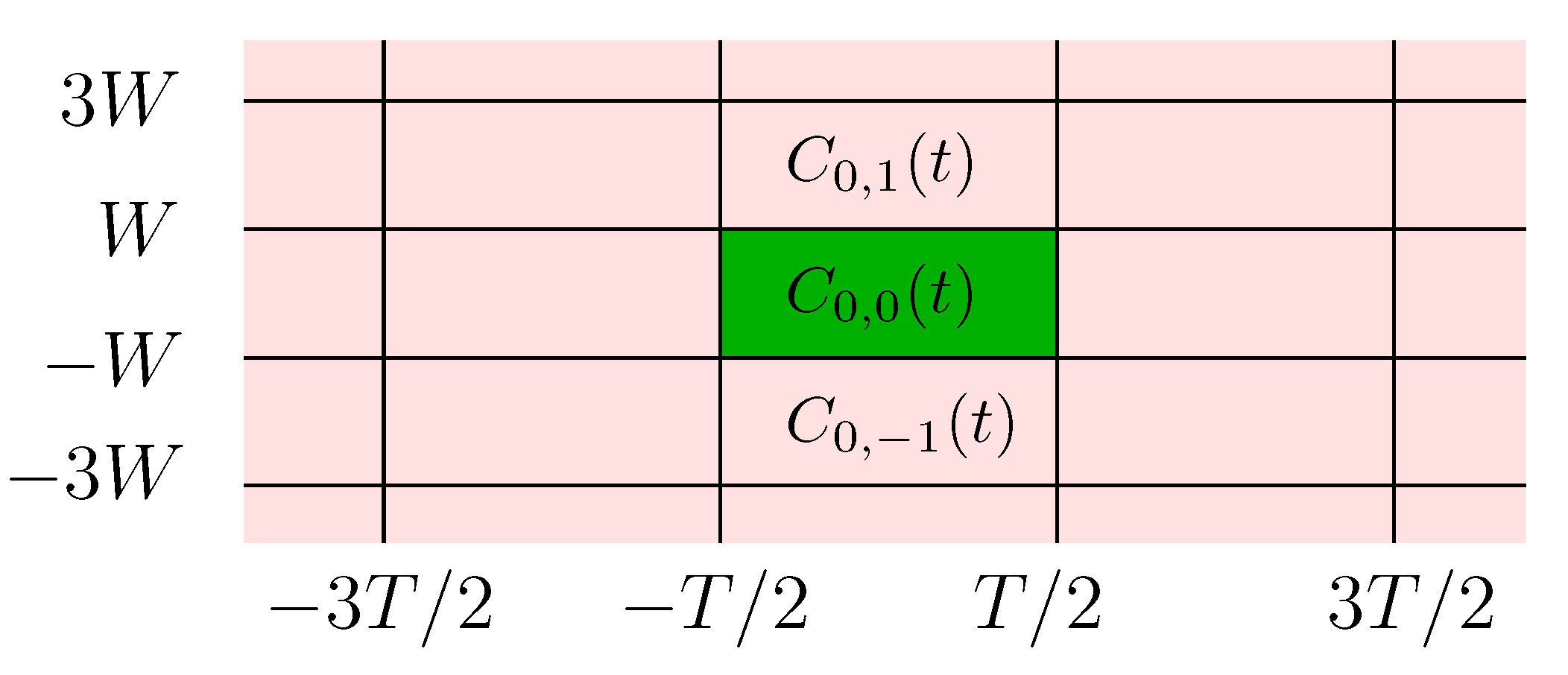1. Introduction
Wireless communication technologies that use radio waves impose tight requirements on the used spectrum as adjacent radio bands may be used by other users or technologies. A specific transmit spectral mask is usually required, a mask that allows the communication system to transmit data within a specific radio band while guaranteeing an acceptable level of interference on the other users or technologies. It is therefore reasonable to consider that in a wireless communication system the transmitter confines its transmitted data within its radio band, and the receiver looks for the transmitted data in this band. The allocated band, the corresponding channel statistics and the available transmit power determine the maximal reliable possible data rate. In his pioneering work, Shannon [
1] derived the capacity of band-limited real additive white Gaussian noise (AWGN) channels, which for the complex channel is
where
W is the bandwidth of the baseband channel,
P is the average transmit power and
is the spectrum of the additive circularly symmetric complex white Gaussian noise. Shannon derived first the channel capacity for the discrete time channel as the block length of the codewords grows towards infinity. He then used the sampling theorem which provides a one-to-one relation between the continuous time and discrete time signals: For
W-Hz band-limited signals when sampled at a rate of
samples per second, the operation is invertible and information lossless making use of the “sinc” function defined in this manuscript as
While the derived results are mathematically rigorous, some of the made assumptions do not hold in practical settings.
