Opportunistic Network Algorithms for Internet Traffic Offloading in Music Festival Scenarios
Abstract
1. Introduction
- Design a mobility model which can emulate the movement patterns of festival attendees and use it to test various opportunistic algorithms;
- Study already existing opportunistic routing solutions;
- Identify the key parameters that have the potential to increase the performance of an opportunistic algorithm in a music festival scenario;
- Create an opportunistic algorithm specifically tailored for high performance at crowded events;
- Study the impact of Bluetooth and Wi-Fi Direct on algorithm performance.
2. Background and Related Work
2.1. Opportunistic Networks
- Nodes can communicate with each other, although there is no route between them;
- Nodes do not require information about the network topology in order to be able to communicate;
- The routes between nodes are built dynamically
- any node can be used as the next hop for a message, if it may bring the message closer to the destination;
- Since the paths between nodes are assumed to be dynamic, this aspect may increase the delivery delay for a message;
- Each node acts as a gateway for a message, exploiting its local knowledge at that time in order to determine the best next hop.
2.2. Belgium Festival Study
2.3. Zurich Festival Study
3. A Festival Mobility Model
3.1. The Sonar Festival Dataset
3.1.1. Description
3.1.2. Challenges
- Duplicate filter—we had to delete the duplicates from the dataset, caused by clock synchronization errors and buffering between the server and the scanners;
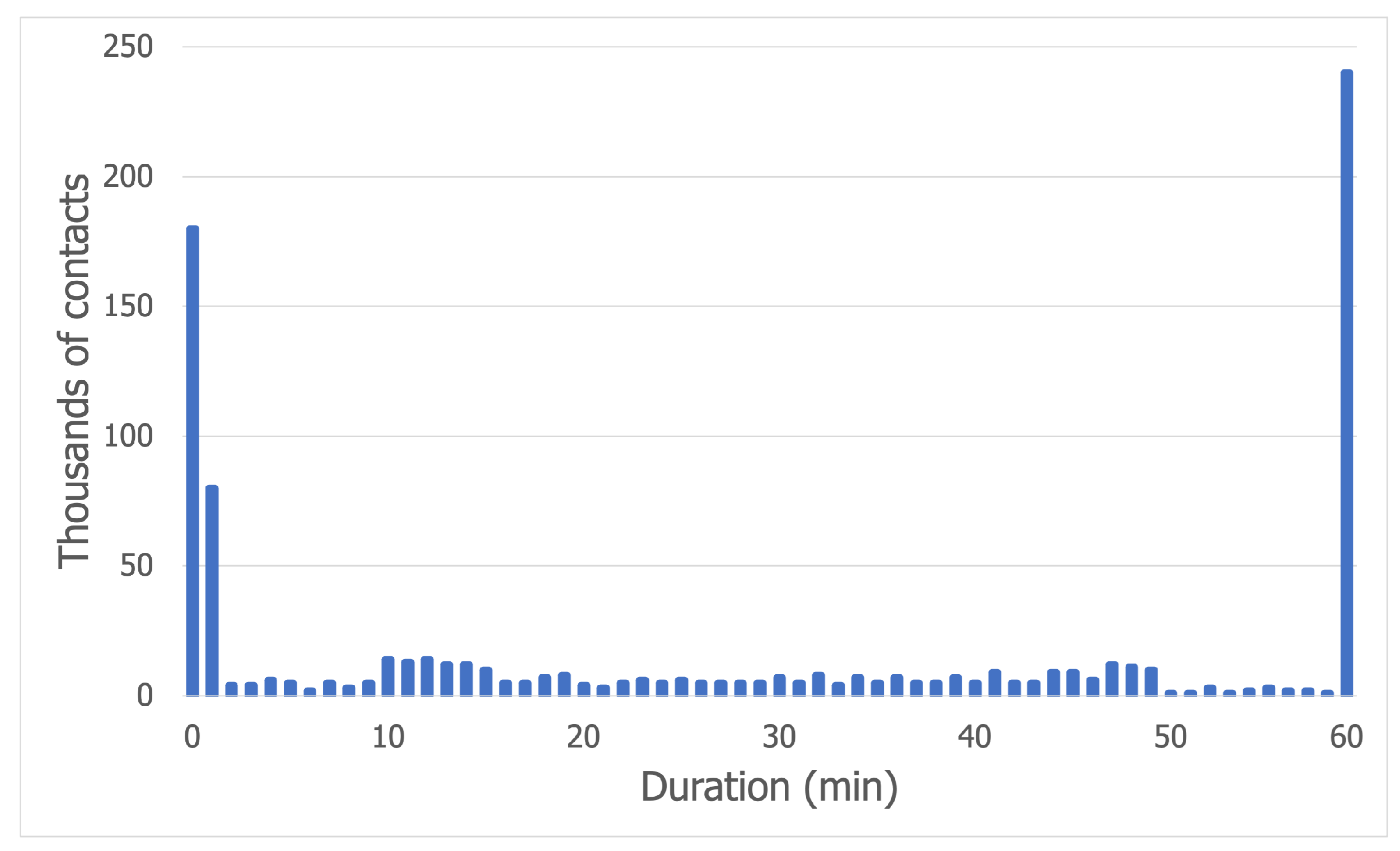
- Format filter—we had to convert the anonymized MAC address to a node identifier format supported by the simulator; the end goal of parsing the dataset was to obtain contacts between nodes, which are the centerpiece structures of a mobility trace; a contact is an interaction between two nodes, which has a start and end timestamp and during which messages are exchanged following a communication protocol;
- Time filter—we checked the data for outlier values and validated that all timestamps were between 9:00 a.m. and 12:00 a.m.
