A Distributed Oracle Using Intel SGX for Blockchain-Based IoT Applications
Abstract
1. Introduction
- Support for data availability: DiOr-SGX consists of multiple distributed oracle servers, where a leader oracle server is elected for collaboration among them. This ensures data availability even when a single oracle server fails.
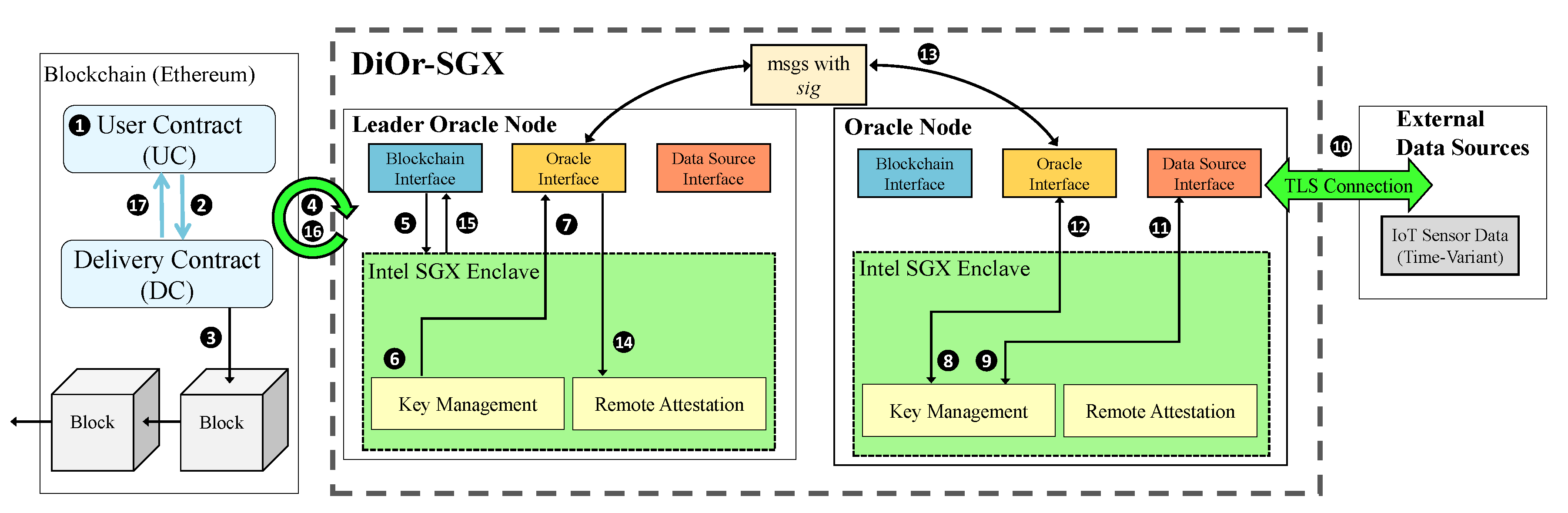
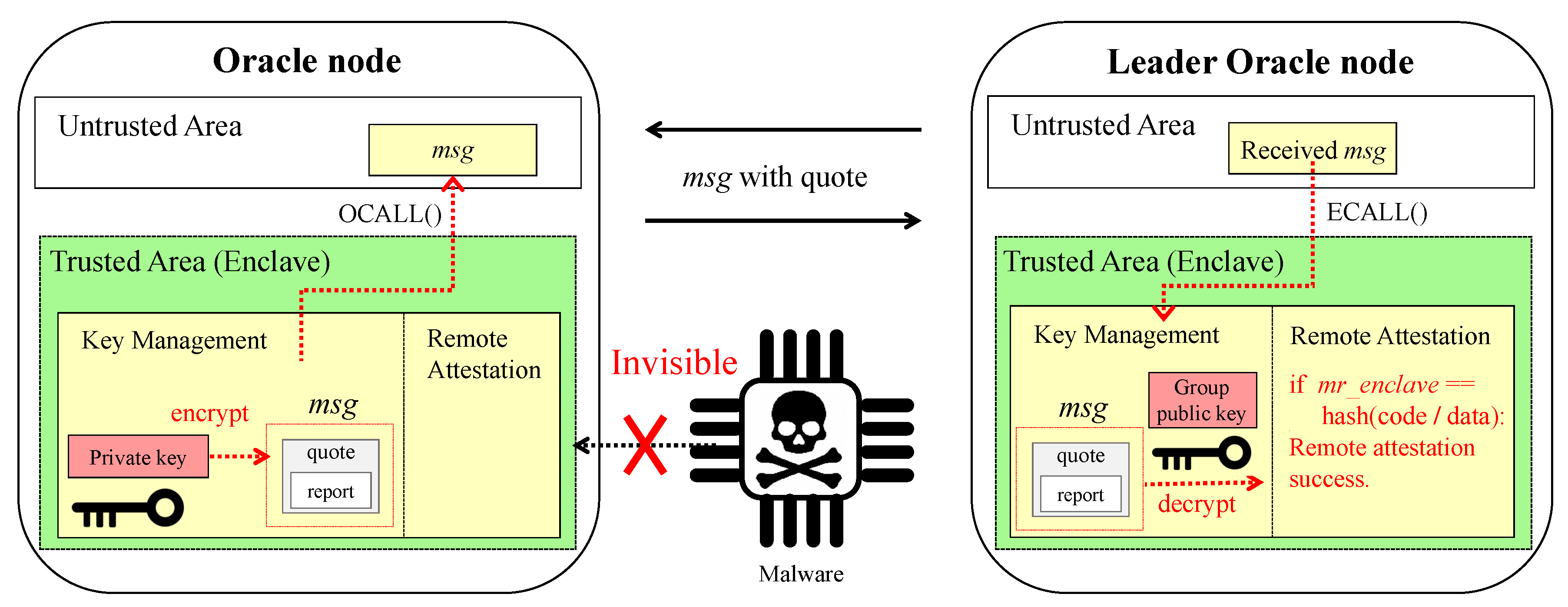
- Support for secure oracle protocol using Intel SGX and TLS: DiOr-SGX guarantees data integrity through Intel SGX and Transport Layer Security (TLS) communication with external data sources. Since DiOr-SGX performs TLS communication for pulling external data inside the SGX enclave of each oracle server, data manipulation is impossible.
