including humans in the loop: The system must consider user preferences and behavior, which requires a shift from infrastructure-centric to human-centric [23] architectures. Therefore, users are no longer a high-end interface but a critical part on the whole information flow.
- Data governance: The system must provide clear means to define which data will be exchanged, by whom and where they will be processed.
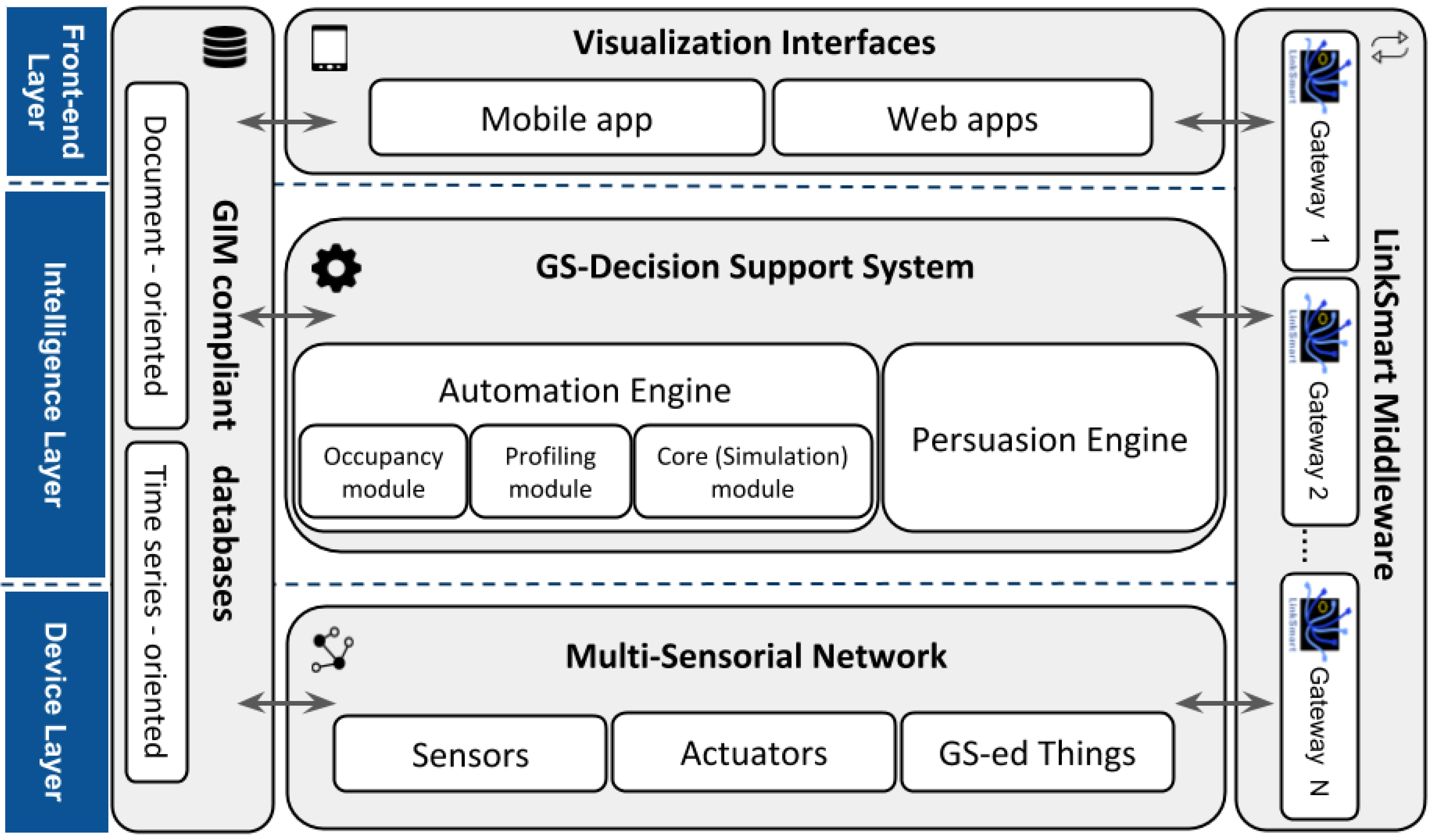
