Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix
Abstract
1. Introduction
2. Theories and Methods
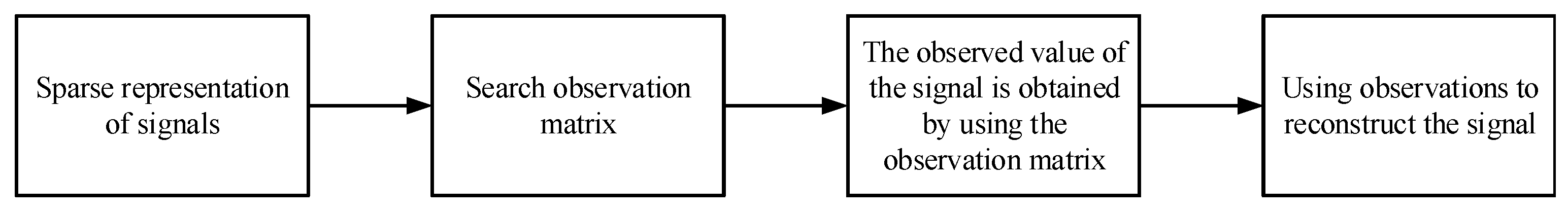
2.1. Mathematical Representation of Compressed Sensing
- Selection of a sparse basis: For a signal X of length N, select a sparse basis. If the K coefficient is not zero, after sparse transformation and , then we say the signal X is K sparse under the sparse basis [22]. The original signal can be recovered, using the sparse signal; however, the approximation of the original signal is obtained.
- Design of a measurement matrix: in the design of a measurement matrix, the restricted isometry property (RIP) needs to be satisfied in order to solve , which is an underdetermined solution problem. The RIP can guarantee the one-to-one mapping of original space to sparse space. In the algorithm proposed here, a chaotic signal is used to generate a measurement matrix, sequence signals generated by a sequence signal generator are then used to generate multiple measurement matrixes, and then, images are compressed and encrypted using multiple measurement matrixes.
