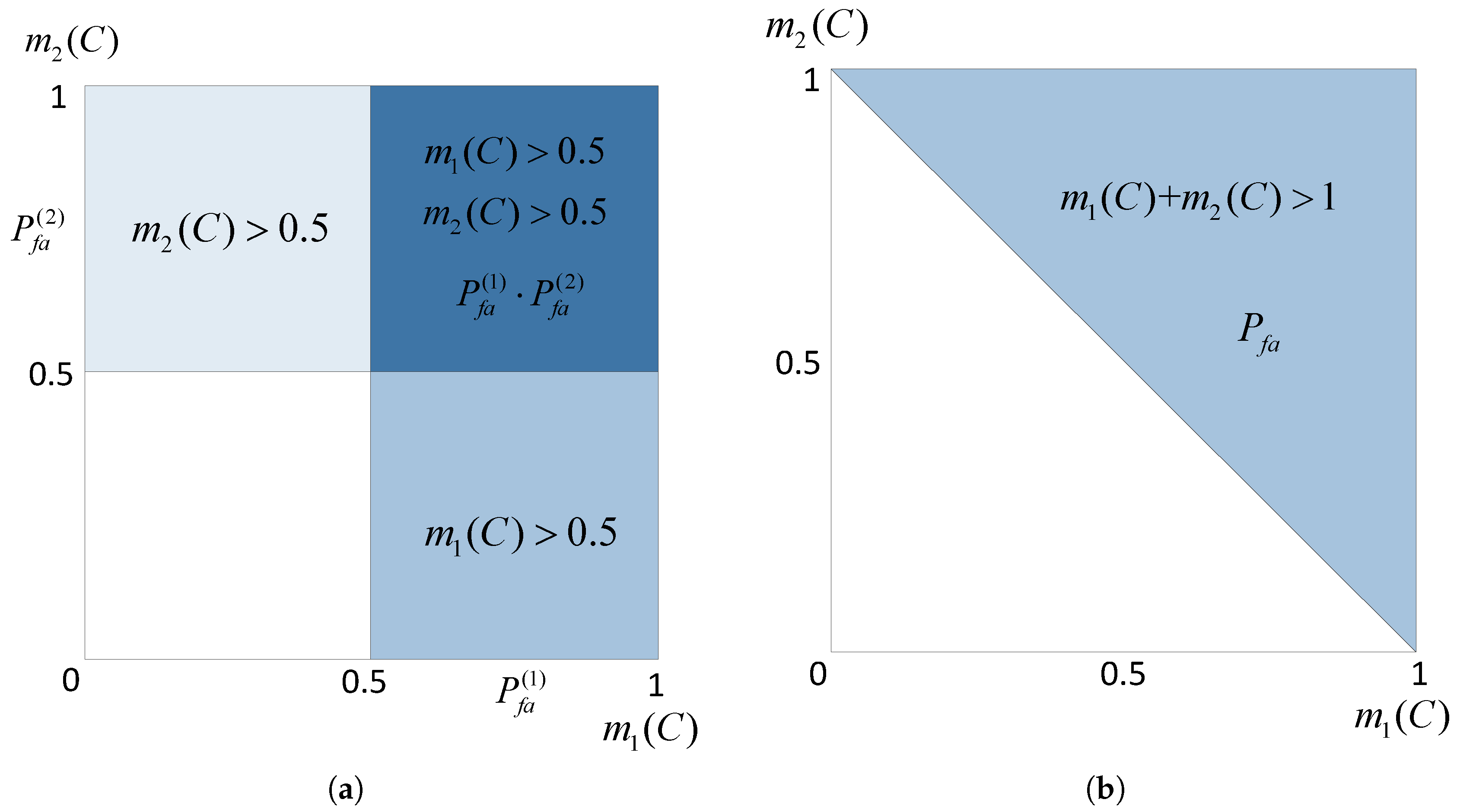A detailed discussion of the proposed method is provided in this section. First, a simplified frame of discernment is given. The simplification is for the purpose of the quantization for detection results. Then, the valuation of the belief function, which is the key of information fusion, is given and discussed. Finally, the performance of detections’ fusion is analyzed briefly.
2.1. The Model of Detections’ Fusion
Most of the spoofing detections focus on the anomalies of signal features or measurements. Generally, each detector aims at only one feature, and the result is evidence of the presence of the spoofing attack. However, this evidence would be inadequate and not absolute reliable in some cases. The combination of the results from multiple detectors is an approach to deal with this problem. A method based on DST to fuse multiple detectors is proposed in the following.