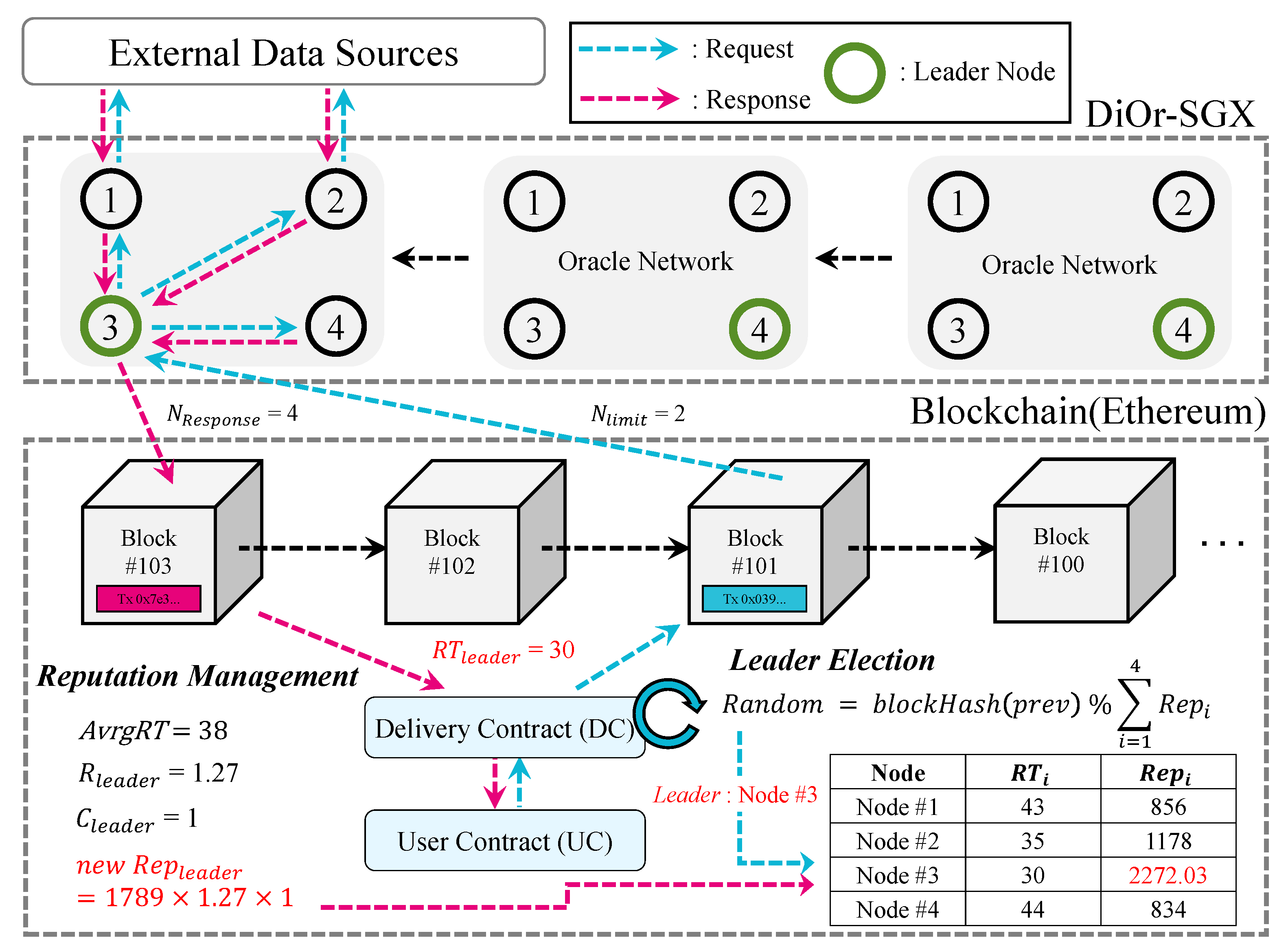
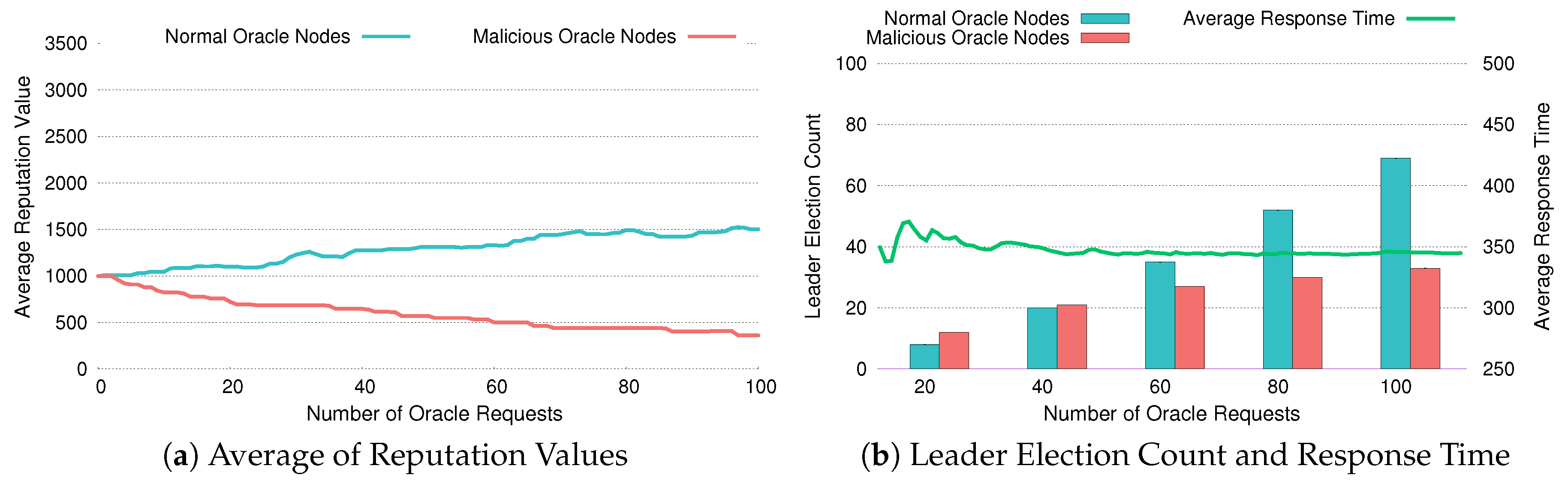
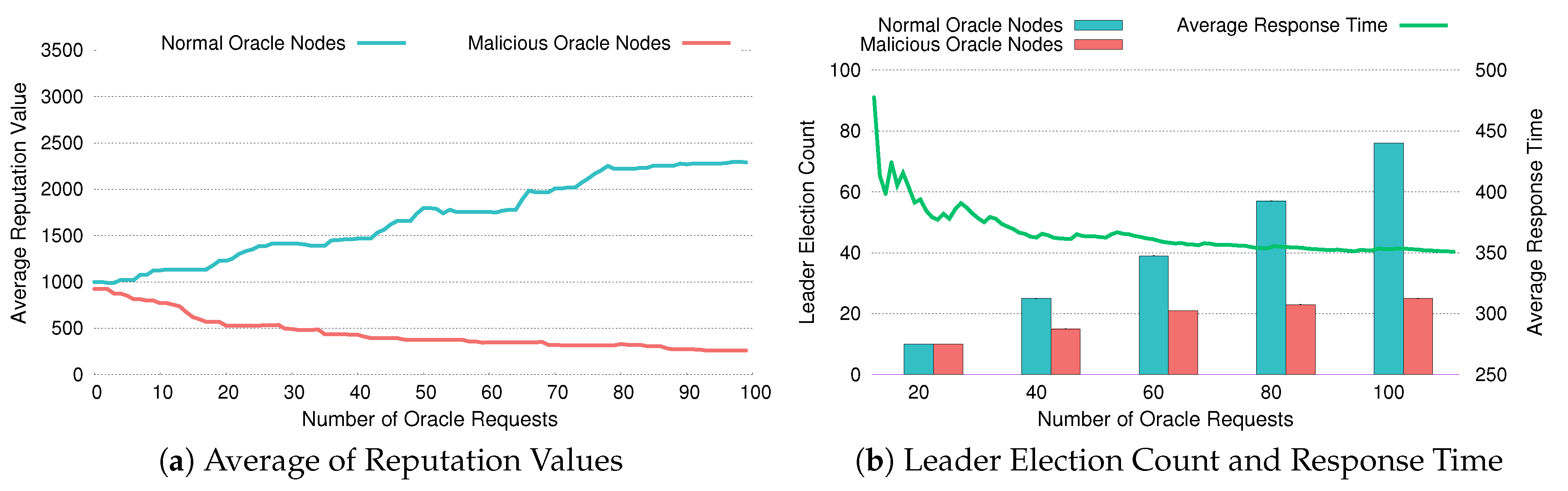
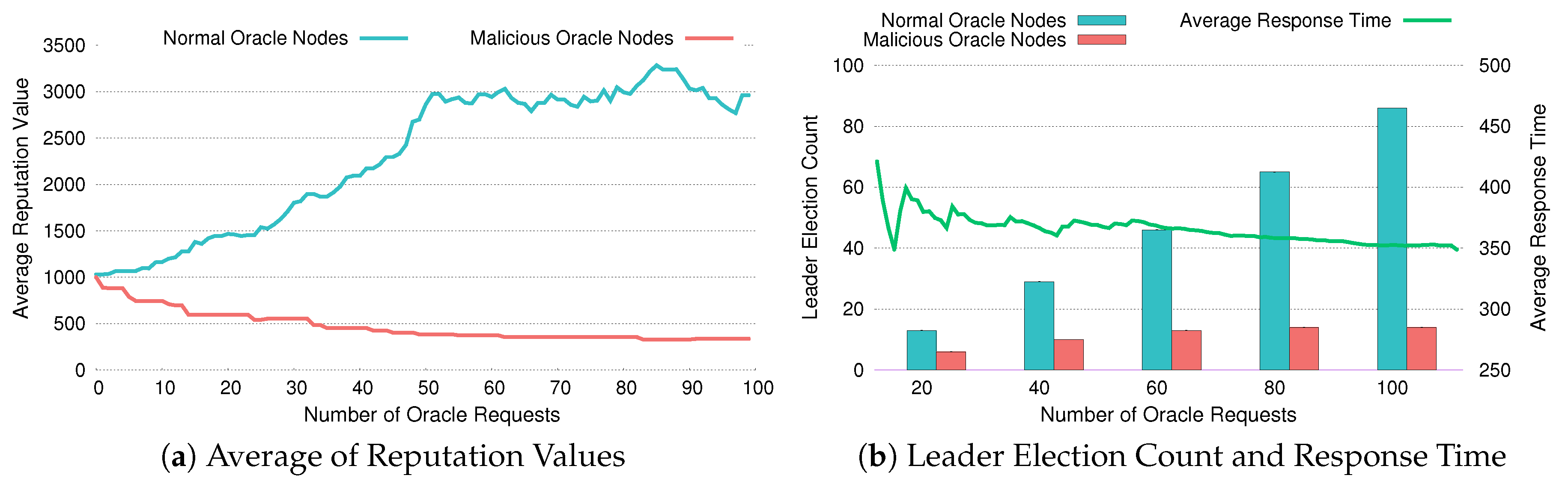
- Support for time-variant IoT data using reputation system: DiOr-SGX can provide time-variant IoT data into the blockchain. For time-variant IoT data, response time is important. DiOr-SGX elects a leader oracle server through a reputation system based on previous response times. This allows DiOr-SGX to provide a relatively consistent response time even if a malicious leader oracle server exists among multiple oracle servers.
