1. Introduction
Indoor localization plays an important role in public safety and disaster management and relief [
1]. Location data can help managers warn people who make unauthorized entry into areas to enhance public safety. Such situations include the monitoring of dangerous military areas or indoor inflammable stacking areas. Another example is the fire emergence response: when a fire incident occurs in a building, management personnel can locate both the disaster site and people quickly [
2]. During disaster relief operations, location information can assist rescuers to quickly acquire tools, get closer to those to be rescued and evacuate them [
3,
4].
Common indoor positioning technologies include range-based and non-range-based [
5,
6]. The former is realized by measuring the physical relationship between the measurable parameters and the position of the signal arrival time and signal strength. The latter includes two phases: offline and online. During the offline phase, different signal strengths are received for different locations in the room, which is used to generate a wireless signal fingerprint radio map. During the online phase, a real-time signal fingerprint received from the actual location is matched with the fingerprint database to obtain the fingerprint with the highest similarity, thereby estimating the target position. At present, wireless local area network (WLAN) -based indoor fingerprint positioning is the main technology, largely due to the WiFi availability and its low cost.
The indoor positioning methods available for different disaster sites are different. For instance, in the event of a fire in a building, the environment changes quickly: such a situation is not suitable for received signal strength indication (RSSI) ranging or RSSI fingerprinting. Instead, pedestrian dead reckoning (PDR) positioning [
2] or other wearable sensing networks [
7] are used. However, indoor fingerprint positioning can achieve good results where the environment does not change quickly, such as monitoring dangerous areas for unauthorized entry or for chemical poison or toxin gas leakage.
No matter which indoor positioning technology is adopted in disaster management, its primary requirements are accuracy and real-time response [
1,
2,
3,
4,
8]. Accurate positioning can avoid false positives and false negatives when, at a disaster site, response personnel may have less than one minute for rescue or evacuation [
4]. However, the accuracy and real-time performance of indoor positioning is usually conflicting. Generally speaking, if positioning accuracy needs to be improved, more complex algorithms or more reference data are required [
2,
9]. Conversely, if a simpler algorithm is adopted, the estimated location may not be accurate enough. Thus, choosing a good localization algorithm is important but not easy in disaster management.
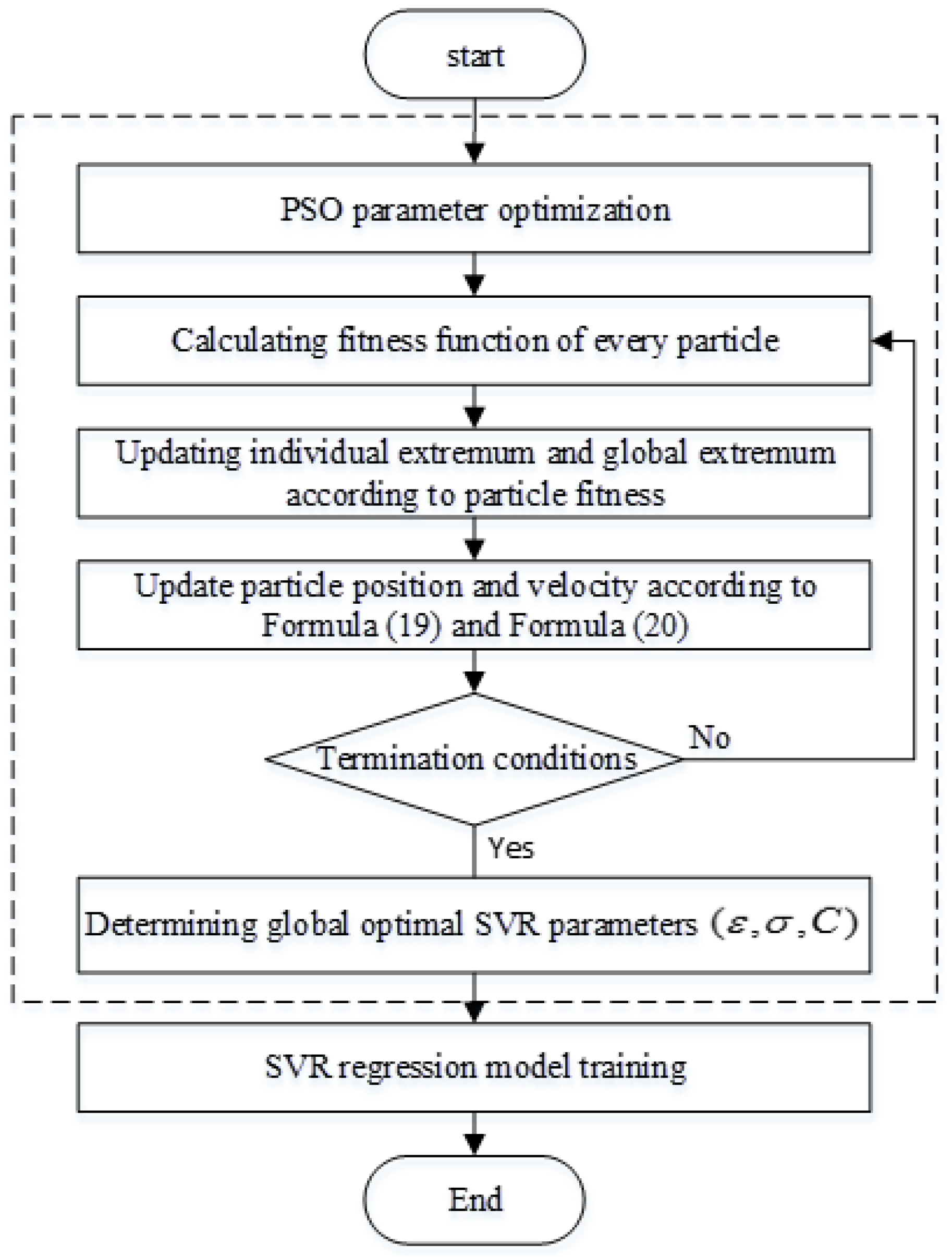
