1. Introduction
The currency we know in modern society and businesses has transitioned over various stages starting from the barter system [
1] for exchanging goods/services to commodity money such as gold and silver coins to paper-printed currency. However, paper currency has several drawbacks such as lack of transparency, excessive anonymity, and environmental impact, including carbon footprint [
2] and counterfeiting issues [
3]. In the last two decades, blockchain-based decentralized cryptocurrencies have appeared, fostering progress in areas such as governance, voting systems, supply chain management, decentralized autonomous organizations, and the creation of Central Bank Digital Currencies (CBDCs). A CBDC [
4] is a digital currency issued by a centralised authority. CBDC is defined as a digital form of fiat money issued by a central bank, adhering to standard rules and overcoming the limitations of paper currency. CBDC offers several benefits [
5,
6,
7] such as reduced operational costs, enhanced security, and increased transparency, contributing to financial inclusion and sustainability [
3]. The paper-currency system offers digital services, also known as digital fiat currency (DFC), allowing balance transfers via telecom connectivity [
3]. However, if connectivity is lost, reliance on paper currency ensures transaction success. With the advent of Central Bank Digital Currency (CBDC), a new challenge arises in situations where internet connectivity is either absent or poor; because of its fully digital and centralised nature, CBDC relies on active telecom/internet connectivity [
3] for a transaction/transfer to occur. Internet or telecom connectivity remains a challenge not only in the developing/underdeveloped world but also, for various reasons, in the developed world. For example, frequent bank-server downtimes for maintenance, coupled with internet outages during natural disasters, exacerbate this issue [
8]. Thus, such dependency on network connectivity limits spending freedom and hence prompts for an offline-payment transaction system to ensure uninterrupted transactions even without network connectivity [
3].
Currently, there are two main methods for offline payments [
9]: those that rely on smart cards [
10] and those that use smartphones [
11,
12,
13,
14]. We have chosen to focus on smartphone-based payments for their clear advantages over the smart card approach, such as greater convenience and ease of carrying. In contrast, smart card transactions require both parties to have their cards and to use a Point of Sale (POS) terminal. This means that for any transaction to happen, a bulky terminal device is necessary, making it less practical since it is an additional item to carry around. Smartphone-based payments streamline this process, making transactions simpler and more accessible.
In response, we have developed a smartphone-based offline payment system called Peer-to-Peer Extended Digital Offline Payment System (‘ElasticPay’), which prioritizes security measures [
9] and introduces an additional feature of
preserving user privacy in offline situations. It is meticulously crafted to support transactions using both Central Bank Digital Currencies (CBDCs) and various forms of digital money. This dual compatibility ensures that our solution is versatile, future-proof, and backwards-compatible, thus catering to all types of digital transactions while ensuring security and privacy in offline environments. Privacy is the most sought-after feature in a digital euro [
15], highlighting that the need for privacy extends beyond just this currency to all digital transactions. The main features of our system include comprehensive security measures [
9], immediate settlement, extended support, privacy protection, and transaction failure recovery.
Throughout the remainder of this paper, the terms “telecom connectivity” and “internet connectivity” will be collectively referred to as “network connectivity” for brevity and clarity. This unified term encompasses all forms of telecommunications and internet connections that facilitate digital communication and transactions.
The main contributions of this paper are:
Enhanced Privacy Protection: We enhance the privacy of both the sender and receiver in offline payment transactions.
Robust Security Features: While Trusted Execution Environments (TEEs) are widely used to enhance security, we propose integrating the Trusted Platform Module (TPM) with TEE. This integration will further strengthen the system’s resilience, especially in offline environments, against various attacks.
Comprehensive Explanation: This paper provides a clear and detailed explanation of the mechanisms and processes involved in offline digital payment transactions, offering valuable insights into their implementation and benefits.
The rest of this paper is organized as follows:
Section 2 gives preliminary concepts and definitions necessary for understanding the subsequent presentation about our proposed solution. The proposed offline payment system is presented in
Section 3.
Section 4 presents the experimental setup and particulars on experiments carried out. The related work is given in
Section 5, while
Section 6 concludes the paper with a discussion about the contributions of our work and directions for future research in enhancing digital payment systems.
2. Preliminaries
This section elaborates on the basic concepts and definitions that help readers understand subsequent discussions on our proposed solution called ElasticPay. The financial system is supported by three key stakeholders, and they are central banks, intermediary banks, and customers. The central bank issues currency, facilitates credit, regulates monetary policy, maintains financial stability, and oversees the banking system. Intermediary banks promote financial inclusivity, manage deposits, distribute loans, ensure regulatory compliance, provide payment services, and facilitate fund transfers. Ultimately, customers—individuals, businesses, and organizations—drive economic activity by conducting transactions via intermediary banks, including deposits, withdrawals, loans, payments, and investments. Throughout this paper, the term ‘bank’ is used to refer to an intermediary bank, while the term ‘central bank’ is used to refer specifically to the central bank.
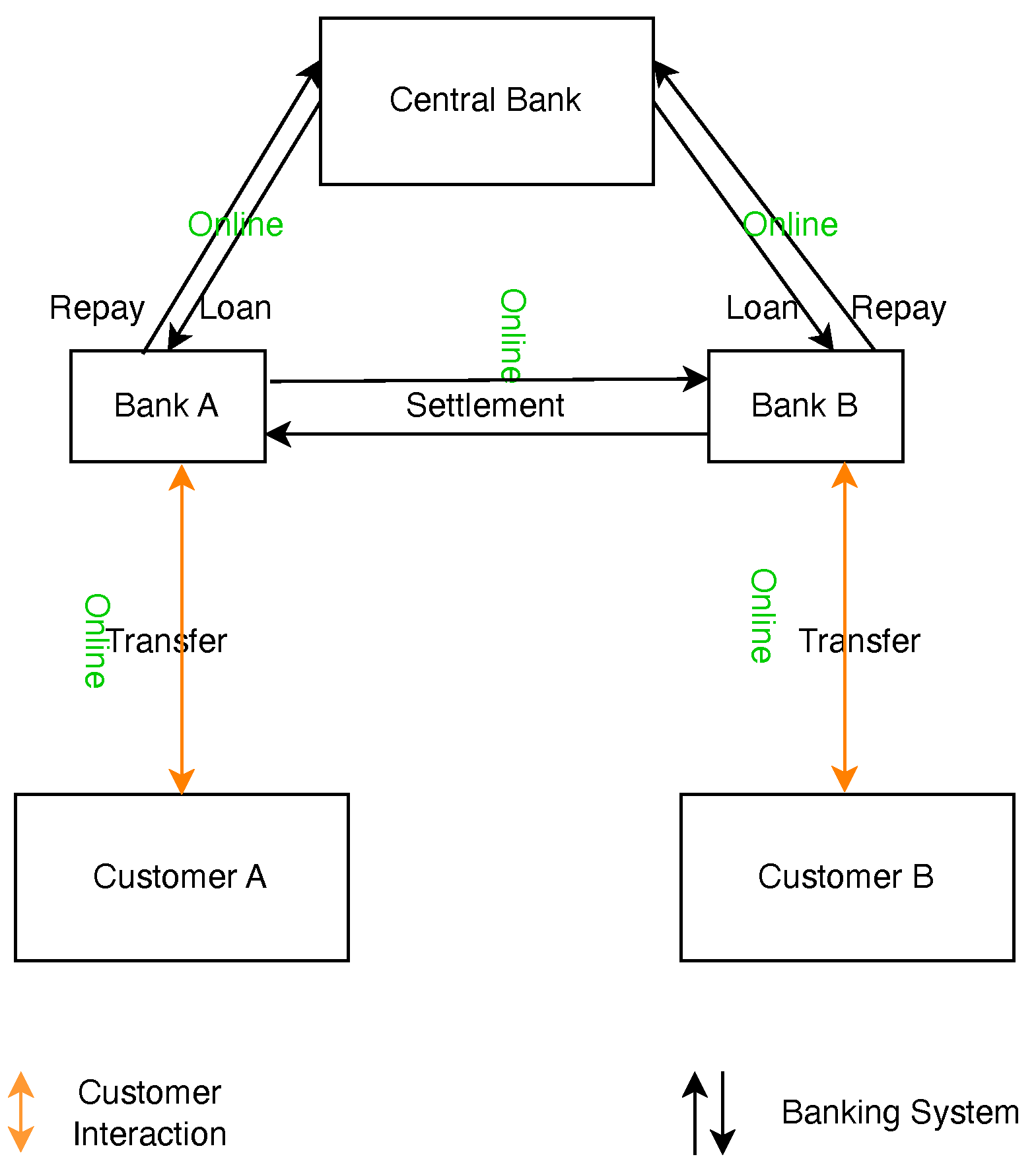
In a typical online banking scenario, such as when a client (Customer A) at one bank wishes to send funds to another (Customer B) at a different bank, as depicted in
Figure 1, the process follows these steps:
Initiation: The sender (Customer A) initiates the transaction through their bank’s digital platform.
Verification: The originating bank verifies transaction details against account status and customer permissions.
Interbank Communication: The transaction details are sent to a central processing system or directly to the recipient’s bank, which may involve interaction with the central bank if CBDCs are utilized.
