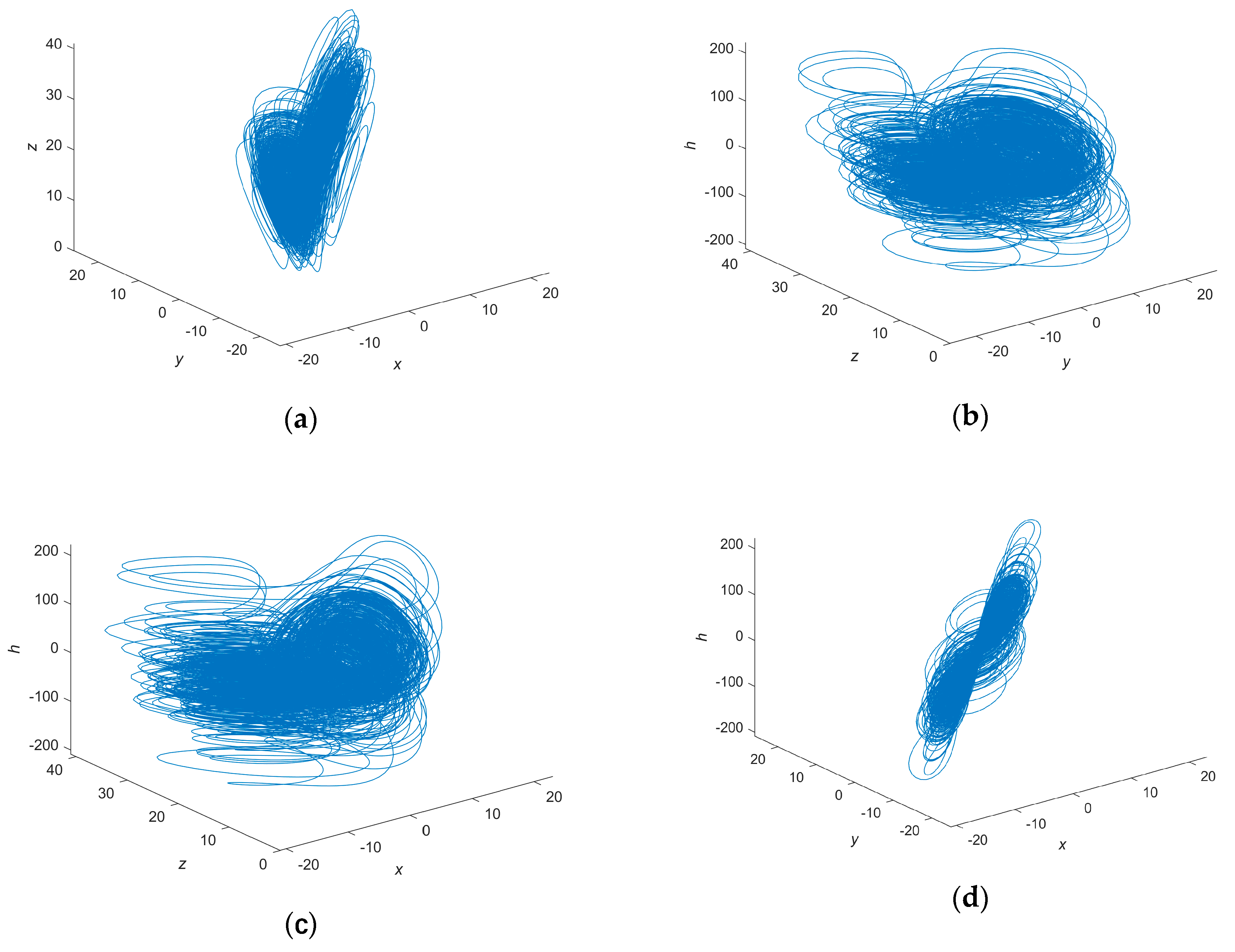
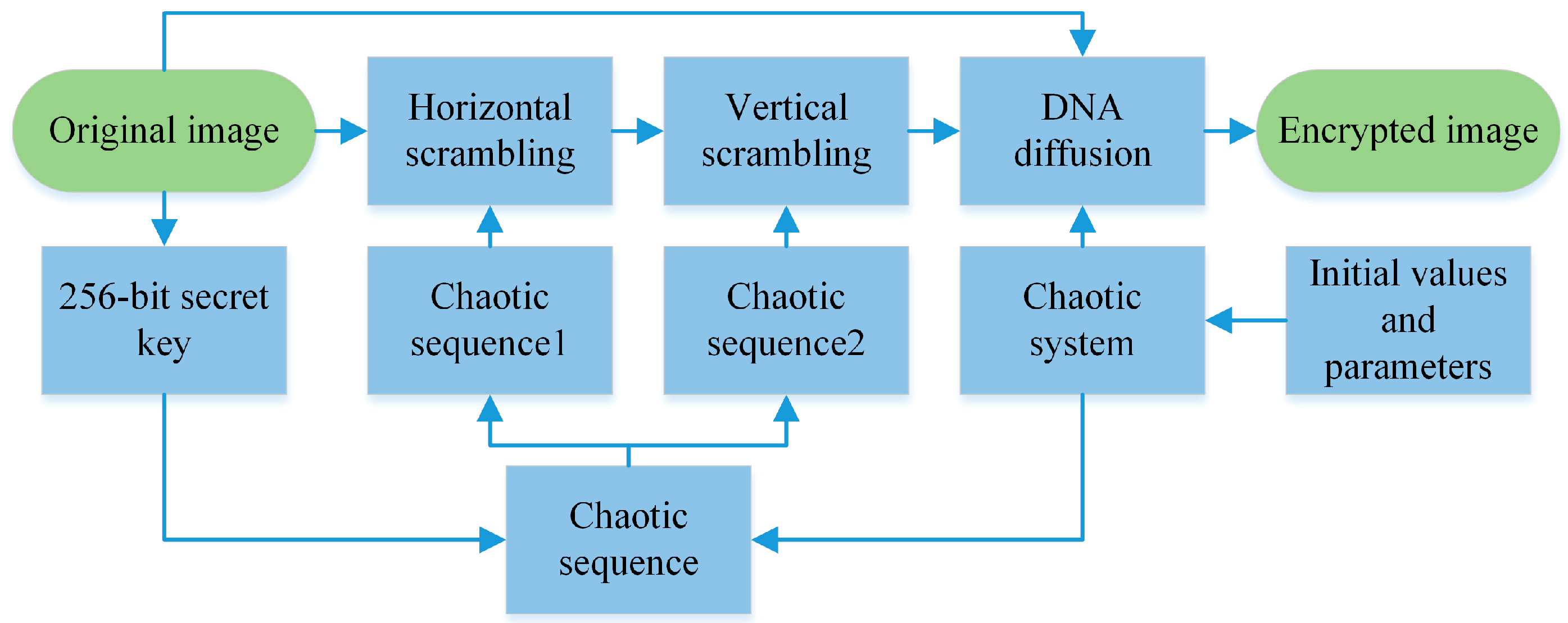
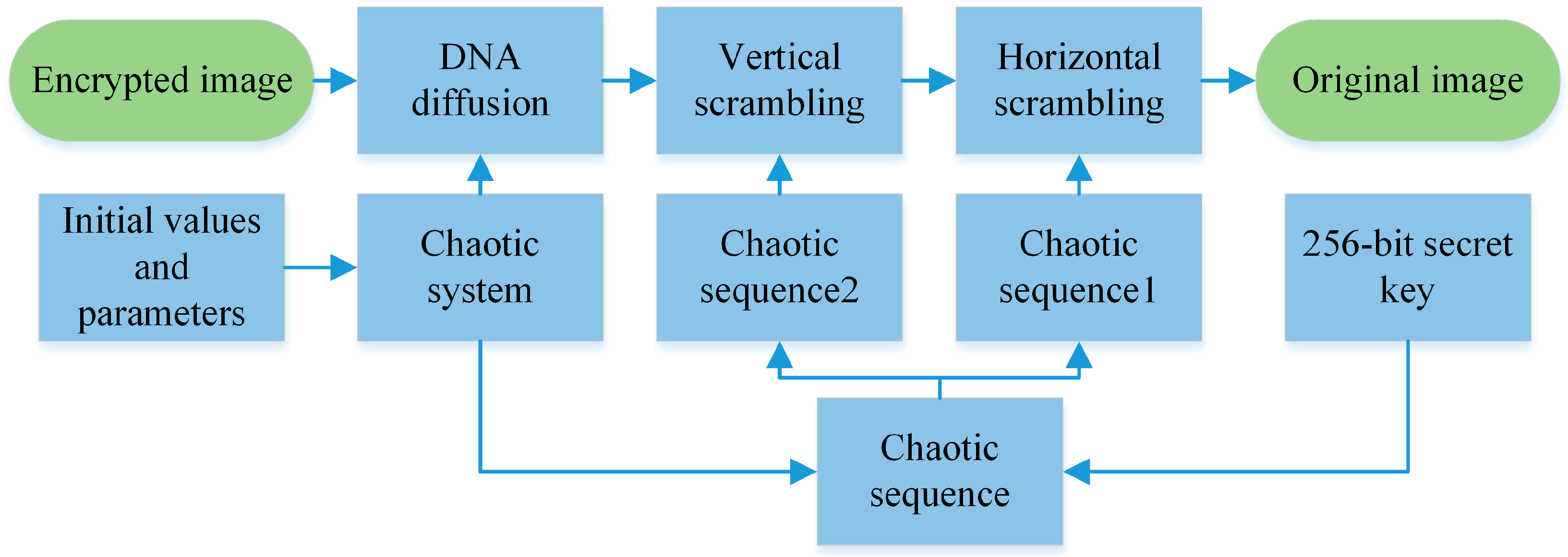
1. Introduction
In recent years, the wide application of the internet and the popularization of digital information have brought significant changes to people’s life and learning styles [
1]. Digital information has been widely used in online teaching, medical imaging, secure communication, and other fields due to its characteristics of easy access, convenient replication, and rapid dissemination, which greatly enriches people’s lives. The digital image is a form of digital information and has been widely used. However, using the openness and sharing of the network to intercept information has seriously harmed the interests of all parties in communication. Therefore, it is increasingly important to design practical and reliable encryption schemes. The encryption of digital images has received extensive attention.
