A Modified FlowDroid Based on Chi-Square Test of Permissions
Abstract
1. Introduction
- (1)
- We propose a permission clustering method based on the use of permissions by malware. Compared with all the permissions of the Android system, the proposed permission cluster contains only a few permissions. By monitoring these permissions and the related call paths in FlowDroid, the analysis can be greatly simplified.
- (2)
- We propose a lightweight malicious application detection method based on the permission clusters and FlowDroid in this article. This method is suitable for pre-installed software and user-installed software. We improved FlowDroid so that it can only monitor the call paths that are related to the permissions in the permission cluster and meet certain risk conditions. This greatly reduces the detection time and memory usage.
2. Related Work
3. Preliminaries
3.1. Android Permission
3.2. FlowDroid
- (1)
- There is no further analysis of taint paths, and the large number of false positive paths results in low accuracy.
- (2)
- There is no clear analysis content and there are no taint path identification criteria. This leads to a large number of irrelevant detection paths, resulting in excessive memory and time consumption.
3.3. Mathematical Background
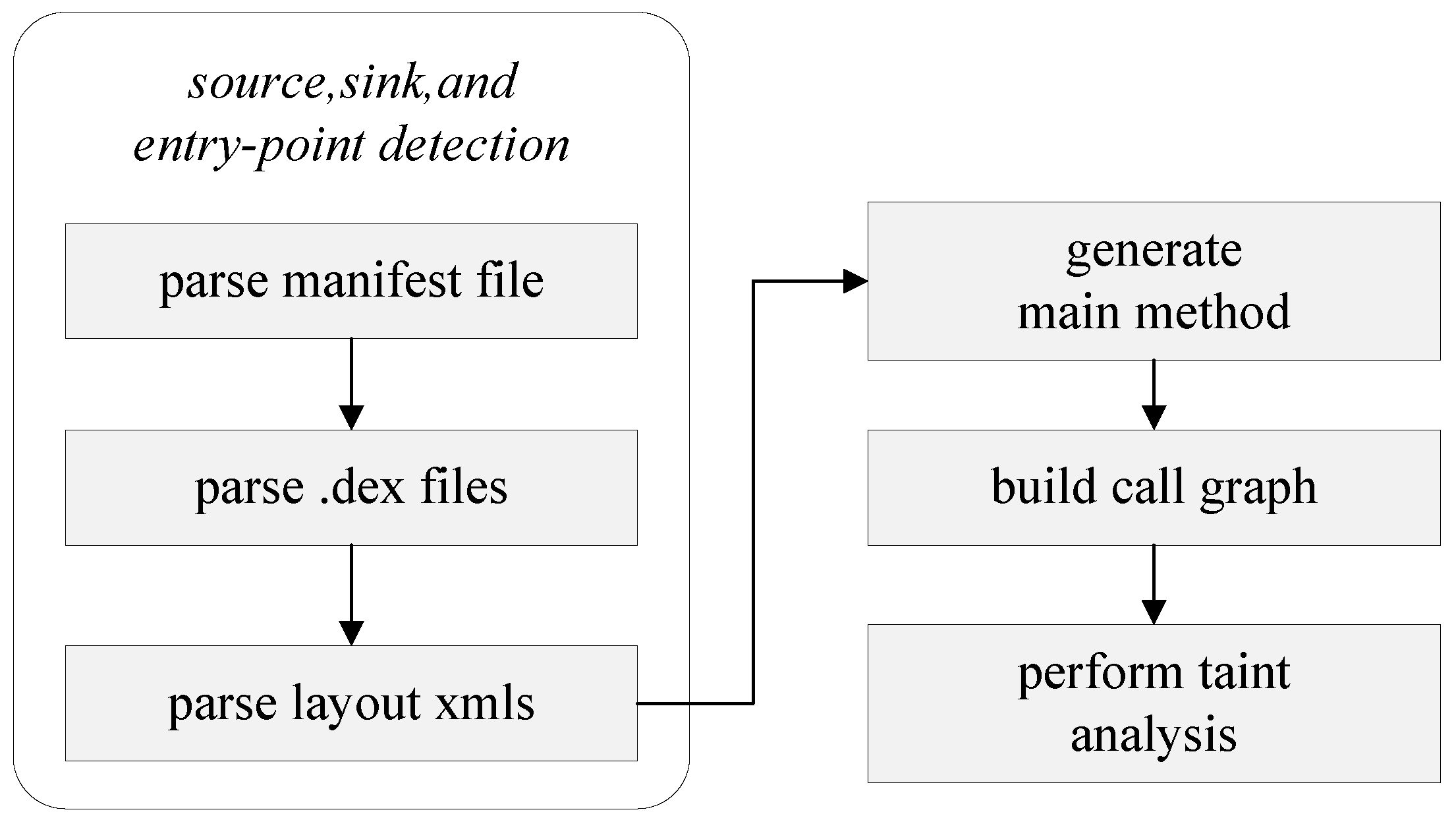
4. The Improved Detection Method
4.1. Permission Cluster Extraction
| Clustering Algorithm Based on Mutual Information: Input: Permissions set Obtained by Chi-Square Test: Output: Cluster Sets: |
|
4.2. Risk Calculation
- (1)
- The risk value decreases as of permission cluster decreases;
- (2)
- The risk values of to are greater than 1;
