Abstract
In this paper, we propose a rateless codes-based communication protocol to provide security for wireless systems. In the proposed protocol, a source uses the transmit antenna selection (TAS) technique to transmit Fountain-encoded packets to a destination in presence of an eavesdropper. Moreover, a cooperative jammer node harvests energy from radio frequency (RF) signals of the source and the interference sources to generate jamming noises on the eavesdropper. The data transmission terminates as soon as the destination can receive a sufficient number of the encoded packets for decoding the original data of the source. To obtain secure communication, the destination must receive sufficient encoded packets before the eavesdropper. The combination of the TAS and harvest-to-jam techniques obtains the security and efficient energy via reducing the number of the data transmission, increasing the quality of the data channel, decreasing the quality of the eavesdropping channel, and supporting the energy for the jammer. The main contribution of this paper is to derive exact closed-form expressions of outage probability (OP), probability of successful and secure communication (SS), intercept probability (IP) and average number of time slots used by the source over Rayleigh fading channel under the joint impact of co-channel interference and hardware impairments. Then, Monte Carlo simulations are presented to verify the theoretical results.
1. Introduction
Physical-layer security (PLS) [1,2,3,4] has attracted much attention of the researchers as an efficient method to attain security. Due to the simple implementation, i.e., only exploiting characteristics of wireless medium such as link distance and channel state information (CSI), PLS can be implemented efficiently in wireless sensor networks (WSNs), internet-of-things (IoT) networks, etc. [5,6,7,8]. To enhance the secrecy performance, diversity transmission methods can be employed. In [9,10,11,12], MIMO-based transmit–receive methods such as Transmit Antenna Selection-Maximal Ratio Combining (TAS-MRC), Maximal Ratio Transmission-MRC (MRT-MRC), MRT-Selection Combining (MRT-SC), MRT-SC were proposed and analyzed. In addition, performance of secure communication protocols can be also enhanced with cooperative relaying methods [13,14,15,16]. In [17,18,19,20], the authors proposed cooperative jamming (CJ) techniques to reduce quality of the eavesdropping channels, where friendly jammers are employed to generate artificial noises on the eavesdropper, and the legitimate receivers have to cooperate with the jammers to remove the interference in the received signals. The results presented that the schemes which combine the diversity transmission and the jamming techniques outperform the conventional cooperative ones without using CJ. However, energy efficiency may become a critical issue when the jammer nodes continuously transmit the artificial noises by using their own energy. Recently, radio frequency (RF) energy harvesting (EH) is an efficient method to prolong lifetime for wireless networks [21,22,23,24]. Particularly, the wireless devices can harvest energy from full-energy nodes [21,22] or from power stations deployed in networks [25,26] or even from co-channel interferences caused by outside sources [27,28]. References [20,29] proposed and analyzed performance of RF-EH-based secure communication protocols. To support energy for the jammer nodes, the authors of [20,29] proposed harvest-to-jam (HJ) methods, where the cooperative jammers harvest energy from the RF signals, and then use it to generate artificial noises.
Rateless codes or Fountain codes (FCs) [30,31,32,33] have drawn much attention due to their simple implementation. In FCs, a transmitter uses Fountain encoder to generate a limitless number of encoded packets, and then transmit them to intended receivers. If the receivers can receive a sufficient number of the encoded packets, they can recover the original message of the transmitter. Due to broadcast of the wireless channels, the encoded packets can be overheard by eavesdroppers. Therefore, the security becomes a critical issue for the FCs-based communication systems. Recently, some published works considering the secure communication protocols with FCs have been reported in [34,35,36]. In [34], the authors proposed a secure delivery scheme, in which the security can be achieved if the legitimate user receives enough Fountain packets before the eavesdropper. In [35], a dynamic Fountain-encoded at a transmitter was proposed to enhance the data security. The authors of [36] proposed a FC-based cooperative relay protocol. In [36], the source and the jammer cooperate to remove the interference components in the received signals at the destination. Reference [37] proposed an efficient FCs-based multicast scenario to achieve security for Internet of Things (IoT) systems.
In this paper, we propose a FCs based secure communication protocol, where a multi-antenna source selects its best antenna to transmit the encoded packets to a single-antenna destination, in presence of a single-antenna eavesdropper who attempts to overhear the source information. When the destination can receive sufficient encoded packets for decoding the original data, it would send a feedback to the source to terminate the transmission. As a result, to obtain the secure transmission, the destination must receive a sufficient number of the encoded packets before the eavesdropper. Otherwise, the original information is intercepted. The main contributions of this paper can be summarized as follows:
- To the best of our knowledge, we first propose the FCs based communication protocol using the harvest-to-jam based cooperative jamming technique to reduce the quality of the eavesdropping link. Different with [34,35,36,37], we propose a cooperative jamming technique, where a cooperative jammer node harvests energy from the RF signals of the source and the interference sources to generate noises to the eavesdropper. Different with our previous works [38,39], in the proposed protocol, there exist interference sources in the network that cause co-channel interferences on both the destination and the eavesdropper.
- Until now, almost published works related to secrecy performance evaluation have assumed that the transceiver hardware of the wireless devices is perfect. However, in practice, it is not perfect due to phase noise, I/Q imbalance (IQI), amplifier non-linearity [40,41,42,43]. In this paper, the joint impact of hardware noises and co-channel interference on the system performances is investigated.
- For performance evaluation, we derive exact closed-form expressions of outage probability (OP), probability of successful and secure communication (SS), intercept probability (IP) and average number of the time slots used by the source over Rayleigh fading channel. The closed-form formulas are easy-to-compute, and hence they can be easily used to design and optimize the considered system. In addition, all of the derived expressions are verified by Monte Carlo simulations.
2. System Model
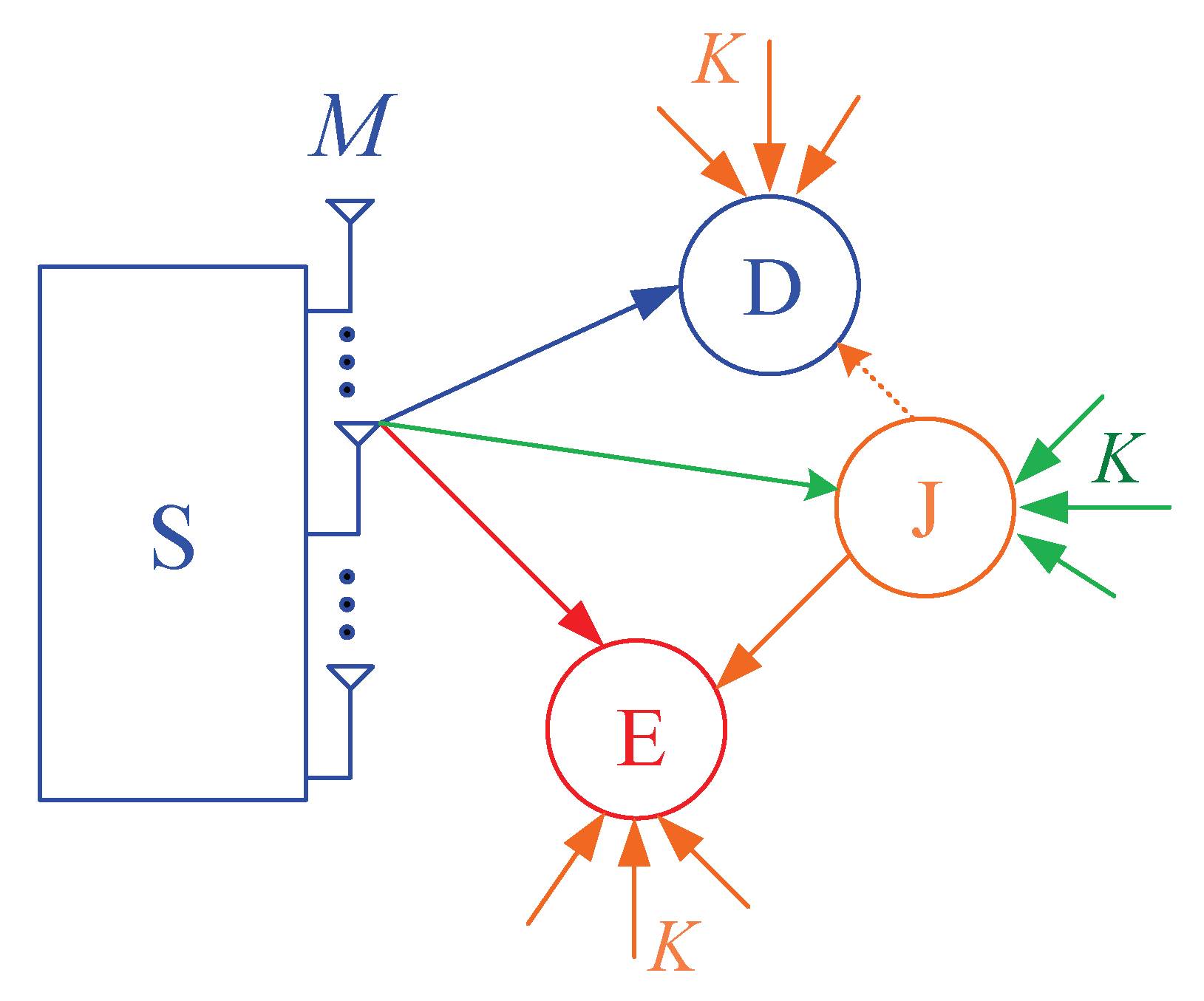
Figure 1 illustrates the system model of the proposed protocol, where the source node (S) equipped with M antennas communicates with the single-antenna destination (D), in presence of the single-antenna eavesdropper (E) who attempts to overhear the source data. All of the receivers such as D and E are suffered from co-channel interference caused by K ambient sources (denoted by ). To reduce the quality of the eavesdropping link, the cooperative jamming technique can be used, where the single antenna jammer (J) is employed to continuously generate the artificial noises to E. We assume that the nodes D and J are close with each other so that D can remove the co-channel interference generated by J [38]. Moreover, the jammer (J) uses the energy harvested from the RF signals of the source and the interference sources for transmitting the jamming signals.
