1. Introduction
The internet of things (IoT) is a networking technology that connects sensors, controllers, and machinery. The IoT technology achieves intelligent management and control of machines through the connection of objects and will inevitably help humanity move toward a more intelligent and convenient future society. With the development of information technology, low-cost information devices have reached households of millions, and the number of devices connected to the Internet is increasing geometrically. According to a report by IBM, the number of connected devices in 2020 is expected to exceed 25 billion units [
1]. Traditional IoT models usually consist of a centralized data center that is responsible for collecting and processing data from connected devices. However, this method has drawbacks of high life-cycle costs. Since the maintenance costs of centralized servers are very high, when the number of IoT devices increases to tens of billions, a traditional IoT model may not be capable of meeting the growing demands of the IoT ecosystem.
With the continuous accumulation of unstructured information, most companies do not have practical solutions to the use of their data in order to make profits. The McKinsey research shows that most IoT companies are not yet able to make full use of their IoT data [
2]. The first challenge lies in integrating IoT data with other enterprise data in databases and enabling different technologies to work transparently together to fulfil specific goals. Another primary issue is the vast amount of IoT data, and the generating speed is accelerating. However, only a small percentage of these data can be stored permanently [
3]. The third problem is the IoT data security. IoT devices generate and process vast amounts of security and safety–critical data as well as privacy–sensitive information, and hence are appealing targets of various attacks [
4]. In summary, it is desirable to design a useful and secure solution for IoT data management.
There are already some researches and practices focusing on data solutions for IoT. Jiang et al. [
5] proposed a data storage framework for IoT data based on the cloud computing platform. Strohbach et al. [
