IoT and Blockchain Integration: Applications, Opportunities, and Challenges
Abstract
1. Introduction
Motivation and Contribution
- precisely defines and exemplifies IoT, blockchain technology-related, and relevant security terminologies.
- examines the importance of IoT and Blockchain security as evolving technologies.
- explains the challenges of IoT and Blockchain integration.
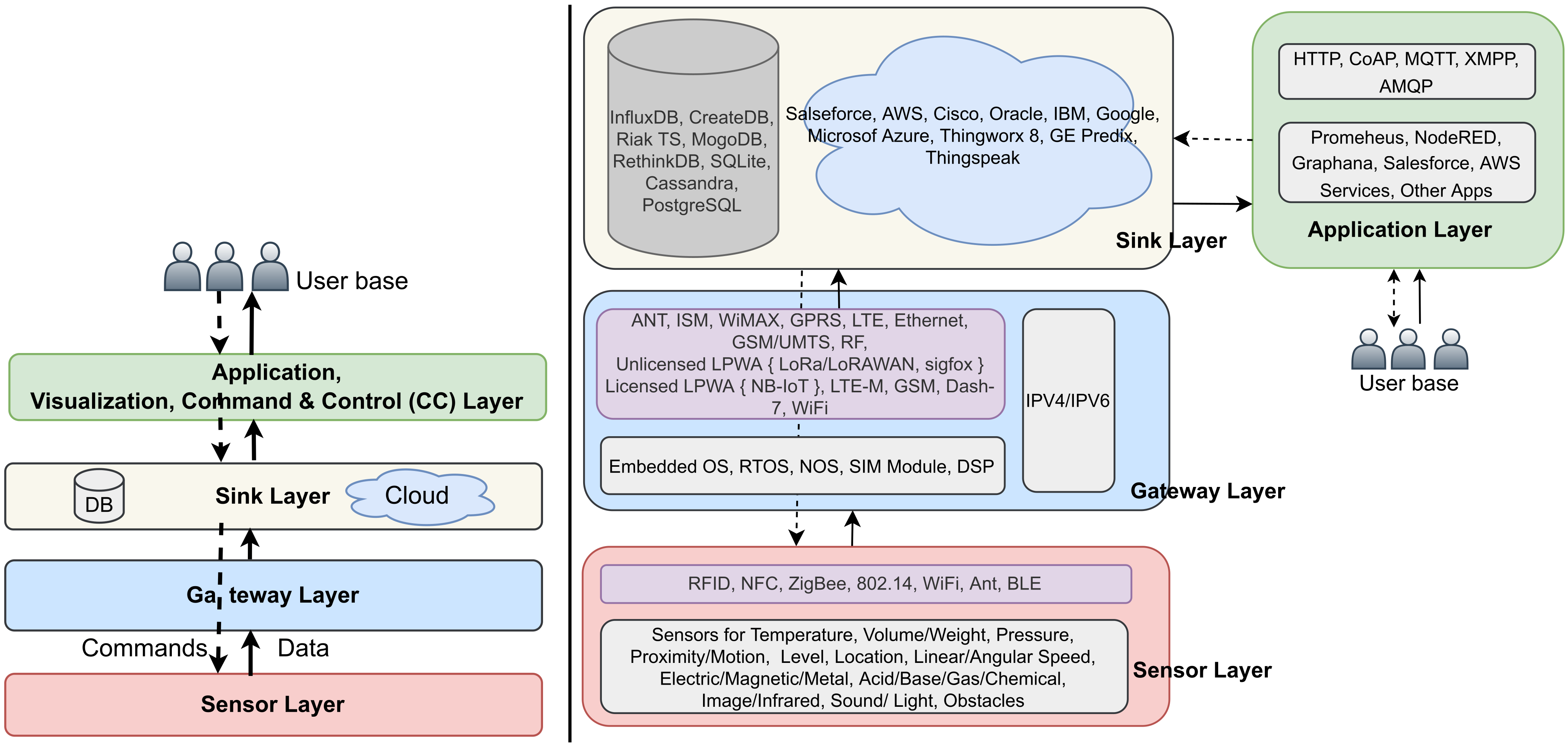
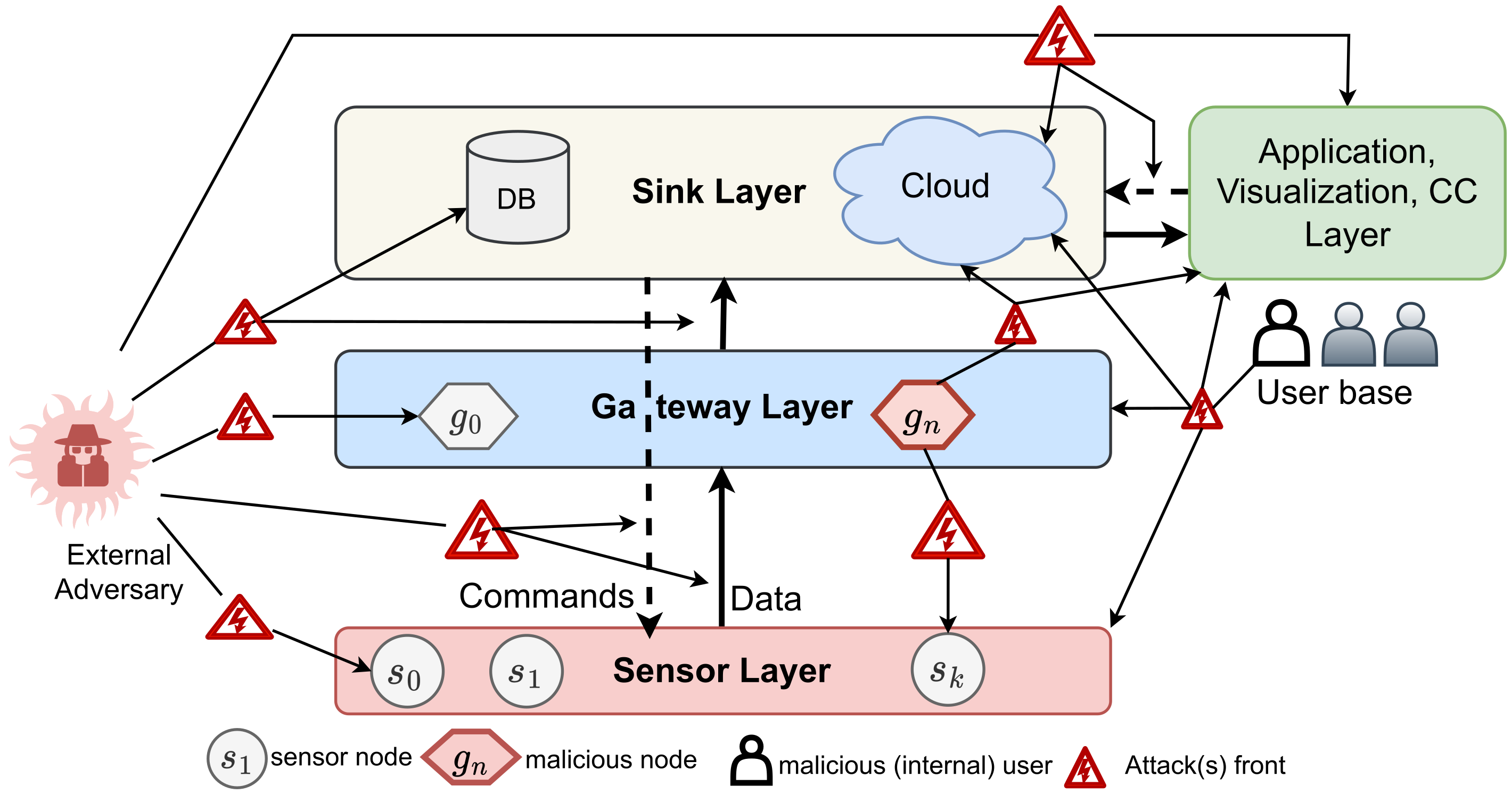
2. Architecture of IoT
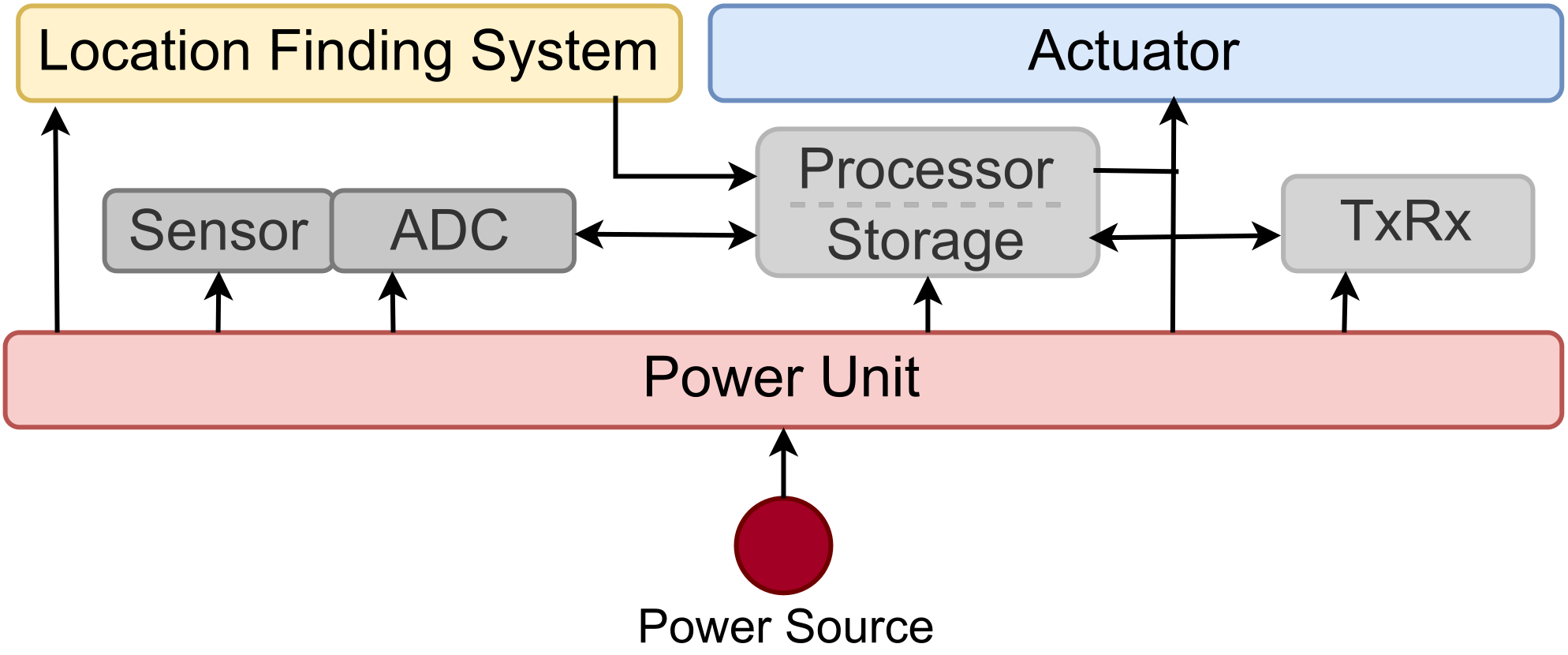
2.1. Sensor Layer
2.2. Gateway Layer
2.3. IoT Sink Layer
2.4. IoT Application, Visualization, Command, and Control Layer
3. Applications and Categories of IoTs
- (1)
- Climate and Environmental (Aquatic/Terrestrial) IoT: Environmental IoTs are composed of sensors employed for different purposes, such as detecting pathogens, chemicals, gas, temperature, and(or) other variables in an environment, such as land or water bodies [21]. For instance, regulatory bodies such as Environment Protection Agency (EPA) often employ IoT to monitor the risk factors that affect human and environmental health. Similarly, industries based on land and water resources have benefited from the IoTs for various business needs. For instance, climate and environmental IoTs have been used for real-time monitoring and forecasting of weather, and climatic conditions in an area [8].
- (2)
- (3)
- Industrial IoT: The use of IoTs has been profitable in industries of varying kinds, such as hospitals [2], manufacturing industries, and retail and whole-shale markets, among others. Everyday use cases of an industrial IoT include remote condition monitoring, digital work instructions, predictive mainteisce, and disaster management. Using industrial IoTs brings several benefits, such as maximizing revenue, reducing time to market, and lowering operational costs.
