Privacy-Aware Access Protocols for MEC Applications in 5G †
Abstract
:1. Introduction
2. Review and Related Work
2.1. Review
2.2. Related Work
3. Statement of the Problem
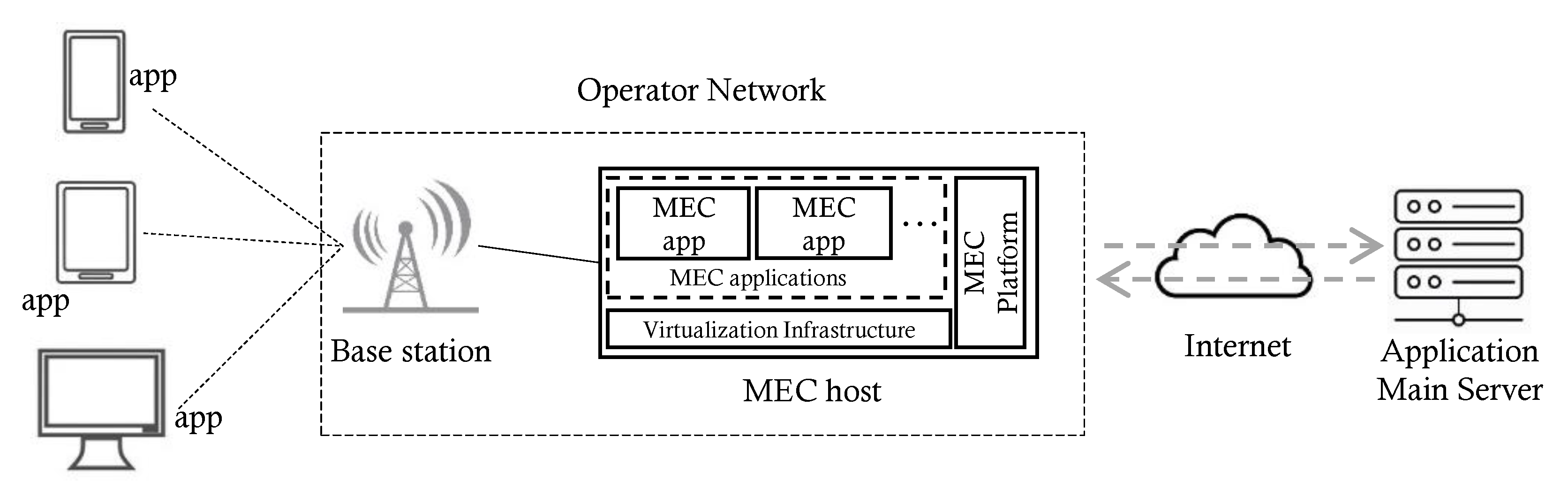
3.1. System Model
3.2. Adversary Model
3.2.1. Justification of the Adversary Model
3.3. Privacy Requirements
- R1-MNO-D: MNO should not learn which MEC application Alice is using.
- R2-MNO-D: MNO should not learn the content of what Alice sends to and receives from APPIFY.
- R3-MNO-I: MNO should not learn that Alice13 is the identifier of Alice for APPIFY.
- R4-MNO-U: MNO should not be able to distinguish whether two messages are related to the same MEC application.
- R5-MNO-U: MNO should not be able to distinguish whether two messages are related to the same user identifier for the MEC application.
- R6-MEC-D: MEC should not learn the content that Alice sends to and receives from APPIFY.
- R7-MEC-I: MEC should not learn that identifiers “Alice” or IMSI are relevant to the messages.
- R8-MEC-I: MEC should not learn that identifier Alice13 is relevant to the messages.
- R9-MEC-U: MEC should not be able to distinguish whether two messages are related to the same person or the same IMSI.
- R10-MEC-U: MEC should not be able to distinguish whether two messages are related to the same user identifier for a MEC application.
- R11-APP-D: APPIFY should not learn anything related to Alice in addition to what can be deduced from information that Alice provides while communicating with APPIFY.
- R12-APP-I: APPIFY should not learn that “Alice” or IMSI is related to Alice13.