- Some of the timestamps were between 12:00 a.m. and 9:00 a.m., although the researchers mention they had only collected data between 12:00 p.m. and 10:00 p.m.; we chose not to include data recorded during the night in the final dataset;
- Some of the nodes were observed consistently in the same place for hours; these data points might exist because the main stage was surrounded by food trucks and other non-music related attractions; naturally, if a node spent around 11 h at a location, it can be assumed that it was the phone (or other device with Wi-Fi connectivity) of one of the staff members;
- Some of the nodes were observed for a brief period of time in a location, so we discarded them.
- Each day, there were a significant number of nodes present at the festival for less than 60 min; whatever the causes might be, we have chosen not to consider these nodes as contact-worthy (in order to account for communication or data collection errors that might affect and alter our conclusions);
- Although there were around 100 nodes that spent more than 10 h at the festival each day, we considered them for contact opportunities only if that time was not spent at the same location.
3.1.3. Analysis
3.1.4. Generating Contacts
3.1.5. Conclusions
- People spend different amounts of time at a festival, which could be implemented in a synthetic mobility model;
- Some areas are more popular than others, and hence more crowded;
- The number of people varies throughout the day.
3.2. Wi-Fi Direct vs. Bluetooth
3.3. Communication Use Case at a Music Festival
- Pick a generation time—-this is done randomly, since a festival participant might need to communicate with other people at any time;
- For each node in the simulation, generate a fixed number of messages and copies corresponding to a message—the destination type of a message is established through the use of a Zipf distribution (A method for generating Zipfian random values is presented here: https://medium.com/@jasoncrease/zipf-54912d5651cc, accessed on 10 May 2021); the nodes which are both in the social network and the discovered community (A node’s discovered community is a group of other nodes that it comes in contact with often. Aside from the group of friends (which will also be part of the social network community), a discovered community will also most likely include “familiar strangers”, meaning unknown persons that are often encountered for long periods of time.) of the node are more likely to be selected as the destination, followed by nodes in the social network, nodes in the community, and finally random nodes.
- If the node is not part of a chat pair, pick a random message destination, the only constraint being that the destination has to be a friend;
- For every chat pair, generate two messages, each message originating from one of the two pair members.
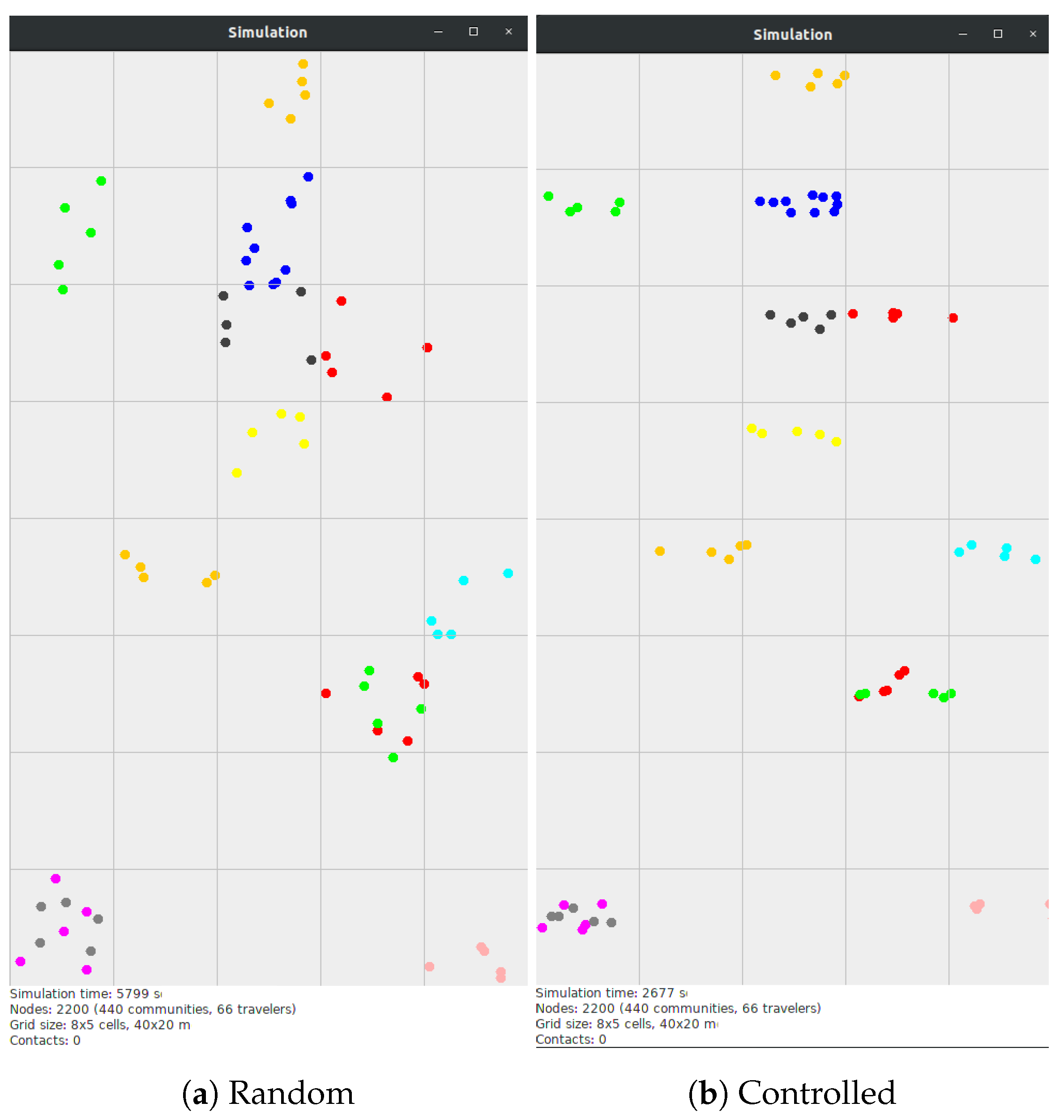
3.4. Simulating Festival Mobility Behavior
- Even after applying outlier removal to the Sonar dataset and grouping the nodes by location, we found it challenging to generate a close-to-reality trace due to the lack of location information; without any data regarding the vicinity of a node or its social ties, no strategy other than randomly generating contacts can be assumed to be better;
