1. Introduction
The main aim of the error-correction codes is overcoming the noise in public communication channels, but there is a long record of results on employment of error-correction coding theory for developing systems for secret communications. These systems belong to one of the following two main categories: the systems without the so called cryptographic keys, as well as the cryptographic keys controlled ones (see [
1], for example).
The first coding based technique for secret communication over noisy channels without employment of cryptographic keys have been proposed in [
2] where a dedicated coding scheme has been employed which provides secret communication over a public channel under assumption that the wiretapper faces sample collection through the channel with an
higher noise in comparison with the one in the main channel over which communicate the legitimate parties, and a lot of papers have appeared as a follow-up of [
2].
Employment of error-correction codes controlled by the cryptographic keys have been addressed in the both two major settings: the secret (symmetric) key setting and the public (asymmetric) key one. The most famous coding based system is McEliece public key encryption system [
3] and this proposal has been followed by a number of results on its analysis and alternative proposals. McEleiece public key system is based on difficulty of decoding a random block error correcting code which is NP-complete in the worst case scenario as shown in [
4].
Within the secret key cryptographic setting there are the following two major directions of employment error correction coding: (i) developing certain code-based encryption techniques; and (ii) enhancing security of certain lightweight encryption schemes. A number of symmetric key encryption schemes have been reported based on employment of the code-based and noisy channel paradigm. An illustrative and recent example on code-based secret key encryption schemes is the proposal [
5] and its cryptanalysis reported in [
6] which has shown insecurity of the proposal. The previous example illustrates that design of efficient code based symmetric encryption techniques appears as a tricky issue.
An alternative approach is to employ coding theory in symmetric key crypto-systems for security enhancement of certain lightweight encryption techniques, and goal of this paper is to add some novel results to this approach. Employment of results on error-correction coding and noisy channels for the security enhancement has been reported in a number of papers, and we could identify the following main directions within this approach. One direction is the enhancement employing a model of noisy channel with the additive noise and related coding results. The other direction is employment of the paradigm of the channels with synchronization errors and results on the related coding techniques. Illustrative techniques for security enhancement based on a model of noisy channels with additive errors have been reported in [
7,
8,
9,
10,
11], and security evaluation of a generic model of these techniques from information-theoretic and computational complexity points of view are reported in [
12,
13], respectively. The enhancement approach based on the channels with synchronization errors and in particular an encryption approach which involves a communication channel with the errors in the form of
bits insertion is reported in [
14,
15].
Motivation for the work. According to the above consideration of the topic, security enhancement of lightweight encryption techniques employing results on communication channels with synchronization errors and related coding appears as an interesting issue, and a particular goal could be consideration of the enhancement employing a deletion channel controlled by the secret key. Also, the addressed issue could be considered as a generalization of the shrinking and self-shrinking encryption techniques reported in [
16,
17], and a way to overcome the reported weaknesses of these techniques (see, [
18,
19,
20], for example).
Summary of the results. This paper yields: (i) a proposal of the encryption-decryption scheme for the security enhancement of lightweight block ciphers based on a binary block error-correction coding and a simulator of the deletion channel controlled by the secret key, and (ii) cryptographic security evaluation of the proposed scheme. We suppose that a building component for developing security enhanced scheme is a block encryption algorithm with a known security level (specified by Definition 2), and we consider this algorithm which is the subject of enhancement as the “initial” encryption scheme. Main results of the paper are in
Section 2.2 and
Section 4.2.
Section 2.2 provides a construction for security enhancement of a given encryption scheme employing a suitable block error-correction code for a binary erasure channel which performs mapping
,
, and a simulator of a binary channel with the deletions rate
d controlled by the secret key. The construction is such that the wiretapper faces a problem of cryptanalysis after a communication channel with bits deletion and the legitimate party should only perform the decryption after a channel with bit erasures correctable by the employed error-correction code. The security enhancement is analyzed in terms of the related probabilities, equivocation, mutual information and channel capacity, and it includes employment of certain recent results regarding the upper-bounds on the capacity of channels with deletion errors. Main result of
Section 4.2 is Theorem 1 which in a generic way proves the security enhancement showing that the adversary’s probability to win the specified security evaluation game (specified by Definition 1) is reduced for certain factor
which upper bound is derived, and it is a decreasing function of the coding parameter
n and the deletion rate
d.
Organization. The paper is organized as follows.
Section 2 proposes a framework for security enhancement based on the secret key controlled simulation of a deletion channel and dedicated error-correction coding. Technical background for the security evaluation is summarized in
Section 3. Security evaluation results are given in
Section 4, and the final
Section 5 provides a concluding discussion.