- R13-APP-U: APPIFY should not distinguish whether two messages are coming from the same device.
- R14-APP-U: APPIFY should not distinguish whether two messages are related to the same IMSI.
- R15-OUT-D: Outsiders should not learn which MEC application Alice is using.
- R16-OUT-D: Outsiders should not learn the content of what Alice sends and receives.
- R17-OUT-I: Outsiders should not learn that the identifiers “Alice” or IMSI are relevant to Alice.
- R18-OUT-I: Outsiders should not learn that identifier Alice13 is relevant to Alice.
- R19-OUT-U: Outsiders should not be able to distinguish whether two messages are related to the same MEC application.
- R20-OUT-U: Outsiders should not be able to distinguish whether two messages are related to the same user identifier.
3.3.1. Justification of Requirements
Requirements about MNO (R1–R5)
Requirements about MEC (R6–R10)
Requirements about APPIFY (R11–R14)
Requirements about Outsiders (R15–R20)
3.3.2. Privacy Requirements for Dependent Parties
Combination 1: MNO, MEC, and APPIFY Are Dependent
Combination 2: MNO and MEC Are Dependent
Combination 3: MEC and APPIFY Are Dependent
Combination 4: MNO and APPIFY Are Dependent
4. Results and Discussion
4.1. Solution
4.1.1. Registration
4.1.2. Subsequent Access to the Main Server of APPIFY
4.1.3. Access to APPIFY in MEC
- UE of Alice and MNO run the 5G authentication and key agreement (AKA) procedure. As the result of this procedure, a secure connection is established between the UE of Alice and MNO. During the AKA procedure, IMSI is used as an identifier of Alice, and in the end, a temporary identifier TMSI is shared. After this step, the UE of Alice uses TMSI for further identification to MNO.
- Alice sends a request to MNO for establishing DTLS over UDP connection toward MEC.
- If there is no deployed MEC in the network of MNO, then MNO replies to Alice with an error message. In this case, Alice connects to the main server of APPIFY. Otherwise, MNO sends the IP address of MEC to Alice.
- Alice and MEC complete the DTLS handshake. MEC sends to Alice during the handshake, and Alice verifies this certificate by using the verification key of MNO, .
- Alice sends a request for communication with APPIFY to MEC through the DTLS channel.
- If there is no APPIFY in MEC, then MEC replies to Alice with an error message. In this case, Alice connects to the main server of APPIFY, similarly as in Step 3. Otherwise, MEC assigns a session number N to the DTLS connection and links it with APPIFY.
- MEC confirms to the UE that APPIFY is hosted in MEC.
- Alice sends a request for TLS over the TCP connection with APPIFY through MEC. When MEC receives the request, it inserts the session number N to the message and forwards it to APPIFY. The APPIFY also includes N in the messages directed to Alice in further messages. This way, MEC will deliver the messages to the correct DTLS channels (without the session number). We do not go further into the communication details inside the MEC host.APPIFY sends the certificate to the UE of Alice during the TLS handshake. The UE verifies this certificate by using the verification key of the main server of APPIFY, . The TLS connection is established between Alice and APPIFY after successfully completing the handshake.
- The TLS handshake ensures that Alice is talking with the correct entity. For the mutual authentication, Alice reveals her identity to APPIFY by initiating a post-handshake client authentication with APPIFY. In this phase, Alice sends her certificate to APPIFY, and APPIFY verifies it with the verification key of the main server of APPIFY, .
- Alice sends a service request to APPIFY through the TLS connection.
- APPIFY replies with the service response to Alice through the TLS connection.
- The communication between Alice and APPIFY continues as in Steps 10 and 11.