According to DST, a complete frame of discernment in spoofing detection should contain all possible mutually exclusive declared propositions, such as the noise, authentic signal, counterfeit signal and the mixture of them. They indicate the identity of the signal. However, this complete frame of discernment sets up obstacles for implementation. The main problem is the evaluation of BPA. Thus, it is necessary to simplify this frame for application. In what follows, the noise, authentic and counterfeit signal are denoted as “N”, “A” and “C”, respectively, and the frame of discernment is denoted as Θ.
In practice, noise is universal because the environment temperature cannot be absolute zero. The acquisition module of the GNSS receiver would determine the absence of satellite signals if there is only noise. Thus,
N is redundant in Θ. In what follows, the object is limited to the satellite signal that has been processed by the receiver, regardless of its authenticity. In a broader sense,
C does not only represent the spoofing signal, it also means the abnormal change of the satellite signal. Besides,
A and
C are exclusive for a signal. If authentic and counterfeit signals are mixed together in a processing channel and cannot be separated by the GNSS receiver, they should be marked as “abnormal”, and the identified result should be
C. Thus, it is unnecessary to reserve a position for the mixture “
” in Θ. Therefore, Θ could be simplified as follows:
That is, there are only two possible results of spoofing detector, “authentic” or “counterfeit”; the more generalized description is “no spoofing” or “spoofing”. This simplification of Θ facilitates the valuation of BPA and the belief functions, it also simplifies the combination rule. According to DST, for a possible result of one detector, the BPA is equivalent to the belief function because there are only two elements in Θ. Herein, the belief function is denoted as
, which corresponds to detector
.
follows:
where
ϕ represents an empty set.
implies the believable degree of the evidence from detector
. For example,
tends to determine the signal as “
A” if
; otherwise, it tends to determine the signal as “
C”. The conflict degree of different evidence can be defined as follows:
The combination result is reliable if all evidence is coincident, while it is unreliable when the conflict degree is high. means that some evidence is completely opposite, such as and .
Due to the inference of the combination rule of DST [
13] in the case of binary detection, the combined
are given as follows:
where
N is the number of spoofing detectors. In the case that
, there is
;
cannot be obtained according to Equation (4). It is necessary to add a rule with Equation (4) in such a case as follows:
In what follows, they are denoted as Equation (4) together. After the fusion, a final decision must be made to determine the authenticity of the signal. The decision rule is given as follows:
As , the rule of Equation (5) determines “A” if and determines “C” if . That is, 0.5 is the threshold of the final decision after detections’ fusion.
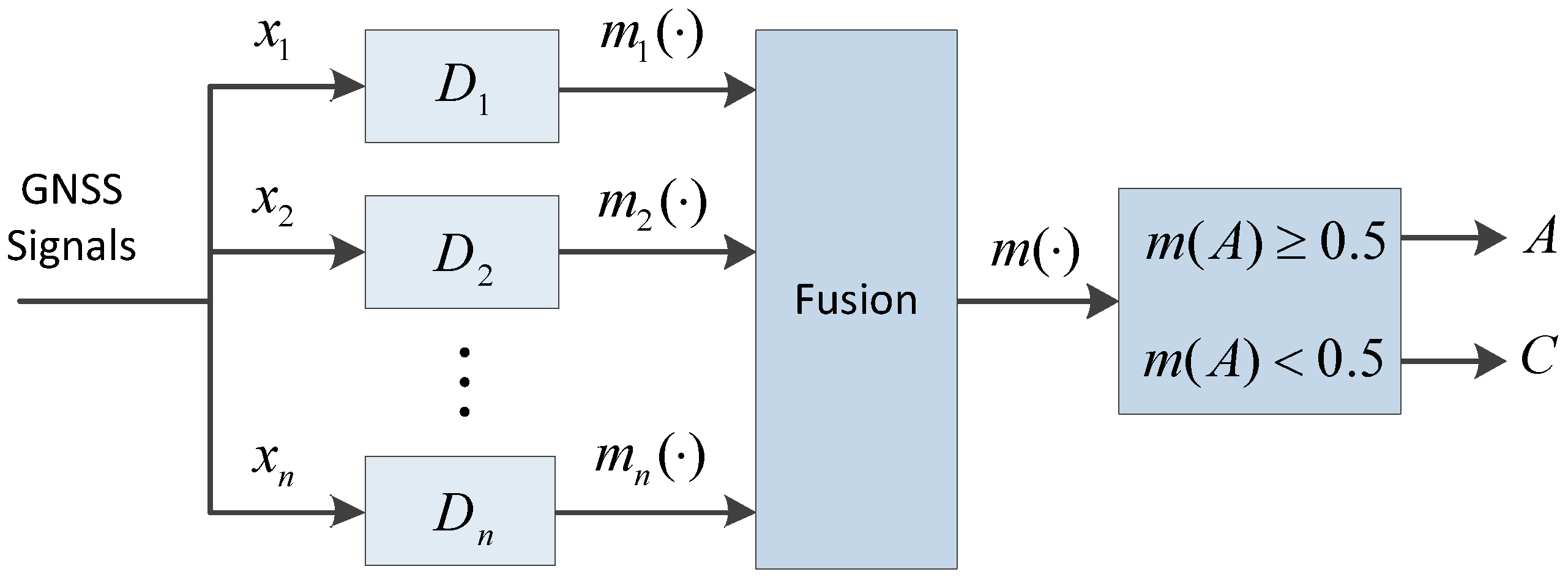
Figure 1 shows the diagram of the detections’ fusion. Detector
points at
, which could be any feature of the GNSS signals or measurements, such as signal power, Doppler shifts, code delay, pseudoranges, the results of positioning, etc.