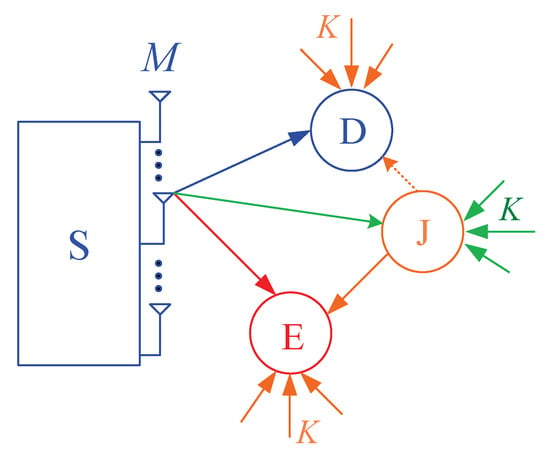
Figure 1.
System model of the proposed scheme.
The source divides its original data into L packets which are encoded appropriately to create the encoded packets. Then, at each time slot, the source uses the TAS technique to send each encoded packet to the destination. At the same time, the eavesdropper tries to receive the encoded packet. The destination and the eavesdropper are assumed to be able to successfully obtain the original data if they can correctly receive at least H encoded packets, where , and is the decoding overhead which depends on concrete code design. Moreover, after the destination receives sufficient number of the encoded packets, it will send an ACK message to inform the source to stop the data transmission. In this case, if the eavesdropper cannot obtain enough number of the encoded packets, it cannot obtain the source data. Otherwise, the original data of the source will be intercepted.
Let us consider the data transmission at an arbitrary time slot. Let , and denote channel coefficients between the antenna of the source and the nodes D, E and J, respectively, where . We also denote and as channel gains of the and links, respectively, where . We assume that all of the link channels are block and flat Rayleigh fading which keeps constant in a time slot but independently changes over time slots. Therefore, the channel gains are exponential random variables (RVs) whose cumulative distribution function (CDF) and probability density function (PDF) are given, respectively as
where is a parameter of i.e., and is an expected operator. We can assume that the RVs are independent and identical, i.e., for all m. On the contrary, the RVs are assumed to be independent and non-identical, i.e., as , where .
With the TAS technique, the source selects the best transmit antenna to send the encoded packet to the destination, using the following method:
where .
Moreover, the CDF of can be obtained as
where is a binomial coefficient.
Let us denote T as a block time of each time slot: a duration of is used for the jammer node to harvest the energy from the source and the interference sources, and the remaining time is spent for the data transmission. Then, the energy harvested by the jammer is expressed as
where is an energy conversion efficiency, and are transmit power of the source (S) and the interference sources , respectively.
Next, the average transmit power of the jammer used for the data transmission phase can be formulated by
where .
It is worth noting that the implementation of the TAS method is simpler than that of the MRT method because it only requires the index of the best antenna which can be feed-backed by the destination (not feedback all of the channel state information (CSI) as in MRT). Moreover, the best transmit antenna selection can be performed before the EH phase, and the time used for this process can be ignored as compared with the EH and packet transmission phases. Finally, the source uses the selected antenna during each time slot for both the EH and data transmission purposes due to scheduling issues, e.g., the source uses the remaining antennas to serve other destinations.
Let us denote U as the length of each encoded packet. If the source sends the signal to the destination, the received signals at the destination and the eavesdropper can be expressed, respectively as
where , and are hardware noises caused by impairments, and are signals transmitted by the nodes J and , respectively, and and are additive white Gaussian noises (AWGNs) at D and E, respectively. The hardware noises and can be modeled as Gaussian RVs with zero-mean and variances of and , respectively, where and is total hardware impairment levels of the and links, respectively.
Because the nodes D and J are close with each other so that we can assume that D knows , and via securely exchanging local messages with J. Therefore, D can remove the interference component from the received signal . Once D can perfectly remove the interference, the instantaneous signal-to-interference-plus-noise ratio (SINR) received by the destination under joint impact of co-channel interference and hardware impairments can be formulated as [44]
where is variance of additive noises which are assumed to be same at all of the receivers, and .
Because the eavesdropper cannot remove the jamming signals, the instantaneous SINR obtained at this node is given as
Next, we can give expressions of the data rate for the data and eavesdropping links, respectively by
Assume that each encoded packet can be decoded successfully if the achievable data rate is higher than a predetermined target rate (denoted by ). Otherwise, the encoded packet cannot be received correctly. Hence, the probability that the destination cannot receive one encoded packet correctly is formulated as
where
Note that the probability of the successful decoding for one encoded packet at D is . Similarly, the probability that one encoded packet can be received correctly and incorrectly by the eavesdropper is given, respectively as
Considering a delay-constrained system where the maximum number of time slots that can be used for transmitting the encoded packets is limited by . This means that the destination cannot recover the original data if it cannot successfully receive H encoded packets within time slots. Let us denote as the number of time slots used by the source (or the number of the encoded packets sent by the source), and as the number of the encoded packets received by the nodes D and E, respectively, after the source stops its transmission. Then, the outage probability (OP) at the destination is formulated by
Next, the probability that the source-destination transmission is successful and secure (SS) is defined as
Equation (15) implies that the destination can receive sufficient number of the encoded packets before the eavesdropper when the number of time slots used is less than or equal to .
Let us consider the intercept probability (IP) defined as the probability that the eavesdropper can obtain H encoded packets before or at same time with the destination:
We note from (16) that when the eavesdropper obtains H encoded packets, it does not need to receive more encoded packets, regardless of whether the source will transmit the encoded packets in the next time slots. Instead, it will start to decode the original data of the source. Finally, we study the average number of the time slots used to transmit encoded packets to the destination, which can be formulated by
In (17), is the probability that the number of the encoded packets received at the destination is when the source used time slots (the destination is in outage), and is the probability that D can obtain sufficient number of the encoded packets within t time slots, where (the data transmission is successful).
3. Performance Analysis
3.1. Derivations of and
Proposition 1.
If , then , and if can be expressed by an exact closed-form formula as
Proof.
See the proof and notations in Appendix A. □
Proposition 2.
If , then , and if we can obtain an exact closed-form expression of as
Proof.
See the proof and notations in Appendix B. □
In case where , Equation (19) reduces to
3.2. Analysis of Outage Probability (OP)
As defined in (14), an exact closed-form expression of OP can be provided as follows:
It is noted from (21) that the possible values of are from 0 to , and there are possible cases for each value of .
3.3. Analysis of Successful and Secure Communication (SS)
From (15), we can rewrite SS by
In (22), is the probability that the destination can correctly receive H encoded packets when the number of time slots used is u. Since the data transmission between the source and the destination ends in the time slot, is given as
3.4. Analysis of Intercept Probability (IP)
The intercept probability (IP) in (16) is given by
3.5. Analysis of Average Number of Time Slots (TS)
Similarly, the probability and in (17) can be calculated respectively as
4. Simulation Results
In this section, Monte Carlo simulations are presented to verify the theoretical results. For illustration purpose, in all of the simulations, we fix the required number of the encoded packets by 10 , the energy conversion efficiency by 1 , the total block time by 1 , the number of the interference sources by 3 , the parameters of the interference links by , and , and the parameters of the remaining links by 1 . In the figures, the simulation and theoretical results are denoted by Sim and Theo, respectively.
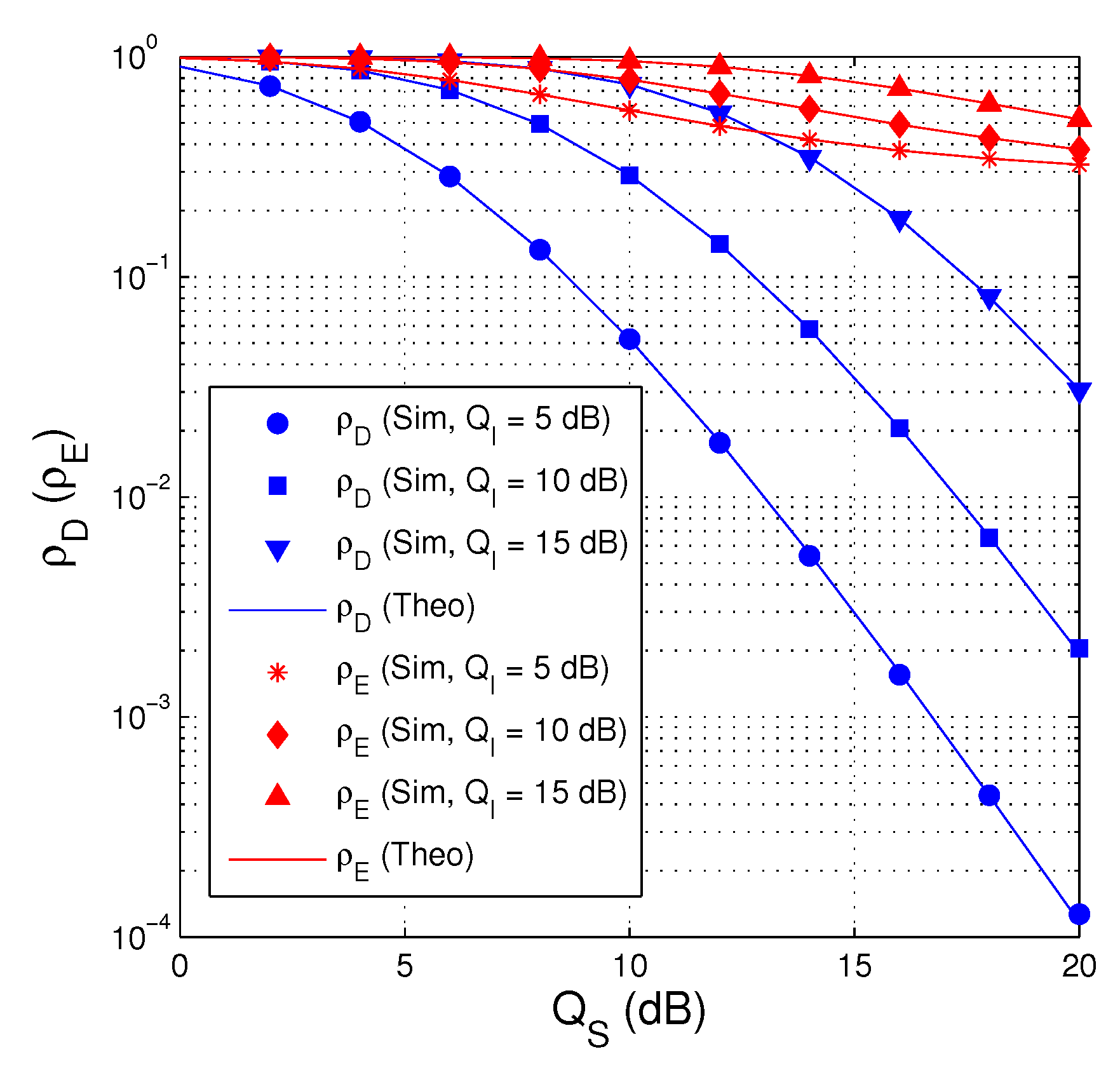
In Figure 2, we present the probability and as a function of in dB. In this figure, the number of antenna equipped by the source is set to 3 , the fraction of time allocated for the EH phase is fixed by 0.3 , the hardware impairment levels are assigned by , and the target rate is set to 0.75 . It can be seen from Figure 2 that and decrease with the increasing of and the decreasing of . However, is much smaller than at medium and high regimes. We also obverse that the simulation and theoretical results are in good agreement, which validates our derivations.
