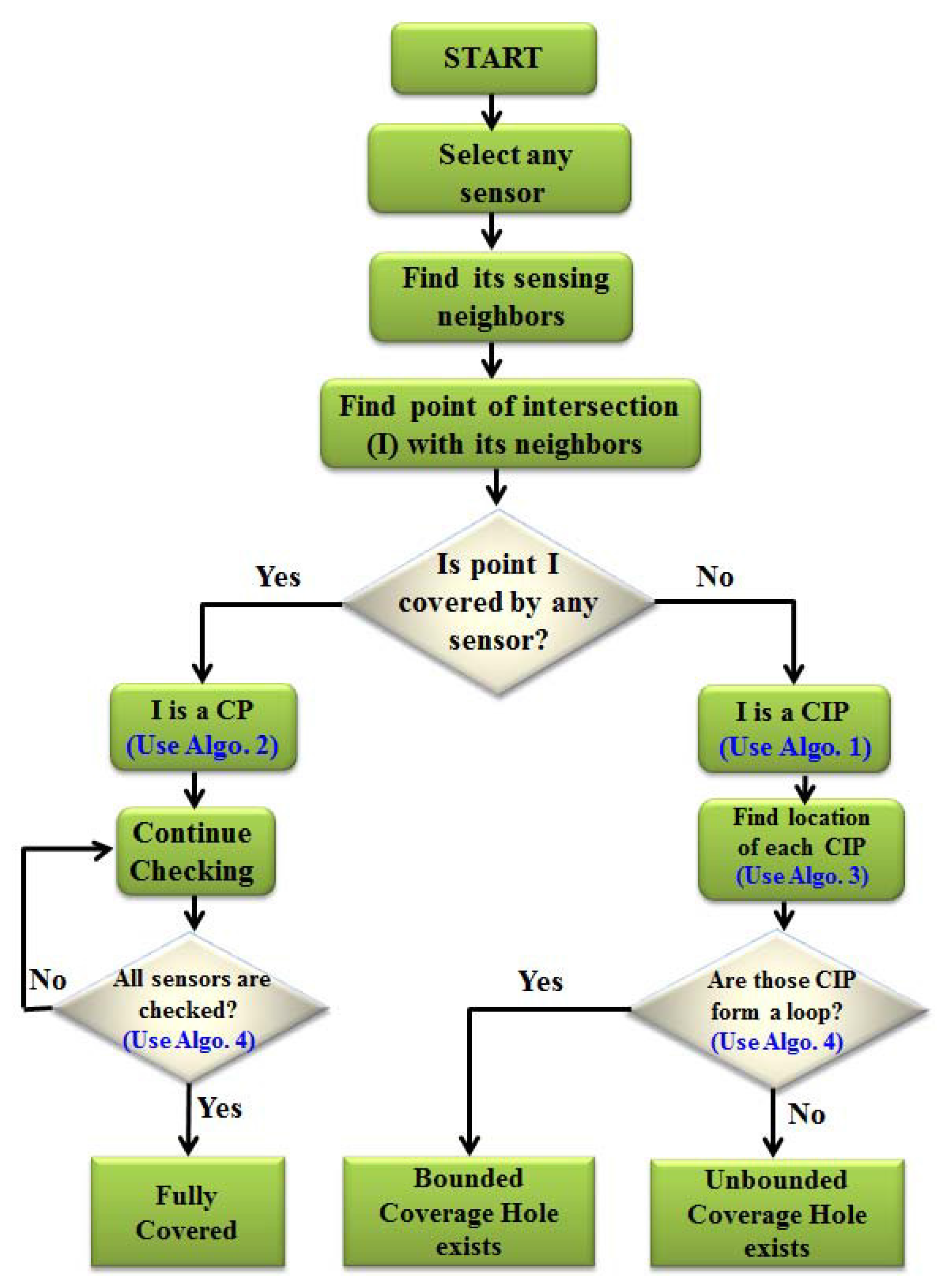
1. Introduction
With the advance of microelectromechanical systems (MEMS) technology, wireless sensor networks (WSNs) [
1] play an important role in transportation, infrastructures and forest monitoring for animals or fire [
2,
3], with its inexpensive, small size and multi-functional abilities. Normally, a wireless sensor network is composed of a large number of sensors deployed over the monitoring region regularly or randomly, and the deployed sensors are self-organized [
4] to form the network. Since a random deployment is usually used in WSNs, the study of coverage issues is very important, which should be studied deeply in addition to the localization, target tracking and time synchronization in WSNs. However, a sensor node is severely constrained by the resources, such as limited memory, battery power, computation and communication capabilities. The energy consumption of each sensor is a function of its own sensing and communication range, and designing algorithms for deployment, localization, duty cycle, coverage and other issues is most important in WSNs.
The sensors are deployed randomly over a monitoring region with a high degree of density of nodes. Due to the random deployment strategy, certain areas of the monitoring region may have coverage holes [
5,
6] or serious coverage overlapping, which significantly degrade the network performance. Besides, the failure of electronic components, software bugs and destructive agents could lead to the random death of the nodes, and also, nodes may die due to the exhaustion of battery power, which may cause the network to be uncovered and disconnected. Since sensors are deployed in remote or hostile environments, such as a battlefield or desert, it is impossible to recharge or replace the battery. However, the data gathered by the sensors are highly critical and may be of scientific or strategic importance. Hence, the coverage provided in the sensor networks is a critical criterion of their effectiveness, and its maintenance is highly essential to form a robust network. The study of such coverage issues means summing of the sensing and communication range, which should be ideal in the monitoring area to provide good QoS for different applications.