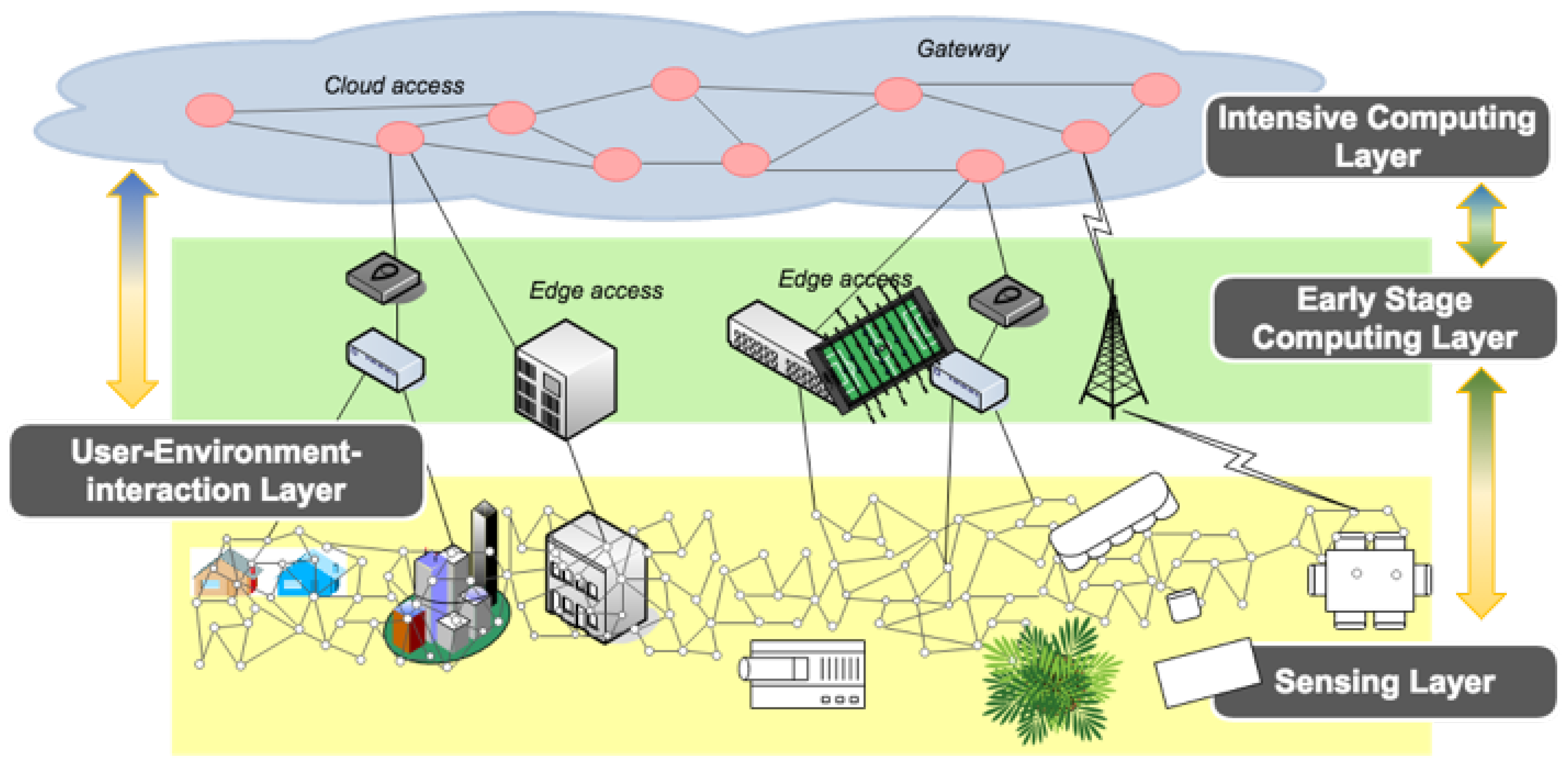
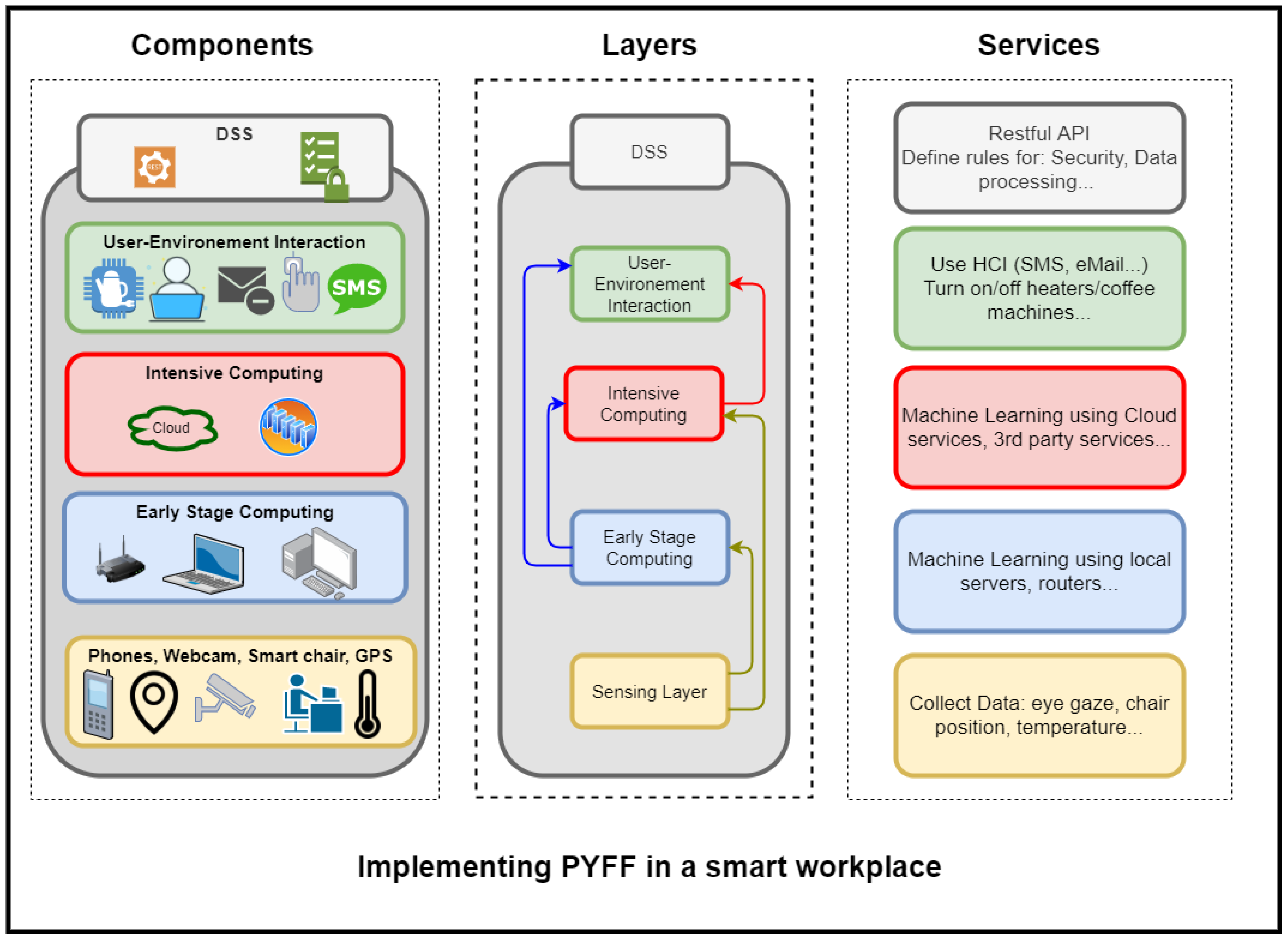
3. PyFF: A Privacy-Fog-Based Flexible Architecture
3.1. PyFF: System Model
3.1.1. Sensing Layer
3.1.2. Early Stage Computing Layer
3.1.3. Intensive Computing and Storage Layer
3.1.4. User–Environment-Interaction Layer
3.1.5. Decision Support System
- Privacy: Where users are enquired regarding their willingness in sharing sensitive data.