Taking, as an example, an indoor fingerprint localization algorithm applied to hazardous area monitoring and disaster relief systems in a chemical plant, this paper proposed a two-level positioning algorithm based on improved clustering and particle swarm optimization (PSO)-support vector regression (SVR) to improve fingerprint matching efficiency. It specifically investigated two issues. Firstly, in the offline phase, the similarity among the fingerprints was measured by the Shepard similarity which stems from the Euclidean distance and the fingerprint database was divided into sub-fingerprint databases by the affinity propagation clustering (APC) algorithm. The localization model based on PSO-SVR was then established for each fingerprint database, where the uncertainty of the parameter selection of the SVR regression model was optimized by the PSO algorithm. Secondly, in the online phase, the most similar sub-fingerprint database was firstly selected according to the similarity between the target point fingerprint and the sub-fingerprint cluster center fingerprint. Within this sub-area, the PSO-SVR was then used again to obtain the accurate location of the tested point. It should be noted that both improved accuracy and the time reduction in the online phase came at the expense of increased workload in the offline phase.
The rest of this paper is arranged as follows:
Section 2 reviews the related literature;
Section 3 introduces the proposed localization algorithm, including the overall framework of the proposed method, APC algorithm based on the Shepard similarity metric and accurate localization based on PSO-SVR;
Section 4 reports the results of performance evaluation based on a real application;
Section 5 provides conclusions and discusses future work.
2. Review of Related Literature
A wireless fingerprint indoor positioning method usually has two phases: offline and online. The positioning performance of the online phase determines the overall performance of the system and its positioning efficiency. Commonly used matching algorithms include K-nearest neighbor (KNN) [
10], kernel-based algorithm [
11], support vector machine [
12], artificial neural network (ANN) [
13,
14], and SVR [
15].
In terms of performance, a localization system using the above algorithms usually cannot simultaneously meet the requirements of localization accuracy, algorithm complexity and storage reduction. For example, the KNN algorithm is simple but not precise enough, while ANN has high positioning accuracy but its algorithm is complex and needs much storage. Research shows that the localization accuracy of the non-parametric methods depends largely on the number of samples [
16,
17]. However, the “flat”, one-by-one matching method increases matching calculations and reduces the matching efficiency for fingerprints [
5,
18] and thus affects the overall efficiency of the system.