Sensing coverage is a fundamental problem in WSNs and has been well studied over the past few years. However, most of the previous works address only one kind of redundancy,
i.e., sensing or communication alone. The authors in [
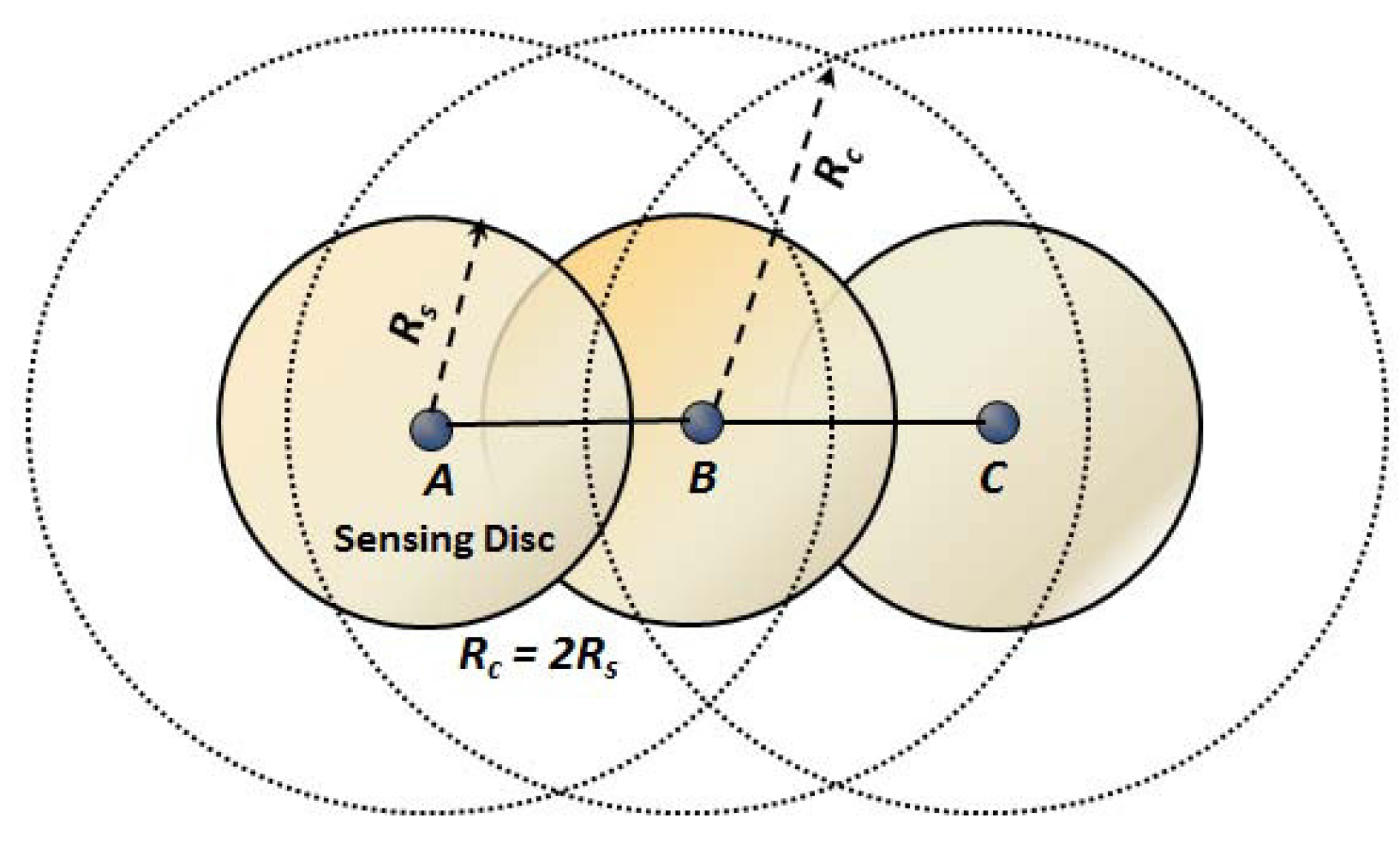
7] address how to combine coverage and connectivity maintenance in a single activity scheduling. In this work, it is proven that the communication range is at least twice the sensing range, which is the sufficient condition to ensure that a full coverage of a convex area implies connectivity among active nodes. In WSNs, nodes are deployed randomly, and it is hard or impossible to guarantee complete coverage of the monitored region, even if the node density is very high. Based on the deployment nature of the wireless sensor networks, the authors in [
8] consider the communication range to be twice the sensing range, which is the sufficient condition and tight lower bound to ensure that the complete coverage preservation implies connectivity among active nodes, if the original network topology is connected.
In WSNs, due to the random deployment of the nodes, some areas cannot be covered [
9,
10,
11] or have no connectivity. If a coverage region is sensed by at least
k nodes, this sensing method is called
k-covered, and the maintenance of a
k-covered region is discussed in [
12,
13,
14]. The coverage probability plays a fundamental role in coverage hole detection and other applications of WSNs, because of existing errors in the sensing and communication range [
15,
16]. Holes are hardly avoided in WSNs due to the various geographical environments of the monitoring region, such as the presence of ponds, obstacles or even due to physical destruction of the nodes. Ignoring the detection of holes affects the efficiency of geographic routing, data congestion and the excessive energy consumption of the hole boundary nodes. Additionally, for information flow, the hole could also affect the overall capacity of the network. Thus, the identification of the holes in sensor networks is of primary interest, because their presence often has a physical correspondence and may also map to one of the special events that are being monitored by the sensor networks.
Depending on the application environments and the level of information constraints, algorithms for identifying various coverage holes in the sensor networks can be generally classified into three categories: the computational geometry approach, the statistical approach and the topological method. In this paper, energy-efficient coverage hole detection algorithms are developed for wireless sensor networks, which can detect the presence of coverage holes distributively. The proposed hole detection methods can be achieved by considering the theoretical analysis of the point of intersection of the sensing discs of the sensors. First, the set of nodes that encloses a coverage hole is identified. This is done by taking location information of the nodes, their sensing coverage overlap and the circumference of the non-overlapping region of the sensors. Then, the coverage hole is detected by collaborating with the one-hop neighbors of the nodes that enclose the hole.
The rest of this paper is organized as follows. Related work is presented in
Section 2.
Section 3 describes the system model for detecting the holes in the WSNs. The proposed hole detection protocol is given in
Section 4. The performance evaluation of the proposed protocol is done in
Section 5, and concluding remarks are made in
Section 6.
2. Related Work
Hole detection is one of the important research issues in WSNs [
10], which can be classified as coverage holes, routing holes, jamming holes, sink/black holes and worm holes. Due to the random deployment of the sensors, some part of the monitoring region is not covered by the sensing disc of a sensor, which is called a coverage hole. The studies on coverage can be divided into two categories. The first category comprises probabilistic approaches for calculating the required node density for ensuring appropriate coverage [
17], though these studies do not prove the hole detection solutions. The second category utilizes computational geometry approaches to discover the coverage holes. In this category, the detected holes problem, which is also called the connected coverage boundary detection problem, is addressed in [
18]. Such a connected coverage boundary detection problem is classified into polygon-based and perimeter-based approaches. In the polygon-based approach, a Voronoi diagram is used for the coverage boundary detection. Briefly speaking, the VP of a node set
V is the partition of the Euclidean space into polygons, called Voronoi polygons (VPs). According to the closeness property, if some portion of the VP is not covered by the nodes inside the VP, it will not be covered by any other node, which implies a coverage hole. However, it has been shown that the VPs of the boundary nodes cannot be locally computed, and the VP-based approach is not a real localized solution. The paper in [
18] proposes a localized Voronoi polygon (LVP) to find the holes locally.