- (4)
- Smart Home IoT An IoT find(s) is one of its most popular applications inside a home setting. Automating lighting, sound, and kitchen work such as cooking and washing are automated by using different connected devices. Controlling and maintaining home climate can also be performed effectively using sensors such as thermostats [1,4,21].
- (5)
- Wearable IoT: Wearable IoT comprises wearable technologies such as Fitbit, Holter monitor, personal alarm devices, smartwatches, etc. The sensing devices have become so small that they have been integrated into normal clothing items such as bras or vests, caps, shoes, and travel/school backpacks [21,24,25]. Wearable IoT has helped monitor personal health and supports remote health services [3].
- (6)
- Smart City IoT: Smart city IoTs are an extended version of the smart home IoT [1]. It comprises many sensor technologies to sense an urban environment, streets, highways, traffic, and vehicle mobility. Smart retail shopping, intelligent health services, and smart parking are also an integral part of a smart city (https://en.wikipedia.org/wiki/Smart_city (accessed on 22 July 2022)) [4].
- (7)
- Vehicular IoT: Vehicular IoT can be considered one of the components of a smart city IoT. Sensors that collect data from terrestrial and aerial vehicular devices constitute vehicular IoT. The data may be helpful to route the vehicular devices efficiently or may be helpful to collect environmental data such as temperature and humidity. For instance, United Parcel Service (UPS), a shipping company, deploys sensors in its transport vehicles to collect data such as mileage, speed, fuel cost, etc., for big data analysis [26,27]. Unmanned aerial vehicles (UAVs) also use different sensor data to optimize their route and operations to support “collaborative autonomous driving, and advanced transportation [28]”.
4. Blockchain Technology
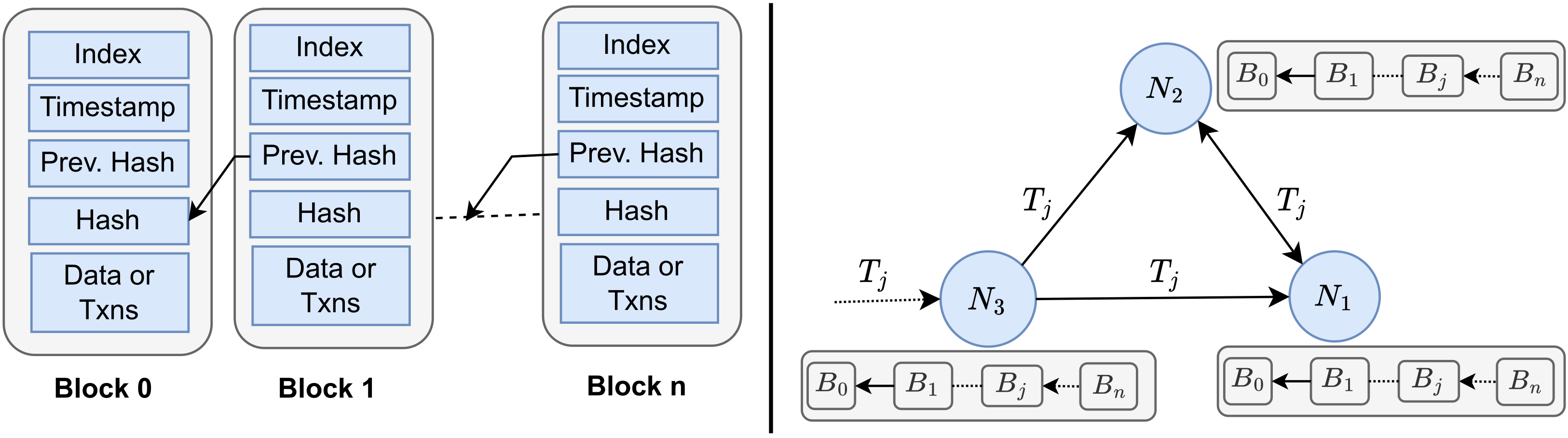
4.1. Overview of Blockchain Network
4.2. Types of Blockchain Networks
4.3. Applications of Blockchain Technology
- Financial Transactions and Trusted Digital Payment:In conventional digital payments, intermediaries such as banks, finances, and credit card companies act as a trusted party between a payee and a payer for any digital transactions [33]. It involves several tasks, such as bank balance verification of the payee, transaction validation, and payment verification. However, the network automates verification and validation with blockchain-based payment systems such as Bitcoin and Ethereum. As its main advantage, it reduces intermediaries’ fees and transaction completion time [30].
- Process Automation: Blockchain networks may also support “smart contracts”. Smart contracts are similar to regular business contracts except for the contract rules, terms (agreements), and transactions are encoded as a computer program and are executed automatically, in real-time, on blockchain network nodes [10]. The blockchain miners validate the outputs of the execution. Smart contracts save business operation time and cost and guarantee contract compliance. They have a higher potential for automating financial payments, financial audits, online transactions, document signature and approval, supply-chain operations, and so on [10].
- E-governance: E-governance is the practice of using information communication technology to provide government services, including issuing citizenship certificates, collecting taxes, delivering social securities, conducting elections, and crowd-sourcing [34,35]. Blockchain technology adds advantages to e-governance by automating most of the administrative services. Countries, including Estonia and China, have invested in research on the use of blockchain in e-governance to promote efficiency and effectiveness in the provision of public services [36,37].
- Data Redundancy: One of the chief features of a blockchain network is distributed data storage [16]. Both private and public blockchain networks enforce that the computing nodes securely keep a copy of application-related data. Any alteration of data in a store can be easily detected and recovered by importing from the network peers. For instance, DokChain (https://bit.ly/3QYRws1 (accessed on 13 July 2022)) project uses blockchain as a distributed data storage to store and process financial and clinical data. Such application enhances data integrity, auditability, and efficiency for healthcare and other related transactions and processes.
5. Materials and Methods
5.1. Research Questions
5.2. Data Sources
5.3. Search Criteria
5.4. Quality Evaluation
- Q1: Does this resource refer to both the {internet of Things, IoT} and {blockchain network, blockchain}?
