Stochastic Computing Implementation of Chaotic Systems
Abstract
1. Introduction
2. Stochastic Computing Implementation of Analog Systems
2.1. Introduction to Stochastic Computing
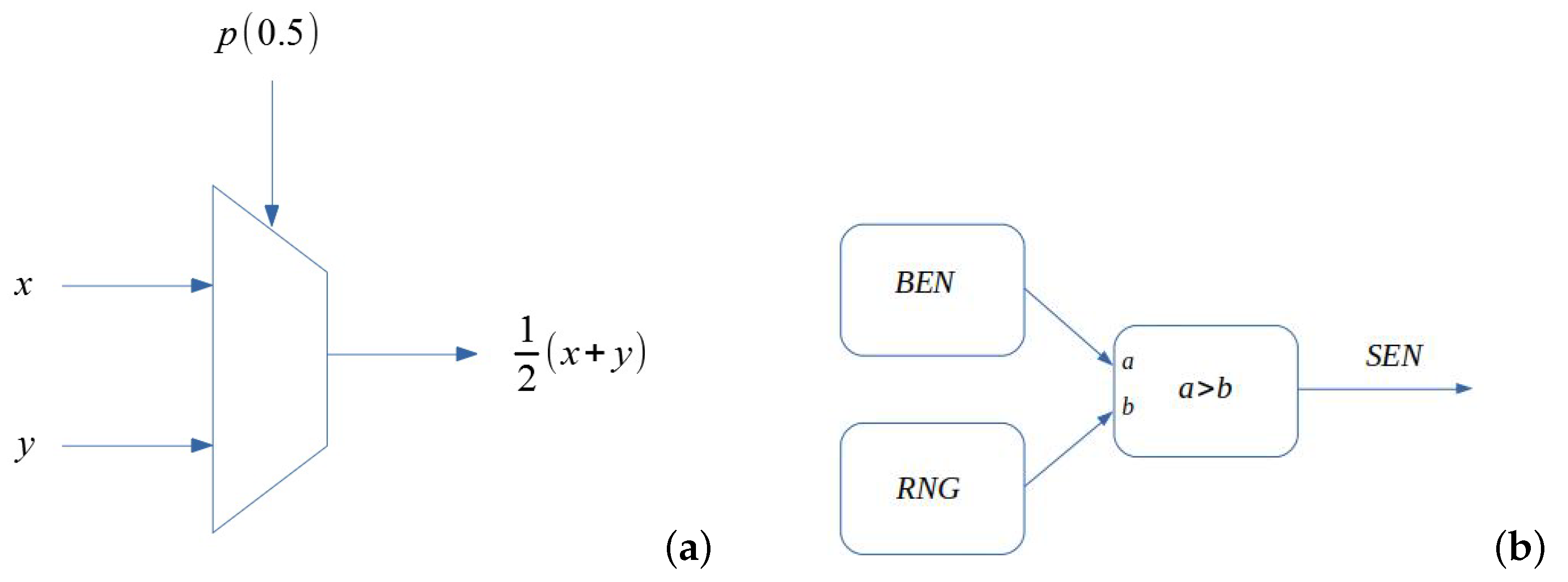
2.2. Implementation of Basic Differential Equations
- Rewriting the equation in a form suited to SC. In the most basic case, this implies replacing all the additions by half additions: . Other, more complex operations may require a harder reworking of the equations to ensure all the operations can be implemented in SC in the [−1,1] or [0,1] range. For instance, in the case of implementing a division, one has to ensure that the result is always going to be in range, which may require an additional scaling and shifting of the variables involved.
- Scaling all the variables into the [−1,1] or [0,1] domains, since those are the values that can be dealt with in SC.
- Then, a final transformation ensures that all the modules of the coefficients in the equations are lower than 1. This is equivalent to a time scaling.
2.3. Basic Examples
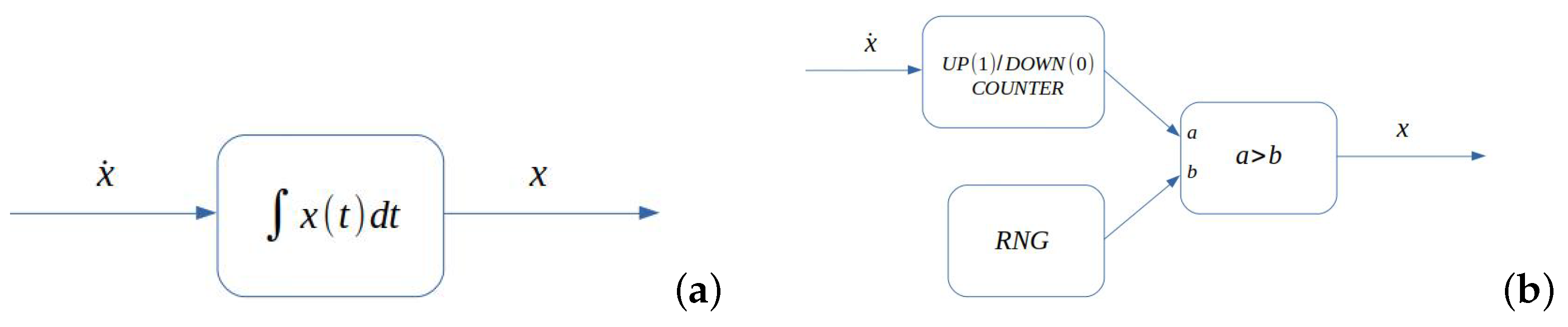
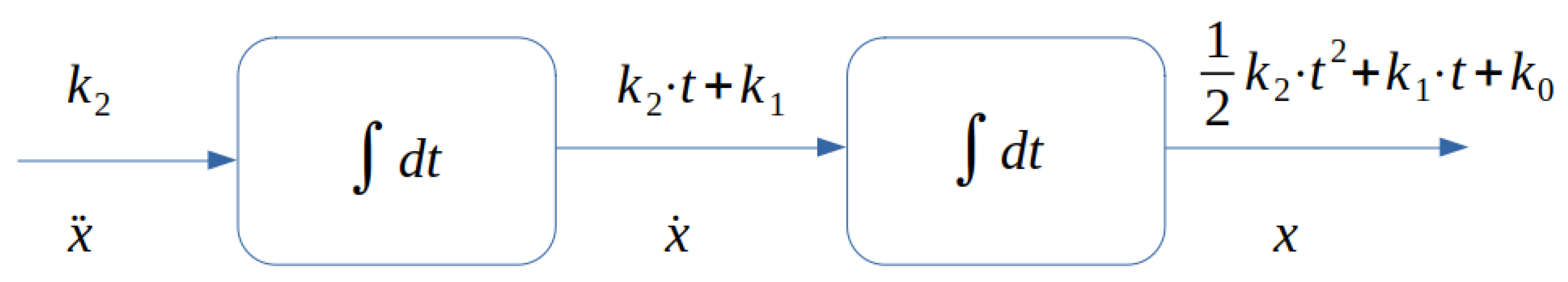
2.3.1. Integrating a Constant (Twice)
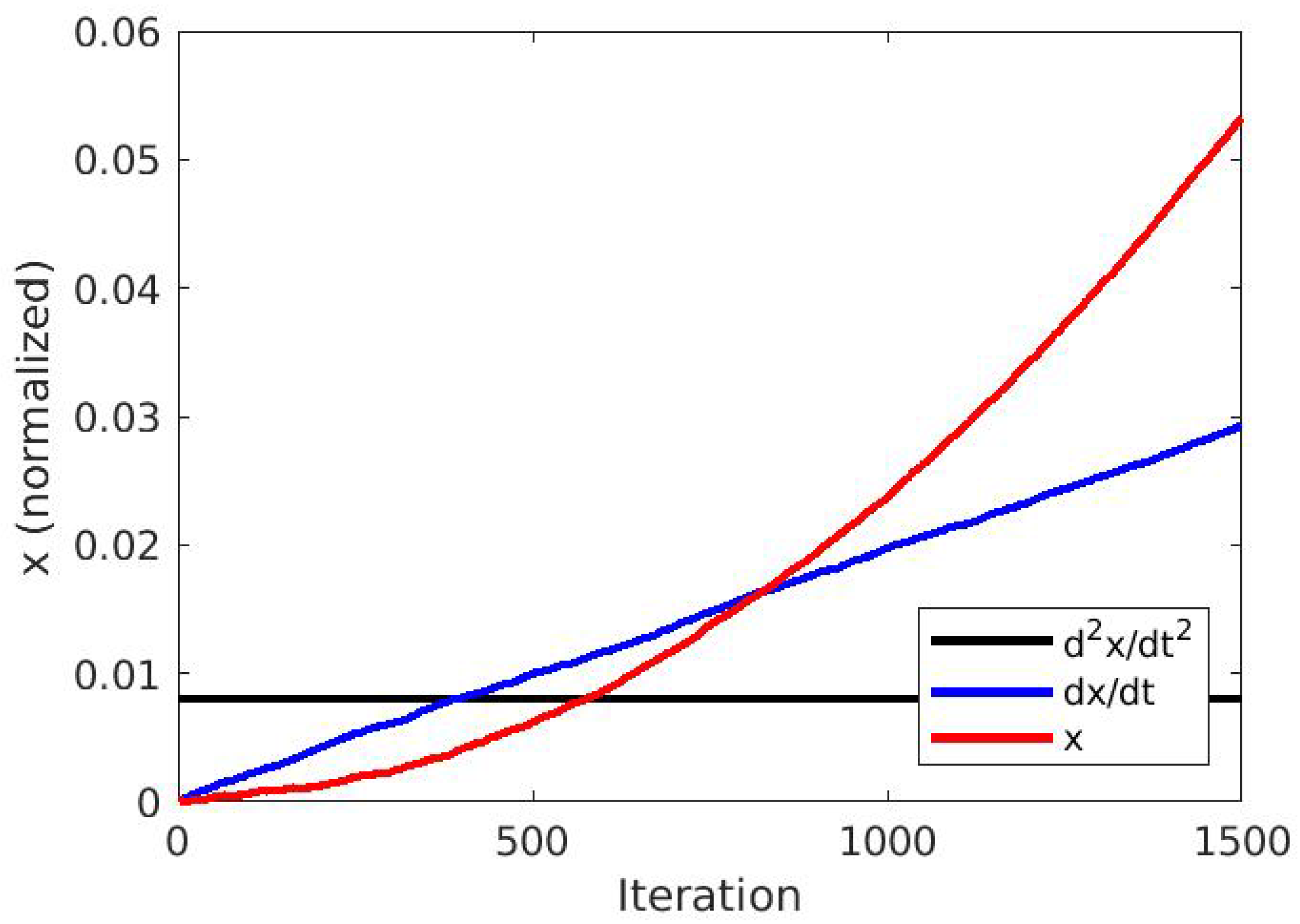
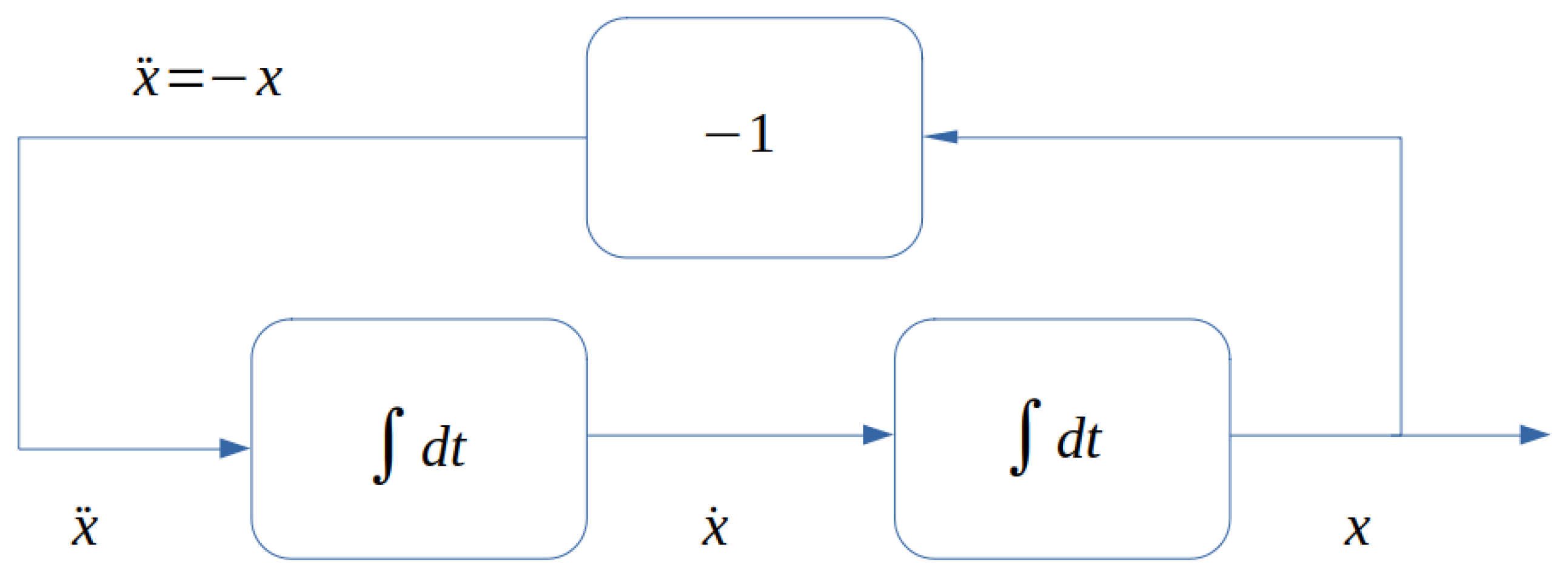
2.3.2. A Simple Oscillator
3. Implementing Chaotic Systems in SC
3.1. The Shimizu-Morioka System
3.2. Equation Preparation
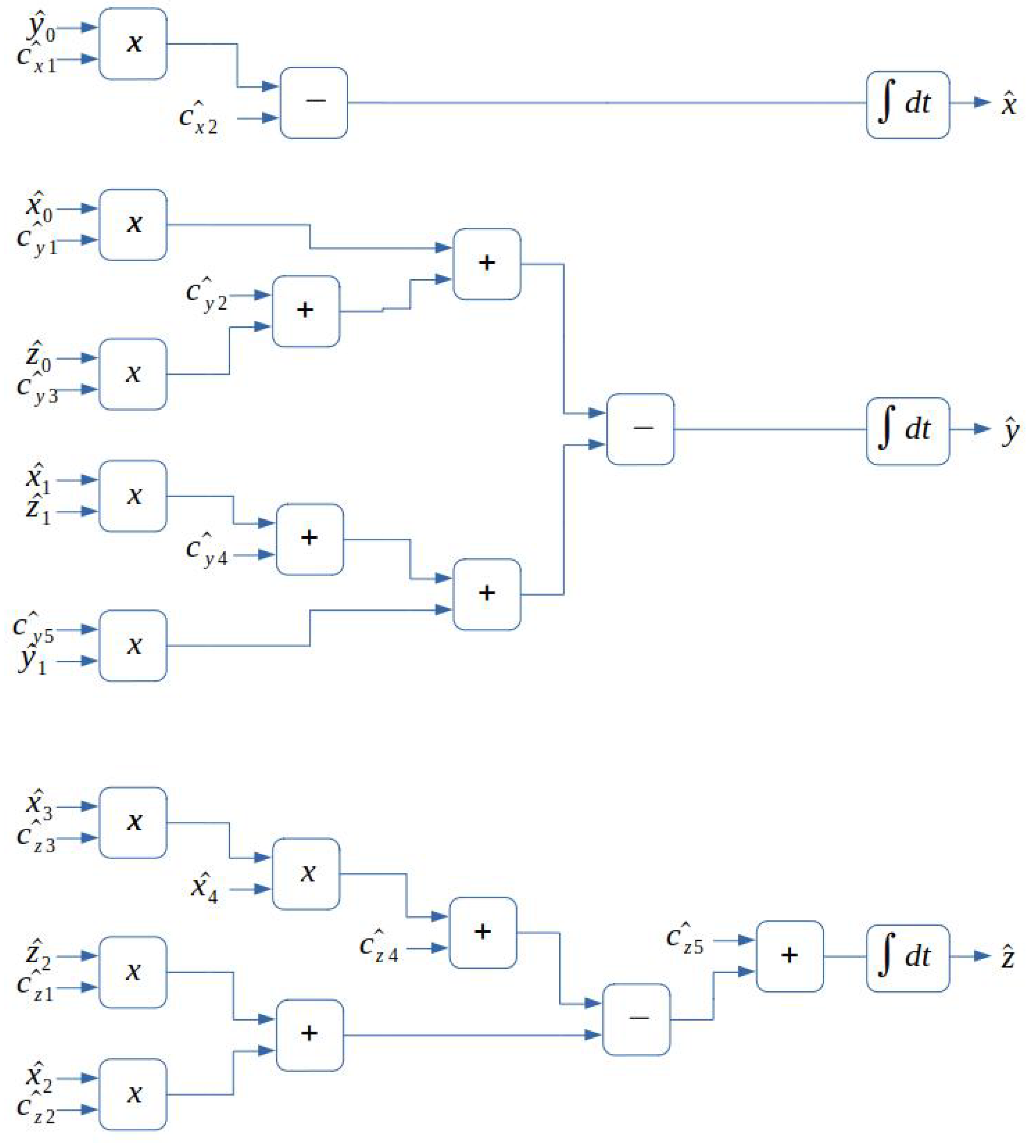
3.3. Implementation
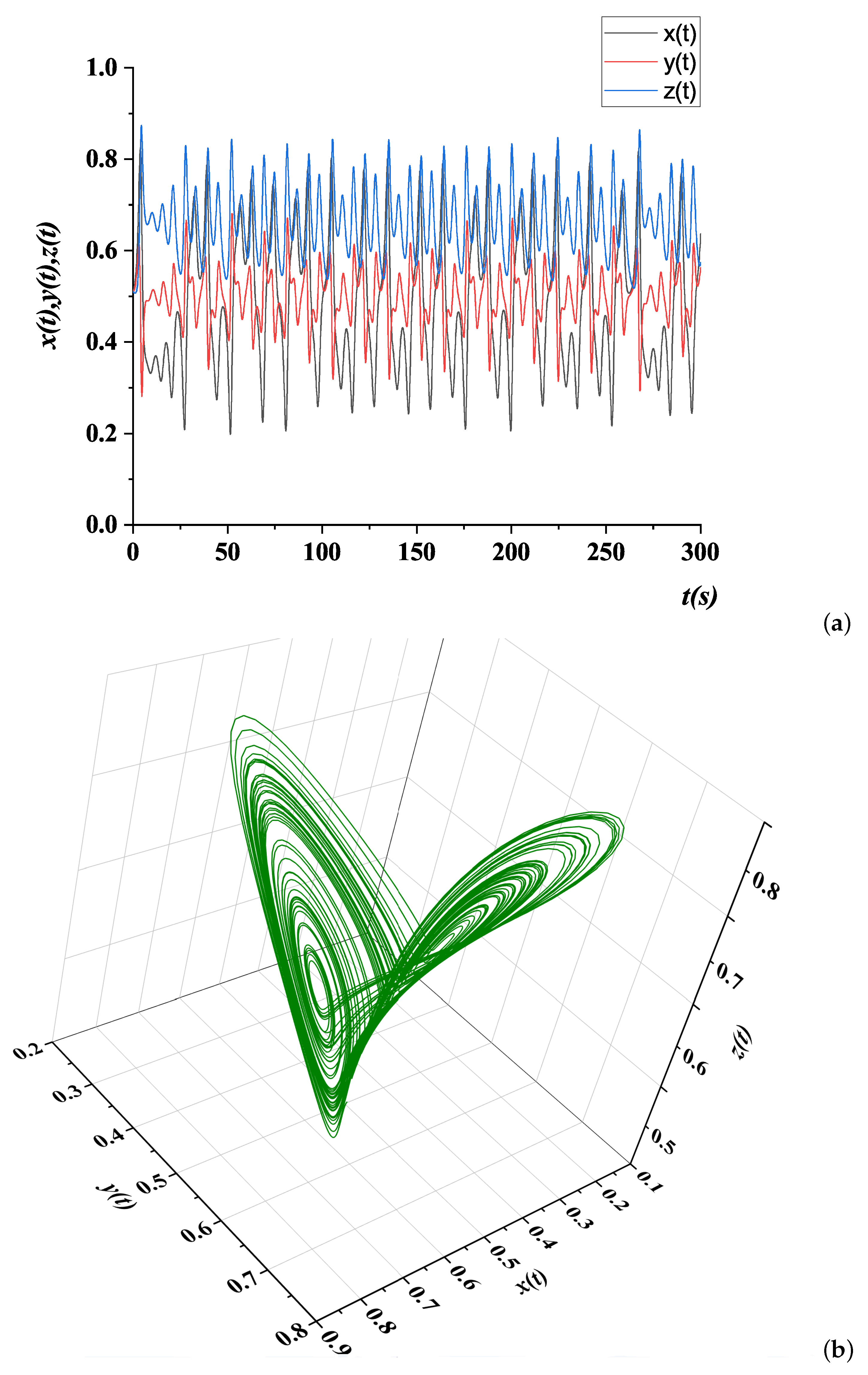
3.4. Chaotic Evaluation
4. Discussion
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| B2S | Binary to Stochastic |
| BEN | Binary Encoded Number(s) |
| FFT | Fast Fourier Transform |
| FPGA | Field Programmable Gate Array |
| IoT | Internet of Things |
| JTAG | Joint Test Action Group |