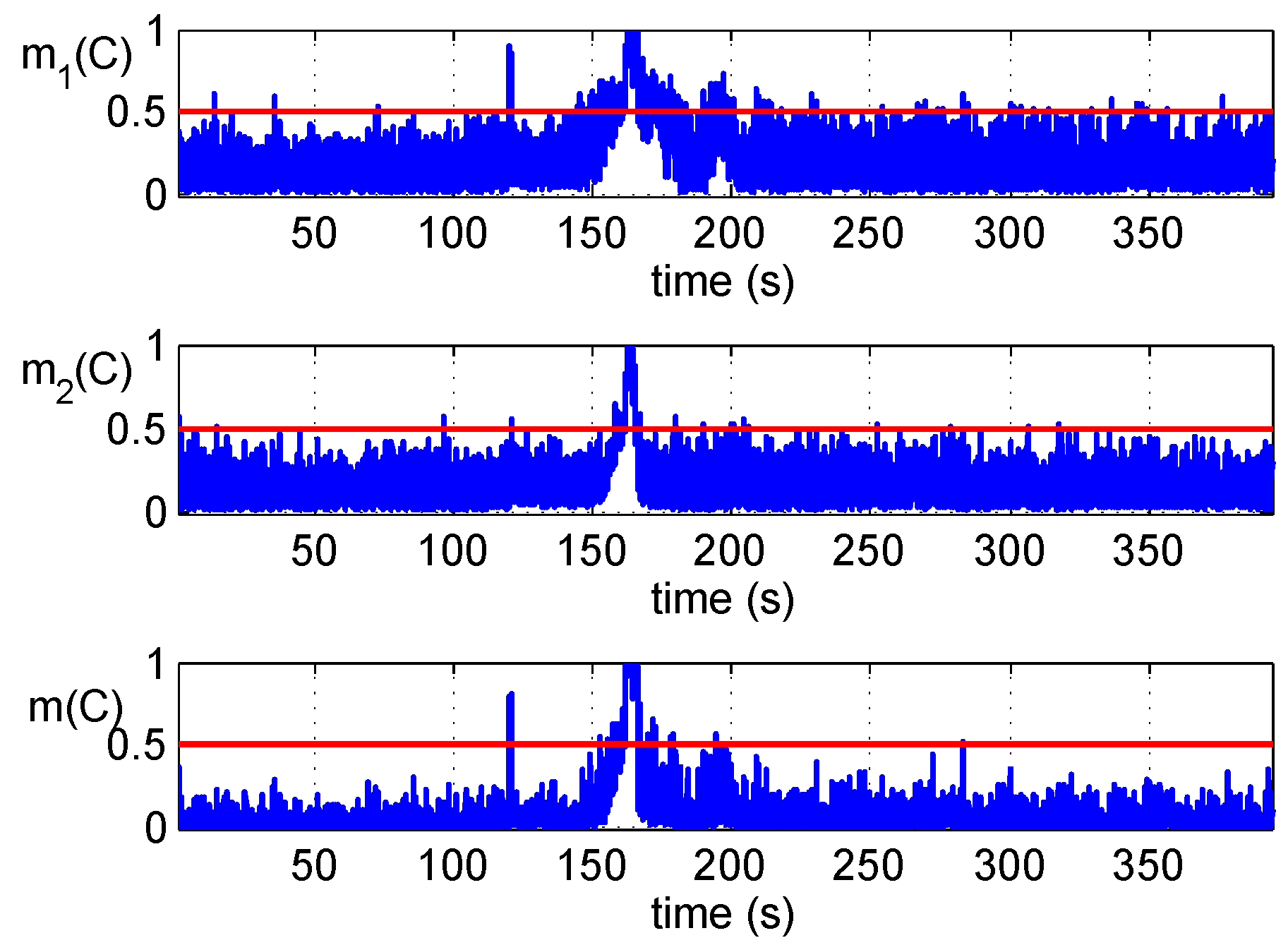
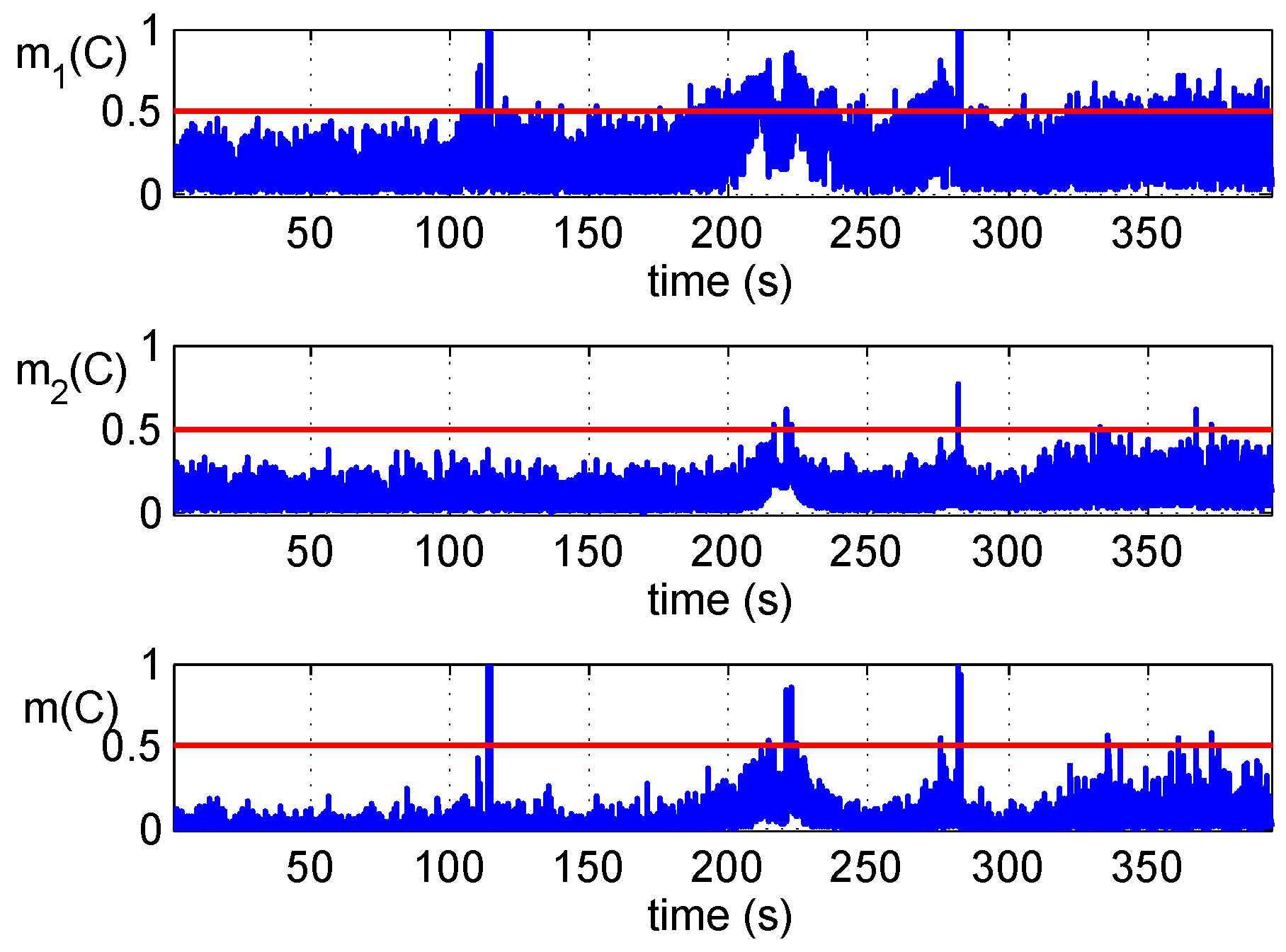
It should be noted that not the different detection methods, but the different signal features are the key of fusion. The evidence of the spoofing attack is collected from the detectors and fused according to the rule of Equation (4). The fusion makes the result more credible if the evidence from different detections is coincident, while it would give a compromise result according to all evidence if it is conflictive. Two examples are provided in
Table 1 as follows to demonstrate the combination of coincident and conflictive evidence.