4.2. Analysis
4.2.1. Independent Case
Data and Identity Confidentiality
Unlinkability
4.2.2. Dependent Cases
MNO and MEC Combination
MEC and APPIFY Combination
MNO and APPIFY Combination
5. Final Remarks
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| 3GPP | 3rd Generation Partnership Project |
| 5G | Fifth Generation |
| AKA | Authentication and Key Agreement |
| AF | Application Function |
| DoS | Denial of Service |
| DTLS | Datagram Transport Layer Security |
| EST | Enrollment over Secure Transport |
| ETSI | European Telecommunication Standards Institute |
| GUTI | Globally Unique Temporary Identifier |
| IMSI | International Mobile Subscriber Identity |
| IoT | Internet of Things |
| MEC | Multi-Access Edge Computing |
| MNO | Mobile Network Operator |
| NFV | Network Function Virtualization |
| OR | Onion Routing |
| SDN | Software-Defined Networking |
| SUPI | Subscription Permanent Identifier |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security |
| TMSI | Temporary Mobile Subscriber Identity |
| UDP | User Datagram Protocol |
| UE | User Equipment |
| UPF | User Plane Function |
| V2X | Vehicle-to-Everything |
| VPN | Virtual Private Network |
References
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On Multi-Access Edge Computing: A Survey of the Emerging 5G Network Edge Cloud Architecture and Orchestration. IEEE Commun. Surv. Tutor. 2017, 19, 1657–1681. [Google Scholar] [CrossRef] [Green Version]
- Giust, F.; Verin, G.; Antevski, K.; Chou, J.; Fang, Y.; Featherstone, W.; Fontes, F.; Frydman, D.; Li, A.; Manzalini, A.; et al. MEC Deployments in 4G and Evolution Towards 5G. White Paper 2018, 24, 1–24. [Google Scholar]
- Pham, Q.V.; Fang, F.; Ha, V.N.; Piran, M.J.; Le, M.; Le, L.B.; Hwang, W.J.; Ding, Z. A Survey of Multi-Access Edge Computing in 5G and Beyond: Fundamentals, Technology Integration, and State-of-the-Art. IEEE Access 2020, 8, 116974–117017. [Google Scholar] [CrossRef]
- 3GPP. 5G System Enhancements for Edge Computing; Technical Specification TS 23.548 V17.1.0; 3GPP: Valbonne, France, 2021. [Google Scholar]
- Parada, C.; Fontes, F.; Marques, C.; Cunha, V.; Leitao, C. Multi-Access Edge Computing: A 5G Technology. In Proceedings of the 2018 European Conference on Networks and Communications (EuCNC), Ljubljana, Slovenia, 18–21 June 2018; IEEE: Ljubljana, Slovenia, 2018; pp. 277–279. [Google Scholar] [CrossRef]
- Mahbub, M.; Apu Gazi, M.S.; Arabi Provat, S.A.; Islam, M.S. Multi-Access Edge Computing-Aware Internet of Things: MEC-IoT. In Proceedings of the 2020 Emerging Technology in Computing, Communication and Electronics (ETCCE), Dhaka, Bangladesh, 21–22 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Naouri, A.; Wu, H.; Nouri, N.A.; Dhelim, S.; Ning, H. A Novel Framework for Mobile-Edge Computing by Optimizing Task Offloading. IEEE Internet Things J. 2021, 8, 13065–13076. [Google Scholar] [CrossRef]
- Sun, Q.; Xu, J.; Ma, X.; Zhou, A.; Hsu, C.H.; Wang, S. Edge-Enabled Distributed Deep Learning for 5G Privacy Protection. IEEE Netw. 2021, 35, 213–219. [Google Scholar] [CrossRef]
- Zhu, R.; Liu, L.; Song, H.; Ma, M. Multi-Access Edge Computing Enabled Internet of Things: Advances and Novel Applications. Neural Comput. Appl. 2020, 32, 15313–15316. [Google Scholar] [CrossRef]