2. A Proposal for the Security Enhanced Encryption
An encryption and decryption algorithm which provide a provably enhanced cryptographic security are proposed in this section. The enhanced security appears as a consequence of the design based on employment of the simulator of a binary noisy channel which appears as the erasure channel at the legitimate party and the deletion one at the wiretapper.
2.1. Underlying Ideas
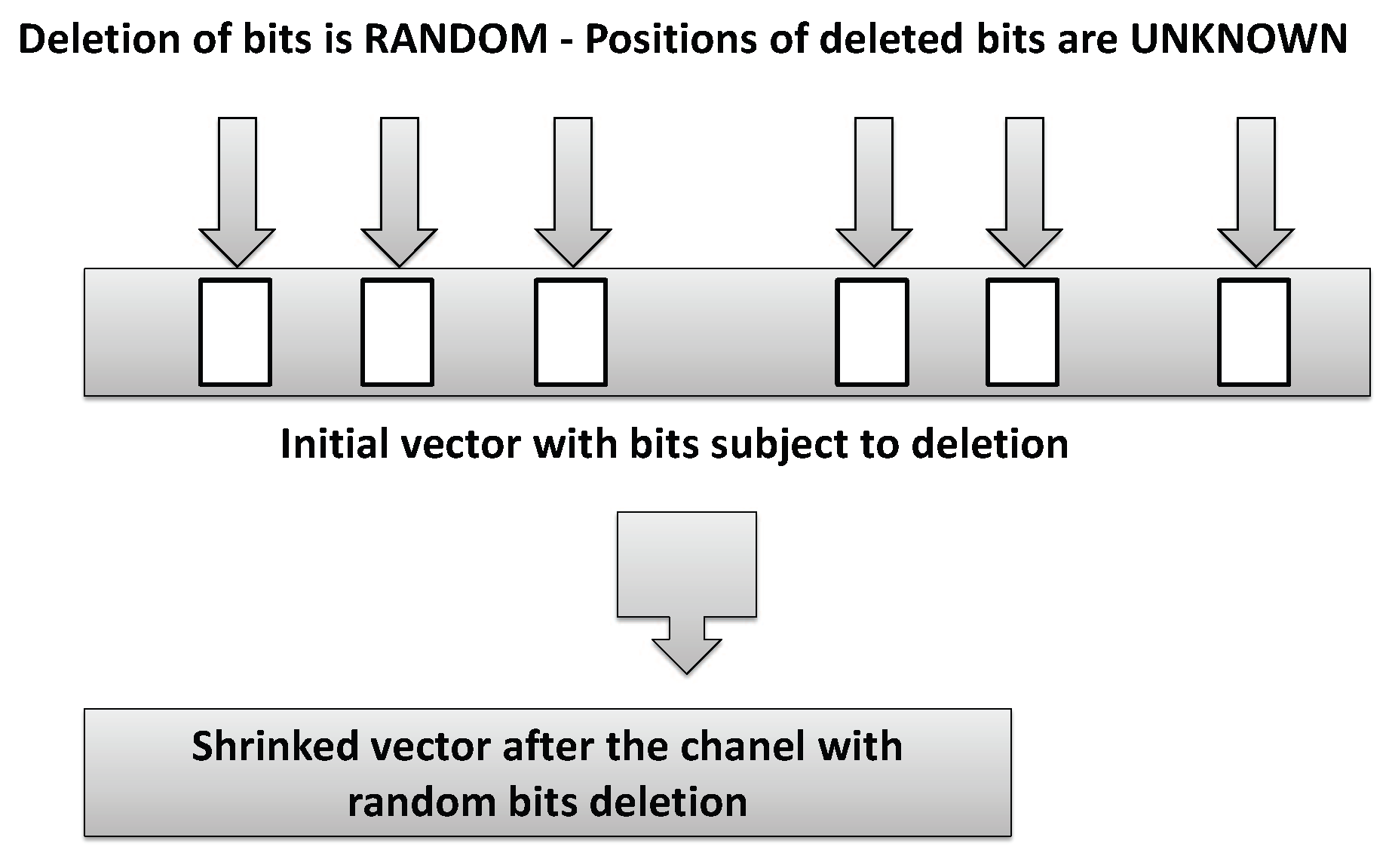
The underlying ideas for the design could be summarized as follows. Enhance security of encryption based on information-theoretic and coding results when a wiretapper faces sample collection after a channel with deletions assuming a binary deletion channel with deletion probability
d which takes input binary string and deletes each bit independently with the probability
d. A model of the deletion channel is illustrated in
Figure 1.
Let a string denotes an input to a binary deletion channel and let the deletion pattern is an increasing subsequence of representing the bits that are not deleted. Consequently, denotes the “transformation” of after a deletion channel with deletion pattern .
Note that when the deletion pattern is known, the deletion channel reduces to the erasure channel and we could consider that is the output of erasure channel for given input .