- The validation of an opportunistic network algorithm relies heavily on how realistic the movement models used in the simulation are [17]; therefore, it is of paramount importance to identify realistic mobility models in order to tailor an algorithm for the desired scenario and to later fine-tune it for better performance.
- CRAWDAD (https://crawdad.org/, accessed on 10 May 2021) is an archive of wireless trace data publicly available to the research community; unfortunately, these traces are related to particular scenarios and can hardly be generalized for different use cases; moreover, there is only one festival trace available, but the data recorded did not suit our needs;
- Many mobility models are based on the random movement of individuals such as the Random Walk model (where nodes move by randomly choosing a direction and speed) or the Random Waypoint model (where pauses are introduced between changes in direction or speed); however, there are also two mobility models, CMM [17] and HCMM [18], which are founded on social network theory and, therefore, closer to reality.
- Has no support for a custom social network;
- Measures cell attractivity differently than CMM—the social attraction towards a cell is evaluated based on the social relationships with nodes having that cell assigned as their home cell; the idea of a home cell is not relevant in a festival scenario, but it is of great importance when simulating a workday in a city;
- Allows for a single group to be placed in a cell regardless of cell size;
- Has no crowd density mechanism.
3.5. A Proposed Festival Mobility Model (FMM)
- Move alone towards a target destination;
- Move with the whole group towards a target destination;
- Return to the community after having spent a certain time at the destination.
- For every cell on the grid, compute a metric called cell attractivity, defined as the sum of the social relationship weights of the nodes present in that cell with regards to the given node;
- Normalize the sum by the total number of nodes present in that cell.
4. An Opportunistic Routing Protocol for a Festival Scenario
- Ideally, it should consume a small amount of resources;
- The delivery delay should be less than 5–10 min for an acceptable quality of service;
- The delivered messages ratio should be above 90%.
| Algorithm 1: SSW1 forwarding. |
 |
| Algorithm 2: SSW2 forwarding. |
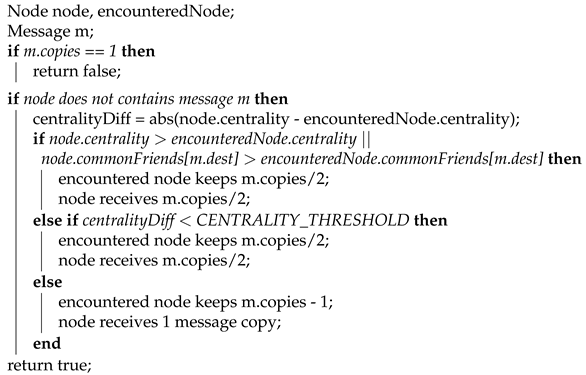 |
5. Evaluation
5.1. Algorithms and Metrics
- Forwarding criterion 1 (FC1)—forward the message if the encountered node is a friend on a social network with the message destination and the carrier node is not;
- Forwarding criterion 2 (FC2)—forward the message if the encountered node has more friends in common with the message destination;
- Forwarding criterion 3 (FC3)—forward the message if the encountered node has a higher centrality;
- Forwarding criterion 4 (FC4)—forward the message if the centrality difference is less than a predefined threshold.