| NF | Noise Figure |
| RNG | Random Number Generator |
| SC | Stochastic Computing |
| SCN | Stochastic Computing Number |
| SEN | Stochastic Encoded Number(s) |
References
- Shi, W.; Pallis, G.; Xu, Z. Edge Computing [Scanning the Issue]. Proc. IEEE 2019, 107, 1474–1481. [Google Scholar] [CrossRef]
- Venkataramani, S.; Roy, K.; Raghunathan, A. Efficient embedded learning for IoT devices. In Proceedings of the 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), IEEE, Macau, China, 25–28 January 2016; pp. 308–311. [Google Scholar]
- Shafique, M.; Theocharides, T.; Bouganis, C.S.; Hanif, M.A.; Khalid, F.; Hafız, R.; Rehman, S. An overview of next-generation architectures for machine learning: Roadmap, opportunities and challenges in the IOT era. In Proceedings of the 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), IEEE, Dresden, Germany, 19–23 March 2018; pp. 827–832. [Google Scholar]
- Xu, Q.; Mytkowicz, T.; Kim, N.S. Approximate computing: A survey. IEEE Des. Test 2015, 33, 8–22. [Google Scholar] [CrossRef]
- Jayakumar, H.; Raha, A.; Kim, Y.; Sutar, S.; Lee, W.S.; Raghunathan, V. Energy-efficient system design for IoT devices. In Proceedings of the 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), IEEE, Macau, China, 25–28 January 2016; pp. 298–301. [Google Scholar]
- Gao, M.; Wang, Q.; Arafin, M.T.; Lyu, Y.; Qu, G. Approximate computing for low power and security in the internet of things. Computer 2017, 50, 27–34. [Google Scholar] [CrossRef]
- Du, L.; Du, Y.; Li, Y.; Su, J.; Kuan, Y.C.; Liu, C.C.; Chang, M.C.F. A reconfigurable streaming deep convolutional neural network accelerator for Internet of Things. IEEE Trans. Circuits Syst. I 2017, 65, 198–208. [Google Scholar] [CrossRef]