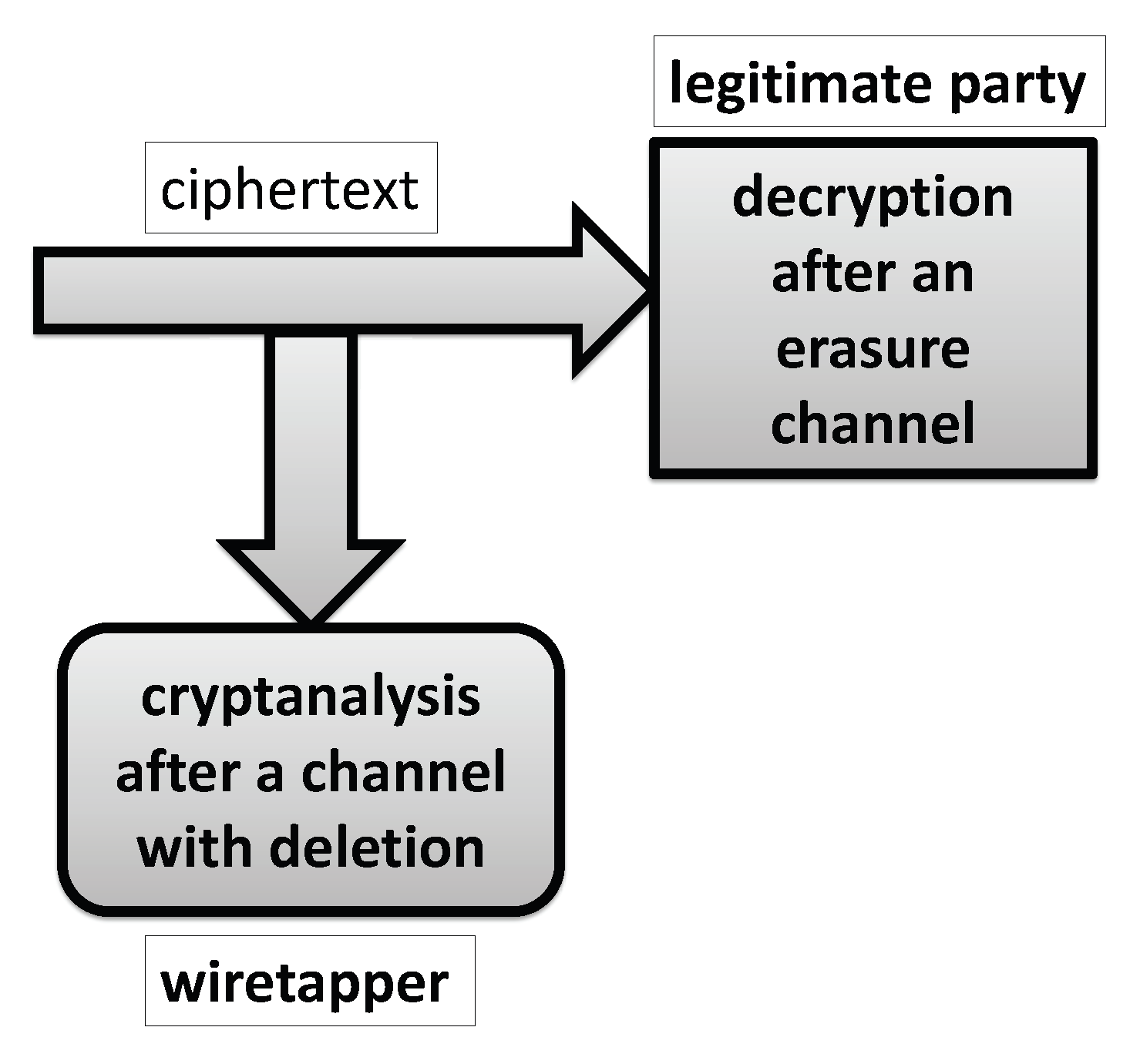
The main underlying idea which this paper employs is to enhance cryptographic security of a given encryption scheme in such a way that a legitimate user faces an erasure channel, and a wiretapper faces a deletion channel, i.e., a legitimate party knows the deletion pattern
and a wiretapper does not know this pattern. Assuming that the deleted bits positions are selected in a pseudorandom manner controlled by the secret key and generated by the encryption/decryption algorithm, note that the legitimate party knows
, but the wiretapper who does not know the secret key does not know
and consequently faces a deletion channel instead the erasure one faced by a legitimate party. Accordingly, the corresponding paradigm is displayed in
Figure 2.
2.2. Framework for Encryption and Decryption
The design proposed in this paper is based on the following building blocks:
a lightweight block cipher;
implementation of an error correction code encoding/decoding for binary erasure channel;
simulation of a deletion channel where the deletion pattern is generated by the employed block cipher.