Digital images are characterized by strong pixel correlation, large capacity, and high redundancy. Therefore, the computationally intensive and time-consuming DES and AES algorithms [
2,
3] are not suitable for real-time image transmission. Thus, technologies based on chaotic systems [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15], deoxyribonucleic acid (DNA) sequences [
14,
15], quantum walk [
16,
17,
18,
19], cellular automata [
20,
21], and the like are widely applied to image encryption algorithms [
22]. On the other hand, chaotic systems are especially suitable for image encryption because of their sensitivity to initial conditions and control parameters, the density of periodic points, and topological transitivity. In recent years, a large number of image encryption algorithms based on chaos have been proposed one after the other [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15]. Yin Q et al. proposed a more sensitive chaotic image encryption scheme based on permutation and diffusion structure, using breadth-first search and dynamic diffusion to enhance security and sensitivity [
13]. Chai Xiuli et al. used a hyperchaotic memory system, cellular automata, and DNA sequence operation to encrypt images [
15]. Self-excited attractors generate chaotic systems in general encryption algorithms. The attraction domain of the self-excited attractor is related to the equilibrium point. Common chaotic systems can be restored by reconstructing the attractor, which will significantly reduce the security of the encryption algorithm [
23].
In contrast, the attraction domain of hidden attractor chaotic systems does not intersect with any neighborhood of the equilibrium point. Attackers cannot restore the chaotic system by reconstructing the attractor, and the security is much better than that of ordinary chaotic systems [
23,
24,
25,
26,
27,
28,
29,
30]. Due to less research on hidden attractor chaotic system, hidden attractor chaotic system is seldom applied to the image encryption scheme. Cavusoglu et al. [
31] focused on the process of generating the hidden attractor chaotic system and did not introduce too much the effect of image encryption. In this paper, a large number of experiments are carried out to fully demonstrate the encryption effect of the encryption algorithm based on the hidden attractor chaotic system, and the security and performance of the algorithm are analyzed.
To resist attackers’ statistical attacks on the encryption system, C.E. Shannon proposed two necessary steps for designing the encryption system: diffusion and confusion. Hence, the image encryption algorithm usually includes these two steps. Many researchers have proposed many practical permutation algorithms such as Arnold transform, Hilbert curve, and baker transform [
32,
33,
34,
35]. However, these classical methods also have many problems, such as obvious periodicity and weak randomness. Shuffle algorithm has good randomness, but Erdal Guvenoglu et al. applied the Knuth–Durstenfeld algorithm to generate keys instead of confusion [
36]. In this paper, the performance of the algorithm is analyzed through a large number of experiments, and the experimental results sufficiently prove that while guaranteeing the image scrambling effect, the Knuth–Durstenfeld shuffling algorithm can reduce the time complexity and space complexity of the algorithm.
Based on the above analysis, this paper proposes a novel hybrid secure image encryption based on a shuffling algorithm and hidden attractor chaotic system. The advantages of the algorithm proposed in this paper are as follows:
The hidden attractor chaotic system is applied to image encryption. The hidden attractor chaotic system is easily affected by initial values and parameters, and the attacker cannot reconstruct the attractor to crack the chaotic system.
The Knuth–Durstenfeld shuffling algorithm is used in the shuffling process. Knuth–Durstenfeld algorithm has lower space complexity and time complexity.
In the encryption process, the key consists of the chaotic sequence of the chaotic system and the hash sequence of the image, which ensures the security of transmission.
The structure of the paper is as follows: The second section introduces the preliminary work and methods. The third section introduces the proposed image encryption scheme. The fourth section, experimental results, and analysis. The fifth section, safety, and performance analysis. The sixth section is the conclusion of the thesis.
5. Security Analysis
In the fifth section, the security of the encryption algorithm is evaluated through key space analysis, key sensitivity analysis, histogram analysis, correlation coefficient analysis of adjacent pixels, information entropy analysis, differential cryptanalysis analysis, noise attack analysis, known plaintext, and selective plaintext attack analysis.
