Abstract
To reduce the consumption of receiving devices, a number of devices at the receiving end undergo low-element treatment (the number of devices at the receiving end is less than that at the transmitting ends). The underdetermined blind-source separation system is a classic low-element model at the receiving end. Blind signal extraction in an underdetermined system remains an ill-posed problem, as it is difficult to extract all the source signals. To realize fewer devices at the receiving end without information loss, this paper proposes an image restoration method for underdetermined blind-source separation based on an out-of-order elimination algorithm. Firstly, a chaotic system is used to perform hidden transmission of source signals, where the source signals can hardly be observed and confidentiality is guaranteed. Secondly, empirical mode decomposition is used to decompose and complement the missing observed signals, and the fast independent component analysis (FastICA) algorithm is used to obtain part of the source signals. Finally, all the source signals are successfully separated using the out-of-order elimination algorithm and the FastICA algorithm. The results show that the performance of the underdetermined blind separation algorithm is related to the configuration of the transceiver antenna. When the signal is 3 × 4 antenna configuration, the algorithm in this paper is superior to the comparison algorithm in signal recovery, and its separation performance is better for a lower degree of missing array elements. The end result is that the algorithms discussed in this paper can effectively and completely extract all the source signals.
1. Introduction
To reduce professional equipment installation for intelligent communication, realize better information transmission with limited resources, and receive a large amount of source information using limited sensors at the receiving end, use of a low-element model at the receiving ends is becoming popular in the field of communication [1,2,3]. Application of low-element treatment for sensors at the receiving ends is highly suitable for areas involving information transmission such as biomedical engineering, seismic monitoring, signal enhancement, and radar and machinery [4,5,6,7,8,9,10]. As the information detected by sensors at each receiving end is the superposition of some source information, independent sources are required to obtain essential information [11]. Therefore, certain auxiliary information processing methods are required to handle the collected information and separate each desired source signal.
Blind-source separation (BSS) involves separating the best estimation of the hidden source signals from certain observed signals (at the receiving end) when the theoretical model of the signal and the source signal are unknown [12,13,14]. Specifically, underdetermined blind-source separation is a low-element model of sensors at the receiving end for signal processing, which remains an ill-posed and abstruse problem for information transmission [15,16,17,18]. At present, there are two types of solutions to address this issue. The first type is based on the statistical properties of source signals, such as uncorrelated autoregressive (AR) model signals [19], nonnegative tensor factorization [20], and beamforming based on a minimum mean square error [21]. The second type is based on the analytical method of signal sparsity, which mainly includes chaotic matrix estimation and source signal restoration methods. In general, a transform-domain sparse representation can yield better source signal estimation [22]. Common time-frequency analytical techniques include Cohen’s class time-frequency distributions [23], short-time Fourier transform (STFT) [24], and empirical mode decomposition [25]. As blind-source separation aims to address the problems of nonlinear signals and the time-frequency analysis uses the non-stationarity of signals, this paper also begins by discussing time-frequency analytical techniques for signal separation.
Currently, although progress has been made in underdetermined blind-source separation based on time-frequency analysis, common methods used still have certain limitations. For example, although STFT can successfully separate the source information with underdetermined blind-source separation, the window function used obscures the time-frequency (TF) representation and is confined by the Heisenberg uncertainty principle, which further restricts the sparsity of a signal [26,27,28]. When a wavelet transform performs underdetermined blind-source separation, various wavelet bases and decomposition layers create a difference between the vortex and approximate signals, thus, influencing the separation of signals and making it difficult to select the wavelet base and decomposition layer number [29,30,31,32,33]. Empirical mode decomposition can cause modal aliasing when dealing with underdetermined blind-source separation, making the separation of source signals difficult [34,35].
Previous transmission carriers mainly consisted of voice information, and information transmission was performed in the forms of text, voice, and images [36]. Generally, images are considered more suitable for modern communication because they are intuitive, capable of carrying a large amount of information, and conducive to observation and summarization [37]. Existing studies on image separation methods based on underdetermined blind-source separation are not sufficient. Studies on low-element receiving ends of images will help address the issue of increasing communication demands.
To resolve these problems, this paper proposes low-element image restoration based on an out-of-order elimination algorithm. The contributions of this study are as follows: first, chaotic hiding information is used in sensors with low-element receiving ends to protect information at the receiving end. Second, to solve the low-element problem at the receiving end and to prevent modal aliasing, this paper proposes empirical mode decomposition to construct multiple components to increase information through the decomposed simple component signals and suppress modal aliasing using the first intrinsic mode function. Finally, as all the source signals cannot be simultaneously extracted by underdetermined blind-source separation, this paper proposes an out-of-order elimination algorithm to reduce the extracted image information. Next, the mixed information can be used for blind extraction to eliminate repeated blind extractions and ensure complete information extraction.
The rest of the paper is organized as follows: Section 2 introduces the principles of 3D digital chaotic systems and empirical mode decomposition, as well as the theoretical models of underdetermined blind-source separation. Section 3 discusses the development of an underdetermined blind-source separation method based on low-element images and introduces the design scheme and model for constructing multi-component complement system and an out-of-order elimination algorithm using empirical mode decomposition in detail. Section 4 shows the overall flow chart and performance evaluation methods. In Section 5, through simulation, the effect of chaos on information hiding and the approximation effect of blind extraction of source information by the proposed low-element algorithm are analyzed. Section 6 summarizes the algorithms used in this paper.
2. Basic Theoretical Method
2.1. Underdeterminate Blind Signal Separation
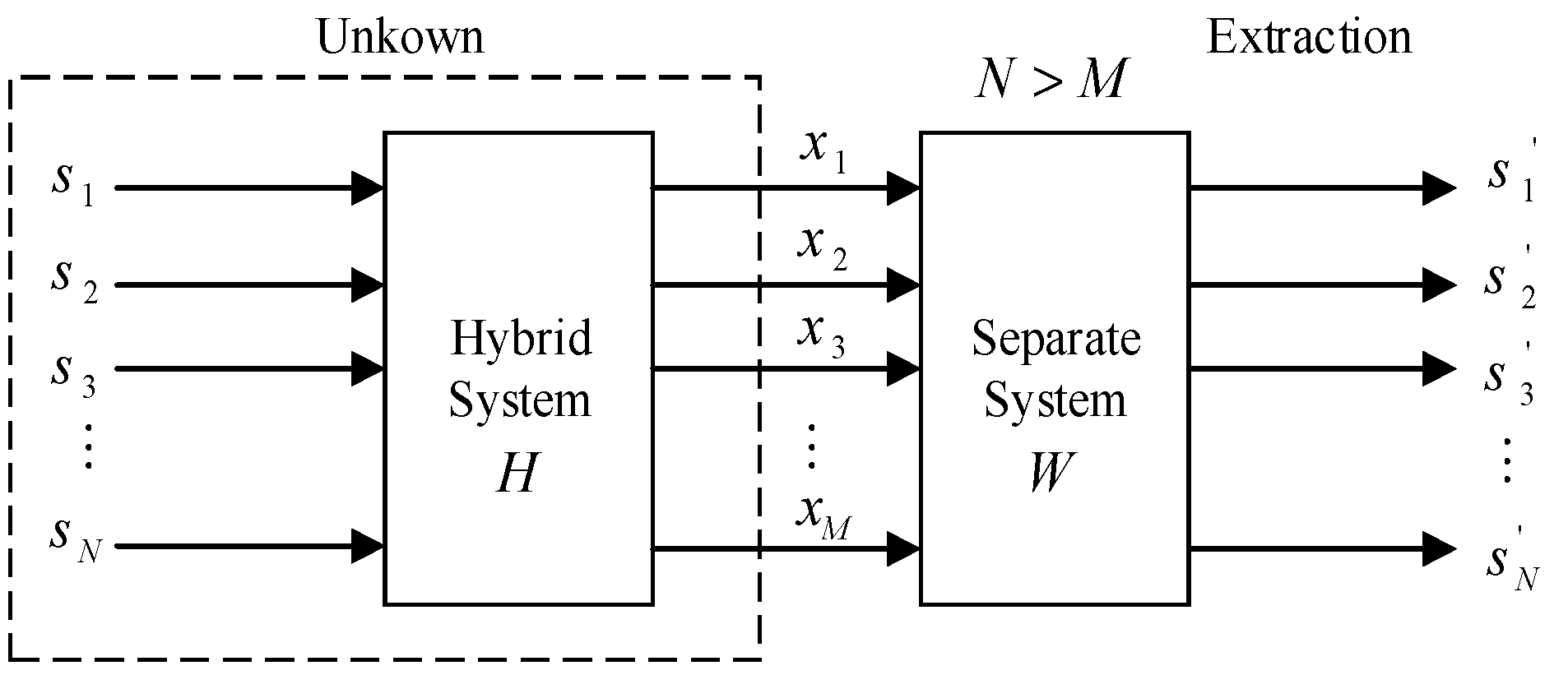
Underdetermined state blind extraction mathematical model shown in Figure 1. Here “blind” means that the transmitter signal is unobservable and the characteristics of the hybrid system are unknown [38,39]. Among them, the independent component analysis (ICA) technology can use the statistical conditions such as independent independence of transmitter signals statistics to reproduce an unobservable transmitter signal from the receiving signals . In the independent component analysis algorithm, fast independent component analysis FastICA is widely used in blind-source separation because of its fast convergence and high stability [40]. Therefore, in the blind-source separation and blind extraction, the FastICA algorithm in independent component analysis will be used in this paper.
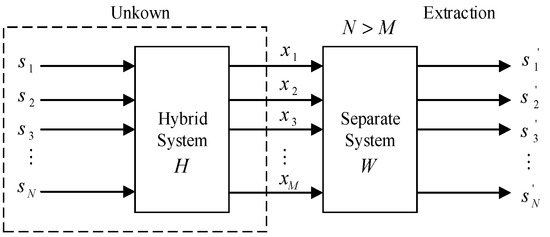
Figure 1.
Underdetermined state blind extraction mathematical model.
Set be the m-dimensional zero-mean random receiving signals. It is n linear mixture of an unknown zero mean independent transmitter semaphore . This linear mixed model can be expressed as:
Among, is a m × n-order full-range transmitter signal mixing matrix; is the n-dimensional column vector of the mixing matrix. The Equation (1) is in the form of a matrix:
In the equation: each mixed signal is a random signal, and each receiving is a sample of the random signal when time is .
In mixed matrix H and transmitter signal s unknown circumstances, only with the sensor detects the mixed receiving signal x separate transmitter signals is most likely true s, can build a separation matrix . When s gets the best estimation of r dimension transmitter signal through the separation matrix transform, it is output column vector . The solution (or the solution mix model) of this problem can be expressed as:
In the equation: G is a global transmission matrix. Under normal circumstances, when G = I (I is an -order unit matrix), and , thus achieving transmitter signal separation. Where, N is the number of transmitter signals and M is the number of receiving signals. Among them, the number of mixed receiving signals is less than the number of transmitter signals, and an underdetermined mathematical model is obtained.
