Guided Electromagnetic Wave Technique for IC Authentication
Abstract
1. Introduction
2. Counterfeit Detection and Avoidance Techniques
2.1. Classical Techniques
2.2. PUF-Based Techniques
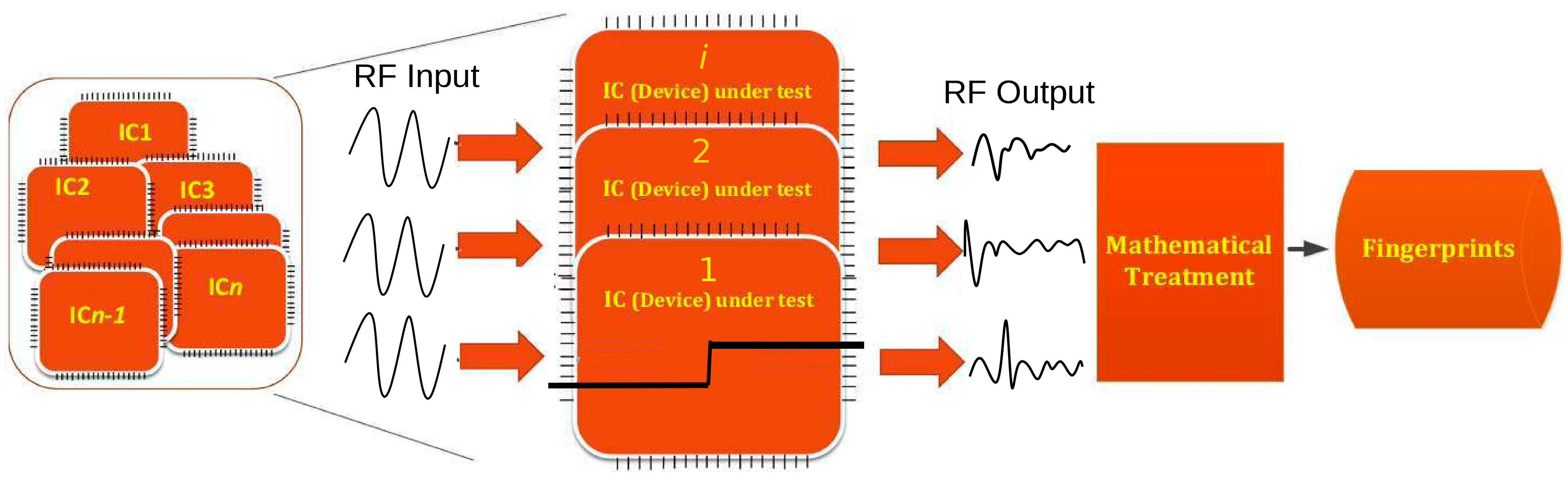