- Accuracy: To decide where (i.e, Fog and/or Cloud) the computation (e.g., a recommendation) will take place.
- User involvement: Where the system decides communication channels used to notify users based on their preferences and the multi-modal channels employed to assess how good or bad was the feedback received.
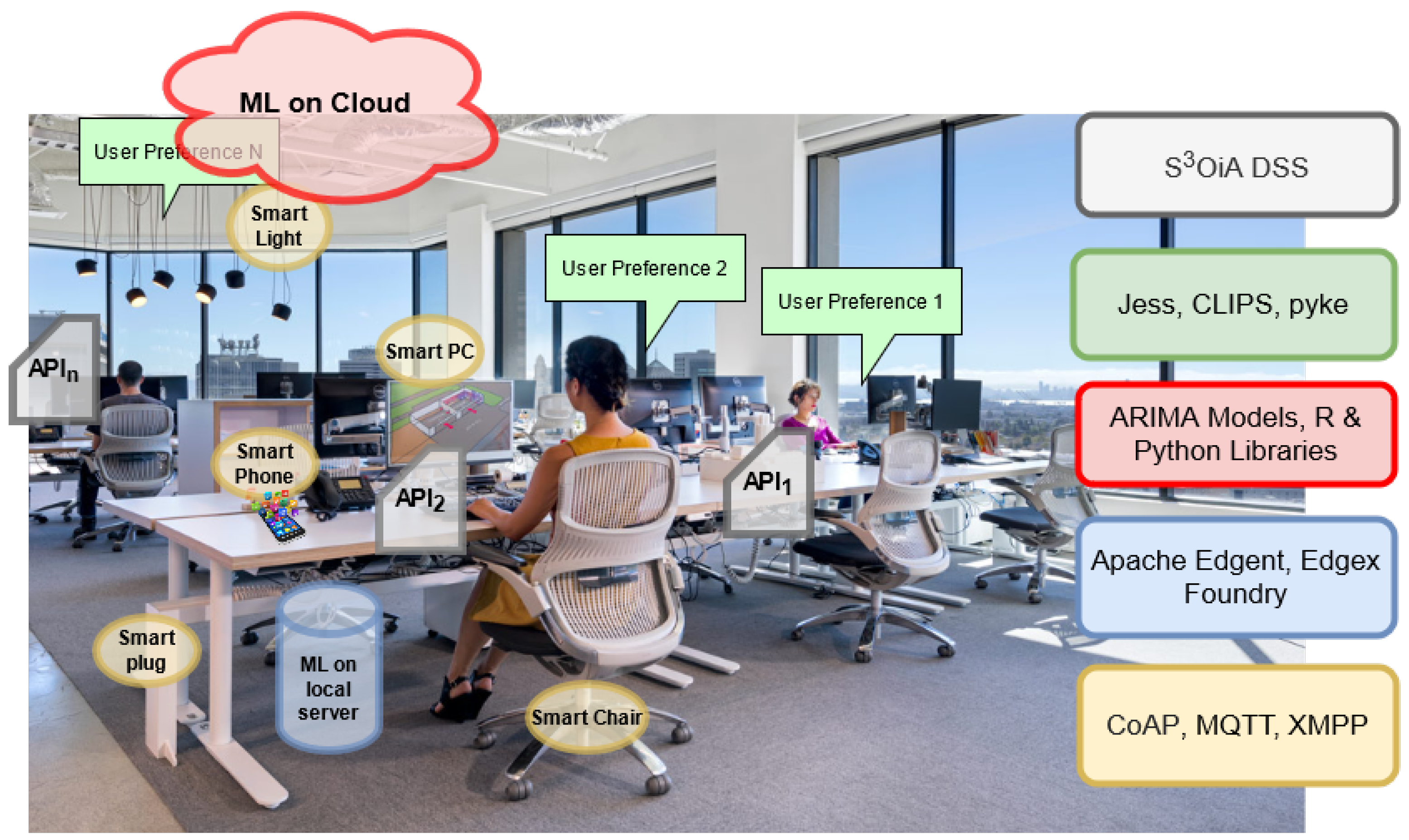
4. Illustrative Example: Smart Workplace
5. Qualitative Evaluation
5.1. Privacy Metrics
5.2. Automation Metrics
5.3. Flexibility Metrics
5.4. Deployment
6. Related Work
7. Conclusions
Author Contributions
Funding
Informed Consent Statement
Conflicts of Interest
References
- Zhu, K.; Dong, S.; Xu, S.X.; Kraemer, K.L. Innovation diffusion in global contexts: Determinants of post-adoption digital transformation of European companies. Eur. J. Inf. Syst. 2006, 15, 601–616. [Google Scholar] [CrossRef]
- Collins, A.; Halverson, R. Rethinking Education in the Age of Technology: The Digital Revolution and Schooling in AMERICA; Teachers College Press: New York, NY, USA, 2018. [Google Scholar]
- Ustundag, A.; Cevikcan, E. Industry 4.0: Managing the Digital Transformation; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar]
- Hars, A. Self-Driving Cars: The Digital Transformation of Mobility. In Marktplàtze im Umbruch: Digitale Strategien fúr Services im Mobilen Internet; Springer: Berlin/Heidelberg, Germany, 2015; pp. 539–549. [Google Scholar] [CrossRef]
- Agarwal, R.; Gao, G.; DesRoches, C.; Jha, A.K. Research commentary—The digital transformation of healthcare: Current status and the road ahead. Inf. Syst. Res. 2010, 21, 796–809. [Google Scholar] [CrossRef] [Green Version]
- Berman, S.J. Digital transformation: Opportunities to create new business models. Strategy Leadersh. 2012, 40, 16–24. [Google Scholar] [CrossRef]
- Majchrzak, A.; Markus, M.L.; Wareham, J. Designing for digital transformation: Lessons for information systems research from the study of ICT and societal challenges. MIS Q. 2016, 40, 267–277. [Google Scholar] [CrossRef]
- Van Deursen, A.J.; Mossberger, K. Any thing for anyone? A new digital divide in internet-of-things skills. Policy Internet 2018, 10, 122–140. [Google Scholar] [CrossRef] [Green Version]
- Paul, C.; Scheibe, K.; Nilakanta, S. Privacy concerns regarding wearable IoT devices: How it is influenced by GDPR? In Proceedings of the 53rd Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2020. [Google Scholar]
- Zheng, S.; Apthorpe, N.; Chetty, M.; Feamster, N. User perceptions of smart home IoT privacy. Proc. ACM Hum. Comput. Interact. 2018, 2, 1–20. [Google Scholar] [CrossRef] [Green Version]
- Voas, J.; Kuhn, R.; Laplante, P.; Applebaum, S. Internet of Things (IoT) Trust Concerns. NIST Tech. Rep 2018, 1, 1–50. [Google Scholar]
- Agaku, I.T.; Adisa, A.O.; Ayo-Yusuf, O.A.; Connolly, G.N. Concern about security and privacy, and perceived control over collection and use of health information are related to withholding of health information from healthcare providers. J. Am. Med. Informatics Assoc. 2013, 21, 374–378. [Google Scholar] [CrossRef] [Green Version]
- General Data Protection Regulation. Available online: https://gdpr-info.eu/ (accessed on 7 May 2021).