- (3)
- The risk values of to are greater than 0;
4.3. Filtration of Taint Data Flow
- (1)
- Route: the taint transmission path set. The element is a pair—<source, sink>—and it indicates that there is a taint transmission path from source to sink, where .
- (2)
- LeakRoute: the privacy leak path set. The element is a triple—<source, sink, risk>—and it indicates that there is a leak path from source to sink with a risk value of risk. The filtering method is shown in Figure 4.
5. Experiments
5.1. Accuracy Experiments
5.2. Efficiency Experiments
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Kumar, P.; Naik, K.K. Android based Wireless Sensor Network application for airborne platforms (AWAAPS). In Proceedings of the 2016 IEEE International Conference on Engineering and Technology (ICETECH), Coimbatore, India, 17–18 March 2016; pp. 776–782. [Google Scholar] [CrossRef]
- Serfass, D.; Yoshigoe, K. Wireless Sensor Networks using android virtual devices and Near Field Communication peer-to-peer emulation. In Proceedings of the 2012 Proceedings of IEEE Southeastcon, Orlando, FL, USA, 15–18 March 2012; pp. 1–6. [Google Scholar] [CrossRef]
- Grano, G.; Di Sorbo, A.; Mercaldo, F.; Visaggio, C.A.; Canfora, G.; Panichella, S. Android apps and user feedback: A dataset for software evolution and quality improvement. In Proceedings of the ACM Sigsoft International Workshop on App Market Analytics; ACM: Chicago, IL, USA, 2017. [Google Scholar]
- McAfee Labs Threats Report|McAfee Labs. August 2019. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterly-threats-aug-2019.pdf (accessed on 20 January 2021).