2.2. Valuation of the Belief Function for GNSS Spoofing Detections
Belief functions are the key to the detections’ fusion. They represent the reliability of the corresponding measurement or features of the signal. The belief function is calculated based on the basic probability assignment (BPA) in DST. As previously mentioned, BPA is equivalent to the belief function in the case of binary detections. However, there is no general way to get BPA or the belief function for a detection result. This section proposes a method to valuate the belief function and provides a brief discussion about two spoofing detections.
Most of the spoofing detections are equivalent to hypothesis testings. They can be described as:
where
and
are hypotheses that represent the absence and presence of a spoofing attack, and they are equivalent to
A and
C of Equation (1), respectively.
is the test statistic of
x, which is a measurement of the signal.
γ is the threshold of detection. Here,
x could be any signal features and measurements, such as the absolute power or carrier-to-noise ratio (
) of the received signal, Doppler shift, outputs of the correlator, pseudorange measurement, etc.
The detection of Equation (6) makes a hard decision to decide whether the signal is authentic or not. It is easy to implement, but it loses some information and increases the error decision.
is a quantization of the anomaly of
x, and it also can be considered as a soft decision of the authenticity of signal. The belief function for the detection results of detector
can be defined as:
where
is the belief function,
and
represent the test statistic and threshold of
, respectively, and
f is the function that maps
and
to a real number. The mapping is subject to:
This is in keeping with the decision rule of Equation (6). However, unlike Equation (6), of Equation (7) provides a soft decision of the authenticity of the signal. Compared with the hard decision, it retains more information of x. More than that, Equation (7) makes it possible to fuse the information from multiple detections to reduce the probability of error decisions.
There are many forms of
f to meet Equation (8). The
p-value of hypothesis testing would have more proper to reflect the reliability of the results than the test statistic and threshold. However, the calculation of the tail probability for each obtained statistics in the method of the
p-value is too complicated. Herein, two definitions of
f are proposed for simplicity in the application. In what follows,
and
are assumed as non-negative, and this is possible in a proper way. One definition of
f can be given as:
is a decreasing function of
, and it is easy to implement. However,
descends slowly even if the anomaly is obvious enough. Besides,
is in a half closed interval