- Ipek, E. Memristive Accelerators for Dense and Sparse Linear Algebra: From Machine Learning to High-Performance Scientific Computing. IEEE Micro 2019, 39, 58–61. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, Z.; Liu, L.; Shen, H.; Huang, Y.; Shi, C.; Cai, S.; Song, Y.; Du, S.; Xu, Q. Secure Communication Scheme Based on a New 5D Multistable Four-Wing Memristive Hyperchaotic System with Disturbance Inputs. Complexity 2020, 2020. [Google Scholar] [CrossRef]
- Dukhan, A.; Jayalath, D.; van Heijster, P.; Senadji, B.; Banks, J. A generalized multilevel-hybrid chaotic oscillator for low-cost and power-efficient short-range chaotic communication systems. EURASIP J. Wirel. Commun. Netw. 2020, 2020, 23. [Google Scholar] [CrossRef]
- Rao, F.Y.; Bertino, E. Privacy Techniques for Edge Computing Systems. Proc. IEEE 2019, 107, 1632–1654. [Google Scholar] [CrossRef]
- Xiao, Y.; Jia, Y.; Liu, C.; Cheng, X.; Yu, J.; Lv, W. Edge computing security: State of the art and challenges. Proc. IEEE 2019, 107, 1608–1631. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Hui, H.; Zhou, C.; Xu, S.; Lin, F. A novel secure data transmission scheme in industrial internet of things. China Commun. 2020, 17, 73–88. [Google Scholar] [CrossRef]
- Voronova, A.; Tsareva, P.; Zhilenkov, A. The Synthesis Problem of a Chaotic Signal Computer System for Secure Data Transmission. In Proceedings of the 2020 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), St. Petersburg and Moscow, Russia, 27–30 January 2020; pp. 551–555. [Google Scholar]
- Peng, H.; Tian, Y.; Kurths, J.; Li, L.; Yang, Y.; Wang, D. Secure and energy-efficient data transmission system based on chaotic compressive sensing in body-to-body networks. IEEE Trans. Biomed. Circ. Syst. 2017, 11, 558–573. [Google Scholar] [CrossRef]