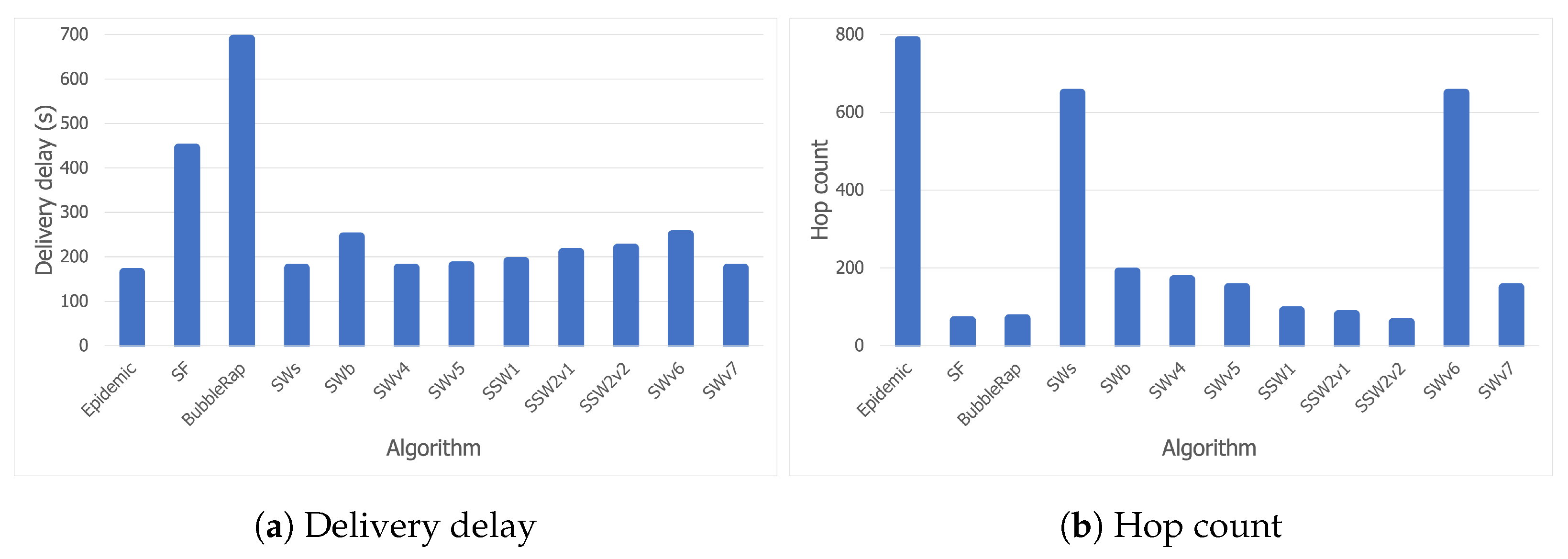
- Delivery rate—the ratio between the number of delivered messages and the total number of created messages;
- Delivery delay—the time elapsed between the generation of a message and its delivery;
- Overhead—the ratio between the total number of exchanged messages and the total number of created messages;
- Number of hops—the number of nodes through which one message has been relayed until reaching its destination; this metric and the overhead are indicators of the network and node congestion.
5.2. Test Data
5.2.1. Bluetooth Trace
5.2.2. Wi-Fi Direct Trace
- Only nodes moving away from their community will play the role of access point (AP) or group owner (GO);
- Once a node is reunited with its community, it stops being an AP;
- to preserve their battery, AP nodes will alternate between being on and off for intervals of 5 min;
- A node can connect to an AP for 1 min;
- A node cannot connect to the same AP twice in a row;
- The rest of the nodes also exchange data via Bluetooth.
- The P2P devices perform a classic Wi-Fi scan, which may lead to discovering other Wi-Fi networks and P2P groups;
- A process called device discovery happens afterward; the devices alternate between two states for randomly distributed periods: search state and listen state; during the search state, a device sends probe requests on channels 1, 6, and 11 in the 2.4 Ghz frequency band; in the listen state, a device will listen for probe requests and then send probe responses;
- GO negotiation will be initiated after two devices have discovered each other; the GO will be elected as a result of a three-way handshake, after which the devices will exchange their GO intent values.