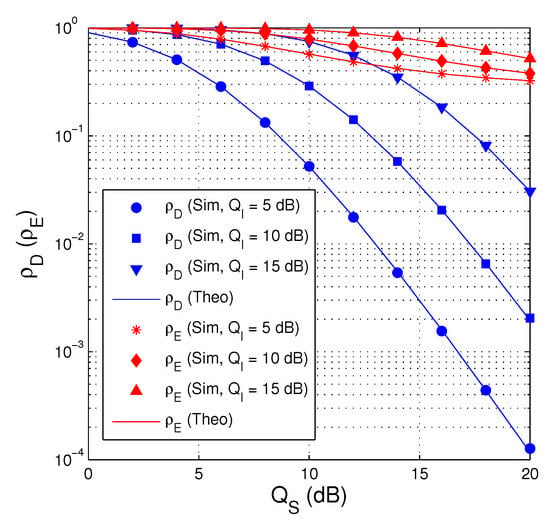
Figure 2.
and as a function of in dB when , , and .
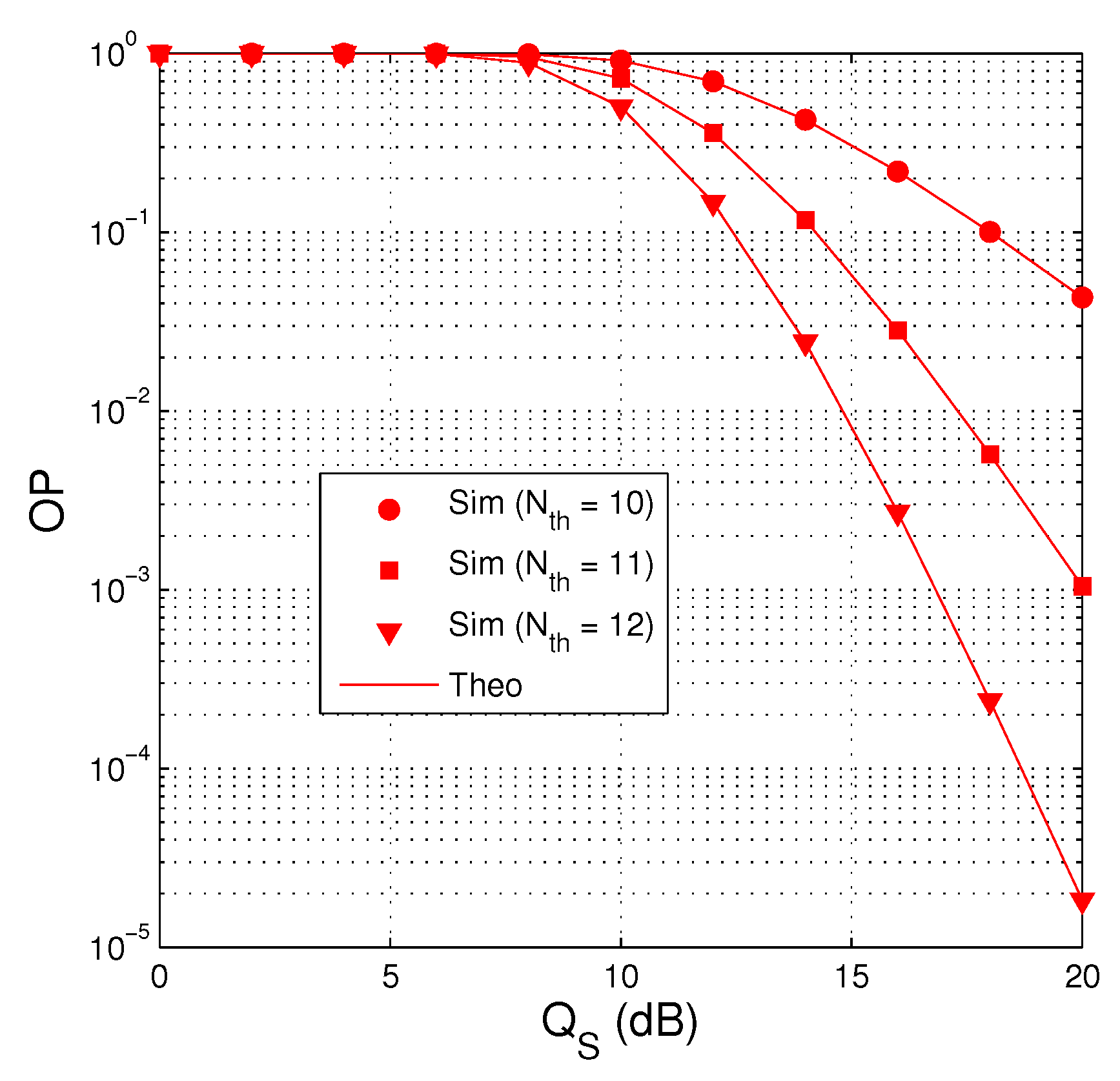
Figure 3 presents outage performance of the proposed protocol as a function of in dB with dB, , , and . It is shown in Figure 3 that the impact of the co-channel interference on the performance is negative, i.e., the value of OP is very high at low regimes. In particularly, when the value of is lower than that of , OP is almost equal to 1. We can also observe that the outage performance is better with high value of because the source has more time slots to transmit the encoded packets to the destination.
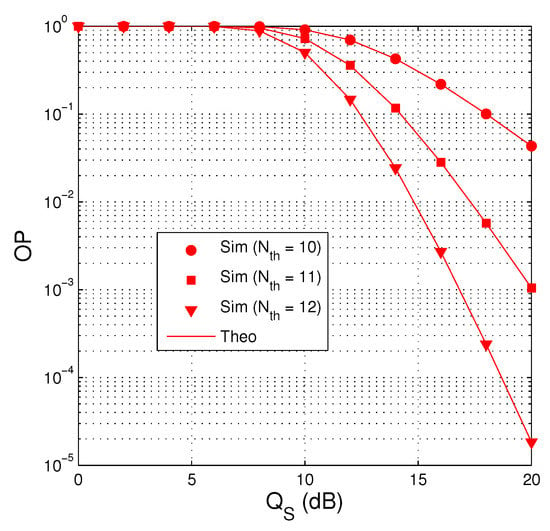
Figure 3.
OP as a function of in dB when dB, , , and .