- Selection of a reconstruction algorithm: In the process of signal reconstruction, choosing an optimal reconstruction algorithm is key to the reconstruction effort. Currently, the reconstruction algorithm of CS is mainly divided into two categories: first, including a greedy algorithm, matching tracking algorithm, orthogonal matching tracking algorithm, etc. The second category includes a convex optimization algorithm, gradient projection method, basis tracking method, minimum Angle regression method, etc.
2.2. Logistic-Tent Chaotic System
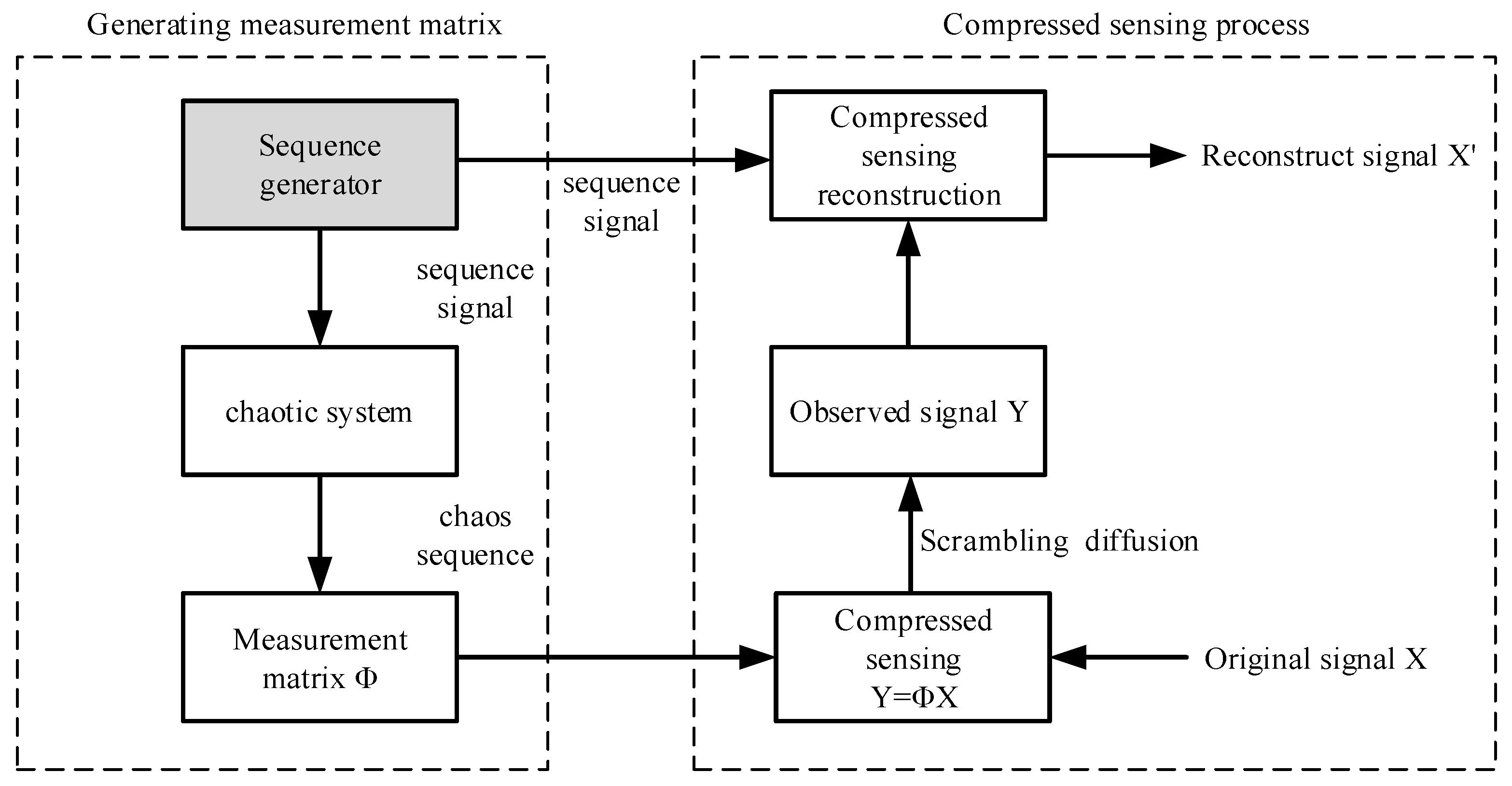
3. Parallel Compressed Sensing Encryption Algorithm Based on Sequence Generator
3.1. Algorithm Principle
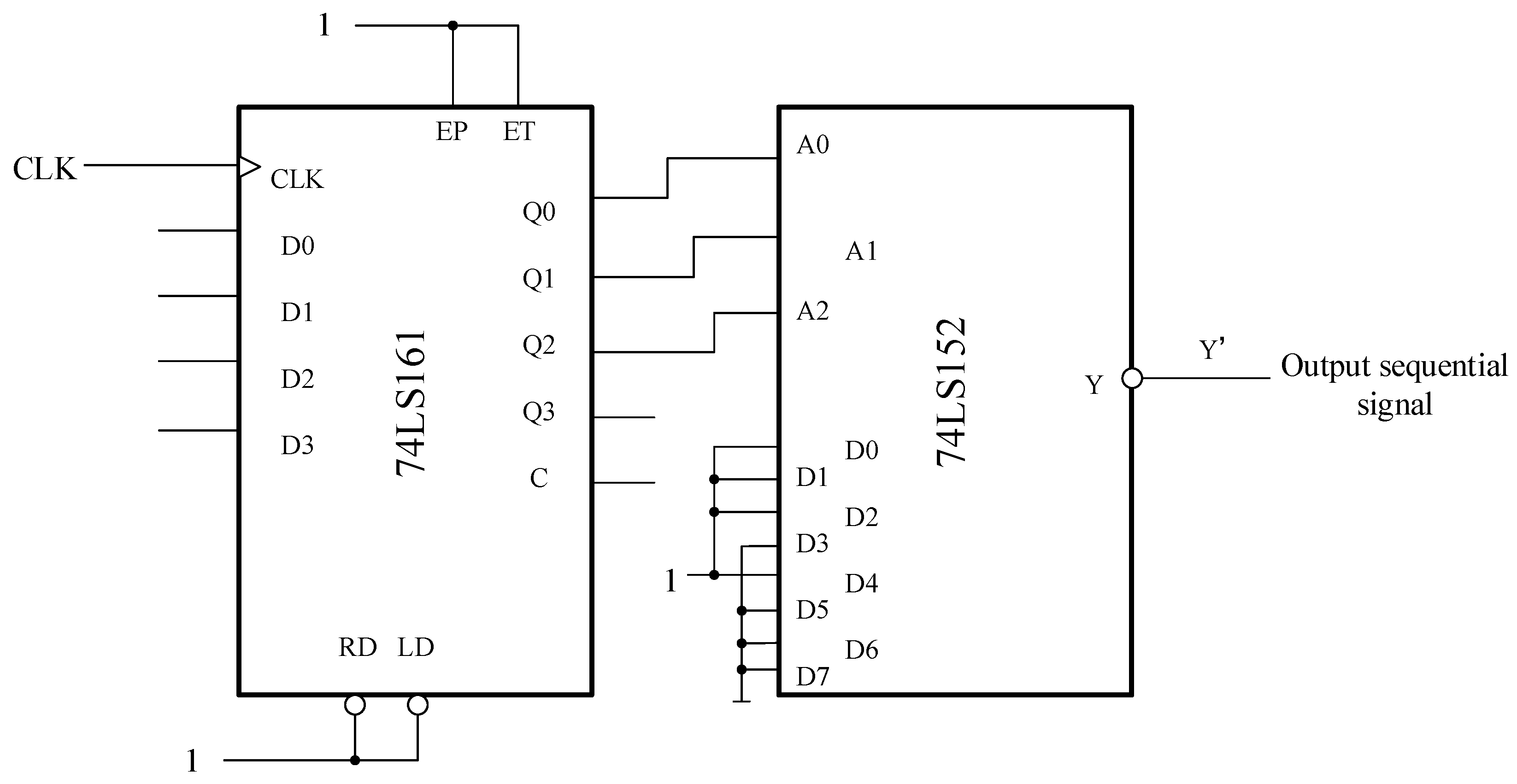
3.2. Sequence Signal Generator Mode
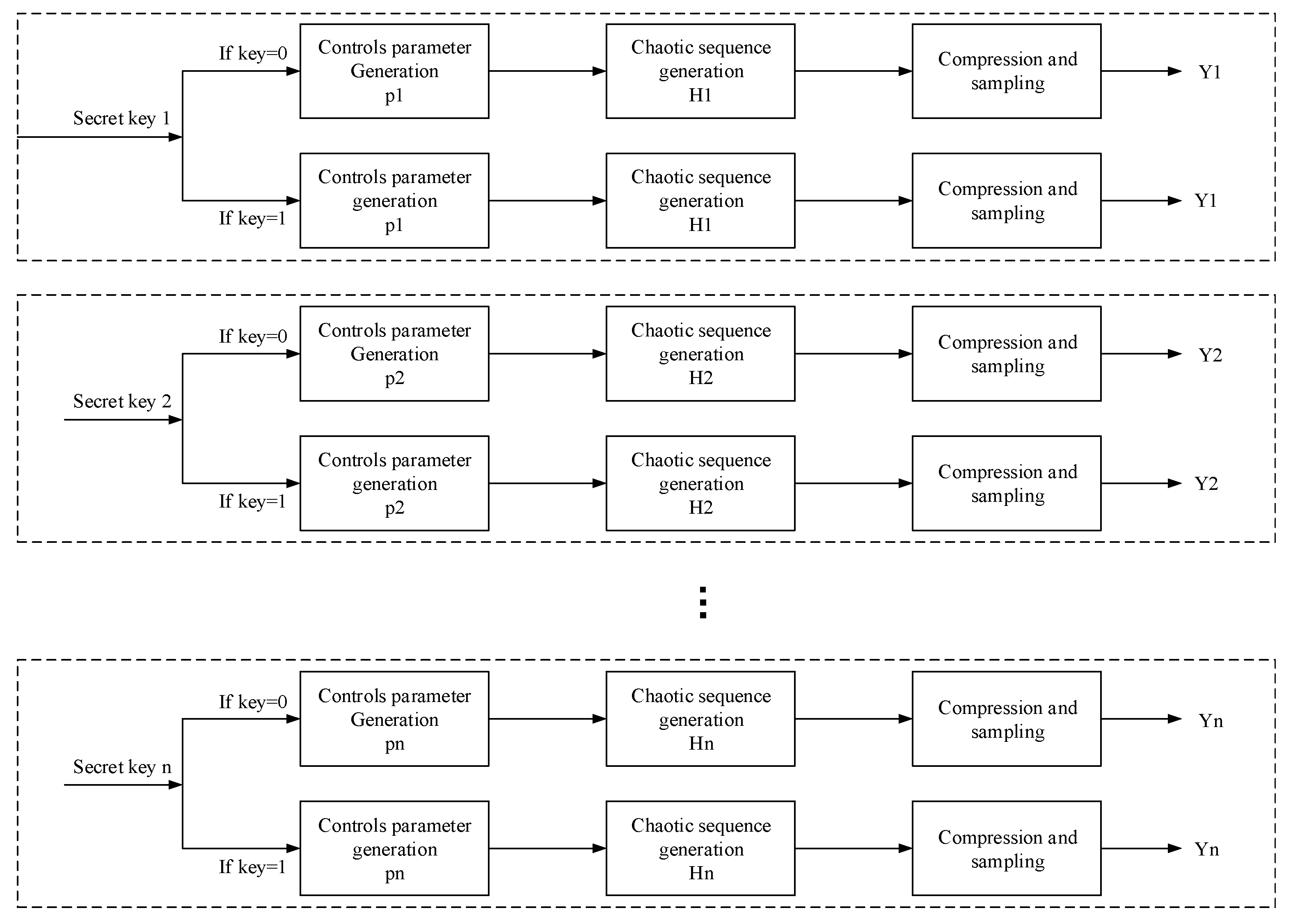
3.3. Parallel Compression Sensing
4. Simulation Results and Security Analysis
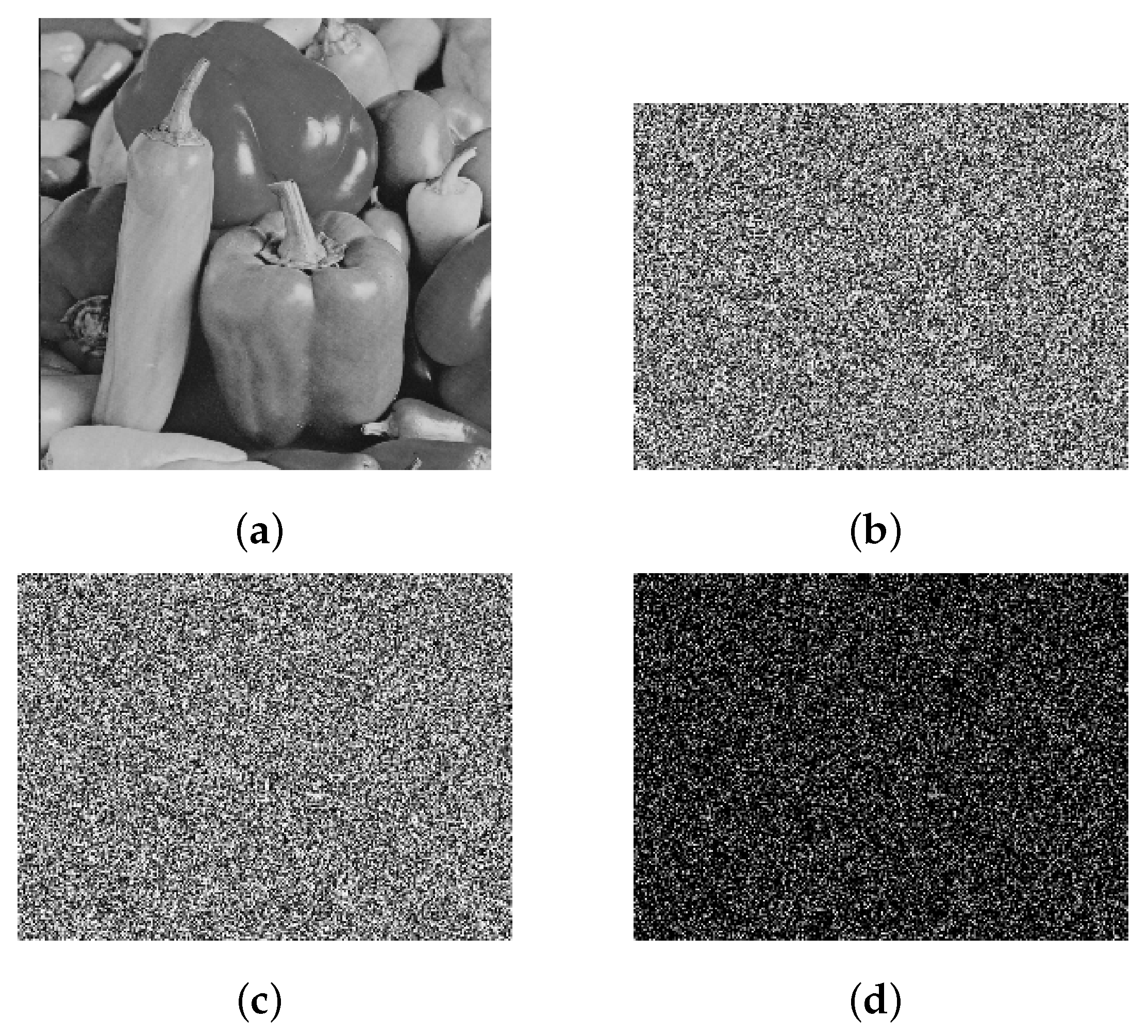
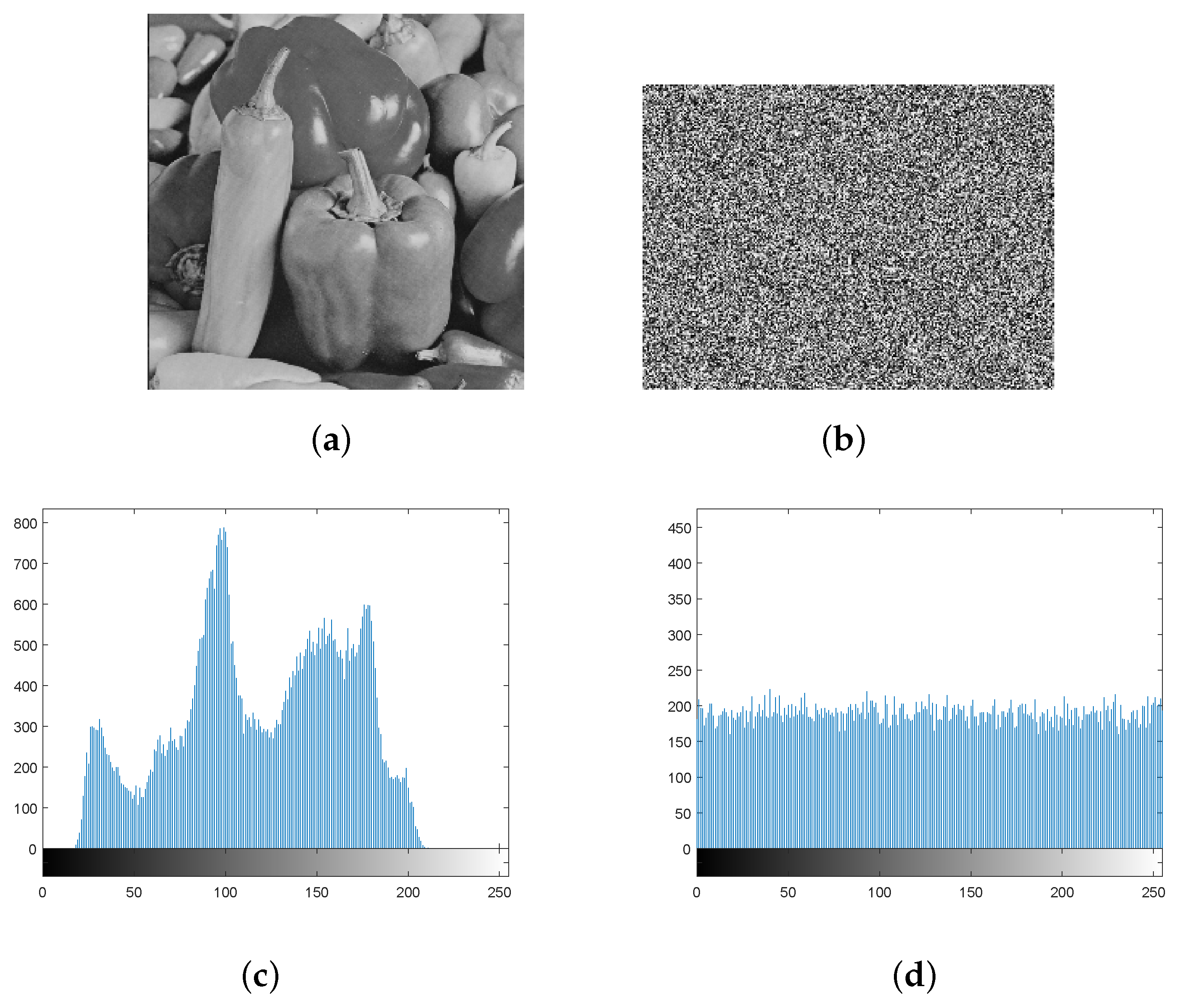
4.1. Encryption Performance Analysis
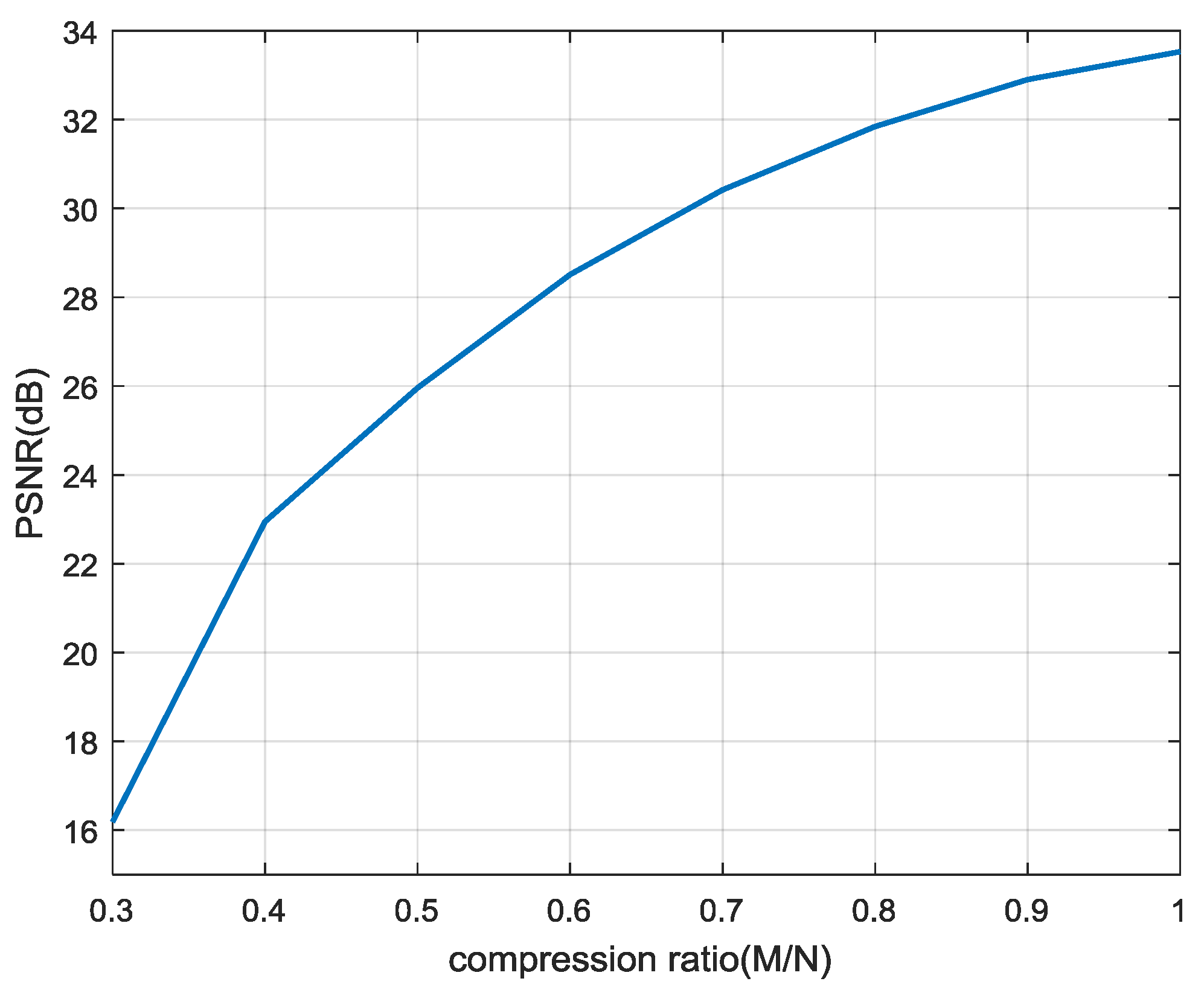
4.2. Decryption (Reconstruction) Performance Analysis
4.3. Key Sensitivity Analysis
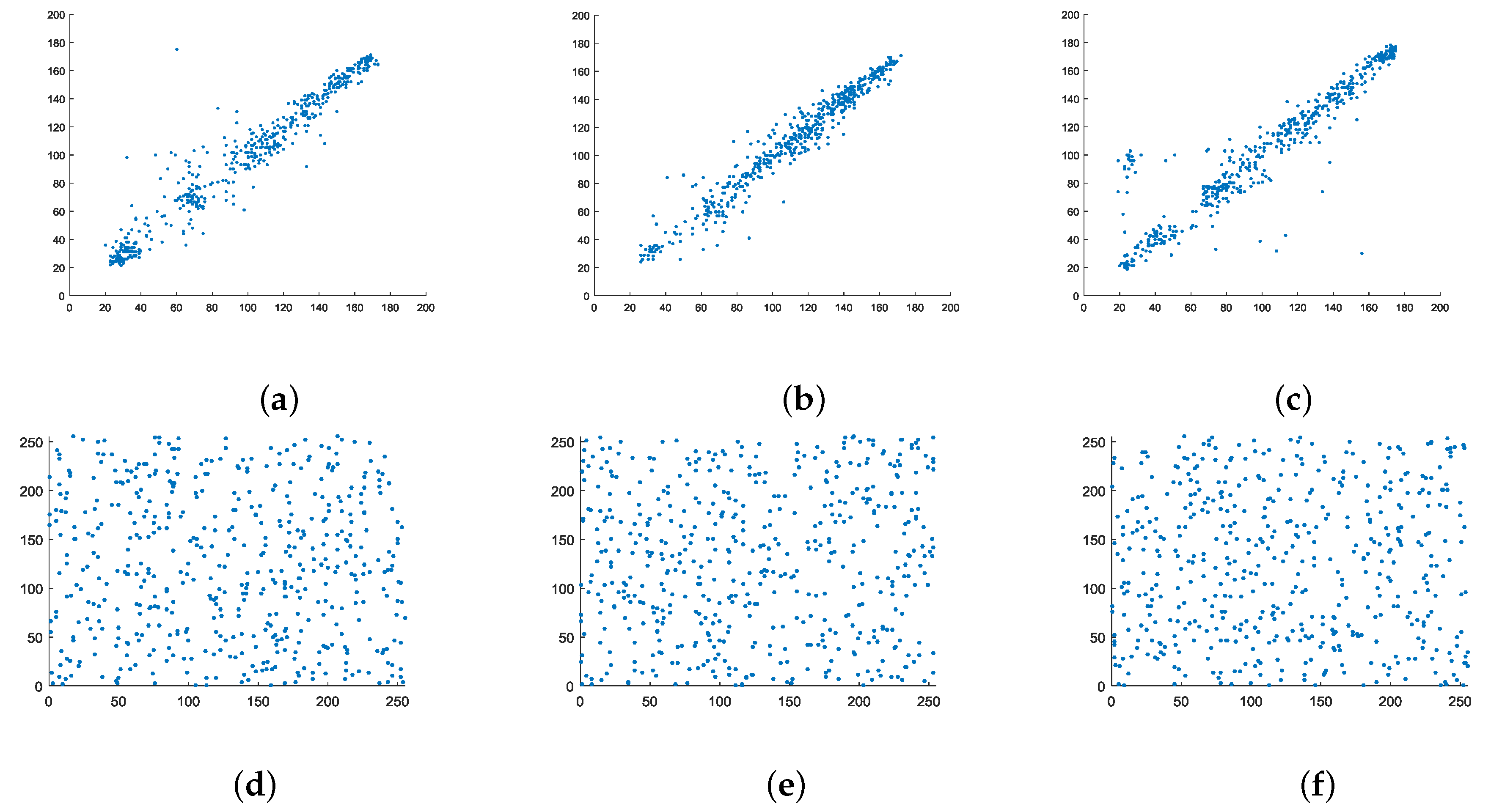
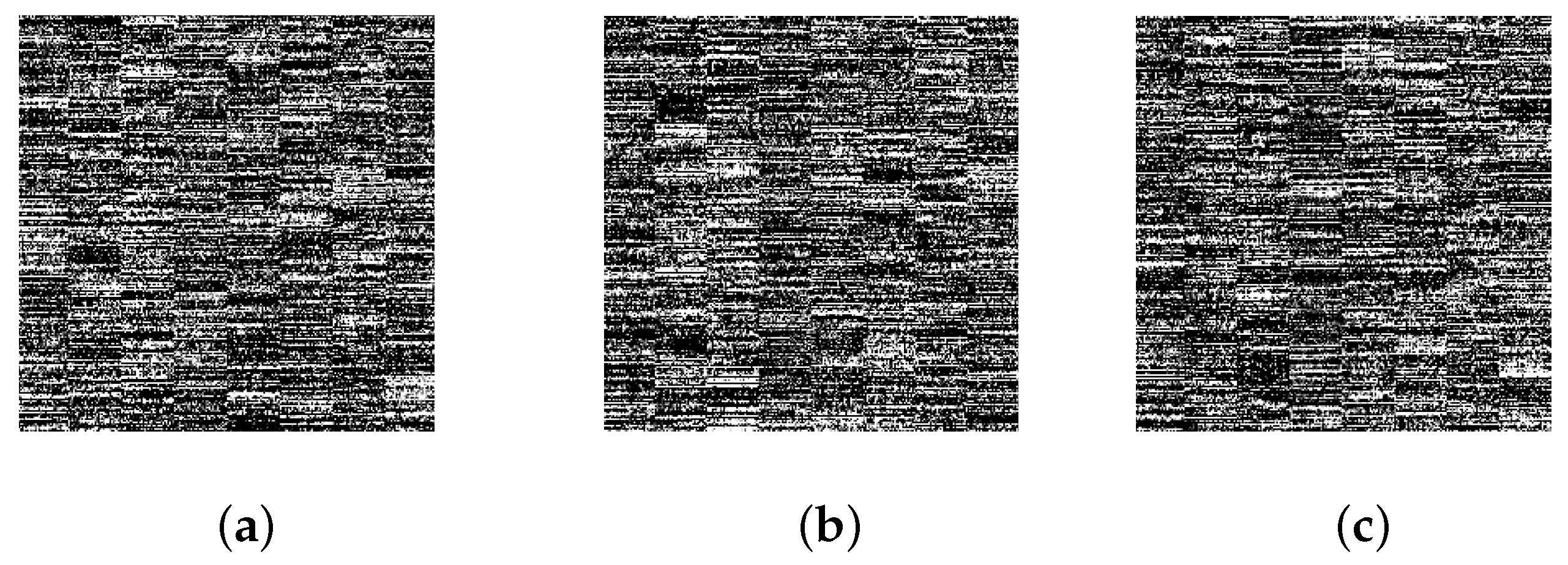
4.4. Safety Analysis
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| MDPI | Multidisciplinary Digital Publishing Institute |