5.2.3. Transfer Speed
5.3. Results
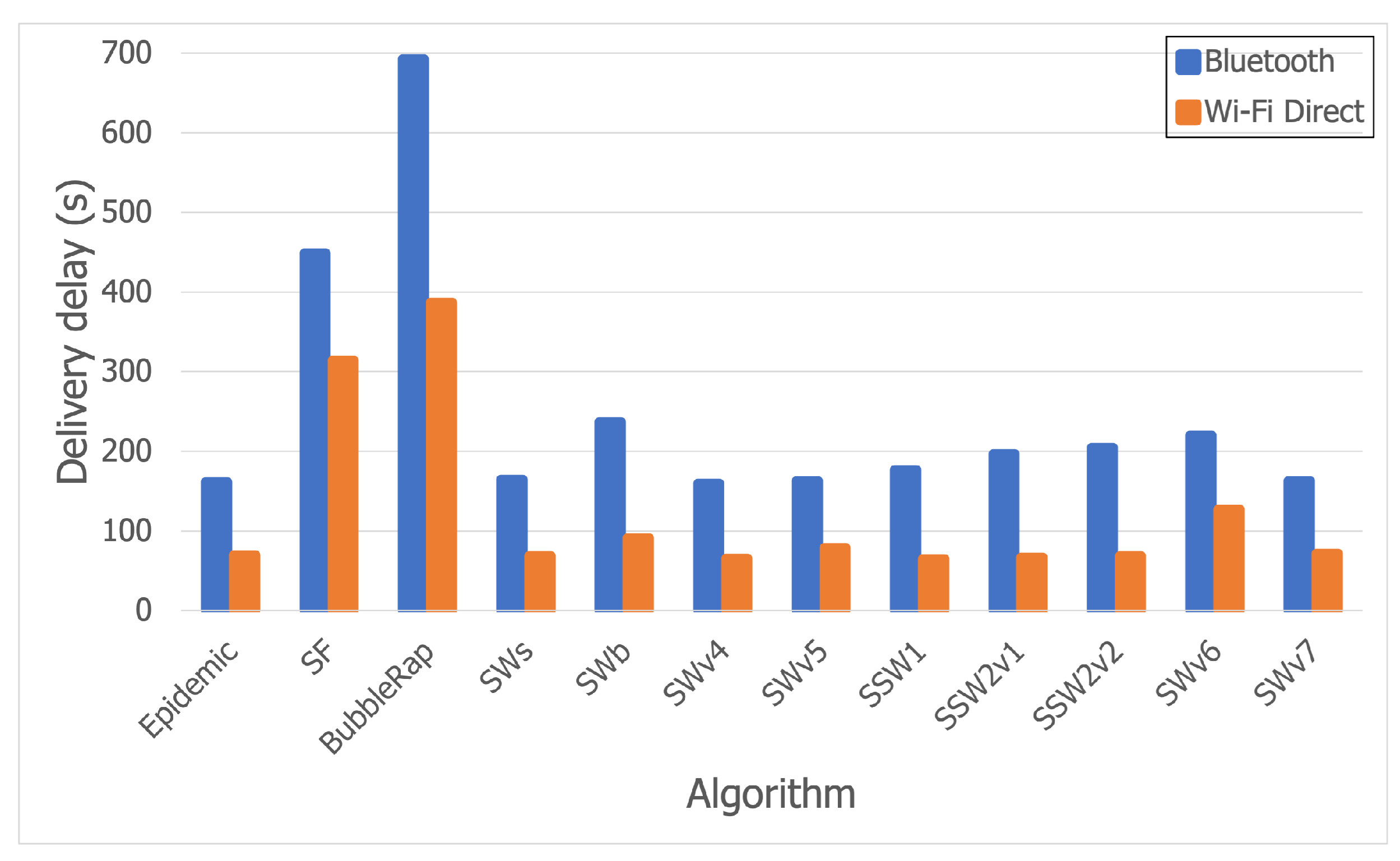
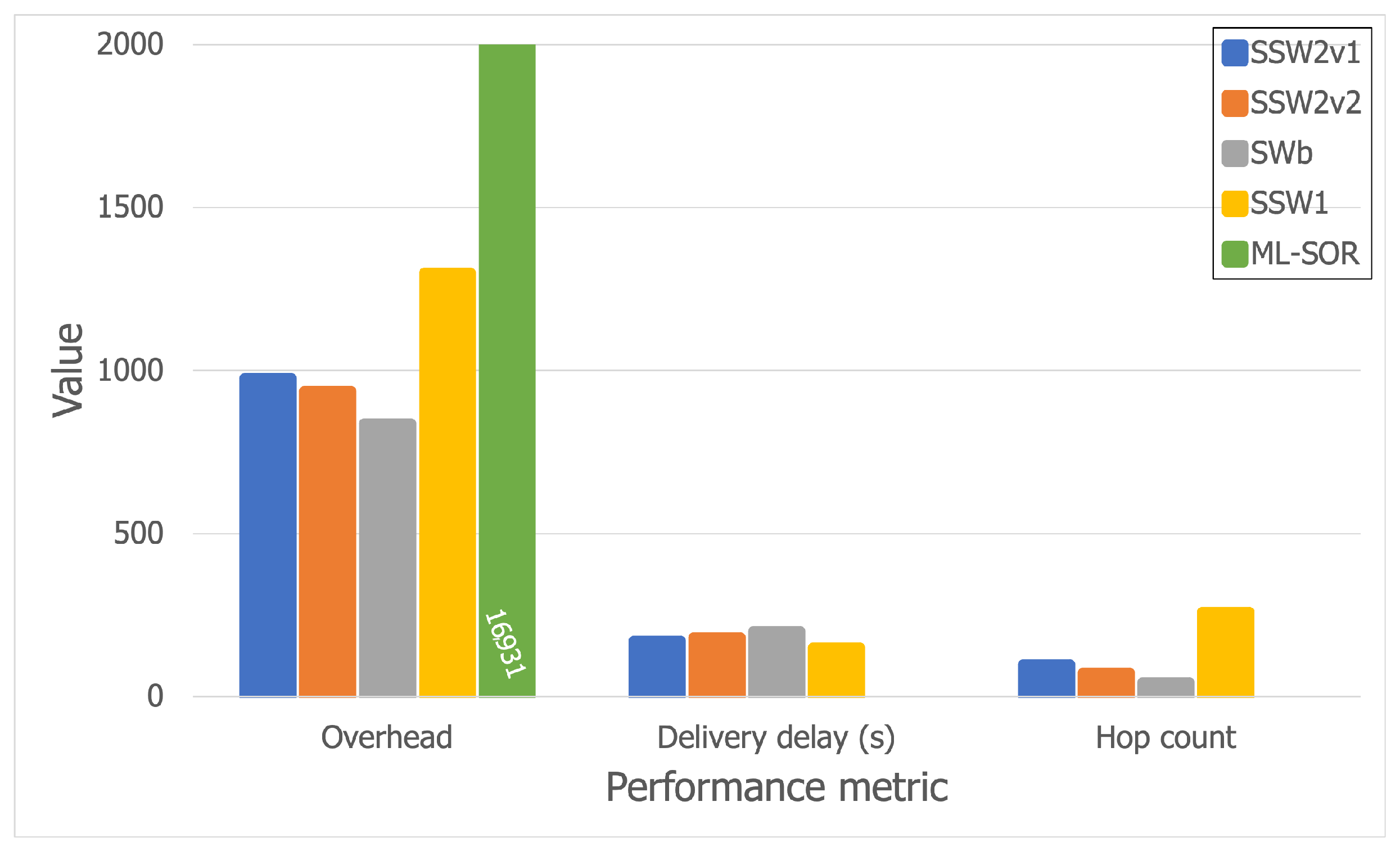
5.3.1. Bluetooth Trace
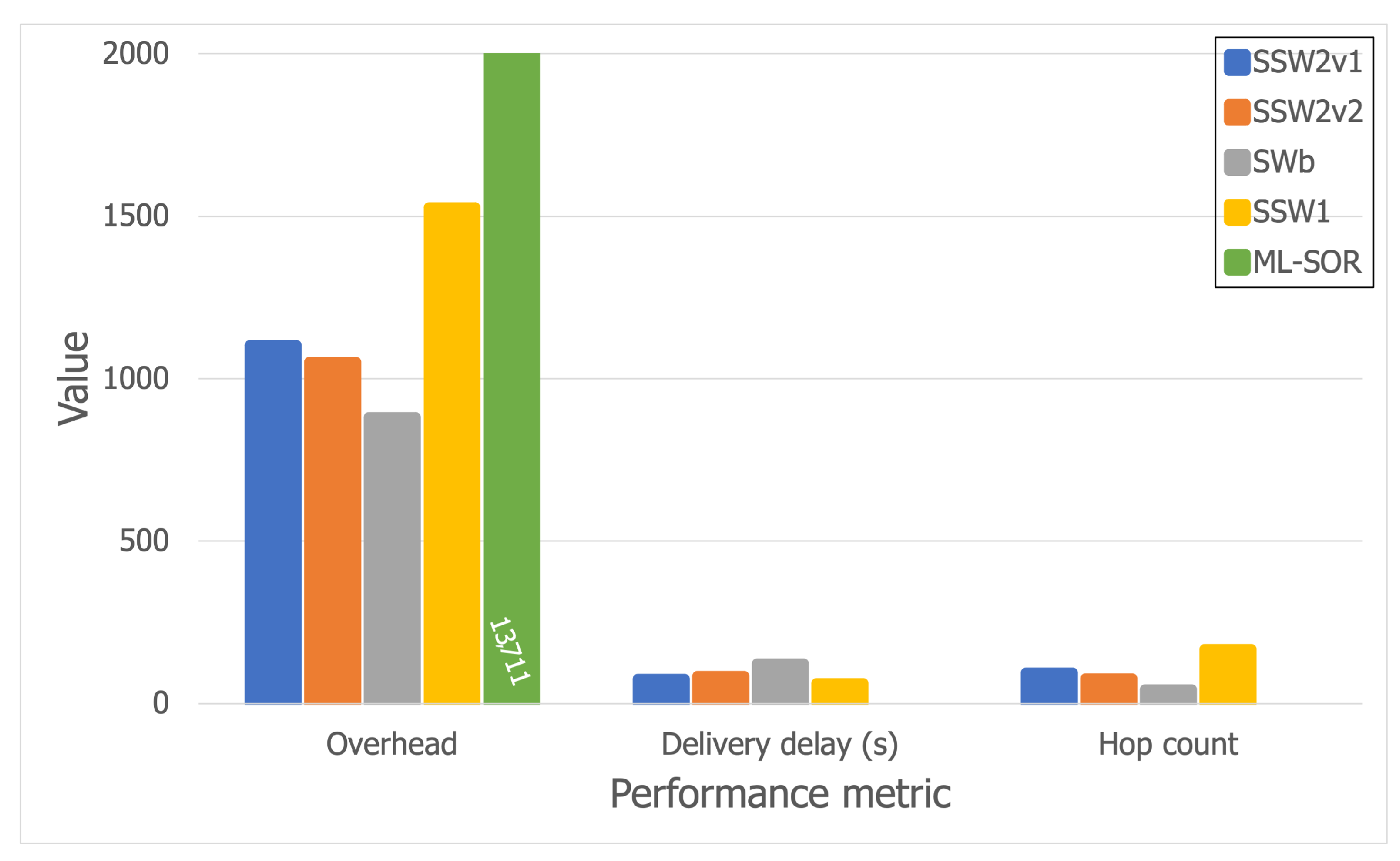
5.3.2. Wi-Fi Direct Trace
5.3.3. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Juang, P.; Oki, H.; Wang, Y.; Martonosi, M.; Peh, L.S.; Rubenstein, D. Energy-Efficient Computing for Wildlife Tracking: Design Tradeoffs and Early Experiences with ZebraNet. In Proceedings of the 10th International Conference on Architectural Support for Programming Languages and Operating Systems (ASPLOS X), San Jose, CA, USA, 5–9 October 2002; Association for Computing Machinery: New York, NY, USA, 2002; pp. 96–107. [Google Scholar] [CrossRef]
- Franke, T.; Negele, S.; Kampis, G.; Lukowicz, P. Leveraging human mobility in smartphone based Ad-Hoc information distribution in crowd management scenarios. In Proceedings of the 2015 2nd International Conference on Information and Communication Technologies for Disaster Management (ICT-DM), Rennes, France, 30 November–2 December 2015; pp. 27–34. [Google Scholar]
- Herrera-Tapia, J.; Hernández-Orallo, E.; Tomás, A.; Manzoni, P.; Tavares Calafate, C.; Cano, J.C. Friendly-sharing: Improving the performance of city sensoring through contact-based messaging applications. Sensors 2016, 16, 1523. [Google