- BUKATY, P. The California Consumer Privacy Act (CCPA): An Implementation Guide; IT Governance Publishing: Ely, UK, 2019. [Google Scholar]
- Brazilian General Data Protection Law. Available online: https://iapp.org/resources/article/brazilian-data-protection-law-lgpd-english-translation/ (accessed on 10 May 2021).
- Kim, Y.; Park, Y.; Choi, J. A study on the adoption of IoT smart home service: Using Value-based Adoption Model. Total Qual. Manag. Bus. Excell. 2017, 28, 1149–1165. [Google Scholar] [CrossRef]
- Weyrich, M.; Ebert, C. Reference architectures for the internet of things. IEEE Softw. 2015, 33, 112–116. [Google Scholar] [CrossRef]
- Amershi, S.; Cakmak, M.; Knox, W.B.; Kulesza, T. Power to the people: The role of humans in interactive machine learning. Ai Mag. 2014, 35, 105–120. [Google Scholar] [CrossRef] [Green Version]
- Labib, N.S.; Brust, M.R.; Danoy, G.; Bouvry, P. Trustworthiness in IoT–A Standards Gap Analysis on Security, Data Protection and Privacy. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28–30 October 2019; pp. 1–7. [Google Scholar]
- Currie, D.J.; Peng, C.Q.; Lyle, D.M.; Jameson, B.A.; Frommer, M.S. Stemming the flow: How much can the Australian smartphone app help to control COVID-19. Public Health Res. Pr. 2020, 30, e3022009. [Google Scholar] [CrossRef] [PubMed]
- Park, S.; Choi, G.J.; Ko, H. Information technology—Based tracing strategy in response to COVID-19 in South Korea—Privacy controversies. JAMA 2020, 323, 2129–2130. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hánsel, K. Wearable and ambient sensing for well-being and emotional awareness in the smart workplace. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing: Adjunct, Heidelberg, Germany, 12–16 September 2016; pp. 411–416. [Google Scholar]
- Conti, M.; Passarella, A.; Das, S.K. The Internet of People (IoP): A new wave in pervasive mobile computing. Pervasive Mob. Comput. 2017, 41, 1–27. [Google Scholar] [CrossRef]
- Nappi, I.; de Campos Ribeiro, G. Internet of Things technology applications in the workplace environment: A critical review. J. Corp. Real Estate 2020. [Google Scholar] [CrossRef]
- Benhamida, F.; Navarro, J.; Gómez-Carmona, O.; Casado-Mansilla, D.; López-de-Ipi na, D.; Zaballos, A. SmartWorkplace: A Privacy-based Fog Computing Approach to Boost Energy Efficiency and Wellness in Digital Workspaces. In Proceedings of the 1st Workshop on Cyber-Physical Social Systems Co-Located with the 9th International Conference on the Internet of Things (IoT 2019), Bilbao, Spain, 22 October 2019; Volume 2530, pp. 9–15. [Google Scholar]
- Casado-Mansilla, D.; Garaizar, P.; López-de Ipina, D. Design-insights for Devising Persuasive IoT Devices for Sustainability in the Workplace. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; pp. 1–6. [Google Scholar]
- Murtagh, N.; Gatersleben, B.; Cowen, L.; Uzzell, D. Does perception of automation undermine pro-environmental behaviour? Findings from three everyday settings. J. Environ. Psychol. 2015, 42, 139–148. [Google Scholar] [CrossRef] [Green Version]
- GreenSoul: Persuasive Eco-awareness for User Engagement through Networked Data Devices. Available online: https://cordis.europa.eu/project/id/696129 (accessed on 7 May 2021).