| DOAJ | Directory of open access journals |
| TLA | Three letter acronym |
| LD | linear dichroism |
References
- Wang, X.; Zhang, Y.; Bao, X. A novel chaotic image encryption scheme using DNA sequence operations. Opt. Laser. Eng. 2015, 73, 53–61. [Google Scholar] [CrossRef]
- Zhou, N.; Zhang, A.; Zheng, F.; Gong, L. Novel image compression–encryption hybrid algorithm based on key-controlled measurement matrix in compressive sensing. Opt. Laser Technol. 2014, 62, 152–160. [Google Scholar] [CrossRef]
- Hu, G.; Xiao, D.; Wang, Y.; Xiang, T. An image coding scheme using parallel compressive sensing for simultaneous compression-encryption applications. J. Vis. Commun. Image Represent. 2017, 44, 116–127. [Google Scholar] [CrossRef]
- Zhu, H.; Zhang, X.; Xiang, H. A Novel Image Encryption Scheme Using the Composite Discrete Chaotic System. Entropy 2016, 18, 276. [Google Scholar] [CrossRef]
- Castiglione, A.; Pizzolante, R.; Palmieri, F.A.N.; Masucci, B.; Carpentieri, B.; De Santis, A.; Castiglione, A. On-Board Format-Independent Security of Functional Magnetic Resonance Images. ACM Trans. Embed. Comput. Syst. 2017, 16, 15. [Google Scholar] [CrossRef]