Scholar] [CrossRef] [PubMed]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and Wait: An Efficient Routing Scheme for Intermittently Connected Mobile Networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking (WDTN ’05), Philadelphia, PA, USA, 22–26 August 2005; Association for Computing Machinery: New York, NY, USA, 2005; pp. 252–259. [Google Scholar] [CrossRef]
- Jadhav, P.; Satao, R. A survey on opportunistic routing protocols for wireless sensor networks. Procedia Comput. Sci. 2016, 79, 603–609. [Google Scholar] [CrossRef]
- Arafath, M.S.; Khan, K.U.R.; Sunitha, K. Incorporating privacy and security in military application based on opportunistic sensor network. Int. J. Internet Technol. Secur. Trans. 2017, 7, 295–316. [Google Scholar] [CrossRef]
- Pentland, A.; Fletcher, R.; Hasson, A. Daknet: Rethinking connectivity in developing nations. Computer 2004, 37, 78–83. [Google Scholar] [CrossRef]
- Zyba, G.; Voelker, G.M.; Ioannidis, S.; Diot, C. Dissemination in opportunistic mobile ad-hoc networks: The power of the crowd. In Proceedings of the 2011 Proceedings IEEE INFOCOM, Shanghai, China, 10–15 April 2011; pp. 1179–1187. [Google Scholar]
- Gorbil, G.; Gelenbe, E. Opportunistic communications for emergency support systems. Procedia Comput. Sci. 2011, 5, 39–47. [Google Scholar] [CrossRef]