2.2. Chaotic System
Chaotic hiding information ensures secure communication. As low-element underdetermined blind-source separation is problematic, to ensure collection of secured information at the receiving end, this paper uses digital chaos to hide and confidentially transmit the transmitter information [41,42]. The kinetic equation of the chaotic system [43] used in chaotic hiding techniques is shown in (4):
where . When the initial values are:
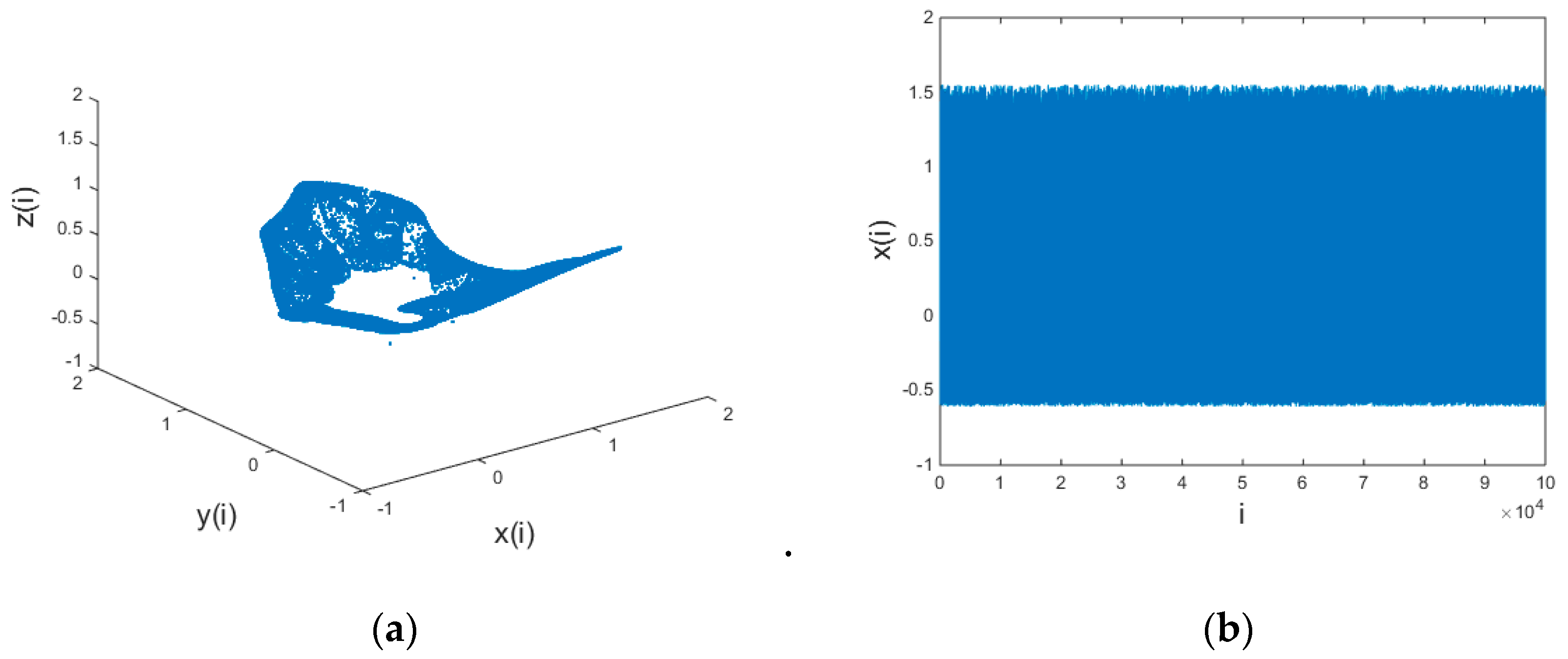
it can iterate into a chaotic state. The chaotic three-dimensional (3D) diagram and the time-domain response diagram of variable x are shown in Figure 2.
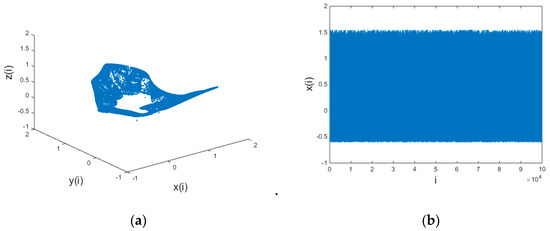
Figure 2.
A 3D discrete chaotic schematic: (a) three-dimensional view of the chaotic system and (b) time domain response graph of x variable of the chaotic system.
The characteristic analysis of a chaotic system [44] reveals that it has a complex structure and irregular dynamic behavior. It is proven in [43] that a chaotic system possesses a good image encryption effect. Therefore, a 3D hyper-chaotic system works well for chaotic hiding information transmission.
2.3. Empirical Mode Decomposition
Empirical Mode Decomposition (Empirical Mode Decomposition—EMD) is the core algorithm of the Hilbert–Huang Transform (HHT) [45]. The EMD algorithm can handle complex and difficult-to-decompose non-stationary signals and decompose them into simple combinations of single-component signals, is a set of better-performing Intrinsic Mode Functions (IMF). The IMF must satisfy the following two conditions [46]:
- The number of signal zero crossings is equal to or at most equal to the number of extreme points of the IMF;
- The mean value of the upper envelope constructed by the local minimum value and the local maximum value is zero.
The specific steps of the EMD algorithm [47,48] are: First, find all the extreme points of the original data sequence , and use the cubic spline curve to fit the upper and lower extreme points, and calculate the average of the upper and lower envelopes. Then, subtract the mean from to determine if the difference is IMF, and if not, repeat the above steps until the criterion is satisfied. The component of signal is obtained after decomposition and the remaining terms :
According to the principle of EMD decomposition, the characteristic scale of the signal can be embodied in each IMF component, and the IMF component also represents the internal modal characteristics of the signal. At the same time, it is found that the most complete signal component of the signal is the first intrinsic mode function component after decomposition.
3. Building the Algorithm Model
3.1. Construct Multi-Component Complementary Method
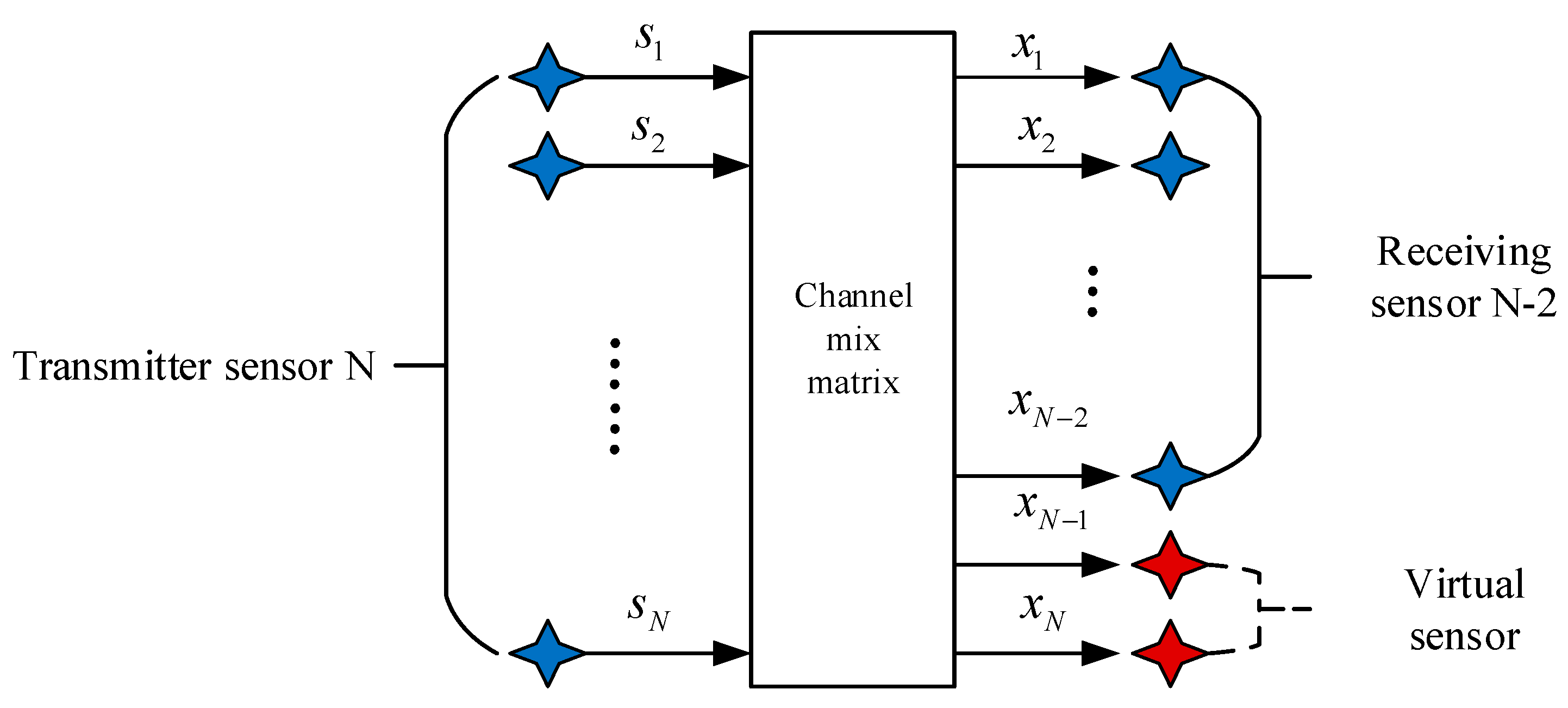
The model of the multi-component complementary method is shown in Figure 3. In this model diagram, it is assumed that the number of receiving sensors is less than the number of transmitting sensors. It can be extended to the model that lacks multiple receiving sensors by missing two receiving sensors in this model. In this model, two virtual receiving sensors will be added to make the underdetermined blind-source separation system positive, which is in Figure 1. The supplementary two-way virtual receiving sensor equation is:
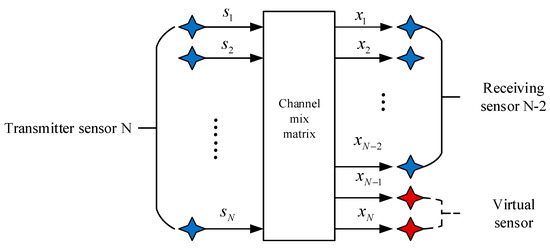
Figure 3.
A virtual receiving array model with multicomponent complement method.
Firstly, the first virtual signal of the receiving sensor is constructed, which is the obtained by the EMD of the receiving end ; Secondly, the virtual signal of the second receiving sensor built is obtained by the odd and even combination of and . In the underdetermined hybrid system, a new set of received signals can be combined through the above two Equations (6) and (7) to be converted into a positive definite system.