6] developed an integrated big data analytical framework for IoT and smart city applications. However, these models are cloud-centric platforms that the quality of service may be affected by its deteriorated bandwidth and connectivity. Edge-centric IoT-based technologies, such as fog and mist computing, offer distributed and decentralized solutions to resolving the drawbacks of cloud-centric models. Perera et al. [
7] reviewed a significant number of IoT solutions in the industrial marketplace. A decentralized consensus system like blockchain is essential to incentivize all participants to share their edge resources [
8]. Decentralized consensus systems adopt either blockchain or blockchainless directed acyclic graph technologies to serve as immutable public ledgers for transactions due to its decentralization, traceability, privacy, secure transfer of value and so on. Yeow et al. [
8] analyzed the pros and cons of the state-of-the-art decentralized consensus systems and presented several open research issues on decentralized consensus for edge-centric IoT. Dorri et al. [
9] proposed a blockchain-based smart home framework and analyzed its security. Their method introduces insignificant overhead relative to its security and privacy gains. Sun et al. [
10] discussed how blockchain technology could contribute to smart cities by developing sharing services. Ali et al. [
11] designed a network architecture to protect IoT data privacy via blockchains and inter-planetary file system (IPFS). They proposed a decentralized access model for IoT data based on a software stack of blockchains and peer-to-peer data storage mechanisms.
However, since a public blockchain has problems such as lack of scalability and high transaction costs, it is not particularly applicable to IoT scenarios. According to [
8], TDAG (Transaction-based Directed Acyclic Graphs) technology (especially IOTA Tangle [
12,
13]) may be the solution to the vast and growing scale of edge-centric IoT. IOTA is a crypto token specially designed and optimized for the Internet-of-Things. The technology has very low-latency micro-payments in a decentralized M2M/P2P (Machine-to-Machine/Peer-to-Peer) infrastructure. The combination of machines and blockchains transforms these machines into economically independent devices for data exchange. Besides, it also reduces the operating costs of the IoT, solves security threats and protects user privacy.