- Barzan, A.; Bonné, B.; Quax, P.; Lamotte, W.; Versichele, M.; Van de Weghe, N. A comparative simulation of opportunistic routing protocols using realistic mobility data obtained from mass events. In Proceedings of the 2013 IEEE 14th International Symposium on “a World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Madrid, Spain, 4–7 June 2013; pp. 1–6. [Google Scholar]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially-Connected Ad Hoc Networks, 2009. Available online: https://bit.ly/3y2dqAX (accessed on 1 April 2021).
- Lindgren, A.; Doria, A.; Schelén, O. Probabilistic Routing in Intermittently Connected Networks. SIGMOBILE Mob. Comput. Commun. Rev. 2003, 7, 19–20. [Google Scholar] [CrossRef]
- Carrasco-Jiménez, J.C.; Cucchietti, F.M.; Garcia-Saez, A.; Marin, G.; Calvo, L. We know what you did last sonar: Inferring preference in music from mobility data. In Intelligent Computing—Proceedings of the Computing Conference; Springer: Cham, Switzerland, 2019; Volume 998, pp. 43–61. [Google Scholar] [CrossRef]
- Ciobanu, R.I.; Marin, R.C.; Dobre, C. Mobemu: A framework to support decentralized ad-hoc networking. In Modeling and Simulation in HPC and Cloud Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 87–119. [Google Scholar]
- Still, G.K. Static Crowd Density, 2019. Available online: https://www.gkstill.com/Support/crowd-density/CrowdDensity-1.html (accessed on 1 April 2021).