The first localized boundary node detection algorithm for the perimeter-based approach is proposed in [
19], which is based on the information about the coverage of the perimeter of each node’s sensing disk. According to the perimeter-based approach, if a node
i is the boundary node that exists at one point
j on the circle, then point
j is not covered by any one of the node
i’s neighborhood sensors. The paper [
20] proposes to check the intersection point by the node
i and
i’s neighborhood sensors not covered by other sensors. In [
21], a coverage configuration protocol (CCP) based on the perimeter-based approach is presented to calculate the degree of the intersection points and to use this degree of intersection to maintain the
k-coverage. In this paper, we define these special intersection points as hole points. However, the perimeter-based approach has two flaws. First, each node needs to check the positions and status of all of its neighbors, which is inefficient when the sensor nodes are densely deployed, and every time when a node dies, all of its neighbors need to check the coverage of their perimeters to update the existing coverage. Secondly, this approach is not efficient for using this information only to check the boundary nodes. In [
22], the authors propose algorithms to construct two sets
P and
Q using the perimeter-based approach, where
P is the end point set and
Q is the edge point set, and the hole exists if two consecutive end points are found in the counterclockwise direction. However, it has two problems. The first problem is it needs more memory to store this information, and the second problem is it cannot solve the flaws of the perimeter-based approach. In [
23], the authors propose a vector method to use the perimeter-based approach to group the hole points and to recover the coverage holes. Though they use the hole point information to recover the coverage holes, they do not consider the redundant sensors to recover them.
The formation of holes in the target field is quite common and is unavoidable due to the nature of the WSN and random deployment. This is very important to ensure that the target field is completely and continuously covered. In [
24], the authors propose an approach called the hybrid hole detection and healing (HHDH) protocol that detects and heals the coverage holes effectively with minimum sensor movements. This protocol can recover the coverage hole formed due to the random deployment of the nodes. In [
25], the authors use the knowledge of the location of each node for detecting coverage holes in randomly-deployed wireless sensor networks. In [
26], the authors present a novel method for coverage hole detection considering the residual energy of the nodes in randomly-deployed wireless sensor networks. In this paper, by calculating the life expectancy of working nodes through the residual energy, the authors make a trade-off between the network repair cost and energy waste in which the working nodes with a short lifetime are screened out according to a proper ratio. As one of the best health indicators of the sensor network, the coverage holes directly decide the quality of the sensor network. In [
27], the authors firstly propose an active contour model-based coverage hole detection algorithm for the sensor network, which can accurately evaluate both the number and the size of the holes.
The hybrid deployment of WSNs with static and mobile nodes in the monitoring area is an important issue to cover a maximum sensing area with a limited number of nodes. Furthermore, mobile sensor nodes can relocate themselves to improve the coverage area in the network. In [
28], the authors propose a method that reduces the complexity of the relocation of the initial deployment and coverage hole healing of mobile sensor nodes in the hybrid WSNs. Their method finds the ways to get the shortest distance movements for the mobile nodes in WSNs. An adaptive threshold distance is used to eliminate some mobile nodes, which are already occupied or situated within the threshold distance from the optimal new positions. In [
29], the authors develop distributed algorithms to detect and localize the coverage holes in sensor networks. This paper uses algebraic topological methods to define a coverage hole and develops algorithms to detect a hole. In [
30], the authors design a stochastic learning weak estimation-based scheme, namely mobility prediction inside a coverage hole. The main objective of this scheme is that it could be able to correctly predict the mobility pattern of a target inside a coverage hole with low computational overhead.
In [
31], the authors propose an intelligent strategy called the improved hybrid particle swarm algorithm to repair the coverage holes. Taking a hybrid sensor network, the authors consider the displacement of mobile sensors, energy consumption and energy balancing together. Their proposed protocol can schedule the redundant mobile sensors effectively to repair the coverage holes by moving them to appropriate locations. Besides, they improve the event detection rate to calculate the event detection lost or the detection error and coverage holes that seriously damage the quality of monitoring in WSNs. In [
32], the authors design a localized coverage force division algorithm to find the coverage quality in WSNs. However, their algorithm can neither detect the coverage holes nor find the shape and size of a hole. In [
33], the authors propose a novel method for describing the coverage holes graphically. Their proposed graphical hole description method is divided into two phases, namely coverage hole detecting and coverage hole describing. In [
34], the authors present a coverage hole healing algorithm taking the existing nodes of the WSN to cover the holes. Their algorithm resolves a full coverage while minimizing the overlapped area of the sensing disks and deploying a minimum number of nodes.
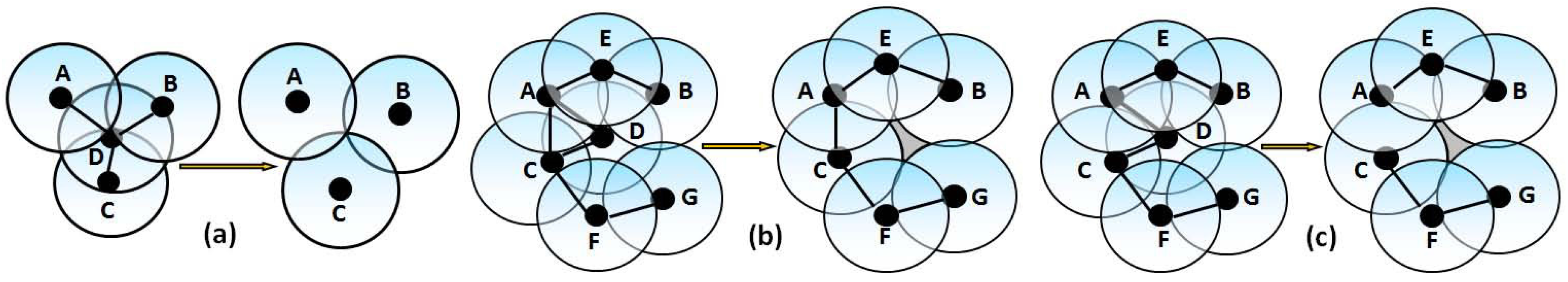
It is to be noted that wireless sensors are deployed to monitor certain regions remotely for a wide range of potential applications, such as environment monitoring, object tracking, habitants monitoring and traffic control. If one or more sensors are dead in the network, the whole purpose of deploying sensors over the monitoring area becomes useless. As shown in
Figure 1a, if the sensor
D is dead, no communication is established among the sensors. As shown in
Figure 1b, if sensor
D is dead, coverage hole is created in the network, and the target within that area remains undetected. As shown in
Figure 1c, if the sensor
D is dead, both coverage, as well as communication holes are created, and therefore, the purpose of deploying sensors to detect any target remains futile.