First: the conversion from discrete time to continuous time and vice versa is not practical since the “sinc” function needs an infinite time support. Moreover, the use of any band-limited function with non-zero finite energy is not possible in practice. In the literature, Wyner [
2,
3] and Gallager [
4] tackled this issue and considered the use of
T-seconds time-limited codewords. However, they derived asymptotic results as
and reached the same formula (
1) derived by Shannon.
In [
2], Wyner considered four different physical models and derived the asymptotic channel capacity for each model. Wyner stated that the first two models suffer from some physical difficulties; the assumed noise in the first model results in an infinite noise power at the receiver, and the use of strictly band-limited signals in the second model is not practical and may produce interference between consecutive codewords. On the other hand, he proved that using a noise model with finite power results in infinite capacity. Wyner made some assumptions to avoid these issues in [
3] and in the third and fourth models in [
2]. He derived the channel capacity of the different models by relating the continuous time to discrete time models as Shannon did in [
1], but by using the prolate spheroidal wave functions (PSWFs) and their property that as
, the first
PSWFs form asymptotically a complete orthonormal (CON) set for the time-limited and approximately band-limited signals.
Gallager [
4] Section 8.5 considered transmitting time-limited signals over an additive real Gaussian noise channel with impulse response
. He used an arbitrary power spectral density (PSD) for the noise
and arbitrary filter
. As
, he derived the channel capacity to be
where
is the Fourier transform of the filter
and
is the transmit spectrum at frequency
f subject to
In [
4] Section 8.3 he considered the special case where
is the ideal low pass filter and the noise is white and found the capacity to be the same as the one derived by Shannon, while avoiding the issues of infinite noise power and infinite capacity. In that special case (where
is the ideal low pass filter) the transformation between continuous time and discrete time was also done through the use of the PSWFs [
4] Sections 8.4 and 8.5. Finally, Gallager provided an intuitive argument regarding inter-codeword interference [
4] Section 8.5; one can introduce a large guard time, say
for some
. Asymptotically, inter-codeword interference is avoided without affecting the data rates since
as
.
A related question is that of determining the degrees of freedom when using
T-seconds time-limited codewords over a
W-Hz band-limited channel. The space of finite-energy functions that are band-limited and time-limited contains only the zero function. It is nevertheless commonly accepted in the literature that the dimension of the W-T space is approximately
. This argument is supported by results in [
5,
6,
7,
8,
9] that were also derived in the asymptotic regime as
, something that we intend to relax hereafter.
Recently, in [
10,
11], we studied the use of
T-seconds time-limited pulses over
W-Hz real band-limited Gaussian channels, and derived the channel capacity by allowing the time duration of the codewords to grow towards infinity. In [
10], we considered a pulse amplitude modulation (PAM) system and we studied optimal signaling; we showed that one can approach Shannon’s capacity by signaling at faster than the Nyquist rate. In [
11], we considered a combined PAM-orthogonal multi-pulse modulation scheme (PAM-OMM) and derived the achievable rates and evaluated them numerically. We showed that these rates can be made arbitrarily close to the Shannon’s capacity by using a finite number of parallel filters. We also established that there are
degrees of freedom when using such system.
Second: the second questionable assumption in practical settings is the use of infinite block-length codewords which is not feasible. In [
12], Polyanskiy derived an approximation for the maximal data rates when given a target probability of error in the finite block-length regime, where only discrete time channels are considered.
In this work, we consider transmitting continuous time and finite duration codewords over a band-limited Gaussian channel. We use the ideal low pass filter as a model for the channel to force the transmitter to confine its transmitted information and energy in the allocated band and also model good receiver designs: Given any practical low pass filter, one can implement a sharper low pass filter that is closer to the ideal one. In such a model, there are no issues when it comes to infinite noise power and/or infinite capacity, however inter-codeword interference is inevitable.
Our main goal is to investigate the degrees of freedom and the achievable pairs of data rates and probability of error. We use a similar approach to [
2,
3,
4] (using the PSWFs) to transform the problem from continuous time to discrete time and vice versa, and then we apply the adapted results by Polyanskiy for parallel discrete time AWGN channels.
Recently, in [
13], we investigated the ‘dual’ problem where we derived an upper bound and a lower bound on the rates of source coding a
T-seconds finite duration piece from a
W-Hz band-limited real white Gaussian process.
The paper is organized as follows: in
Section 2, we provide a brief overview of the PSWFs, some relevant properties in addition to some numerical computations. In
Section 3, we present our system model and formulate the problem. We derive upper and lower bounds for the data rates and the corresponding degrees of freedom in
Section 4. In
Section 5, we present the results of our numerical computations. In
Section 6, we present some possible enhancements on the bounds, and we summarize the results and conclude in
Section 7.