- Yang, C.-Y. Robust high-capacity watermarking scheme based on Euclidean norms and quick coefficient alignment. Multimed. Tools Appl. 2017, 76, 1455–1477. [Google Scholar] [CrossRef]
- Ponuma, R.; Amutha, R. Encryption of image data using compressive sensing and chaotic system. Multimed. Tools Appl. 2018, 78, 11857–11887. [Google Scholar] [CrossRef]
- Rachlin, Y.; Baron, D. The secrecy of compressed sensing measurements. In Proceedings of the 46th Annual Allerton Conference on Communication, Control and Computing, Urbana-Champaign, IL, USA, 23–26 September 2008. [Google Scholar]
- Orsdemir, A.; Altun, H.; Sharma, G.; Bocko, M.K. On the security and robustness of encryption via compressed sensing. In Proceedings of the 2008 IEEE Military Communications Conference (MILCOM 2008), San Diego, CA, USA, 16–19 November 2008. [Google Scholar]
- Zhang, A.; Zhou, N.; Gong, L. Color image encryption algorithm based on compressed sensing with Arnold transform. J. Comput. 2013, 8, 2857–2863. [Google Scholar] [CrossRef]
- Endra, R. Compressive sensing-based image encryption with optimized sensing Matrix. In Proceedings of the 2013 IEEE International Conference on Computational Intelligence and Cybernetics (CYBERNETICSCOM), Yogyakarta, Indonesia, 3–4 December 2013. [Google Scholar]