- Miliou, A.N.; Antoniades, I.P.; Stavrinides, S.G.; Anagnostopoulos, A.N. Secure communication by chaotic synchronization: Robustness under noisy conditions. Nonlinear Anal. Real World Appl. 2007, 8, 1003–1012. [Google Scholar] [CrossRef]
- Anagnostopoulos, A.; Miliou, A.; Stavrinides, S.; Dmitriev, A.; Efremova, E. Digital information transmission using discrete chaotic signal. In Chaos Synchronization and Cryptography for Secure Communications: Applications for Encryption; IGI Global: Hershey, PA, USA, 2011; pp. 439–462. [Google Scholar]
- Stavrinides, S.; Anagnostopoulos, A.; Miliou, A.; Valaristos, A.; Magafas, L.; Kosmatopoulos, K.; Papaioannou, S. Digital chaotic synchronized communication system. J. Eng. Sci. Technol. Rev. 2009, 2, 82–86. [Google Scholar] [CrossRef]
- Stavrinides, S.; Karagiorgos, N.; Papathanasiou, K.; Nikolaidis, S.; Anagnostopoulos, A. A digital nonautonomous chaotic oscillator suitable for information transmission. IEEE Trans. Circ. Syst. 2013, 60, 887–891. [Google Scholar] [CrossRef]
- Miliou, A.; Valaristos, A.; Stavrinides, S.; Kyritsi, K.; Anagnostopoulos, A. Characterization of a non-autonomous second-order non-linear circuit for secure data transmission. Chaos Solitons Fractals 2007, 33, 1248–1255. [Google Scholar] [CrossRef]
- Miliou, A.; Stavrinides, S.; Valaristos, A.; Anagnostopoulos, A. Nonlinear electronic circuit, Part II: Synchronization in a chaotic MODEM scheme. Nonlinear Anal. Theory Methods Appl. 2009, 71, e21–e31. [Google Scholar] [CrossRef]
- Sprott, J.C. Chaos and Time-Series Analysis; Oxford University Press Inc.: Oxford, UK, 2003. [Google Scholar]
- Von Neumann, J. Probabilistic logics and the synthesis of reliable organisms from unreliable components. Autom. Stud. 1956, 34, 43–98. [Google Scholar]