It is assumed that encryption and decryption parties share a secret key. As usually, before the session, the both parties (encryption and decryption ones) establish a session key (to be used later on), employing the secret key and the public data.
The encryption and decryption are performed as follows.
Encryption:
- -
a lightweight block cipher generates n dimensional binary vector where denotes the block cipher encryption according to the secret key and performs one-to-one mapping ;
- -
an erasure error correction encoding capable to provide correction up to t erasure errors generates -bit vector as the corresponding mapping , , where t is a given parameter, and ;
- -
a simulator of a binary channel with random bits deletion performs mapping controlled by a vector generated by the employed block cipher, .
Decryption:
- -
an erasure error correction decoding controlled by a vector generated by the employed block cipher generates n-bit vector by the corresponding mapping , ;
- -
a lightweight block cipher generates n dimensional binary vector where denotes the block cipher decryption according to the secret key .
The proposed encryption and decryption framework is displayed in
Figure 3.
The objective of this paper is to provide a framework for the security enhancement and show the enhancement gain. Accordingly, consideration of particular instantiations of the framework is out of the scope of this paper. We just point out that a candidate coding scheme could be the polar coding, and that [
21] provides an illustrative discussion of polar coding over a binary erasure channel, as well as the decoding complexity after a deletion channel.
Regarding similarity/dissimilarity of the proposed framework and the one reported in [
5], note the following. The scheme [
5] is based on a suitable block error-correction code and two shift registers which provide that the wiretapper faces a problem of decoding after a channel with flipping, insertion and deletion of the codeword bits. On the other hand, the proposed scheme is based on an (initial) encryption algorithm which has certain security level and a simulator of the deletion channel which in a provable way enhances security of the entire scheme. So, although the block representation of the both schemes has a similarity, they are substantially different because the one reported in [
5] is a code-based design of encryption and the one proposed in this paper belongs to a class of the security enhanced encryption employing dedicated coding and simulator of a noisy channel.
3. Security Evaluation Background
3.1. Notations and Preliminaries
A random variable is denoted by an upper-case letter (e.g., A) and its realization is denoted by a lower-case letter (e.g., a). The entropy of a random object A is denoted by , and the mutual information between two random objects A and B is denoted by . The binary entropy function is denoted by .
The entropy of a random variable
A is defined as:
The mutual information
between jointly distributed random variables
A and
B is defined as follows:
where conditional entropy is defined as
and
Consequently, the conditional mutual information when the third variable
Z is given is:
Following [
1], the mutual information
between the message
and the related sample
, or the uncertainty, i.e., the equivocation
are traditionally employed as the main information-theoretic security metric. On the other hand, according to certain recent considerations, the average mutual information
should be addressed as a strong information-theoretic security metric, and
as a corresponding weak one.
3.2. The Probability of Error and The Equivocation after a Noisy Channel
Let A and B be discrete random variables which correspond to input and output, respectively, of a communication channel. Let the possible realizations of A and B are , and , , respectively, , and let a decision rule on A when B can be considered as identification of a realization when is given, and we denote by the probability of the identification (classification) error.
Suppose the random variables
A and
B represent input and output messages (out of
m possible messages), and the given conditional entropy
represents the average amount of information lost on
A when
B is given. According to [
22] or [
23], for example, we have the following general upper bound on the equivocation:
where
is the binary entropy function and
. The above inequality can be rewritten as follows:
and when
A is such that it has the maximum possible entropy we have:
which can be further transformed into:
3.3. The Capacity of a Deletion Channel
The Shannon capacity of a channel is denoted by
and is defined as
where
A corresponds the channel input,
B corresponds to the channel output, and the supremum is over the choice of the distribution of
A.
As reported in [
24], the capacity
of a deletion channel with the deletion rate
d is upperbounded as follows:
for
, and logarithm is taken to base
e.
5. Concluding Notes
This paper has proposed a framework for security enhancement of certain encryption schemes and its security evaluation. The final security evaluation result given in Theorem 1 also shows the security gain which the security enhanced encryption provides in comparison with the initial one. The lower bound on the security gain is a function of the encryption block size and the deletion rate in the simulated channel with deletion errors. The result given in Theorem 1 is a generic one and it holds for any particular instantiation of the proposed encryption framework.
An interesting future direction is design of particular instantiations of the proposed framework within the given implementation constraints where dedicated basic (initial) encryption, a code for correction of erasure errors and simulator of a channel with deletion errors controlled by the secret key are specified, and complexity of implementation overhead implied by the enhancement is evaluated. Regarding overhead implied by employment of the coding scheme, as an illustration, we point to the polar coding [
21] which provides encoding and decoding complexities
assuming that the encoding performs the mapping
,
.