because the base number of the power function is less than one. Another definition of
f is given as:
meets Equation (8), as well, and it is in a closed interval
. However,
descends quickly, and it makes a decision
even if the anomaly is not obvious enough. The decision
is strong, and it makes an irrevocable decision while all other detectors are meaningless.
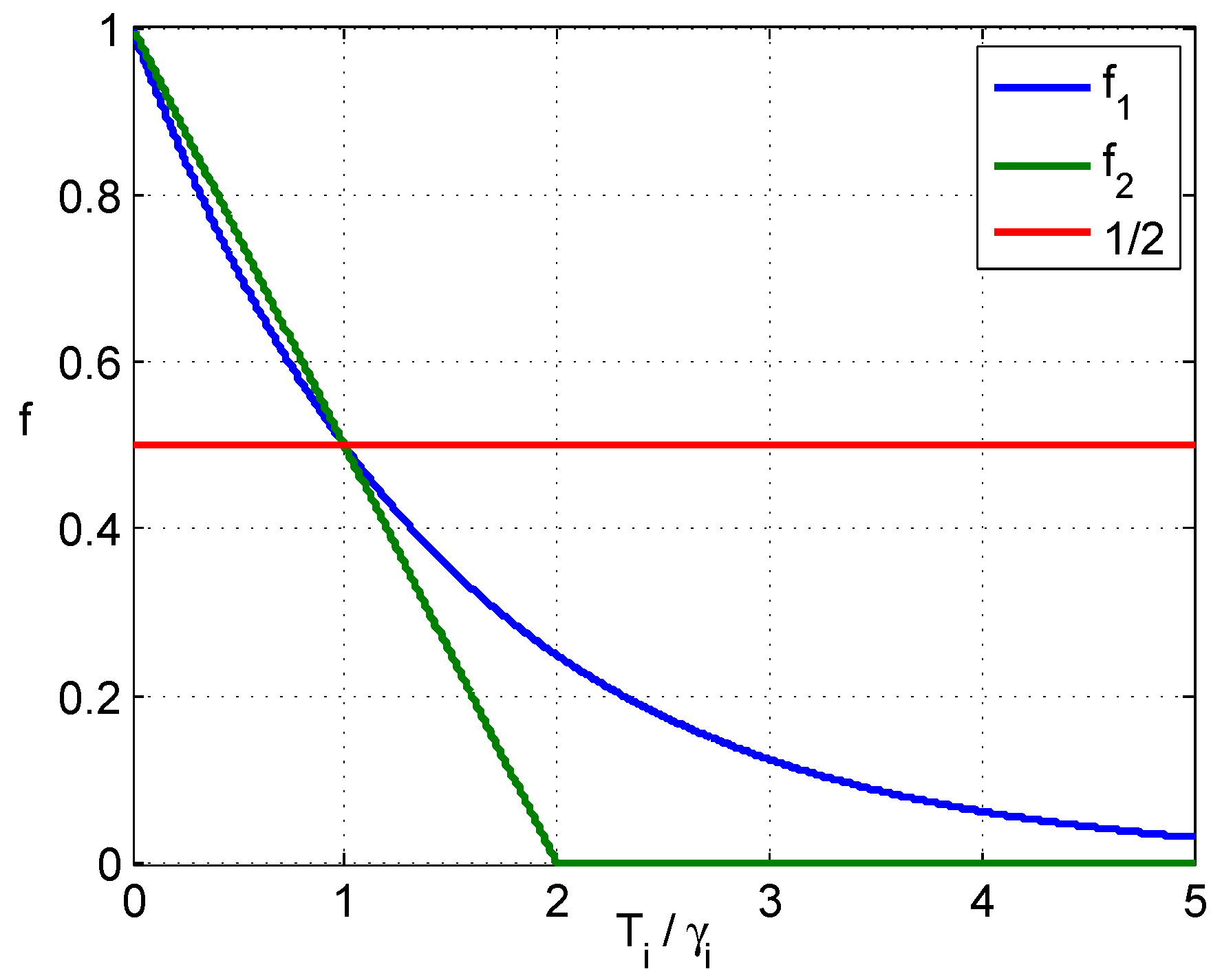
Figure 2 shows the curves of
and
, where
is plotted on the horizontal axis, and the red line is the threshold to determine “
A” or “
C”.
As mentioned previously, both
and
have weakness in practice. The linear combination of them would be applicable, and it can be given as follows:
where
α is the weight of
; it can be set according to the actual implementation.
2.3. Performance of Detections’ Fusion
A spoofing detection can be fused with others by the method as mentioned previously, as long as it could be depicted by a hypothesis testing as Equation (6). There are two types of errors in hypothesis testings. One is false alarm and the other is missed detection. The former is the incorrect rejection of the true hypothesis
, while the latter is the failure to reject the false hypothesis
. The probabilities of these two errors can be described as follows:
where
is the false alarm probability and
is the missed detection probability. They are contradictory. For a given sample set,
increases with the reduction of
, and vice versa.
and
cannot be reduced simultaneously unless the sample size increases, but this is infeasible especially in practice. Detection aiming at data set for a long time cannot reflect the real-time changes of signals. This limits the performance of single spoofing detection. However, it is different in case that multiple detections are fused, because the false alarms would not happen simultaneously in different detectors. This means that false alarms of fused detection would be much less than those of each detector.
Herein, a brief derivation of
is given in the case that only two detections are fused. The probabilities of
under hypotheses
and
are denoted as
and
, respectively. The false alarm probability of detector
is denoted as
, and the corresponding missed detection probability is denoted as
. In the case that only two detections are fused,
is equivalent to
, and
is equivalent to
. The derivation is provided in
Appendix A. Based on Equations (4) and (5),
of fused detections can be given as follows:
where 0.5 is the threshold of
to determine the authenticity of the signal.
is the false alarm probability of two detectors if their results are not fused together. In such a case, each false alarm would be mistaken for a spoofing attack no matter in which detector it happens. This can be explained as
Figure 3.