- Ardakani, A.; Leduc-Primeau, F.; Onizawa, N.; Hanyu, T.; Gross, W.J. VLSI implementation of deep neural network using integral stochastic computing. IEEE Trans. Very Large Scale Integrat. (VLSI) Syst. 2017, 25, 2688–2699. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.; Yu, J.; Seo, J.; Lee, J.; Choi, K. Dynamic energy-accuracy trade-off using stochastic computing in deep neural networks. In Proceedings of the 53rd Annual Design Automation Conference, Austin, TX, USA, 5–9 June 2016; pp. 1–6. [Google Scholar]
- Morro, A.; Canals, V.; Oliver, A.; Alomar, M.L.; Rossello, J.L. Ultra-fast data-mining hardware architecture based on stochastic computing. PLoS ONE 2015, 10, e0124176. [Google Scholar] [CrossRef] [PubMed]
- Wang, R.; Han, J.; Cockburn, B.; Elliott, D. Stochastic circuit design and performance evaluation of vector quantization. In Proceedings of the 26th International Conference on Application-specific Systems, Architectures and Processors (ASAP), IEEE, Toronto, ON, Canada, 27–29 July 2015; pp. 111–115. [Google Scholar]
- Yuan, B.; Wang, Y.; Wang, Z. Area-efficient scaling-free DFT/FFT design using stochastic computing. IEEE Trans. Circ. Syst. 2016, 63, 1131–1135. [Google Scholar]
- Marin, S.T.; Reboul, J.Q.; Franquelo, L.G. Digital stochastic realization of complex analog controllers. IEEE Trans. Ind. Electron. 2002, 49, 1101–1109. [Google Scholar] [CrossRef]
- Toral, S.; Quero, J.; Ortega, J.; Franquelo, L. Stochastic A/D sigma-delta converter on FPGA. In Proceedings of the 42nd Midwest Symposium on Circuits and Systems (Cat. No.99CH36356), IEEE, Las Cruces, NM, USA, 8–11 August 1999; Volume 1, pp. 35–38. [Google Scholar]
- Moons, B.; Verhelst, M. Energy-Efficiency and Accuracy of Stochastic Computing Circuits in Emerging Technologies. IEEE J. Emerg. Select. Top. Circ. Syst. 2014, 4, 475–486. [Google Scholar] [CrossRef]