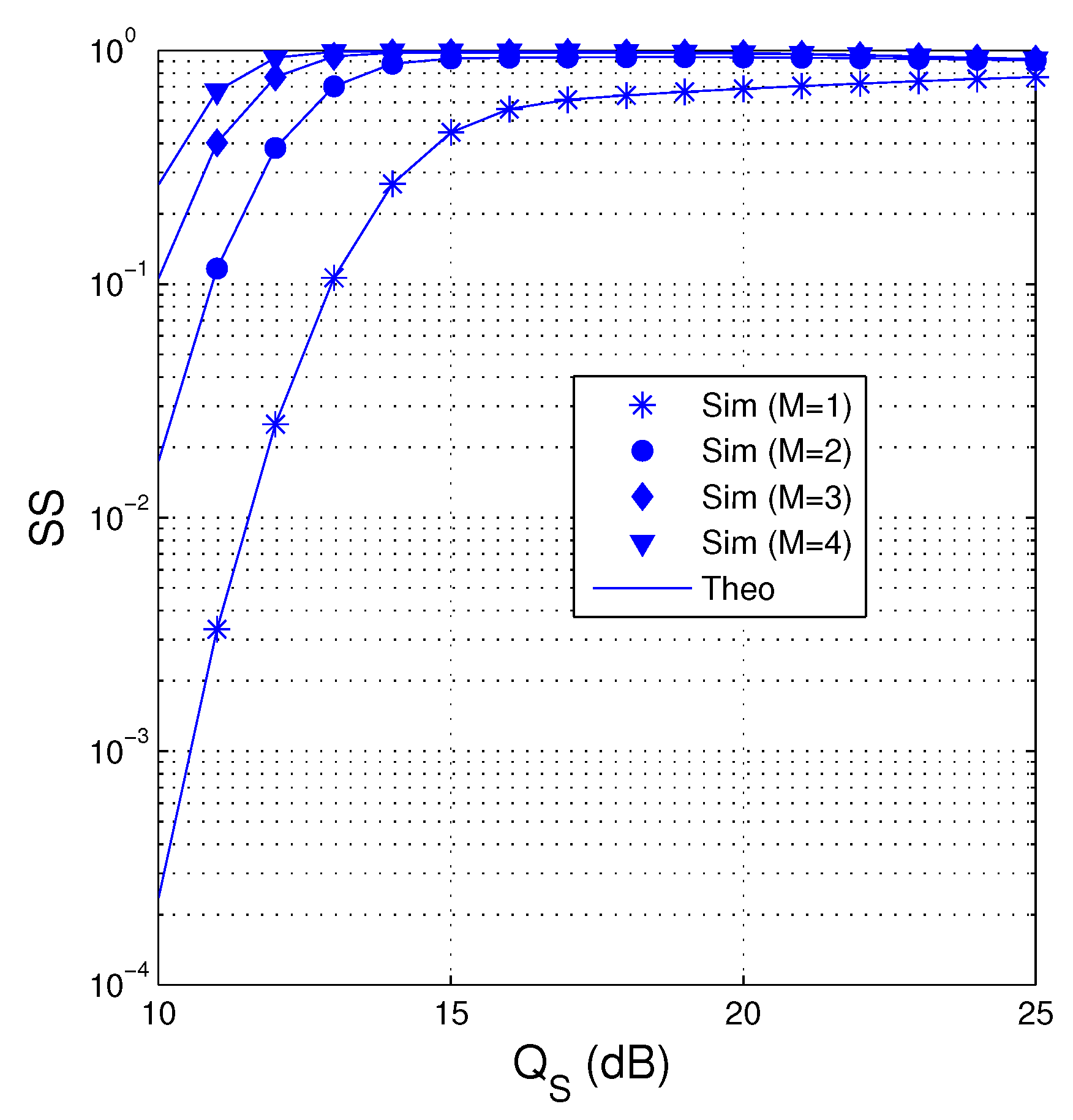
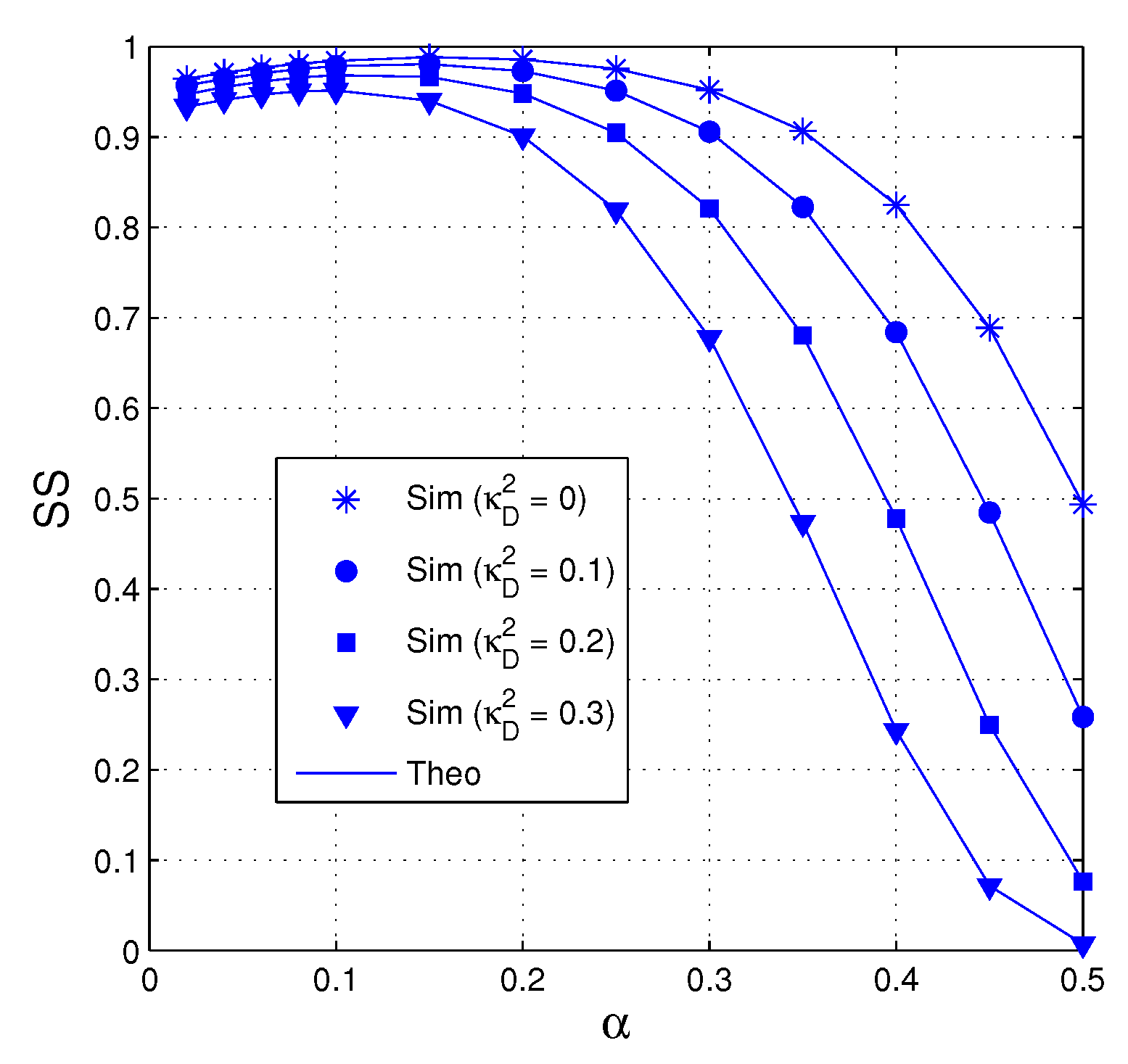
In Figure 4, we present the value of SS as a function of in dB when dB , , , , and . We can see that the proposed protocol obtains higher value of SS when more antennas are equipped at the source. It is also seen that when , the SS performance is significantly degraded because no transmit diversity gain is obtained. Moreover, SS also increases as increasing . It is due to the fact that at high values, the destination almost obtains sufficient number of the encoded packets before the eavesdropper. However, it can be seen from Figure 4 that when the value of is very high, the value of SS slightly decreases due to high overhearing possibility of the eavesdropper. Moreover, the SS performance in all values of is almost same at high regimes.
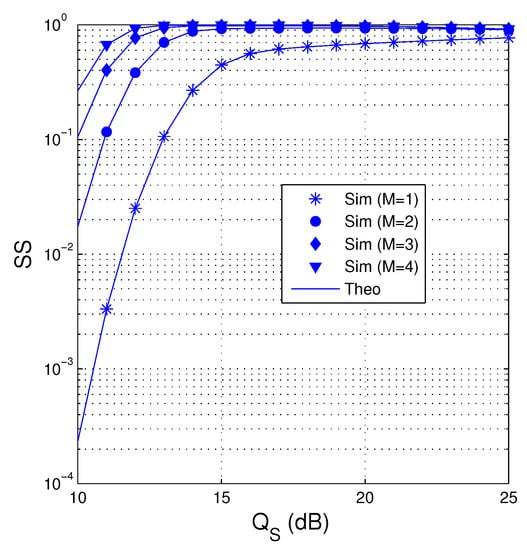
Figure 4.
SS as a function of in dB when dB, , , , and .
In Figure 5, the value of SS is presented as a function of when dB, , , and . As we can see, the performance significantly degrades with high hardware impairment levels of the data links, i.e., is high. Moreover, we can observe from that the fraction of time allocated for the EH phase impacts on the value of SS. It can be seen that there exists an optimal value of at which the value of SS is highest.
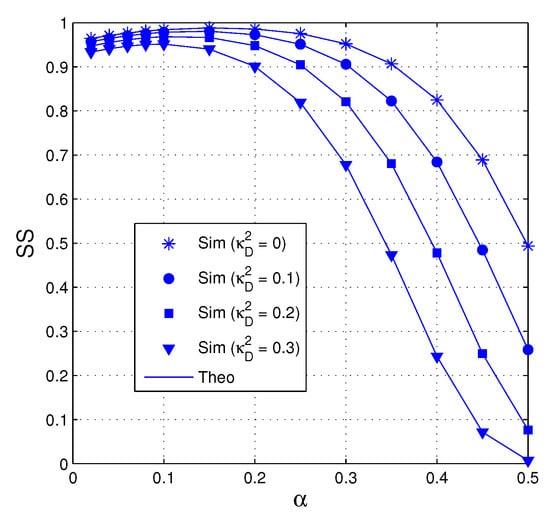
Figure 5.
SS as a function of when dB, , , and .