5.1. Key Space Analysis
According to references, the key space of the algorithm must be large enough to resist various violent attacks, and the key space should be at least 2
100 ≈ 10
30 [
40,
41]. In this algorithm, the key space consists of three parts: SHA-256 function value of the original image, the initial values of the chaotic system, and parameters of a chaotic system. The ideal key space of SHA-256 is 2
128, if the accuracy of four parameters
x0,
y0,
z0, and
h0 of a chaotic system is set to 10
−15, the key space can reach 10
60, and the key space of the algorithm can reach 2
327, much larger than 2
100 [
42],
Table 8 shows the key space comparison between the algorithm in this paper, and that in reference [
43,
44,
45,
46,
47], the algorithm in this paper has a larger key space, it is generally believed that the algorithm’s key length up to 128 bit is secure. The algorithm’s key space has reached a security standard. From literature [
48], it can be seen that the algorithm in this paper can resist all kinds of exhaustive attacks.
5.2. Key Sensitivity Analysis
A good encryption algorithm should be susceptible to keys. In the process of decrypting encrypted images, minor changes in the key will also cause the recovery of encrypted images to fail. The sensitivity of the algorithm key is analyzed to verify the security of the encryption algorithm. In the experiment, x0 in the original key is modified to x0 + 10−15, and uses the modified key set to decrypt the encrypted image.
In
Table 9, the first column is the original image, the second column is the encrypted image, the third column is the decrypted image using the wrong key, and the fourth column is the decrypted image using the correct key. When the error rate of a single key reaches the order of 10
−15, the original image cannot be obtained. When any one of the multiple keys is changed, the original image cannot be decrypted, as shown in
Table 10. Experimental results show that the encryption algorithm is highly sensitive to keys.
5.3. Statistical Attack Analysis
5.3.1. Histogram Analysis
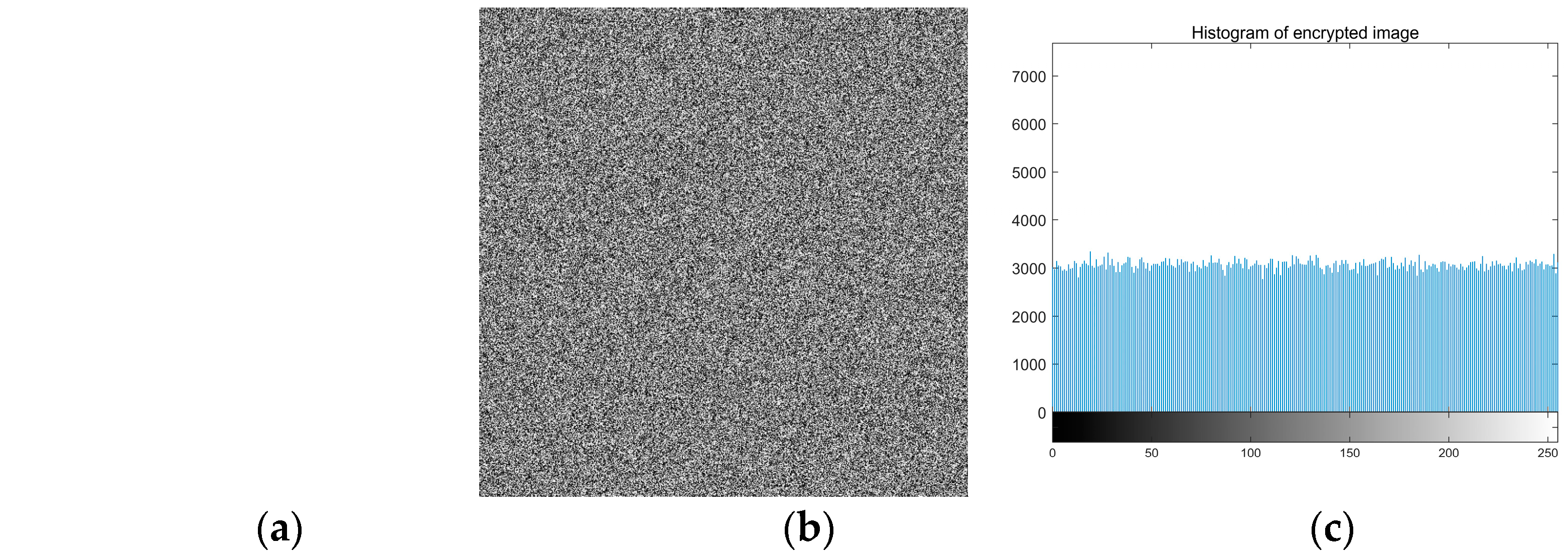
The encryption system must make the encrypted image have a uniform histogram to resist statistical attacks because the image histogram represents the distribution of pixel intensity values in the image. Histograms of the original image and encrypted image are shown in
Table 11. The abscissa of the histogram is the gray level, and the ordinate is the frequency of occurrence of the gray level.