2. Preliminaries: The Prolate Spheroidal Wave Functions
In [
14], Slepian and Pollak showed that the PSWFs possess properties that make them useful in the Fourier analysis of band-limited functions and time-limited functions. For any
, they defined the PSWFs as an infinitely countable set of real functions
, normalized solutions of the integral equation where for every
,
The PSWFs form a CON set for band-limited functions [
14] with
where
is the Kronecker delta. Additionally, these functions are orthogonal over the time window
T:
where
are the eigenvalues that are all in the range
and decreasing in
l [
14]. The eigenvalue
may be hence viewed as the energy concentration of
in the time interval
and
has the highest energy concentration. Additionally, the PSWFs are real continuous functions that are even when
l is even and odd when
l is odd.
In his book [
4] Section 8.4, Gallager proved that the PSWFs are the desirable functions when sending time-limited signals over a band-limited channel. He made use of one important property of the PSWFs, namely the Fourier transform
of the PSWF
is a scaled version of a time-limited PSWF:
where
.
In this paper we define
as index for the PSWFs, which is different from the one used by Slepian and Pollak. More specifically
here is the same as
in [
14]. We also denote here by “
” the
T-seconds time-limited version of a PSWF. More specifically,
and since
is its energy, the normalized time-limited PSWF is
. We denote by
the Fourier transform of
which is equal to
Based on (
2)–(
4), when
is passed through an ideal low pass filter with transfer function
, the output is
:
We have used a debugged version of the software package by Adelman et al. [
15] to compute the eigenvalues of the PSWFs. While it is known [
4] Section 8.4 that for any
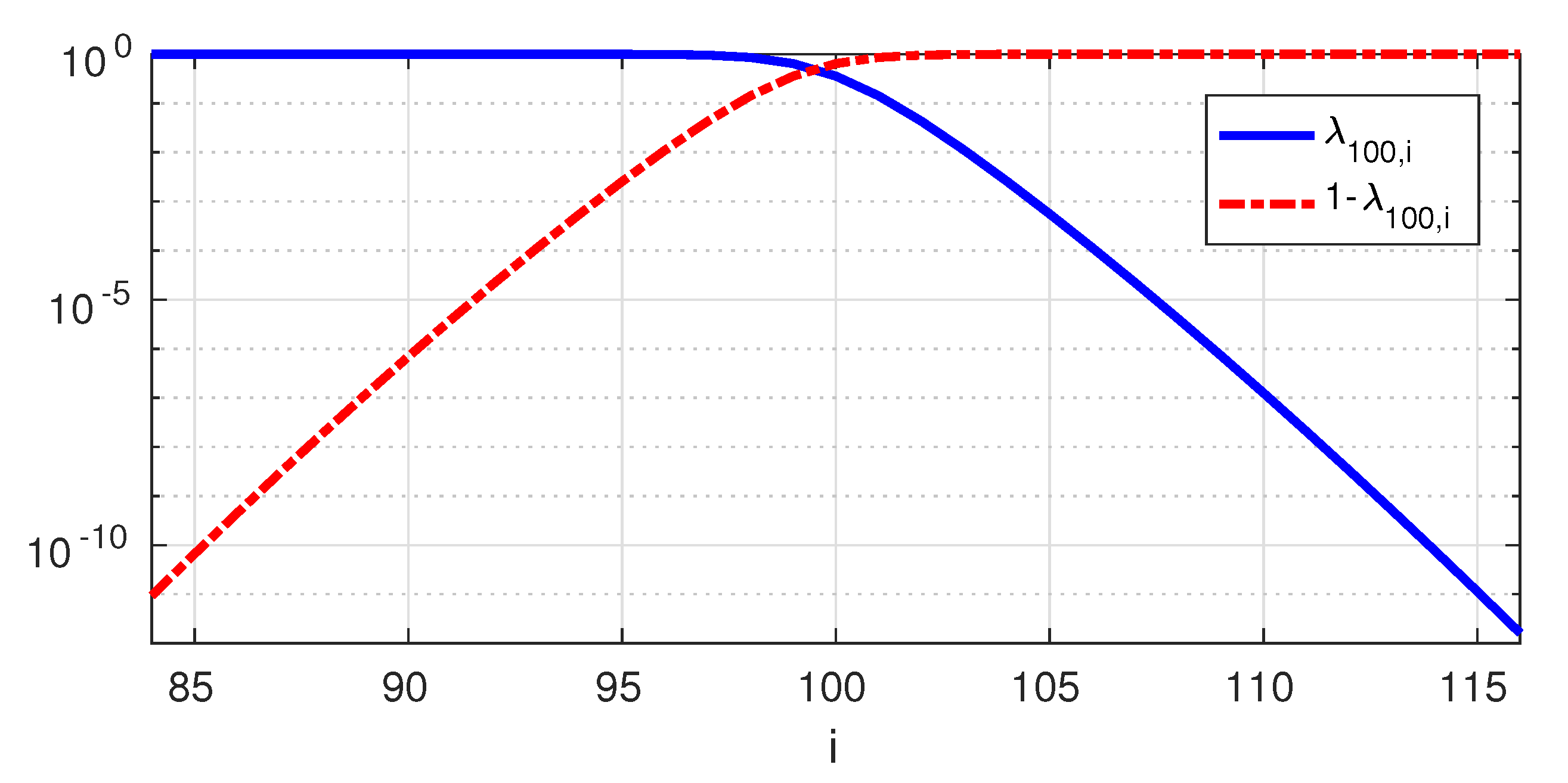
Figure 1 shows the eigenvalues
of the PSWFs for
and
. Note that
This transition region between the “extreme” eigenvalues (very close to 1 or 0) is known to have a length proportional to the logarithm of
c [
4] Section 8.4. For example, for
,
is between
and
only in the range
.