3.2. Out-of-Order Elimination Algorithm
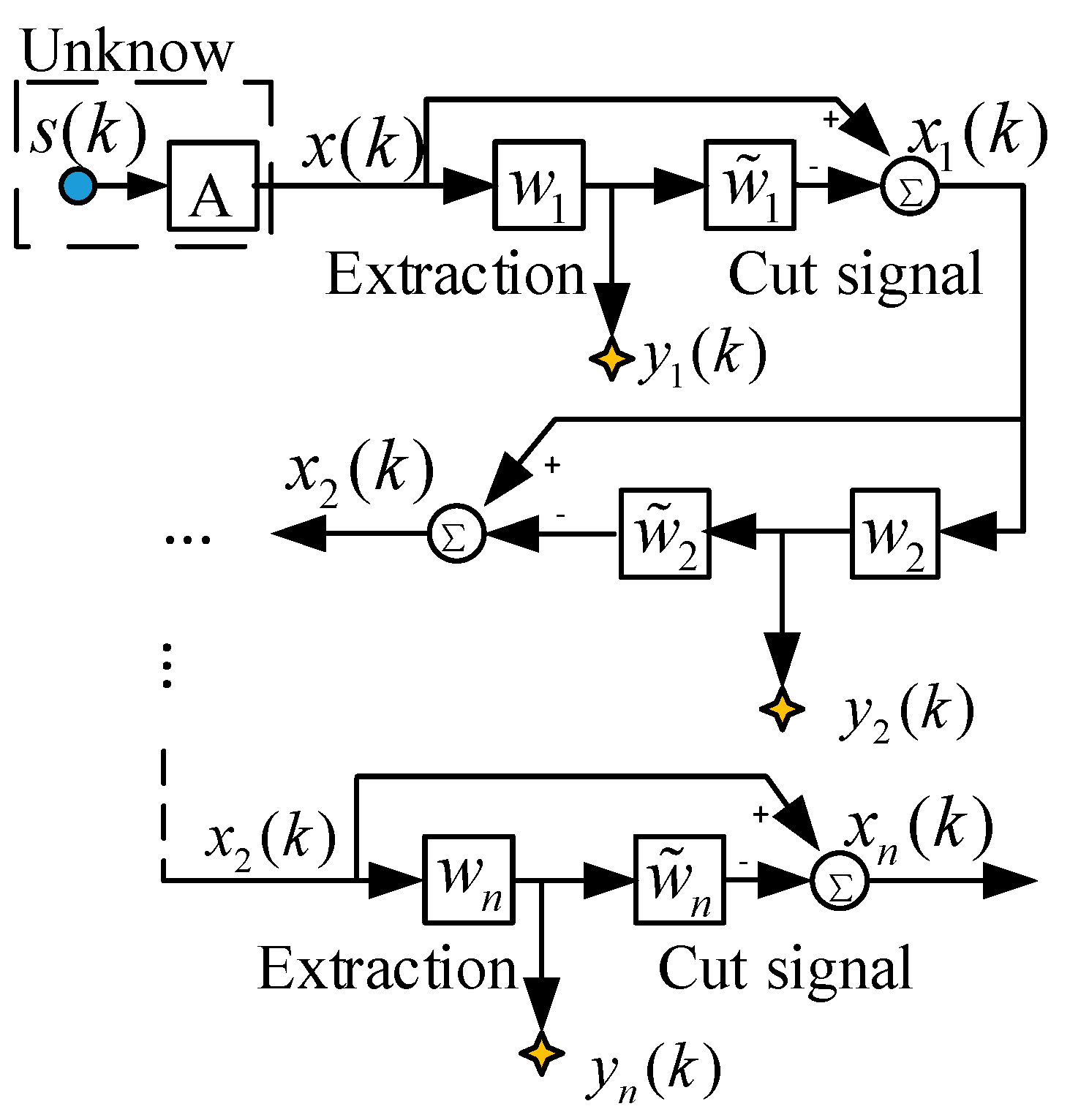
The construction of the above multi-component complementary method transforms the underdetermined blind-source separation into a positive definite model that can be extracted blindly. However, considering that only part of the signal may be obtained in one extraction, this paper proposes an algorithm of out-of-order elimination algorithm. The function of this algorithm is to subtract the successfully extracted signal from the mixed received sensor signal and use the remaining mixed signal information for more efficient blind extraction. The model of the algorithm is shown in Figure 4.
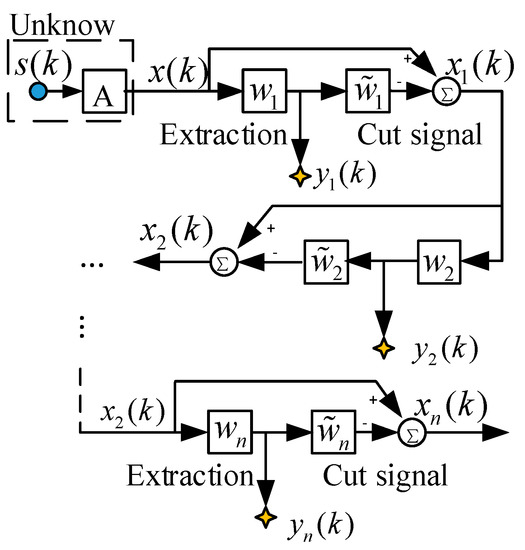
Figure 4.
Implementation of extraction and reduction.
The algorithm adopts a hierarchical extraction structure and utilizes two different types of processing modules that are connected in a cascaded manner. The first layer is an extraction module, which is used for blind extraction of mixed signals by linear feature extraction. The second layer is the elimination module, which applies the principle of minimum absolute deviation and subtracts the signal successfully extracted by the first layer from the received signal.
The j-th extraction module and the elimination module respectively extract the source signal from the input end and subtract the newly extracted source signal. The first subtraction module excludes the newly extracted transmitter signal from the input side mixed signal, and then gives the remaining subtracted mixed signal to the next (j + 1) module for a new round of extraction and elimination.
We will assume that the first source signal is successfully extracted, and then the successfully extracted information is subtracted from the received mixed signal. The process of extracting and subtracting the remaining mixed signals can be used recursively until all the transmitter signals are extracted and terminated when no extraction signal is available. In this process, the following equation can be obtained:
where can be optimized by minimizing the cost (energy) function:
where is the target function, and . Intuitively, such a target function can be regarded as an energy function. When of the extracted source signal is subtracted in the mixed signal of the source, the energy function should reach the minimum value.
4. Overall Flowchart and Performance Analysis Indicators
4.1. Overall Flow Chart
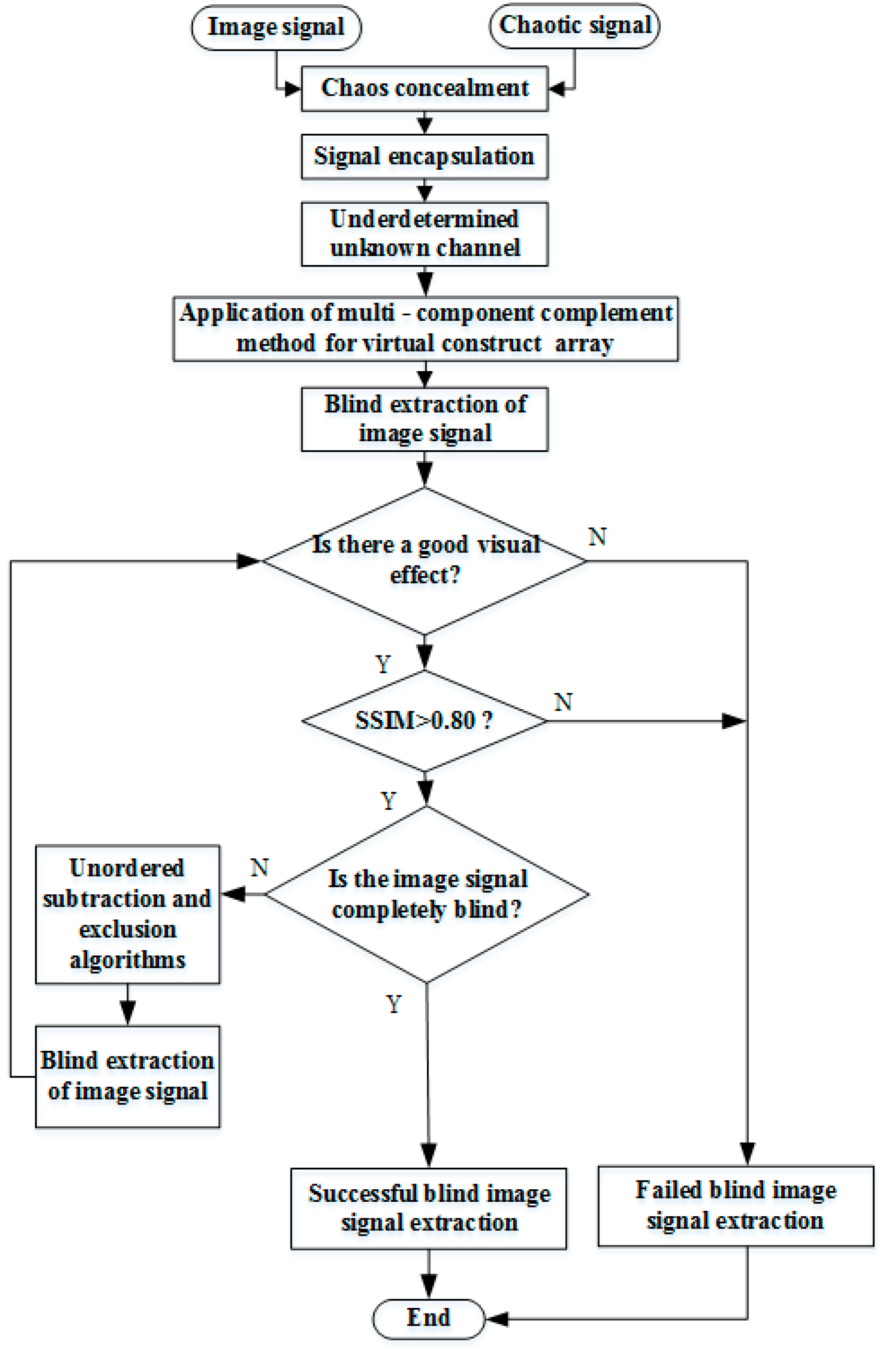
Figure 5 depicts an overall flow chart of low-element image restoration based on the out-of-order elimination algorithm, which describes the complete algorithmic process. First, to ensure that the observed signals at the receiving end are kept confidential, the x-component of the chaotic signal is used as the transmitter signal to transmit alongside other source information. Second, as low-element problems are encountered at the receiving end, the EMD algorithm is used to decompose the virtual signals for constructing multiple components to convert the low-element sensors at the receiving end into a positive definite state, to realize effective blind extraction of the mixed signals. Finally, as it is difficult to simultaneously extract all the transmitter signals of the low-element sensors at the receiving end, the proposed out-of-order elimination algorithm is used to accurately and quickly extract the non-extracted signals.