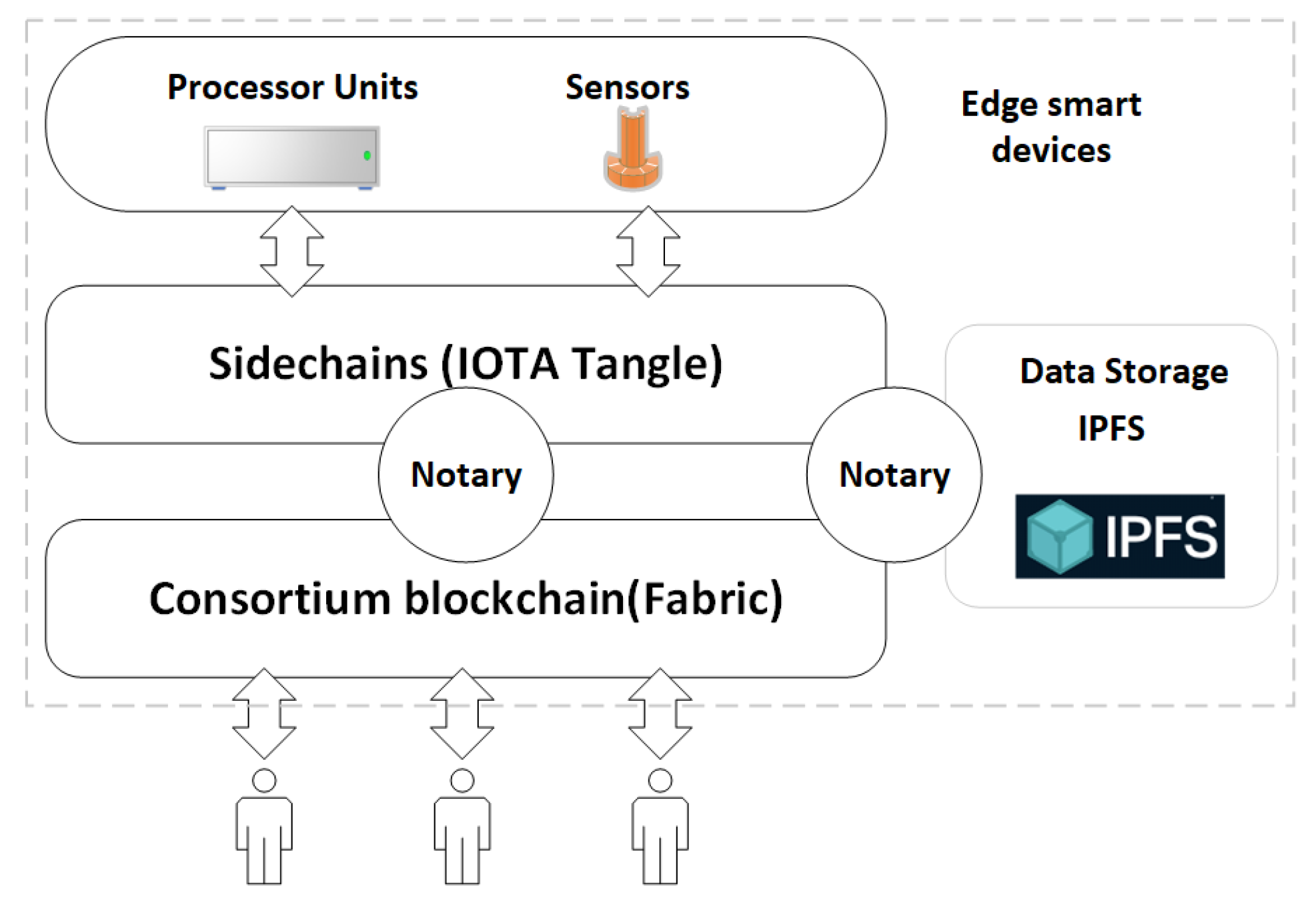
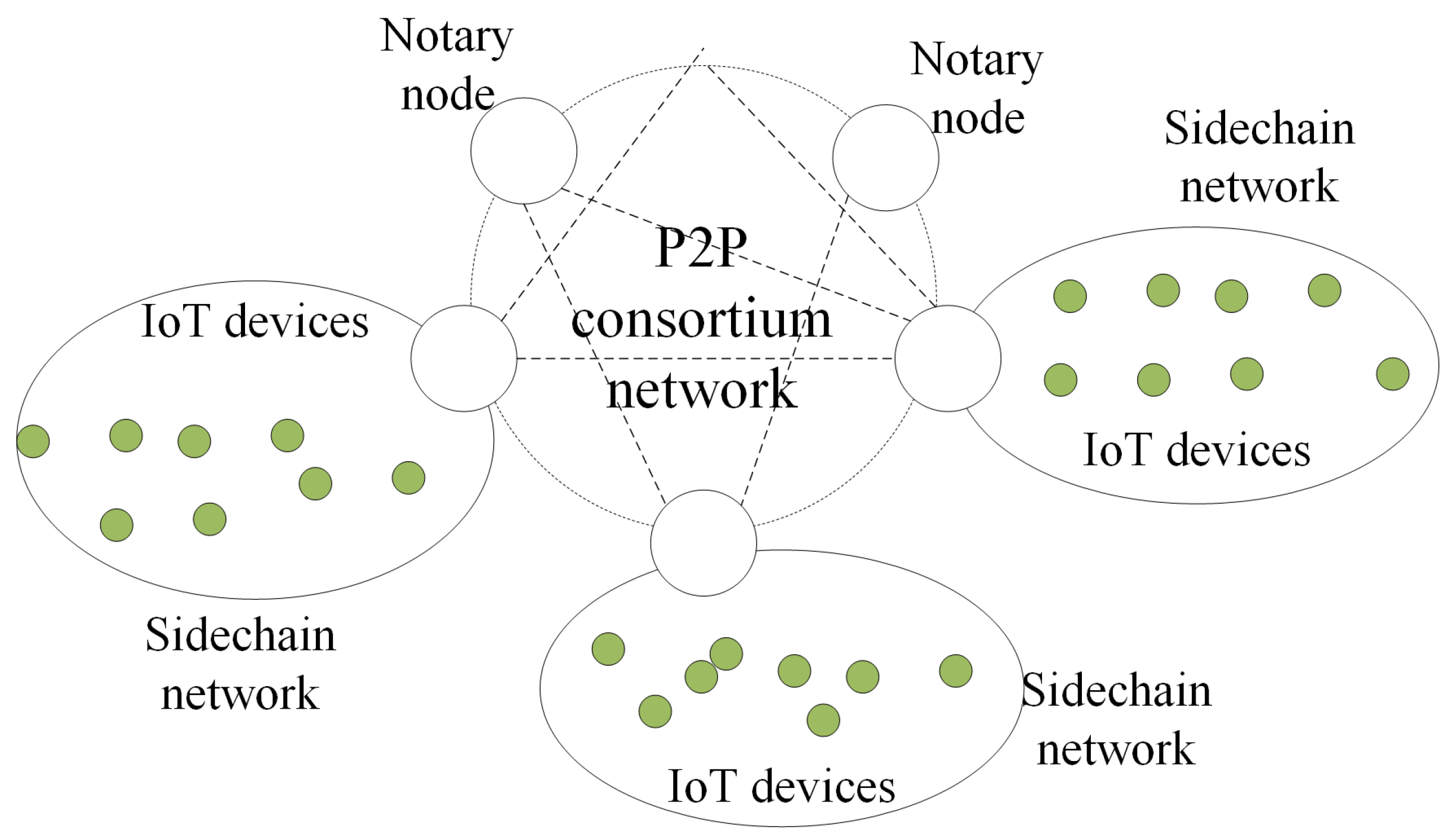
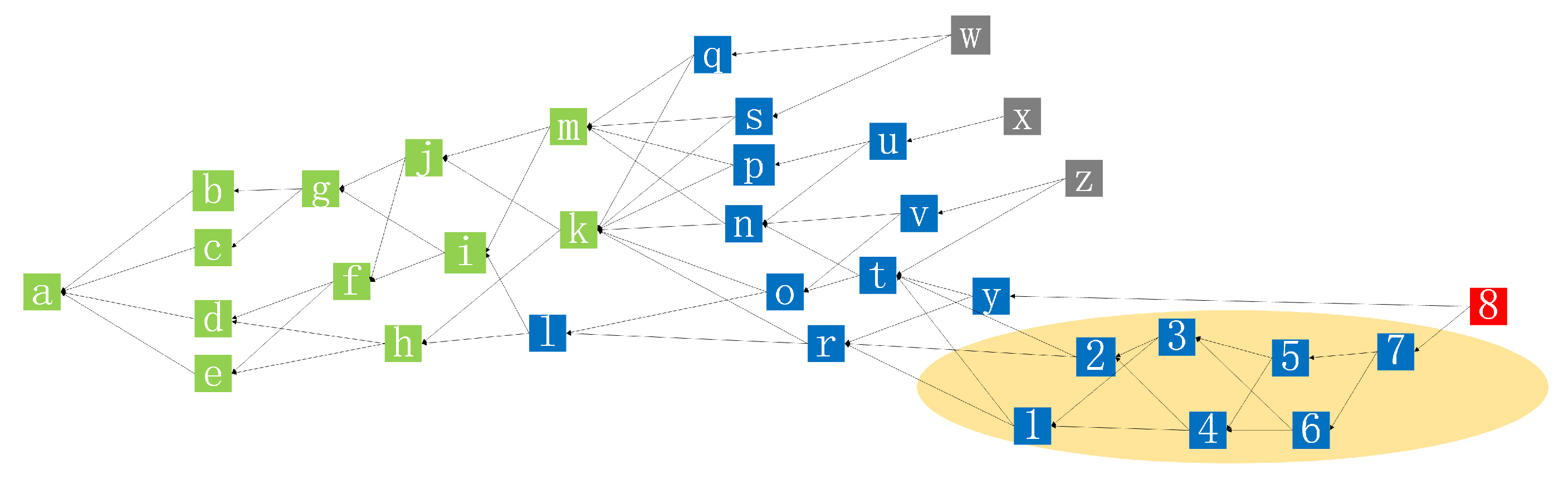
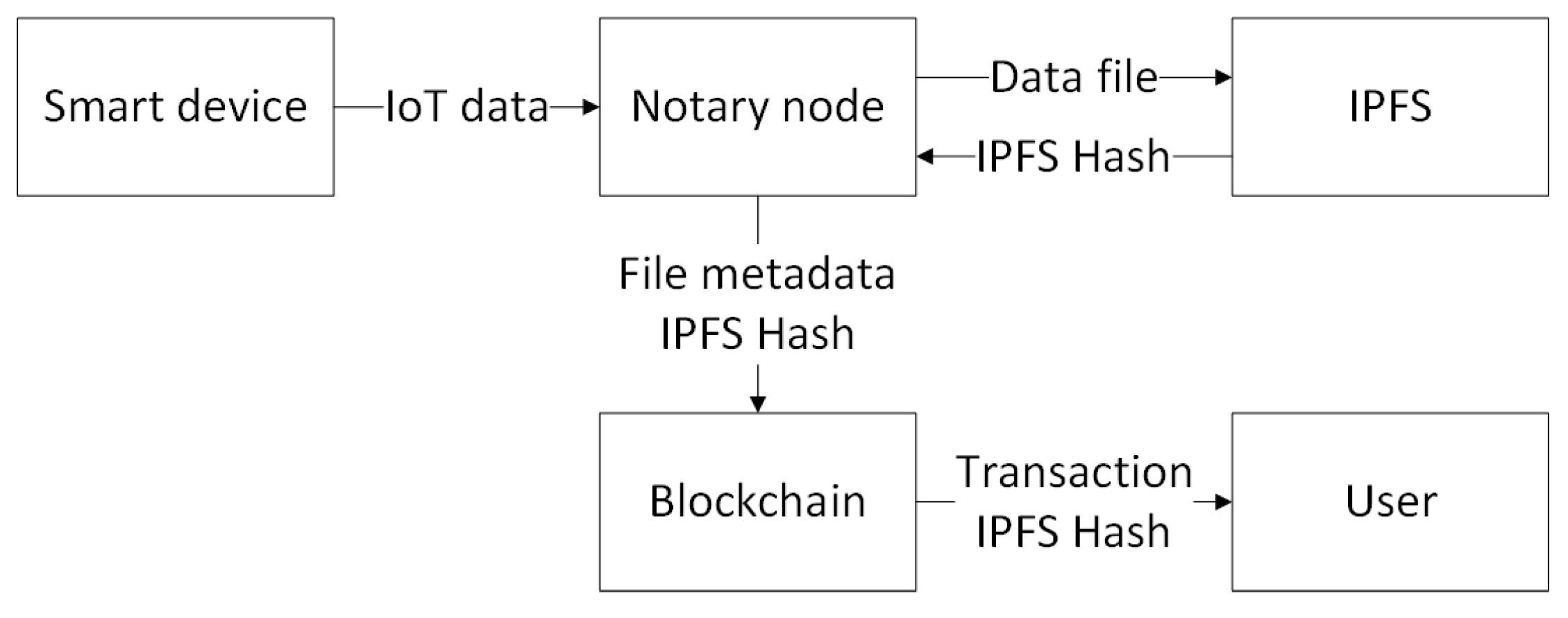
In this paper, we propose a cross-chain framework to integrate multiple blockchains for efficient and secure IoT data management. Explicitly, we integrate Tangle into the IoT blockchains by building a cross-chain based decentralized access model in the context of data management. In our decentralized access control architecture, we use a consortium blockchain as a control station, while Tangle runs as the backbone of the interconnected IoT devices. We connect the IoT devices to the consortium blockchain through notaries and group the IoT devices for a single use case into sub-Tangles. Our solution provides immutable logs of all IoT data operations, including generation, access and so on. Each sub-Tangle is responsible for maintaining the security logs of the IoT data operations. The sub-Tangle is connected to a more extensive and decentralized consortium blockchain network. The consortium blockchain is responsible for securely recording incoming access to any data and performing access control on these requests. However, it is nontrivial to solve the challenges associated with integrating blockchain to IoT networks.
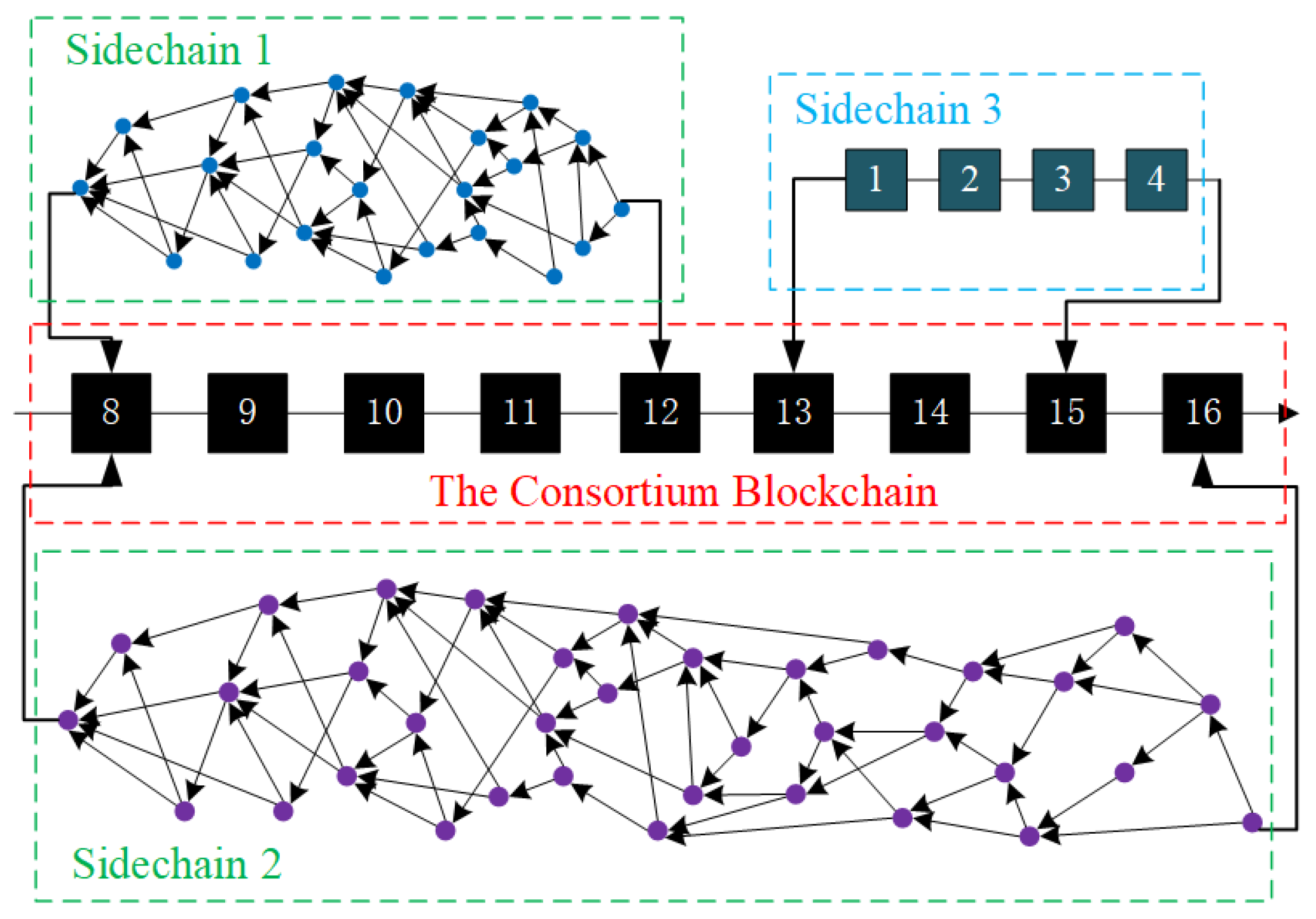
One of the challenges is the scalability of IoT blockchains. Since each entry on the blockchain requires consensus among all network nodes, the blockchain based on a single architecture do not scale well. To solve this problem, we introduce Tangle using directed acyclic graph (DAG) data structures and decompose the network into multiple smaller sub-Tangles similar to “sidechains”. We then connect these sidechain networks to form a decentralized network. Sub-Tangles are used for different IoT use cases, running on an IoT device cluster, and can be added or removed from the consortium network in a modular fashion. The advantage of implementing sub-Tangles is that nodes in a sub-Tangle do not have to verify transactions that occurred in other sub-Tangles. Users can own and manage one or more sub-Tangles according to different requirements.