In this manuscript, shifted (in time and frequency) PSWFs will come in handy. Denote by
the inner product between the
normalized time-limited PSWF already shifted in time and frequency by
-seconds and
-Hz, respectively, and the band-limited version of the
normalized time-limited PSWF. By Equation (
5) and using Parseval,
which can be interpreted as the inner product between the bandlimited shifted normalized
PSWF and the
normalized time-limited PSWF. In
Appendix A, we study the magnitude of
and derive various bounds that are used throughout this document.
3. System Model and Problem Formulation
We consider a system model where a
T-seconds time-limited codeword is transmitted over a linear Gaussian channel with transfer function
—assumed to be an ideal
W-Hz low-pass filter, and an additive complex Gaussian noise
, assumed to be a stationary
W-Hz band-limited “white” process with mean zero and PSD
for
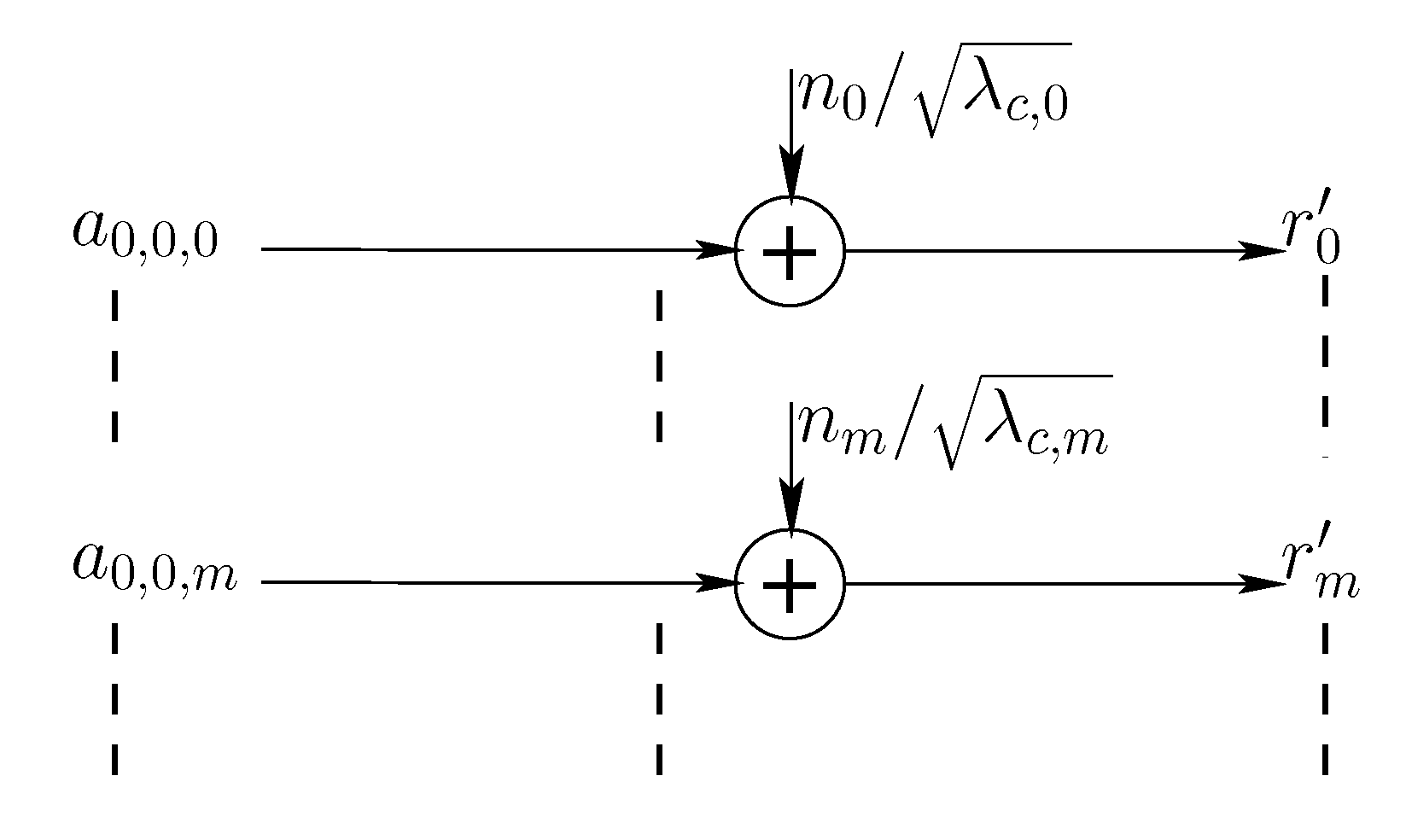
. With a system in mind whereby other codewords may be transmitted—possibly by other users—consecutively and/or in neighboring bands, we denote by
the codeword carrying the data packet of interest, and by
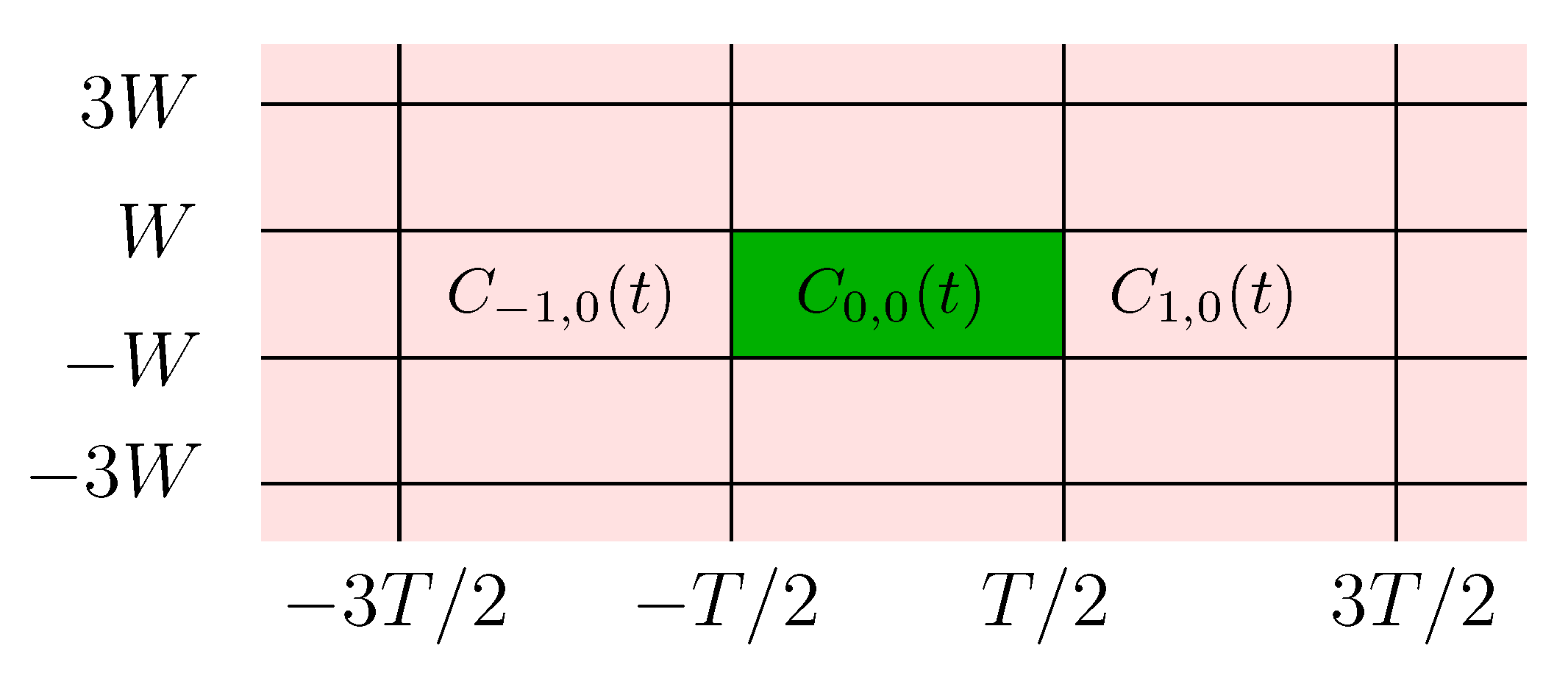
those carrying other data packets, possibly transmitted by other devices and interfering with the message of interest as illustrated in
Figure 2. Our model is based on the reasonable assumption that all codewords follow the same modulation techniques, since every frequency band is usually allocated to a unique technology which abides by specific standards, and the neighboring bands are more likely to be used by the same technology.