In this paper, we propose a perimeter-based approach to find the coverage holes considering the points of intersection of the sensing discs of the wireless sensors deployed randomly over a monitoring region. The main contribution of this work over the existing hole detection protocols can be summarized as follows:
A distributed coverage hole detection (DCHD) protocol is proposed to detect the coverage holes without the help of the sink by simply calculating the points of intersection of a node with its one-hop neighbors and checking them as covered or not.
Algorithms are designed to filter the points of intersection into covered and non-covered points and then use this filtering method to detect the coverage hole. Such a filtering method can be done dynamically in an autonomous manner by maintaining the network integrity.
Our proposed algorithms can detect the nature and shape of the coverage holes, which can be highly useful and make it easier to redeploy the nodes.
4. Proposed Hole Detection Protocol
In this section, a
distributed coverage hole detection (DCHD) algorithm is designed to detect the bounded or non-bounded coverage holes present in the monitoring region. This scheme is proposed not only to solve the flaws of the perimeter-based coverage hole detection approaches, but also to consider the CIP to find a hole, which can reduce the time complexity of the coverage hole detection. In the first phase of the scheme, each sensor finds out its CIP set, as described in
Section 4.1. In the second phase, each sensor also verifies if any of its points of intersection belong to a CP set or not, as described in
Section 4.2. In the third phase, as described in
Section 4.3, each sensor localizes and separates its CIP, which is used to determine the bounded or unbounded coverage hole. In the fourth phase, a sensor collaborates with its one-hop neighbors in the clock-wise direction and connect to its CIP to detect the presence of a coverage hole, as described in
Section 4.4.
4.1. Determination of CIP
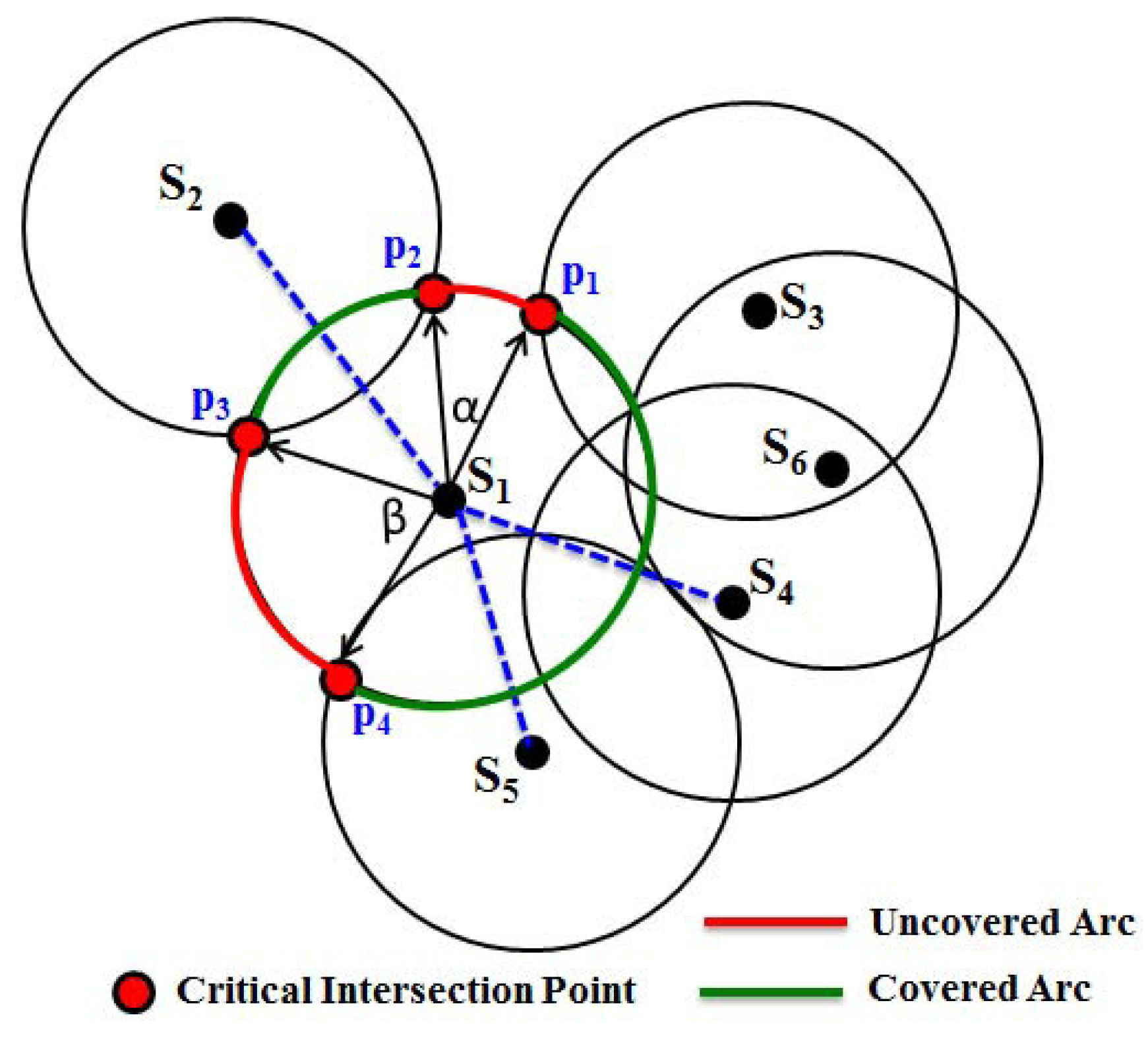