- Zhou, N.; Li, H.; Wang, D.; Pan, S.; Zhou, Z. Image compression and encryption scheme based on 2D compressive sensing and fractional Mellin transform. Opt. Commun. 2015, 343, 10–21. [Google Scholar] [CrossRef]
- George, S.; Pattathil, D. A secure LFSR based random measurement matrix for compressive sensing. Sens. Imaging 2014, 15, 1–29. [Google Scholar] [CrossRef]
- George, S.; Augustine, N.; Pattathil, D. Audio security through compressive sampling and cellular automata. Multimed. Tools Appl. 2015, 74, 10393–10417. [Google Scholar] [CrossRef]
- Nardo, L.; Nepomuceno, E.; Arias-Garcia, J.; Butusov, D. Image encryption using finite-precision error. Chaos Solitons Fractals 2019, 123, 69–78. [Google Scholar] [CrossRef]
- Nepomuceno, E.; Nardo, L.; Arias-Garcia, J.; Butusov, D.; Tutueva, A. Image encryption based on the pseudo-orbits from 1D chaotic map. Chaos 2019, 29, 061101. [Google Scholar] [CrossRef] [PubMed]
- Ponuma, R.; Amutha, R. Compressive sensing based image compression-encryption using Novel 1D-Chaotic map. Multimed. Tools Appl. 2017, 77, 19209–19234. [Google Scholar] [CrossRef]