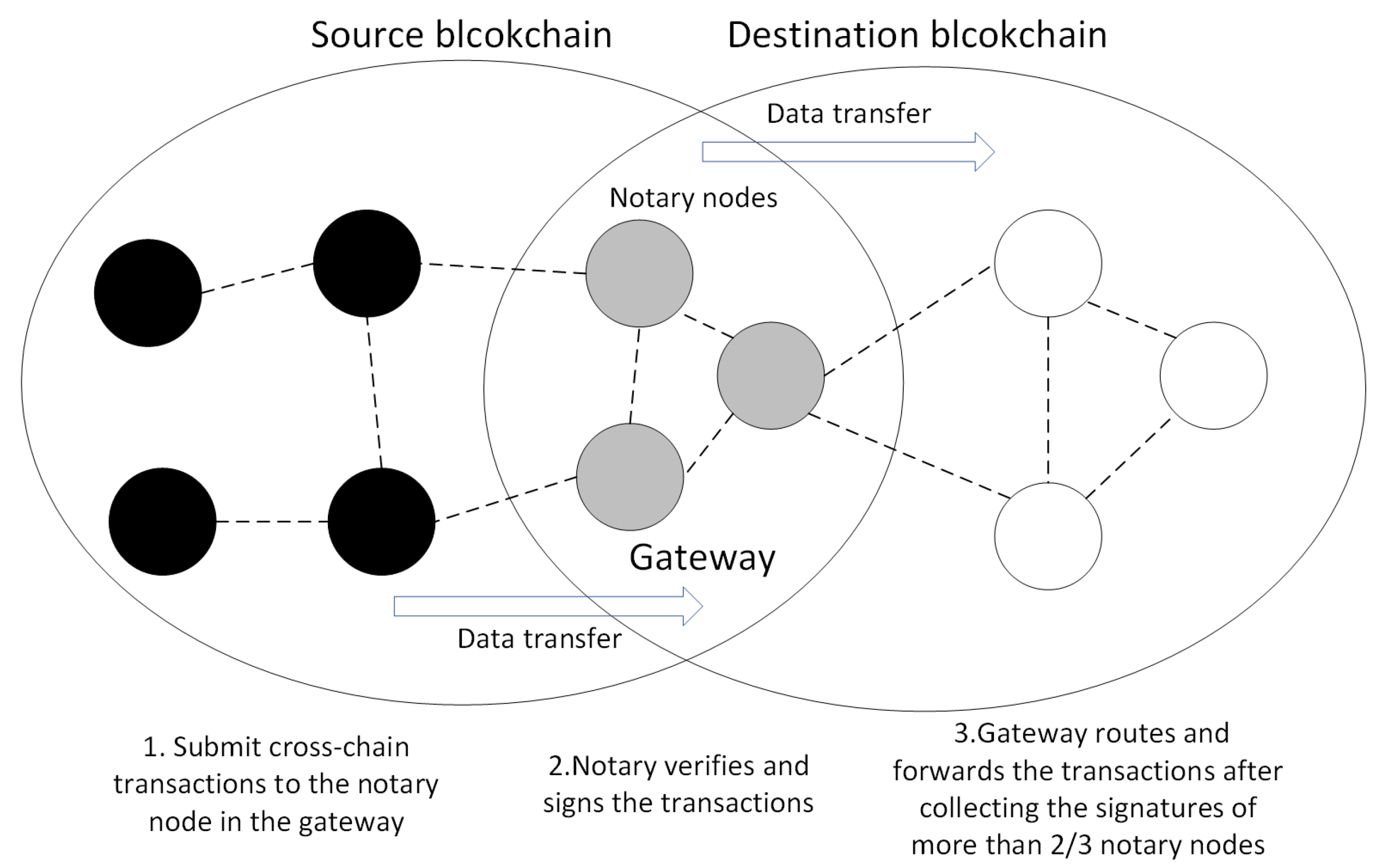
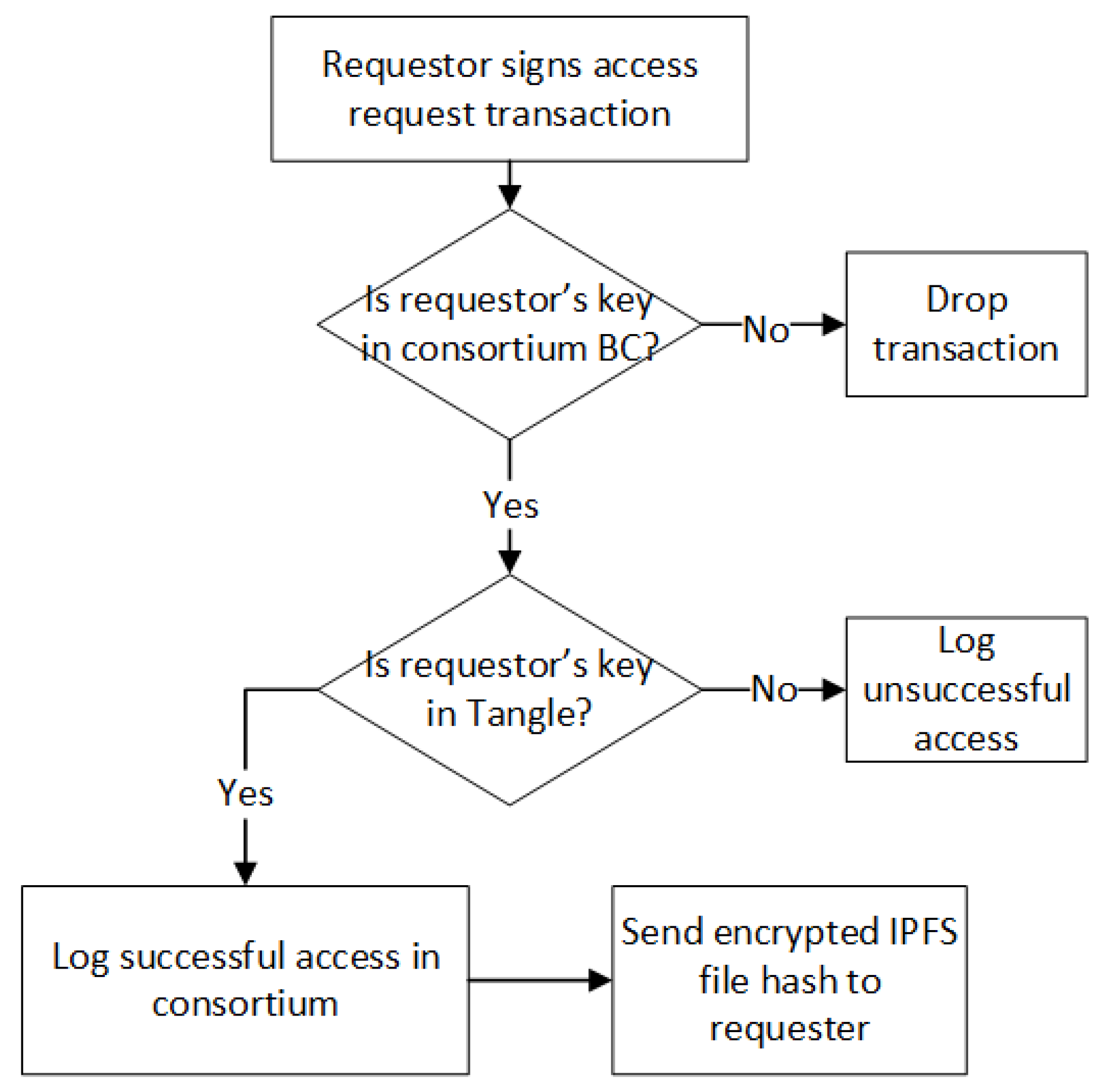
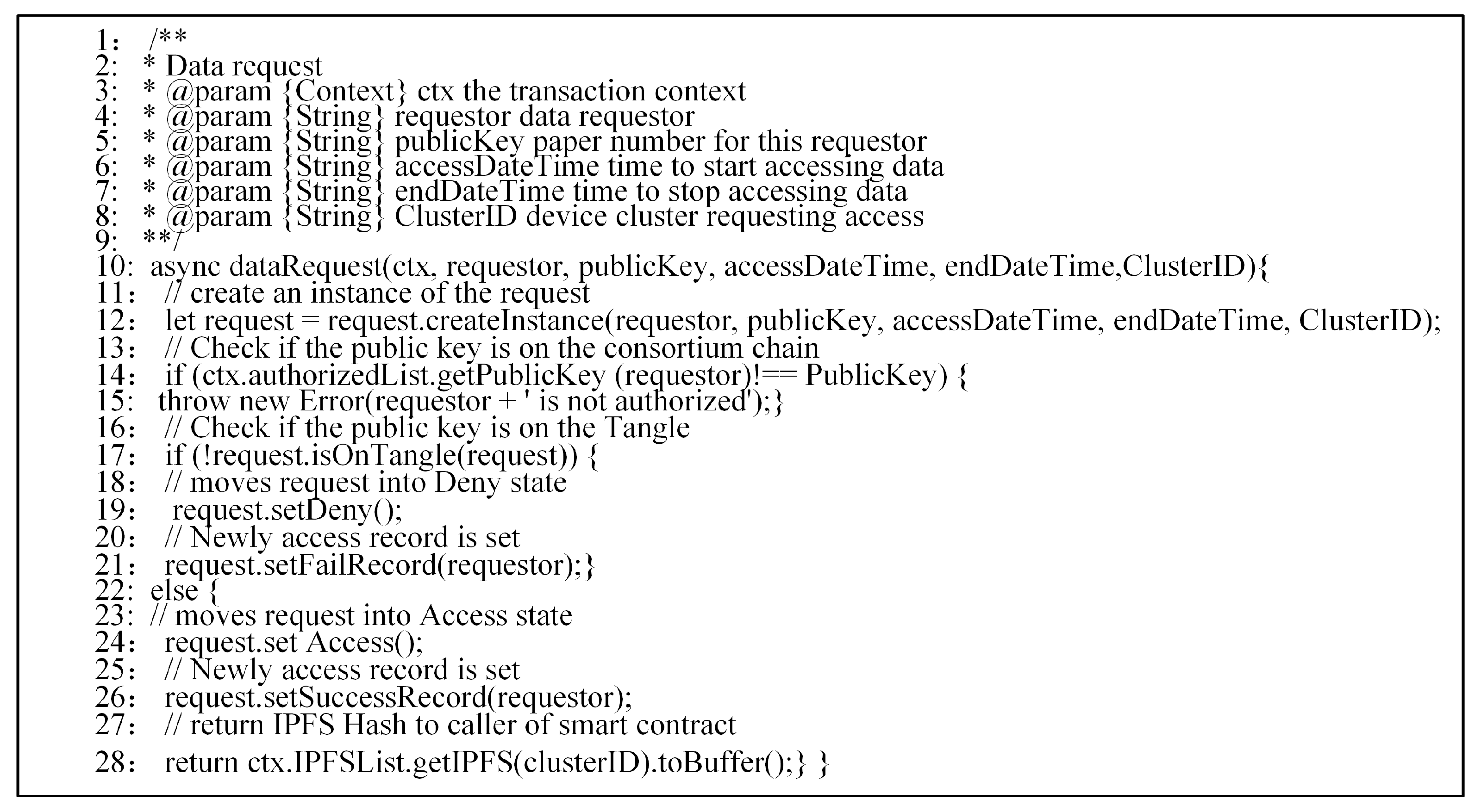
Another challenge is the privacy issue of the IoT blockchain. To tackle this issue, we propose an access control model. In order to access a sub-Tangle’s IoT data, the requester must issue an access request as a member of the consortium network. The consortium blockchain prevents any unauthorized access from one cluster of IoT devices to another cluster. Separating the logging responsibilities of sub-Tangles through the consortium blockchain helps to ease the public visibility of blockchain content. However, as far as the architecture is concerned, the members of the consortium network can only access records of IoT data through access requests. However, the log creation events remain private within each sub-Tangle.
We also address other practical problems. To reduce the high multi-agent collaboration cost and prevent individuals from being attacked, we use a consortium blockchain as a control station through smart contracts. To provide secure and trustful data transactions suitable for IoT scenarios, we use Tangle to tag machines to provide cryptographically secure identities and gather data from an object according to its identity. To address the problems of data storage, indexing, and queries for analytics, we use the IPFS [
14] and BigchainDB [
15] as the decentral storage in an immutable way. To introduce interactive cross-chain verifications between Tangles and the consortium blockchain, we design a particular notary mechanism. To address the privacy and security issues, we design a data access control protocol and new transaction types.
In summary, we make the following contributions:
We build a cross-chain interactive decentralized access model in the context of IoT data management.
We provide a feasible solution for users to optimize device management and convert their data to cash flow.
We design a data access control protocol for IoT data privacy protection in the interaction between sidechains and the consortium blockchain.