It is assumed that each sensor knows its own location information. After deployment of the nodes, each sensor exchanges its location information to know the location of its one-hop sensing neighbors. For simplicity, throughout the paper, sensing neighbors are refereed to as the neighbors. Upon receiving the location information from its one-hop neighbors, each sensor has to determine its CIP set (
P) and
sensing neighbors set (
N). The algorithm for calculating the CIP is given in Algorithm 1. Upon executing the CIP calculation algorithm, each node has to maintain the list of its one-hop neighbor’s information and corresponding CIP, as given in
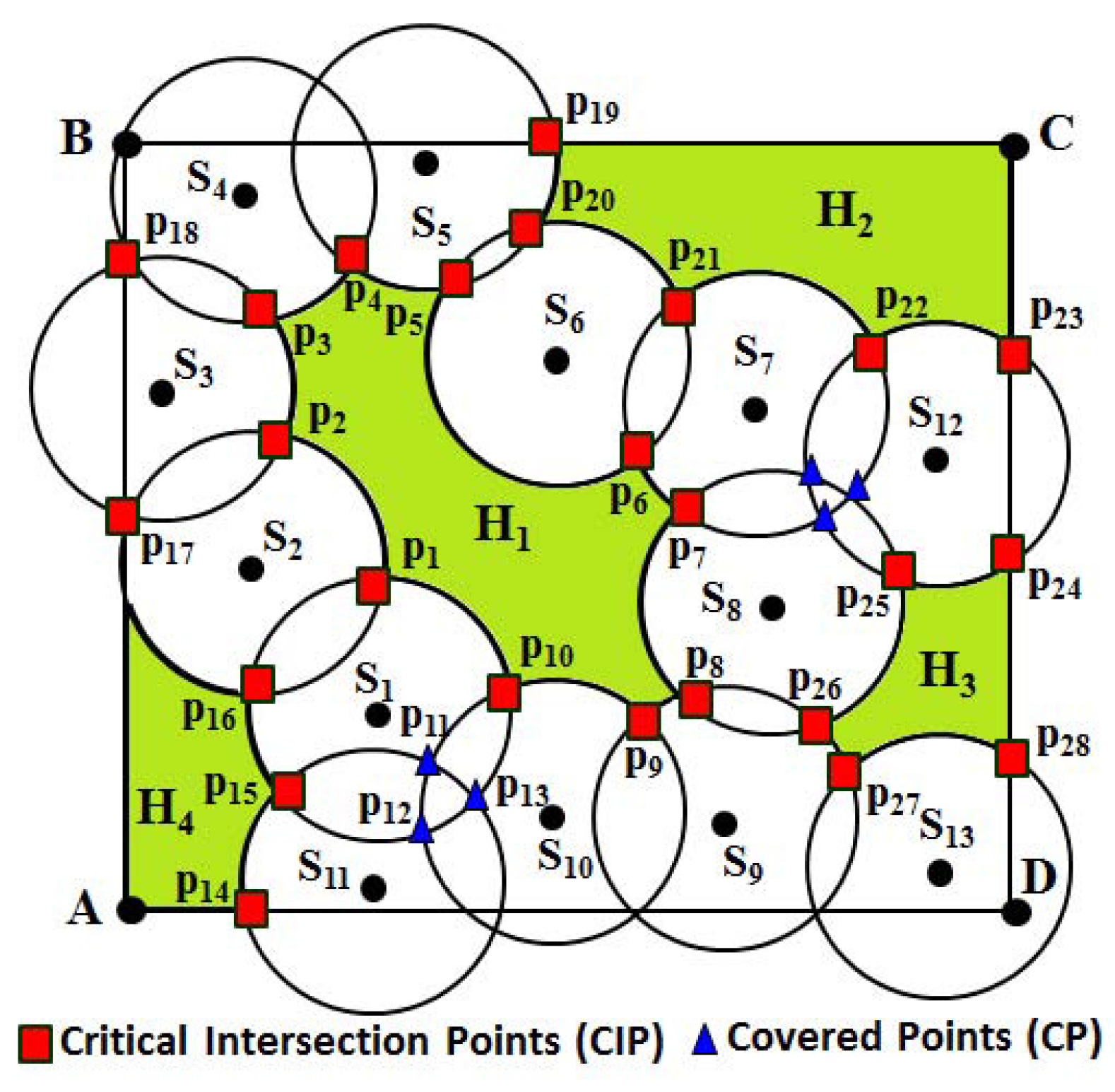
Table 1. For example, the neighbors and CIP of different nodes given in
Figure 2 can be shown in
Table 1.
It is to be noted that there may be some isolated sensors deployed over the monitoring region R. Since the isolated sensors cannot have any sensing neighbors, they would not execute Algorithm 1, and there must be a coverage hole around that sensor. Suppose any sensor isolate has to calculate its CIP. First, chooses its one neighbor from its neighbor set N and calculates the intersection points . If or is inside the monitoring region R and is not covered by any other neighbors of , and become the elements of the CIP set P. Besides, is selected as the member of the sensing neighbors’ set N. This process continues for all of the neighbors of .
For example, as shown in
Figure 2, let us consider sensor
. The one-hop sensing neighbors’ set of
can be
. Since the sensing disc of
intersects the sensing disc of
and both points of intersection are not covered by any of its neighbor, points
and
becomes the CIP. Similarly, the sensing disc of
also intersects the sensing disc of
, where the point of intersection
is covered by another neighbor
, whereas the point
is not covered by any of its neighbors. Hence, only point
becomes the CIP. Thus, the CIP set of
can be given as
. Based on Algorithm 1, after the sensor
finds its CIP, its next hop sensing neighbor
clockwise finds its one-hop sensing neighbors set,
i.e.,
, and its CIP set can be given as
. Thus, the process continues for all sensors, and finally, as shown in
Figure 2, the set of CIP can be calculated as
.