Completion: Upon validation, the recipient’s (Customer B) bank credits their account, thereby concluding the transaction process.
Initiating an offline transaction requires a sufficient balance in the sender’s device-stored offline wallet, which is pre-funded by transferring funds from their primary bank account. To enable the exchange between sender and receiver, the system utilizes inherent wireless communication protocols like Bluetooth or NFC, obviating the need for a network connection, thus characterizing the truly offline nature of the payment process.
Online transactions typically involve intermediaries, but our focus is on offline payments, where only the sender and receiver are involved. This setup presents unique challenges, as it increases the potential for attacks. There is a chance that either party might intentionally manipulate the transaction to their advantage, whether to benefit jointly or individually. Achieving integrity, maintaining all transaction properties, and effectively mitigating potential attacks pose significant challenges in such environments.
The offline systems heavily rely on robust encryption technology both in hardware and software. Cryptography plays a crucial role in safeguarding transactions and communications in both digital and physical payment systems. Cryptography guarantees the confidentiality and integrity of data exchanged between transaction parties, facilitates the authentication of their identities, and ensures non-repudiation, preventing any party from denying their involvement in the transaction. Among the key cryptographic frameworks is the Public Key Infrastructure (PKI) [
16], where users are assigned a pair of keys. These include a publicly known key called
Public-key and a privately held key called
Private-key that remains secret. PKI allows securing communication channels and data, authenticating the identity of communicators, and managing the digital certificates to validate user keys. Two essential cryptographic constructs, digital signatures [
17] and digital certificates [
18], fortify the security framework. A Digital Signature acts much like a virtual fingerprint, a unique identifier for a person or entity, established using a private key and verifiable via its corresponding public key. This assures that the signatory is genuine and that the signed data are nottampered with from their inception. Analogously, a digital certificate is akin to a digital ID card, binding a public key with its owner’s identity details, such as name and issuing authority, and is critical for affirming identities in electronic transactions. However, the effectiveness of cryptography depends significantly on the secrecy maintained around these cryptographic keys.
Given the risks associated with software-based [
19] storage of cryptographic keys and operations, because manipulation is possible if the root key is compromised and also in functional operations like hashing, encryption and decryption, it is advisable to utilize hardware-based security mechanisms [
20]. There is a hardware-based approach called a Secure Element (SE) [
20] that offers robust protection for storing cryptographic keys. A Secure Element (SE) is a tamper-resistant hardware component designed to securely store sensitive data, such as cryptographic keys, passwords, and personal information, and to perform cryptographic operations in a way that protects these data from unauthorized access or tampering. It is resilient against sophisticated attacks such as ion beams, microchip decapsulation, and scanning microscopes [
21]. Besides storage, SEs produce truly random numbers, which eliminates key duplication or theft [
22].
Beyond key protection, ensuring the integrity of sensitive payment processes is also crucial. Most, if not all, of the payment solutions have application logic that can be manipulated on the user’s device and poses a severe threat. The Trusted Execution Environment (TEE) [
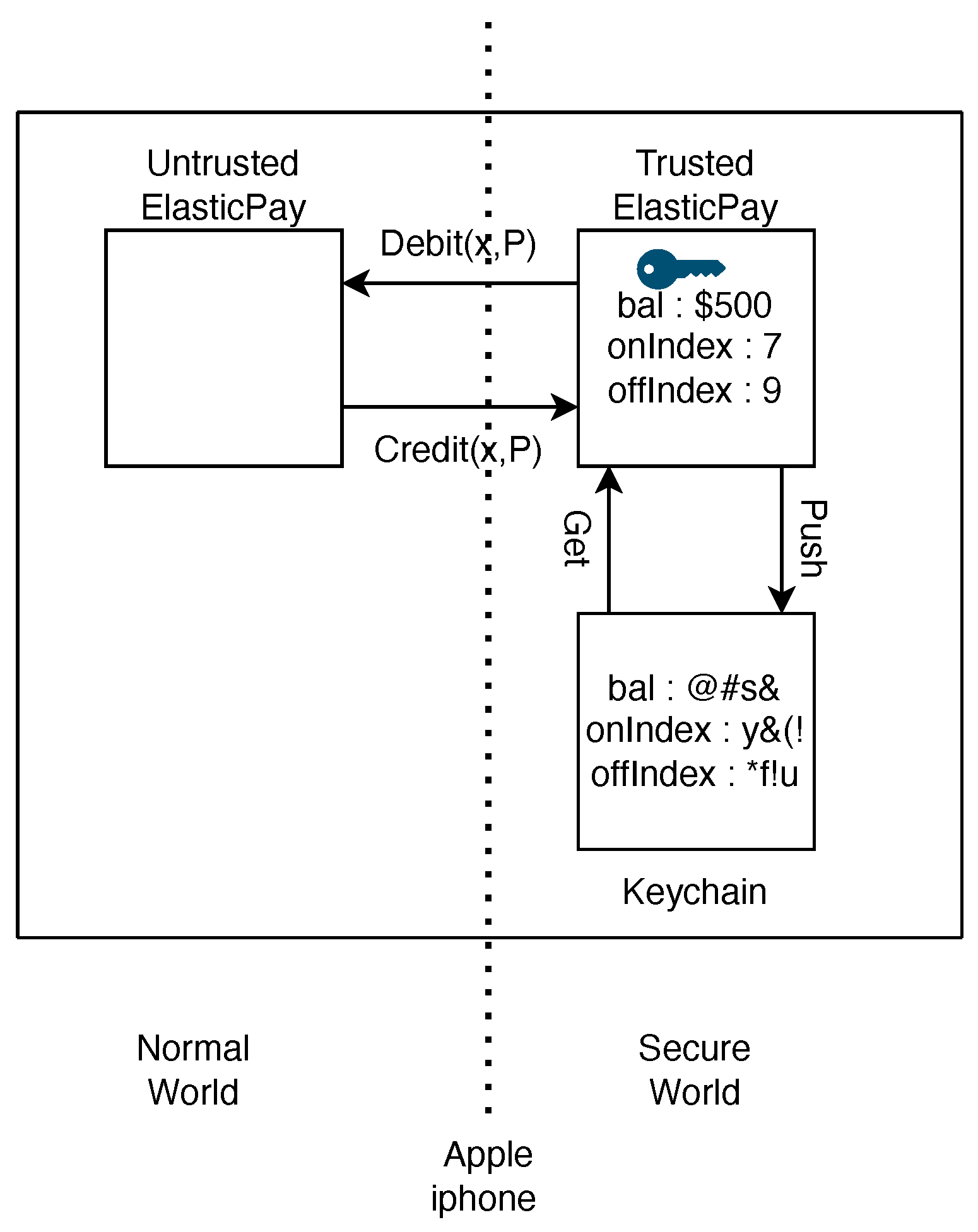
23] provides a solution against this threat. A Trusted Execution Environment (TEE) is a secure area within a main processor. It ensures that the code and data loaded inside it are protected with respect to confidentiality and integrity. The TEE is an isolated mode of operation in which critical code is run and hence cannot be manipulated. This isolation of the TEE makes it immune to theft. For a visual representation of this architecture, refer to
Figure 2. The TEE depicted in
Figure 2 corresponds to ARM’s architecture. The essence of a Trusted Execution Environment (TEE) is to strategically divide hardware resources, including memory segments, buses, peripherals, and interrupts into two distinct zones: the secure world and the non-secure world. The secure world runs a trusted OS for sensitive operations and houses trusted applications, isolated from the normal world’s Rich Execution Environment (REE) [
24] that operates a standard OS and untrusted applications. The communication between these worlds is facilitated through a secure and controlled interface, ensuring data integrity and confidentiality, thus maintaining robust security even if the normal OS is compromised. In summary, the TEE protects sensitive code/data and their execution/storage from threats and attacks emanating from the OS layer [
24]. Intel SGX [
25], AMD Secure Encrypted Virtualization (SEV) [
26], and ARM’s TrustZone [
27] are some of the most widely recognized commercial implementations of Trusted Execution Environments (TEEs). In contrast, Keystone [
28] stands out as a prominent open-source TEE solution built on the RISC-V architecture, offering a flexible and secure alternative for developers. In the early stages, several vulnerabilities were identified and exploited within TEEs, leading to various security breaches and attacks [
5,
29,
30]. The effectiveness of a Trusted Execution Environment (TEE) relies on the secure loading of a trusted operating system (TOS). A compromised TOS could jeopardize the entire TEE’s security, making it crucial to verify the OS’s integrity before execution. This is where a Trusted Platform Module (TPM) [
31] plays a vital role. A TPM is a hardware chip that acts as a root of trust [
32]. During the boot process, known as measured boot [
33], it takes cryptographic measurements of system components like the TOS. These measurements are stored in Platform Configuration Registers (PCRs) within the TPM [
34]. Initially, the Trusted Platform Module (TPM) functions as a hardware root of trust, performing an essential role in the security architecture by first verifying the integrity of the hardware to ensure it has not been tampered with or compromised. Subsequently, the TPM extends this verification process to the firmware, followed by the trusted operating system, and ultimately the rich operating system. Each of these stages is secured through the cryptographic validation of hashes using Platform Configuration Registers (PCRs). This multi-layered approach is foundational in securing the device, as it establishes a robust chain of trust, ensuring the integrity of both hardware and software components. Having a Trusted Platform Module (TPM), Secure Element (SE), and a Trusted Execution Environment (TEE) significantly strengthens the security within the device and processes executed in the device.