In what follows, we consider various scenarios where some or all of those interfering codewords are present and we denote by
the set of other present codewords. The overall signal going through the channel can hence be written as the sum of the codeword of interest and the other interfering codewords:
where
is non-zero only over
. On the receiver side, the data packet of interest is to be recovered from
, a
T-seconds time-limited version of the output of the channel
.
We assume that, whenever present, a transmitted codeword satisfies the power constraint,
As Gallager proved that the PSWFs are the desirable CON set when sending a time-limited codeword over a band-limited channel [
4] Section 8.4, we use the normalized time-limited PSWF as orthogonal pulses to send the data symbols. Hence the codewords can be written as
where
. Representing the continuous time signal
by the symbols
is known as “signal space representation” in the context of digital communications. The
’s are chosen from a given complex signal constellation and by Plancherel and (
7) they satisfy
When it comes to the noise,
is band-limited and can be hence decomposed as
where
are independent zero-mean complex circular Gaussian random variables with variance
.
At the receiver, sufficient statistics are clearly obtained by projecting on the set of normalized time-limited PSWF to extract the data symbols. It is worth noting that since is band-limited and has finite energy, it is necessarily analytic and it is therefore sufficient to know over any open interval to determine it fully. As a consequence, from an information-theoretic perspective, whether as whole is available or only , the information rates are identical.
The problem at hand is to maximize the information rates given a maximal probability of error. This is naturally related to the available degrees of freedom when sending time-limited codewords over a band-limited channel, which is the maximal number of independent data symbols that can be transmitted to the receiver.
In the following section, we consider various scenarios and derive upper and lower bounds for the data rates and the degrees of freedom.
5. Numerical Results
In what follows, we use KHz and in our computations. Since we consider the complex base-band channel, an equivalent real pass-band channel will have -Hz bandwidth (i.e., 2 KHz in our case), and L complex degrees of freedom in base-band is equivalent to real degrees of freedom in passband.
In the following we evaluate the degrees of freedom and the data rates for different 𝖲𝖭𝖱 levels (in dB) as
L depends on the 𝖲𝖭𝖱; for example, since the water-filling algorithm is used for Equation (
10),
L can be increased by increasing the “water level” in the water-filling algorithm, which means that the 𝖲𝖭𝖱 level must be increased. Note that for a fixed
c, the ratio of the derived bounds to Shannon’s capacity depends only on
and
W through the ratio
, and the results for
KHz can be extracted from our presented results for an appropriate range of 𝖲𝖭𝖱
.
To evaluate the bounds in Equations (
10), (
13), (
15) and (
16), we used the optimization toolbox in MATLAB to search for the optimal solution in
. When it comes to the upper bound (
10), the water-filling choice used by Polyanskiy only maximizes the term
and not the whole expression. However, the water-filling choice almost achieves the same performance as the optimization routine with negligible differences. When it comes to the term
, we specialize it to
for the sake of numerical computations; we used the constant
as Polyanskiy conjectured in Equation (4.218) in his thesis [
12], and we used the term
inside
since the number of real independent variables is
(as explained in
Section 4.1).
5.1. Upper Bound
To solve Equation (
10), we maximize the following quantity using the optimization tool in MATLAB
over
for different values of
N. The solution being decreasing with
m,
L is the value of
N where
saturates (which is the same as the number of non-zero
’s after saturation). We adopt similar method and notations for all the bounds presented hereafter.
Figure 6 shows the obtained
for
and at 𝖲𝖭𝖱
dB, and in this example the obtained degrees of freedom are
. The upper bound on the rates is
We compute
L and the corresponding upper bound
for different values of
c and for different levels of 𝖲𝖭𝖱.