- Mahmood, A.; Gaze, A. Combined speech compression and encryption using chaotic compressive sensing with large key size. IET Signal Process. 2018, 12, 214–218. [Google Scholar]
- Zhang, L.; Wong, K.; Zhang, Y.; Zhou, J. Bi-level protected compressive sampling. IEEE Trans. Multimedia 2016, 18, 1720–1732. [Google Scholar] [CrossRef]
- Zhang, T.; Li, S.; Ge, R.; Yuan, M.; Ma, Y. A novel 1D hybrid chaotic map-based image compression and encryption using compressed sensing and Fibonacci-Lucas transform. Math. Probl. Eng. 2016, 2016, 1–15. [Google Scholar] [CrossRef]
- Zhou, K.; Fan, J.; Fan, H.; Li, M. Secure image encryption scheme using double random-phase encoding and compressed sensing. Opt. Laser Technol. 2020, 121, 105769. [Google Scholar] [CrossRef]
- Huang, H.; Yang, S. Image Encryption Technique Combining Compressive Sensing with Double Random-Phase Encoding. Math. Probl. Eng. 2018, 2018, 6764052. [Google Scholar] [CrossRef]
- Gan, H.; Xiao, S.; Zhao, Y. A Novel Secure Data Transmission Scheme Using Chaotic Compressed Sensing. IEE Access 2018, 6, 4587–4598. [Google Scholar] [CrossRef]
- Deng, J.; Zhao, S.; Wang, Y. Image compression-encryption scheme combining 2D compressive sensing with discrete fractional random transform. Multimed. Tools Appl. 2017, 76, 10097–10117. [Google Scholar] [CrossRef]