The shadow areas in
Figure 3a represent the region of false alarms under the hypothesis of
in the case that two detections are not fused, while in
Figure 3b, the shaded region is lessened in the case that two detectors are fused together. This is the graphical interpretation of the inequality (13). Meanwhile, the dark shaded area in
Figure 3a, denoted as
, represents the region in which false alarms happen simultaneously in both
and
. Denoting the shaded area in
Figure 3b as
,
is a subset of
, i.e.,
. Thus, there is:
The above inequality can be deduced as follows:
Based on Equations (13) and (14), the range of
can be given as:
Meanwhile,
of fused detections can be given as follows:
where
is the missed detection probability of two detectors if their results are not fused together. Each missed detection cannot be re-examined in the case that two detectors are not fused. Similar to Equation (14), there is:
Based on Equations (17) and (18), the range of
can be given as:
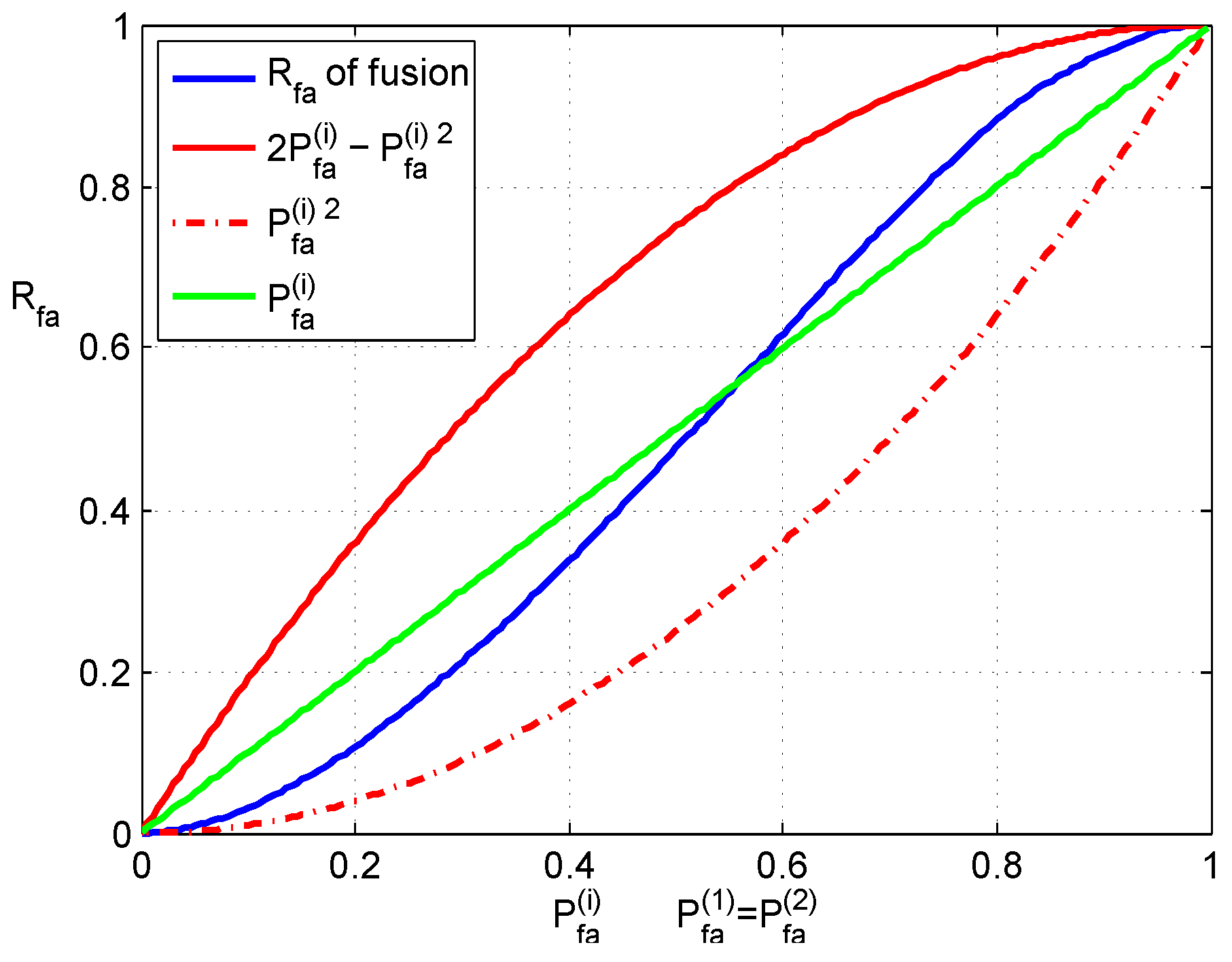