We implement a prototype of our model and evaluate its performance with extensive experiments. The results demonstrate the effectiveness and efficiency of our model.
The rest of this paper is organized as follows. In
Section 2, we compare the advantages of mainstream blockchain systems in the IoT scenarios. In
Section 3, we present the proposed architecture of the framework. In
Section 4, we describe the implementation of our method and conduct experiments to evaluate the effectiveness and efficiency of the system. In
Section 5, we review related work. We conclude this paper in
Section 6.
2. Blockchains in the IoT Scenario
At present, the problems faced by the internet of things mainly include central server failure, a single point of failure, the infeasibility of fine-grained data sharing, and a lack of privacy. The blockchain techniques have some natural features such as decentralized architecture, fault tolerance, and cryptographic security, to solve these problems.
There are currently a large number of blockchain platforms, including Bitcoin [
16], Ethereum [
17], Hyperledger-Fabric [
18], and IOTA [
13]. The mainstream consensus algorithms include proof of work (POW), proof of stake (POS), practice byzantine fault tolerant (PBFT), and IOTA (Tangle). We compare and analyze the functionality, security, and applicability of these mainstream blockchain systems and consensus algorithms in the IoT scenarios. Makhdoom et al. [
19] analyzed the difficulties and prospects of combining blockchain with IoT. They believed that the main challenge lies in the fact that IoT devices are growing too fast and transaction concurrency is too strong. The performance of the current blockchain networks is still not up to the requirements of the IoT. Yi et al. [
20] conducted preliminary researches on some classic and newly developed consensus algorithms. They suggested that Ethermint implemented by Tendermint is a suitable choice for the blockchain system of the IoT platform. We obtain the four requirements for blockchain systems that are suitable for IoT scenarios, including the ability to provide a heterogeneous network, quick consensus (BFT-based consensus algorithm), no transaction fees, and good scalability.
First, a blockchain platform should provide a heterogeneous network. Nowadays IoT increasingly requires a heterogeneous network that includes multiple sub-networks to handle a wide variety of business logic. For example, the entire smart city IoT can be considered as a heterogeneous network, and sub-networks include smart transportation, smart medical, smart home and so on. These sub-networks have independent businesses and run in parallel. However, they share data to provide a more valuable service. With the development of the internet of things, the blockchain platform is required to provide a heterogeneous network to solve the coordination problem of many sub-networks.
Second, we also believe that a blockchain network with higher throughput, better scalability and without transaction fees is more suitable for IoT scenarios. Fast transaction confirmation is a vital reference factor for the IoT environment, which requires the blockchain to reach consensus without forking. Only BFT-based consensus algorithms satisfy this requirement. Considering that the IoT network needs to process millions of transactions every day, and the number of devices increases persistently, the number of transactions will continue to rise. Transaction fees will bring unaffordable costs for consumers. Hyperledger Fabric has kept this factor optional. However, the blockchain should use strict device authority authentication and well-designed data access control to avoid data storms.
Thirdly, a blockchain system needs to have good scalability. Faced with the rapid growth of IoT devices, the blockchain system needs to handle more and more business. For IoT, such a large number of users, transaction volume, and a large amount of data, or a significant increase in the number of users, the system has put forward higher capacity and scalability requirements, and the single-chain architecture will always encounter software architecture or hardware resources. The system characteristics of the blockchain determine that adding nodes in the blockchain will only enhance the system’s fault tolerance and increase the participants’ credit endorsement without increasing performance.
Table 1 shows the comparisons of several main blockchain platforms. Comprehensive analysis shows that no single blockchain can satisfy the complete requirements of the IoT scenario. However, a combination of Fabric and IOTA is more suitable for the IoT environment.
4. Experiments
4.1. Implementation
We implemented a prototype of the proposed model. We build a consortium blockchain based on the Hyperledger Fabric [
23]. Hyperledger Fabric is a business blockchain development platform which uses the BFT algorithm to reach consensus. We built a private Tangle based on the IOTA architecture.
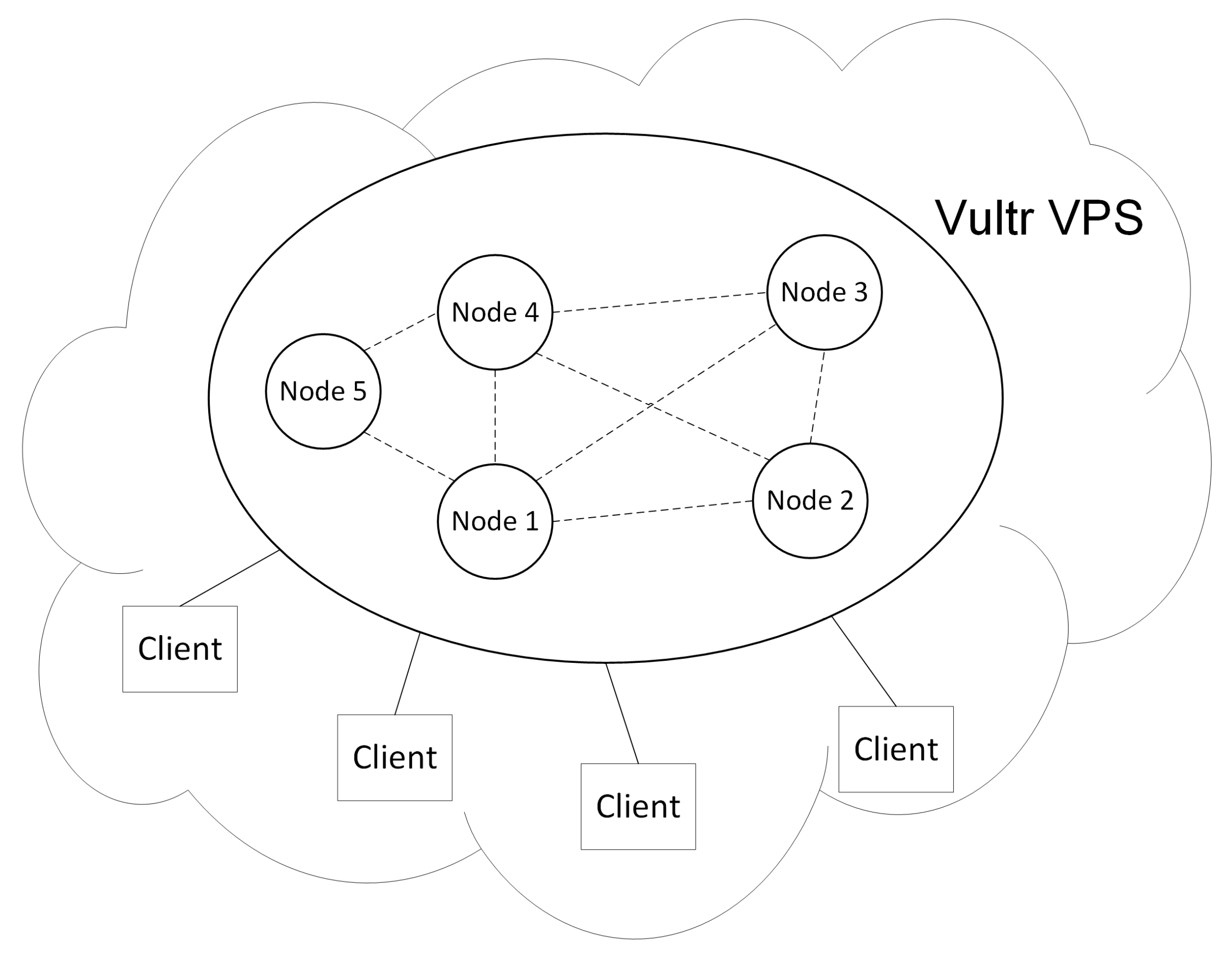
Figure 9 illustrates the experimental setups. We deployed five nodes on the Vultr VPS [
24] with Ubuntu 16.04 xenial. Nodes 1, 2, 3, and 4 served as typical peers of the Hyperledger Fabric and Node 5 served as the orderer node of the Hyperledger Fabric. Nodes 1, 2, 3, and 4 also run full deployments of IOTA. We implemented the notary gateway network on Nodes 1, 2, 3, and 4, which also connect to the public IPFS service. Every node received data from multiple Hyperlegder Fabric clients that can interact with the blockchain network.