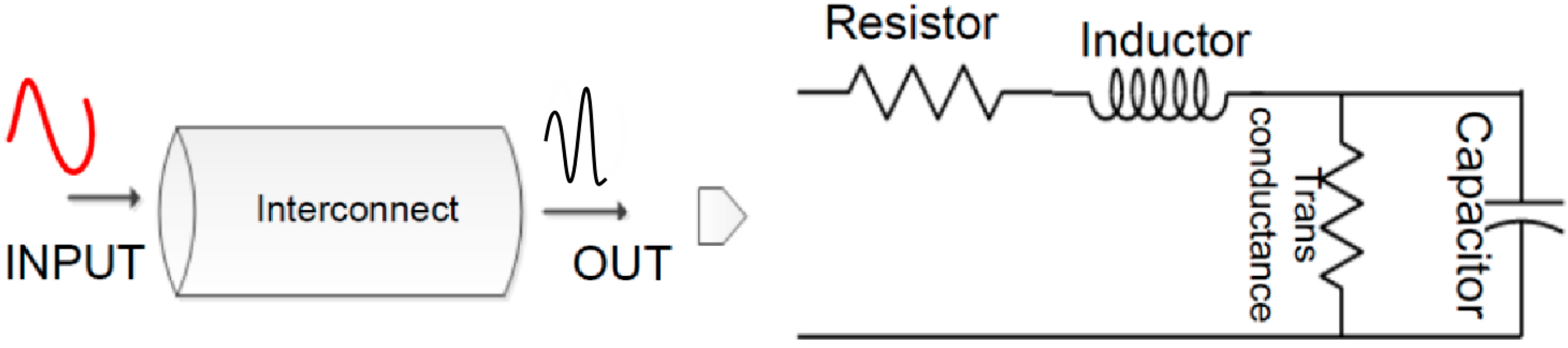
3. Guided EM Wave Principle
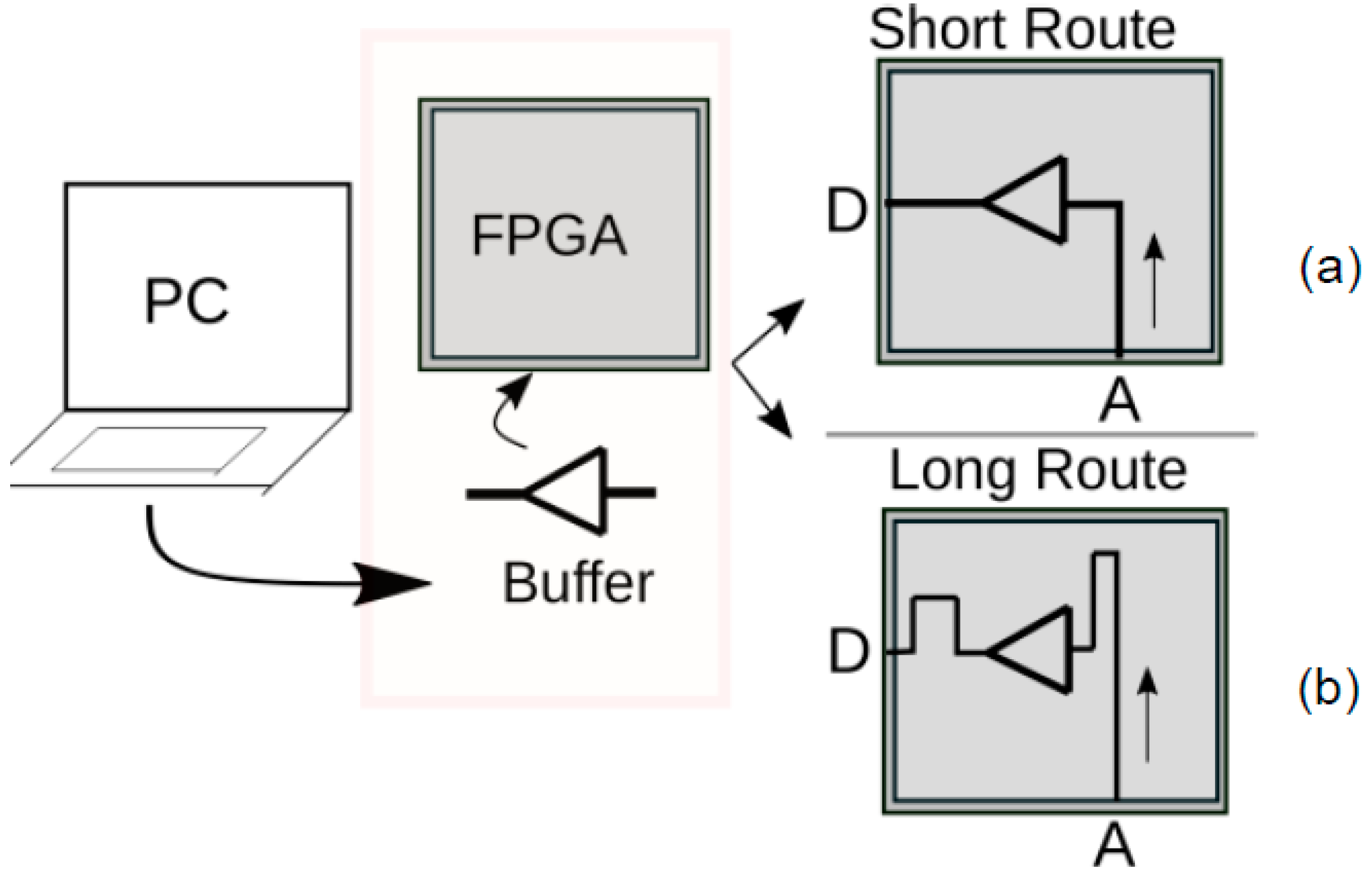
3.1. Implementation Overview
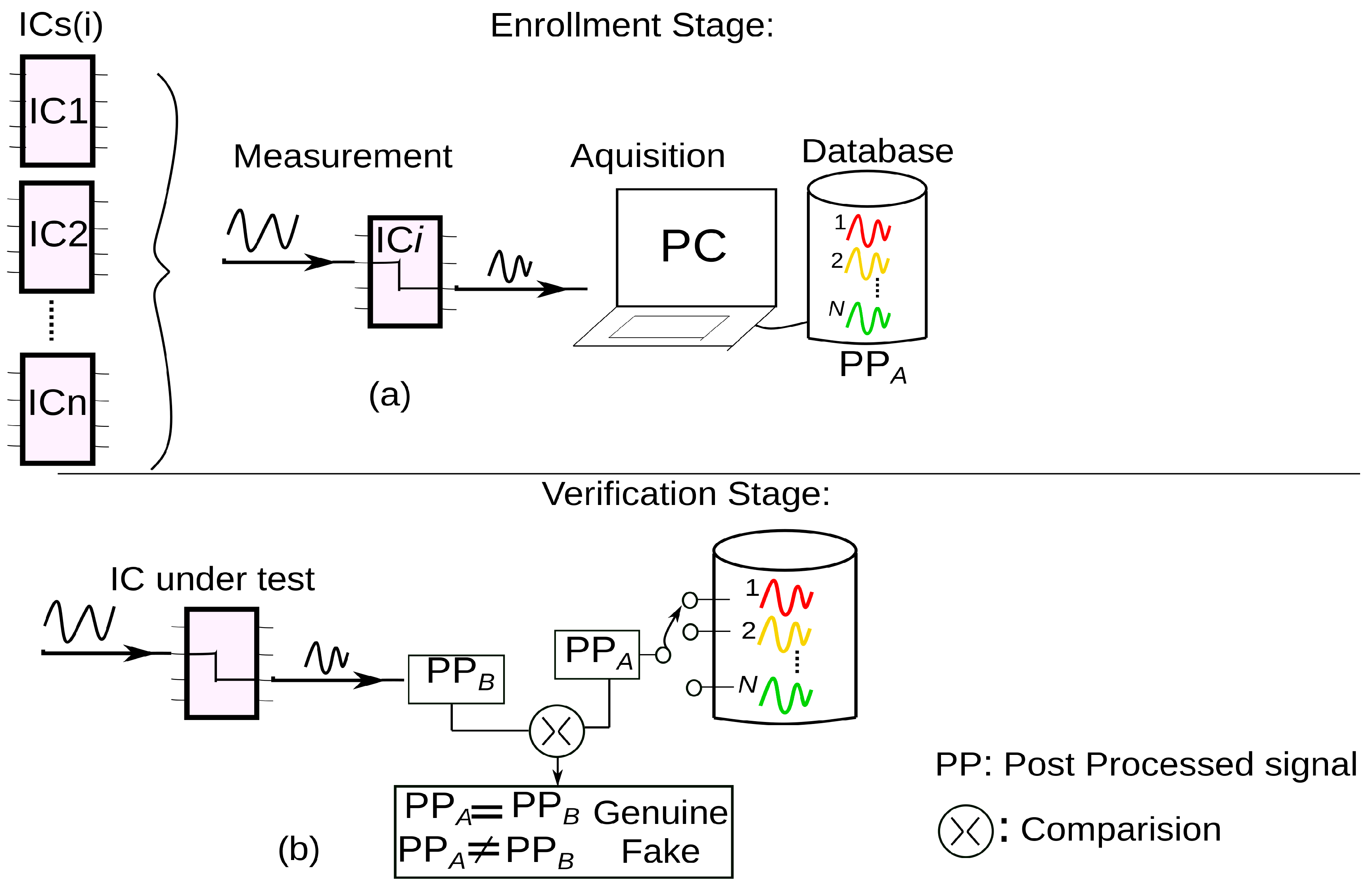
3.2. Authentication Steps