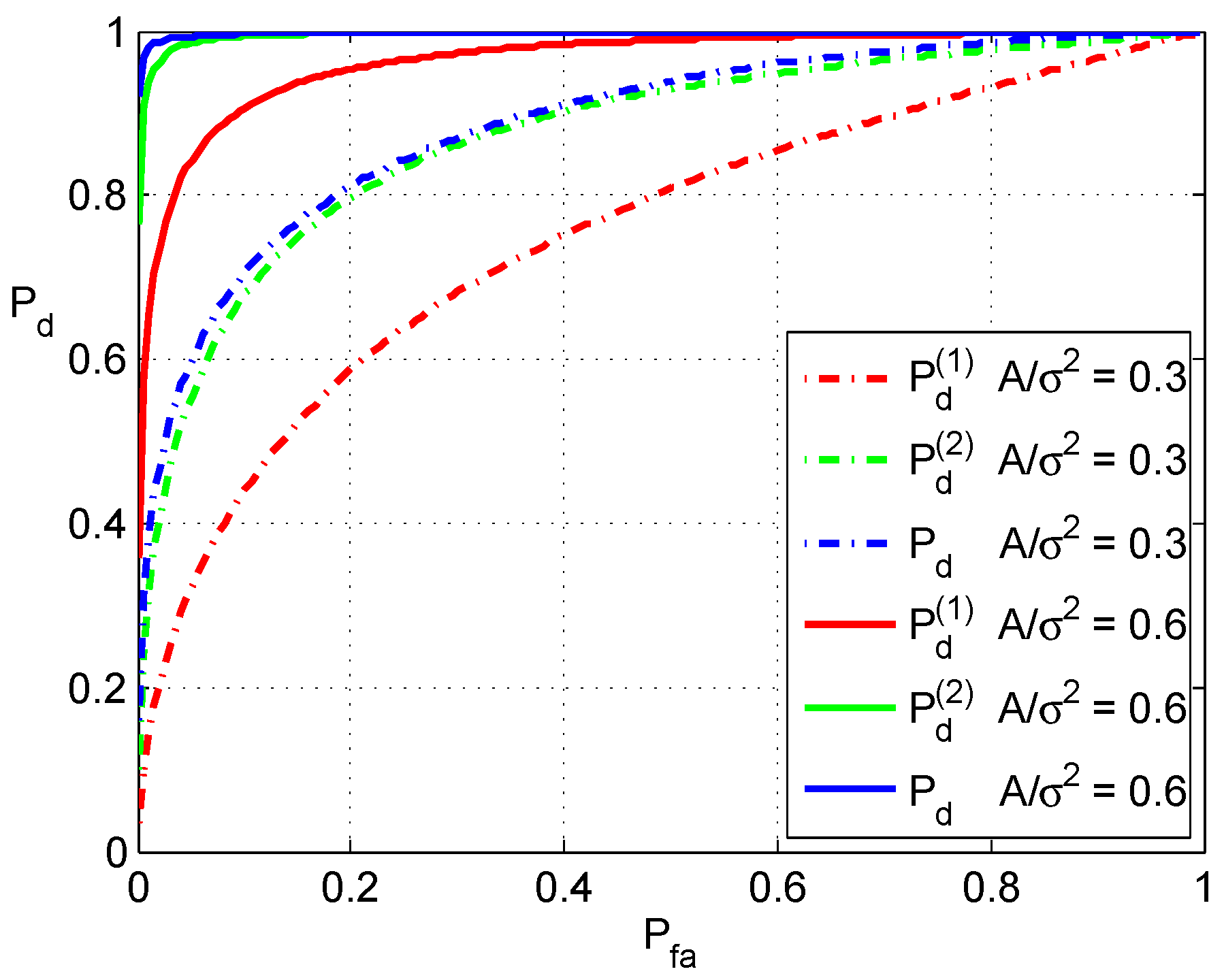
The range of and , Equations (16) and (19), just provides rough boundaries of and . They clearly show that both and in the case of fusion are less than the corresponding values in the case that detections are not fused. The actual ranges depend on the performance of the detectors, which are fused. Monte Carlo simulations based on two detectors are given in the following section to demonstrate the performance of fusion.
The above discussions are based on the fusion of two detectors. Actually, the combination rule of Equation (4) is associative, that is:
where ⊕ represents the operation of the combination and
represents the combination of
and
. The derivation of the associative law is provided in
Appendix B. Equation (20) means that the combination of multiple detections can be equivalent to the combination of two detections after some of them are fused together. Thus, discussions about two detections are sufficient to extend to the cases of multiple detections.