- Q2: Does this resource refer to an {challenges, application} of {internet of Things, IoT} and/or {blockchain network, blockchain}?
- Q3: Does this resource’s title, abstract, or any portion of body refer to an {application, combination, merging, issues, challenges} of {Internet of Things, IoT} and/or {blockchain network, blockchain}?
6. Security Assurances and IoT Threat Model
6.1. Definitions of Security Assurances
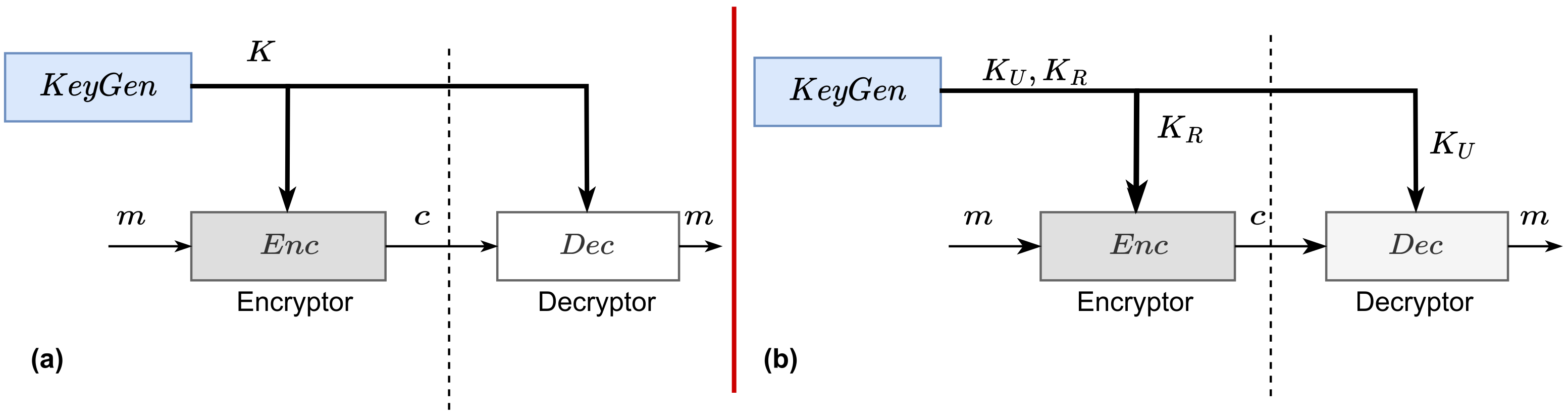
6.1.1. Confidentiality
6.1.2. Authentication and Authorization
6.1.3. Integrity
6.1.4. Availability
6.1.5. Physical Security
6.1.6. Anonymity
6.1.7. Trustworthiness
6.2. IoT Threat Model
6.2.1. Threat and Attacks on Confidentiality
6.2.2. Threat and Attacks on Availability
6.2.3. Threat and Attacks on Integrity
6.2.4. Threat and Attacks on Authentication and Authorization
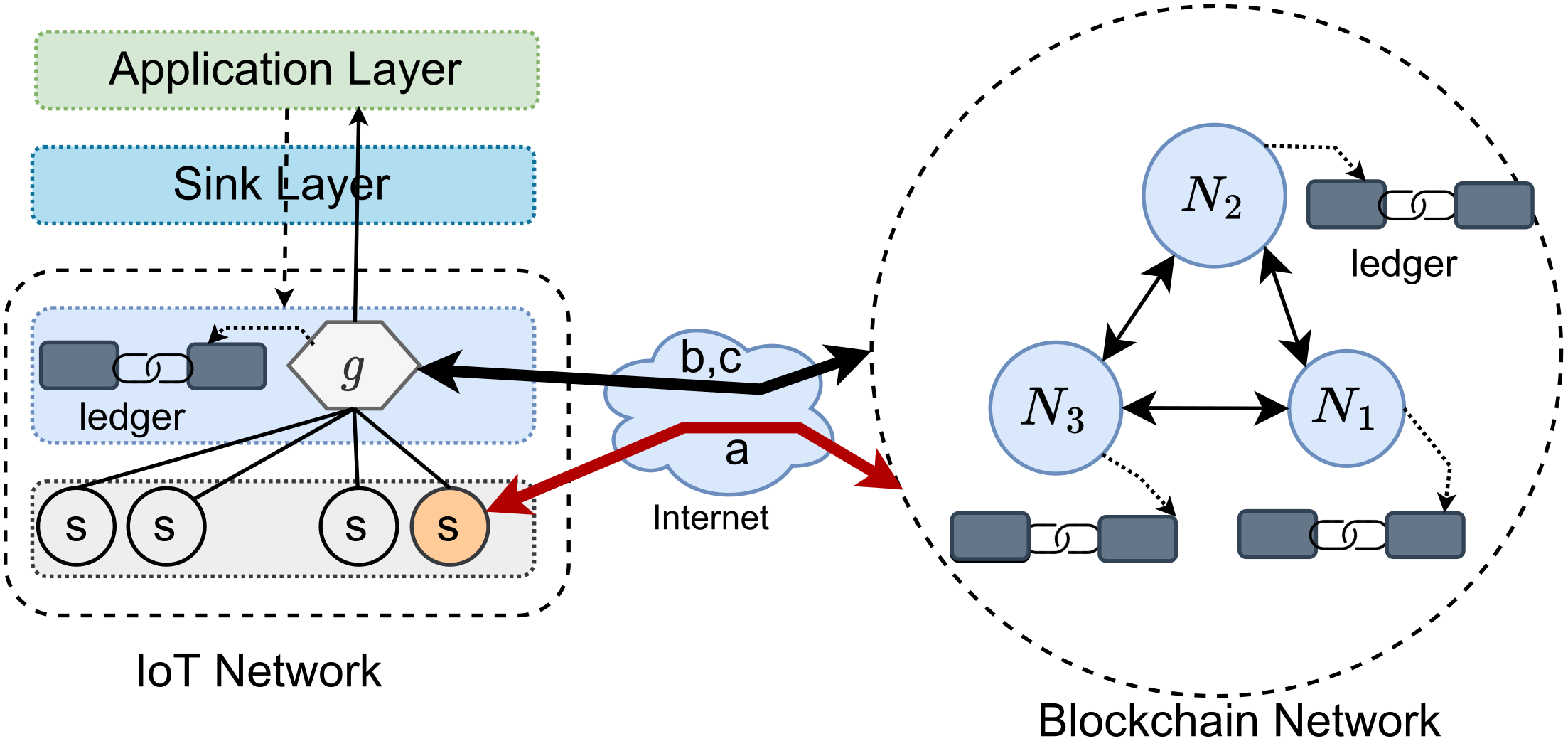
7. IoT and Blockchain Integration
- Sensor devices as Transaction Issuer (SaTi): In this integration model(see the interaction (a) between sensor node s and BCN in Figure 6), IoT devices such as sensors take part in issuing transactions to the external BCN. Such IoT devices should be designed to accommodate computational power and bandwidth requirements. However, the typical IoT devices do not have the storage capacity to store a complete blockchain. In many use cases, such as industrial IOTs, this model may be too costly and ineffective for sensors to communicate with an external BCN. In that case, edge devices such as IoT gateways may be employed to issue transactions on behalf of all the low-power, resource constraint IoT devices.