| Algorithm 1 Algorithm for determining CIP of a node i. |
- 1:
Input: - 2:
: Set of all sensing neighbors of a node i; - 3:
Output: - 4:
: Set of CIP of node i; - 5:
CIP Set Calculation Procedure: - 6:
Select any node i randomly; - 7:
Initialize ; - 8:
if () - 9:
{ - 10:
Scan all members of ; - 11:
if (i is a non-border sensor) - 12:
{ - 13:
Find intersection point p of node i with all members of ; - 14:
Find corresponding sensing neighbor s having an intersection point with node i; - 15:
Update and ; - 16:
} - 17:
if (i is a border sensor) - 18:
{ - 19:
Scan all members of ; - 20:
Find point of intersection b of node i with border line of the monitoring region R; - 21:
Find point of intersection p of node i with all members of ; - 22:
Update and ; - 23:
} - 24:
} - 25:
else - 26:
{ - 27:
i is an isolated sensor; - 28:
Terminate the procedure; - 29:
}
|
4.2. Determination of CP
It is assumed that each node knows its sensing neighbors set (N). Taking the set of sensing neighbors set N as the input, each sensor can find out if the point of intersection with its one-hop neighbor is a CP or not. The details of the procedure for calculating a point as CP or not is given in Algorithm 2.
| Algorithm 2 Algorithm for determining the CP of a node i. |
- 1:
Input:: Set of all sensing neighbors of node i; - 2:
Output:: Set of covered points of node i; - 3:
Calculation Procedure of CP set: - 4:
Select any node i randomly; - 5:
Initialize ; - 6:
if () - 7:
{ - 8:
Scan all members of ; - 9:
if (i is a non-border sensor) - 10:
{ - 11:
Find intersection point of node i with j, which is one member of ; - 12:
Check if the point p is covered by a sensor k, which is another member of and ; - 13:
if (p is covered by k) - 14:
p is a CP; - 15:
else - 16:
{ - 17:
p is a CIP or a border point; - 18:
Execute Algorithm 1 to find CIP; - 19:
} - 20:
} - 21:
else - 22:
{ - 23:
i is a border sensor; - 24:
Find point of intersection b of node i with border line of the monitoring region R; - 25:
Check if point b is covered by any neighbors of i; - 26:
if (point b is covered) - 27:
b is a CP; - 28:
else - 29:
Execute Algorithm 1 to find CIP; - 30:
} - 31:
} - 32:
else - 33:
i is an isolated sensor;
|
Let us consider an example, as shown in
Figure 2. As shown in the figure,
is the one-hop sensing neighbors set of
. Based on Algorithm 2, let the sensor
first find its one-hop neighbors and then find the point of intersection with its sensing neighbor
.
and
are the points of intersection of the sensing disk of
with
, out of which
is covered by its other neighbor
. Hence,
becomes the CP, whereas
becomes the CIP, as it is not covered by any other sensor of the network. Similarly, the sensing disc of the sensor
can have points of intersection
and
with the sensing disc of the sensors
and
with the sensing disc of
. Here, points
and
are covered by the neighbors
and
, respectively. Hence, the points of intersection
and
become CP as marked in blue color in
Figure 2. It is to be noted that a point of intersection that falls outside the monitoring region
R is not taken into consideration for determining it as a CIP or CP.
4.3. Localization of CIP
In this section, we describe how to localize all of the CIP to detect the coverage hole. As discussed in
Section 4.1 and
Section 4.2, the points of intersection of all of the sensors with their one-hop neighbors are classified into CP or CIP. However, a sensor may have more than one CIP at different sides of its sensing disc. It is to be noted that there is no confusion in detecting the coverage hole if the intersection point of a sensor has only one CIP. However, if a sensor has more than one CIP, it is necessary to localize them either on the lower or upper side of the line connecting the location of the sensor to the location of its neighboring sensor. For example, as shown in
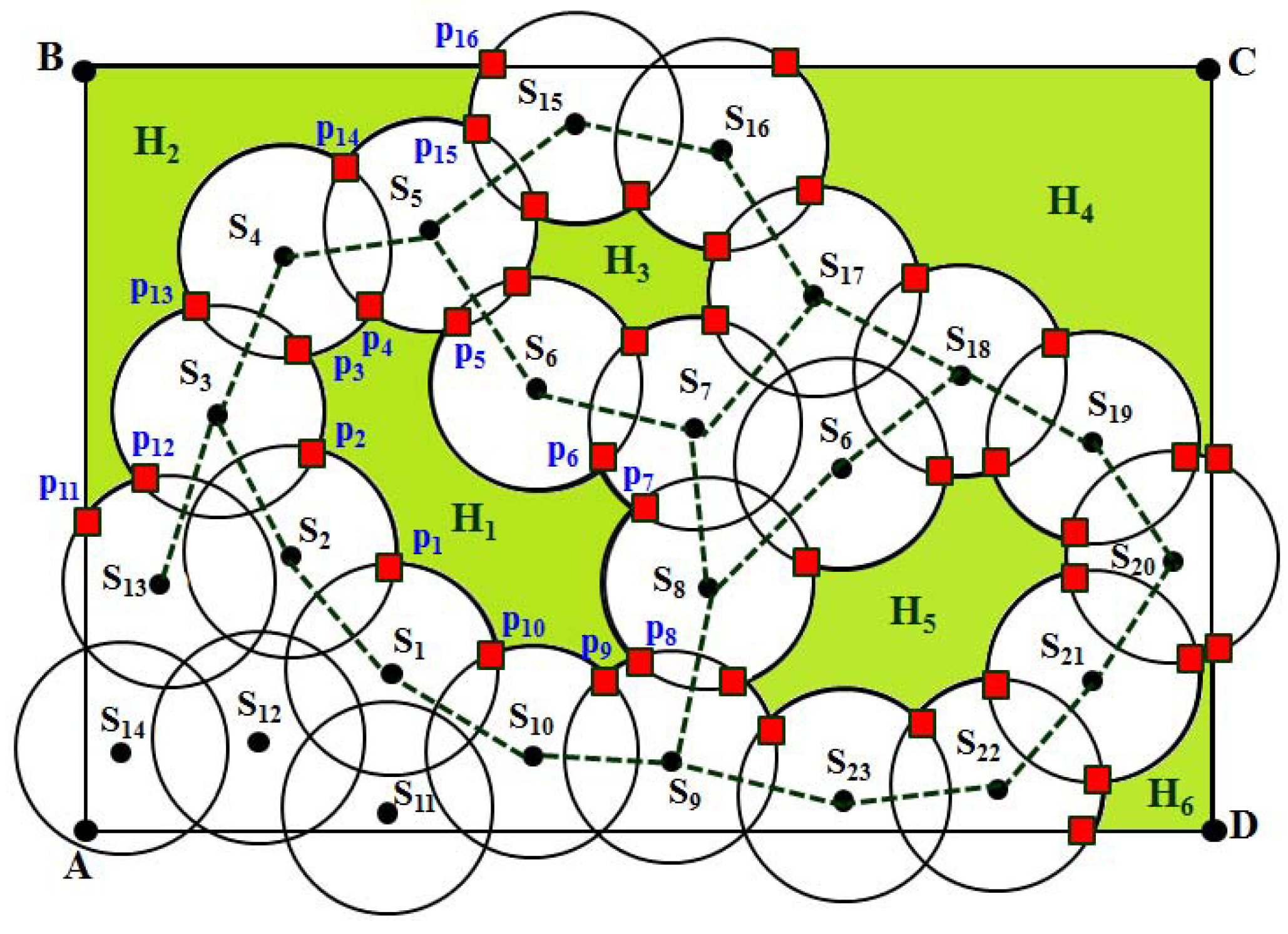
Figure 4, sensor
has four different CIP, such as
and
, out of which
and
are located at one side of the sensing disc of
, whereas
and
are located at the other side of its sensing disc. Then, it is important to know how to differentiate those points theoretically to detect the coverage holes remotely. In order to differentiate those points, first, connect the location of one sensor to the location of a one-hop neighbor of that sensor, as shown in
Figure 4. For example, sensors
and
are the one-hop neighbors of
. Here,
and
are the CIP between the sensors
and
. Now, draw a line
between the centers of the sensing disc of sensors
and
. Using simple coordinate geometry, it can be calculated that
and
lie below and above the
, respectively. Similarly,
and
are one-hop neighbors of
, and
and
are the CIP between the sensors
and
, respectively. By joining the centers of the sensing disc of
and
, it is observed that CIP
lies below the line
, whereas CIP
lies above the line
.