- Real implementation: DiOr-SGX has been implemented over Ethereum blockchain [22] and its performance is compared with other competitors. The benchmarking results show that DiOr-SGX ensures response time even in an environment where a malicious oracle server exists, while the decrease in response time of 14% compared to the existing centralized oracles is minimal.
2. Background and Motivation
2.1. Ethereum and Smart Contract
2.2. Blockchain Oracle Problem
2.3. Intel SGX
2.4. Motivation
3. Related Work
4. Design and Implementation
4.1. Overall Architecture
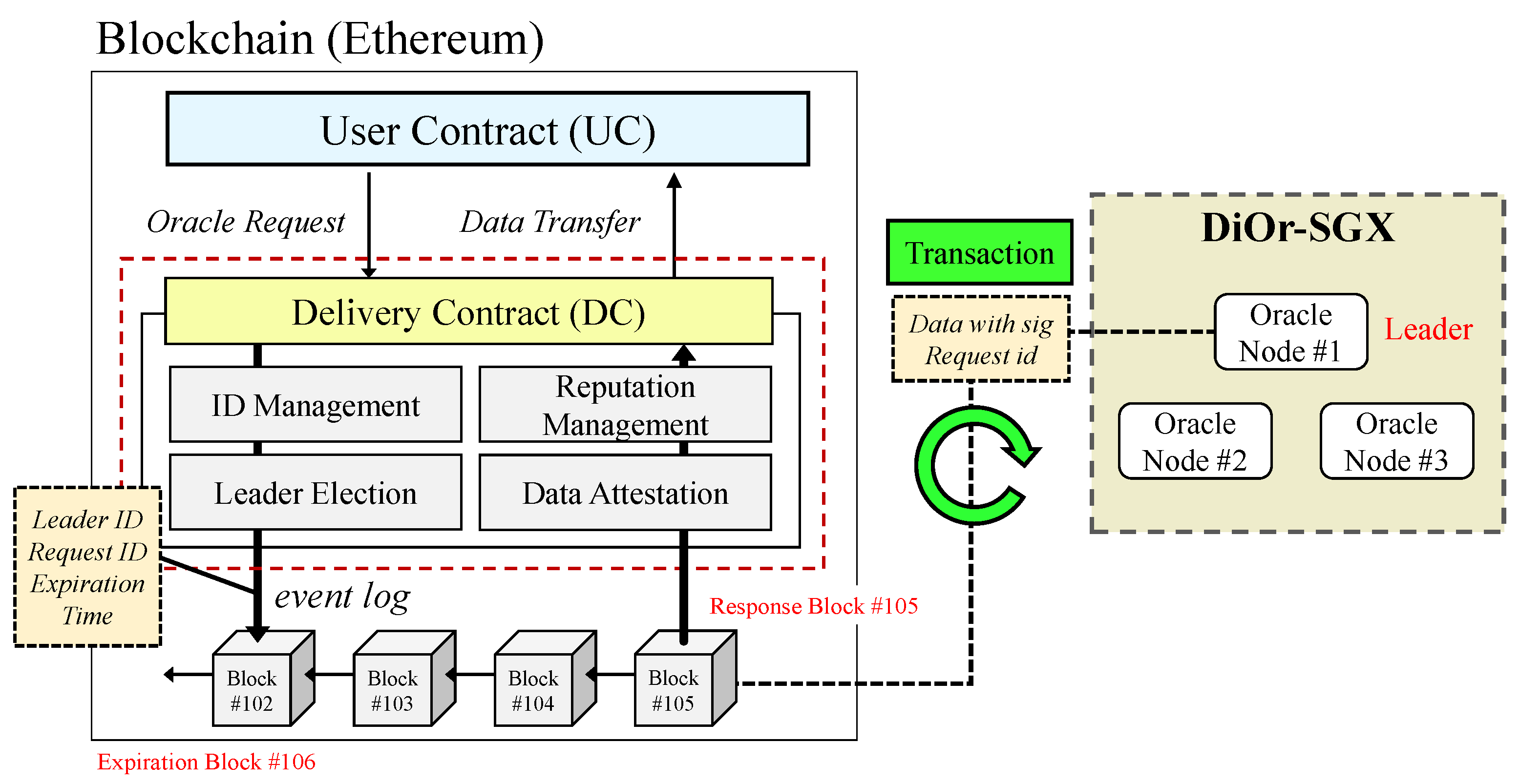
4.2. Delivery Contract
4.3. Securing Oracle Node Using Intel SGX
4.4. Reputation Management and Leader Election
| Algorithm 1: Reputation Management and Leader Election Algorithm |
| Require: |
| blockHash(previous): Hash of previous block |
| block#(response): Block number of response time |
| block#(request): Block number of request time |
| Repi: Reputation of each oracle node |
| procedure Reputation_Management(): |
| 1: sum ← 0, i ← 1 |
| 2: RTleader = (block#(response) − block#(request)) × blockInterval |
| 3: while i ≤ Noracle do |
| 4: sum += RTi |
| 5: i ≤ i + 1 |
| end |
| 6: AvrgRT = sum/Noracle |
| 7: Rleader = AvrgRT/RTleader |
| 8: Cleader = min(Nresponse/Nlimit, 1) |
| 9: Repleader = Repleader × Rleader × Cleader |
| 10: |
| procedure Leader_Election(): |
| 11: sum ← 0, i ← 1 |
| 12: while i ≤ Noracle do |
| 13: sum += Repi |
| 14: i ← i + 1 |
| end |
| 15: mod = blockHash(previous)%sum |
| 16: while mod ≥ 0 do |
| 17: mod = mod − Repi |
| 18: if mod < 0 then |
| 19: i-th oracle node is elected as a leader node |
| end |
| 20: i ← i + 1 |
| end |
5. Performance Evaluation
5.1. Experiment Setup
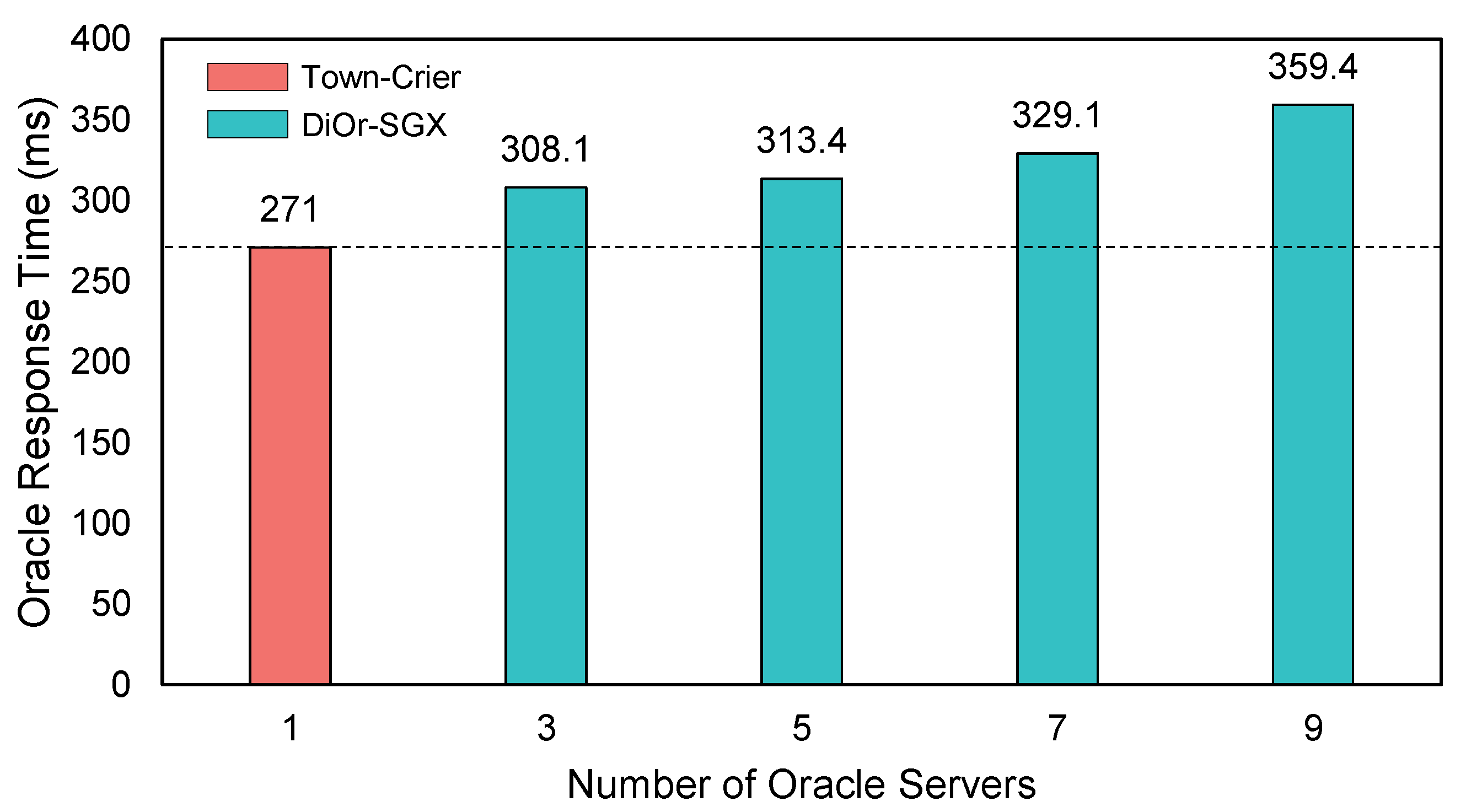
5.2. Evaluation of Response Time
5.3. Evaluation of Reputation System
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System; Technical Report; Manubot; 2019. [Google Scholar]