The experimental results show that the pixels of the encrypted image obey the uniform distribution, that is to say, the frequency of each pixel value after encryption is very close, and the attacker will not be able to obtain the statistical law of the encrypted image. To verify whether the histogram of the encrypted image obeys uniform distribution, the encrypted image is quantized by chi-square test, and the formula is as shown [
49];
fe is the expected value of the pixel point, fi is the value of the 1st-pixel point, n is the total number of pixels, and the significance level is 0.05.
In addition to the Chi-square test, this paper calculates the variance of the histogram to evaluate the uniformity of encrypted image distribution. The smaller the variance is, the closer it is, the higher the consistency of the encrypted image is, the better the uniformity of the encrypted image is. In this paper, we calculate two variances of the same original image encrypted by two different sets of keys. The variance formula is as follows:
, Z is the frequency at which gray values occur. In the experiment, the “Lena” image is used for the experiment. The variance of the histogram of the original image is 33,860. Only one key in the two key groups is different. The variance value of the encrypted image is about 250, indicating that the average value of the number of pixels in each gray value is about 13 pixels. Experiments show that the histogram of the encrypted image is very uniform and will not provide any information to the attacker.
Table 11 shows the experimental results of the chi-square test. As can be seen from
Table 11, the pixel distribution of the encrypted image follows a uniform distribution, and it is difficult for the attacker to crack the algorithm by analyzing the histogram of the encrypted image. The encrypted image will not provide any useful information to the attacker. The encryption algorithm proposed in this paper can effectively protect images from statistical attacks.
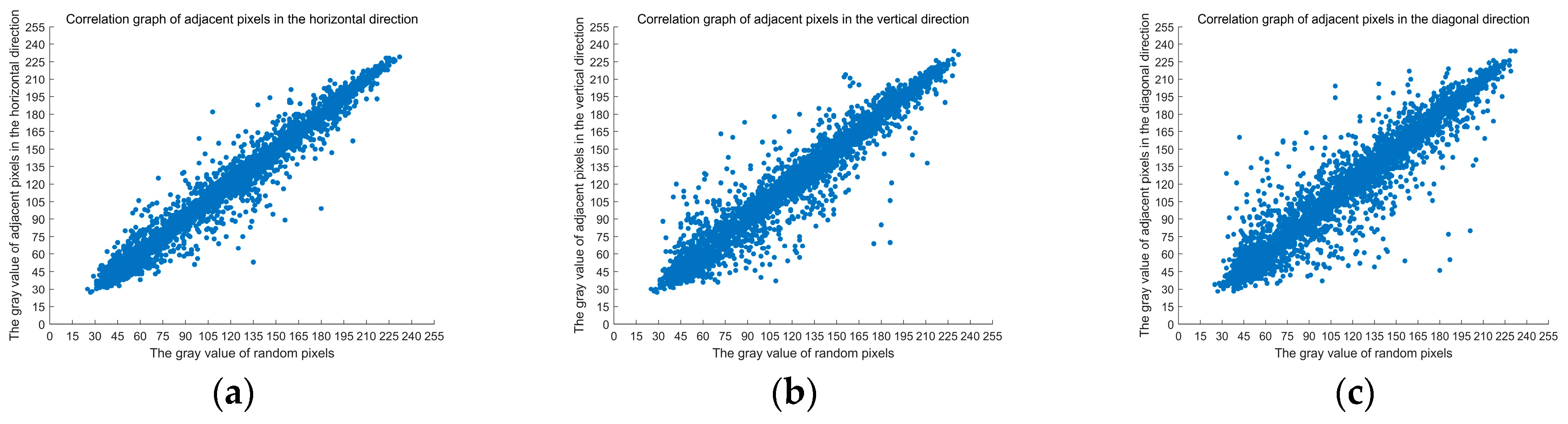
5.3.2. Correlation Analysis
Adjacent pixels of the original image has a strong correlation in all directions. Only when the correlation coefficient of adjacent pixels of the encrypted image is low enough, the image processed by the encryption algorithm resist statistical attacks. Adjacent pixels are randomly selected from each direction of the original image, and the encrypted image, correlation coefficients are calculated. The correlation between adjacent pixels in the original image and the encrypted image is analyzed. The calculation formula of the correlation coefficient
rxy is shown in formula (10):
In the above formula, N is the total number of pixel points, x and y are gray values of adjacent pixels, E(x) is the average value of the pixel, D(x) is the variance, cov(x, y) is the correlation function, and rxy is the correlation coefficient, the higher the absolute value, the stronger the correlation.