- Alzaylaee, M.K.; Yerima, S.Y.; Sezer, S. DL-Droid: Deep learning based android malware detection using real devices. Comput. Secur. 2020, 89, 101663. [Google Scholar] [CrossRef]
- Enck, W.; Gilbert, P.; Han, S.; Tendulkar, V.; Chun, B.-G.; Cox, L.P.; Jung, J.; McDaniel, P.; Sheth, A.N. TaintDroid: An information flow tracking system for real-time privacy monitoring on smartphones. ACM Trans. Comput. Syst. 2010, 32, 1–29. [Google Scholar] [CrossRef]
- Bugiel, S.; Davi, L.; Dmitrienko, A.; Fischer, T.; Sadeghi, A.-R. Xmandroid: A New Android Evolution to Mitigate Privilege Escalation Attacks; Technical Report TR-2011-04; Technische Universität Darmstadt: Darmstadt, Germany, 2011. [Google Scholar]
- Arzt, S.; Rasthofer, S.; Fritz, C.; Bodden, E.; Bartel, A.; Klein, J.; Traon, Y.L.; Octeau, D.; McDaniel, P. FlowDroid: Precise Context, Flow, Field, Object-Sensitive and Life Cycle-Aware Taint Analysis for Android Apps; ACM: Edinburgh, UK, 2014. [Google Scholar]
- Han, K.S.; Lee, Y.; Jiang, B.; Im, E.G. How to Violate Android’s Permission System without Violating It. In Proceedings of the Third International Conference on Digital Information Processing and Communications (ICDIPC2013), the Society of Digital Information Wireless Communication, Dubai, UAE, 30 January–1 February 2013; pp. 18–25. [Google Scholar]
- Enck, W.; Ongtang, M.; Mcdaniel, P. On lightweight mobile phone application certification. In Proceedings of the ACM Conference on Computer and Communications Security; ACM: Chicago, IL, USA, 2009. [Google Scholar]
- Zhao, Z.; Osono, F.C.C. “TrustDroid™”: Preventing the use of SmartPhones for information leaking in corporate networks through the used of static analysis taint tracking. In Proceedings of the International Conference on Malicious and Unwanted Software, Fajardo, PR, USA, 16–18 October 2012; IEEE Computer Society: Piscataway, NJ, USA, 2012. [Google Scholar]
- Yang, Z.; Yang, M. LeakMiner: Detect Information Leakage on Android with Static Taint Analysis. In Proceedings of the Software Engineering, Wuhan, China, 6–8 November 2012; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar]
- Cen, L.; Gates, C.S.; Si, L.; Li, N. A probabilistic discriminative model for android malware detection with decompiled source code. IEEE Trans. Dependable Secur. Comput. 2014, 12, 400–412. [Google Scholar] [CrossRef]
- Kang, H.; Jang, J.W.; Mohaisen, A.; Kim, H.K. Detecting and classifying android malware using static analysis along with creator information. Int. J. Distrib. Sens. Netw. 2015, 11, 479174. [Google Scholar] [CrossRef]
- Song, J.; Han, C.; Wang, K.; Zhao, J.; Ranjan, R.; Wang, L. An integrated static detection and analysis framework for Android. Pervasive Mob. Comput. 2016, 32, 15–25. [Google Scholar] [CrossRef]
- Sun, M.; Li, X.; Lui, J.C.; Ma, R.T.; Liang, Z. Monet: A user-oriented behavior-based malware variants detection system for Android. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1103–1112. [Google Scholar] [CrossRef]
- Rovelli, P.; Vigfússon, Ý. PMDS: Permission-based malware detection system. In ICISS 2014; LNCS; Prakash, A., Shyamasundar, R., Eds.; Springer: Cham, Germany, 2014; Volume 8880, pp. 338–357. [Google Scholar] [CrossRef]
- Fan, M.; Liu, J.; Wang, W.; Li, H.; Tian, Z.; Liu, T. DAPASA: Detecting Android Piggybacked Apps Through Sensitive Subgraph Analysis. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1772–1785. [Google Scholar] [CrossRef]
- Talha, K.A.; Alper, D.I.; Aydin, C. APK Auditor: Permission-based Android malware detection system. Digit. Investig. 2015, 13, 1–14. [Google Scholar] [CrossRef]
- Li, C.; Mills, K.; Niu, D.; Zhu, R.; Zhang, H.; Kinawi, H. Android malware detection based on factorization machine. IEEE Access 2019, 7, 184008–184019. [Google Scholar] [CrossRef]
- Reshetova, E.; Bonazzi, F.; Asokan, N. SELint: An SEAndroid Policy Analysis Tool. In Proceedings of the 3rd International Conference on Information Systems Security and Privacy, Porto, Portugal, 19–21 February 2017. [Google Scholar]
- Vallee-Rai, R.; Gagnon, E.; Hendren, L.; Lam, P.; Pominville, P.; Sundaresan, V. Optimizing Java Bytecode Using the Soot Framework: Is It Feasible? In Proceedings of the International Conference on Compiler Construction, Berlin, Germany, 25 March–2 April 2000; Springer: Berlin/Heidelberg, Germany, 2000. [Google Scholar]
- Reps, T.; Horwitz, S.; Sagiv, M. Precise inter procedural dataflow analysis via graph reachability. In Proceedings of the ACM Sigplan-sigact Symposium on Principles of Programming Languages; ACM: Chicago, IL, USA, 1995. [Google Scholar]
- Sagiv, M.; Reps, T.; Horwitz, S. Precise Inter procedural Dataflow Analysis with Applications to Constant Propagation. Theor. Comput. Sci. 1996, 167, 131–170. [Google Scholar] [CrossRef]
- Bodden, E. Inter-procedural data-flow analysis with ifds/ide and soot. In Proceedings of the ACM SIGPLAN International Workshop on State of the Art in Java Program analysis, SOAP ’12, Beijing, China, 14 June 2012; pp. 3–8. [Google Scholar]
- Allen, F.E. Control flow analysis. ACM Sigplan Not. 1970, 5, 1–19. [Google Scholar] [CrossRef]
- NIST/SEMATECH e-Handbook of Statistical Methods. 2020. Available online: http://www.itl.nist.gov/div898/handbook/ (accessed on 20 January 2021).