- Nipkow, J.; Bush, E.; Josephy, B.; Pilone, A. For a tasty but efficient coffee. Proc. ECEEE 2011, 11, 1453–1470. [Google Scholar]
- Casado-Mansilla, D.; López-de Armentia, J.; Ventura, D.; Garaizar, P.; López-de Ipina, D. Embedding intelligent eco-aware systems within everyday things to increase people’s energy awareness. Soft Comput. 2016, 20, 1695–1711. [Google Scholar] [CrossRef]
- Ventura, D.; Casado-Mansilla, D.; López-de Armentia, J.; Garaizar, P.; López-de Ipina, D.; Catania, V. ARIIMA: A real IoT implementation of a machine-learning architecture for reducing energy consumption. In Proceedings of the International Conference on Ubiquitous Computing and Ambient Intelligence; Springer: Berlin/Heidelberg, Germany, 2014; pp. 444–451. [Google Scholar]
- Milfont, T.; Duckitt, J. A brief version of the environmental attitudes inventory. 2007. Unpublished Manuscript. [Google Scholar]
- Tribble, S.L. Promoting Environmentally Responsible Behaviors Using Motivational Interviewing Techniques. Ph.D. Thesis, Illinois Wesleyan University, Bloomington, IL, USA, 2008. [Google Scholar]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Emei Moutain, China, 14–15 December 2013; pp. 663–667. [Google Scholar]
- Mendez, D.M.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security and privacy. arXiv 2017, arXiv:1707.01879. [Google Scholar]
- Arrieta-Salinas, I.; Armendáriz-Inigo, J.E.; Navarro, J. Epidemia: Variable consistency for transactional cloud databases. J. Univers. Comput. Sci. 2014, 20, 14. [Google Scholar]
- Rao, P.; Lin, D.; Bertino, E.; Li, N.; Lobo, J. An algebra for fine-grained integration of XACML policies. In Proceedings of the 14th ACM Symposium on Access Control Models and Technologies, Stresa, Italy, 3–5 June 2009; pp. 63–72. [Google Scholar]
- Riad, K.; Cheng, J. Adaptive XACML access policies for heterogeneous distributed IoT environments. Inf. Sci. 2021, 548, 135–152. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing; MCC’12; ACM: New York, NY, USA, 2012; pp. 13–16. [Google Scholar] [CrossRef]
- Langheinrich, M. Privacy by design—Principles of privacy-aware ubiquitous systems. In Proceedings of the International Conference on Ubiquitous Computing; Springer: Berlin/Heidelberg, Germany, 2001; pp. 273–291. [Google Scholar]
- Vega-Barbas, M.; Casado-Mansilla, D.; Valero, M.A.; López-de Ipina, D.; Bravo, J.; Flórez, F. Smart spaces and smart objects interoperability architecture (S3OiA). In Proceedings of the Innovative Mobile and Internet Services in Ubiquitous Computing (IMIS), 2012 Sixth International Conference, Palermo, Italy, 4–6 July 2012; pp. 725–730. [Google Scholar]
- Alonso-Rosa, M.; Gil-de Castro, A.; Medina-Gracia, R.; Moreno-Munoz, A.; Ca nete-Carmona, E. Novel Internet of Things Platform for In-Building Power Quality Submetering. Appl. Sci. 2018, 8, 1320. [Google Scholar] [CrossRef] [Green Version]
- Cao, Z.; Hidalgo, G.; Simon, T.; Wei, S.; Sheikh, Y. OpenPose: Realtime Multi-Person 2D Pose Estimation using Part Affinity Fields. CoRR 2018, abs/1812.08008. Available online: http://xxx.lanl.gov/abs/1812.08008 (accessed on 7 May 2021). [CrossRef] [Green Version]
- Dizdarević, J.; Carpio, F.; Jukan, A.; Masip-Bruin, X. A survey of communication protocols for internet of things and related challenges of fog and cloud computing integration. ACM Comput. Surv. (CSUR) 2019, 51, 1–29. [Google Scholar] [CrossRef]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Zhao, W.; Lun, R.; Gordon, C.; Fofana, A.B.M.; Espy, D.D.; Reinthal, M.A.; Ekelman, B.; Goodman, G.D.; Niederriter, J.E.; Luo, X. A human-centered activity tracking system: Toward a healthier workplace. IEEE Trans. Hum. Mach. Syst. 2017, 47, 343–355. [Google Scholar] [CrossRef]
- Armbrust, M.; Fox, A.; Griffith, R.; Joseph, A.D.; Katz, R.; Konwinski, A.; Lee, G.; Patterson, D.; Rabkin, A.; Stoica, I.; et al. A view of cloud computing. Commun. ACM 2010, 53, 50–58. [Google Scholar] [CrossRef] [Green Version]
- Challal, Y.; Benhamida, F.Z.; Nouali, O. Scalable Key Management for Elastic Security Domains in Fog Networks. In Proceedings of the 2018 IEEE 27th International Conference on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE), Paris, France, 27–29 June 2018; pp. 187–192. [Google Scholar] [CrossRef]
- Liu, D.; Gu, T.; Xue, J.P. Rule engine based on improvement rete algorithm. In Proceedings of the The 2010 International Conference on Apperceiving Computing and Intelligence Analysis Proceeding, Chengdu, China, 17–19 December 2010; pp. 346–349. [Google Scholar]
- Friedman-Hill, E. Jess, the Rule Engine for the Java Platform. 2008. Available online: http://alvarestech.com/temp/fuzzyjess/Jess60/Jess70b7/docs/embedding.html (accessed on 7 May 2021).