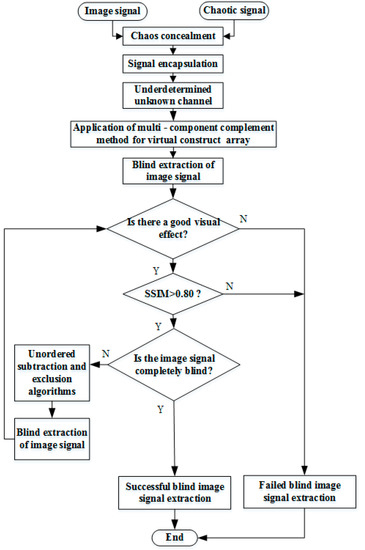
Figure 5.
Overall flow chart.
4.2. Performance Analysis Index
In this study, to better see the encryption effect of chaos on digital images, the encrypted image was analyzed according to the information entropy against statistical attack ability [49]. The information entropy describes the information uncertainty. For higher information uncertainty, more information is needed for factual clarification. Therefore, the larger the information entropy of the encrypted image, the more secure the corresponding encryption algorithm. The following equation was used to evaluate the information entropy of the original and encrypted images:
where represents the probability at and 2n is the number of image pixel values. For a grayscale image, there are 256 gray levels, and the ideal information entropy is close to 8. If the information entropy of an encrypted image is closer to 8, the corresponding encryption method is more secure, and the ability to resist entropy attacks is stronger.
Generally, both qualitative and quantitative performance evaluations of BSSor blind extraction problem-solving algorithms can be performed. As the current study targets blind extraction of image information, a qualitative evaluation can be conducted using subjective visual analysis of the human eye. Primarily, the image information before and after the BSS or blind extraction is compared and analyzed to yield an intuitive discrimination. Quantitative evaluation is performed using performance indicators such as the structural similarity (SSIM) [50], mean-square error (MSE), and peak signal-to-noise ratio (PSNR).
SSIM: From the perspective of image composition, structural information is defined as being independent of brightness and contrast, instead reflecting the properties of the object structure in the scene. The distortion is modeled as a combination of three different factors: brightness, contrast, and structure. The definition is:
In the equation, x is the estimated value of the image information after blind separation or blind extraction, and y is the true value of the image information in the source signal. and are their mean and variance, respectively, is their covariance. are two constants that are used to maintain stability. L is the dynamic range of the pixel value. . When the two images are exactly the same, the SSIM value is equal to one. In this paper, when the SSIM approaches 1, it can be determined that the blind extracted image has high similarity to the source image information, which is an estimate of the source image information.
MSE: The MSE is defined as:
where, represent the images before and after encryption, respectively, and M and N are the image height and width, respectively. A smaller MSE for an evaluation image restoration indicates higher-accuracy image restoration.
PSNR: The PSNR is essentially identical to the MSE and is defined as:
Use of the PSNR is an objective image restoration evaluation method. In general, a higher PSNR value corresponds to less distortion.
In addition, when the global transmission matrix in Equation (3) is the generalized permutation matrix [51], that is, ( is the permutation matrix, is the non-singular diagonal scale matrix). The source signal can be obtained from the signal , which is . Then, the estimated performance of is optimal, which means that the global matrix can also be used as a basis for the separation performance. When the global matrix is the dominant matrix, the separation performance is good. The dominant matrix is that for every row and column in the matrix, only one element approaches 1, while the rest of the elements approach 0.
5. Simulation Results and Performance Evaluation
5.1. Chaotic Hiding Observation Signals
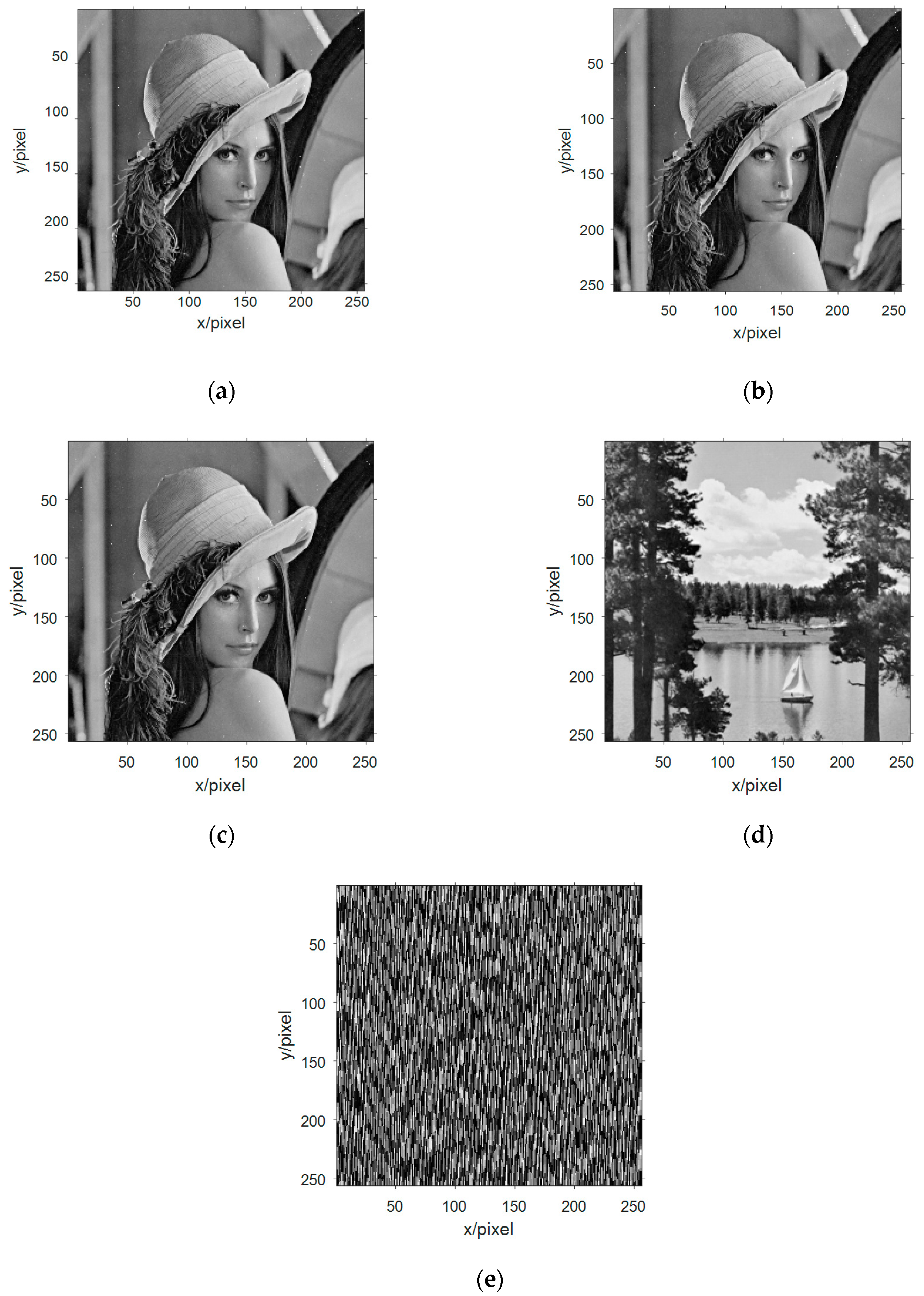
Selecting the grayscale image information from the four standard test image libraries is shown in Figure 6a–d, and they are converted from a two-dimensional array data into a one-dimensional array of data, and then binarize one-dimensional data. The x-components in the Chen chaotic system are selected and these five signals are packaged as an n-source signal vector.

Figure 6.
The image information of the source signal: (a) image information of the first source; (b) image information of the second source; (c) image information of the third source; and (d) image information of the fourth source.
For the unknown channel of the analog channel, the system randomly generates a mixed receiving matrix and the encapsulated data to be aliased to obtain three mixed receiving signals. The randomly generated mixing matrix H in this system is:
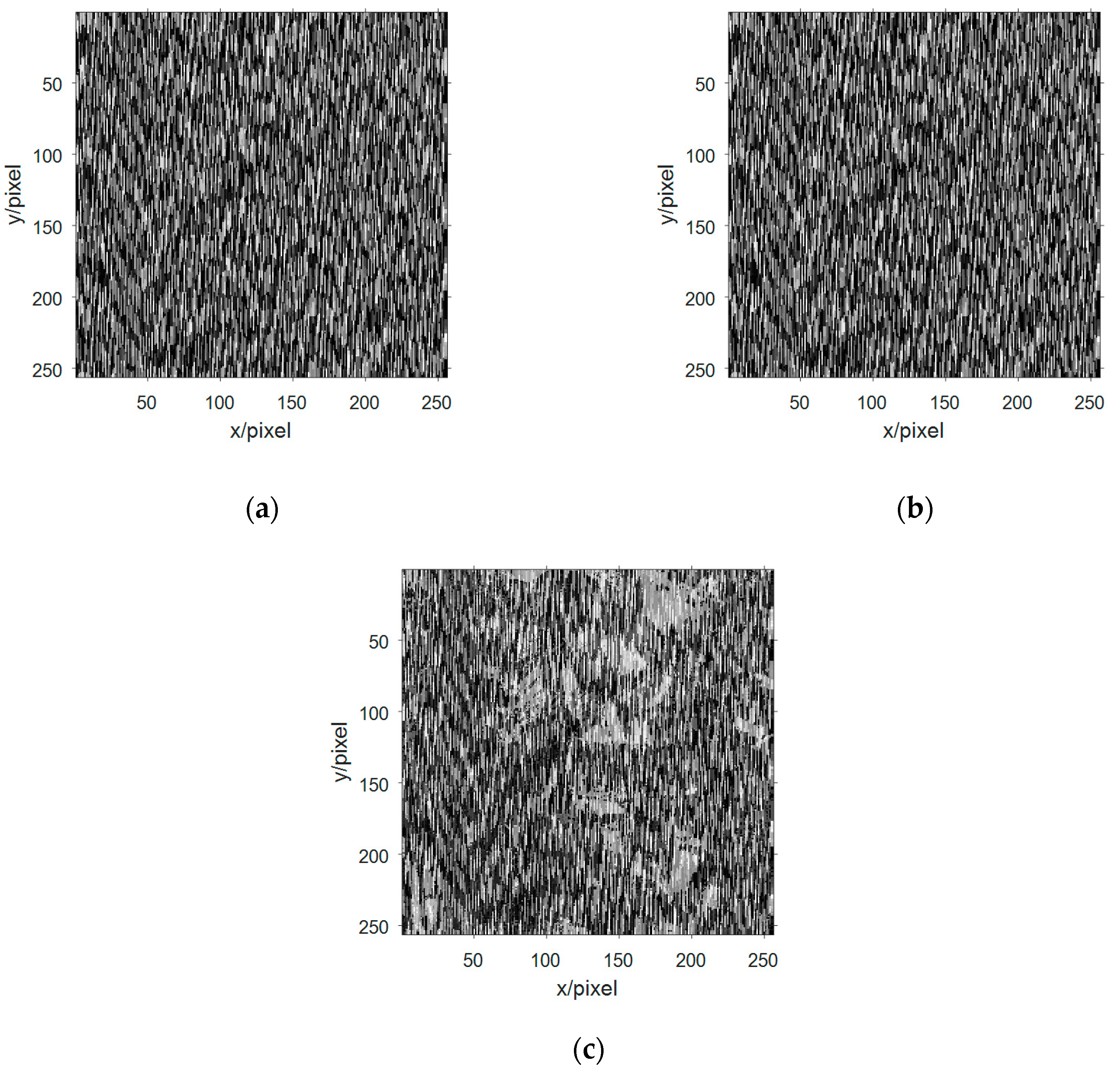
Decimalizing the data and performing a two-dimensional arraying to obtain three-channel image information as shown in Figure 7a–c. Observing the three-way image information of the mixed receiving signal, the image information is disorderly and disorderly, and the information in the image cannot be recognized. The content of the image information is better obscured by the signals of the 3D chaotic motion system and can no longer be recognized by human eyes.