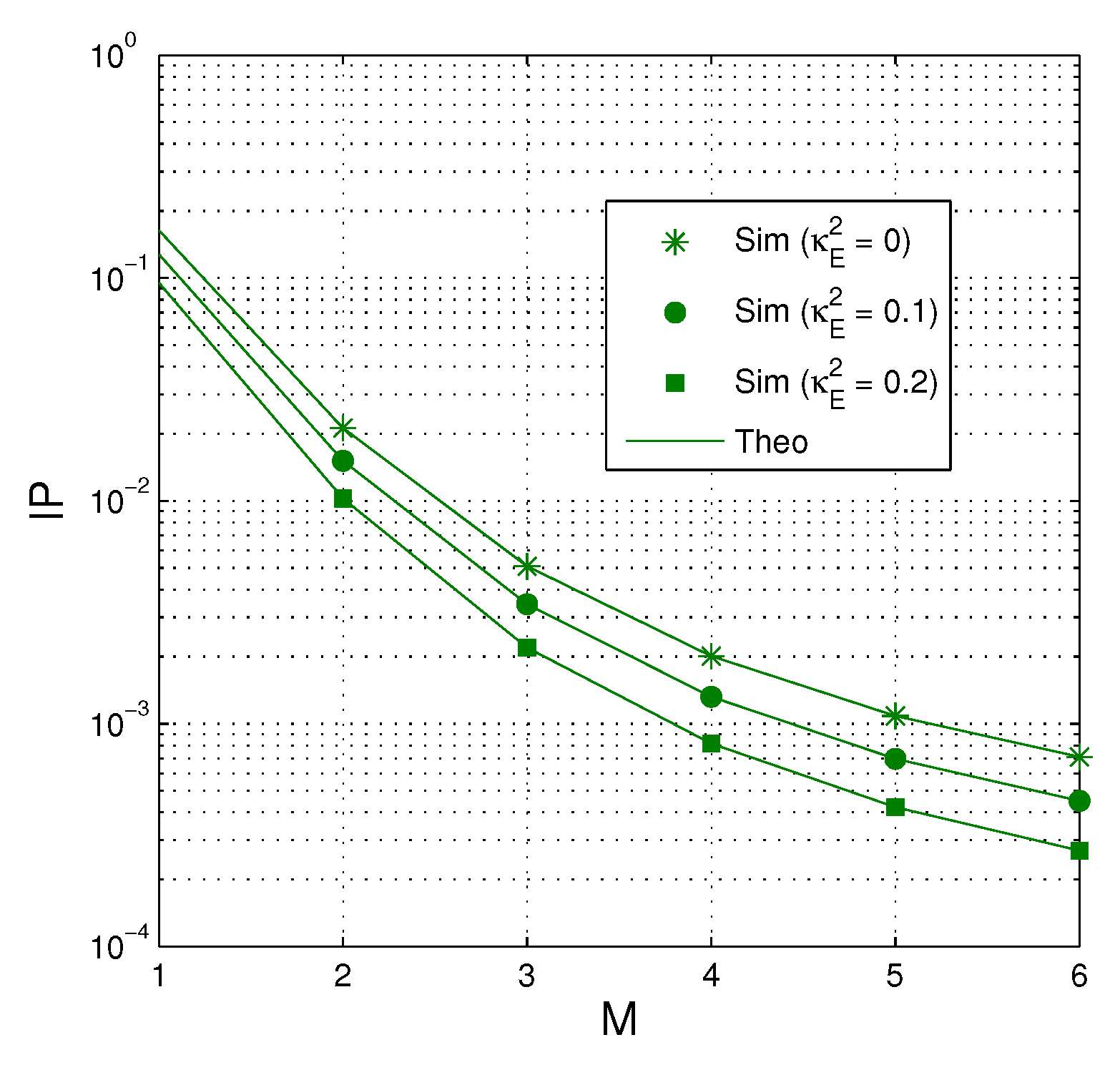
In Figure 6, the intercept probability of the proposed protocol is presented as a function of M when dB, , , and . As we can see, the value of IP decreases when more antennas are equipped at the source. Also, IP is lower when the hardware impairment level of the eavesdropping links is high.
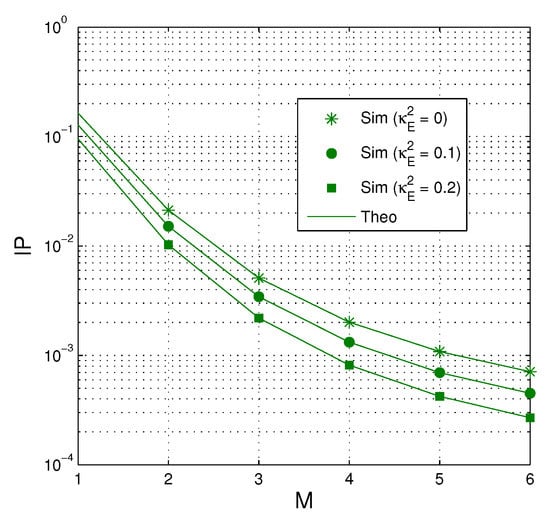
Figure 6.
IP as a function of M when dB, , , and .
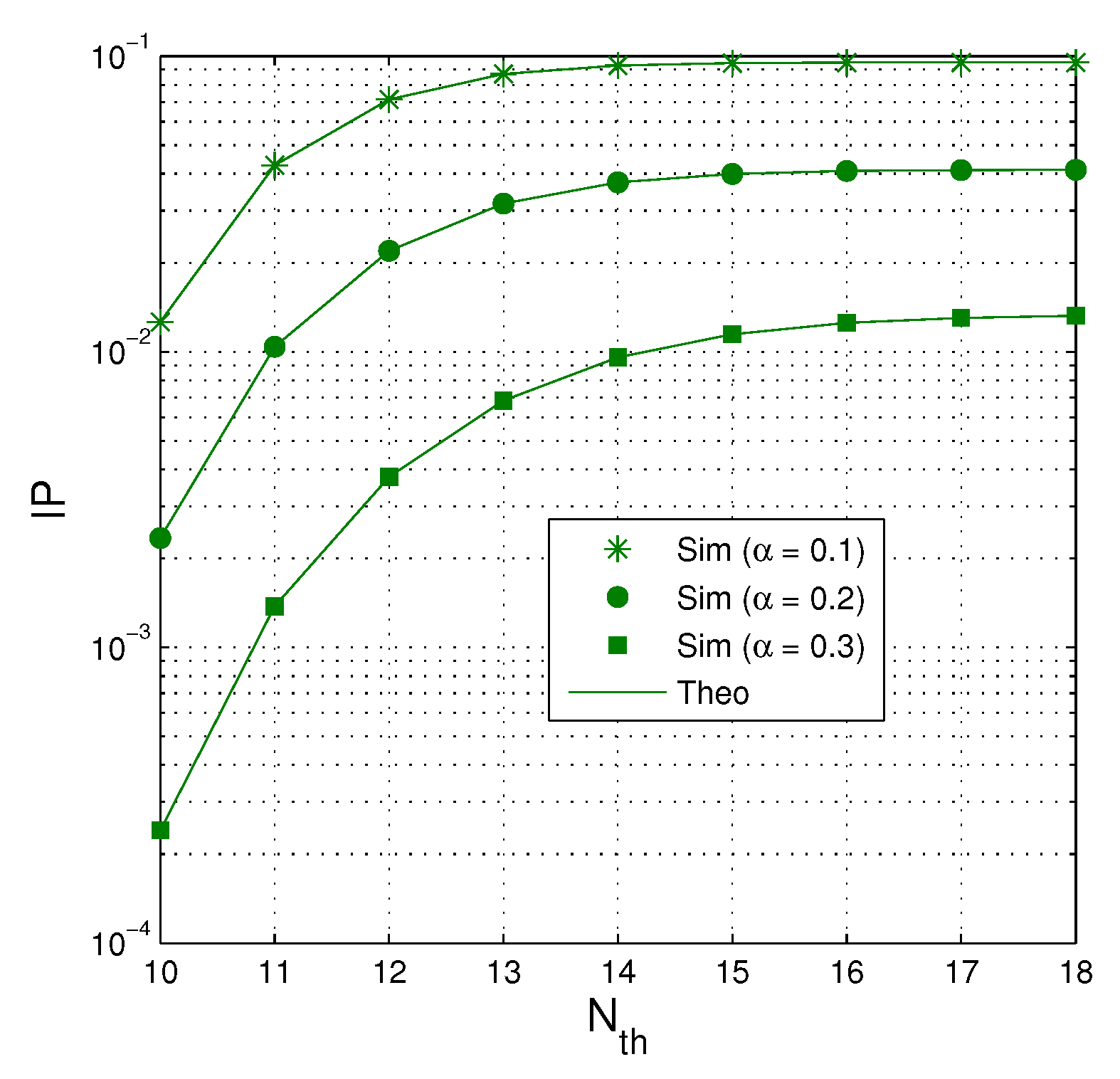
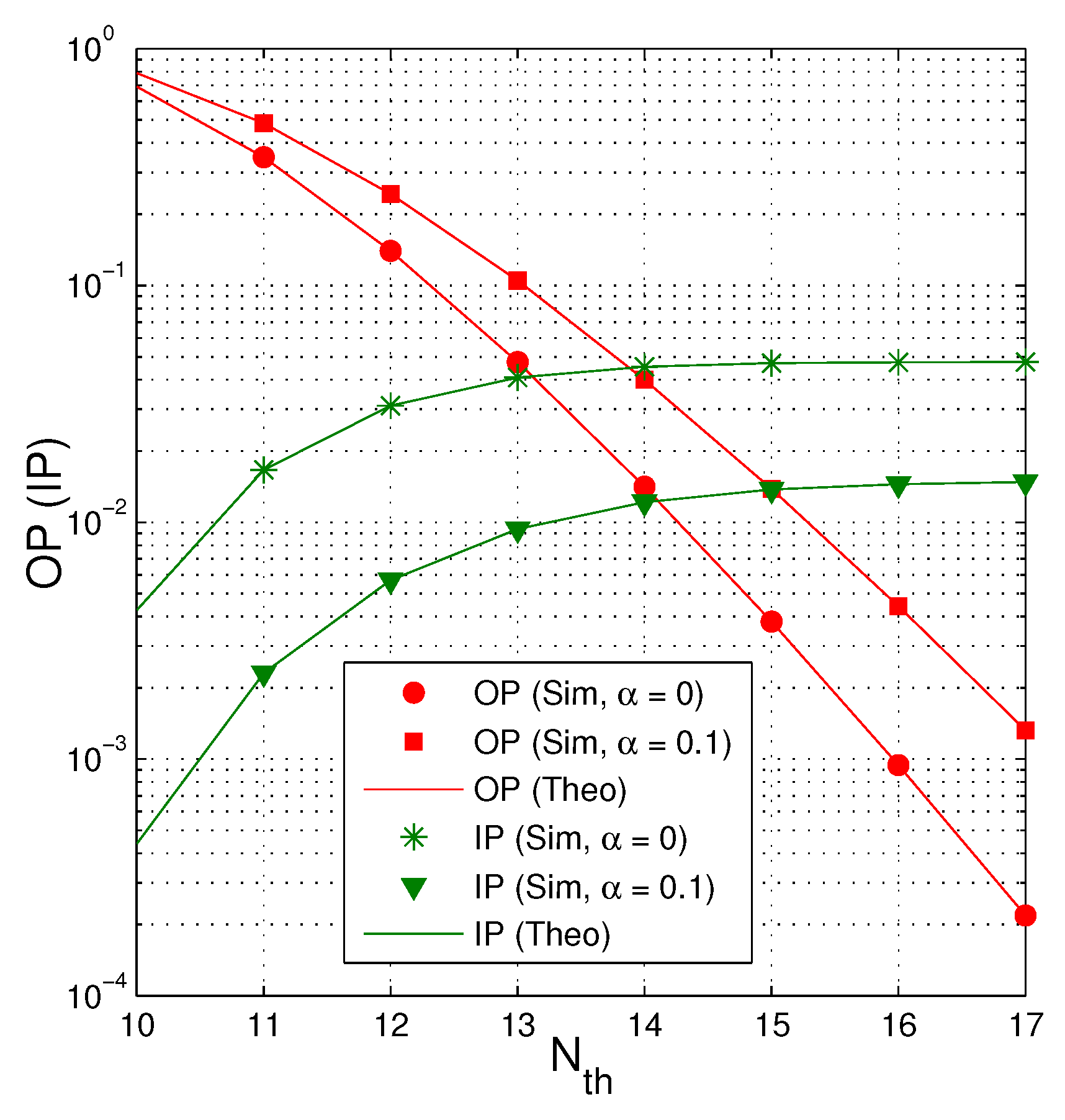
Figure 7 investigates impact of on the intercept probability as dB, , , and . It can be seen that the value of IP is higher when the number of increases. However, when the number of is high enough, IP converges to a constant. As expected, IP is lower when more time used for the EH phase (because the transmit power of the jammer is higher).