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on E-health Networking, Applications and Services (Healthcom), Munich, Germany, 14–17 September 2016; pp. 1–3. [Google Scholar]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Korea, 19–22 February 2017; pp. 464–467. [Google Scholar]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar]
- John, M. ShipChain Whitepaper; ShipChain: Los Angeles, CA, USA, 2018. [Google Scholar]
- Stevens, G.C. Integrating the supply chain. Int. J. Phys. Distrib. Mater. Manag. 1989, 19, 3–8. [Google Scholar] [CrossRef]
- Irina, C.; David, W.; Asim, N. AutoCoin Whitepaper: Revolutionizing an Industry That Has Earned Its Reputation for Dishonesty; AutoCoin: North London, UK, 2018. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Bernani, T. Oraclize; London, UK, 2016; Available online: http://www.oraclize.it (accessed on 10 May 2020).
- Zhang, F.; Cecchetti, E.; Croman, K.; Juels, A.; Shi, E. Town crier: An authenticated data feed for smart contracts. In Proceedings of the 2016 aCM sIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 270–282. [Google Scholar]
- Adler, J.; Berryhill, R.; Veneris, A.; Poulos, Z.; Veira, N.; Kastania, A. Astraea: A decentralized blockchain oracle. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1145–1152. [Google Scholar]
- Kamiya, R. Shintaku: An End-to-End-Decentralized Generalpurpose Blockchain Oracle System. 2018. Available online: https://gitlab.com/shintaku-group/paper/blob/master/shintaku.pdf (accessed on 26 March 2020).
- Ellis, A.S.; Juels, S.N. Chainlink: A Decentralized Oracle Network. Retrieved March 2017, 11, 2018. [Google Scholar]
- Bahga, A.; Madisetti, V.K. Blockchain platform for industrial internet of things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef]
- Park, J.S.; Youn, T.Y.; Kim, H.B.; Rhee, K.H.; Shin, S.U. Smart contract-based review system for an IoT data marketplace. Sensors 2018, 18, 3577. [Google Scholar] [CrossRef] [PubMed]
- Ether Betball. 2019. Available online: https://eth-bet.com/f (accessed on 14 March 2020).