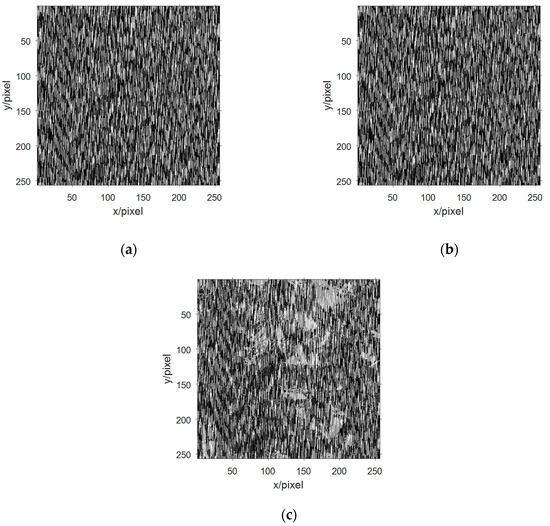
Figure 7.
The image information of the observed signal in the multicomponent complement model: (a) image information of the first observation signal; (b) image information of the second observation signal; and (c) image information of the third observation signal.
5.2. Security Analysis of the Observed Signals at the Receiving End
5.2.1. Entropy
For a grayscale image, the closer the information entropy of the encrypted image to 8, the more secure the corresponding encryption method, and the stronger the ability to resist entropy attacks. In this study, 3D chaos was selected for entropy analysis of the concealed and encrypted images, as detailed in Table 1.

Table 1.
Image entropy analysis after chaotic hiding.
The four images were encrypted through chaotic masking (four image data plus one chaotic data can be understood as five channels of signal transmission) and underdetermined blind source analysis channels to obtain three-way hiding images. From Table 1, the five signals are encrypted by chaotic hiding and underdetermined blind-source separation channels to obtain three-way encrypted images. Table 1 shows that that when two types of 3D hyper-chaotic systems (Lorenz and 3D chaos) are used for chaotic hiding transmission of information from four source signals (Lena, Cameraman, Lake, and Peppers), the information entropy values of the three mixed receiving signals received by the low-element receiving ends are close to 8. Therefore, the two chaotic signals can provide a good encryption effect and have the ability to resist entropy attacks. The 3D chaotic system is selected for transmission of chaotic hiding information in this study, as the entropy value obtained by it is better than that of Lorenz chaos.
5.2.2. Statistical Analysis
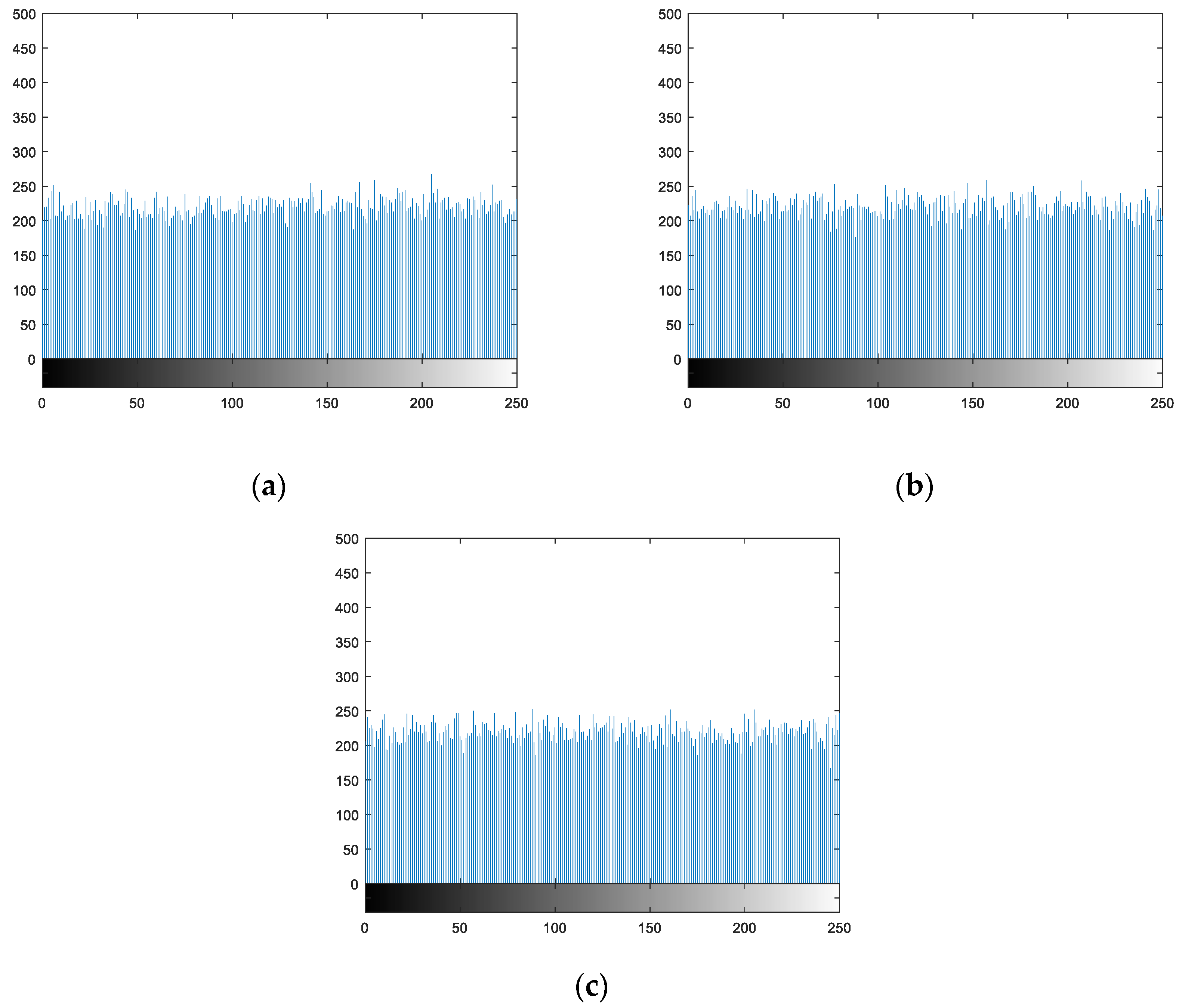
For Lena, Cameraman, Lake, and Peppers four gray image hiding operations, draw a clear image of the statistics histogram, respectively, and the corresponding hiding statistical histogram of the image. The result is shown in Figure 8, you can see from the picture clear image pixel gray value of occurrence probability is very uneven, but after the hiding image of each pixel gray value probability is very uniform, shows that the hiding image pixel gray value taken the probability of all possible values tend to be equal. Therefore, this algorithm can effectively resist the attack of statistical analysis.
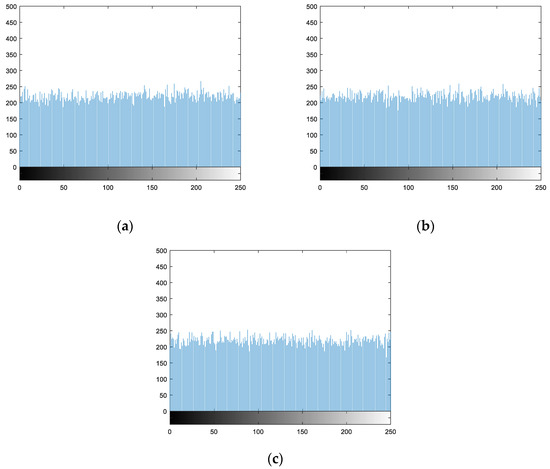
Figure 8.
Statistical histograms of hiding images. (a)–(c) is the statistical histogram of the hiding image in Figure 7.
5.2.3. Differential Attack Analysis
The ability of an image hiding to resist differential attacks can be analyzed with the two indicators: Number of Pixels Change Rate (NPCR) and the Unified Average Changing Intensity (UACI) [52]. The calculation equation for NPCR and UACI are defined as follows:
where is the normal hiding image and is the hiding image when the value of one pixel in the original image is changed, is the size of the hiding image. NPCR and UACI under the experimental data are shown in Table 2, indicating that the hiding scheme proposed in this paper can effectively resist differential attacks.

Table 2.
Average Number of Pixels Change Rate (NPCR) and the Unified Average Changing Intensity (UACI) values.
5.3. Blind Extraction of Underdetermined Blind-Source Separation
With the above underdetermined blind-source separation, three mixed receiving images are obtained. To separate the mixed receiving images under chaotic hiding, the study applies the method of constructing multi-component complementation discussed in Section 3. The first received signal is selected, and the first intrinsic mode component obtained after the EMD decomposition is used as the fourth received signal. This intrinsic mode function is compensated with the first received signal to obtain the fifth received signal, thereby forming a new received signal vector.
The received signal vector is processed by FastICA algorithm to obtain the estimated signal, and the estimated signal value is decimalized and two-dimensional arrayed. The image information obtained after blind separations are shown in Figure 9.
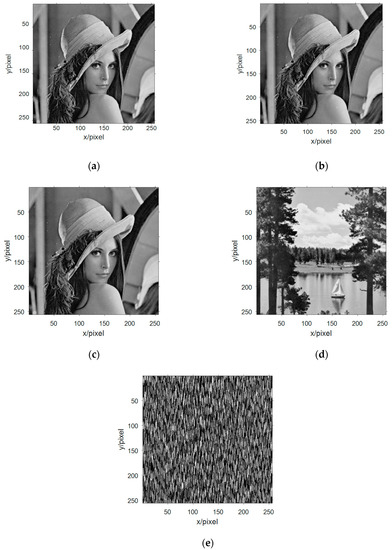
Figure 9.