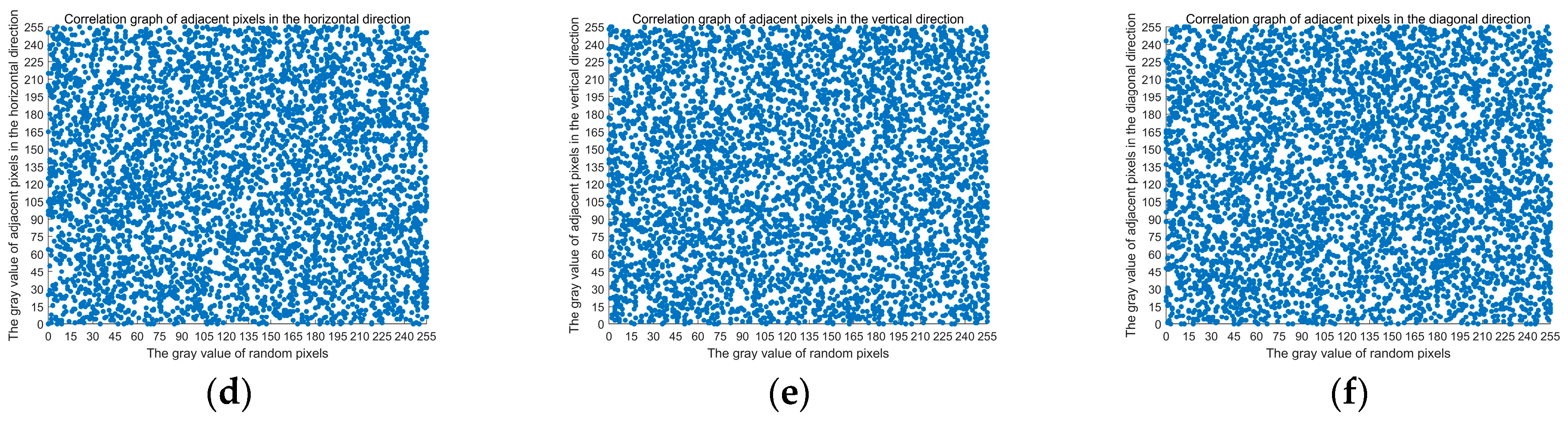
Table 12 shows the pixel correlation coefficients of the original image and the encrypted image in all directions. The correlation coefficients of adjacent pixels in the original image are all close to 1, and the correlation coefficients of encrypted images are all close to 0, which indicates that the original image has a significant correlation between pixels in different directions. Still, the correlation of adjacent pixels is eliminated after encryption algorithm processing.
To more intuitively compare the correlation between adjacent position data values of images before and after encryption, the image “Lena” and its encrypted images are taken as examples. The correlation of their two adjacent pixels in the horizontal, vertical, and diagonal directions are plotted respectively, the abscissa is the data value of the random point position, and the ordinate is the data value of the random point adjacent position, as shown in
Figure 5.
In
Figure 5a is the horizontal distribution of adjacent pixels before encryption,
Figure 5b is the vertical distribution of adjacent pixels before encryption,
Figure 5c is the diagonal distribution of adjacent pixels before encryption,
Figure 5d is the horizontal distribution of adjacent pixels after encryption,
Figure 5e is the vertical distribution of adjacent pixels after encryption, and
Figure 5f is the diagonal distribution of adjacent pixels after encryption.
As can be seen from
Figure 5, the adjacent pixel points of the original image are continuously distributed, and the adjacent pixel point values of the ciphertext image are randomly distributed. They are distributed all over the two-dimensional space. The ciphertext image eliminates the correlation of the adjacent pixels and masks the data characteristics of the original image.
The experimental results show that the encryption algorithm greatly reduces the pixel correlation of encrypted images, and attackers cannot obtain useful information from encrypted images through statistical attacks. The algorithm in this paper has high security, and statistical attacks cannot crack the encryption algorithm in this paper.
5.3.3. Information Entropy Analysis
There are many indexes to judge the randomness of pixels, of which the information entropy is the most commonly used and essential index, and its specific mathematical definition is shown in Equation (14):
Among them, the proportion of image gray value
xi is expressed by (
xi), and the gray level of the image is 2
N. If the gray level of the image is
M, then
Hmax = log
2M (bit/symbol) has its maximum entropy. When
M = 256 = 2
8,
Hmax = 8, the closer the number is to 8, the less likely the attacker is to crack the encrypted image. In the experiment, information entropy was calculated for the ciphertext images of ten test images, comparison with the literature [
51], and the results are shown in
Table 13.
As can be seen from
Table 13, the Shannon entropy of the encrypted image exceeds 7.99, which is very close to the theoretical value of 8, and the entropy value is higher than the literature [
51]. Therefore, the encrypted image generated by the encryption algorithm proposed in this paper has good randomness and sufficient security to resist statistical attacks.