- Edge devices as Transaction Issuer (EaTi): In this integration model (see the interaction (b) between edge device g and BCN in Figure 6), specially designed IoT edge devices such as gateway routers may be actively issuing transactions to an external BCN, without actually storing a copy of the blockchain ledger. This integration model is efficient, given that it requires a limited number of edge devices for interacting with the BCN.
- Edge devices as Transaction Verifier (EaTv): This integration model extends the EaTi model, where specially designed IoT edge devices issue transactions to the BCN and maintain an entire blockchain ledger for active block validations. In many cases, edge devices could handle both issues and validate transactions being an active node for a BCN. However, unless business interests require it, an industry may not use edge devices for transaction validations, which are computationally intensive and require higher storage and bandwidth. In the figure, interaction (c) is part of this integration model.
- Hybrid: In a hybrid integration model, IoT and blockchain interact through edge devices and specially designed IoT sensor devices. It depends on the applications whose interactions go through edge and IoT devices. In the figure, interactions (a), (b), and (c) are part of the hybrid integration model. In other words, sensor devices issue transactions, and edge devices issue, and validate transactions for a BCN. Nonetheless, this model imposes redundancy in issuing transactions for a BCN, which is costly in terms of bandwidth.
7.1. Application Areas of IoT and BCN Integration
7.1.1. IoT Devices and IoT Applications’ Security Enforcement
- Trust Platform: As discussed in the previous section, a blockchain network is a platform that supports transaction and process verification and public audit of the data stored in the temper-detectable blockchain ledger. Thus, the blockchain network has the potential to be used as a trusted platform for several IoT-related applications. Dedeoglu et al. [54] presented a blockchain-based trust architecture for building end-to-end trust for various IoT-based applications. Tang et al. [55] proposed a decentralized trust framework called IoT Passport for cross-platform collaborations using blockchain to enforce trusted interactions between IoT devices across platforms.
- Authentication and Access Control: Access control is a mechanism of mapping computational resources with users with appropriate access, including reading, writing, and executing. Because the blockchain network guarantees the integrity of stored data, access control mechanisms for IoT devices and applications are built and encoded on the blockchain ledger. Ji et al. [56] used an identify-based data access control model, BDAC, to provide fine-grained data access control for IoT systems. Muzammal et al. [57] proposed an enhanced authentication and access control method for IoT devices to add features, such as decentralization, secured authentication, authorization, and scalability. Zhang et al. [58] proposed an attribute-based collaborative access control scheme on top of a blockchain for IoT devices. Recently, Pal et al. [59] proposed blockchain-based IoT access control mechanisms that are claimed to provide critical features, including resource management, access rights transfer, permission enforcement, attribute management, and scalability. Košťál et al. [60] proposed using the blockchain network to manage and monitor IoT devices. Previous works from [61,62,63] were heavily focused on using Blockchain for IoT access control management.
- Privacy and Integrity of IoT data: Privacy and integrity are the essential properties of the IoT ecosystem. Tan et al. [64] proposed Shamir’s threshold cryptography for protecting the privacy of the IoT data stored in the cloud. In this model, the end-users request decryption keys from the blockchain network to decrypt the encrypted data in the cloud. Negka et al. [65] proposed using hardware-derived functions known as physical unclonable functions (PUFs) to detect counterfeit IoT devices. Wu et al. [66] simulated a system of assuring and detecting IoT data integrity using a distributed blockchain system. Naresh et al. discussed a blockchain-based method to monitor the topographic integrity of an IoT network.
7.1.2. Industrial IoT Devices and Identity Management
7.1.3. Industrial IoT Data Management and Resource Sharing/Trading
8. Challenges of IoT, Blockchain and the Integration
8.1. Network and Communication Security
8.2. Scalability
8.3. Interoperability, Standardization, Regulation, and Governance
8.4. Deployment and Detection
8.5. Performance and Resource Constraints
8.6. Maintenance and Patching
9. Meeting the IoT-BCN Challenges: Tools, Techniques and Strategies
9.1. Physical Security of IoT Devices
9.2. Confidentiality through Encryption
9.3. Authentication
9.4. Anonymizing the IoT Data
9.5. Authorization
9.6. Availability
9.7. Trustworthiness
9.8. IoT Security Controls and Policies
- Implement IoT devices and firmware version inventory management: This control encourages network owners to create an effective inventory of authorized network and sensor devices. This inventory assists in establishing authorized network devices and detecting unauthorized devices.
- Implement IoT application services and version management: This control provides a mechanism to create an inventory of software or firmware packages used by IoT devices. Such inventory is valuable during firmware/software vulnerability fixing and patch management.
- Implement IoT network or device access control management: Access control mechanism is one of the crucial techniques to provide operational and other permissions over IoT devices. It also assists in monitoring IoT device access by different users. Proper authentication mechanisms should also be implemented to avoid leaking or reusing user credentials such as usernames and passwords.
- Implement IoT network and application isolation: It is crucial to establish a distinction between an IoT network and an application (or analysis) layer. While an IoT network is a network of devices contributing to harvesting sensor data, the application layer consists of services used by end users to support organization decisions. A stringent isolating boundary should be created to mitigate risks of vulnerabilities affecting each other.