- Pee, S.J.; Nans, J.H.; Jans, J.W. A Simple Blockchain-based Peer-to-Peer Water Trading System Leveraging Smart Contracts. In Proceedings of the International Conference on Internet Computing (ICOMP). The Steering Committee of The World Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp), Dong Hoi City, Vietnam, 19–21 March 2018; pp. 63–68. [Google Scholar]
- Dowling, M.D.; Thompson, A.R.; Levitan, A.; Severino, R.A. International Trade Finance Blockchain System. U.S. Patent App. 15/639,986, September 2018. [Google Scholar]
- Papadodimas, G.; Palaiokrasas, G.; Litke, A.; Varvarigou, T. Implementation of smart contracts for blockchain based IoT applications. In Proceedings of the 2018 9th International Conference on the Network of the Future (NOF), Poznan, Poland, 19–21 November 2018; pp. 60–67. [Google Scholar]
- Zinonos, Z.; Christodoulou, P.; Andreou, A.; Chatzichristofis, S. ParkChain: An IoT Parking Service Based on Blockchain. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini, Greece, 29–31 May 2019; pp. 687–693. [Google Scholar]
- Costan, V.; Devadas, S. Intel SGX Explained. IACR Cryptol. EPrint Arch. 2016, 2016, 1–118. [Google Scholar]
- Buterin, V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform. 2014. Available online: https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf (accessed on 21 March 2020).
- Dannen, C. Introducing Ethereum and Solidity; Springer: Berlin/Heidelberg, Germany, 2017; Volume 1. [Google Scholar]