5.4. Analysis of Known-Plaintext and Selective-Plaintext Attacks
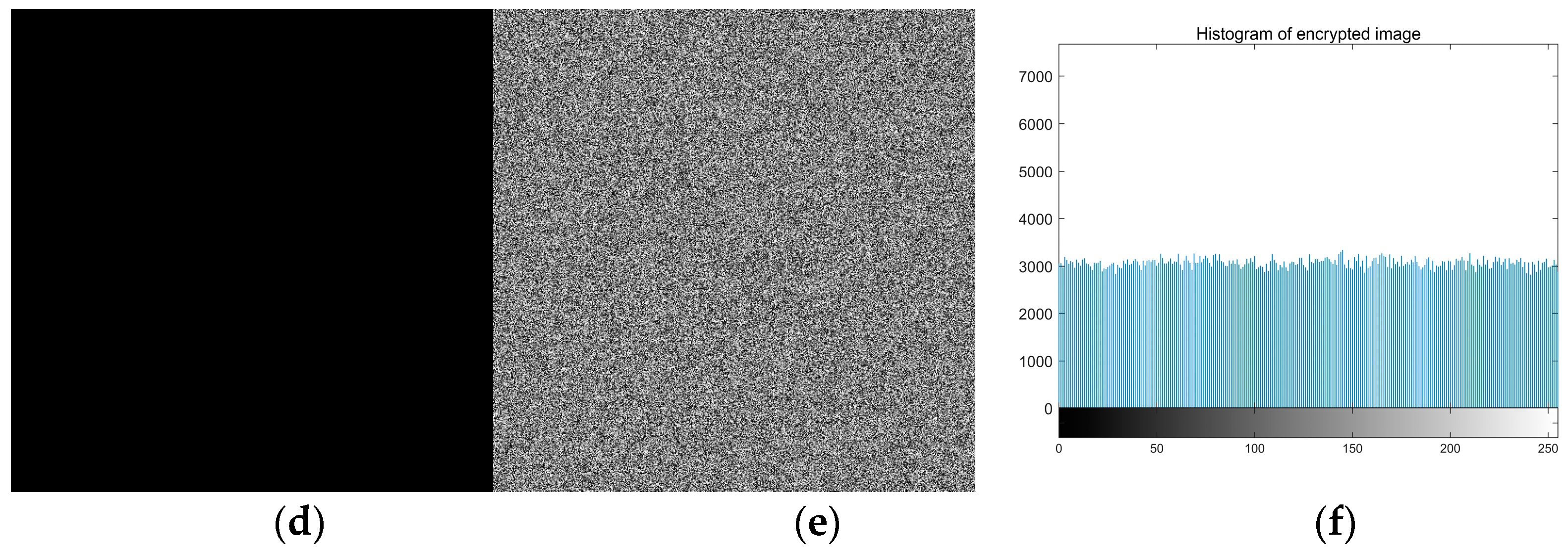
In the encryption process, the algorithm uses the SHA-256 function, and the key space includes the hash value of the original image, so the diffusion and scrambling process is closely related to the original image. The algorithm is susceptible to slight changes in the original image.
In this paper, we test all black and all white images to analyze whether the experiment will fail the encryption algorithm. The chi-square test results of information entropy, NPCR, UACI, pixel correlation coefficient, and histogram are shown in
Table 14.
Figure 6 shows the histogram of the original image and encrypted image. The unified average change intensity (UACI) is one of the important analyses of the sensitivity tests. The number of pixel changing rate (NPCR) manifests the possibility of the differential attack by its sensitivity. The typical values of NPCR and UACI are 99.61% and 33.46%, respectively. The calculation formula is as follows:
Table 14 shows that the entropy of encrypted images is more significant than 7.99. The UACI value and the NPCR value approach the theory, the results show that the two images before and after encryption, are entirely different; The correlation coefficients of pixels in three directions are close to 0 and accord with uniform distribution, so useful information cannot be obtained. This algorithm can resist known plaintext attacks and selective plaintext attacks. The experimental results show that the encryption algorithm in this paper cannot be cracked by using all-white and all-black images.
5.5. Differential Attack Analysis
Take the image “5.2.08” as an example [
52], compare the image encryption algorithm in this paper with that in literature [
53,
54], and obtain the average value of UACI and NPCR, as shown in
Table 15. To make the encryption algorithm resist the differential attack, we must make the algorithm very sensitive to the original image, and the small changes of the original image can produce significant changes in the encrypted image. There are many evaluation criteria for the anti-differential cryptanalysis ability of the encryption algorithm, which are generally measured by average change intensity (UACI) and pixel change rate (NPCR). UACI and NPCR values of different images are shown in
Table 16.