In the following experiments, we evaluate the performance of the system by examining the metrics of throughput, latency and resource consumption such as memory, CPU, and network traffic overhead.
4.2. Throughput and Latency
We tested the throughput and latency for different transaction send rates under different configuration environment of the node. In this experiment, we tested the throughput and latency of our P2P consortium network by varying the send rates. We generated and sent 5000 transactions by the APIs provided by Hyperledger Fabric in each test. All transactions are queries to access the data on Tangle via Hyperledger Fabric. The chaincode (smart contract) in Hyperledger Fabric was ran as a container. The results are presented from
Table 2,
Table 3,
Table 4 and
Table 5. Tps means transactions per second.
From the results, the throughput generally increases as the send rate increases. Moreover, as memory and the number of CPU cores increases, the throughput is closer to the default send rate, the latency of transaction processing also gradually decreases. Especially when the number of CPU cores increases, the performance improvement is more prominent.
4.3. Resource Consumption
We also tested the memory, CPU and network traffic usage of the system. We chose results in the 4G memory and four cores configuration.
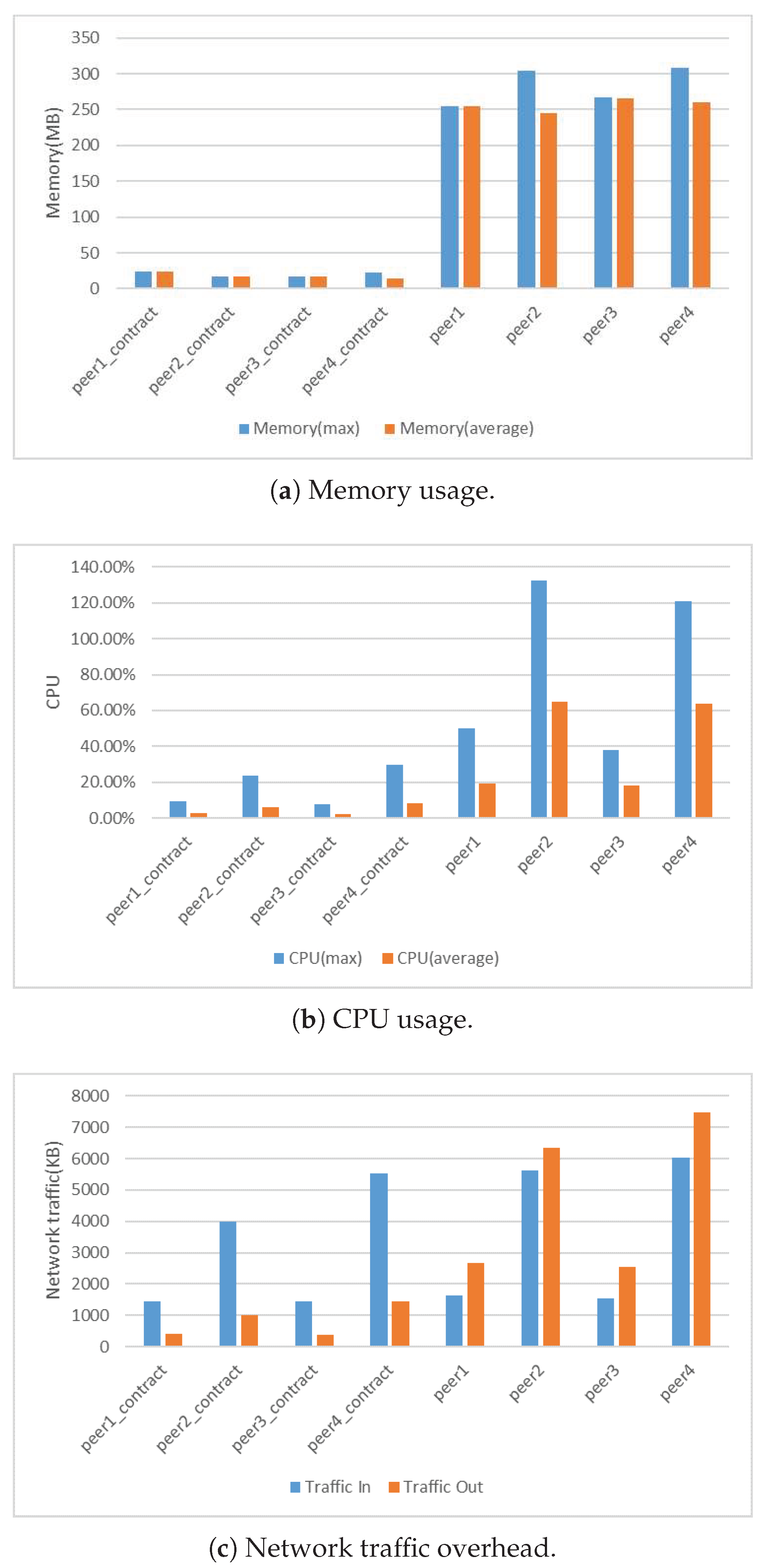
Figure 10 presents the results. We compared the processing resource consumption by comparing the average memory and CPU usage. The results presented in
Figure 10a,b show that a Fabric peer required at least 300 MB of memory, and an average of 40% CPU usage. From the perspective of memory and CPU usage, Hyperledger Fabric was not suitable for deployment in IoT devices with limited resources compared to Tangle light nodes. In blockchain applications, network nodes communicate with each other to reach consensus. In this experiment, we also measured the traffic overhead of the consortium network. We evaluated the traffic overhead of our blockchain network by monitoring the input and output traffic of the peer container of the Fabric network. Network traffic overhead mainly includes transactions and data disseminated through the network.
Figure 10c shows that the BFT consensus has huge network traffic overhead. In order to reduce the traffic flowing into the blockchain network, we can use fog nodes as notary nodes to process IoT data in practice, which can significantly reduce the network congestion. Besides, we also compared the peak memory usage of a specific process of different Tangle node and clients.
Table 6 displays the results.