- Li, S.; Glova, A.O.; Hu, X.; Gu, P.; Niu, D.; Malladi, K.T.; Zheng, H.; Brennan, B.; Xie, Y. SCOPE: A Stochastic Computing Engine for DRAM-Based In-Situ Accelerator. In Proceedings of the 2018 51st Annual IEEE/ACM International Symposium on Microarchitecture (MICRO), Fukuoka, Japan, 20–24 October 2018; pp. 696–709. [Google Scholar]
- Schuster, H.; Just, W. Deterministic Chaos: An Introduction; Wiley: Hoboken, NJ, USA, 2006. [Google Scholar]
- Toral, S.; Quero, J.; Franquelo, L. Stochastic pulse coded arithmetic. In Proceedings of the 2000 IEEE International Symposium on Circuits and Systems (ISCAS), Geneva, Switzerland, 28–31 May 2000; Volume 1, pp. 599–602. [Google Scholar]
- Khanday, F.A.; Akhtar, R. Reversible stochastic computing. Int. J. Num. Model. Electron. Netw. Devi. Fields 2020, 33, e2711. [Google Scholar] [CrossRef]
- Camps, O.; Picos, R.; de Benito, C.; Al Chawa, M.M.; Stavrinides, S.G. Effective accuracy estimation and representation error reduction for stochastic logic operations. In Proceedings of the 2018 7th International Conference on Modern Circuits and Systems Technologies (MOCAST), IEEE, Thessaloniki, Greece, 7–9 May 2018; pp. 1–4. [Google Scholar]
- Liu, S.; Gross, W.J.; Han, J. Introduction to Dynamic Stochastic Computing. IEEE Circ. Syst. Mag. 2020, 20, 19–33. [Google Scholar] [CrossRef]
- Shimizu, T.; Morioka, N. On the bifurcation of a symmetric limit cycle to an asymmetric one in a simple model. Phys. Lett. A 1980, 76, 201–204. [Google Scholar] [CrossRef]
- Neugebauer, F.; Polian, I.; Hayes, J.P. S-box-based random number generation for stochastic computing. Microproces. Microsyst. 2018, 61, 316–326. [Google Scholar] [CrossRef]
