Secure User Pairing and Power Allocation for Downlink Non-Orthogonal Multiple Access against External Eavesdropping
Abstract
1. Introduction
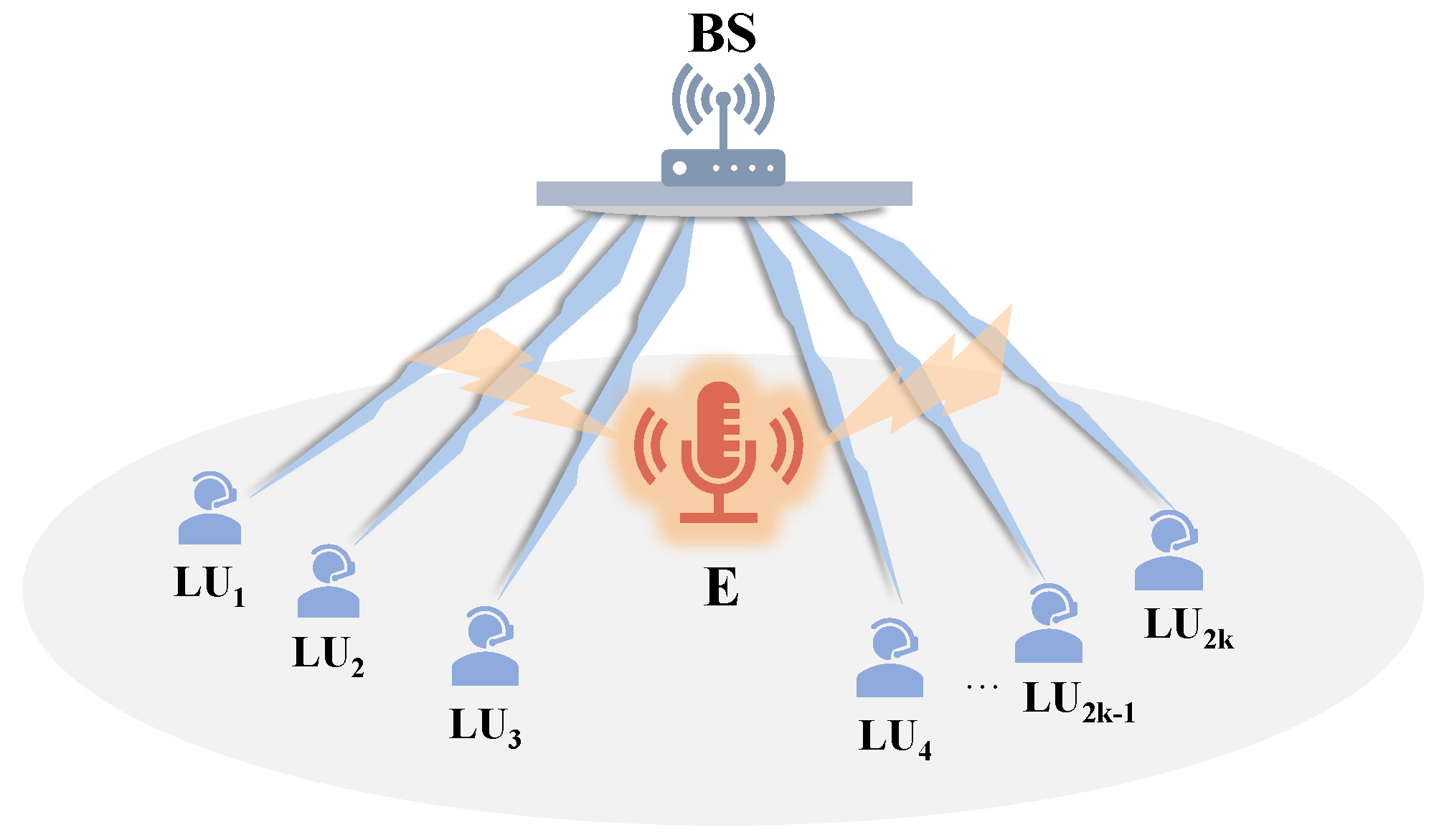
2. System Model and Problem Formulation
2.1. System Model
2.2. Problem Formulation
3. PA for NOMA Involving Two Paired Users
4. Optimal User Pairing
4.1. UP for NOMA Involving Four Users
4.1.1. Pairing Solutions
4.1.2. Optimal UP for NOMA with Four Users
4.2. UP for NOMA with Users
- (1)
- When , we need to prove , i.e., user 1 pairs with user . We prove it by contradiction. We assume user 1 is paired with user i () instead of user , and user is paired with user j (, ) instead of user 1 in the optimal user pairing solution. Following Theorem 3, we haveThat is to say, we can re-pair users 1, i, j, and to increase the ASSR, which contradicts the statement that the original pairing solution is optimal. Thus, user 1 must be paired with user to increase the ASSR, i.e., .