Multi-component complement method first extracts signal image information. (a)–(c) three effective Lena graphs were extracted blind at the first blind extraction; (d) the effective Lake information was extracted blind at the first blind extraction; and (e) information of no interest.
With human subjective visual judgment, it was found that there are four images information similar to the image information in Figure 6, which can be calculated by similarity with similar image information in Figure 6, respectively. Figure 9a and Figure 6a The SSIM is 0.9869, the SSIM in Figure 9b and Figure 6a is 0.9869, the SSIM in Figure 9c and Figure 6a is 0.9869, Figure 9d and Figure 6d SSIM is 0.9990. Based on the evaluation of SSIM, it can be judged that Figure 6a,d have been successfully evaluated. Through calculation, it can be seen that Figure 9a–c are the same image, so the simulation experiment extracts three different image information. The global transmission matrix in this simulation is:
Observing the matrix, the dominance is 3, corresponding to the three different image information extracted in the simulation. Substituting the values of Figure 9a,d into Equation (11) in turn yields two values. Respectively and .
In Equation (10), the original mixed signal value is successively subtracted from the value of the extracted image information in the original mixed receiving signal, and then a new set of mixed signal values can be obtained, and the new mixed signal matrix is subjected to FastICA algorithm blind-source separation. Three-way estimated signal values are obtained, and decimal conversion is performed on it, and the image information shown in Figure 10 is two-dimensionalized.
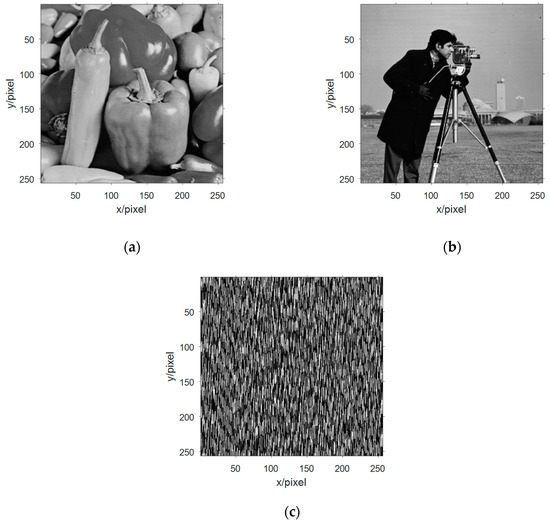
Figure 10.
Image information of the second extraction of signal in multicomponent complement method. (a) The second blind extraction of the remaining information of valid Peppers image information; (b) The second blind extraction of the remaining information of valid Cameraman image information; and (c) Information of no interest.
By comparing the mixed receiving of Figure 10 with the figure, it is found that Figure 10a is an estimate of Figure 6c and Figure 10b is an estimate of Figure 6b. Respectively, the SSIM between them was 0.9943 and 0.9930. The second blind extraction of the multi-component complementary method has effectively extracted the remaining image information.
Shannon’s theory points out that the channel capacity of additive Gaussian white noise channel is the lower limit, which exists widely in all resistive components and has wide spectrum characteristics similar to the chaotic masking signal in this paper. Therefore, in order to verify the effectiveness of the experiment, white Gaussian noise with different intensity is added to the channel to verify the image hiding method of BSS. The results are presented in Table 3.

Table 3.
Relationship between noise intensity and correlation coefficient.
As apparent from the table, the noise at the source has little effect on the image hiding, and the effect of the image hiding was also reduced as the noise intensity changed.
The results show that the performance of the underdetermined blind separation algorithm is related to the configuration of the transceiver antenna. We defined the missing degree as:
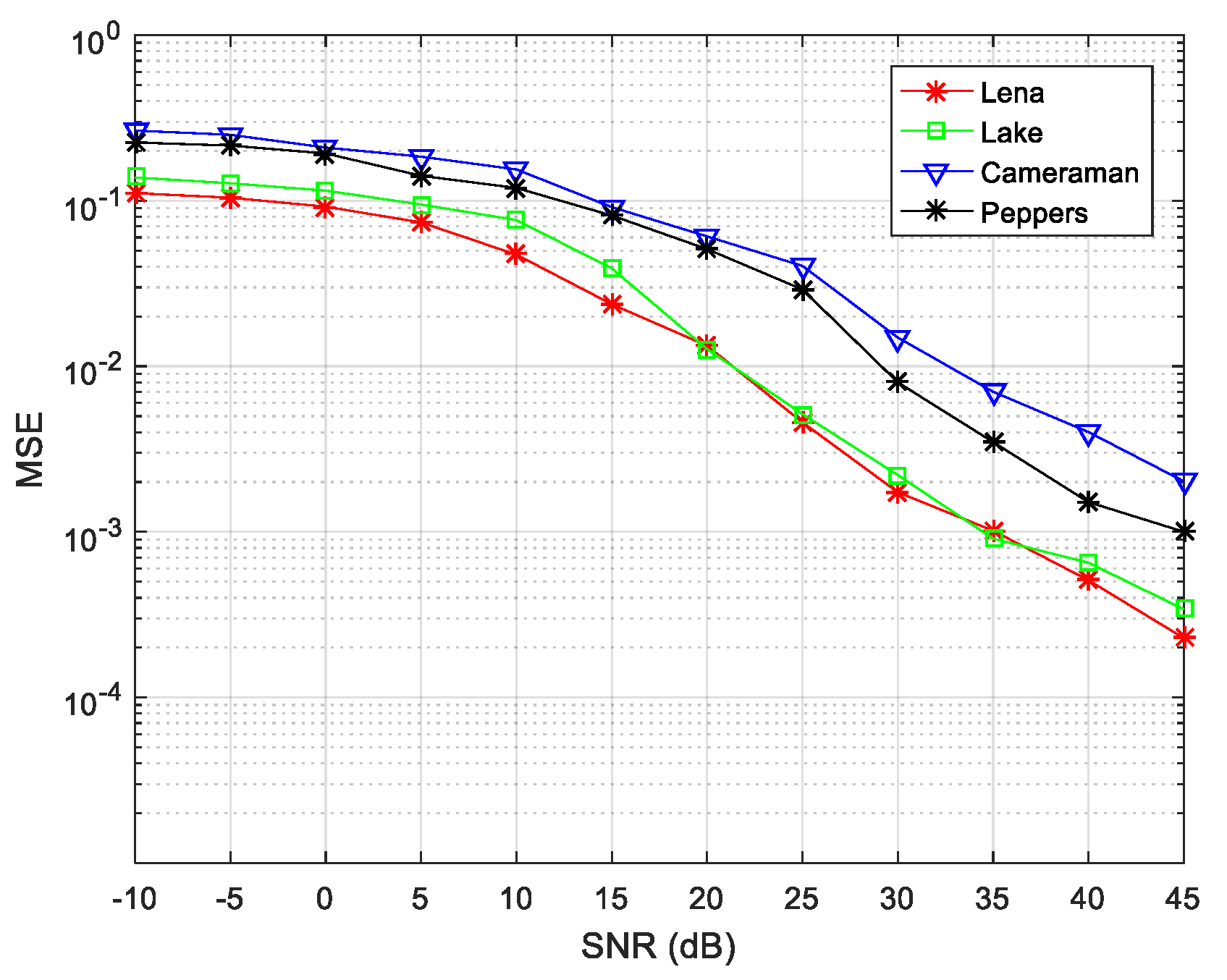
where, N is the number of transmitter signals and M is the number of mixed receiving signals. The above results indicate that the transmitter signal of the simulation experiment was basically restored in the absence of noise. As the above simulation was performed under noiseless conditions, the algorithm performance was examined when the SNR value was changed several times for transmitter and receiver signals of . The line graph of Figure 11 reveals that the hiding images were all successfully extracted, and the image effect extracted by the first BSS (for Lena and Lake) is better than the second BSS (Cameraman and Peppers).
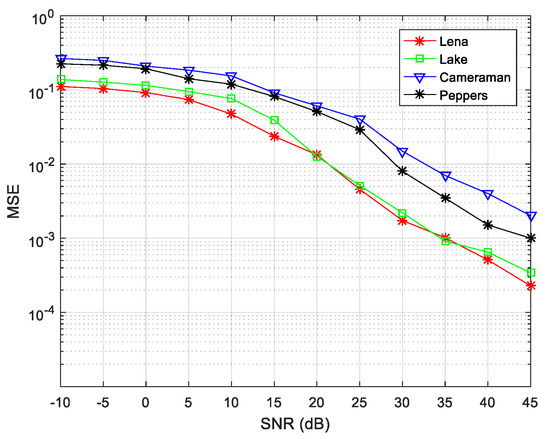
Figure 11.
Decryption effects of 5 × 3 signals of source and receiver at different signal-to-noise ratio (SNRs).
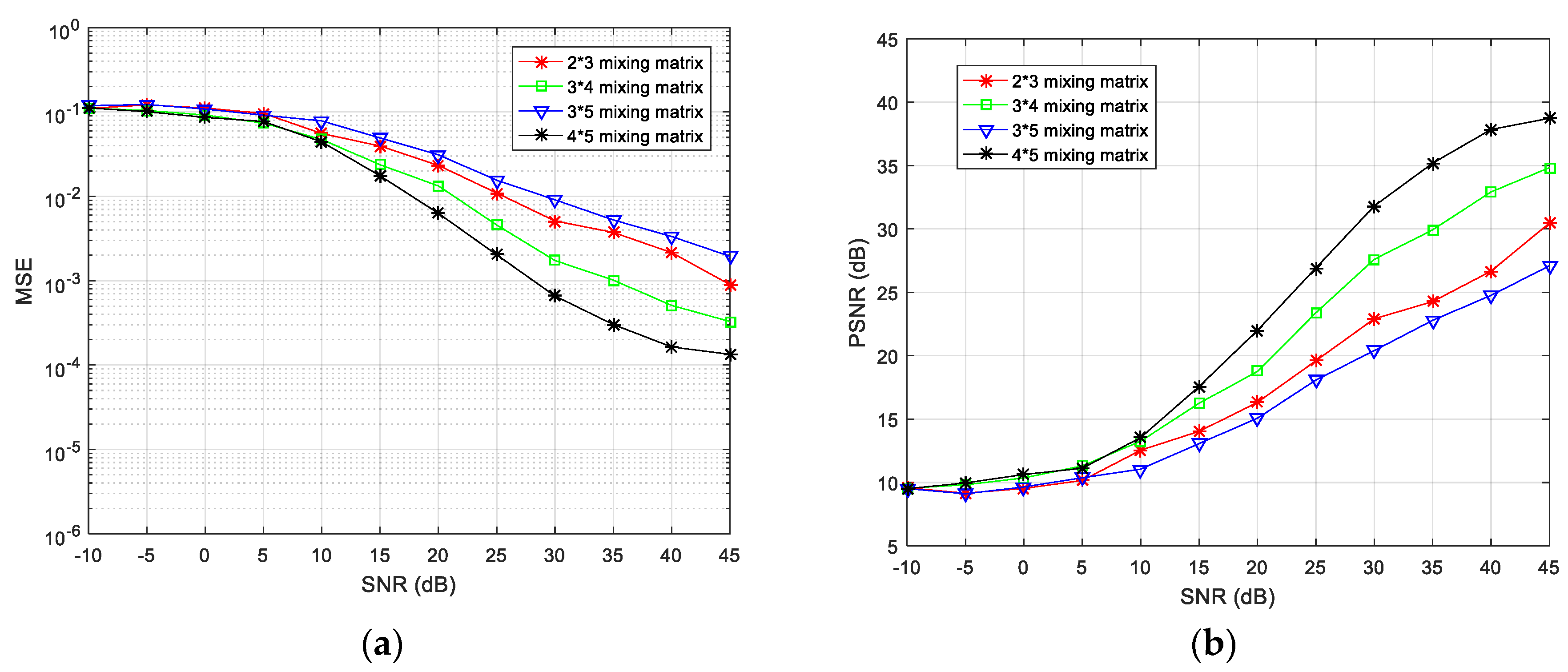
Finally, to evaluate the overall performance of the proposed algorithm, the number of transmitter and receiver sensors was changed to and simulation experiments were performed. The algorithm encryption matrix was randomly generated and the simulation results at different SNRs are shown in Figure 12.