- Delmolino, K.; Arnett, M.; Kosba, A.; Miller, A.; Shi, E. A Programmer’s Guide to Ethereum and Serpent. Available online: Https://mc2-umd.github.io/ethereumlab/docs/serpent_tutorial.pdf (accessed on 6 May 2016).
- Likar, K.; Jevšnik, M. Cold chain maintaining in food trade. Food Control 2006, 17, 108–113. [Google Scholar] [CrossRef]
- TLSnotary—A Mechanism for Independently Audited https Sessions. 2014. Available online: https://tlsnotary.org/TLSNotary.pdf (accessed on 6 March 2020).
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the OSDI, Cambridge, MA, USA, 22 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Russinovich, M. Introducing Azure Confidential Computing; Microsoft: Redmond, DC, USA, 2017. [Google Scholar]
- Open Enclave: Build Trusted Execution Environment Based Applications with an Open Source SDK; GitHub: San Francisco, CA, USA, 2019.
- Seoul Average Air Pollution Information. 2019. Available online: https://cleanair.seoul.go.kr (accessed on 26 December 2019).
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Divya, M.; Biradar, N.B. IOTA-next generation block chain. Int. J. Eng. Comput. Sci. 2018, 7, 23823–23826. [Google Scholar]
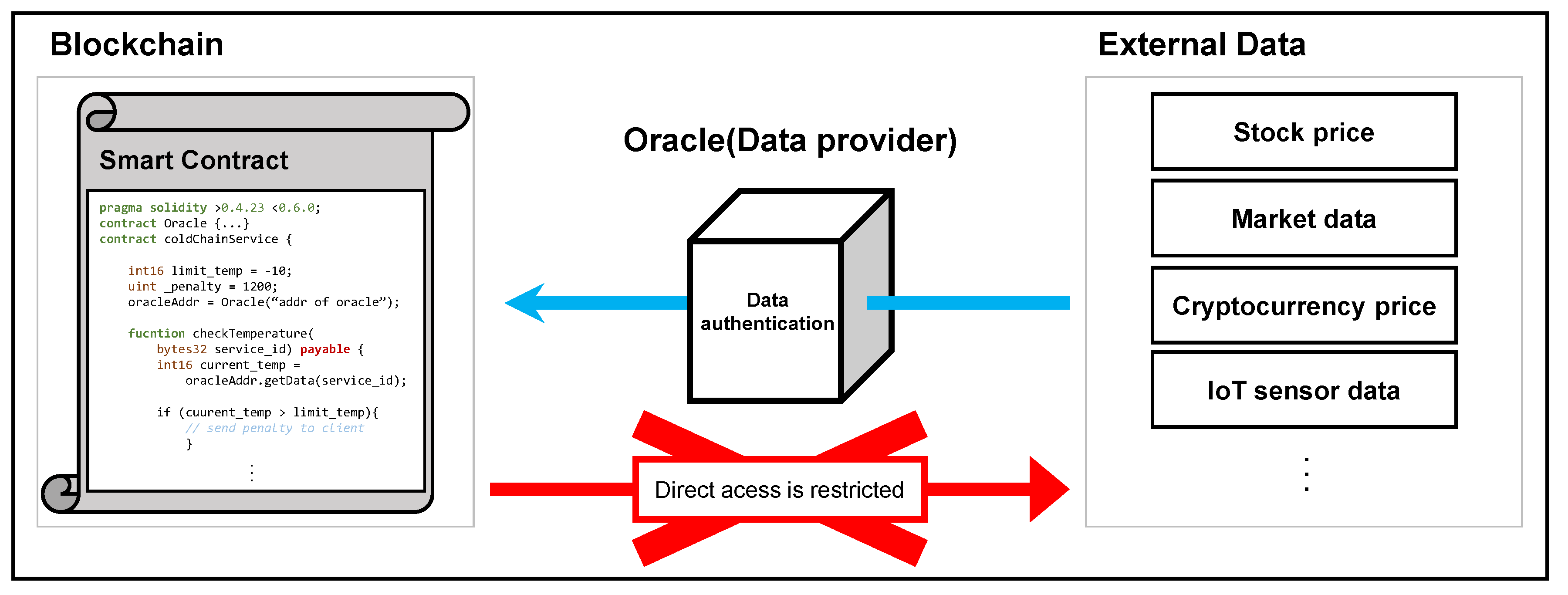
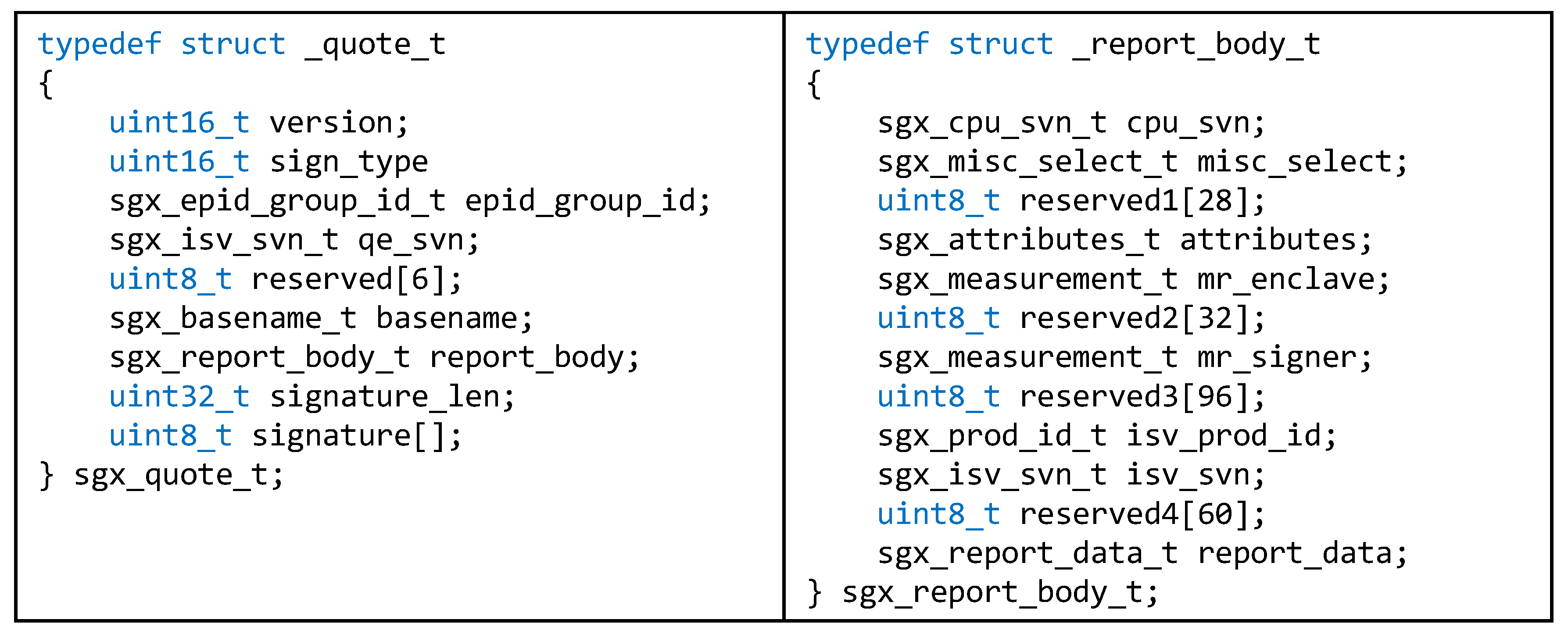
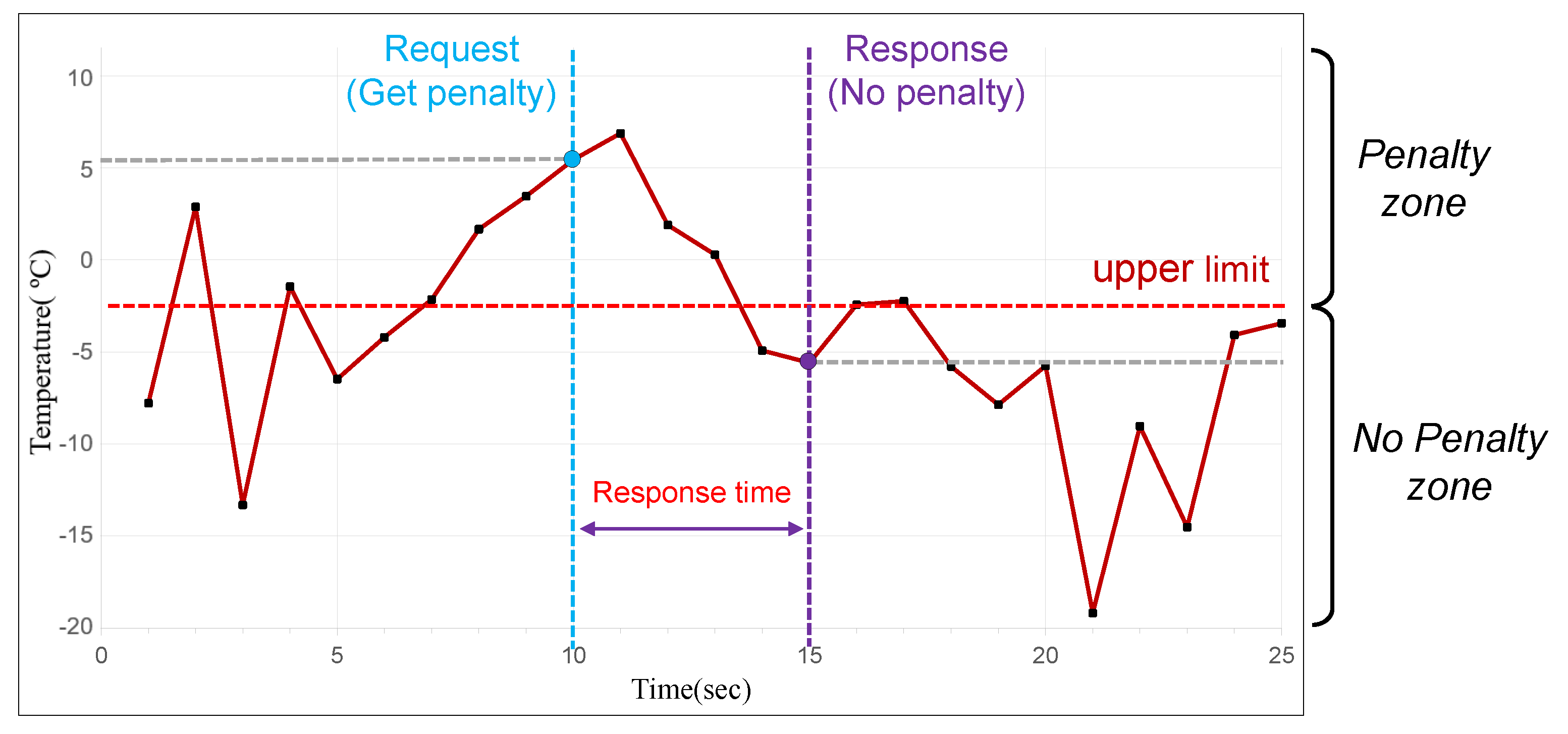
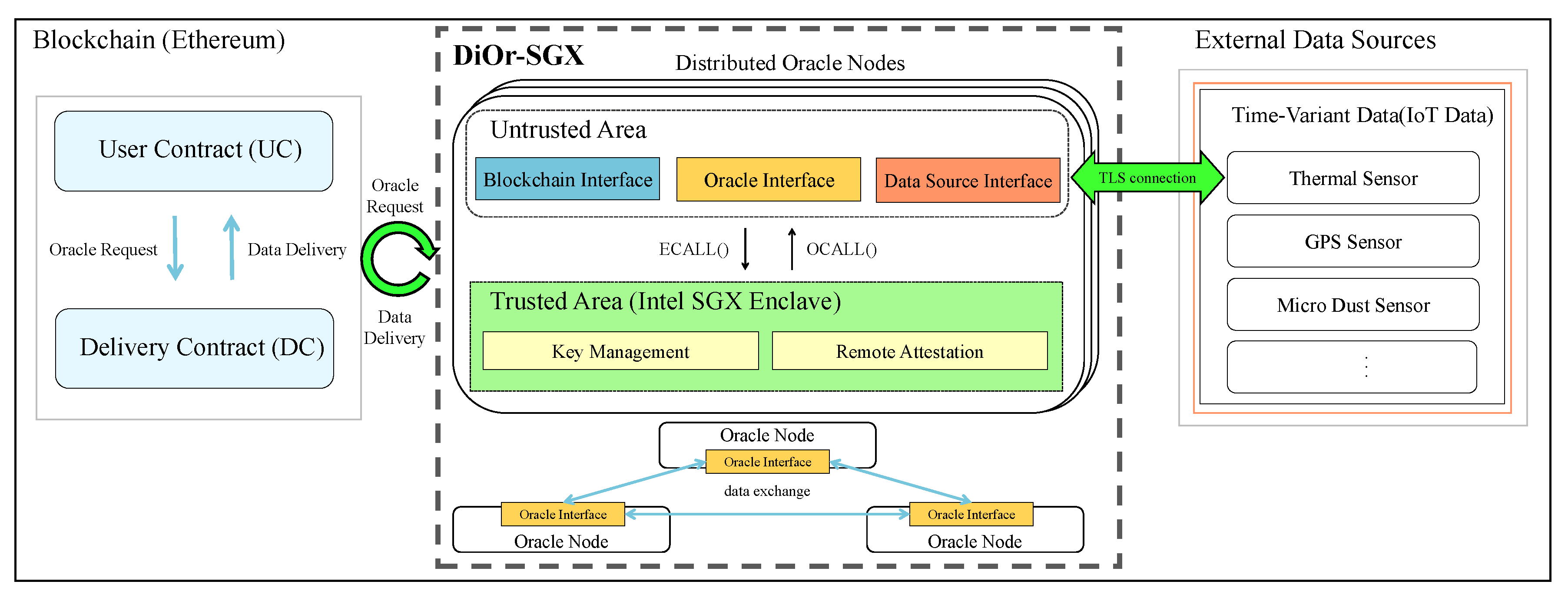
| Oracle | Data | Data | Support Time | Guarantee |
|---|---|---|---|---|
| Protocols | Availability | Integrity | Variant Data | Response Time |
| Oraclize [9] | × | △ | ◯ | × |
| Town-crier [10] | × | ◯ | △ | × |