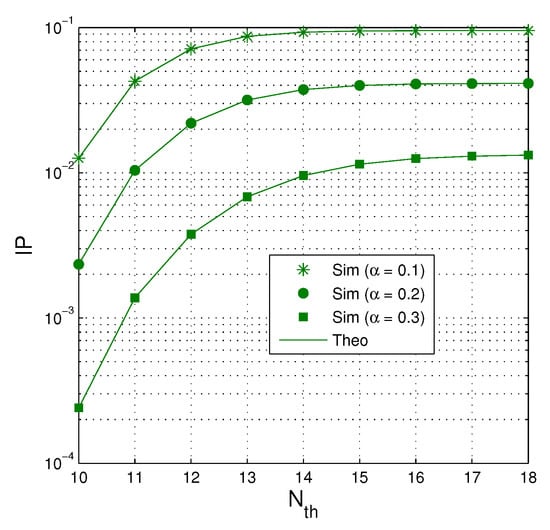
Figure 7.
IP as a function of when dB, , and .
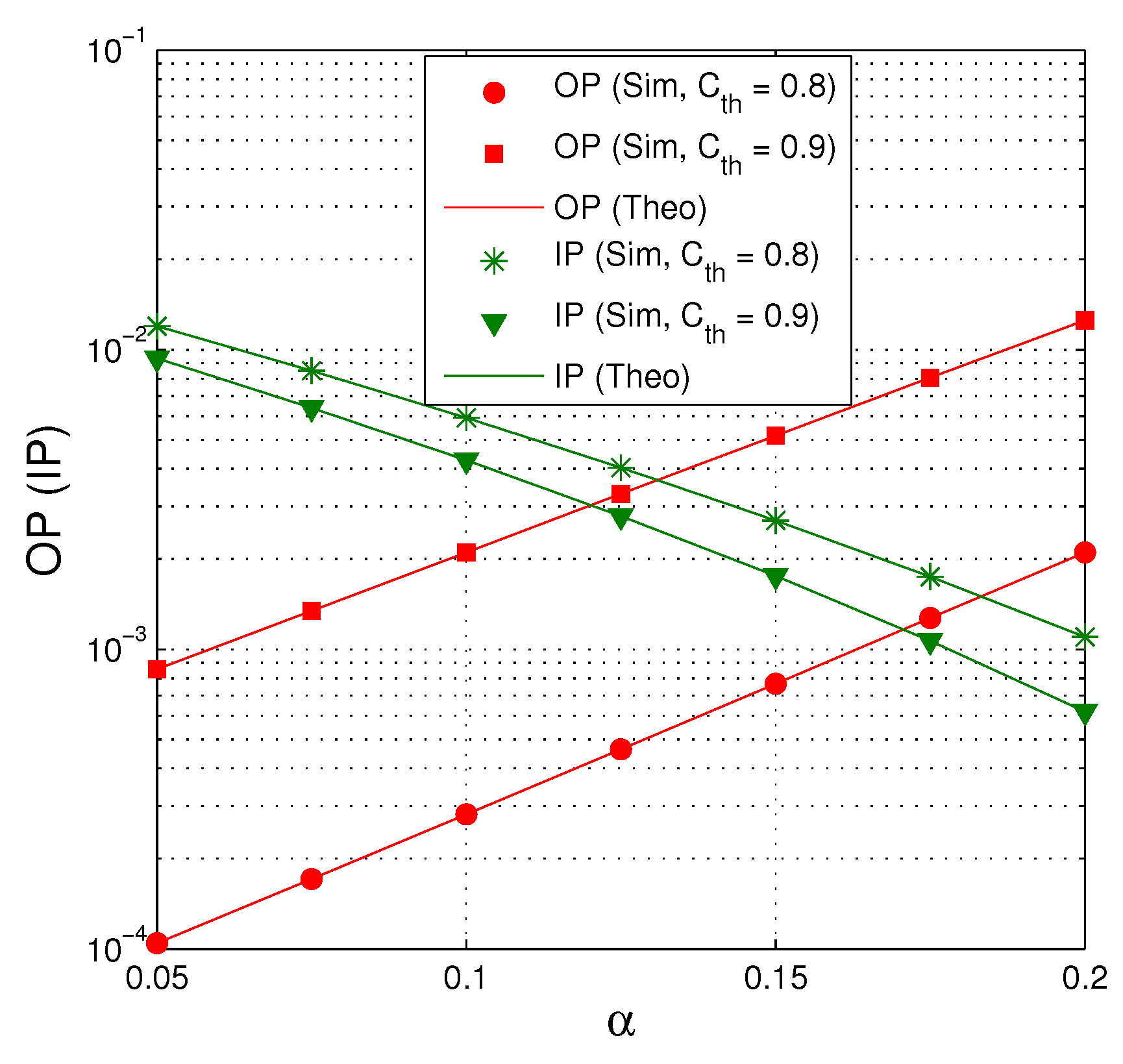
Figure 8 presents OP and IP as a function of when dB, , and . We can see that there exists a trade-off between OP and IP. Indeed, OP increases when increasing the value of , while IP decreases with higher value of . We can also see that when , OP is below when the value of is higher than (about) 0.15, but the intercept probability is higher than . In addition, OP significantly decreases as decreasing the value of .

Figure 8.
OP and IP as a function of when dB, , and .
Figure 9 shows the trade-off between OP and IP when dB, , and . As we can observe, when the cooperative jamming technique is not used , the OP value is lower but the IP one is higher. Similarly, to increase the reliability of the data transmission, we can increase the number of . However, the intercept possibility of the eavesdropper also increases with higher value of .
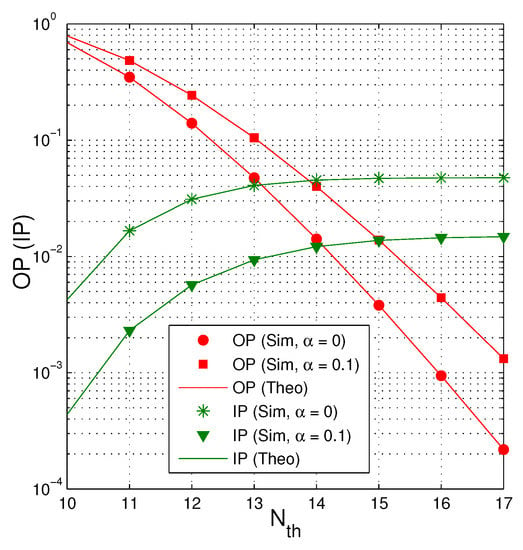
Figure 9.
OP and IP as a function of when dB, , and .