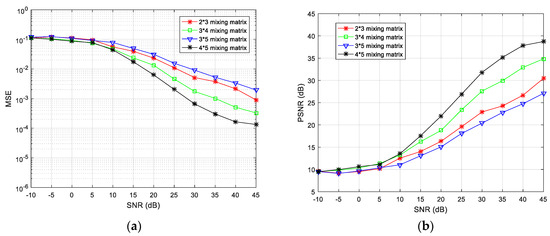
Figure 12.
Comparisons of (a) mean-square error (MSE) and (b) peak signal-to-noise ratio (PSNR) values when the number of source signals and receiving sensors are different.
The simulation results reveal that, as the degree of loss of the receiving antenna element increases, the separation performance gradually decreases. Taking and antennas as an example, the missing degree of the antenna is 1/4, and the missing degree of the 2 × 3 antenna is 1/3, thus, the MSE index is poor for the configuration. For the same receiving array, as for the and configuration schemes, it can also be seen that the MSE index under the configuration is poor. In summary, the algorithm proposed in this paper can achieve underdetermined blind extraction under different antenna configurations, and its separation performance is better for a lower degree of missing array elements.
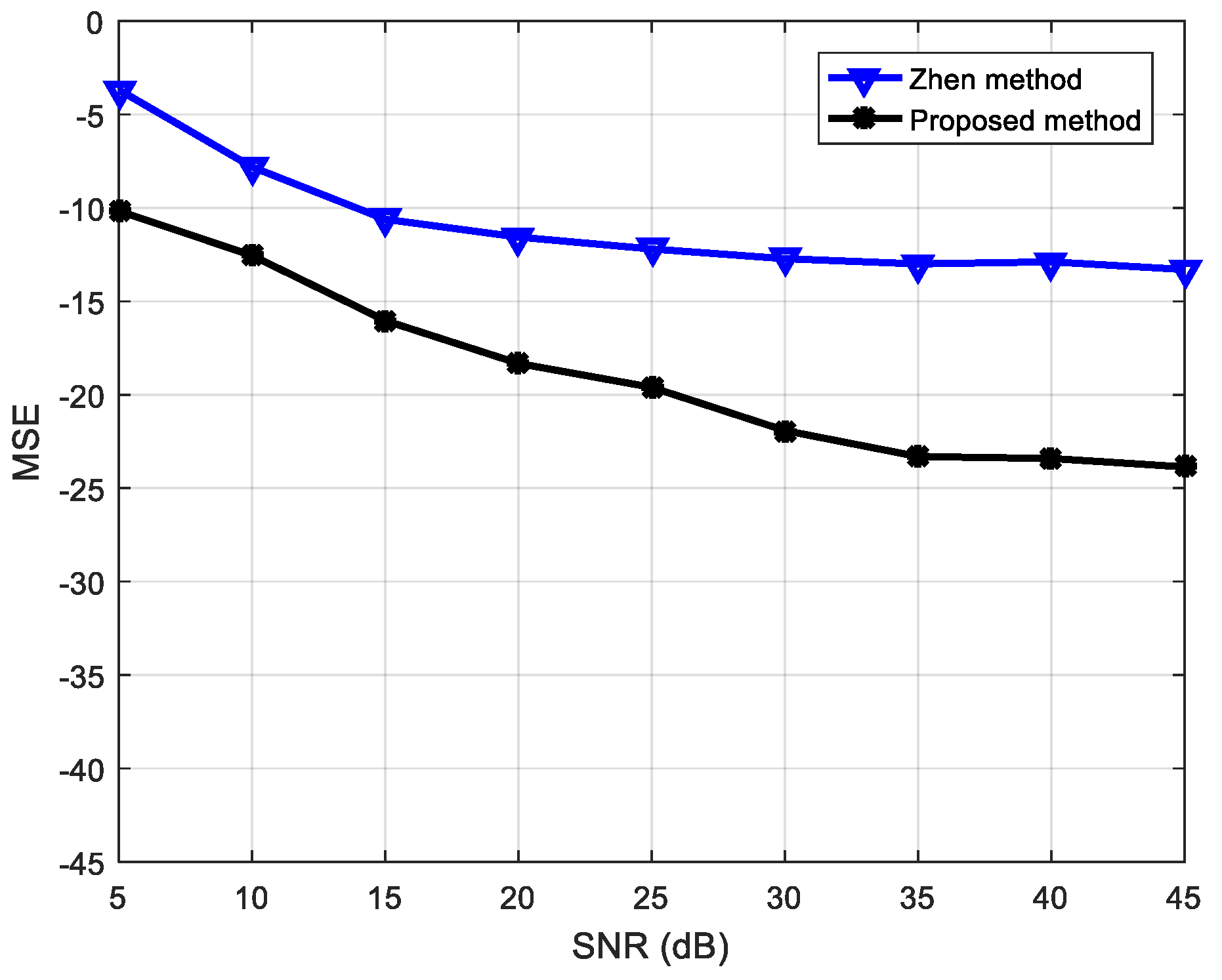
Previously, Zhen [53] analyzed the underdetermined BSS based on a speech signal for a antenna configuration. To compare the advantages of the proposed algorithm, the algorithm used in this study was also simulated in the same configuration and compared with the results in [53]. The experiment results are shown in Figure 13. From the MSE values according to the SNR, it is apparent that the algorithm proposed in this paper is superior to that in the literature [53] as regards signal restoration.
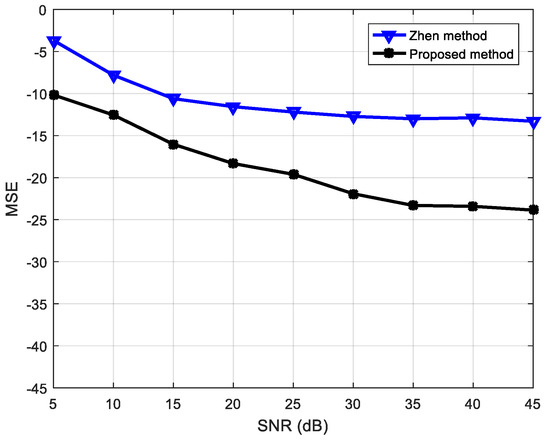
Figure 13.
Performance comparison of proposed algorithm and that in [53].
In the overall experiment, several aspects should be considered: firstly, the chaotic masking technology is universal for encryption, and the appropriate chaotic system can be selected according to the required situation. Secondly, the core part of this paper is the multi-component complementary method and out-of-order Elimination Algorithm proposed in Section 3. Only through the combination of the two algorithms can we successfully extract the interested sending end signals step-by-step. Finally, our experiment mainly considers the degree of noise and missing degree at the source, which will be further studied in the future.
6. Conclusions
In this paper, an image blind extraction algorithm based on an out-of-order elimination algorithm is proposed, and a virtual multicomponent array is constructed to transform the undetermined blind-source separation into a positive definite model. By combining the multi-component complementarity method and an out-of-order elimination algorithm, the image information which is concealed by chaos is extracted successfully. Experiments show that the EMD decomposition technique is used to extract the strongest representation of the received signal, and the virtual receiving signal vector is obtained by the parity cross sequence compensation method in the multi-component complement method. By using the algorithm of out-of-order elimination, the image information can be extracted completely. There are still some deficiencies in this algorithm. In the future, we will analyze the influence of signal source noise, channel noise and receiving sensor noise on the modified algorithm, and verify the effectiveness and universality of this algorithm.
Author Contributions
Y.X. conceived and wrote the paper; X.C. and J.Y. devoted to the simulation experiments; Q.D. and E.W. analyzed the data; E.W. gave some theoretical guidance. All authors have read and approved the final manuscript.
Funding
This research was funded by National Natural Science Foundation of China, grant number 61571181 and Natural Science Foundation of Heilongjiang Province, grant number LH2019F048.
Acknowledgments
This work was supported by the Natural Science Foundation of China (No. 61571181), and the Natural Science Foundation of Heilongjiang Province, China (No. LH2019F048).
Conflicts of Interest
The authors declare no conflict of interest.