From the results, because the contract installed on the peer in the Fabric started a separate runtime environment in the form of a container, this container was only responsible for providing the contract with the running environment and the processing of contract calls, so the overall resource consumption was relatively low compared to the peers. During the query, the peer’s out-traffic was significantly higher than the in-traffic. It was because the query transaction queried the ledger on the peers by calling the contract and the peers send query result back to the requester.
4.4. Deployment Considerations and Analysis
From the experiments above, we can see that due to the memory occupied by the Tangle full nodes and the consortium blockchain, the memory required for the notary node was relatively large, and the memory occupied by the light node client in the edge device is tiny compared to notaries. Besides, our notary node’s CPU usage in different scenarios during a day remained almost the same. Therefore notary nodes can be deployed on the servers of each member of the consortium. Through our use of the consortium network, we found that network traffic had increased significantly in the case of large transaction volumes. The results of network traffic overhead show that the BFT consensus had huge network traffic overhead. In order to reduce the traffic flowing into the blockchain network, we can use fog nodes as notary nodes to process IoT data, which can significantly reduce the network congestion. The throughput of our network was mainly affected by the consortium blockchain. When the transaction request per second reaches the processing limit of the consortium blockchain, the throughput of our consortium network becomes stable. However, the throughput of Tangle still increased as the transaction rate increased. It was because transactions on the sub-Tangle can be verified in parallel on the Tangle, which enhanced the processing performance of the system.
5. Related Work
The combination of blockchain and the Internet of Things has attracted the most attention recently. Due to the lack of an IoT-centric consensus protocol, the existing blockchain system cannot meet the requirements of the Internet of Things in terms of transaction delay and scalability. Many approaches have been proposed to address these problems. Sagirlar et al. [
25] designed a hybrid blockchain architecture for IoT which is named as hybrid-IoT. In hybrid-IoT, IoT devices form subgroups which use Proof of Work consensus algorithms. We refer the subgroup as POW sub-blockchains. The POW sub-blockchains employ a BFT interconnection framework, such as Polkadot or Cosmos. Li et al. [
26] used the blockchain system to design an identity authentication mechanism and a data protection mechanism for IoT devices. Compared with their proposed system, our advantage is that IoT devices can customize their access control and have more autonomy. Alphand et al. [
27] proposed IoTChain, which is a combination of OSCAR architecture and ACE authorization framework. IoTChain provides an end-to-end solution for securely authorized access to IoT resources. In the system they propose, the data is stored by the server, and we use IPFS to store the data. Our models have lower storage costs and greater data privacy, preventing problems such as single points of failure on the server. Ouaddah et al. [
28] proposed FairAccess as a new decentralized pseudonymous and privacy-preserving authorization management framework. The framework leverages the consistency of blockchain technologies to manage access control. However, the solution has not yet been implemented. Oscar Novo [
29] developed a fully distributed access control system for IoT based on blockchain technology. However, the system suffers high transaction latency since underlying blockchain based on the Ethereum. Reilly et al. [
30] developed an integrity-first communication protocol for IoT based on the Ethereum blockchain. They implemented light clients for the resources limited IoT devices by reducing the code related to the miner and avoiding to store data on the blockchain. However, they do not solve the transaction latency problem. Puthal et al. [
31] proposed a new consensus algorithm named PoAh (Proof-of-Authentication) for Scalable Blockchain in Resource-Constrained Distributed Systems.
There have been many techniques taking the advantages of blockchain in different ways to improve the IoT services, although the combination of blockchain and IoT is relatively new. Blockchain can benefit IoT techniques in many scenarios. For example, sensors attached to many IoT devices can be traced through the traceability of blockchain, which provides useful information about the distributions of the devices. Analogously, the blockchain technology also enriches the sensed data provided by many IoT applications.
Ethereum [
17] is one of the most popular platforms for IoT blockchain applications. It has more features than Bitcoin. Besides, Ethereum provides the function of smart contracts which significantly boosts its applications in IoT scenarios. Slock.it [
32] proposes a blockchain framework to address security, identity, coordination, and privacy over billions of IoT devices. It aims to build a sharing economy where each IoT asset can be rented securely and quickly without the need for any authority [
32]. MyBit [
33] aims to build an ecosystem of data-sharing services. People can share the revenues of their owned IoT assets (e.g., drones, cars, smart home, and so on.). It employs Ethereum smart contracts to fulfill the goal. The project of Atonomi [
34] is built on the Ethereum network. The goal of Atonomi is to provide a universal trust environment for billions of IoT devices through its device identity registration service and reputation service. IoTex [
35] is a decentralized network for the Internet of things powered by a privacy-centric blockchain. The root chain manages several separate blockchains or sub-chains which are connected to similar IoT devices. Waltchain [
36], similar to IoTex in architecture, is committed to combining the blockchain with RFID (Radio Frequency Identification) in order to solve the problem of product traceability.
The autonomous decentralized peer-to-peer telemetry (ADEPT) [
37] IoT system was jointly created by IBM and Samsung and uses blockchain technology to create a decentralized IoT. The full name of ADEPT is “autonomous decentralized peer-to-peer telemetry”, which aims to provide optimal security for transactions. The system is based on three protocols: Blockchain, BitTorrent, and TeleHash. ADEPT employs Ethereum [
17] which is a smart contract-based system, and ADEPT can enable devices connected to it to communicate securely and efficiently with each other and implement complex business logic. ADEPT is a user-centric complete IoT platform, similar to IOTA Tangle. However, IOTA does not use a blockchain. Instead, it uses a distributed database model called Tangle (DAG), which is technically superior compared to a blockchain in terms of scalability and the feasibility of micro-payments.
Unlike the use of Ethereum, Innogy [
38] combines IPFS, IPDB, and IOTA in supply chain/IoT applications. IPFS is used for file systems and Blob storage. IPDB (using BigchainDB) is used for metadata storage and query queues. Innogy utilizes physical objects through the supply chain and provides the “trust-to-data”. These datasets are tracked automatically and verified through IOTA disputes in the supply chain. Innogy aims to create digital twin [
39]. A digital twin is a digital representation of a physical, biological or digital object. The Innogy Digital Twin project Twin of Things seeks to give every physical object a story. Moreover, the first practical application of a digital twin with IOTA is CarPass for vehicles telematics data. The CarPass solution securely captures telematics data and stores them immutable in the digital twin for private passenger, fleet or commercial vehicles.
IOTA has proved scalable due to the particular DAG structure of transactions. While running smart contracts on IOTA is a challenge, the combination of Hyperledger Fabric and IOTA Tangle can well address this problem. We integrate Tangle into the blockchains, and our cross-chain interactive decentralized IoT access model considers better data access privacy. We use a consortium blockchain running in a control station, while Tangle as the backbone of the IoT system runs on all the devices, this architecture takes full advantage of the features of blockchain and Tangle. Different from existing work, our solution uses the BFT consensus algorithm. The throughput of our proposal is acceptable considering the overhead of cross-chain interaction. Besides, due to the scalability and the nature of parallel verification of Tangle, as the number of participant nodes increases, Tangle can lead to higher throughput and better system performance.