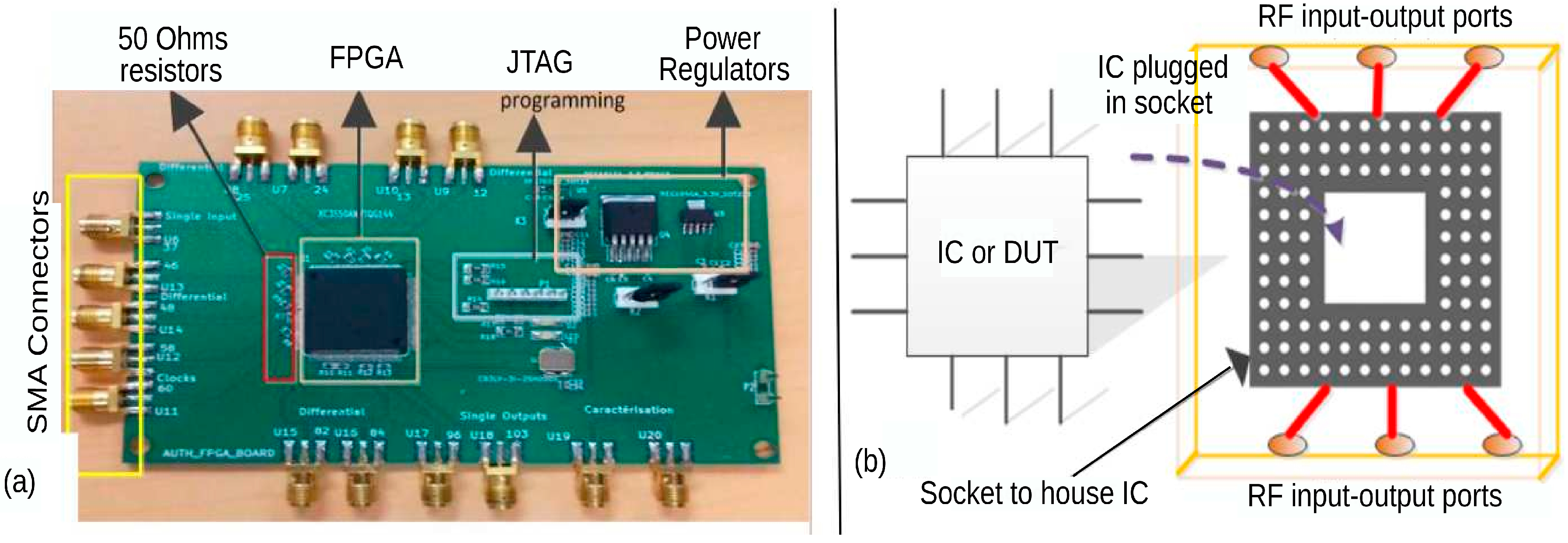
4. Measurement Bench
5. Implementations in FPGA: Exploit PV Effects
5.1. FPGA Programmed Circuit
5.2. Multiple Routes between IO Pins
5.3. Experimental Steps
- Select the DUT to be authenticated.