- Zanzi, L.; Cirillo, F.; Sciancalepore, V.; Giust, F.; Costa-Perez, X.; Mangiante, S.; Klas, G. Evolving Multi-Access Edge Computing to Support Enhanced IoT Deployments. IEEE Commun. Stand. Mag. 2019, 3, 26–34. [Google Scholar] [CrossRef]
- ETSI. Multi-Access Edge Computing (MEC); V2X Information Service API; Group Specification GS MEC 030 V2.1.1; ETSI: Sophia Antipolis, France, 2020. [Google Scholar]
- Porambage, P.; Okwuibe, J.; Liyanage, M.; Ylianttila, M.; Taleb, T. Survey on Multi-Access Edge Computing for Internet of Things Realization. IEEE Commun. Surv. Tutor. 2018, 20, 2961–2991. [Google Scholar] [CrossRef] [Green Version]
- Kekki, S.; Featherstone, W.; Fang, Y.; Kuure, P.; Li, A.; Ranjan, A.; Purkayastha, D.; Feng, J.; Frydman, D.; Verin, G.; et al. MEC in 5G Networks; White Paper 28; ETSI: Sophia Antipolis, France, 2018. [Google Scholar]
- Hammer, J.; Moll, P.; Hellwagner, H. Transparent Access to 5G Edge Computing Services. In Proceedings of the 2019 IEEE International Parallel and Distributed Processing Symposium Workshops (IPDPSW), Rio de Janeiro, Brazil, 20–24 May 2019; pp. 895–898. [Google Scholar] [CrossRef]
- Meir, M. What Is a Third-Party Service Provider? 2021. Available online: https://securityscorecard.com/blog/what-is-a-third-party-service-provider (accessed on 17 January 2022).
- ETSI. Multi-Access Edge Computing (MEC); Phase 2: Use Cases and Requirements; Group Specification GS MEC 002 V2.1.1; ETSI: Sophia Antipolis, France, 2018. [Google Scholar]
- Dresch, A.; Lacerda, D.P.; Antunes, J.A.V., Jr. Design Science Research: A Method for Science and Technology Advancement; Springer International Publishing: Cham, Switzerland, 2015. [Google Scholar] [CrossRef]
- Peffers, K.; Tuunanen, T.; Rothenberger, M.A.; Chatterjee, S. A Design Science Research Methodology for Information Systems Research. J. Manag. Inf. Syst. 2007, 24, 45–77. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.D.; Liyanage, M. Survey on Multi-Access Edge Computing Security and Privacy. IEEE Commun. Surv. Tutor. 2021, 23, 1078–1124. [Google Scholar] [CrossRef]
- University of Delaware. Managing Data Confidentiality. 2020. Available online: https://www1.udel.edu/security/data/confidentiality.html (accessed on 15 December 2021).
- 3GPP. 3G Security; Security Architecture; Technical Specification TS 33.102 V16.0.0; 3GPP: Valbonne, France, 2020. [Google Scholar]
- Paverd, A.; Martin, A.; Brown, I. Modelling and Automatically Analyzing Privacy Properties for Honest-but-Curious Adversaries; Technical Report; University of Oxford: Oxford, UK, 2014. [Google Scholar]
- Alshalan, A.; Pisharody, S.; Huang, D. A Survey of Mobile VPN Technologies. IEEE Commun. Surv. Tutor. 2016, 18, 1177–1196. [Google Scholar] [CrossRef]
- Singh, K.K.V.V.; Gupta, H. A New Approach for the Security of VPN. In Proceedings of the Second International Conference on Information and Communication Technology for Competitive Strategies—ICTCS ’16, Udaipur, India, 4–5 March 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Sawalmeh, H.; Malayshi, M.; Ahmad, S.; Awad, A. VPN Remote Access OSPF-based VPN Security Vulnerabilities and Counter Measurements. In Proceedings of the 2021 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Zallaq, Bahrain, 29–30 September 2021; pp. 236–241. [Google Scholar] [CrossRef]