It is to be noted that the two points of intersection
and
between any two sensors
and
having locations
and
, respectively, can be calculated as given in Equations (1) and (2), where
is the distance between sensors
and
. Equation (3) represents the equation of the sensing disc of sensors
and
. Let
=
and
=
be the two points of intersection between the sensors
and
. Then,
Considering the location of each sensor and CIP, as given in the above equations, the procedure for localizing each CIP is given in Algorithm 3.
| Algorithm 3 Localization of CIP. |
- 1:
Input: - 2:
: Set of all sensing neighbors of node ; - 3:
: Any sensing neighbor of node ; - 4:
and : CIP between sensors and ; - 5:
: Set of all lines connecting to the location of sensor to location of ; - 6:
Output: - 7:
: Set of CIP below the line ; - 8:
: Set of CIP above the line ; - 9:
Localization of CIP - 10:
Initialize and ; - 11:
Do: for all CIP between sensors and ; - 12:
{ - 13:
Select any sensor ; - 14:
Select another sensor from the set ; - 15:
Check location of with respect to the line ; - 16:
if ( is above ) - 17:
{ - 18:
Assign ←; - 19:
Update ; - 20:
} - 21:
else - 22:
{ - 23:
Assign ←; - 24:
Update ; - 25:
} - 26:
}
|
4.4. Detection of Coverage Holes
In this section, the CIP are organized to detect the hole based on their location either above or below the line connecting to the location of any two neighboring sensors. The points that are below the connecting lines form a set of points as set , whereas the points above the line form a set . Then, in each set, those points are arranged in a clockwise fashion to check whether the nature of the hole is bounded or unbounded. By arranging the points either in the set or in the clockwise direction, a bounded coverage hole is detected if all elements of those sets form a loop, i.e., if the initial and terminal points are the same. However, an unbounded coverage hole is detected, if all elements of a set do not form a loop. It is to be noted that whether the coverage hole is bounded or unbounded is determined by the sensors that enclose them. The DCHD algorithm is run in each node to find the CIP and to detect the hole in collaboration with its one-hop neighbors. Once the hole detection procedure is terminated by the sensors, the information is transmitted to the sink by the sensor that has initiated this procedure. It could be possible that a node may be adjacent to more than one hole. In this case, the hole does not prevent the sensor from sending data to the sink. The node has to send information about the presence of both holes along with the nature of the holes to the sink. In our protocol, it is assumed that coverage holes are created due to the death of the nodes, and the role of the DCHD protocol is to detect the holes instead of detecting whether a node is dead or not. However, it is obvious that a node cannot have sensing overlapping with its one-hop neighbors, if a node is dead, and therefore, CIP is calculated and the hole detection done in the network.
In order to explain the detection of the coverage hole, let us take an example as shown in
Figure 4. As discussed in the above subsection, the CIP are classified into two different sets based on their position. After calculating the position of each CIP either above or below the lines connecting to the centers of each sensing disc, two sets of points can be classified as sets
and
. Thus, for the sensors
∼
, the set
, where
is revisited, which implies that these points can form a loop, and therefore, a bounded coverage hole exists in between those sensors. Similarly, for the sensors
,
,
,
,
and
, the set
, where no point is revisited, which implies that though there is a coverage hole, the hole must be unbounded. It is to be noted that as shown in
Figure 4, by connecting sensors
,
,
,
and
, though those connecting lines can form a loop, no CIP is localized below those lines. This implies that all points of intersection between those sensors below the lines are detected as CP, and therefore, no coverage hole can be detected there. Taking all of the phases of the coverage hole detection procedure, the complete flow of the DCHD protocol can be shown as in
Figure 5, and the DCHD algorithm is given in Algorithm. 4.