- Adapt and customize a testbench to carry out the experiments efficiently.
- Select required instruments and determine various electrical parameters that ascertain to correct operation of the DUT for proper experimentation.
- Select the technique that can accentuate the exploitation of PV effects.
- Record the response and post-process it numerically to determine statistical difference between responses of the DUTs.
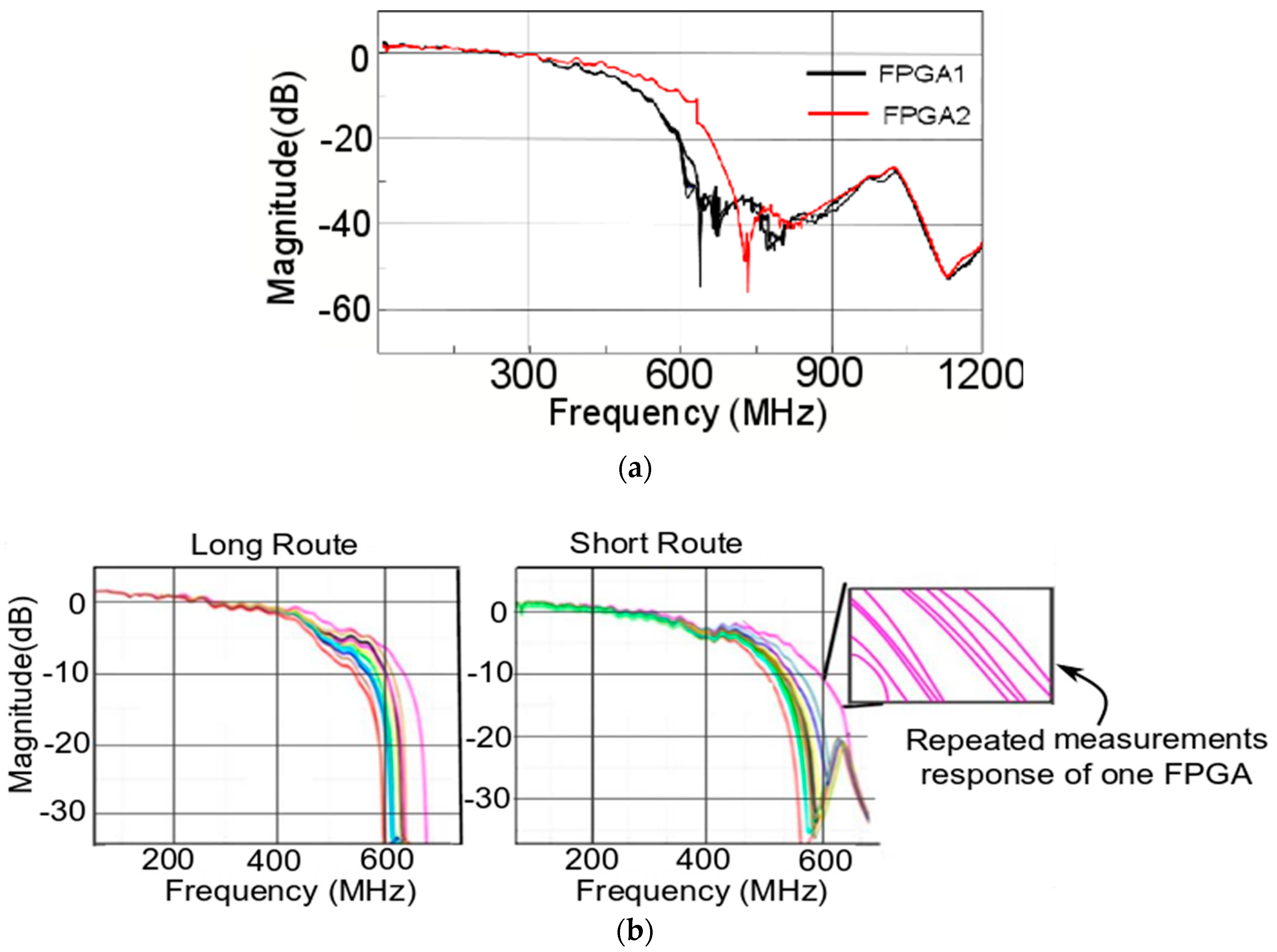
6. Measurement Results
6.1. S21 Parameter Response
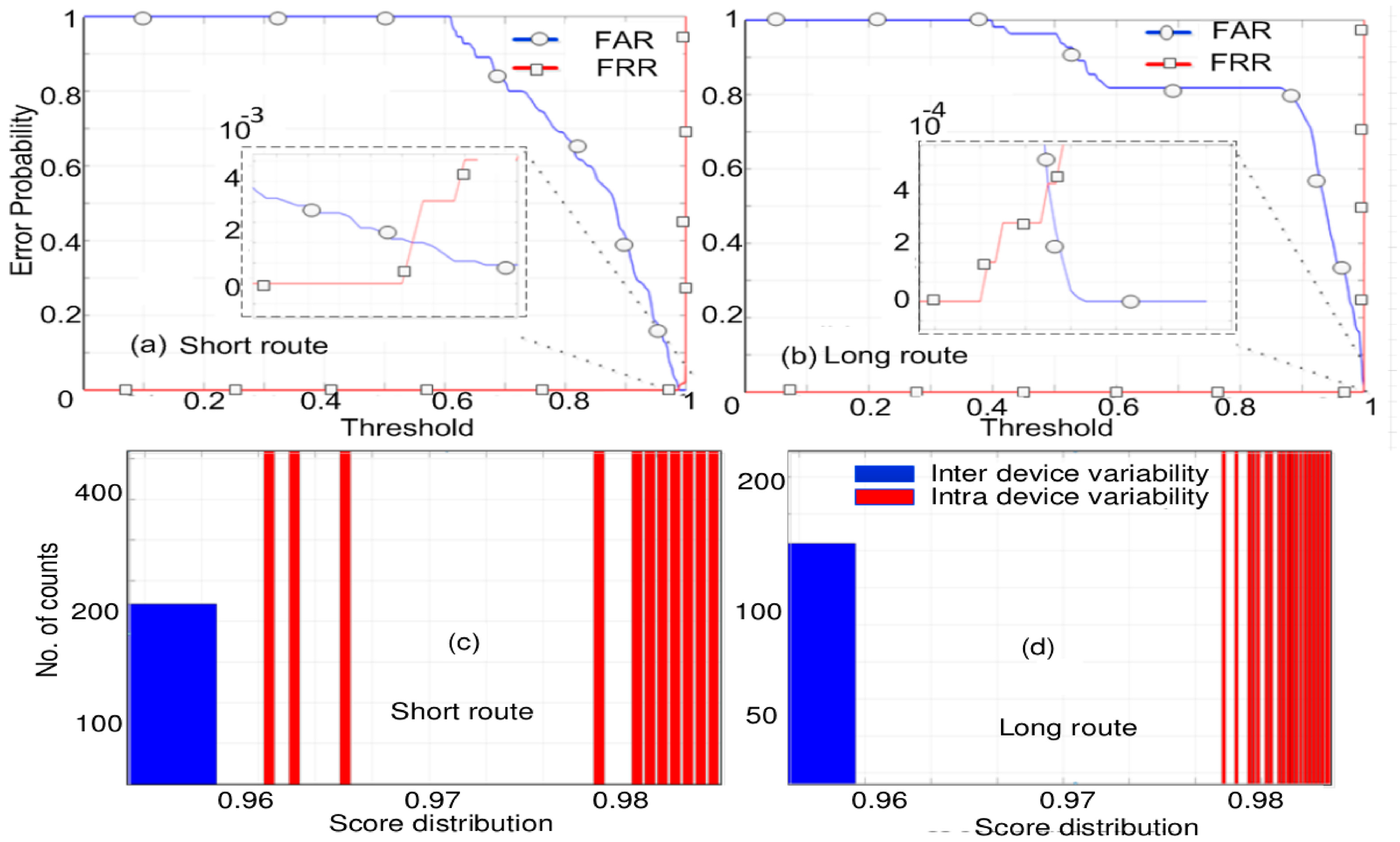
6.2. Statistical Distribution of the Response
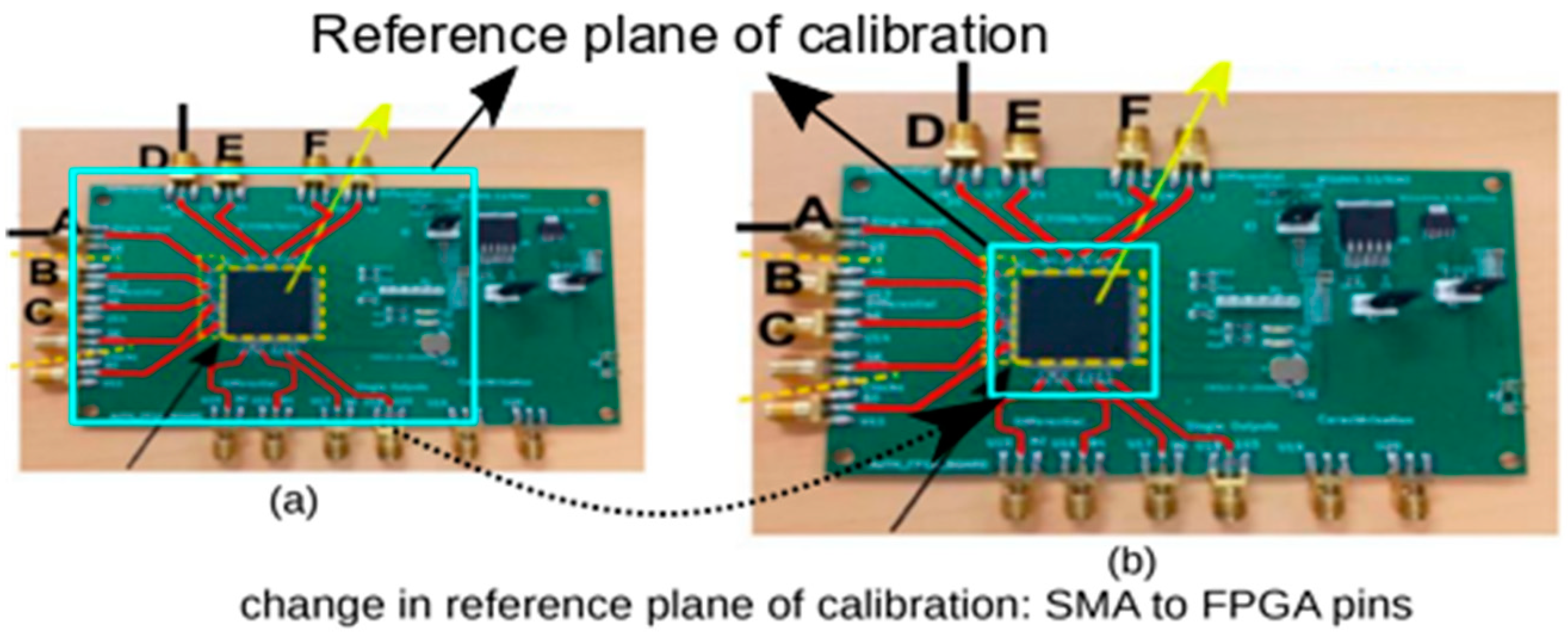
6.3. Mitigating Systematic Errors
6.4. Differential Setting for Error Removal
7. Conclusion and Prospects
7.1. Inference
7.2. Limitations of the Proposed Technique
7.3. Conclusions and Future Perspectives
Author Contributions
Funding
Conflicts of Interest
References
- Huang, K.; Carulli, J.M.; Makris, Y. Counterfeit electronics: A rising threat in the semiconductor manufacturing industry. In Proceedings of the 2013 IEEE International Test Conference (ITC), Anaheim, CA, USA, 6–13 September 2013; pp. 1–4. [Google Scholar] [CrossRef]
- Tehranipoor, M.; Forte, D. Tutorial T4: All You Need to Know about Hardware Trojans and Counterfeit ICs. In Proceedings of the IEEE 2014 27th International Conference on VLSI Design and 2014 13th International Conference on Embedded Systems, Mumbai, India, 5–9 January 2014; pp. 9–10. [Google Scholar] [CrossRef]
- Ahmed, M.M.; Hely, D.; Barbot, N.; Siragusa, R.; Perret, E.; Bernier, M.; Garet, F. Radiated Electromagnetic Emission for Integrated Circuit Authentication. IEEE Microw. Wirel. Compon. Lett. 2017, 27, 1028–1030. [Google Scholar] [CrossRef]