- Implement IoT network and access Log management: This control encourages network owners to collect, alert, review and retain events logs that could assist in detecting, comprehending, and recovering from any attack on an IoT system.
- Data protection and recovery management: Critical asset produced by an IoT is the vast set of application-specific data. Implementing adequate data backup procedures is crucial to avoid data loss during an attack or a disaster. User access and data encryption should also be properly managed to prevent information leaks.
10. Discussion and Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| ABE | Attribute-Based Encryption |
| AES | Advanced Encryption Standards |
| BC | Blockchain |
| BCN | Blockchain Network |
| CIS | Center for Internet Security |
| CVSS | Common Vulnerability Scoring System |
| DES | Data Encryption Standard |
| DoS | Directory of open access journals |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| FDI | False Data Injection |
| IIRA | The Industrial Internet Reference Architecture |
| LTE-M | data |
| LoRa | Long Range |
| MAC | Mandatory Access Control |
| MIM | Man-in-the-Middle |
| NFC | Near Field Communication |
| OWL | Web Ontology Language |
| PASTA | Process for Attack Simulation and Threat Analysis |
| PoS | Proof of Stake |
| PoW | Proof of Work |
| RBAC | Role Based Access Control |
| RFID | Radio Frequency Identification |
| RSA | Rivest–Shamir–Adleman Algorithm |
| TCP | Transport Control Protocol |
| TLS/SSL | Transport Layer Securuirty/Socket Layer Security |
| TXN | Transactions (Plr. TXNs) |
| Temp. | Temperature |
| UAV | Unmanned Aerial Vehicle |
| WIMAX | Worldwide Interoperability for Microwave Access |
| WWW | World Wide Web |
| ZB | Zettabytes |
References
- Ainane, N.; Ouzzif, M.; Bouragba, K. Data security of smart cities. In Proceedings of the 3rd International Conference on Smart City Applications, Tetouan, Morocco, 10–11 October 2018. [Google Scholar] [CrossRef]
- YIN, Y.; Zeng, Y.; Chen, X.; Fan, Y. The internet of things in healthcare: An overview. J. Ind. Inf. Integr. 2016, 1, 3–13. [Google Scholar] [CrossRef]
- Arunkumar, N.; Pandimurugan, V.; Hema, M.S.; Azath, H.; Hariharasitaraman, S.; Thilagaraj, M.; Govindan, P. A Versatile and Ubiquitous IoT-Based Smart Metabolic and Immune Monitoring System. Comput. Intell. Neurosci. 2022, 2022, 9441357. [Google Scholar] [CrossRef] [PubMed]
- Ibrahim, J.M.; Karami, A.; Jafari, F. A secure smart home using Internet-of-Things. In Proceedings of the 9th International Conference on Information Management and Engineering, Barcelona, Spain, 9–11 October 2017; pp. 69–74. [Google Scholar] [CrossRef]
- Dineva, K.; Atanasova, T. Design of Salable IoT Architecture based on AWS for Smart Livestock. Animal 2021, 11, 2697. [Google Scholar] [CrossRef] [PubMed]
- Sudha, M.K.; Manorama, M.; Aditi, T. Smart Agricultural Decision Support Systems for Predicting Soil Nutrition Value Using IoT and Ridge Regression. Agris Online Pap. Econ. Inform. 2022, 14, 95–106. [Google Scholar] [CrossRef]
- Oliver, S.T.; González-Pérez, A.; Guijarro, J.H. An IoT proposal for monitoring vineyards called senviro for agriculture. In Proceedings of the 8th International Conference on the Internet of Things, IOT 2018, Santa Barbara, CA, USA, 15–18 October 2018. [Google Scholar] [CrossRef]
- Ahire, D.B.; Gond, D.V.J.; Ahire, N.L. IoT Based Real-Time Monitoring of Meteorological Data: A Review. In Proceedings of the 3rd International Conference on Contents, Computing & Communication (ICCCC-2022), Nashik, India, 26–27 February 2022; pp. 1–12. [Google Scholar] [CrossRef]
- Casola, V.; De Benedictis, A.; Rak, M.; Villano, U. Toward the automation of threat modeling and risk assessment in IoT systems. Internet Things 2019, 7, 100056. [Google Scholar] [CrossRef]
- Pennino, D.; Pizzonia, M.; Vitaletti, A.; Zecchini, M. Blockchain as IoT Economy Enabler: A Review of Architectural Aspects. J. Sens. Actuator Netw. 2022, 11, 20. [Google Scholar] [CrossRef]
- Huh, S.; Cho, S.; Kim, S. Managing IoT devices using blockchain platform. In Proceedings of the International Conference on Advanced Communication Technology, ICACT, PyeongChang, Republic of Korea, 19–22 February 2017; pp. 464–467. [Google Scholar] [CrossRef]
- Mehta, P.; Gupta, R.; Tanwar, S. Blockchain envisioned UAV networks: Challenges, solutions, and comparisons. Comput. Commun. 2020, 151, 518–538. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Technical Report. 2008. Available online: bitcoin.org (accessed on 19 September 2022).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32 2019. [Google Scholar]
- Bayılmış, C.; Ebleme, M.A.; Çavuşoğlu, Ü.; Küçük, K.; Sevin, A. A survey on communication protocols and performance evaluations for Internet of Things. Digit. Commun. Netw. 2022, 8, 1094–1104. [Google Scholar] [CrossRef]
- Lao, L.; Li, Z.; Hou, S.; Xiao, B.; Guo, S.; Yang, Y. A survey of IoT applications in blockchain systems: Architecture, consensus, and traffic modeling. ACM Comput. Surv. 2020, 53, 1–32. [Google Scholar] [CrossRef]
- Ray, P.P. A survey on Internet of Things architectures. J. King Saud Univ. Comput. Inf. Sci. 2018, 30, 291–319. [Google Scholar] [CrossRef]
- Lea, P. Internet of Things for Architects, 1st ed.; Packt Publishing: Birmingham, UK, 2018; pp. 1–676. [Google Scholar]
- Dahlberg, R.; Pulls, T.; Peeters, R. Efficient Sparse Merkle Trees Caching Strategies and Secure (Non-) Membership Proofs. Lect. Notes Comput. Sci. 2016, 10014 LNCS, 199–215. [Google Scholar] [CrossRef]