Every transaction involves two parties. These parties carry out a transaction using digital devices. For absolute security purposes, it becomes mandatory to establish that every participant and device is trustworthy in the first hand. Imagine if there is a mechanism through which a device can make trustworthy claims about itself with another party. This is what is called remote attestation.
Remote attestation verifies the integrity and trustworthiness of a remote system (attester or prover) to another party (verifier). It confirms that the remote system is running the expected software in a secure and unmodified state.
Let us see the mechanism:
The attester generates a report containing measurements of its hardware and software configuration (boot sequence, OS, running applications, etc.).
This report is cryptographically signed to ensure its authenticity and integrity.
The attester sends the report to the verifier.
The verifier checks the signature and compares the measurements to known good reference values.
If there is a match, the verifier gains trust in the system’s state.
Thus, the above process lets us conclude if the prover’s device can be trusted for secure transactions.
Let us try to understand Central Bank Digital Currencies (CBDC) [
4]. There are two different implementations for CBDCs. The first is a direct, one-tier system where the central bank is the sole manager and distributor of currency to the people. The second and more favoured model is the two-tier system, also called retail CBDC [
35], where the central bank issues a wholesale CBDC to intermediary banks, which in turn distribute such retail CBDC to the populace. This model has intermediary banks, which are pivotal in fostering and stabilizing the economy, making use of their sophisticated infrastructure.
Figure 3 shows these architectures.
In the discussion of CBDC banking models, the two-tier model stands out for its widespread acceptance and implementation within the financial sector. Although the technical underpinnings of Central Bank Digital Currencies (CBDCs) differ significantly, from a consumer perspective, the process resembles traditional online financial transactions.
There are five security requirements [
9] to be met by a CBDC so that it qualifies as a robust payment system:
prevention of double-spending,
unforgeability,
non-repudiation,
verifiability, and
maintaining anonymity. No double-spending ensures that digital currencies cannot be illicitly replicated and spent multiple times. Unforgeability protects against the creation of counterfeit currency or the impersonation of entities within the system. Anonymity is a feature that offline payment systems should have; also, providing complete anonymity in CBDCs can cause the same money laundering, tax evasion, and illegal activity problems that happen in conventional financial systems. So, ‘pseudonymity’ [
36] is a suitable thing to consider. Our proposed ElasticPay solution is designed to seamlessly integrate with both Central Bank Digital Currencies (CBDCs) and existing digital fiat currency (DFC) systems. Since the transaction flow for both CBDC and DFC is fundamentally similar in the online environment, our approach is adaptable to both systems. For the remainder of this paper, we will refer to both systems collectively as “online banking transactions”, emphasizing their shared digital nature and the fact that our solution caters to both.
3. Our Proposed Solution
In addressing security against the above attacks within the proposed offline digital payment system, we propose a synergic combination of technologies—Trusted Platform Module (TPM) [
31], Trusted Execution Environment (TEE), and Secure Element (SE). As attacks can be devised with device bootup, compromising operations in the processor and key theft, the proposed trio combination mitigates potential attacks during these phases.
This integrated approach ensures that only authorized applications can access their designated data, effectively shielding them against potential security breaches, even those that might involve sophisticated hardware-based attacks. Moving beyond software-only security solutions is essential due to their limitations in countering advanced cyber threats, highlighting the need for substantial hardware security mechanisms.
The comprehensive security strategy extends to the entire device, securing every interaction and transaction. The TPM, TEE, and SE together create a robust defense system, essential for maintaining data integrity and confidentiality throughout the device’s operation.
The integration of these technologies is increasingly becoming a standard in the smartphone industry. Many new and existing devices on the market are equipped with these features, demonstrating a commitment to high security standards and providing users with the confidence to safely engage in digital transactions.
While the TPM, SE, and TEE can operate independently, their combined use can enhance the security of a device significantly. In our analysis, the concept of ‘trust’ within a device spans its operating system, applications and physical hardware, all of which are expected to meet strict security protocols. A device featuring a Trusted Execution Environment (TEE), Secure Element (SE), and Trusted Platform Module (TPM) clearly demonstrates such trustworthiness.
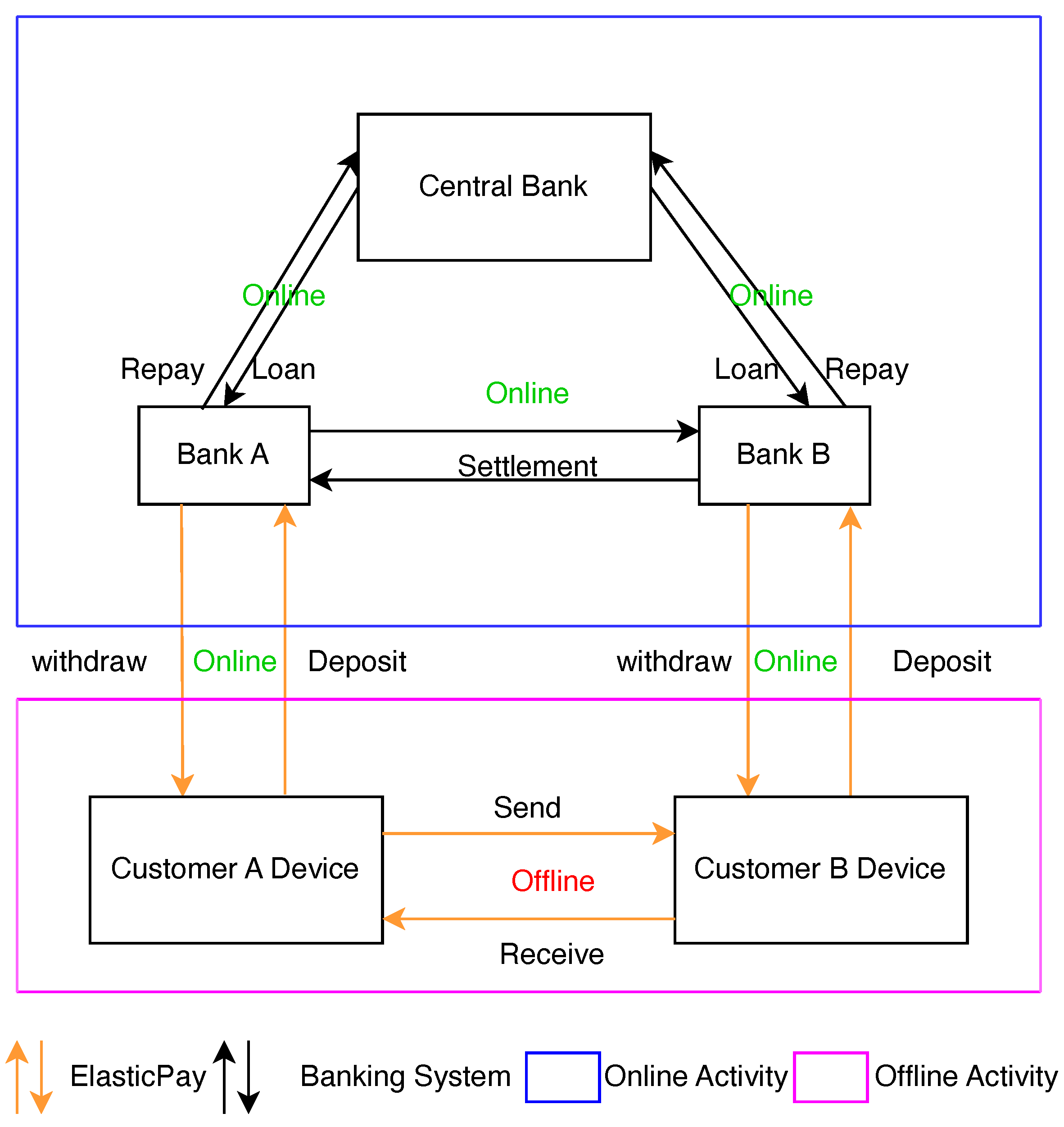
Figure 4 illustrates the architectural integration of our proposed ElasticPay solution within the existing online banking transaction framework (
Figure 1). ElasticPay extends the capabilities of traditional online banking by introducing a secure offline payment layer, enabling seamless transactions even in the absence of network connectivity, thereby improving accessibility and reliability for users.
Recall that in the preliminaries, the concept of attestation is briefly explained. To prove that we have an integral system with all three features enabled, we employ the attestation technique. In the following, the attestation process that ensures the integrity of ElasticPay is summarized:
TPM-based Attestation: Ensuring the integrity of the device’s boot process and the operating system.
TEE-based Attestation: Verifying that the payment application running within the TEE has not been tampered with and is executing as expected.
SE-based Attestation: Demonstrating that the cryptographic keys have been generated and are stored securely and that any cryptographic operations are performed in a secure environment.