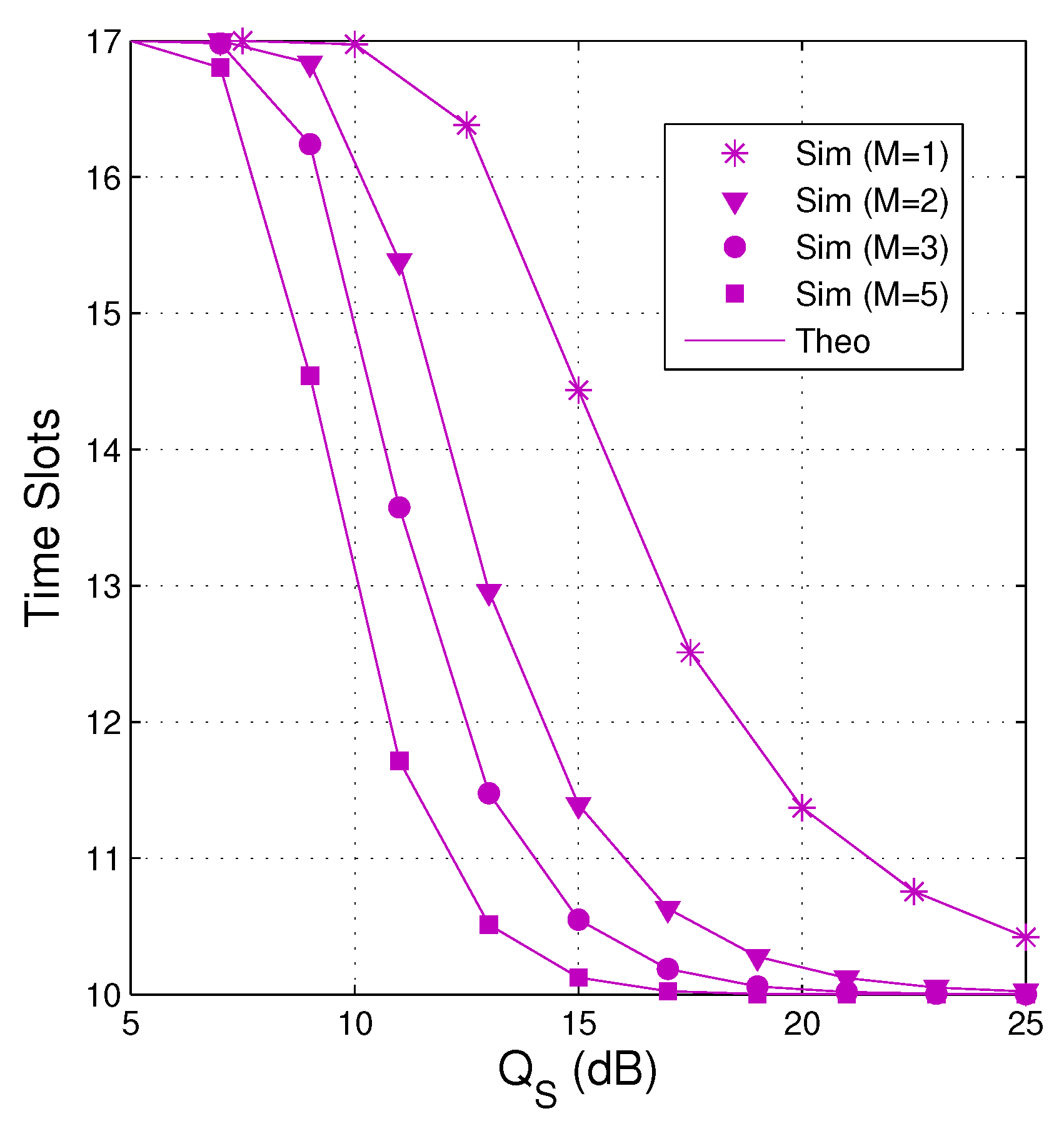
In Figure 10, we present average number of the time slots as a function of in dB when dB, , , and . We see that the number of time slots used decreases when increasing the number of antennas and the transmit power of the source. It is also seen that as the source has a single antenna (), the average number of time slots is much higher. Moreover, reducing the number of time slots means reducing the delay time and transmit power, which are an important metric of wireless communication systems.
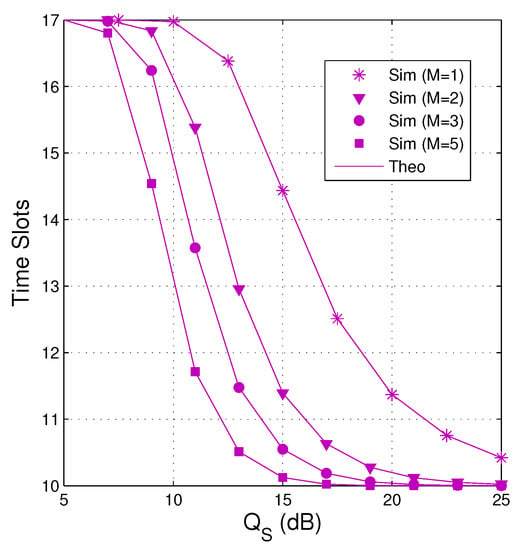
Figure 10.
Average number of time slots as a function of in dB when dB, , , and .
5. Conclusions
In this paper, we proposed an FC-based MISO scheme using the TAS and EH-based cooperative jamming techniques for the secure communication under the joint impact of hardware impairments and co-channel interference. The performance of the proposed scheme such as outage probability (OP), probability of successful and secure communication (SS), intercept probability (IP) and average number of the time slots was evaluated via both simulation and theory. The results presented that the hardware impairment levels, the co-channel interference, the fraction of time allocated for the EH phase and the number of transmit antennas at the source significantly impact on the system performance. Moreover, there exists a trade-off between the security and reliability, i.e., between OP and IP. Finally, the fraction of time allocated for the EH phase should be designed appropriately to optimize system performance.
Author Contributions
The main contributions of P.T.T. (Phu Tran Tin) and P.T.T. (Phuong T. Tran) were to create the main ideas and execute performance evaluation by simulations, while the main contributions of T.T.D., T.N.N., M.V. and N.Q.S. are to discuss, create, and advise the main ideas and performance evaluations together.
Funding
This research received support from the grant SGS reg. No. SP2019/41 conducted at VSB Technical University of Ostrava, Czech Republic, and is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2017.317.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Proof of Proposition 1
From (A1), we observe that if , then ; and if , we can rewrite (A1) as
where
Moreover, Equation (A2) can be rewritten by
Using the CDF obtained by (3), we have
Appendix B. Proof of Proposition 2
We observe from (A6) that if , then , and if , we can rewrite (A6) as
where
Setting , from (A7), we have
Substituting the CDF of and the PDF of provided by (1) into (A9), after some manipulations, which yields
Now, our objective is to calculate the integral in (A10). At first, we rewrite under the following form:
Next, we attempt to find the CDF of Z. Setting , the CDF of Z can be formulated by
Before calculating the CDF of Y, we note that Y is sum of the exponential RVs, i.e., and . Indeed, because and are exponential RVs whose parameters are and , respectively, hence and are also exponential RVs, and their parameters are and , respectively. Hence, the CDF of Y can be given as
where
Substituting (A13) into (A12), we obtain
Using (Equation (3.324.1) of [45]) for the corresponding integrals in (A15), we arrive at
where is modified Bessel function of the second kind [45]. Then, substituting (A16) into (A11), we obtain (A17) as
Next, changing variable , we can rewrite (A17) as
Applying (Equation (6.631.3) of [45]) for the corresponding integrals in (A18), we obtain
where is the Whittaker function [45].
Moreover, from (Equation (46) of [46]), we have
where is exponential integral function [45].
Combining (A19) and (A20), after some manipulations, we obtain
It is worth noting that to attain (A21), we used the following equation:
Finally, substituting (A21) into (A10), we obtain (19), and finish the proof.