- Wang, X.; Wang, Q.; Zhang, Y. A fast image algorithm based on rows and columns switch. Nonlinear Dyn. 2015, 79, 1141–1149. [Google Scholar] [CrossRef]
- Liu, W.; Sun, K.; Zhu, C. A fast image encryption algorithm based on chaotic map. Opt. Laser Eng. 2016, 84, 26–36. [Google Scholar] [CrossRef]
- Xu, L.; Li, Z.; Li, J.; Hua, W. A novel bit-level image encryption algorithm based on chaotic maps. Opt. Laser Eng. 2016, 78, 17–25. [Google Scholar] [CrossRef]
- Xu, Q.; Sun, K.; Cao, C.; Zhu, C. A fast image encryption algorithm based on compressive sensing and hyper chaotic map. Opt. Laser Eng. 2019, 121, 203–214. [Google Scholar] [CrossRef]

| 0 | 0 | 0 | 0 | |
| 1 | 0 | 0 | 1 | |
| 2 | 0 | 1 | 0 | |
| 3 | 0 | 1 | 1 | |
| 4 | 1 | 0 | 0 | |
| 5 | 1 | 0 | 1 | |
| 6 | 1 | 1 | 0 | |
| 7 | 1 | 1 | 1 | |
| 8 | 0 | 0 | 0 |
| Entropy | Compression Ratio | |||||||
|---|---|---|---|---|---|---|---|---|
| 0.3 | 0.4 | 0.5 | 0.6 | 0.7 | 0.8 | 0.9 | 1 | |
| Cipher image | 7.9903 | 7.9934 | 7.9939 | 7.9957 | 7.9958 | 7.9963 | 7.9974 | 7.9968 |
| Algorithm | Horizontal Direction | Vertical Direction | Diagonal Direction |
|---|---|---|---|