The above attestation verifies that:
The device has booted with a verified and untampered operating system with the help of the TPM.
The payment application running is the authentic version and is operating securely within the TEE.
The cryptographic keys, which are fundamental to the security of the transaction, are generated and stored securely within the SE.
So, whenever we say attestation from here onward, we mean the combination of those three results.
ElasticPay employs NIST P-256 elliptic curve cryptography (ECC) for encryption, coupled with SHA-256 for generating the message digest. We use interchangeably userA, Alice (A), and Sender, which all mean the same, and similarly , Bob(B), and Receiver are the same. Here, we use ‘BS’ for the bank server, which takes care of online registration, third-party verifiers, and root certificate authority. T is a trusted application that runs on the user TEE side, UT is an untrusted application that runs in the normal world, and the entire combined device is called the secure device (SD).
Table 1 and
Table 2 provide the notation and terminology used throughout this paper to describe the protocols and algorithms that realize ElasticPay.
ElasticPay comprises three core protocols that facilitate secure and efficient offline digital payments:
Registration Protocol: This protocol enables the registration of users and their devices within the ElasticPay system. During registration, the Trusted Application (T) on the user’s device establishes its trust through remote attestation and obtains the necessary credentials for secure transaction processing.
Funds Transfer Protocol: These protocols encompass two distinct scenarios:
Withdraw scenario: This protocol allows users to securely transfer funds from their online accounts held on the bank server (BS) to their offline wallets managed by the T.
Deposit scenario: This protocol facilitates the reverse process, enabling users to deposit offline funds from their T wallets back to their online accounts on the BS.
Peer-to-Peer (P2P) Protocol: This protocol allows for direct transactions between users’ devices. It utilizes cryptographic mechanisms to ensure secure and verifiable transfers even in the absence of network connectivity.
3.1. Registration Protocol
The first and crucial step before engaging in any offline transaction is to register with the bank server (BS). This registration is essential as it establishes the authenticity of both the user and their device, which is necessary for gaining the trust of the transaction receiver.
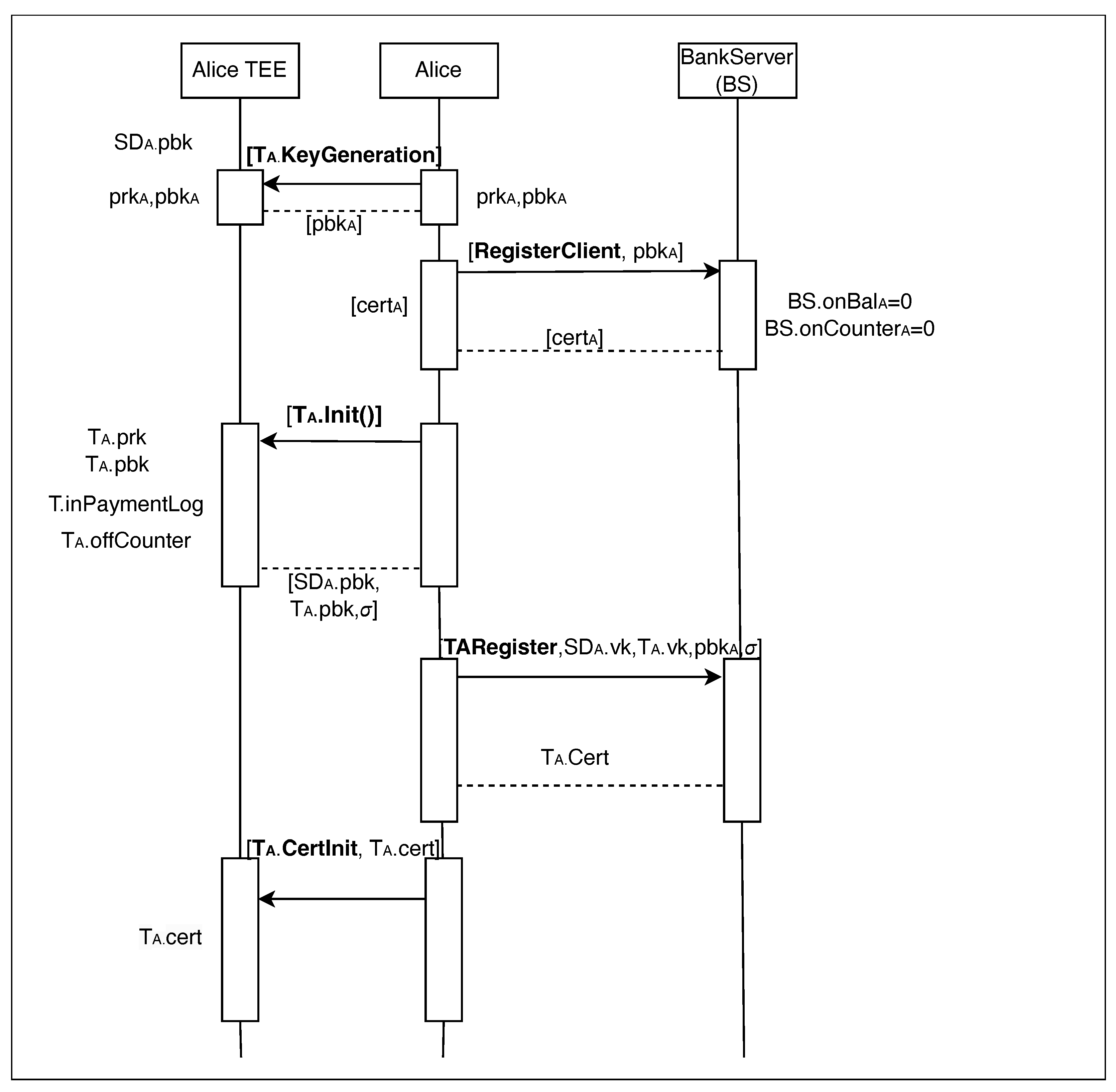
The procedure is meticulously documented in a sequence diagram in
Figure 5, which clarifies the functions executed within the Trusted Execution Environment (TEE) and those processed on the server side. Although the diagram includes entities like Alice, Alice TEE, and the bank server as separate units, this separation is intended to facilitate a clearer understanding of the distinct roles each plays in the registration process.
Initial user registration within ElasticPay requires an existing online bank account. As illustrated in
Figure 5, the user instructs their device’s Trusted Execution Environment (TEE), leveraging the Secure Element (SE) for secure random number generation, to generate a cryptographic key pair, denoted as (
,
), using the
. KeyGeneration function. The public key,
, is then transmitted to the bank server (BS) for registration. If the BS detects any conflicts, such as the key already being in use, the user is prompted to regenerate and resubmit a new key.
Upon successful registration of the public key, the BS initializes the user’s online balance BS. and online transaction counter Bs. to 0. The BS then issues a digital certificate to authenticate the user’s account, transmitting this certificate to the user.
The user has now successfully registered his or her online account. For a detailed view of the algorithmic operation that facilitated this registration, please refer to Algorithm 1 in the accompanying documentation.
| Algorithm 1 Client registration protocol. |
Alice generates a key pair (. C sends [RegisterClient, ] to BS. Upon receiving [RegisterClient, ], BS performs the following steps:
- (a)
Abort if BS.Registry. - (b)
Add ( to BS.Registry. - (c)
Initialize Alice’s account balance to zero: BS.onBal0. - (d)
Create a certificate such that .pbk ← and .sig ← Sign(, ), where is BS’s private signing key. - (e)
Send to Alice.
|
We have seen client registration, and now we will see device registration. The user begins by registering their trusted device via a trusted application, denoted as T, operating within the Trusted Execution Environment (TEE); we denote Alice’s trusted application as
. This process starts with the initiation function
.Init(), which is detailed in
Table 3. During this initialization, the application generates cryptographic keys, specifically
.prk (private key) and
.pbk (public key). It also sets initial values: offline balance
.offBal to ‘0’, trusted applications certificate
.cert to undefined (⊥),
.inPaymentLog to undefined (⊥) and transaction counters
.offCounter to ’0’. For clarity and consistency, throughout this paper, the subscript A is used to indicate entities and variables specific to the user Alice. For example,
represents Alice’s public key,
refers to her trusted application instance and
.KeyGeneration() is the function called by Alice’s T to generate cryptographic keys. Similarly, the subscript B denotes entities and variables associated with another user, Bob.
Following these setups, the application executes a remote attestation mechanism, generating an attestation signature and packaging the application’s public key .pbk. This information is then transmitted to the user’s application layer. Subsequently, the process integrates the secure device’s (SD) root public key .pbk with the user’s public key .pbk and initiates the TARegister protocol with the BS.
The server’s role is to ensure that no other keys are associated with the user’s public key and to validate the attestation signature against known benchmarks. Once verified, the server issues a digital certificate for the user’s trusted application, .cert. This certificate is sent back to the user. We have previously discussed the importance of ‘trust’ in our system and how remote attestation facilitates this trust. Once remote attestation is completed, the device receives a digital certificate from the certificate authority (CA)—in this context, represented by the BS—confirming the device’s genuineness. .cert enables both parties in a transaction, the sender and the receiver, to verify that the device involved has not been tampered with by monitoring changes in the cryptographic hash.