- Yang, C.H.; Zhang, Y.S. Research on the Architecture of Iot Middleware Platform Based on BeiDou Navigation Satellite System. Procedia Comput. Sci. 2020, 166, 46–50. [Google Scholar] [CrossRef]
- Blair, G.; Schmidt, D.; Taconet, C. Middleware for Internet distribution in the context of cloud computing and the Internet of Things: Editorial Introduction. Ann. Des. Telecommun. Telecommun. 2016, 71, 87–92. [Google Scholar] [CrossRef] [Green Version]
- Azeem, N.S.A.; Tarrad, I.; Hady, A.A.; Youssef, M.I.; El-kader, S.M.A. Shared Sensor Networks Fundamentals, Challenges, Opportunities, Virtualization Techniques, Comparative Analysis, Novel Architecture and Taxonomy. J. Sens. Actuator Netw. 2019, 8, 29. [Google Scholar] [CrossRef] [Green Version]
- Antonini, M.; Vecchio, M.; Antonelli, F. Fog computing architectures: A reference for practitioners. IEEE Internet Things Mag. 2019, 2, 19–25. [Google Scholar] [CrossRef]
- Pore, M.; Chakati, V.; Banerjee, A.; Gupta, S. Middleware for fog and edge computing: Design issues. In Fog and Edge Computing: Principles and Paradigms; Wiley: Hoboken, NJ, USA, 2019; pp. 123–144. [Google Scholar]
- Zimmermann, O. Microservices tenets. Comput. Sci. Res. Dev. 2017, 32, 301–310. [Google Scholar] [CrossRef]
- Chen, J.H.; Hsu, S.C.; Chen, C.L.; Tai, H.W.; Wu, T.H. Exploring the association rules of work activities for producing precast components. Autom. Constr. 2020, 111, 103059. [Google Scholar] [CrossRef]
- Bowen, J.; Hinze, A.; Griffiths, C.; Kumar, V.; Bainbridge, D. Personal Data Collection in the Workplace: Ethical and Technical Challenges. In Proceedings of the British Human Computer Interaction Conference, (BHCI), Sunderland, UK, 3–6 July 2017; pp. 1–11. [Google Scholar]
- Ajunwa, I.; Crawford, K.; Schultz, J. Limitless worker surveillance. Cal. L. Rev. 2017, 105, 735. [Google Scholar]
- Shabha, G. A critical review of the impact of embedded smart sensors on productivity in the workplace. Facilities 2006, 24, 538–549. [Google Scholar] [CrossRef]
- Pape, S.; Rannenberg, K. Applying privacy patterns to the internet of things’(iot) architecture. Mob. Netw. Appl. 2019, 24, 925–933. [Google Scholar] [CrossRef]
- Hermsen, S.; Frost, J.; Renes, R.J.; Kerkhof, P. Using feedback through digital technology to disrupt and change habitual behavior: A critical review of current literature. Comput. Hum. Behav. 2016, 57, 61–74. [Google Scholar] [CrossRef] [Green Version]
- Holzinger, A. Interactive machine learning for health informatics: When do we need the human-in-the-loop? Brain Inform. 2016, 3, 119–131. [Google Scholar] [CrossRef] [Green Version]
- Zanzotto, F.M. Human-in-the-loop Artificial Intelligence. J. Artif. Intell. Res. 2019, 64, 243–252. [Google Scholar] [CrossRef] [Green Version]
- Muangprathub, J.; Boonnam, N.; Kajornkasirat, S.; Lekbangpong, N.; Wanichsombat, A.; Nillaor, P. IoT and agriculture data analysis for smart farm. Comput. Electron. Agric. 2019, 156, 467–474. [Google Scholar] [CrossRef]
- Doukas, C.; Maglogiannis, I. Bringing IoT and cloud computing towards pervasive healthcare. In Proceedings of the 2012 Sixth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Palermo, Italy, 4–6 July 2012; pp. 922–926. [Google Scholar]
- Hiremath, S.; Yang, G.; Mankodiya, K. Wearable Internet of Things: Concept, architectural components and promises for person-centered healthcare. In Proceedings of the 2014 4th International Conference on Wireless Mobile Communication and Healthcare-Transforming Healthcare Through Innovations in Mobile and Wireless Technologies (MOBIHEALTH), Athens, Greece, 3–5 November 2014; pp. 304–307. [Google Scholar]
- GhaffarianHoseini, A.; Dahlan, N.D.; Berardi, U.; GhaffarianHoseini, A.; Makaremi, N. The essence of future smart houses: From embedding ICT to adapting to sustainability principles. Renew. Sustain. Energy Rev. 2013, 24, 593–607. [Google Scholar] [CrossRef]
- Sánchez-Corcuera, R.; Nu nez-Marcos, A.; Sesma-Solance, J.; Bilbao-Jayo, A.; Mulero, R.; Zulaika, U.; Azkune, G.; Almeida, A. Smart cities survey: Technologies, application domains and challenges for the cities of the future. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719853984. [Google Scholar] [CrossRef] [Green Version]
- Simmers, C.A.; Anandarajan, M. The Internet of People, Things and Services: Workplace Transformations; Routledge: London, UK, 2018. [Google Scholar]
- Young, W.; Davis, M.; McNeill, I.M.; Malhotra, B.; Russell, S.; Unsworth, K.; Clegg, C.W. Changing behaviour: Successful environmental programmes in the workplace. Bus. Strategy Environ. 2015, 24, 689–703. [Google Scholar] [CrossRef] [Green Version]
- Timmer, D.; Appleby, D.; Timmer, V. Sustainable Lifestyles: Options & Opportunities in the Workplace; One planet; One Earth: Vancouver, BC, Canada, 2018. [Google Scholar]