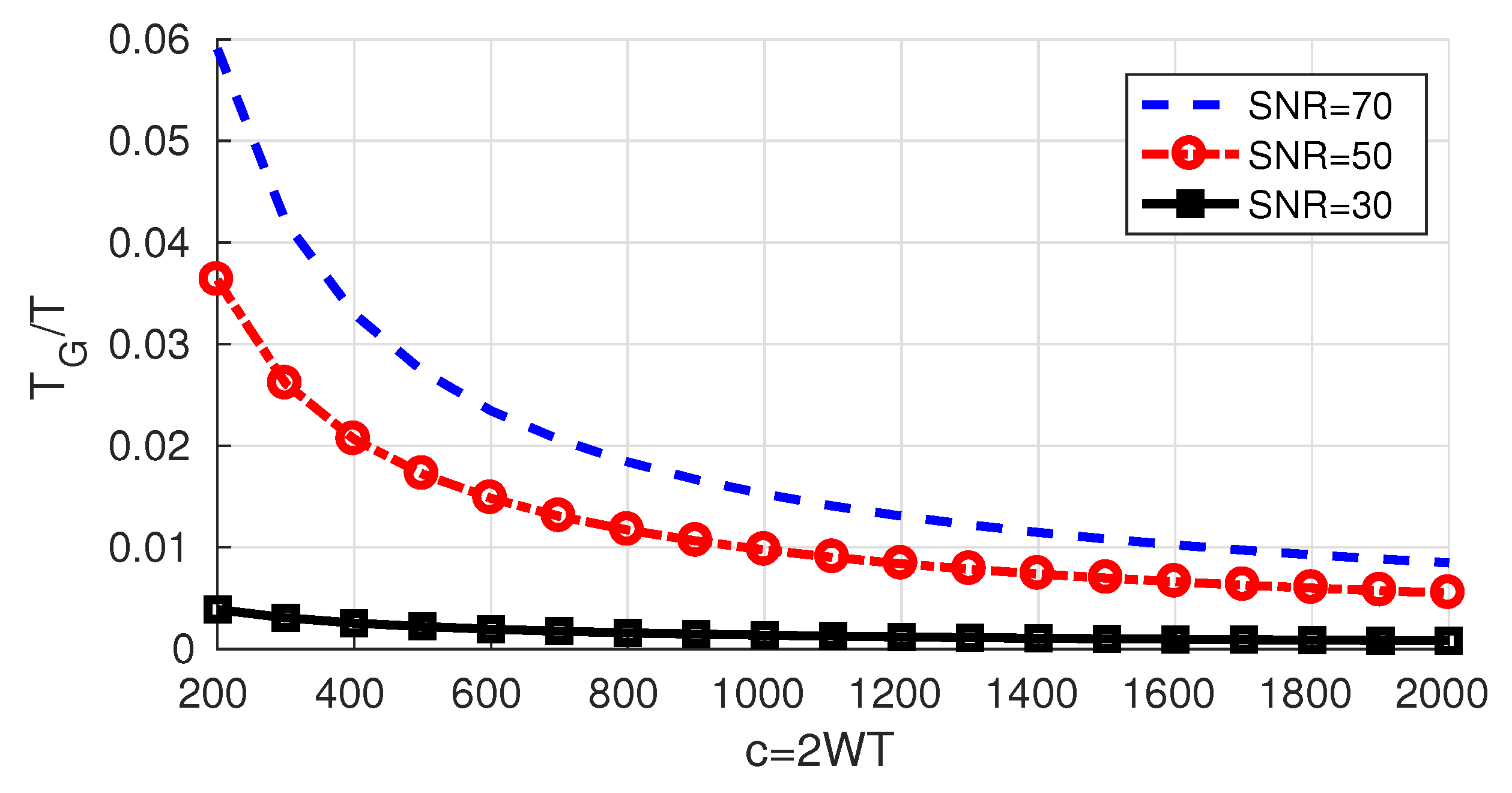
Figure 7 shows the difference
between the obtained degrees of freedom and
, and as expected,
L increases as the 𝖲𝖭𝖱 increases (in a manner akin to the water-filling solution: as the water level increases, it is possible to use additional PSWFs). However, the additional degrees of freedom (beyond c) increase slowly with
c and
as
c increases towards infinity.
In
Figure 8 we plot the obtained upper bound on the rates together with the Shannon capacity. We notice that the gap between the upper bounds and the Shannon capacity decreases as
c increases.