Upon receiving the
.cert from BS, the user stores the certificate within the trusted application residing in the TEE by executing the CertInit operation
.CertInit, which is detailed in
Table 3. This step finalizes the secure registration of the trusted application, ensuring that all communications between the parties and transactions performed by
are authenticated and secure. For a detailed view of the algorithmic operation for device registration, please refer to Algorithm 2.
| Algorithm 2 TA registration protocol. |
Alice obtains (.pbk, .Init() and sends [TARegister, .pbk, .pbk, , ] to BS. Upon receiving [TARegister, .pbk, .pbk, , ] from Alice, Bank server BS does the following steps:
- (a)
Abort if any of the following conditions is true:
(pbk BS.Registry. OEMVerify(.pbk, , .pbk) ≠ 1.
- (b)
Create a certificate cert such that cert.pbk ← .pbk; cert.sig ← Sign([.pbk, ‘T’], ). - (c)
Send [.cert] to Alice. - (d)
Replace (pbk with (, cert.pbk) in S.Registry.
Upon receiving [.cert] from BS, client A invokes TA.CertInit(.cert).
|
3.2. Fund Transfer Protocol
Having covered the device and user registration process, we now turn our attention to the fund transfer protocol. The sequence diagram for deposit and withdrawal scenarios shown in
Figure 6, while the details of the trusted application
T functions running within the TEE can be found in
Table 3.
Let us proceed with the deposit scenario. This crucial procedure allows users to securely transfer funds from their online accounts held on the bank server to their device’s offline wallet, facilitating seamless offline transactions.
Deposit Initiation: To initiate a deposit, the user Alice sends a request to the bank server S specifying the desired amount x to be transferred from her online account to her offline wallet. This request is denoted as [Deposit, x].
Server-Side Validation and Signature: Upon receiving the deposit request, the BS first verifies that Alice’s online balance BS. is sufficient to cover the requested amount x. If the balance is adequate, the BS debits the amount from her online account BS.← BS.− x and increments its online transaction counter BS.onCounter BS. + 1. The BS then generates a digital signature on the transaction data—which includes the recipient’s public key .pbk, the amount x, and the updated counter BS.—using its private key BS.prk. Finally, the BS sends a confirmation message DepositConfirmed containing the amount, transaction counter, and signature back to Alice.
Trusted Application Verification and Credit: Alice’s device receives the
DepositConfirmed message and forwards it to the trusted application T residing in the TEE. The T then executes the
. Deposit function can be found in
Table 3, which performs a series of security checks:
Verifies that a valid certificate .cert is present.
Confirms that the online transaction counter BS. matches the expected next value in the T’s offline counter.
Validates the authenticity of the signature using the BS’s public key . If any of these checks fail, the transaction is aborted. Otherwise, the T credits the amount x to Alice’s offline wallet T.offBal ← .offBal + x and increments its offline counter .offCounter ← .offCounter + 1. The T then notifies Alice of the successful deposit with a DepositSuccess message.
The deposit scenario, visualized in
Figure 6 and formally described in Algorithm 3, enables the secure conversion of online funds into offline funds within the ElasticPay framework. This process involves crucial steps on both the bank server and the user’s trusted device, ensuring the integrity and authenticity of the transaction. This procedure is also called
online fund to
offline fund conversion.
| Algorithm 3 Deposit protocol. |
Alice sends [Deposit, x] to BS. Upon receiving [Deposit, x] from Alice, server BS does the following steps:
- (a)
Abort if x > BS.. - (b)
BS.onbal BS. - x. - (c)
BS.i BS. + 1. - (d)
Send [DepositConfirmed, x, BS.i] to A, where Sign([.pbk, x, BS.], BS.prk).
Upon receiving [DepositConfirmed, x, BS.onCounter] from BS. A invokes T.Deposit(x, BS.onCounter).
|
The incrementing counter mechanism plays a crucial role in preventing replay attacks. In a replay attack, a malicious actor would attempt to fraudulently credit their offline wallet multiple times by repeatedly sending the same, previously valid [Deposit, x, BS.onCounter] message to the trusted application T. However, the T maintains its own counter .offCounter, which is synchronized with the bank server’s counter BS. during the initial deposit. Subsequent deposit messages are only accepted if the server’s counter is exactly one increment higher than the T’s stored counter. This ensures that each deposit message is unique and can only be processed once, effectively mitigating the threat of replay attacks.
In addition to deposits, ElasticPay enables the secure transfer of funds from a user’s offline wallet back to their online bank account. This is accomplished through the withdrawal protocol, which, as shown in
Figure 6, involves a series of interactions between the user’s device and the bank server (BS) and formally described in Algorithm 4.
The complete details of the withdrawal protocol, including the algorithm executed by the
T and the interaction between entities, are outlined in Algorithm 4 and illustrated in
Figure 6.
| Algorithm 4 Withdrawal protocol. |
Client A sends [Withdraw, k, .offCounter, ] to Bank-server (BS), where [k, .offCounter, ] ← .Withdraw(k). Upon receiving [Withdraw, k, .offCounter, ] from A, BS performs the following steps:
- (a)
Abort if .offCounter ≠ BS. + 1 or SigVerify([k, .offCounter], , .pbk) ≠ 1. - (b)
BS.onBal BS. + k. - (c)
BS.onCounter BS. + 1. - (d)
Send [WithdrawConfirmed] to A.
|
3.3. Peer-to-Peer (P2P) Protocol
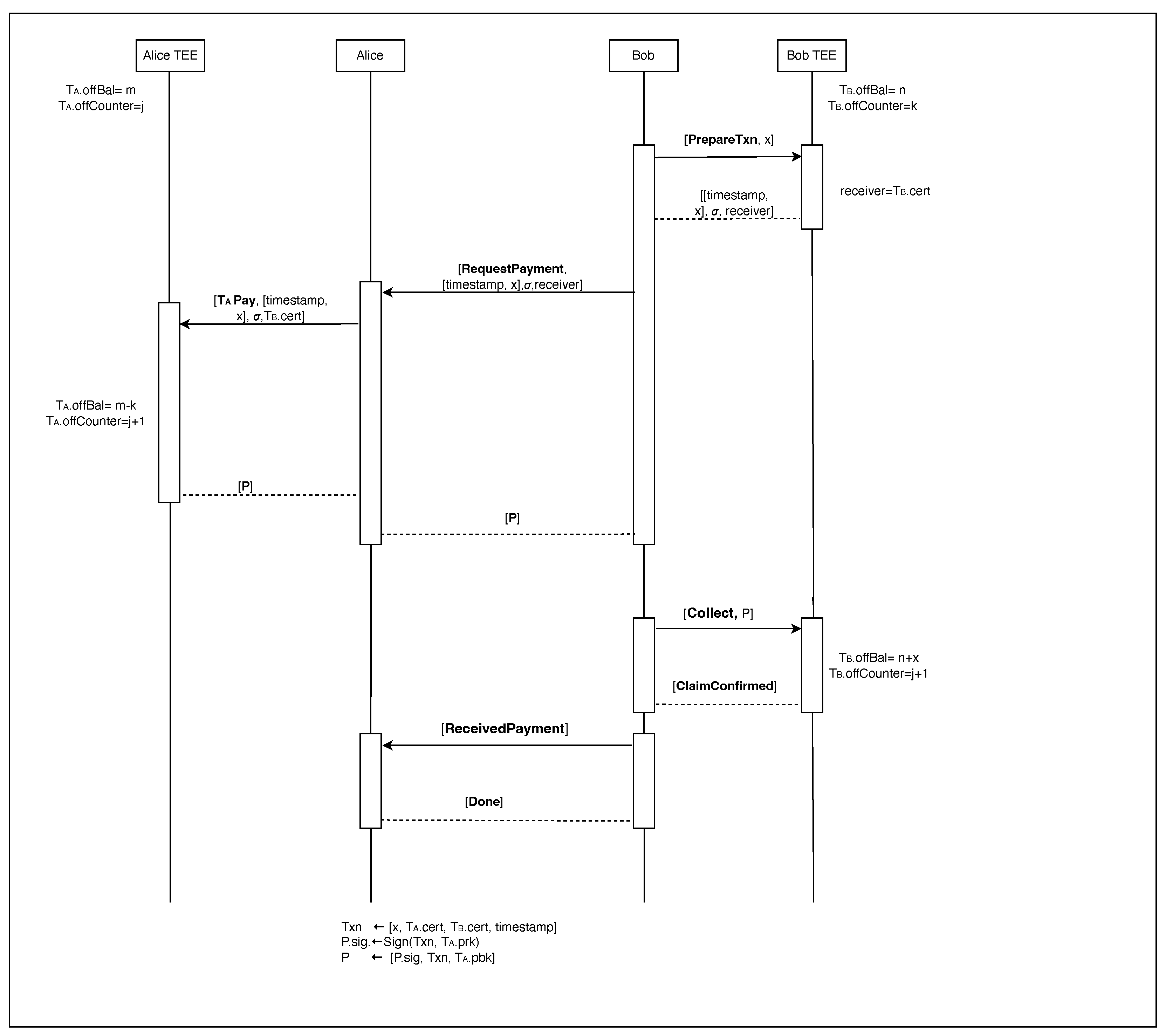
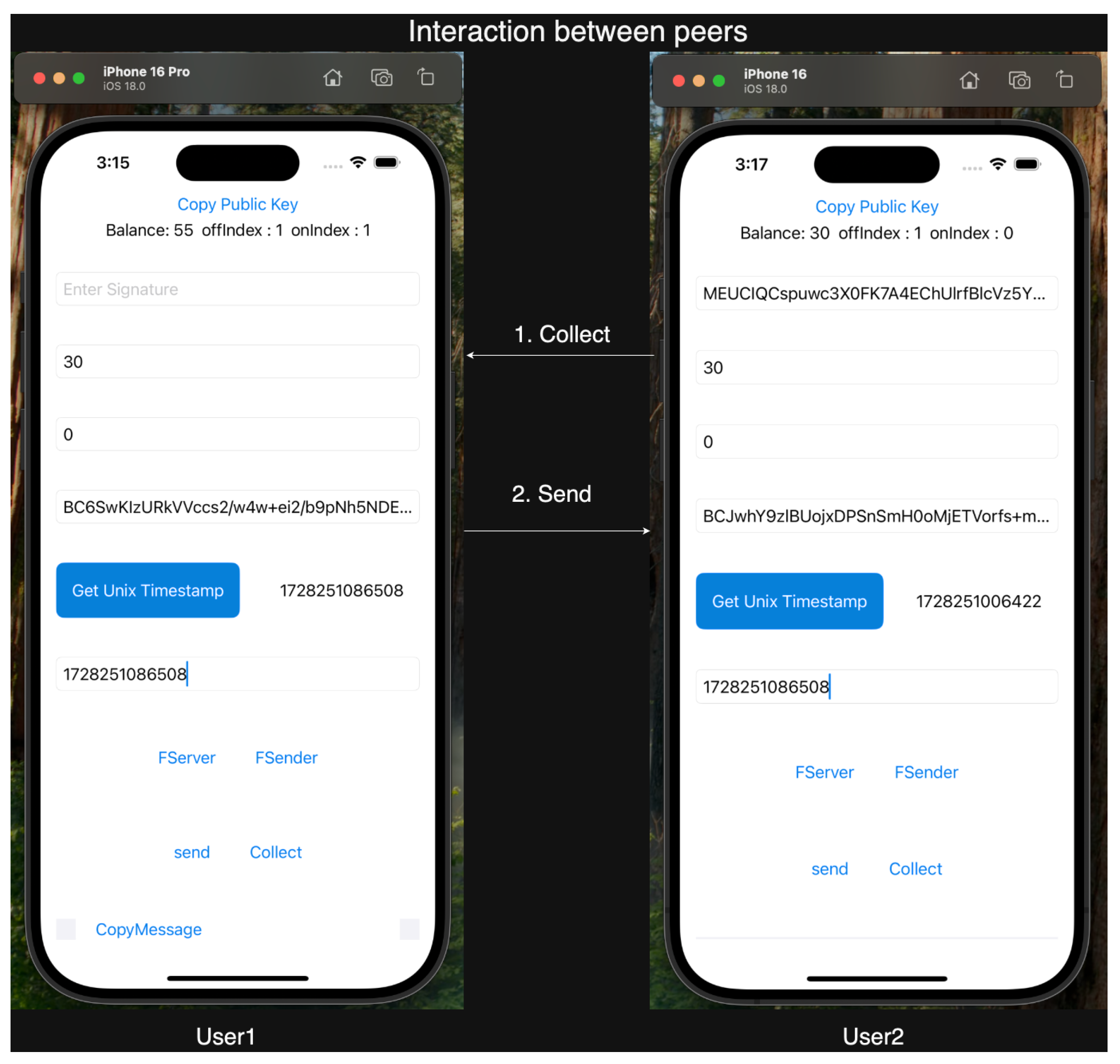
The P2P protocol facilitates direct offline transactions between two users, as illustrated in
Figure 7. All operations within the Trusted Execution Environment (TEE) are detailed in
Table 3, while the complete P2P protocol is outlined in Algorithm 5.
Transaction Preparation (Receiver):
The receiver (Bob) initiates the transaction by instructing his trusted application to prepare a transaction for amount x, using the PrepareTxn (x) function.
retrieves a timestamp from the device’s clock and generates a signature on the amount x and timestamp using its private key .prk.
Bob sends the signed transaction request [x, timestamp, .cert, ] to the sender Alice.
Payment Initiation and Verification (Sender):
Alice’s untrusted application UA receives the signed transaction request and forwards it to the sender’s trusted application by invoking the .Pay function.
verifies:
- –
The validity of Bob’s signature using his public key .cert.pbk.
- –
The presence of a valid certificate .cert.
- –
The sufficiency of funds in Alice’s offline wallet .offBal ≥ x.
If all checks pass, debits the amount x from Alice’s offline balance .offBal and increments its transaction counter .offCounter by one.
It creates the transaction payment P with the following information P.amount ← x, P.sender ← .cert, P.receiver ← .cert, P.timestamp ← timestamp, Txn ← [P.amount, P.sender, P.receiver, P.timestamp], P.sig ← Sign(Txn,.prk).
Sends P to the receiver (Bob) where P ← [Txn, P.sig, .pbk].
returns P to the UA, which transmits it to Bob.
Payment Collection (Receiver):
| Algorithm 5 Peer-to-peer protocol. |
B sets receiver ← .cert if .cert and calls .PrepareTxn in his trusted application T. Otherwise, receiver ← and calls prepare transaction Algorithm 7 from his untrusted application UT. The output is forwarded to B and then forwarded to A with message including message ‘RequestPayment’ [RequestPayment, [timestamp, x], , receiver]. Upon receiving [RequestPayment, [timestamp, x], , receiver] from B, client A sends P to B where P ← TA.Pay (x, timestamp, receiver). Upon receiving P from A, client B performs the following steps:
- (a)
Abort if any of the following conditions is true: PayVerify(P) ≠ 1 or P.receiver ≠ receiver or P ∈ B.inPaymentLog. - (b)
B adds P to B.inPaymentLog in his UT and sends [ReceivedPayment] to A. - (c)
If P.receiver.type = “T”, then B calls .Collect (P). - (d)
Otherwise, B engages in the Claim protocol Algorithm 8 with BS as soon as B is online.
|
If all checks succeed:
- –
If Bob provided his online banking certificate , UA initiates the Claim protocol (Algorithm 8) to eventually credit his online account.
- –
If Bob provided his T certificate .cert, UA initiates the .Collect protocol to eventaully credit his offline account.
| Algorithm 6 PayVerify function. |
| PayVerify(P): |
Return 1 if and only if all of the following conditions hold:
TACertVerify(P.sender) = 1 and SigVerify([P.amount, P.sender, P.receiver, P.timestamp], P.sig, P.sender.pbk) = 1.
|
| Algorithm 7 PrepareTxn. |
PrepareTxn (x):If = ⊥ then abort. receiver ← . Output [[timestamp, x], , receiver] where Sign([timestamp, x], )
|
| Algorithm 8 Claim protocol. |
B sends [Claim, P] to BS. Upon receiving [Claim, P] from B. Bank server BS performs the following steps.
- (a)
Abort if any of the following conditions is true:
P.receiver.type ≠ ‘UA’. PayVerify(P) ≠ 1. P ∈ BS.paymentLog
- (b)
BS.onBal ← BS.onBal + P.amount. - (c)
Add P to BS.inpaymentLog; - (d)
Send [ClaimConfirmed] to B.
|
3.4. Integration of ElasticPay with Digital Fiat Currencies
ElasticPay can seamlessly integrate with digital fiat currency systems, much like its integration with Central Bank Digital Currencies (CBDCs), as illustrated in the sequence diagram in
Figure 5 and detailed in
Section 3.1. In this scenario, intermediary banks, rather than central banks, handle Know-Your-Customer (KYC) processes and customer verification. When a user (the sender) converts their online balance to offline, their corresponding intermediary bank, Bank ‘A’, manages the process. This includes setting up the sender’s device, remote attestation, and certificate assignment.
For offline transactions, the receiver’s device, managed by their intermediary bank, Bank ‘B’, verifies the sender’s certificate issued by Bank ‘A’. This verification involves a two-layer process: first, validating the user’s certificate issued by Bank ‘A’, and then ensuring that Bank ‘A’s public key is listed in the receiver’s Trusted Execution Environment (TEE). This dual-layer verification ensures the authenticity and security of the transaction, allowing only authorized banks to validate certificates.
This integration method applies the same ElasticPay protocols to both CBDCs and digital fiat currencies, ensuring seamless compatibility across different systems.
4. Experimentation
The primary objective of our research was to develop ElasticPay. This system aims to significantly reduce the attack surface commonly associated with digital transactions. To achieve this level of security, we utilized Trusted Execution Environments (TEEs), Trusted Platform Modules (TPM-like features) and Secure Elements (SEs), which are essential for maintaining the integrity and confidentiality of transactions.