| Algorithm 4 Distributed coverage hole detection (DCHD) procedure. |
- 1:
Input: - 2:
: Set of all sensing neighbors of node ; - 3:
: Set of CIP below the connecting line; - 4:
: Set of CIP above the connecting line; - 5:
Output: - 6:
Type of coverage holes; - 7:
Detection of coverage holes: - 8:
Select any sensor ; - 9:
Select another sensor from the set ; - 10:
Find points of intersection between and ; Let it be and ; - 11:
Select another sensor from the set ; - 12:
Check and are covered by or not; - 13:
if ( and are not covered by ) - 14:
{ - 15:
Assign ←, ←; - 16:
Execute Algorithm 3; - 17:
Function call: Hole_Type(); - 18:
} - 19:
if ( || is a CIP) (ex: Let be a CIP) - 20:
{ - 21:
Assign ←; - 22:
Execute Algorithm 3; - 23:
Function call: Hole_Type(); - 24:
} - 25:
if (both and are covered) - 26:
{ - 27:
Assign ← and ; - 28:
The network is fully covered; - 29:
Terminate the hole detection procedure; - 30:
} - 31:
Hole_Type() - 32:
Arrange all points of and in clock-wise; - 33:
if (initial point == terminal point) - 34:
Hole is bounded; - 35:
Else: Hole is unbounded;
|
4.5. Construction of Covered and Uncovered Arcs
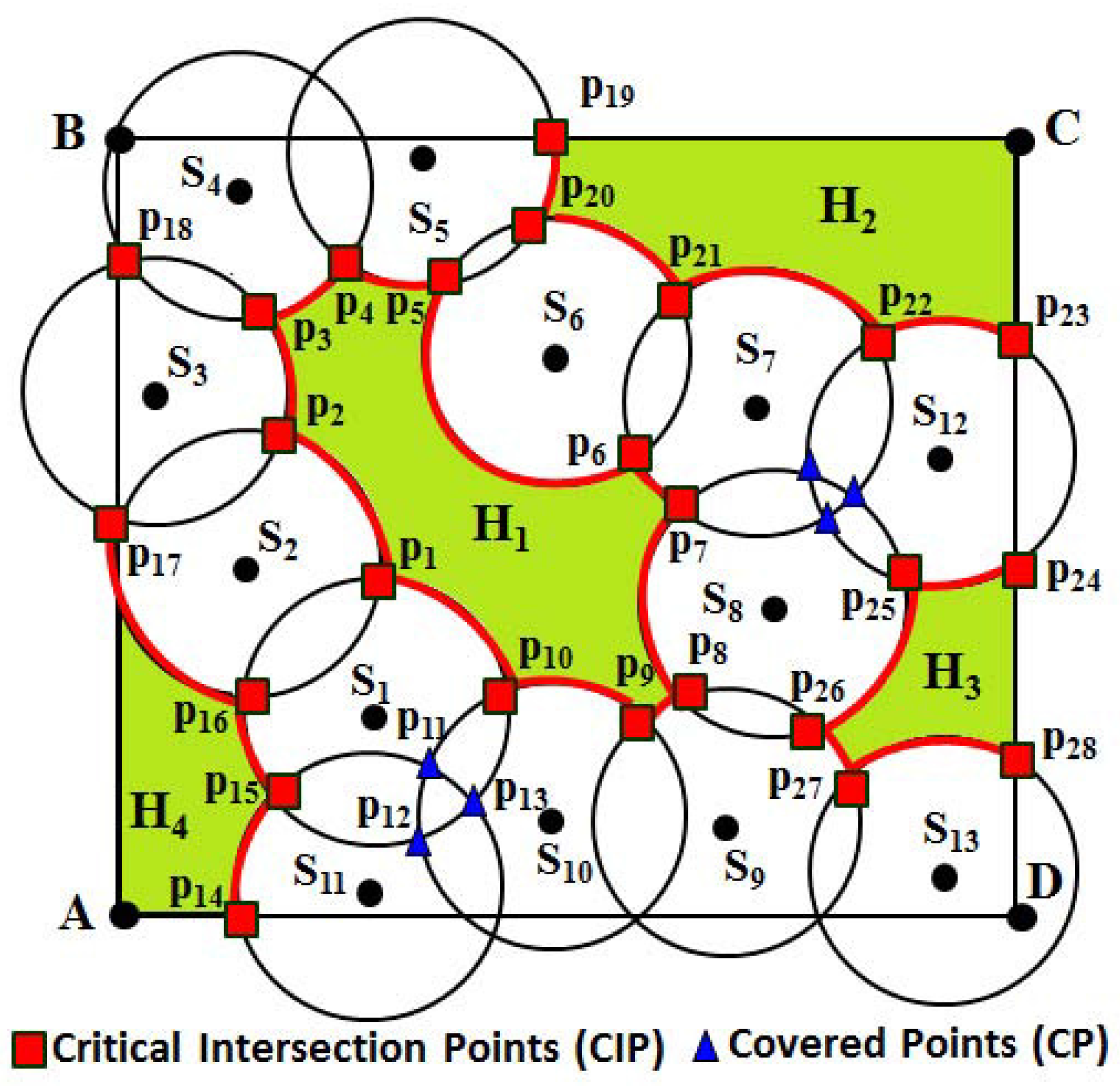
As discussed in the previous subsections, the presence of a coverage hole is detected by using the critical intersection points and after knowing their locations. However, it is essential to know the shape of the bounded or unbounded coverage holes. In this section, we propose a mechanism for how to get the shape of the hole by constructing covered and uncovered arcs. As shown in
Figure 6, let
,
,
,
and
be the sensing neighbors of the node
. Here,
,
,
and
are the CIP of the sensor
. As discussed in the above subsection, it can be determined that
and
are located at one side of its sensing disc, whereas
and
are located at the other side of the sensing disc. It is to be noted that the location of all CIP and the position of each sensor are known. Since the locations of the one-hop neighbors of a sensor are known, we can connect the location of one sensor to another. Thus, as shown in
Figure 6, first, the lines
,
,
,
are drawn, and the arcs are constructed as follows.
After locating the CIP, we have to construct the arcs along the circumference of the sensing disc of the sensor
. For this reason, first consider the points
,
to draw the vectors
and
from the position of the sensor
. Let
α be the angle between these two vectors, which can be calculated using the formula
α = arccos
. Then, the arc length of the arc can be calculated as
=
. Thus, the arcs
,
and
are calculated. However, if any of those arcs intersect with the
,
,
,
, they are considered as
covered arcs and, therefore, are omitted for constructing the coverage hole. Based on this rule, as shown in the figure, only arcs
and
are considered as the
uncovered arcs and are separated, as they do not intersect any of those connecting lines. Since arcs
and
are at different sides of the sensing disc, they are separated into two sets. Based on the initial point and terminal points of each arc, finally, they are connected with each other to construct the coverage hole by which, the shape of the hole can be known. For example, as shown in
Figure 7, taking
as the starting sensor, the arcs
,
,
,
, ∼
marked in red are connected to each other, which can form a hole. Thus, these uncovered arcs enclose the bounded coverage hole
. Similarly, as shown in
Figure 7, coverage holes
,
and
are enclosed by the arcs marked in red.