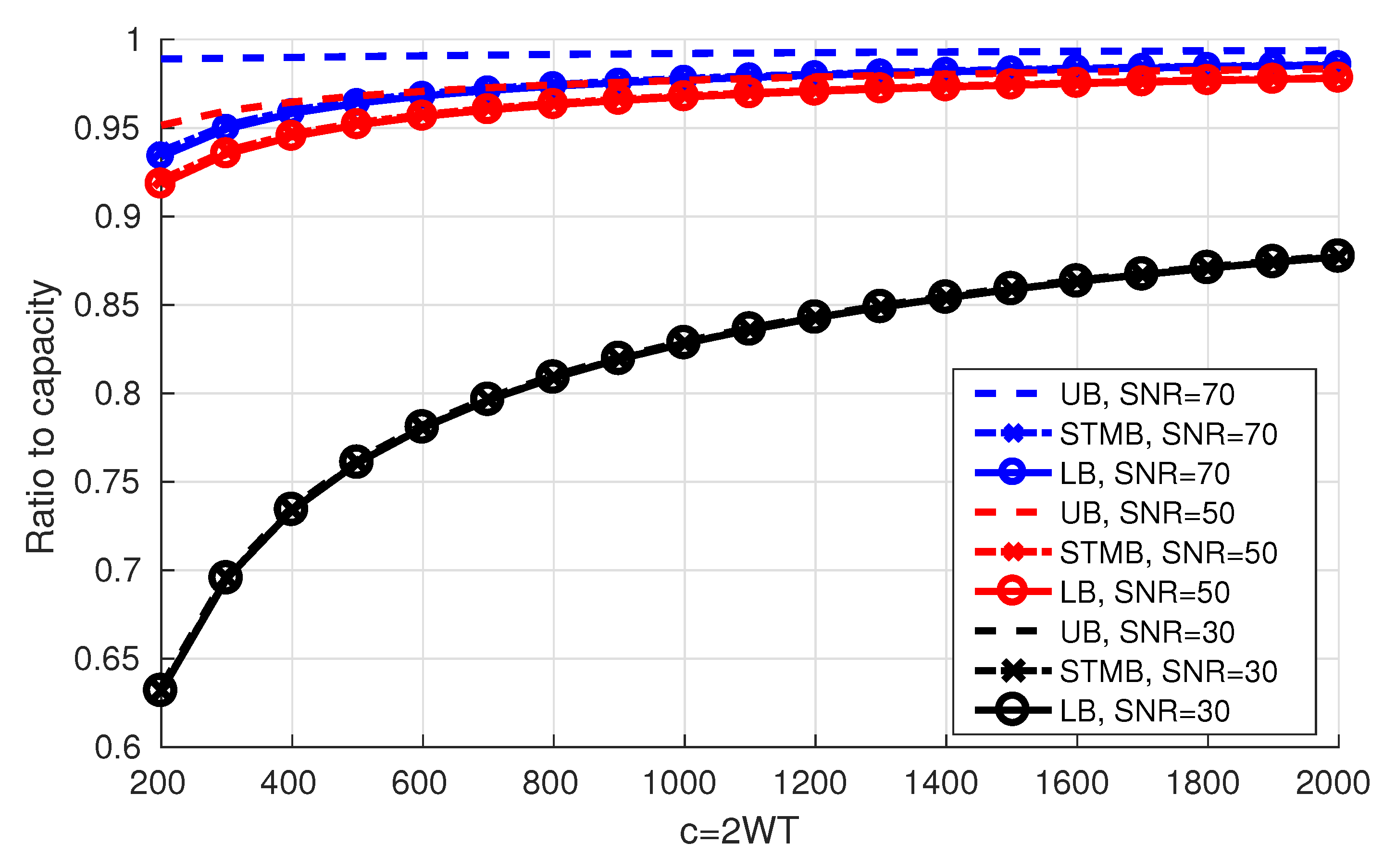
The ratio of the bounds to the Shannon capacity can be seen in Figure 10 below.
5.2. Lower Bounds
In this section, we present the numerical results for
Section 4.2.1,
Section 4.2.2 and
Section 4.2.3 (Equations (
13), (
15) and (
16)), and we apply the same numerical method we used in the previous section. We notice that the lower bounds when using either CSB or STMB are almost the same with no significant differences and we omit the results for CSB.
Figure 9 shows the obtained lower bounds on the degrees of freedom. We note that for given scenario (CSB, STMB or the general lower bound), the results are almost the same for different 𝖲𝖭𝖱 levels; increasing the signal power will only lead to increasing the power of the interference (see Equations (
13), (
15) and (
16)), and the effect on the signal to interference ratio remains negligible. Moreover, the results for the different scenarios are very close (
on average). Although
decreases as
c increases, it decreases slowly and
as
c increases towards infinity.
We propose approximating the degrees of freedom for the general lower bound by the following equation
and we draw “
” in
Figure 9. It is expected that “
” is a logarithmic function of
c since the transition region of the eigenvalues of PSWFs is a logarithmic function of
c (as shown in
Section 2).
Figure 10 shows the ratio of the obtained bounds to the Shannon capacity. For a fixed
c and as 𝖲𝖭𝖱 increases, the bounds get relatively closer to capacity and the gap between the upper bound and the lower bound increases. In addition, for a fixed 𝖲𝖭𝖱, as
c increases, the gap between the bounds decreases.