As part of our proposed approach, we utilize Trusted Execution Environments (TEEs), Trusted Platform Modules (TPMs), and Secure Elements (SEs) to enhance security. These components typically operate collaboratively to fortify security measures. However, in Apple devices, these functionalities are consolidated into a single hardware component in the system on a chip (SoC) known as the Secure Enclave. This integration provides robust isolation from the main processor and system, ensuring that all sensitive operations are securely managed and segregated from the rest of the device architecture. Today, most mid-range mobile devices are equipped with technologies such as TPM, TEE, and SE, either separately or as part of the SoC, as their inclusion has become a mandatory standard. These technologies play a vital role in enhancing device functionality and improving the overall user experience.
4.1. Why iPhone?
Visualizing Apple’s Security Architecture
Apple’s Secure Enclave is a comprehensive security system within its devices that employs a dedicated Secure Enclave Processor for isolated operations, a Memory Protection Engine for encrypted storage, and a Secure Enclave Boot Monitor for secure booting. It also includes a True Random Number Generator for cryptographic operations, Root Cryptographic Keys unique to each device, an AES Engine for hardware-accelerated encryption, and a Public Key Accelerator for secure communications. Additionally, secure non-volatile storage safeguards sensitive data, all combining to create a robust security infrastructure for Apple devices. Please refer to
Figure 8 for a depiction of the Apple SoC architecture. For an in-depth understanding, you can refer to [
37].
The iPhone was chosen as our primary experimental platform because of its sophisticated and integrated security architecture. This architecture includes several key features.
Secure Boot and Measured Boot: The iPhone’s boot process involves several stages of security checks—from the immutable Boot ROM, through the Low-Level Bootloader (LLB), to the iBoot that loads the iOS kernel. Each stage ensures that only Apple-signed software can proceed, effectively preventing unauthorized modifications.
Secure Enclave: Integral to Apple’s hardware, the Secure Enclave provides an isolated execution environment similar to a TEE. It is designed for secure cryptographic operations and sensitive data handling, effectively protecting cryptographic keys used during transactions and other operations.
Apple Keychain: We leveraged Apple Keychain for securely storing sensitive transaction data such as account balances, digital certificates, and transaction counters. Keychain’s robust encryption features and anti-replay mechanisms make it an ideal tool for securing financial transactions.
App Sandboxing: App sandboxing is a crucial security feature of iOS that confines each app to its own secure environment, preventing it from accessing data or resources belonging to other apps without explicit user permission. In our experiment, app sandboxing plays a vital role in isolating the peer-to-peer offline payment application, shielding it from potential threats and ensuring that sensitive payment data remain confidential and secure.
Memory Manipulation, Memory Dump, and Sniffing Prevention: The iPhone incorporates advanced security mechanisms, such as Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR), to prevent memory manipulation, memory dump attacks, and data sniffing. These defences safeguard the application’s data from unauthorized access and manipulation, ensuring the integrity and confidentiality of payment transactions.
Isolated Application Execution and Trusted Execution Environment (TEE): The iPhone’s security model ensures the isolated execution of applications, preventing unauthorized access or manipulation of data between applications. The Trusted Execution Environment (TEE), represented by the Secure Enclave, provides a secure and isolated environment for executing sensitive operations, such as cryptographic operations and biometric authentication. This enhances the security of the offline payment system by shielding sensitive operations from potential threats and vulnerabilities.
Trusted Operating System Loading: During the boot process, the iPhone verifies the integrity of the operating system using cryptographic signatures and secure boot mechanisms. This ensures that only a trusted operating system, signed by Apple, is loaded into the device’s memory. Additionally, hardware-based security features, such as the Secure Enclave, monitor and enforce the integrity of the operating system, preventing unauthorized modifications or tampering.
Secure Communications: iOS implements strong encryption protocols for network communications, ensuring that data transmitted between your application and external servers are encrypted and secure. This protects against eavesdropping and data interception, maintaining the confidentiality of sensitive information exchanged during transactions.
By leveraging these advanced security features of the iPhone, our experiment establishes a Trusted Execution Environment for the offline payment system, ensuring the integrity and confidentiality of payment transactions. These robust security measures protect against potential threats and vulnerabilities, safeguarding the broader economic ecosystem from security risks and ensuring user privacy.
4.2. ElasticPay Implementation
In ElasticPay, transaction processing is handled within the Secure Enclave to ensure the integrity and confidentiality of each transaction. Interaction with the Apple Keychain allows for the secure retrieval and storage of encrypted data as shown in
Figure 9. During a transaction, encrypted data are fetched from the Keychain, decrypted within the Secure Enclave, and updated and re-encrypted before being securely stored back. This process ensures that sensitive transaction data are protected throughout their lifecycle. With our system, users can initiate credit or debit operations by directly interacting with the trusted ElasticPay service. To do so, they will use the regular (non-trusted) ElasticPay application and provide the necessary transaction details. The application gathers the inputs and securely relays them to the trusted service. After processing is complete, ElasticPay provides results that the user can then independently forward to the appropriate party—such as a bank server or the transaction recipient.
In the initial section of our discussion, we covered the standard remote attestation mechanisms involving the TEE, TPM and SE. Moving to the experimental phase with an Apple iPhone, it is noteworthy that Apple employs a robust code-signing process to verify the authenticity of applications before they run. Integrated with this, the Secure Enclave validates the software’s integrity by confirming firmware and booting protocols and by generating detailed attestation reports. This comprehensive validation process effectively prevents any unauthorized or altered applications from executing, reinforcing Apple’s strong commitment to security.