- Rai, V.K.; Tripathy, S.; Mathew, J. Memristor based random number generator: Architectures and evaluation. Proc. Comput. Sci. 2018, 125, 576–583. [Google Scholar] [CrossRef]
- Yang, B.B.; Xu, N.; Zhou, E.R.; Li, Z.W.; Li, C.; Yi, P.Y.; Fang, L. A method of generating random bits by using electronic bipolar memristor. Chin. Phys. B 2020, 29, 048505. [Google Scholar] [CrossRef]
- Téllez, M.; Mejía, J.; López, H.; Hernández, C. Random Number Generator with Long-Range Dependence and Multifractal Behavior Based on Memristor. Electronics 2020, 9, 1607. [Google Scholar] [CrossRef]
- Picos, R.; Roca, M.; Iniguez, B.; Garcia-Moreno, E. A new procedure to extract the threshold voltage of MOSFETs using noise-reduction techniques. Solid-State Electron. 2003, 47, 1953–1958. [Google Scholar] [CrossRef]
- Takens, F. Detecting strange attractors in turbulence. In Dynamical Systems and Turbulence, Warwick 1980; Springer: Berlin/Heidelberg, Germany, 1981; pp. 366–381. [Google Scholar]
- Grassberger, P.; Procaccia, I. Characterization of strange attractors. Phys. Rev. Lett. 1983, 50, 346. [Google Scholar] [CrossRef]
- Grassberger, P.; Procaccia, I. Dimensions and entropies of strange attractors from a fluctuating dynamics approach. Phys. D Nonlinear Phenomen. 1984, 13, 34–54. [Google Scholar] [CrossRef]
- Grassberger, P.; Procaccia, I. Measuring the strangeness of strange attractors. In The Theory of Chaotic Attractors; Springer: Berlin/Heidelberg, Germany, 2004; pp. 170–189. [Google Scholar]
- Bryant, P.; Brown, R.; Abarbanel, H.D. Lyapunov exponents from observed time series. Phys. Rev. Lett. 1990, 65, 1523. [Google Scholar] [CrossRef] [PubMed]
- Abarbanel, H.D.; Brown, R.; Sidorowich, J.J.; Tsimring, L.S. The analysis of observed chaotic data in physical systems. Rev. Modern Phys. 1993, 65, 1331. [Google Scholar] [CrossRef]