To more intuitively display the influence on the encrypted image when the pixel value at a certain position of the image changes, taking the image “Lena” as the experimental object, Compare the encrypted image after changing the pixel with the encrypted image of the original image, the experimental results are shown in
Table 17.
From the above two tables, it can be seen that the encryption scheme is susceptible to the changes in the original image, and UACI and NPCR are close to the theoretical values. Even if the changes in the original image are minimal, two completely different encrypted images can be obtained. Therefore, the algorithm in this paper can effectively resist differential attack.
5.6. Analysis of noise attack
In fact, in the process of image transmission, it is often affected and destroyed by noise, resulting in inevitable errors, which makes it difficult to decrypt. To test the anti-noise performance of the algorithm, different levels of Gaussian noise and salt and pepper noise are added to the ciphertext image to simulate the noise in the transmission process, which is a reasonable assumption derived from the real physical channel. If the encryption system is sensitive to noise, the change of the encrypted image will hinder the image decryption [
42]. In Lena’s encrypted image, Gaussian noise with different variance, salt and pepper noise with different intensity are added respectively, and the noise is evenly distributed in the encrypted image.
Figure 7 is a decrypted image in each case. For each image in
Figure 7, the correlation coefficient between the decrypted image and the noisy decrypted image is determined by the structural similarity method. The closer the structural similarity coefficient i
s to 1, it is proved that the smaller the error between the decrypted image and the noisy decrypted image is, the stronger the anti-noise ability of the system is. As shown in
Table 18, the measurement value of the correlation coefficient between two images proves the robustness of noise. The correlation coefficient is close to 1 and larger than the literature [
47]. That is to say, and the decrypted image still retains the whole information of the original image, which verifies the system’s ability of anti-noise attack.
5.7. Analysis of Algorithm Complexity and Performance
In addition to paying attention to security, the encryption algorithm should also consider the operation speed of the algorithm, usually including time complexity and space complexity. The algorithm with low complexity has fast processing speed and can be used for real-time encryption.
The time complexity of the algorithm in this paper depends on key stream generation, permutation operation, and diffusion operation. Let the size of the original image P be m × n. The length of chaotic sequences generated by the system is m × n, and the time complexity is O(m × n). The diffusion part includes DNA encoding and XOR, with a complexity of O(m × n).
Table 19 shows that compared with the algorithms of the References [
55,
56,
57,
58,
59], the encryption algorithm in this paper has lower time complexity. Spatial complexity is an important index to measure the complexity of algorithms. In this paper, the Knuth–Durstenfeld algorithm is applied to the scrambling process, where the space complexity of the algorithm is O (1), which means that the encryption algorithm does not need more complicated calculations in the scrambling phase. However, many existing encryption schemes [
13,
15,
20] have larger space complexity than O(1) and are less efficient than the algorithm in this paper.
Taking the image “Lena” as an example, the correlation coefficients of adjacent pixels in the horizontal, vertical, and diagonal directions of the encrypted image are calculated, as shown in
Table 20. The results prove that the encryption scheme in this paper can achieve the encryption effect of the encryption algorithm in reference [
55,
56,
57,
58,
59]. The application of the Knuth–Durstenfeld algorithm to scrambling not only ensures the scrambling impact, but also reduces the complexity of the algorithm and improves the efficiency of the algorithm. Moreover, with the increase of image size, the advantages of the algorithm will gradually become obvious.
In
Table 20, the correlation coefficient of the encrypted image of the encryption scheme in this paper is less than or close to that of documents [
57,
60,
61,
62], which indicates that the shuffling algorithm adopted in this paper can achieve the scrambling effect of other encryption algorithms. The information entropy of encrypted images is larger than that of documents [
57,
60,
61,
62] and closer to the theoretical value of 8, which proves that the images encrypted by the encryption scheme in this paper have good randomness. Combined with the above experimental results, the encryption scheme in this paper is superior to that in literature [
57,
60,
61,
62].
6. Conclusions
This paper proposes hybrid secure image encryption based on the shuffle algorithm and the hidden attractor chaos system. The hidden attractor chaotic system generates the chaotic sequence required for image encryption. The NIST and TESTU01 tests are carried out on the chaotic sequence generated by the hidden attractor chaotic system, which proves that the hidden attractor chaotic system is suitable for image encryption. Because the shuffling algorithm has good randomness, this paper uses a shuffling algorithm to scramble images. In this paper, the security of the scheme is verified through a large number of experimental analyses: exhaustive attack, statistical attack, differential cryptanalysis, known-plaintext attack and selective plaintext attack, and noise attack. The experimental results show that the scheme is useful and practical in the field of image encryption, but there are still many areas to be explored and improved. The algorithm in this paper is mainly designed for grayscale images, which need to convert data into grayscale images and encrypt them. In the future, the range of encryption algorithm can be expanded to encrypt more image types.