- Leygue, C.; Ferguson, E.; Spence, A. Saving energy in the workplace: Why, and for whom? J. Environ. Psychol. 2017, 53, 50–62. [Google Scholar] [CrossRef]
- Sparks, K.; Faragher, B.; Cooper, C.L. Well-being and occupational health in the 21st century workplace. J. Occup. Organ. Psychol. 2001, 74, 489–509. [Google Scholar] [CrossRef]
- Ilvesmaki, A. Drivers and challenges of personal health systems in workplace health promotion. In Proceedings of the 2007 29th Annual International Conference of the IEEE Engineering in Medicine and Biology Society; IEEE: New York, NY, USA, 2007; pp. 5878–5881. [Google Scholar]
- Appelbaum, E.; Batt, R.L. The new American Workplace: Transforming Work Systems in the United States; Cornell University Press: Ithaca, NY, USA, 1994. [Google Scholar]
- Maman, Z.S.; Yazdi, M.A.A.; Cavuoto, L.A.; Megahed, F.M. A data-driven approach to modeling physical fatigue in the workplace using wearable sensors. Appl. Ergon. 2017, 65, 515–529. [Google Scholar] [CrossRef] [PubMed]
- Taylor, W.; Suminski, R.; Das, B.; Paxton, R.; Craig, D. Organizational Culture and Implications for Workplace Interventions to Reduce Sitting Time Among Office-Based Workers: A Systematic Review. Front. Public Health 2018, 6, 263. [Google Scholar] [CrossRef] [PubMed]
- Stephenson, A.; McDonough, S.M.; Murphy, M.H.; Nugent, C.D.; Mair, J.L. Using computer, mobile and wearable technology enhanced interventions to reduce sedentary behaviour: A systematic review and meta-analysis. Int. J. Behav. Nutr. Phys. Act. 2017, 14, 105. [Google Scholar] [CrossRef]
- Holtermann, A.; Schellewald, V.; Mathiassen, S.E.; Gupta, N.; Pinder, A.; Punakallio, A.; Veiersted, K.B.; Weber, B.; Takala, E.P.; Draicchio, F.; et al. A practical guidance for assessments of sedentary behavior at work: A PEROSH initiative. Appl. Ergon. 2017, 63, 41–52. [Google Scholar] [CrossRef]
- Jimenez, P.; Bregenzer, A. Integration of eHealth tools in the process of workplace health promotion: Proposal for design and implementation. J. Med Internet Res. 2018, 20, e65. [Google Scholar] [CrossRef]
- Huang, Y.; Benford, S.; Blake, H. Digital Interventions to Reduce Sedentary Behaviors of Office Workers: Scoping Review. J. Med. Internet Res. 2019, 21, e11079. [Google Scholar] [CrossRef]
- Pedersen, S.J.; Cooley, P.D.; Mainsbridge, C. An e-health intervention designed to increase workday energy expenditure by reducing prolonged occupational sitting habits. Work 2014, 49, 289–295. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Howarth, A.; Quesada, J.; Silva, J.; Judycki, S.; Mills, P.R. The impact of digital health interventions on health-related outcomes in the workplace: A systematic review. Digit. Health 2018, 4, 2055207618770861. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Cheng, J.; Zhou, B.; Sundholm, M.; Lukowicz, P. Smart chair: What can simple pressure sensors under the chairs legs tell us about user activity. In Proceedings of the UBICOMM13: The Seventh International Conference on Mobile Ubiquitous Computing, Systems, Services and Technologies, Porto, Portugal, 29 September–3 October 2013; pp. 81–84. [Google Scholar]
- Kaur, H.; Williams, A.C.; McDuff, D.; Czerwinski, M.; Teevan, J.; Iqbal, S. Optimizing for Happiness and Productivity: Modeling Opportune Moments for Transitions and Breaks at Work. In Proceedings of the ACM Conference on Human Factors in Computing Systems (CHI), Honolulu, HI, USA, 25–30 April 2020; pp. 1–15. [Google Scholar]
- Roossien, C.; Stegenga, J.; Hodselmans, A.; Spook, S.; Koolhaas, W.; Brouwer, S.; Verkerke, G.; Reneman, M.F. Can a smart chair improve the sitting behavior of office workers? Appl. Ergon. 2017, 65, 355–361. [Google Scholar] [CrossRef] [PubMed]
- Ahmed, E.; Yaqoob, I.; Gani, A.; Imran, M.; Guizani, M. Internet-of-things-based smart environments: State of the art, taxonomy, and open research challenges. IEEE Wirel. Commun. 2016, 23, 10–16. [Google Scholar] [CrossRef]
- Podgorski, D.; Majchrzycka, K.; Dabrowska, A.; Gralewicz, G.; Okrasa, M. Towards a conceptual framework of OSH risk management in smart working environments based on smart PPE, ambient intelligence and the Internet of Things technologies. Int. J. Occup. Saf. Ergon. 2017, 23, 1–20. [Google Scholar] [CrossRef] [Green Version]
- Irizar-Arrieta, A.; Casado-Mansilla, D. Coping with user diversity: UX informs the design of a digital interface that encourages sustainable behaviour. In Proceedings of the 11th International Conference on Interfaces and Human Computer Interaction, Lisbon, Portugal, 21–23 July 2017; pp. 1–8. [Google Scholar]
- Irizar-Arrieta, A.; Casado-Mansilla, D.; Retegi, A. Accounting for User Diversity in the Design for Sustainable Behaviour in Smart Offices. In Proceedings of the 2018 3rd International Conference on Smart and Sustainable Technologies (SpliTech), Split, Croatia, 26–29 June 2018; pp. 1–6. [Google Scholar]