- Guin, U.; Huang, K.; DiMase, D.; Carulli, J.M.; Tehranipoor, M.; Makris, Y. Counterfeit integrated circuits: A rising threat in the global semiconductor supply chain. Proc. IEEE 2014, 102, 1207–1228. [Google Scholar] [CrossRef]
- Ahmed, M.M.; Hely, D.; Perret, E.; Barbot, N.; Siragusa, R.; Bernier, M.; Garet, F. Robust and Noninvasive IC Authentication Using Radiated Electromagnetic Emissions. J. Hardw. Syst. Secur. 2019, 3, 273–288. [Google Scholar] [CrossRef]
- Jeong, M.; Lee, C.; Kim, J.; Choi, J.; Toh, K.; Kim, J. Changeable Biometrics for Appearance Based Face Recognition. In Proceedings of the 2006 Biometrics Symposium: Special Session on Research at the Biometric Consortium Conference, Baltimore, MD, USA, 19–21 September 2006; pp. 1–5. [Google Scholar] [CrossRef]
- Voloshynovskiy, S.; Holotyak, T.; Bas, P. Physical object authentication: Detection-theoretic comparison of natural and artificial randomness. In Proceedings of the 2016 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Shanghai, China, 20–25 March 2016; pp. 2029–2033. [Google Scholar] [CrossRef]
- Serov, V.N.; Fetisov, L.Y.; Morozov, A.A.; Fetisov, Y.K. Threshold Magnetic Field Sensor Based on the Oscillator with a Magnetosensitive Piezoelectric Transducer in the Feedback. IEEE Sens. J. 2015, 15, 6409–6412. [Google Scholar] [CrossRef]
- Kurzawski, P.; Lazic, I.; Hagleitner, C.; Hierlemann, A.; Baltes, H. Multi-transducer recordings from a single-chip gas sensor system coated with different polymers. In Proceedings of the TRANSDUCERS ’03. 12th International Conference on Solid-State Sensors, Actuators and Microsystems. Digest of Technical Papers (Cat. No.03TH8664), Boston, MA, USA, 8–12 June 2003; Volume 2, pp. 1359–1362. [Google Scholar] [CrossRef]