- (2)
- We assume holds when , i.e., .
- (3)
- According to the principle of mathematical induction, we need to prove holds when , i.e., holds, and we also prove it by contradiction. We assume that user is paired with user i () and user is paired with user j (, ). Following Theorem 3, we havewhich contradicts the assumption. Thus, user must pair with user , i.e., , to achieve a higher ASSR.
- (4)
- In conclusion, we can conclude that holds for all , and we complete the proof.
4.3. Computational Complexity
5. Simulation and Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| NOMA | Non-Orthogonal Multiple Access |
| UP | User Pairing |
| PA | Power Allocation |
| ASSR | Achievable Sum Secrecy Rate |
| MINLP | Mixed Integer Nonlinear Programming |
| SIC | Successive Interference Cancellation |
| PLS | Physical Layer Security |
| MIMO | Multiple Input–Multiple Output |
| CRN | Cognitive Radio Network |
| AN | Artificial Noise |
| SSR | Secrecy Sum Rate |
| UAV | Unmanned Aerial Vehicle |
| IRS | Intelligent Reflecting Surface |
| BS | Base Station |
| ASR | Achievable Secrecy Rate |
| CSI | Channel Side Information |
| SNR | Signal–Noise Ratio |
References
- Ding, Z.; Poor, H.V. On the Application of BAC-NOMA to 6G umMTC. IEEE Commun. Lett. 2021, 25, 2678–2682. [Google Scholar] [CrossRef]
- Vaezi, M.; Schober, R.; Ding, Z.; Poor, H.V. Non-Orthogonal Multiple Access: Common Myths and Critical Questions. IEEE Wirel. Commun. 2019, 26, 174–180. [Google Scholar] [CrossRef]
- Choi, J. Non-Orthogonal Multiple Access in Downlink Coordinated Two-Point Systems. IEEE Commun. Lett. 2014, 18, 313–316. [Google Scholar] [CrossRef]
- Ding, Z.; Yang, Z.; Fan, P.; Poor, H.V. On the Performance of Non-Orthogonal Multiple Access in 5G Systems with Randomly Deployed Users. IEEE Signal Process. Lett. 2014, 21, 1501–1505. [Google Scholar] [CrossRef]
- Wang, P.; Xiao, J.; Ping, L. Comparison of orthogonal and non-orthogonal approaches to future wireless cellular systems. IEEE Veh. Technol. Mag. 2006, 1, 4–11. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; Chih-lin, I.; Wang, Z. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Yu, Y.; Chen, H.; Li, Y.; Ding, Z.; Vucetic, B. On the Performance of Non-Orthogonal Multiple Access in Short-Packet Communications. IEEE Commun. Lett. 2018, 22, 590–593. [Google Scholar] [CrossRef]
- Liu, Y.; Zhang, S.; Mu, X.; Ding, Z.; Schober, R.; Al-Dhahir, N.; Hossain, E.; Shen, X. Evolution of NOMA Toward Next Generation Multiple Access (NGMA) for 6G. IEEE J. Sel. Areas Commun. 2022, 40, 1037–1071. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, N.; Chen, Y.; Jin, M.; Ding, Z.; Li, Y.; Yu, F.R. Secure Transmission via Beamforming Optimization for NOMA Networks. IEEE Wirel. Commun. 2020, 27, 193–199. [Google Scholar] [CrossRef]
- Poor, H.V.; Schaefer, R.F. Wireless physical layer security. Proc. Nat. Acad. Sci. USA 2017, 114, 19–26. [Google Scholar] [CrossRef]
- Nandan, N.; Majhi, S.; Wu, H.C. Secure Beamforming for MIMO-NOMA-Based Cognitive Radio Network. IEEE Commun. Lett. 2018, 22, 1708–1711. [Google Scholar] [CrossRef]
- Feng, Y.; Yan, S.; Yang, Z.; Yang, N.; Yuan, J. Beamforming Design and Power Allocation for Secure Transmission With NOMA. IEEE Trans. Wirel. Commun. 2019, 18, 2639–2651. [Google Scholar] [CrossRef]