- Jönsson, L.; Broms, L.; Katzeff, C. Watt-Lite: Energy statistics made tangible. In Proceedings of the 8th ACM Conference on Designing Interactive Systems, Aarhus, Denmark, 16–20 August 2010; pp. 240–243. [Google Scholar]
- Morgan, E.; Webb, L.; Carter, K.; Goddard, N. Co-Designing a Device for Behaviour-Based Energy Reduction in a Large Organisation. Proc. ACM Hum. Comput. Interact. 2018, 2, 125. [Google Scholar] [CrossRef] [Green Version]
- Casado-Mansilla, D.; Moschos, I.; Kamara-Esteban, O.; Tsolakis, A.C.; Borges, C.E.; Krinidis, S.; Irizar-Arrieta, A.; Kitsikoudis, K.; Pijoan, A.; Tzovaras, D.; et al. A Human-centric & Context-aware IoT Framework for Enhancing Energy Efficiency in Buildings of Public Use. IEEE Access 2018, 6, 31444–31456. [Google Scholar] [CrossRef]
- Gomez-Carmonaa, O.; Casado-Mansillaa, D.; Garcıa-Zubiab, J. Opportunities and Challenges of Technology-ased Interventions to Increase Health-wareness in the Workplace. Transform. Ergon. Pers. Health Intell. Work. 2019, 25, 33. [Google Scholar]
- Schall, M.C., Jr.; Sesek, R.F.; Cavuoto, L.A. Barriers to the adoption of wearable sensors in the workplace: A survey of occupational safety and health professionals. Hum. Factors 2018, 60, 351–362. [Google Scholar] [CrossRef] [PubMed]
- Helfrich, C.D.; Kohn, M.J.; Stapleton, A.; Allen, C.L.; Hammerback, K.E.; Chan, K.; Parrish, A.T.; Ryan, D.E.; Weiner, B.J.; Harris, J.R.; et al. Readiness to change over time: Change commitment and change efficacy in a workplace health-promotion trial. Front. Public Health 2018, 6, 110. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lindell, Y. Secure multiparty computation for privacy preserving data mining. In Encyclopedia of Data Warehousing and Mining; IGI Global: Hershey, PA, USA, 2005; pp. 1005–1009. [Google Scholar]
- Léauté, T.; Faltings, B. Protecting privacy through distributed computation in multi-agent decision making. J. Artif. Intell. Res. 2013, 47, 649–695. [Google Scholar] [CrossRef]

| Metrics | Qualitative Evaluation | |||
|---|---|---|---|---|
| GreenSoul | Smart Sustainable Coffee Machines | PyFF | ||
| Privacy | Data protection | + (anonymization & encryption) | + (anonymization) | ++ (based on privacy policy) |
| Data usage | Edge | Cloud | Device, Edge, Cloud (based on user’s choice) | |
| Homogeneity | Yes | Yes | heterogenous privacy rules & preferences | |
| Disruption/Intrusion | -(many new deployed devices) | - -(full automation) | ++(Interaction-based scheme & no extra devices) | |
| Automation | User involvement | +(one-way recommendations) | - -(full automation) | ++ (full-duplex & adapted to user involvement preferences) |
| Recommendation accuracy | Fog-based | Cloud-based | Cloud/Fog (parameter) | |
| ICT/HCI | dashboard | dashboard | depends on user’s behavior/preference | |
| Real-time | Yes | Yes | Yes | |
| Flexibility | Adaptive reasoning | Non-existent | Non-existent | layer-based |
| Context-based | Energy | Energy(coffee machines) | Any context | |
| Scalability | workplace - | home & workplace + | ++ | |
| Deployment | Deployment cost | Hardware + software | Hardware + software | Hardware + software |
| Fault isolation and tolerance | NA | Yes | Yes | |
| Heterogeneous devices | Yes | No | Yes | |
| Reliability | - (fog-ML-based recommendation) | +(Statistical method) | NA | |
| Distributed | No | No | Yes | |
| Event management | + DSS | NA | ++ DSS + User-Environment layer | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Benhamida, F.Z.; Navarro, J.; Gómez-Carmona, O.; Casado-Mansilla, D.; López-de-Ipiña, D.; Zaballos, A. PyFF: A Fog-Based Flexible Architecture for Enabling Privacy-by-Design IoT-Based Communal Smart Environments. Sensors 2021, 21, 3640. https://doi.org/10.3390/s21113640
Benhamida FZ, Navarro J, Gómez-Carmona O, Casado-Mansilla D, López-de-Ipiña D, Zaballos A. PyFF: A Fog-Based Flexible Architecture for Enabling Privacy-by-Design IoT-Based Communal Smart Environments. Sensors. 2021; 21(11):3640. https://doi.org/10.3390/s21113640
Chicago/Turabian StyleBenhamida, Fatima Zohra, Joan Navarro, Oihane Gómez-Carmona, Diego Casado-Mansilla, Diego López-de-Ipiña, and Agustín Zaballos. 2021. "PyFF: A Fog-Based Flexible Architecture for Enabling Privacy-by-Design IoT-Based Communal Smart Environments" Sensors 21, no. 11: 3640. https://doi.org/10.3390/s21113640
APA StyleBenhamida, F. Z., Navarro, J., Gómez-Carmona, O., Casado-Mansilla, D., López-de-Ipiña, D., & Zaballos, A. (2021). PyFF: A Fog-Based Flexible Architecture for Enabling Privacy-by-Design IoT-Based Communal Smart Environments. Sensors, 21(11), 3640. https://doi.org/10.3390/s21113640