- Song, P.; Stellari, F.; Weger, A. Counterfeit IC detection using light emission. In Proceedings of the IEEE 2014 International Test Conference, Seattle, WA, USA, 20–23 October 2014; pp. 1–8. [Google Scholar] [CrossRef]
- Ahmed, M.M.; Hely, D.; Barbot, N.; Siragusa, R.; Perret, E.; Bernier, M.; Garet, F. Towards a robust and efficient EM based authentication of FPGA against counterfeiting and recycling. In Proceedings of the 2017 19th International Symposium on Computer Architecture and Digital Systems (CADS), Kish Island, Iran, 21–22 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Guin, U.; DiMaes, D.; Tehranipoor, M. Counterfeit Integrated Circuits: Detection, Avoidance, and the Challenges Ahead. J. Electron. Test. 2014, 30, 9–23. [Google Scholar] [CrossRef]
- He, K.; Huang, X.; Tan, S.X. EM-based on-chip aging sensor for detection and prevention of counterfeit and recycled ICs. In Proceedings of the 2015 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, TX, USA, 2–6 November 2015; pp. 146–151. [Google Scholar] [CrossRef]
- Herder, C.; Yu, M.; Koushanfar, F.; Devadas, S. Physical Unclonable Functions and Applications: A Tutorial. Proc. IEEE 2014, 102, 1126–1141. [Google Scholar] [CrossRef]
- Maes, R.; Herrewege, A.; Van Verbauwhede, I. PUFKY: A Fully Functional PUF-Based Cryptographic Key Generator. In Proceedings of the BT—Cryptographic Hardware and Embedded Systems—CHES 2012—14th International Workshop, Leuven, Belgium, 9–12 September 2012. [Google Scholar] [CrossRef]