- Li, Y.; Wang, W.; Liu, M.; Zhao, N.; Jiang, X.; Chen, Y.; Wang, X. Joint Trajectory and Power Optimization for Jamming-Aided NOMA-UAV Secure Networks. IEEE Syst. J. 2023, 17, 732–743. [Google Scholar] [CrossRef]
- Chen, Y.; Ji, X. Secure Downlink Transmission Strategies against Active Eavesdropping in NOMA Systems: A Zero-Sum Game Approach. Comput. Model. Eng. Sci. 2023, 136, 531–553. [Google Scholar] [CrossRef]
- Wang, W.; Liu, X.; Tang, J.; Zhao, N.; Chen, Y.; Ding, Z.; Wang, X. Beamforming and Jamming Optimization for IRS-Aided Secure NOMA Networks. IEEE Trans. Wirel. Commun. 2022, 21, 1557–1569. [Google Scholar] [CrossRef]
- Zhu, L.; Zhang, J.; Xiao, Z.; Cao, X.; Wu, D.O. Optimal User Pairing for Downlink Non-Orthogonal Multiple Access (NOMA). IEEE Wirel. Commun. Lett. 2019, 8, 328–331. [Google Scholar] [CrossRef]
- Wei, Z.; Ng, D.W.K.; Yuan, J.; Wang, H.M. Optimal Resource Allocation for Power-Efficient MC-NOMA With Imperfect Channel State Information. IEEE Trans. Commun. 2017, 65, 3944–3961. [Google Scholar] [CrossRef]
- Ding, Z.; Fan, P.; Poor, H.V. Impact of User Pairing on 5G Nonorthogonal Multiple-Access Downlink Transmissions. IEEE Trans. Veh. Technol. 2016, 65, 6010–6023. [Google Scholar] [CrossRef]
- Liang, W.; Ding, Z.; Li, Y.; Song, L. User Pairing for Downlink Non-Orthogonal Multiple Access Networks Using Matching Algorithm. IEEE Trans. Commun. 2017, 65, 5319–5332. [Google Scholar] [CrossRef]
- Köse, A.; Koca, M.; Anarim, E.; Médard, M.; Gökcesu, H. Graph-Theoretical Dynamic User Pairing for Downlink NOMA Systems. IEEE Commun. Lett. 2021, 25, 3234–3238. [Google Scholar] [CrossRef]
- Liu, Z.; Liang, C.; Yuan, Y.; Chan, K.Y.; Guan, X. Resource Allocation Based on User Pairing and Subcarrier Matching for Downlink Non-Orthogonal Multiple Access Networks. IEEE/CAA J. Autom. Sin. 2021, 8, 679–689. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, H.M.; Yang, Q.; Ding, Z. Secrecy Sum Rate Maximization in Non-orthogonal Multiple Access. IEEE Commun. Lett. 2016, 20, 930–933. [Google Scholar] [CrossRef]
- Tao, L.; Yang, W.; Yan, S.; Wu, D.; Guan, X.; Chen, D. Covert Communication in Downlink NOMA Systems With Random Transmit Power. IEEE Wirel. Commun. Lett. 2020, 9, 2000–2004. [Google Scholar] [CrossRef]
- Cormen, T.H.; Leiserson, C.E.; Rivest, R.L.; Stein, C. Introduction to Algorithms, 4th ed.; The MIT Press: Cambridge, MA, USA, 2022; p. 1312. [Google Scholar]



Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Y.; Chen, Y.; Ji, X. Secure User Pairing and Power Allocation for Downlink Non-Orthogonal Multiple Access against External Eavesdropping. Entropy 2024, 26, 64. https://doi.org/10.3390/e26010064
Li Y, Chen Y, Ji X. Secure User Pairing and Power Allocation for Downlink Non-Orthogonal Multiple Access against External Eavesdropping. Entropy. 2024; 26(1):64. https://doi.org/10.3390/e26010064
Chicago/Turabian StyleLi, Yuxuan, Yanqiu Chen, and Xiaopeng Ji. 2024. "Secure User Pairing and Power Allocation for Downlink Non-Orthogonal Multiple Access against External Eavesdropping" Entropy 26, no. 1: 64. https://doi.org/10.3390/e26010064
APA StyleLi, Y., Chen, Y., & Ji, X. (2024). Secure User Pairing and Power Allocation for Downlink Non-Orthogonal Multiple Access against External Eavesdropping. Entropy, 26(1), 64. https://doi.org/10.3390/e26010064