- Goldschlag, D.M.; Reed, M.G.; Syverson, P.F. Hiding Routing Information. In Proceedings of the First International Workshop on Information Hiding, Cambridge, UK, 30 May–1 June 1996; Springer: Berlin/Heidelberg, Germany, 1996; pp. 137–150. [Google Scholar]
- Buccafurri, F.; De Angelis, V.; Idone, M.F.; Labrini, C.; Lazzaro, S. Achieving Sender Anonymity in Tor against the Global Passive Adversary. Appl. Sci. 2022, 12, 137. [Google Scholar] [CrossRef]
- Chauhan, M.; Singh, A.K. Survey of Onion Routing Approaches: Advantages, Limitations and Future Scopes. In Proceeding of the International Conference on Computer Networks, Big Data and IoT (ICCBI—2019), Madurai, India, 19–20 December 2019; Pandian, A.P., Palanisamy, R., Ntalianis, K., Eds.; Springer International Publishing: Cham, Switzerland, 2020; Volume 49, pp. 686–697. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.; Liyanage, M. MEC-enabled 5G Use Cases: A Survey on Security Vulnerabilities and Countermeasures. ACM Comput. Surv. 2021, 54, 1–37. [Google Scholar] [CrossRef]
- Du, M.; Wang, K.; Chen, Y.; Wang, X.; Sun, Y. Big Data Privacy Preserving in Multi-Access Edge Computing for Heterogeneous Internet of Things. IEEE Commun. Mag. 2018, 56, 62–67. [Google Scholar] [CrossRef]
- Okwuibe, J.; Liyanage, M.; Ahmad, I.; Ylianttila, M. Cloud and MEC Security. In A Comprehensive Guide to 5G Security; Liyanage, M., Ahmad, I., Abro, A.B., Gurtov, A., Ylianttila, M., Eds.; John Wiley & Sons, Ltd.: Chichester, UK, 2018; pp. 373–397. [Google Scholar] [CrossRef]
- Kim, Y.; Park, J.G.; Lee, J.H. Security Threats in 5G Edge Computing Environments. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 21–23 October 2020; pp. 905–907. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.D.; Liyanage, M. Realizing Multi-Access Edge Computing Feasibility: Security Perspective. In Proceedings of the 2019 IEEE Conference on Standards for Communications and Networking (CSCN), Granada, Spain, 28–30 October 2019; pp. 1–7. [Google Scholar] [CrossRef] [Green Version]
- He, X.; Jin, R.; Dai, H. Deep PDS-Learning for Privacy-Aware Offloading in MEC-Enabled IoT. IEEE Internet Things J. 2019, 6, 4547–4555. [Google Scholar] [CrossRef]
- Lee, J.; Kim, D.; Park, J.; Park, H. A Multi-Server Authentication Protocol Achieving Privacy Protection and Traceability for 5G Mobile Edge Computing. In Proceedings of the 2021 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 10–12 January 2021; pp. 1–4. [Google Scholar] [CrossRef]
- Zhang, P.; Durresi, M.; Durresi, A. Mobile Privacy Protection Enhanced with Multi-access Edge Computing. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Krakow, Poland, 16–18 May 2018; pp. 724–731. [Google Scholar] [CrossRef]
- Kotulski, Z.; Niewolski, W.; Nowak, T.W.; Sepczuk, M. New Security Architecture of Access Control in 5G MEC. In Security in Computing and Communications; Thampi, S.M., Wang, G., Rawat, D.B., Ko, R., Fan, C.I., Eds.; Communications in Computer and Information Science; Springer: Singapore, 2021; Volume 1364, pp. 77–91. [Google Scholar] [CrossRef]
- Khan, R.; Kumar, P.; Jayakody, D.N.K.; Liyanage, M. A Survey on Security and Privacy of 5G Technologies: Potential Solutions, Recent Advancements, and Future Directions. IEEE Commun. Surv. Tutor. 2020, 22, 196–248. [Google Scholar] [CrossRef] [Green Version]