- Rührmair, U.; van Dijk, M. PUFs in Security Protocols: Attack Models and Security Evaluations. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 286–300. [Google Scholar] [CrossRef]
- Ghosh, S.; Roy, K. Parameter Variation Tolerance and Error Resiliency: New Design Paradigm for the Nanoscale Era. Proc. IEEE 2010, 98, 1718–1751. [Google Scholar] [CrossRef]
- Aryanpour, A.; Cowan, G.E.R. A circuit design and fabrication approach to address global process variation. In Proceedings of the 2009 52nd IEEE International Midwest Symposium on Circuits and Systems, Cancun, Mexico, 2–5 August 2009; pp. 455–458. [Google Scholar] [CrossRef]
- Jargon, J.A.; Williams, D.F.; Sanders, A. The Relationship Between Switch-Term-Corrected Scattering-Parameters and Wave-Parameters Measured with a Two-Port Vector Network Analyzer. IEEE Microw. Wirel. Compon. Lett. 2018, 28, 951–953. [Google Scholar] [CrossRef]
- Yanagi, T.; Sakairi, H.; Otake, H.; Kuroda, N.; Kitagawa, S.; Hashimoto, N.; Takeda, R.; Nakahara, K. Circuit simulation of a silicon-carbide MOSFET considering the effect of the parasitic elements on circuit boards by using S-parameters. In Proceedings of the 2018 IEEE Applied Power Electronics Conference and Exposition (APEC), San Antonio, TX, USA, 4–8 March 2018; pp. 2875–2878. [Google Scholar] [CrossRef]
- Kayssi, A. Macromodeling C- and RC-loaded CMOS inverters for timing analysis. In Proceedings of the Sixth Great Lakes Symposium on VLSI, Ames, IA, USA, 22–23 March 1996; pp. 272–276. [Google Scholar] [CrossRef]
- Boucher, T.O.; Gogus, O. Reliability, validity, and imprecision in fuzzy multicriteria decision-making. IEEE Trans. Syst. Man Cybern. Part C 2002, 32, 190–202. [Google Scholar] [CrossRef]