4.3. Comparison with Android Devices
While our focus was on the iPhone due to its advanced features, it is important to note that similar security components such as TEEs, TPM-like features, and SEs are also present in many Android devices. These components are theoretically sufficient to support secure applications like ElasticPay. However, the additional security layers provided by Apple, including the unified ecosystem and advanced Secure Enclave, offer enhanced protections that are particularly valuable for financial applications demanding stringent security measures.
4.4. Summary
The integration of these sophisticated technologies within the iPhone platform provides an ideal testing ground for ElasticPay, demonstrating that leveraging this integrated security architecture enables secure, efficient, and reliable offline transactions.
4.5. Experimental Setup
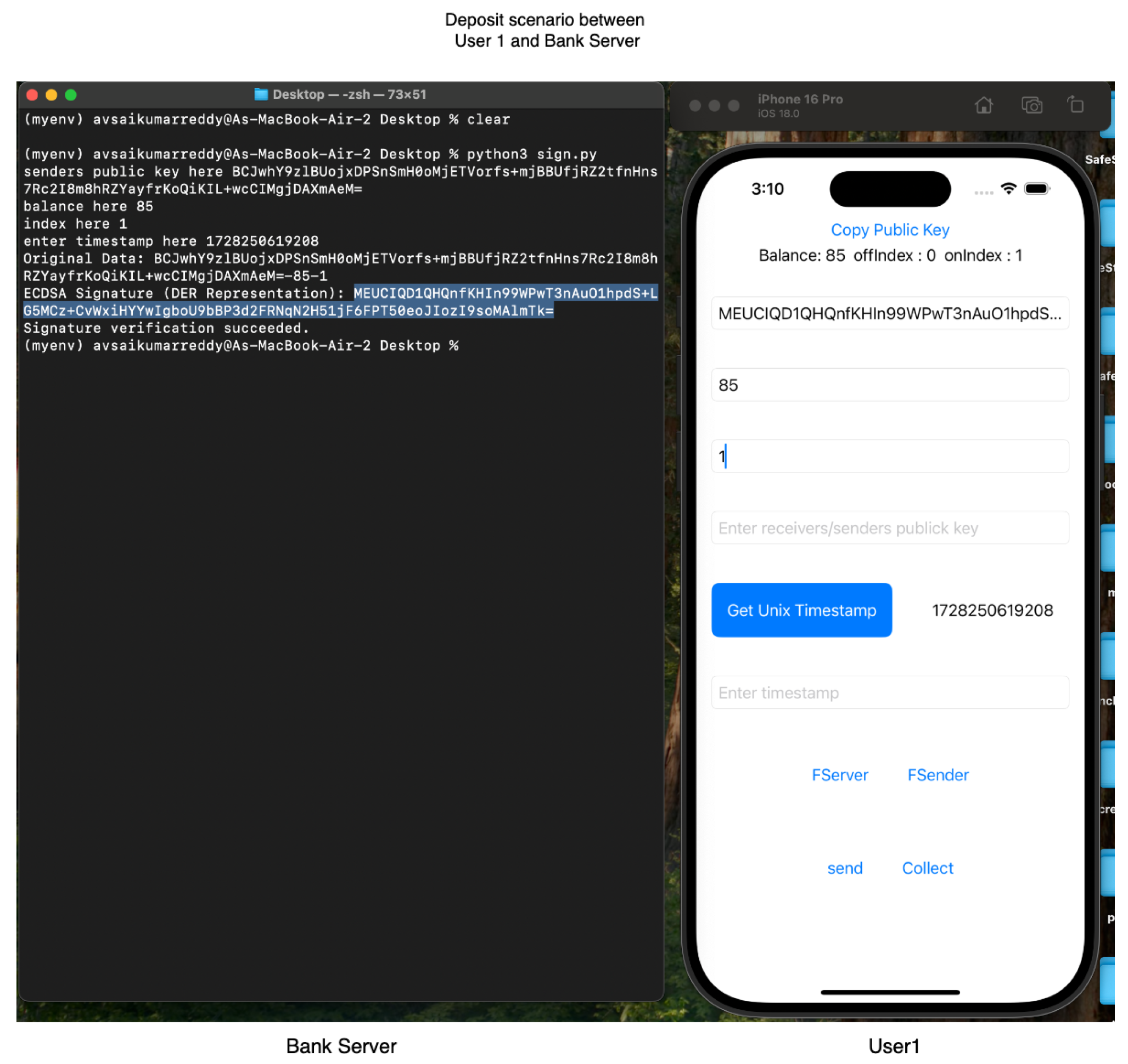
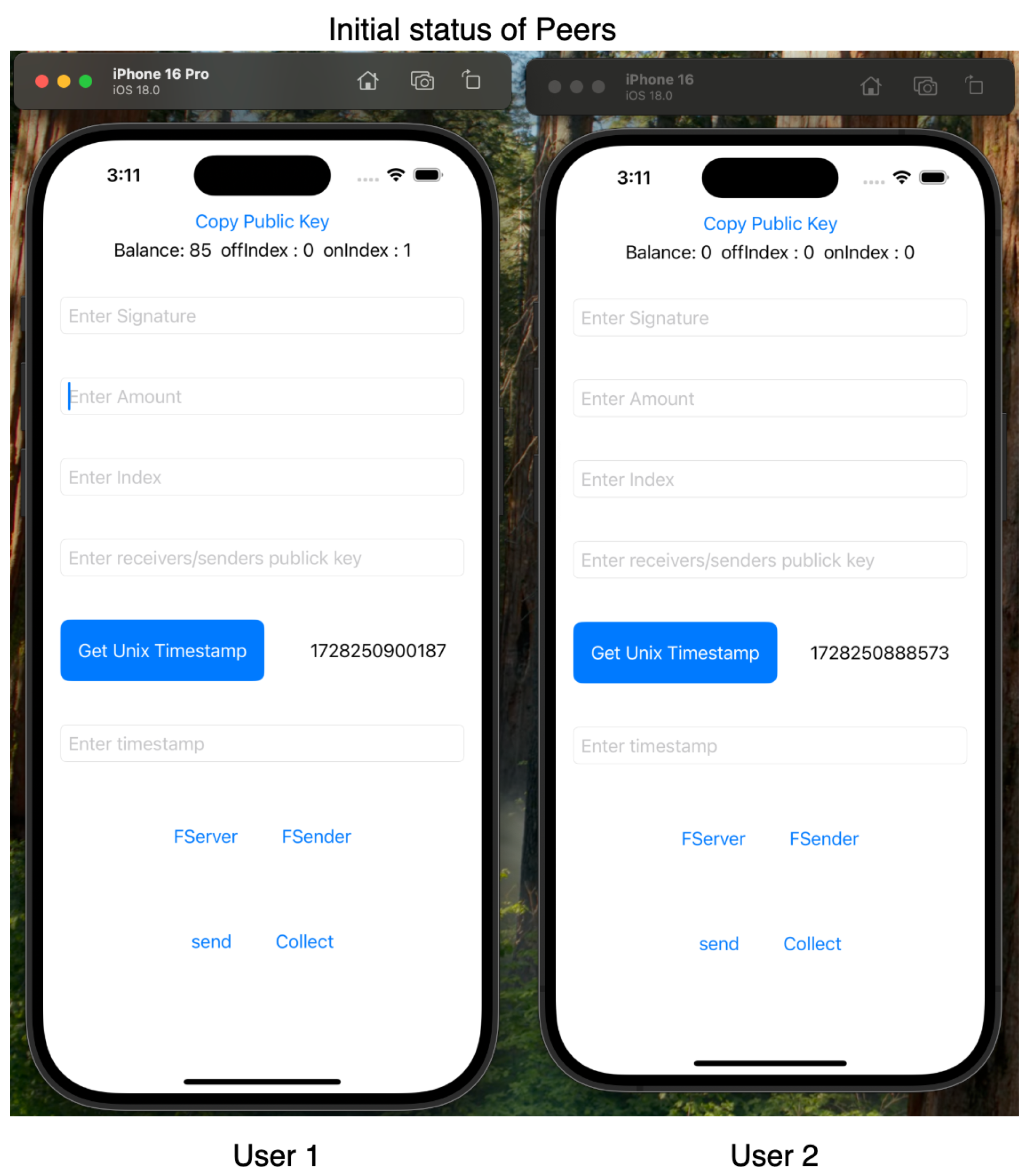
For our experiments, we employed Apple iPhone 16 and iPhone 16 Pro devices, both running iOS 16, to leverage the Multipeer Connectivity framework. Our testing confirmed ElasticPay as a viable solution. Screenshots of the ElastciPay application, implemented according to the established protocols, are shown in
Figure 10,
Figure 11 and
Figure 12.
The Multipeer Connectivity framework facilitates seamless communication by dynamically choosing between Bluetooth Low Energy (BLE) and Peer-to-Peer Wi-Fi. When devices are in close proximity, Bluetooth Low Energy is prioritized due to its low power consumption and efficiency, in line with our commitment to sustainability. In cases where devices are farther apart, the framework defaults to Peer-to-Peer Wi-Fi, which does not require an external Wi-Fi access point and ensures a stable connection over longer distances. Given that the transaction messages exchanged are relatively small, Bluetooth is preferred for communication, offering an optimal balance between speed, power efficiency, and responsiveness. During offline transactions, it is anticipated that devices will be in close range, making Bluetooth the typical communication medium. However, in situations where Bluetooth is unavailable or impractical, Wi-Fi serves as a reliable fallback, ensuring continued functionality.
The latency comparison between ElasticPay and a basic transaction system is presented in
Table 4. In a single transaction, the total message size for ElasticPay is 80 bytes, which includes the following components:
16 bytes for the message payload (comprising the Unix timestamp and the amount);
32 bytes for the SHA-256 hash of the message;
32 bytes for the encrypted hash (signature), which is generated using NIST P-256 elliptic curve cryptography (ECC).
At the sender’s side, the system performs encryption of the 16-byte payload, and at the receiver’s side, decryption occurs to verify the authenticity. This process is coupled with hashing (SHA-256) to generate the message digest for signing. In contrast, in a basic transaction, no encryption or decryption is involved. The system only transfers an 8-byte message (usually just the amount), making it much simpler and more efficient in terms of data size and computational overhead.
Table 4 presents a latency comparison between ElasticPay (the ElasticPay implementation) and a basic transaction system, which operates without encryption, decryption, or hashing. Both systems were tested on the same experimental device. Both systems follow a sequential transaction model, where each transaction is processed only after the previous one is successfully completed. This behaviour is due to the lack of a central authority in the offline environment in coordinating or ordering transactions.
5. Related Work
In the landscape of smartphone-based offline payment systems, several works stand out, specifically those by [
11,
12,
13] all of which explore different security frameworks. Both [
11,
13] primarily utilize Trusted Execution Environments (TEEs) to secure transactions. While this method ensures some level of security, it has been noted that relying solely on TEE can expose the system to various attacks, especially if key management practices are not robust [
11,
13].
Ref. [
12] expand on this by combining TEE with Secure Elements (SEs), arguing that this duo enhances security by making it more challenging to extract sensitive cryptographic keys [
12]. However, ref. [
12] also acknowledges vulnerabilities during the TEE’s boot process, indicating that even this more complex system is not impervious to threats.
We note key approaches from researchers such as [
11,
12,
13]. These works often grapple with privacy compromises; for instance, Refs. [
12,
13] require senders to share comprehensive transaction histories with recipients to establish trust, a practice that significantly undermines privacy [
11] and attempts to mitigate replay attacks by using an index that increments with each transaction. This index ensures that each transaction is unique, preventing participants from reusing transaction data. However, this approach inadvertently reveals the number of previous transactions. As a result, it can indirectly leak sensitive information, such as the fact that a participant has completed ‘n’ number of transactions.
Our proposed solution, ElasticPay, addresses the limitations of previous approaches by integrating Trusted Platform Modules (TPMs) alongside TEEs and SEs. This multi-layered approach not only enhances security but also prioritizes user privacy. Instead of exposing full transaction histories, ElasticPay utilizes unique Unix epoch timestamps to identify transactions. During a transaction, the receiver selects a timestamp and the sender signs the transaction using this timestamp. This method effectively prevents replay attacks, similar to using an index, but offers the added benefit of efficient log(n) search time when verifying the non-existence of a particular transaction within a large set of transactions, as opposed to the linear O(n) search required for random numbers. By minimizing data exposure and ensuring transaction immutability, ElasticPay establishes a robust security framework for offline payments.
Table 5 and accompanying text present a clear, comprehensive view of how our solution leverages existing technologies while addressing their limitations to enhance both security and privacy.
Table 6 summarizes how ElasticPay addresses five key security requirements for Central Bank Digital Currencies (CBDCs): prevention of double-spending, unforgeability, non-repudiation, verifiability, and maintaining anonymity.