- Sarma, B.P.; Li, N.; Gates, C.; Gates, C.; Potharaju, R.; Nita-Rotaru, C.; Molloy, I. Android Permissions: A Perspective Combining Risks and Benefits. In Proceedings of the ACM Symposium on Access Control Models and Technologies, Barcelona, Spain, 16–18 June 2012; pp. 13–22. [Google Scholar]
- Faruki, P.; Bharmal, A.; Laxmi, V.; Ganmoor, V.; Gaur, M.S.; Conti, M.; Rajarajan, M. Android Security: A Survey of Issues, Malware Penetration, and Defenses. IEEE Commun. Surv. Tutor. 2015, 17, 998–1022. [Google Scholar] [CrossRef]
- Alpaydin, E. Introduction to Machine Learning; MIT Press: Cambridge, MA, USA, 2020. [Google Scholar]
- Sanz, B.; Santos, I.; Laorden, C.; Ugarte-Pedrero, X.; Bringas, P.G.; Álvarez, G. PUMA: Permission Usage to Detect Malware in Android. In International Joint Conference CISIS’12-ICEUTE’12-SOCO’12 Special Sessions; Advances in Intelligent Systems and Computing, LNCS; Springer: Berlin/Heidelberg, Germany, 2013; Volume 189. [Google Scholar]
- Jiang, X.; Mao, B.; Guan, J.; Huang, X. Android Malware Detection Using Fine-Grained Features. Sci. Program. 2020, 2020, 1–13. [Google Scholar] [CrossRef]


| Number of Malicious Apps (X) | Number of Normal Apps (Y) | |
|---|---|---|
| Apps with permission p | ||
| Apps without permission p |
| Permission Clusters | Permissions | Risk Value | |
|---|---|---|---|
| INTERNET ACCESS_NETWORK_STATE CHANGE_WIFI_STATE | 7.693 6.622 6.178 | 7 | |
| CALL_PHONE READ_CONTACT READ_PHONE_STATE | 6.334 4.236 3.855 | 6 | |
| WRITE_EXTERNAL_STORAGE GET_ACCOUNT WRITE_SETTING | 6.012 3.821 2.706 | 5 | |
| SEND_SMS RECIEVE_SMS WRITE_SMS | 5.844 4.689 4.023 | 4 | |
| ACCESS_COARSE_LOCATION ACCESS_FINE_LOCATION | 5.672 2.755 | 3 | |
| RECIEVE_BOOT_COMPLETED INSTALL_PACKAGE WAKE_LOCK | 5.522 3.237 2.468 | 2 | |
| DEVICE_POWER CAMERA FLASHLIGHT | 1.355 1.224 0.698 | 1 |
| Disassembled Successful | |||
|---|---|---|---|
| 500 normal apps | 413 | 81 | 332 |
| 50 malicious apps | 35 | 27 | 8 |
| Type | Number | Result | |||
|---|---|---|---|---|---|
| App Name | M | Taint Paths | R | ||
| News | 8 | Toutiao | 28 | 53 | 0.091 |
| Funinput.Digit | 29 | 43 | 0.089 | ||
| Sina news | 36 | 36 | 0.071 | ||
| Social media | 8 | Zhihu | 29 | 42 | 0.083 |
| BaiduTieba | 26 | 61 | 0.099 | ||
| 27 | 48 | 0.096 | |||
| Services | 7 | Dianping | 27 | 49 | 0.097 |
| FangTianxia | 18 | 38 | 0.134 | ||