- Ahmad, I.; Kumar, T.; Liyanage, M.; Okwuibe, J.; Ylianttila, M.; Gurtov, A. Overview of 5G Security Challenges and Solutions. IEEE Commun. Stand. Mag. 2018, 2, 36–43. [Google Scholar] [CrossRef] [Green Version]
- Carvalho, G.H.S.; Woungang, I.; Anpalagan, A.; Traore, I. When Agile Security Meets 5G. IEEE Access 2020, 8, 166212–166225. [Google Scholar] [CrossRef]
- Ojanpera, T.; Berg, H.V.D.; IJntema, W.; Schwartz, R.D.S.; Djurica, M. Application Synchronization Among Multiple MEC Servers in Connected Vehicle Scenarios. In Proceedings of the 2018 IEEE 88th Vehicular Technology Conference (VTC-Fall), Chicago, IL, USA, 27–30 August 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Do, Q.; Martini, B.; Choo, K.K.R. The role of the adversary model in applied security research. Comput. Secur. 2019, 81, 156–181. [Google Scholar] [CrossRef]
- Rice, T.; Seppala, G.; Edgar, T.W.; Cain, D.; Choi, E. Fused Sensor Analysis and Advanced Control of Industrial Field Devices for Security: Cymbiote Multi-Source Sensor Fusion Platform. In Proceedings of the Northwest Cybersecurity Symposium, Richland, WA, USA, 8–10 April 2019; pp. 1–8. [Google Scholar] [CrossRef] [Green Version]
- Halpern, J.Y.; Pucella, R. Modeling Adversaries in a Logic for Security Protocol Analysis. In Formal Aspects of Security; Goos, G., Hartmanis, J., van Leeuwen, J., Abdallah, A.E., Ryan, P., Schneider, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2003; Volume 2629, pp. 115–132. [Google Scholar] [CrossRef] [Green Version]
- Moradi, A.; Venkategowda, N.K.D.; Pouria Talebi, S.; Werner, S. Distributed Kalman Filtering with Privacy against Honest-but-Curious Adversaries. In Proceedings of the 2021 55th Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 31 October–3 November 2021; pp. 790–794. [Google Scholar] [CrossRef]
- Herzog, J. A computational interpretation of Dolev–Yao adversaries. Theor. Comput. Sci. 2005, 340, 57–81. [Google Scholar] [CrossRef] [Green Version]
- Information Commissioner’s Office (ICO). Estate Agency Fined £80,000 for Failing to Keep Tenants’ Data Safe. 2019. Available online: https://ico.org.uk/about-the-ico/news-and-events/news-and-blogs/2019/07/estate-agency-fined-80-000-for-failing-to-keep-tenants-data-safe/ (accessed on 15 December 2021).
- Freedman, M. How Businesses Are Collecting Data (And What They’re Doing With It). 2020. Available online: https://www.businessnewsdaily.com/10625-businesses-collecting-data.html (accessed on 15 December 2021).
- Guichard, D. Bell numbers. In An Introduction to Combinatorics and Graph Theory; Creative Commons: San Francisco, CA, USA, 2014; pp. 21–27. [Google Scholar]
- Van Tilborg, H.C.A.; Jajodia, S. (Eds.) Commercial Security Model. In Encyclopedia of Cryptography and Security; Springer: Boston, MA, USA, 2011; p. 224. [Google Scholar] [CrossRef]
- Turner, S. EST (Enrollment over Secure Transport) Extensions; IETF RFC 8295; RFC Editor: Wilmington, DE, USA, 2018. [Google Scholar] [CrossRef] [Green Version]
- Rescorla, E.; Modadugu, N. Datagram Transport Layer Security Version 1.2; IETF RFC 6347; RFC Editor: Wilmington, DE, USA, 2012. [Google Scholar] [CrossRef]