- Yang, C.; Sample, A.P. EM-ID: Tag-less identification of electrical devices via electromagnetic emissions. In Proceedings of the 2016 IEEE International Conference on RFID (RFID), Orlando, FL, USA, 3–5 May 2016. [Google Scholar] [CrossRef]
- Ahmed, M.M.; Hely, D.; Perret, E.; Barbot, N.; Siragusa, R.; Bernier, M.; Garet, F. Authentication of microcontroller board using non-invasive em emission technique. In Proceedings of the 2018 IEEE 3rd International Verification and Security Workshop (IVSW), Costa Brava, Spain, 2–4 July 2018; pp. 25–30. [Google Scholar] [CrossRef]

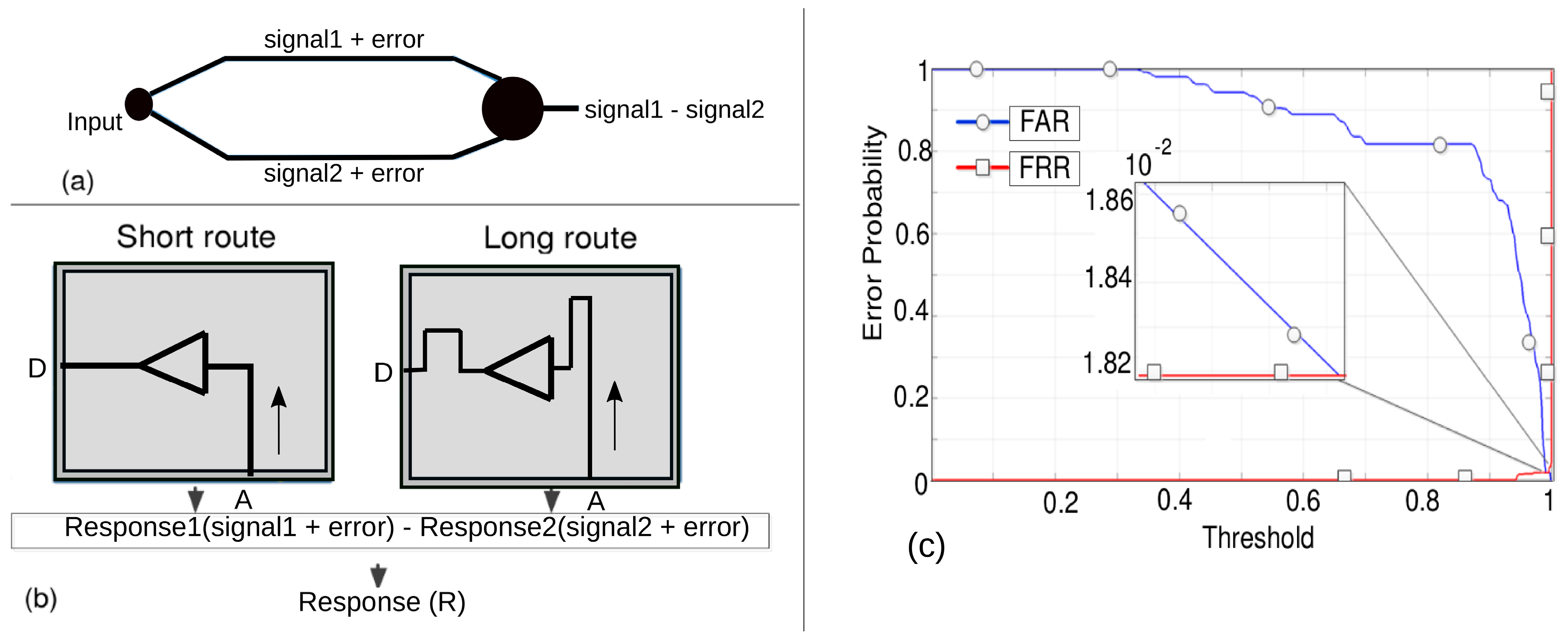
| Route Type | Long | Short | Difference of Routes (Error Removal) |
|---|---|---|---|
| Error Probability | 10−4 | 10−3 | 10−2 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmed, M.M.; Perret, E.; Hely, D.; Siragusa, R.; Barbot, N. Guided Electromagnetic Wave Technique for IC Authentication. Sensors 2020, 20, 2041. https://doi.org/10.3390/s20072041
Ahmed MM, Perret E, Hely D, Siragusa R, Barbot N. Guided Electromagnetic Wave Technique for IC Authentication. Sensors. 2020; 20(7):2041. https://doi.org/10.3390/s20072041
Chicago/Turabian StyleAhmed, Mosabbah Mushir, Etienne Perret, David Hely, Romain Siragusa, and Nicolas Barbot. 2020. "Guided Electromagnetic Wave Technique for IC Authentication" Sensors 20, no. 7: 2041. https://doi.org/10.3390/s20072041
APA StyleAhmed, M. M., Perret, E., Hely, D., Siragusa, R., & Barbot, N. (2020). Guided Electromagnetic Wave Technique for IC Authentication. Sensors, 20(7), 2041. https://doi.org/10.3390/s20072041