| Ganji | 24 | 43 | 0.103 | ||
| Tools | 8 | TencentMobileManager | 41 | 103 | 0.064 |
| SougouTypewriting | 24 | 49 | 0.104 | ||
| UC Browser | 38 | 58 | 0.068 | ||
| Entertainment | 6 | MeituXiuXiu | 26 | 47 | 0.098 |
| Iqiyi | 28 | 54 | 0.092 | ||
| MeiPai | 20 | 38 | 0.121 | ||
| Others | 45 | ||||
| Malicious applications | 35 | com.estrongs.android.pop. apk | 7 | 20 | 0.311 |
| com.evernote. skitch.apk | 18 | 42 | 0.133 | ||
| com.gau.go.launcherex.apk | 9 | 28 | 0.250 | ||
| com.opera.browser.apk | 16 | 46 | 0.153 | ||
| com.outfit7.talkinggina.apk | 19 | 51 | 0.134 | ||
| Name | Size | Runtime | Memory Consumption | |||
|---|---|---|---|---|---|---|
| FlowDroid | PBFlowDroid | FlowDroid | PBFlowDroid | |||
| 1 | InsecureBank.apk | 58.5 KB | 29.33 s | 14.24 s | 82.73 MB | 52.26 MB |
| 2 | outfit7.talkinggina.apk | 109 KB | 41.1 s | 19.58 s | 241.55 MB | 130.45 MB |
| 3 | com.evernote.skitch.apk | 139 KB | 51.76 s | 18.21 s | 272.56 MB | 133.66 MB |
| 4 | BadNews.apk | 1.37 MB | 73.19 s | 29.01 s | 349.33 MB | 166.14 MB |
| 5 | FakeCallandMessage | 3.39 MB | 82.01 s | 41.73 s | 428.16 MB | 212.36 MB |
| 6 | BaiduNews | 23.66 MB | Time Out | 48.86 s | OOM | 325.88 MB |
| 7 | SougouTypewriting | 33.96 MB | Time Out | 101.14 s | OOM | 344.16 MB |
| 8 | YoudaoNote | 63.23 MB | Time Out | 215.84 s | OOM | 683.25 MB |
| Algorithm | Configuration | Accuracy |
|---|---|---|
| NaiveBayes | None | 67.64% |
| IBK 10 | K = 10 | 78.94% |
| RandomForest | I = 10 | 85.82% |
| FlowDroid | None | 76.9% |
| PBFlowDroid | None | 77.2% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, H.; Liu, G.; Wu, Z.; Tian, Y.; Zhang, L. A Modified FlowDroid Based on Chi-Square Test of Permissions. Entropy 2021, 23, 174. https://doi.org/10.3390/e23020174
Kang H, Liu G, Wu Z, Tian Y, Zhang L. A Modified FlowDroid Based on Chi-Square Test of Permissions. Entropy. 2021; 23(2):174. https://doi.org/10.3390/e23020174
Chicago/Turabian StyleKang, Hongzhaoning, Gang Liu, Zhengping Wu, Yumin Tian, and Lizhi Zhang. 2021. "A Modified FlowDroid Based on Chi-Square Test of Permissions" Entropy 23, no. 2: 174. https://doi.org/10.3390/e23020174
APA StyleKang, H., Liu, G., Wu, Z., Tian, Y., & Zhang, L. (2021). A Modified FlowDroid Based on Chi-Square Test of Permissions. Entropy, 23(2), 174. https://doi.org/10.3390/e23020174