- Rescorla, E. The Transport Layer Security (TLS) Protocol Version 1.3; IETF RFC 8446; RFC Editor: Wilmington, DE, USA, 2018. [Google Scholar] [CrossRef]
- Reardon, J.; Goldberg, I. Improving tor using a TCP-over-DTLS tunnel. In Proceedings of the 18th Conference on USENIX Security Symposium, Montreal, QC, Canada, 10–14 August 2009; USENIX Association: Montreal, QC, Canada, 2009; pp. 119–134. [Google Scholar] [CrossRef]
- Rescorla, E.; Dierks, T. The Transport Layer Security (TLS) Protocol Version 1.2; IETF RFC 5246; RFC Editor: Wilmington, DE, USA, 2008. [Google Scholar] [CrossRef]
- Feng, W.C.; Kaiser, E.; Feng, W.C.; Luu, A. The design and implementation of network puzzles. In Proceedings of the IEEE 24th Annual Joint Conference of the IEEE Computer and Communications Societies, Miami, FL, USA, 13–17 March 2005; Volume 4, pp. 2372–2382. [Google Scholar] [CrossRef]
- Gusatu, M.; Olimid, R.F. Improved security solutions for DDoS mitigation in 5G Multi-access Edge Computing. arXiv 2021, arXiv:2111.04801. [Google Scholar]
- Taylor, V.F.; Spolaor, R.; Conti, M.; Martinovic, I. Robust Smartphone App Identification via Encrypted Network Traffic Analysis. IEEE Trans. Inf. Forensics Secur. 2018, 13, 63–78. [Google Scholar] [CrossRef] [Green Version]
- Saltaformaggio, B.; Choi, H.; Johnson, K.; Kwon, Y.; Zhang, Q.; Zhang, X.; Xu, D.; Qian, J. Eavesdropping on Fine-Grained User Activities within Smartphone Apps over Encrypted Network Traffic. In Proceedings of the 10th USENIX Conference on Offensive Technologies, WOOT’16, Austin, TX, USA, 8–9 August 2016; USENIX Association: Austin, TX, USA, 2016; pp. 69–78. [Google Scholar] [CrossRef]
- Pironti, A.; Strub, P.Y.; Bhargavan, K. Identifying Website Users by TLS Traffic Analysis: New Attacks and Effective Countermeasures, Revision 1; Research Report; INRIA: Rocquencourt, France, 2012. [Google Scholar]



| Dependency Combinations | |||||
| Requirements | NONE | ALL | MNO &MEC | MEC &APP | MNO &APP |
| R1-MNO-D | ⚪ | N/A | N/A | ⚪ | ⚪ |
| R2-MNO-D | ⚫ | N/A | ⚫ | ⚫ | - |
| R3-MNO-I | ⚫ | N/A | ⚫ | ⚫ | - |
| R4-MNO-U | ⚪ | N/A | N/A | ⚪ | ⚪ |
| R5-MNO-U | ⚪ | N/A | ⚪ | ⚪ | ⚪ |
| R6-MEC-D | ⚫ | N/A | ⚫ | ⚪ | ⚫ |
| R7-MEC-I | ⚫ | N/A | N/A | ⚫ | ⚫ |
| R8-MEC-I | ⚫ | N/A | ⚫ | N/A | ⚫ |
| R9-MEC-U | ⚪ | N/A | N/A | ⚪ | ⚪ |
| R10-MEC-U | ⚪ | N/A | ⚪ | N/A | ⚪ |
| R11-APP-D | ⚫ | N/A | ⚫ | ⚫ | - |
| R12-APP-I | ⚫ | N/A | ⚫ | ⚫ | - |
| R13-APP-U | ⚪ | N/A | ⚪ | ⚪ | - |
| R14-APP-U | ⚪ | N/A | ⚪ | ⚪ | - |
| R15-OUT-D | ⚪ | ⚪ | ⚪ | ⚪ | ⚪ |
| R16-OUT-D | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ |
| R17-OUT-I | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ |
| R18-OUT-I | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ |
| R19-OUT-U | ⚪ | ⚪ | ⚪ | ⚪ | ⚪ |
| R20-OUT-U | ⚫ | ⚫ | ⚫ | ⚫ | ⚫ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Akman, G.; Ginzboorg, P.; Niemi, V. Privacy-Aware Access Protocols for MEC Applications in 5G. Network 2022, 2, 203-224. https://doi.org/10.3390/network2020014
Akman G, Ginzboorg P, Niemi V. Privacy-Aware Access Protocols for MEC Applications in 5G. Network. 2022; 2(2):203-224. https://doi.org/10.3390/network2020014
Chicago/Turabian StyleAkman, Gizem, Philip Ginzboorg, and Valtteri Niemi. 2022. "Privacy-Aware Access Protocols for MEC Applications in 5G" Network 2, no. 2: 203-224. https://doi.org/10.3390/network2020014