- Camps, O.; Stavrinides, S.G.; Picos, R. Efficient Implementation of Memristor Cellular Nonlinear Networks using Stochastic Computing. In Proceedings of the 2020 European Conference on Circuit Theory and Design (ECCTD), IEEE, Sofia, Bulgaria, 7–10 September 2020; pp. 1–4. [Google Scholar]
- Mathur, M.; Aarnav. Demystification of Vedic Multiplication Algorithm. Am. J. Comput. Math. 2017, 7, 94. [Google Scholar] [CrossRef][Green Version]
- Kamble, M.M.; Ugale, S.P. FPGA implementation and analysis of different multiplication algorithms. Int. J. Comput. Appl. 2016, 149, 8887. [Google Scholar]
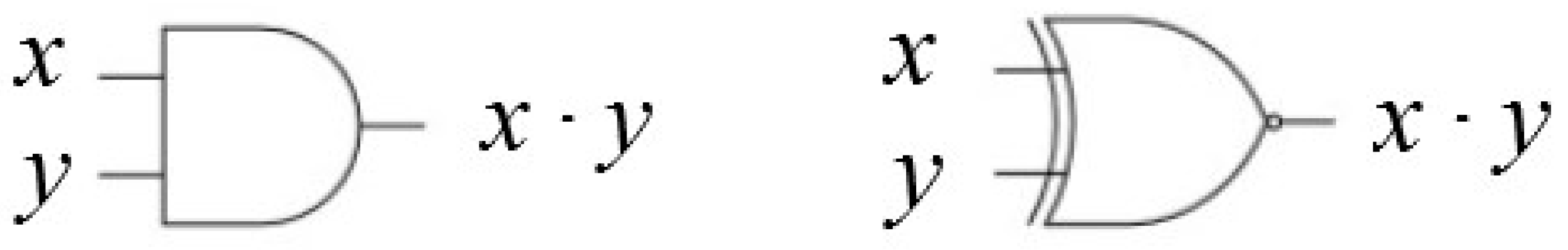

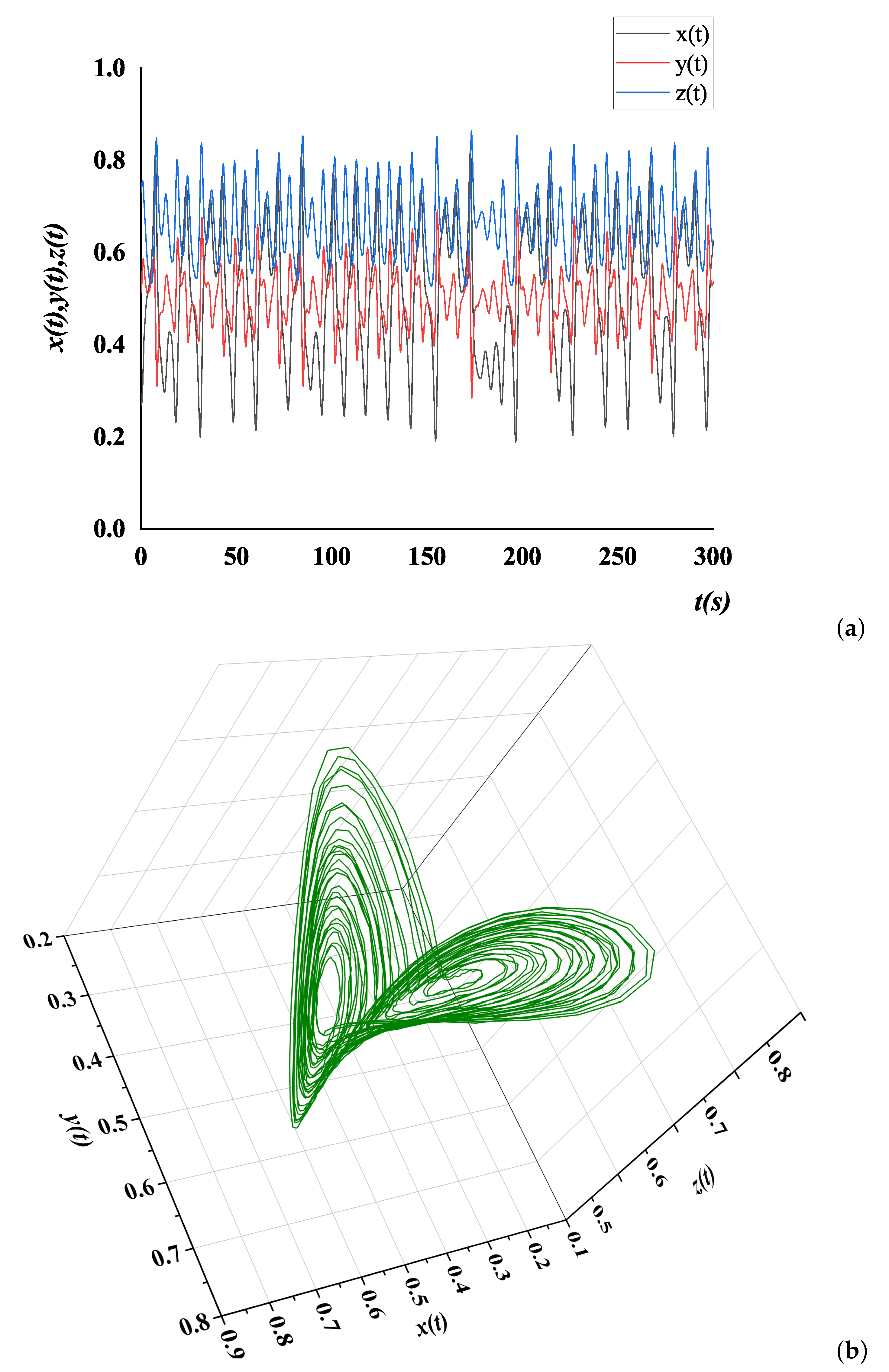

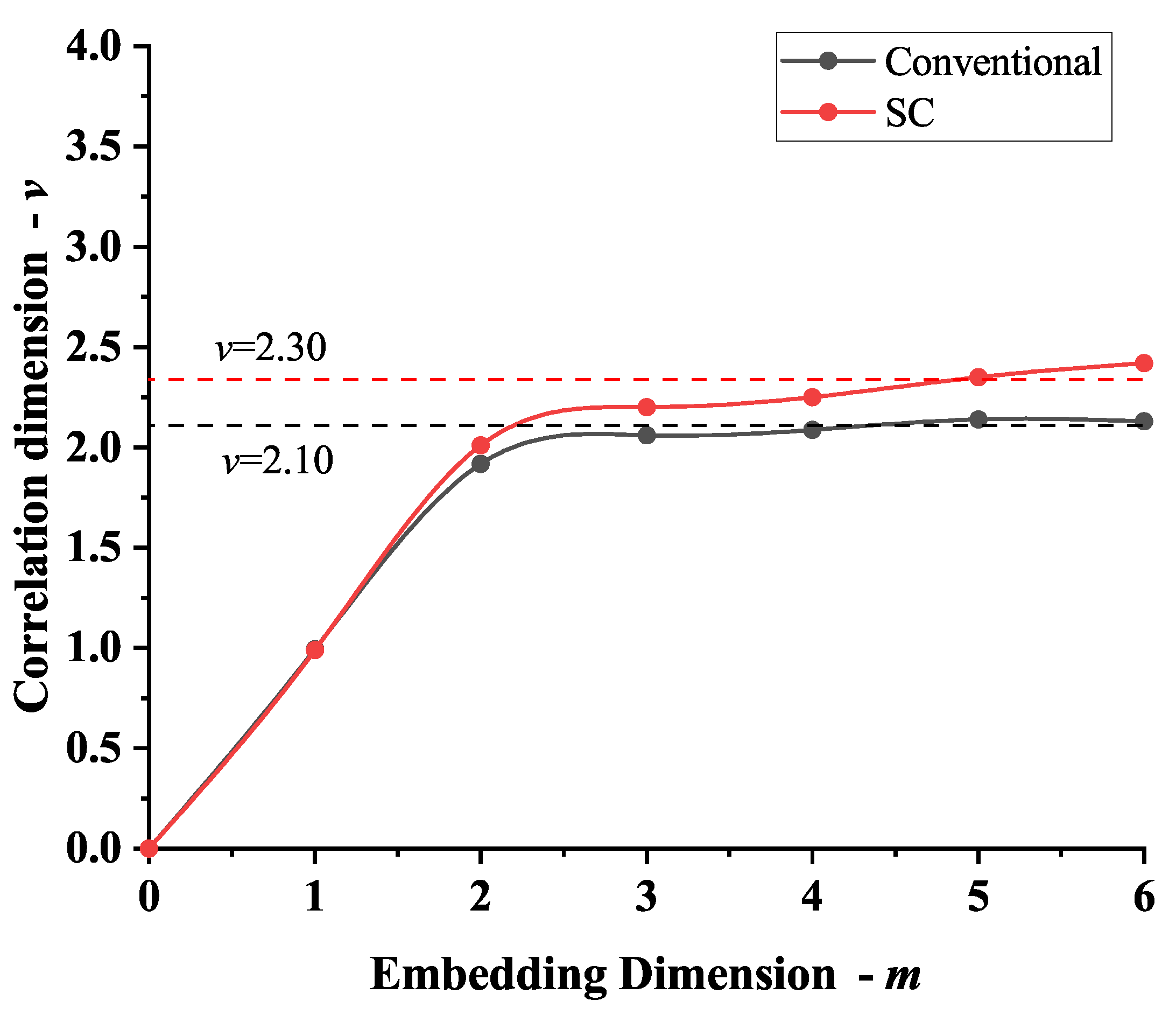

| Order | Classical | SC |
|---|---|---|
| 0.02112 | 0.03774 | |
| −0.00487 | −0.00462 | |
| −0.31142 | −0.29139 |
| Algorithm | bits | Slices | LUTs |
|---|---|---|---|
| Vedic | 4 | 19 | 33 |
| SC | 6 | 1 | 1/3 * |
| Vedic | 16 | 346 | 622 |
| SC | 22 | 1 | 1/3 * |
| Vedic | 32 | 1427 | 2566 |
| SC | 32 | 1 | 1/3 * |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Camps, O.; Stavrinides, S.G.; Picos, R. Stochastic Computing Implementation of Chaotic Systems. Mathematics 2021, 9, 375. https://doi.org/10.3390/math9040375
Camps O, Stavrinides SG, Picos R. Stochastic Computing Implementation of Chaotic Systems. Mathematics. 2021; 9(4):375. https://doi.org/10.3390/math9040375
Chicago/Turabian StyleCamps, Oscar, Stavros G. Stavrinides, and Rodrigo Picos. 2021. "Stochastic Computing Implementation of Chaotic Systems" Mathematics 9, no. 4: 375. https://doi.org/10.3390/math9040375
APA StyleCamps, O., Stavrinides, S. G., & Picos, R. (2021). Stochastic Computing Implementation of Chaotic Systems. Mathematics, 9(4), 375. https://doi.org/10.3390/math9040375