| ASTRAEA [11] | ◯ | × | × | × |
| Shintaku [12] | ◯ | × | × | × |
| Chainlink [13] | ◯ | × | × | × |
| DiOr-SGX (proposed) | ◯ | ◯ | ◯ | ◯ |
| Activity | Town-Crier | N = 3 | N = 5 | N = 7 | N = 9 | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| Time | Ratio | Time | Ratio | Time | Ratio | Time | Ratio | Time | Ratio | |
| Msg Generation | 0 | 0 | 20 | 6.5 | 32 | 10.2 | 49 | 14.8 | 65 | 18.0 |
| Validation | 0 | 0 | 4.1 | 1.3 | 6.4 | 2.0 | 9.1 | 2.7 | 10.4 | 2.8 |
| Tx Generation | 20 | 7.4 | 20 | 6.5 | 19 | 6.0 | 19 | 5.7 | 19 | 5.2 |
| Subtotal | 20 ms | 44.1 ms | 57.4 ms | 77.1 ms | 94.4 ms | |||||
| TLS connection | 251 | 92.6 | 264 | 85.7 | 256 | 81.7 | 252 | 76.5 | 265 | 73.8 |
| Total | 271 ms | 308.1 ms | 313.4 ms | 329.1 ms | 359.4 ms | |||||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Woo, S.; Song, J.; Park, S. A Distributed Oracle Using Intel SGX for Blockchain-Based IoT Applications. Sensors 2020, 20, 2725. https://doi.org/10.3390/s20092725
Woo S, Song J, Park S. A Distributed Oracle Using Intel SGX for Blockchain-Based IoT Applications. Sensors. 2020; 20(9):2725. https://doi.org/10.3390/s20092725
Chicago/Turabian StyleWoo, Sangyeon, Jeho Song, and Sungyong Park. 2020. "A Distributed Oracle Using Intel SGX for Blockchain-Based IoT Applications" Sensors 20, no. 9: 2725. https://doi.org/10.3390/s20092725
APA StyleWoo, S., Song, J., & Park, S. (2020). A Distributed Oracle Using Intel SGX for Blockchain-Based IoT Applications. Sensors, 20(9), 2725. https://doi.org/10.3390/s20092725