References
- Smith, S.; Pischella, M.; Terre, M. A Moment-Based Estimation Strategy for Underdetermined Single-Sensor Blind-source separation. IEEE Signal Process. Lett. 2019, 26, 788–792. [Google Scholar]
- Hentschel, T. The six-port as a communications receiver. IEEE Trans. Microw. Theory Tech. 2005, 53, 1039–1047. [Google Scholar] [CrossRef]
- Castillo-Vazquez, M.; Puerta-Notario, A. Single-channel imaging receiver for optical wireless communications. IEEE Commun. Lett. 2005, 9, 897–899. [Google Scholar] [CrossRef]
- Guo, Y.; Naik, G.R.; Nguyen, H. Single channel blind-source separation based local mean decomposition for Biomedical applications. Conf. Proc. IEEE Eng. Med. Biol. Soc. 2017, 2013, 6812–6815. [Google Scholar]
- Guo, W.; Huang, L.; Chen, C.; Zou, H.; Liu, Z. Elimination of end effects in local mean decomposition using spectral coherence and applications for rotating machinery. Digit. Signal Process. 2016, 55, 52–63. [Google Scholar] [CrossRef]
- Mostajabi, A.; Karami, H.; Azadifar, M.; Ghasemi, A.; Rubinstein, M.; Rachidi, F. Single-Sensor Source Localization Using Electromagnetic Time Reversal and Deep Transfer Learning: Application to Lightning. SCIENTIFIC REPORTS. 2019, 9, 1–14. [Google Scholar]
- Zhu, H.J.; Wang, X.Q.; Rui, T. Shift invariant sparse coding for blind-source separation of single channel mechanical signal. J. Vib. Eng. 2015, 28, 625–632. [Google Scholar]
- Chen, C.Z.; Meng, Q.; Zhou, H.; Zhang, Y. Rolling Bearing Fault Diagnosis Based on Blind-source separation. Appl. Mech. Mater. 2012, 217, 2546–2549. [Google Scholar] [CrossRef]
- Deng, W.; Liu, Z.; Deng, Z.; Jia, X.; Wang, Z. Extraction of interference phase in frequency-scanning interferometry based on empirical mode decomposition and Hilbert transform. Appl. Opt. 2018, 57, 2299–2305. [Google Scholar] [CrossRef]
- Ma, S.; Wang, G.; Fan, R.; Tellambura, C. Blind Channel Estimation for Ambient Backscatter Communication Systems. IEEE Commun. Lett. 2018, 22, 1296–1299. [Google Scholar] [CrossRef]
- Cheng, X.; Ji, L. Single-channel mixed signal blind-source separation algorithm based on multiple ICA processing. Proc. SPIE 2017, 322, 1032203. [Google Scholar]
- Akkalkotkar, A.; Brown, K.S. An algorithm for separation of mixed sparse and Gaussian sources. PLoS ONE 2017, 12, e0175775. [Google Scholar]
- Puntonet, C.G.; Lang, E.W. Blind-source separation and independent component analysis. Neurocomputing 2005, 69, 1413–1824. [Google Scholar] [CrossRef]
- Zibulevsky, M.; Pearlmutter, B.A. Blind-source separation by sparse decomposition in a signal dictionary. Neural Comput. 2014, 13, 863–882. [Google Scholar] [CrossRef] [PubMed]
- Fu, W.; Chen, J.; Yang, B. Source recovery of underdetermined blind-source separation based on SCMP algorithm. IET Signal Process. 2017, 11, 877–883. [Google Scholar] [CrossRef]
- Filippi, M.; Desvignes, M.; Moisan, E. Robust Unmixing of Dynamic Sequences Using Regions of Interest. IEEE Trans. Med. Imaging 2017, 37, 306–315. [Google Scholar] [CrossRef]
- Behr, M.; Holmes, C.; Munk, A. Multiscale Blind-source separation. Ann. Stat. 2018, 46, 711–744. [Google Scholar] [CrossRef]
- Su, Q.; Shen, Y.; Wei, Y.; Deng, C. Underdetermined Blind-source separation by a Novel Time–frequency Method. AEU Int. J. Electron. Commun. 2017, 77, 43–49. [Google Scholar] [CrossRef]
- Liu, B.; Reju, V.G.; Khong, A.W.H. A Linear Source Recovery Method for Underdetermined Mixtures of Uncorrelated AR-Model Signals Without Sparseness. IEEE Trans. Signal Process. 2014, 62, 4947–4958. [Google Scholar] [CrossRef]
- Zhang, J.; Zhang, Y. Underdetermined Blind Sources Separation Based on Nonnegative Tri-Matrix Factorization. Adv. Mater. Res. 2014, 971, 1843–1846. [Google Scholar] [CrossRef]
- Koldovský, Z.; Tichavský, P.; Phan, A.H.; Cichocki, A. A Two-Stage MMSE Beamformer for Underdetermined Signal Separation. IEEE Signal Process. Lett. 2013, 20, 1227–1230. [Google Scholar] [CrossRef]
- Amini, F.; Hedayati, Y. Underdetermined blind modal identification of structures by earthquake and ambient vibration measurements via sparse component analysis. J. Sound Vib. 2016, 366, 117–132. [Google Scholar] [CrossRef]
- Nigam, V.; Priemer, R. Generalized Blind Delayed Source Separation Model for Online Non-invasive Twin-fetal Sound Separation: A Phantom Study. J. Med. Syst. 2008, 32, 123. [Google Scholar] [CrossRef] [PubMed]
- Zhang, G. Time-phase amplitude spectra based on a modified short-time Fourier transform. Geophys. Prospect. 2018, 66, 34–46. [Google Scholar] [CrossRef]
- Li, Q.; Ji, X.; Liang, S.Y. Bi-dimensional Empirical Mode Decomposition and Nonconvex Penalty Minimization Lq (q =0.5) Regular Sparse Representation-based Classification for Image Recognition. Pattern Recognit. Image Anal. 2018, 28, 59–70. [Google Scholar] [CrossRef]
- Zan, P.; Liu, Y.; Chang, M. Research of rectal dynamic function diagnosis based on FastICA-STFT. IET Sci. Meas. Technol. 2018, 12, 965–969. [Google Scholar] [CrossRef]
- Jurado, F.; Saenz, J.R. Comparison between discrete STFT and wavelets for the analysis of power quality events. Electr. Power Syst. Res. 2002, 62, 183–190. [Google Scholar] [CrossRef]
- Benesty, J.; Cohen, I. Single-Channel Speech Enhancement in the STFT Domain. Speech Enhanc. 2018. [Google Scholar] [CrossRef]
- Zhou, Y.; Wang, Y.; Wang, X.H. Face recognition algorithm based on wavelet transform and local linear embedding. Clust. Comput. 2019, 22, 1529–1540. [Google Scholar] [CrossRef]
- Marques, J.P.M.J.; Junior, G.C.; Morais, A.P.D. New Methodology for Identification of Sympathetic Inrush for a Power Transformer using Wavelet Transform. IEEE Lat. Am. Trans. 2018, 16, 1158–1163. [Google Scholar] [CrossRef]
- Ng, S.C.; Raveendran, P. Enhanced mu rhythm extraction using blind-source separation and wavelet transform. IEEE Trans. Biol. Med. Eng. 2009, 56, 2024. [Google Scholar]
- Mowla, M.R.; Ng, S.C.; Zilany, M.S.; Paramesran, R. Artifacts-matched blind-source separation and wavelet transform for multichannel EEG denoising. Biomed. Signal Process. Control 2015, 22, 111–118. [Google Scholar] [CrossRef]
- Belaid, S.; Hattay, J.; Naanaa, W.; Aguili, T. A new multi-scale framework for convolutive blind-source separation. Signal Image Video Process. 2016, 10, 1203–1210. [Google Scholar]
- He, P.; Chen, X. A method for extracting fetal ECG based on EMD-NMF single channel blind-source separation algorithm. Technol. Health Care 2015, 24, S17. [Google Scholar] [CrossRef] [PubMed]
- Tang, B.; Dong, S.; Tao, S. Method for eliminating mode mixing of empirical mode decomposition based on the revised blind-source separation. Signal Process. 2012, 92, 248–258. [Google Scholar] [CrossRef]
- Zhang, H.; Hua, G.; Yu, L.; Cai, Y.; Bi, G. Underdetermined blind separation of overlapped speech mixtures in time–frequency domain with estimated number of sources. Speech Commun. 2017, 89, 1–16. [Google Scholar] [CrossRef]
- Hayami, H.; Takehara, H.; Nagata, K.; Haruta, M.; Noda, T.; Sasagawa, K.; Ohta, J. Wireless image-data transmission from an implanted image sensor through a living mouse brain by intra body communication. Jpn. J. Appl. Phys. 2016, 55, 04EM03. [Google Scholar] [CrossRef]
- Zhinong, L.I. Underdetermined Blind-source separation Method of Machine Faults Based on Local Mean Decomposition. J. Mech. Eng. 2011, 47, 97. [Google Scholar]
- Sha, Z.C.; Huang, Z.T.; Zhou, Y.Y.; Wang, F.H. Frequency-hopping signals sorting based on underdetermined blind-source separation. IET Commun. 2013, 7, 1456–1464. [Google Scholar]
- Langkam, S.; Deb, A.K. Dual estimation approach to blind-source separation. IET Signal Process. 2017, 11, 527–536. [Google Scholar]
- Chen, G.; Mao, Y.; Chui, C.K. A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos Solitons Fractals 2004, 21, 749–761. [Google Scholar] [CrossRef]
- Danca, M.F.; Kuznetsovc, N.; Chen, G. Approximating hidden chaotic attractors via parameter switching. Chaos 2018, 28, 013127. [Google Scholar] [CrossRef] [PubMed]
- Xie, Y.; Yu, J.; Guo, S.; Ding, Q.; Wang, E. Image Encryption Scheme with Compressed Sensing Based on New Three-Dimensional Chaotic System. Entropy 2019, 21, 819. [Google Scholar] [CrossRef]
- Gao, T.; Chen, G.; Chen, Z.; Cang, S. The generation and circuit implementation of a new hyper-chaos based upon Lorenz system. Phys. Lett. A 2016, 361, 78–86. [Google Scholar]
- Shih, M.T.; Doctor, F.; Fan, S.Z.; Jen, K.K.; Shieh, J.S. Instantaneous 3D EEG Signal Analysis Based on Empirical Mode Decomposition and the Hilbert–Huang Transform Applied to Depth of Anaesthesia. Entropy 2015, 17, 928–949. [Google Scholar] [CrossRef]
- Alberti, T.; Consolini, G.; Carbone, V.; Yordanova, E.; Marcucci, M.F.; De Michelis, P. Multifractal and Chaotic Properties of Solar Wind at MHD and Kinetic Domains: An Empirical Mode Decomposition Approach. Entropy 2019, 21, 320. [Google Scholar] [CrossRef]
- Wang, J.; Wei, Q.; Zhao, L.; Yu, T.; Han, R. An improved empirical mode decomposition method using second generation wavelets interpolation. Digit. Signal Process. 2018, 79, 164–174. [Google Scholar] [CrossRef]
- Motin, M.A.; Karmakar, C.K.; Palaniswami, M. Selection of Empirical Mode Decomposition Techniques for Extracting Breathing Rate From PPG. IEEE Signal Process. Lett. 2019, 26, 592–596. [Google Scholar] [CrossRef]
- Wang, C.; Ding, Q. A Class of Quadratic Polynomial Chaotic Maps and Their Fixed Points Analysis. Entropy 2019, 21, 658. [Google Scholar] [CrossRef]
- Golestani, H.B.; Ghanbari, M. Minimisation of image watermarking side effects through subjective optimization. IET Image Process. 2013, 7, 733–741. [Google Scholar]
- Nouye, Y.; Hirano, K. Cumulant-Based blind identification of linear multi-Input-Multi-Output systems driven by colored inputs. IEEE Trans. Signal Process. 1997, 45, 1543–1552. [Google Scholar]
- Ye, G. Chaotic Image Encryption Algorithm Using Multi-Generalized Logistic Maps. J. Comput. Theor. Nanosci. 2013, 10, 2789–2795. [Google Scholar] [CrossRef]
- Zhen, L.; Peng, D.; Yi, Z.; Xiang, Y.; Chen, P. Underdetermined Blind-source separation Using Sparse Coding. IEEE Trans. Neural Netw. Learn. Syst. 2017, 28, 3102–3108. [Google Scholar] [CrossRef] [PubMed]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).