| Proposed algorithm | −0.0065 | 0.0073 | 0.0042 |
| Ref. [12] | 0.0586 | −0.0021 | 0.0269 |
| Ref. [24] | 0.0597 | −0.0766 | 0.0083 |
| SSIM | Compression Ratio | |||||||
|---|---|---|---|---|---|---|---|---|
| 0.3 | 0.4 | 0.5 | 0.6 | 0.7 | 0.8 | 0.9 | 1 | |
| Reconstructed image | 0.4302 | 0.6129 | 0.7349 | 0.8388 | 0.9033 | 0.9424 | 0.9645 | 0.9801 |
| Cipher image | 0.0028 | 0.0032 | 0.0045 | 0.0047 | 0.0065 | 0.0071 | 0.0076 | 0.0085 |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, J.; Guo, S.; Song, X.; Xie, Y.; Wang, E. Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix. Entropy 2020, 22, 76. https://doi.org/10.3390/e22010076
Yu J, Guo S, Song X, Xie Y, Wang E. Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix. Entropy. 2020; 22(1):76. https://doi.org/10.3390/e22010076
Chicago/Turabian StyleYu, Jiayin, Shiyu Guo, Xiaomeng Song, Yaqin Xie, and Erfu Wang. 2020. "Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix" Entropy 22, no. 1: 76. https://doi.org/10.3390/e22010076
APA StyleYu, J., Guo, S., Song, X., Xie, Y., & Wang, E. (2020). Image Parallel Encryption Technology Based on Sequence Generator and Chaotic Measurement Matrix. Entropy, 22(1), 76. https://doi.org/10.3390/e22010076