Since 2014, two-level localization algorithms have been widely adopted in the fields of disaster management [
2,
19] and other fields [
9,
20,
21]. Research and experimentation [
13,
22,
23] show that, according to the similarity between target-position fingerprints and offline-collected fingerprints, the number of fingerprints matched can be effectively reduced [
24,
25] by selectively matching some appropriate fingerprints, thus establishing a hierarchical search algorithm. This can simultaneously achieve considerable precision. To achieve this, the positioning database is divided into a certain number of sub-databases in the off-line stage to achieve database partition [
26]. In the online stage, the matching range is narrowed by searching the sub-databases adjacent to the target point [
27]. Therefore, there are typically two kinds of important algorithms: one is the clustering algorithm which is critical to sub-database partition in the offline stage, and the other is the classification algorithm of fine localization in the online stage.
Although there are many algorithms proposed and developed in the literature for clustering, such as K-Means, density-based spatial clustering of applications with noise (DBSCAN), the expectation maximization (EM) based on Gaussian mixture model (GMM), and APC, for algorithm simplicity and localization speed, the K-Means and APC algorithms are the most widely used in indoor fingerprint localization no matter whether in “flat” or hierarchical localization methods.
The K-Means is considered to be the simplest of all clustering algorithms, and was also used in a two-level localization algorithm [
28], but the initial value of the K parameter of K-Means clustering is difficult to determine, and it cannot cluster samples with complex distribution, such as non-convex distributed samples. So, in some instances, it is not appropriate to use the K-Means for clustering.
An alternative solution is the APC algorithm, which can naturally form the number of clusters, hence avoiding the problem of some parameters presetting. Currently, some non-hierarchical localization algorithms [
1,
21,
29,
30] use APC as the clustering algorithm. In some hierarchical localization algorithms, APC is also used [
9,
22]. All the current APC algorithms use the Euclidean distance as the similarity metric, which stems from the most primitive algorithm [
31]. However, according to the literature [
9,
32], RSSI does not have a linear relationship with the Euclidean distance, so it is unreasonable to measure the RSSI similarity with the Euclidean distance metric. This will be further discussed in
Section 3.2.1.
The second kind of important algorithms in hierarchical localization is classification. Commonly, weighted
k-nearest neighbor (W
kNN) [
9,
20], SVR [
22] and ANN [
33] are adopted. W
kNN is the most popular used algorithm, but sometimes it cannot achieve good accuracy. On the contrary, ANN is the most accurate, but it is the most complex. SVR is an efficient classification algorithm due to its high generalization ability and excellent ability of non-linear mapping with the kernel function.
Compared with a “flat” localization algorithm, all the classification algorithms in hierarchical localization can save operation time because of their reduced search range. However, all these algorithms still face the same problem as the K-Means clustering algorithm: the parameters used in the algorithms must be preset in advance, such as the k parameter in WkNN and the insensitivity coefficient ɛ in SVR. If the parameters are not properly preset, accuracy will deteriorate.
5. Conclusions and Future Work
One of the core technologies for disaster management is the indoor positioning system, which can help rescue more people and prevent property loss due to the accurate and rapid localization of people and assets at the beginning of a disaster.
However, due to the fluctuation of wireless signals, the change in environments and monitoring areas, and the increase of reference points, indoor fingerprint positioning systems often face the contradiction of positioning accuracy, computational complexity and storage requirements. This paper proposed a two-level positioning method to address the challenge: in the coarse positioning stage, an APC algorithm based on Shepard similarity was used to realize clustering; then, in the fine positioning stage, an SVR with PSO parameter optimization was used for precise positioning. Both experiment results and actual implementations proved that the proposed method was more suitable than other methods in term of algorithm complexity, storage requirements and localization accuracy in dangerous area monitoring
Future work will focus on the miniaturization of the mobile device and the integration of fingerprint indoor positioning with pedestrian dead reckoning (PDR) positioning. In fire scenarios, where the environment changes quickly, the fusion of indoor fingerprint positioning and PDR can be used for disaster management. Other sensors, such as magnetometers, gyroscopes and accelerometers can also be considered for integration with indoor RSSI fingerprint positioning to improve positioning performance.