References
- Wyner, A.D. The Wire-tap Channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Csiszar, I.; Korner, J. Broadcast Channels with Confidential Messages. IEEE Trans. Inf. Theory 1978, 2, 339–348. [Google Scholar] [CrossRef]
- Liu, R.; Maric, I.; Spasojevic, P.; Yates, R.D. Discrete Memoryless Interference and Broadcast Channels with Conffdential Messages: Secrecy Rate Regions. IEEE Trans. Inf. Theory 2008, 2, 2493–2507. [Google Scholar] [CrossRef]
- Gopala, P.K.; Lai, L.; Gamal, H.E. On the Secrecy Capacity of Fading Channels. IEEE Trans. Inf. Theory 2008, 2, 4687–4698. [Google Scholar] [CrossRef]
- Zhang, J.; Duong, T.Q.; Woods, R.; Marshall, A. Securing Wireless Communications of the Internet of Things from the Physical Layer, An Overview. Entropy 2017, 19, 420. [Google Scholar] [CrossRef]
- Sun, L.; Du, Q. A Review of Physical Layer Security Techniques for Internet of Things: Challenges and Solutions. Entropy 2018, 2, 730. [Google Scholar] [CrossRef]
- Tin, P.T.; Hung, D.T.; Tan, N.N.; Duy, T.T.; Voznak, M. Secrecy Performance Enhancement for Underlay Cognitive Radio Networks Employing Cooperative Multi-hop Transmission With and Without Presence of Hardware Impairments. Entropy 2019, 21, 217. [Google Scholar] [CrossRef]
- Tin, P.T.; Nam, P.M.; Duy, T.T.; Phuong, T.T.; Voznak, M. Secrecy Performance of TAS/SC-based Multi-hop Harvest-to-Transmit Cognitive WSNs under Joint Constraint of Interference and Hardware Imperfection. Sensors 2019, 19, 1160. [Google Scholar] [CrossRef] [PubMed]
- Zhang, T.; Cai, Y.; Huang, Y.; Duong, T.Q.; Yang, W. Secure Transmission in Cognitive MIMO Relaying Networks With Outdated Channel State Information. IEEE Access 2016, 4, 8212–8224. [Google Scholar] [CrossRef]
- Huang, Y.; Wang, J.; Zhong, C.; Duong, T.Q.; Karagiannidis, G.K. Secure Transmission in Cooperative Relaying Networks with Multiple Antennas. IEEE Trans. Wirel. Commun. 2016, 2, 6843–6856. [Google Scholar] [CrossRef]
- Yang, M.; Guo, D.; Huang, Y.; Duong, T.Q.; Zhang, B. Secure Multiuser Scheduling in Downlink Dual-hop Regenerative Relay Networks over Nakagami-m Fading Channels. IEEE Trans. Wirel. Commun. 2016, 2, 8009–8024. [Google Scholar] [CrossRef]
- Zhao, R.; Lin, H.; He, Y.-C.; Chen, D.-H.; Huang, Y.; Yang, L. Secrecy Performance of Transmit Antenna Selection for MIMO Relay Systems with Outdated CSI. IEEE Trans. Commun. 2018, 2, 546–559. [Google Scholar] [CrossRef]
- Mo, J.; Tao, M.; Liu, L. Relay Placement for Physical Layer Security: A Secure Connection Perspective. IEEE Commun. Lett. 2012, 2, 878–881. [Google Scholar]
- Lee, J.-H.; Sohn, I.; Kim, Y.-H. Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors 2016, 2, 1726. [Google Scholar] [CrossRef] [PubMed]
- Keshav, S.; Ku, M.-L.; Biswas, S.; Ratnarajah, T. Energy-Efficient Subcarrier Pairing and Power Allocation for DF Relay Networks with an Eavesdropper. Energies 2017, 2, 1953. [Google Scholar]
- Hieu, T.D.; Duy, T.T.; Kim, B.-S. Performance Enhancement for Multi-hop Harvest-to-Transmit WSNs with Path-Selection Methods in Presence of Eavesdroppers and Hardware Noises. IEEE Sens. J. 2018, 2, 5173–5186. [Google Scholar] [CrossRef]
- Cao, K.; Cai, K.; Wu, Y.; Yang, W. Cooperative Jamming for Secure Communication with Finite Alphabet Inputs. IEEE Commun. Lett. 2017, 2, 2025–2028. [Google Scholar] [CrossRef]
- Kang, J.M.; Yang, J.; Ha, J.; Kim, I.M. Joint Design of Optimal Precoding and Cooperative Jamming for Multiuser Secure Broadcast Systems. IEEE Trans. Veh. Technol. 2017, 2, 10551–10556. [Google Scholar] [CrossRef]
- Ma, H.; Cheng, J.; Wang, X.; Ma, P. Robust MISO Beamforming with Cooperative Jamming for Secure Transmission From Perspectives of QoS and Secrecy Rate. IEEE Trans. Commun. 2018, 2, 767–780. [Google Scholar] [CrossRef]
- Zhang, G.; Xu, J.; Wu, Q.; Cui, M.; Li, X.; Lin, F. Wireless Powered Cooperative Jamming for Secure OFDM System. IEEE Trans. Veh. Technol. 2018, 2, 1331–1346. [Google Scholar] [CrossRef]
- Nasir, A.A.; Zhou, X.; Durrani, S.; Kennedy, R.A. Relaying Protocols for Wireless Energy Harvesting and Information Processing. IEEE Trans. Wirel. Commun. 2013, 2, 3622–3636. [Google Scholar] [CrossRef]
- Atapattu, S.; Evans, J. Optimal Energy Harvesting Protocols for Wireless Relay Networks. IEEE Trans. Wirel. Commun. 2016, 2, 5789–5803. [Google Scholar] [CrossRef]
- Wang, L.; Wong, K.K.; Jin, S.; Zheng, G.; Heath, R.W. A New Look at Physical Layer Security, Caching, and Wireless Energy Harvesting for Heterogeneous Ultra-Dense Networks. IEEE Commun. Mag. 2018, 2, 49–55. [Google Scholar] [CrossRef]
- Chang, S.; Li, J.; Fu, X.; Zhang, L. Energy Harvesting for Physical Layer Security in Cooperative Networks Based on Compressed Sensing. Entropy 2017, 19, 462. [Google Scholar] [CrossRef]
- Xu, C.; Zheng, M.; Liang, W.; Yu, H.; Liang, Y.C. Outage Performance of Underlay Multihop Cognitive Relay Networks with Energy Harvesting. IEEE Commun. Lett. 2016, 2, 1148–1151. [Google Scholar] [CrossRef]
- Xu, C.; Zheng, M.; Liang, W.; Yu, H.; Liang, Y.C. End-to-end Throughput Maximization for Underlay Multi-hop Cognitive Radio Networks with RF Energy Harvesting. IEEE Trans. Wirel. Commun. 2017, 2, 3561–3572. [Google Scholar] [CrossRef]
- Zhu, G.; Zhong, C.; Suraweera, H.A.; Karagiannidis, G.K.; Zhang, Z.; Tsiftsis, T.A. Wireless Information and Power Transfer in Relay Systems with Multiple Antennas and Interference. IEEE Trans. Commun. 2015, 2, 1400–1418. [Google Scholar] [CrossRef]
- Chen, E.; Xia, M.; Da Costa, D.; Aissa, S. Multi-hop Cooperative Relaying with Energy Harvesting from Co-Channel Interferences. IEEE Commun. Lett. 2017, 2, 1199–1202. [Google Scholar] [CrossRef]
- Liu, M.; Liu, Y. Power Allocation for Secure SWIPT Systems with Wireless-Powered Cooperative Jamming. IEEE Commun. Lett. 2017, 2, 1353–1356. [Google Scholar] [CrossRef]
- MacKay, D. Fountain Codes. IEE Proc. Commun. 2005, 2, 1331–1346. [Google Scholar] [CrossRef]
- Castura, J.; Mao, Y. Rateless Coding over Fading Channels. IEEE Commun. Lett. 2006, 2, 46–48. [Google Scholar] [CrossRef]
- Nguyen, H.D.T.; Tran, L.N.; Hong, E.K. On Transmission Efficiency for Wireless Broadcast Using Network Coding and Fountain Codes. IEEE Commun. Lett. 2011, 2, 569–571. [Google Scholar] [CrossRef]
- Yue, J.; Lin, Z.; Vucetic, B. Distributed Fountain Codes With Adaptive Unequal Error Protection in Wireless Relay Networks. IEEE Trans. Wirel. Commun. 2014, 2, 4220–4231. [Google Scholar] [CrossRef]
- Niu, H.; Iwai, M.; Sezaki, K.; Sun, L.; Du, Q. Exploiting Fountain Codes for Secure Wireless Delivery. IEEE Commun. Lett. 2014, 2, 777–780. [Google Scholar] [CrossRef]
- Li, W.; Du, Q.; Sun, L.; Ren, P.; Wang, Y. Security Enhanced via Dynamic Fountain Code Design for Wireless Delivery. In Proceedings of the IEEE 2016 IEEE Wireless Communications and Networking Conference, Doha, Qatar, 3–6 April 2016; pp. 1–6. [Google Scholar]
- Sun, L.; Ren, P.; Du, Q.; Wang, Y. Fountain-coding Aided Strategy for Secure Cooperative Transmission in Industrial Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2016, 2, 291–300. [Google Scholar] [CrossRef]
- Du, Q.; Xu, Y.; Li, W.; Song, H. Security Enhancement for Multicast over Internet of Things by Dynamically Constructed Fountain Codes. Wirel. Commun. Mob. Comput. 2018, 2018, 8404219. [Google Scholar] [CrossRef]
- Hung, D.T.; Duy, T.T.; Trinh, D.Q.; Bao, V.N.Q. Secrecy Performance Evaluation of TAS Protocol Exploiting Fountain Codes and Cooperative Jamming under Impact of Hardware Impairments. In Proceedings of the 2nd International Conference on Recent Advances in Signal Processing, Telecommunications & Computing (SigTelCom), Ho Chi Minh City, Vietnam, 29–31 January 2018; pp. 164–169. [Google Scholar]
- Hung, D.T.; Duy, T.T.; Trinh, D.Q.; Bao, V.N.Q.; Hanh, T. Security-Reliability Analysis of Power Beacon-Assisted Multi-hop Relaying Networks Exploiting Fountain Codes with Hardware Imperfection. In Proceedings of the International Conference on Advanced Technologies for Communications (ATC), Ho Chi Minh City, Vietnam, 18–20 October 2018; pp. 354–359. [Google Scholar]
- Mokhtar, M.; Gomaa, A.; Al-Dhahir, N. OFDM AF Relaying under I/Q Imbalance: Performance Analysis and Baseband Compensation. IEEE Trans. Commun. 2013, 2, 1304–1313. [Google Scholar] [CrossRef]
- Björnson, E.; Matthaiou, M.; Debbah, M. A New Look at Dual-Hop Relaying: Performance Limits with Hardware Impairments. IEEE Trans. Commun. 2013, 2, 4512–4525. [Google Scholar] [CrossRef]
- Son, P.N.; Kong, H.Y. Energy-Harvesting Decode-and-Forward Relaying under Hardware Impairments. Wirel. Pers. Commun. 2017, 2, 6381–6395. [Google Scholar] [CrossRef]
- Solanki, S.; Upadhyay, P.K.; da Costa, D.B.; Bithas, P.S.; Kanatas, A.G.; Dias, U.S. Joint Impact of RF Hardware Impairments and Channel Estimation Errors in Spectrum Sharing Multiple-Relay Networks. IEEE Trans. Commun. 2018, 2, 3809–3824. [Google Scholar] [CrossRef]
- Zarei, S.; Gerstacker, W.H.; Aulin, J.; Schober, R. Multi-Cell Massive MIMO Systems with Hardware Impairments: Uplink-Downlink Duality and Downlink Precoding. IEEE Trans. Wirel. Commun. 2017, 2, 5115–5130. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Elsevier Inc.: San Diego, CA, USA, 2007. [Google Scholar]
- Duy, T.T.; Alexandropoulos, G.C.; Vu, T.T.; Vo, N.-S.; Duong, T.Q. Outage Performance of Cognitive Cooperative Networks with Relay Selection over Double-Rayleigh Fading Channels. IET Commun. 2016, 2, 57–64. [Google Scholar] [CrossRef]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).