- Chancay-Garcia, L.; Hernández-Orallo, E.; Manzoni, P.; Calafate, C.T.; Cano, J.C. Evaluating and enhancing information dissemination in urban areas of interest using opportunistic networks. IEEE Access 2018, 6, 32514–32531. [Google Scholar] [CrossRef]
- Musolesi, M.; Mascolo, C. A Community Based Mobility Model for Ad Hoc Network Research. In Proceedings of the 2nd International Workshop on Multi-Hop Ad Hoc Networks: From Theory to Reality (REALMAN ’06), Florence, Italy, 26 May 2006; Association for Computing Machinery: New York, NY, USA, 2006; pp. 31–38. [Google Scholar] [CrossRef]
- Boldrini, C.; Conti, M.; Passarella, A. Users mobility models for opportunistic networks: The role of physical locations. In Proceedings of the Wireless Rural and Emergency Communications Conference (WRECOM 2007), Rome, Italy, 30 September–2 October 2007. [Google Scholar]
- Larsen, J.; Sapiezynski, P.; Stopczynski, A.; Mørup, M.; Theodorsen, R. Crowds, Bluetooth and Rock’n’Roll: Understanding Music Festival Participant Behavior. In Proceedings of the Sunbelt 2013, 33rd Sunbelt Social Networks Conference of the International Network for Social Network Analysis (INSNA 2013), Hamburg, Germany, 21–26 May 2013. [Google Scholar]
- Maslov, S.; Sneppen, K.; Zaliznyak, A. Detection of topological patterns in complex networks: Correlation profile of the internet. Phys. A Stat. Mech. Its Appl. 2004, 333, 529–540. [Google Scholar] [CrossRef]
- Hui, P.; Crowcroft, J.; Yoneki, E. BUBBLE Rap: Social-Based Forwarding in Delay-Tolerant Networks. IEEE Trans. Mob. Comput. 2011, 10, 1576–1589. [Google Scholar] [CrossRef]
- Hui, P.; Yoneki, E.; Chan, S.Y.; Crowcroft, J. Distributed Community Detection in Delay Tolerant Networks. In Proceedings of the 2nd ACM/IEEE International Workshop on Mobility in the Evolving Internet Architecture (MobiArch ’07), Kyoto, Japan, 27 August 2007; Association for Computing Machinery: New York, NY, USA, 2007. [Google Scholar] [CrossRef]
- Kärkkäinen, T.; Välimaa, M.; Roy, S.K.; Hyytiä, E.; Ott, J. Practical opportunistic content dissemination performance in dense network segments. Comput. Commun. 2018, 123, 65–80. [Google Scholar] [CrossRef]
- Marin, R.C.; Ciobanu, R.I.; Dobre, C. Improving opportunistic networks by leveraging device-to-device communication. IEEE Commun. Mag. 2017, 55, 86–91. [Google Scholar] [CrossRef]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and Focus: Efficient Mobility-Assisted Routing for Heterogeneous and Correlated Mobility. In Proceedings of the Fifth Annual IEEE International Conference on Pervasive Computing and Communications Workshops (PerComW’07), White Plains, NY, USA, 19–23 March 2007; pp. 79–85. [Google Scholar]
- Camps-Mur, A.D.; Garcia-Saavedra, P.S. Device to device communications with WiFi Direct: Overview and experimentation. IEEE Wirel. Commun. 2013, 20, 96–104. [Google Scholar] [CrossRef]
- Socievole, A.; Yoneki, E.; De Rango, F.; Crowcroft, J. ML-SOR: Message routing using multi-layer social networks in opportunistic communications. Comput. Netw. 2015, 81, 201–219. [Google Scholar] [CrossRef]







| Name | Spray Phase | Wait Phase |
|---|---|---|
| SWv1 | SWb | FC1 |
| SWv2 | SWb | FC2 |
| SWv3 | SWb | FC3 |
| SWv4 | if FC3 {SWb} else {SWs} | SW wait |
| SWv5 | if FC2 {SWb} else {SWs} | SW wait |
| SSW1 | if (FC2 or FC3) {SWb} else {SWs} | SW wait |
| SSW2 | if (FC2 or FC3) {SWb} elseif FC4 {SWb} else {SWs} | SW wait |
| SWv6 | if (FC2 and FC3) {SWb} else if FC1 {SWs} | SW wait |
| SWv7 | if FC3 {SWb} else if FC2 {SWs} | SW wait |
| Parameter | Value |
|---|---|
| Area | 30 × 20 m2 |
| Protocol | Bluetooth |
| Bluetooth range | 5 m |
| Wi-Fi Direct range | 30 m |
| Message size | 100 KB |
| Data memory | 5000 messages |
| Trace duration | 1 h |
| Group size | 5 |
| Parameter | Value |
|---|---|
| Nodes | 1700 |
| Contacts | 839,680 |
| Messages | 8282 |
| Maximum neighbors | 7 |
| Parameter | Value |
|---|---|
| Nodes | 1700 |
| Contacts | 683,945 |
| Messages | 8282 |
| Maximum neighbors | 7 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Manole, A.-Ș.; Ciobanu, R.-I.; Dobre, C.; Purnichescu-Purtan, R. Opportunistic Network Algorithms for Internet Traffic Offloading in Music Festival Scenarios. Sensors 2021, 21, 3315. https://doi.org/10.3390/s21103315
Manole A-Ș, Ciobanu R-I, Dobre C, Purnichescu-Purtan R. Opportunistic Network Algorithms for Internet Traffic Offloading in Music Festival Scenarios. Sensors. 2021; 21(10):3315. https://doi.org/10.3390/s21103315
Chicago/Turabian StyleManole, Aida-Ștefania, Radu-Ioan Ciobanu, Ciprian Dobre, and Raluca Purnichescu-Purtan. 2021. "Opportunistic Network Algorithms for Internet Traffic Offloading in Music Festival Scenarios" Sensors 21, no. 10: 3315. https://doi.org/10.3390/s21103315
APA StyleManole, A.-Ș., Ciobanu, R.-I., Dobre, C., & Purnichescu-Purtan, R. (2021). Opportunistic Network Algorithms for Internet Traffic Offloading in Music Festival Scenarios. Sensors, 21(10), 3315. https://doi.org/10.3390/s21103315