- Wang, G.; Shi, Z.; Nixon, M.; Han, S. ChainSplitter: Towards blockchain-based industrial IoT architecture for supporting hierarchical storage. In Proceedings of the 2019 2nd IEEE International Conference on Blockchain, Blockchain 2019, Atlanta, GA, USA, 14–17 July 2019; pp. 166–175. [Google Scholar] [CrossRef]
- McGrath, M.J.; Scanaill, C.N. Sensor Technologies—Healthcare, Wellness and Environmental Applications; Apress: Berkeley, CA, USA, 2013; pp. 1–302. [Google Scholar] [CrossRef]
- Gupta, M.; Abdelsalam, M.; Khorsandroo, S.; Mittal, S. Security and Privacy in Smart Farming: Challenges and Opportunities. IEEE Access 2020, 8, 34564–34584. [Google Scholar] [CrossRef]
- Sontowski, S.; Gupta, M.; Laya Chukkapalli, S.S.; Abdelsalam, M.; Mittal, S.; Joshi, A.; Sandhu, R. Cyber Attacks on Smart Farming Infrastructure. In Proceedings of the 2020 IEEE 6th International Conference on Collaboration and Internet Computing, CIC 2020, Virtual, 1–3 December 2020; Institute of Electrical and Electronics Engineers Inc.: Interlaken, Switzerland, 2020; pp. 135–143. [Google Scholar] [CrossRef]
- Mann, S. Historical account of the ‘WearComp’ and ‘WearCam’ inventions developed for applications in ‘personal imaging’. In Proceedings of the International Symposium on Wearable Computers, Digest of Papers, Cambridge, MA, USA, 13–14 October 1997; pp. 66–73. [Google Scholar] [CrossRef]
- Tariq, N.; Qamar, A.; Asim, M.; Khan, F.A. Blockchain and smart healthcare security: A survey. In Procedia Computer Science; Elsevier: Amsterdam, The Netherlands, 2020; Volume 175, pp. 615–620. [Google Scholar] [CrossRef]
- Chao, H.; Maheshwari, A.; Sudarsanan, V.; Tamaskar, S.; Delaurentis, D.A. UAV traffic information exchange network. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, GA, USA, 25–29 June 2018. [Google Scholar] [CrossRef]
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE internet Things J. 2017, 4, 642–646. [Google Scholar] [CrossRef]
- Peng, C.; Wu, C.; Gao, L.; Zhang, J.; Yau, K.L.A.; Ji, Y. Blockchain for Vehicular internet of Things: Recent Advances and Open Issues. Sensors 2020, 20, 5079. [Google Scholar] [CrossRef] [PubMed]
- Ramkumar, M.; Adhikari, N. Blockchain Based Redistricting with Public Participation. J. Inf. Secur. 2022, 13, 140–164. [Google Scholar] [CrossRef]
- Ali, M.S.; Vecchio, M.; Pincheira, M.; Dolui, K.; Antonelli, F.; Rehmani, M.H. Applications of Blockchains in the internet of Things: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2019, 21, 1676–1717. [Google Scholar] [CrossRef]
- Alotaibi, B. Utilizing Blockchain to Overcome Cyber Security Concerns in the internet of Things: A Review. IEEE Sens. J. 2019, 19, 10953–10971. [Google Scholar] [CrossRef]
- Xu, J. The Application of Blockchain Technology in Equity Incentive. E3S Web Conf. 2021, 235, 15–18. [Google Scholar] [CrossRef]
- Vora, G. Cryptocurrencies: Are Disruptive Financial Innovations Here? Mod. Econ. 2015, 06, 816–832. [Google Scholar] [CrossRef]
- Hou, H. The Application of Blockchain Technology in E-Government in China. In Proceedings of the 6th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017; Volume 235, pp. 1–4. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C. A systematic literature review of blockchain-based applications: Current status, classification and open issues. Telemat. Inform. 2019, 36, 55–81. [Google Scholar] [CrossRef]
- Saxena, S.; Shao, D.; Nikiforova, A.; Thapliyal, R. Invoking blockchain technology in e-government services: A cybernetic perspective. Digit. Policy Regul. Gov. 2022, 24, 246–258. [Google Scholar] [CrossRef]
- Kassen, M. Blockchain and e-government innovation: Automation of public information processes. Inf. Syst. 2022, 103, 101862. [Google Scholar] [CrossRef]
- Stallings, W. Cryptography and Network Security: Principles and Practice 7th Global Edition, 7th ed.; Pearson Education Limited: Harlow, UK, 2017. [Google Scholar]
- Tiedemann, P. The Human Right to Privacy. Philos. Found. Hum. Right 2020, 44, 197–214. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT Privacy and Security: Challenges and Solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Pass, R.; Shelat, A. A Course in Cryptography, 3rd ed.; Printed Online; 2010; pp. 1–192. Available online: https://bit.ly/3GZEiGN (accessed on 19 December 2022).
- Bruce, S. Applied Cryptography: Protocols, Algorithms, and Source Code in C, 2nd ed.; John Wiley & Sons, Inc: New York, NY, USA, 1996. [Google Scholar]
- Brown, A.; Bethel, G.; Koehler, S. Threats To Percision Agriculture. Technical Report. 2018. Available online: https://bit.ly/3XNsSwC (accessed on 20 October 2022).
- Samarati, P.; Sweeney, L. Protecting privacy when disclosing information: K-anonymity and its enforcement through generalization and suppression. In Proceedings of the IEEE Symposium on Research in Security and Privacy (S&P), Oakland, CA, USA, 3–6 May 1998. [Google Scholar]
- IEEE Std 2144.1-2020; IEEE Standard for Framework of Blockchain-based Internet of Things (IoT) Data Management. Institute of Electrical and Electronics Engineers Inc.: New York, NY, USA, 2021; pp. 1–20. [CrossRef]
- Bradbury, M.; Jhumka, A.; Watson, T.; Flores, D.; Burton, J.; Butler, M. Threat-modeling-guided Trust-based Task Offloading for Resource-constrained internet of Things. ACM Trans. Sens. Netw. 2022, 18, 1–41. [Google Scholar] [CrossRef]
- Hilt, S.; Kropotov, V.; Mercês, F.; Rosario, M.; Sancho, D. The Internet of Things in the Cybercrime Underground. Available online: https://bit.ly/2lZRnKv (accessed on 20 December 2022).
- Chukkapalli, S.S.L.; Piplai, A.; Mittal, S.; Gupta, M.; Joshi, A. A Smart-Farming Ontology for Attribute Based Access Control. In Proceedings of the 2020 IEEE 6th Intl Conference on Big Data Security on Cloud, BigDataSecurity 2020, 2020 IEEE Intl Conference on High Performance and Smart Computing, HPSC 2020 and 2020 IEEE Intl Conference on Intelligent Data and Security, IDS 2020, Baltimore, MD, USA, 25–27 May 2020; pp. 29–34. [Google Scholar] [CrossRef]
- Line, M.B.; Zand, A.; Stringhini, G.; Kemmerer, R. Targeted attacks against industrial control systems: Is the power industry prepared? In Proceedings of the ACM Conference on Computer and Communications Security. Association for Computing Machinery, Scottsdale, AZ, USA, 3–7 November 2014; Volume 2014, pp. 13–22. [Google Scholar] [CrossRef]
- Nguyen, A.; Yosinski, J.; Clune, J. Deep Neural Networks are Easily Fooled: High Confidence Predictions for Unrecognizable Images. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR), Boston, MA, USA, 7–12 June 2015. [Google Scholar]
- Tyagi, T. Botnet of Things: Menace to Internet of Things. In Proceedings of the Third International Conference on Computing: Communication, Network and Security (IC3NS-2018), Sikar, Rajasthan, India, 25–27 October 2018; pp. 61–65. [Google Scholar]
- Wüst, K.; Gervais, A. Do you need a Blockchain? In Proceedings of the 2018 Crypto Valley Conference on Blockchain Technology (CVCBT), Zug, Switzerland, 20–22 June 2018; pp. 45–54. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Dedeoglu, V.; Jurdak, R.; Putra, G.D.; Dorri, A.; Kanhere, S.S. A Trust Architecture for Blockchain in IoT. In Proceedings of the 16th EAI International Conference on Mobile and Ubiquitous Systems: Computing, Networking and Services, Houston, TX, USA, 2–14 November 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 190–199. [Google Scholar] [CrossRef]
- Tang, B.; Kang, H.; Fan, J.; Li, Q.; Sandhu, R. IoT Passport: A Blockchain-Based Trust Framework for Collaborative internet-of-Things. In Proceedings of the 24th ACM Symposium on Access Control Models and Technologies, Toronto, ON, Canada, 3–6 June 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 83–92. [Google Scholar] [CrossRef]
- Ji, Y.; Xiao, X.; Wu, F.; Chen, F.; Liu, S. BIDAC: Blockchain-Enabled Identity-Based Data Access Control in IoT. In Proceedings of the IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology, Melbourne, Australia, 14–17 December 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 400–405. [Google Scholar] [CrossRef]
- Muzammal, S.M.; Murugesan, R.K. Enhanced Authentication and Access Control in internet of Things: A Potential Blockchain-Based Method. Int. J. Grid Util. Comput. 2021, 12, 469–485. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, B.; Liu, B.; Wu, J.; Wang, Y.; Yang, X. An Attribute-Based Collaborative Access Control Scheme Using Blockchain for IoT Devices. Electronics 2020, 9, 285. [Google Scholar] [CrossRef]
- Pal, S.; Dorri, A.; Jurdak, R. Blockchain for IoT access control: Recent trends and future research directions. J. Netw. Comput. Appl. 2022, 203, 103371. [Google Scholar] [CrossRef]
- Košťál, K.; Helebrandt, P.; Belluš, M.; Ries, M.; Kotuliak, I. Management and Monitoring of IoT Devices Using Blockchain. Sensors 2019, 19, 856. [Google Scholar] [CrossRef]
- Banerjee, S.; Bera, B.; Das, A.K.; Chattopadhyay, S.; Khan, M.K.; Rodrigues, J.J. Private blockchain-envisioned multi-authority CP-ABE-based user access control scheme in IIoT. Comput. Commun. 2021, 169, 99–113. [Google Scholar] [CrossRef]
- Iftekhar, A.; Cui, X.; Tao, Q.; Zheng, C. Hyperledger Fabric Access Control System for internet of Things Layer in Blockchain-Based Applications. Entropy 2021, 23, 1054. [Google Scholar] [CrossRef] [PubMed]
- Tan, L.; Shi, N.; Yu, K.; Aloqaily, M.; Jararweh, Y. A Blockchain-Empowered Access Control Framework for Smart Devices in Green internet of Things. ACM Trans. Internet Technol. 2021, 21, 80. [Google Scholar] [CrossRef]
- Tan, L.; Yu, K.; Yang, C.; Bashir, A.K. A Blockchain-Based Shamir’s Threshold Cryptography for Data Protection in Industrial internet of Things of Smart City. In Proceedings of the 1st Workshop on Artificial Intelligence and Blockchain Technologies for Smart Cities with 6G, New Orleans, LA, USA, 25–29 October 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 13–18. [Google Scholar] [CrossRef]
- Negka, L.; Gketsios, G.; Anagnostopoulos, N.A.; Spathoulas, G.; Kakarountas, A.; Katzenbeisser, S. Employing Blockchain and Physical Unclonable Functions for Counterfeit IoT Devices Detection. In Proceedings of the International Conference on Omni-Layer Intelligent Systems, Crete, Greece, 5–7 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 172–178. [Google Scholar] [CrossRef]
- WU, X.; Kong, F.; Shi, J.; Bao, L.; Gao, F.; Li, J. A Blockchain internet of Things Data Integrity Detection Model. In Proceedings of the International Conference on Advanced Information Science and System, Singapore, 15–17 November 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Nuss, M.; Puchta, A.; Kunz, M. Towards Blockchain-Based Identity and Access Management for internet of Things in Enterprises. In Trust, Privacy and Security in Digital Business; Furnell, S., Mouratidis, H., Pernul, G., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 167–181. [Google Scholar]
- Vallois, V.; Mehaoua, A.; Amziani, M. Blockchain-based Identity and Access Management in Industrial IoT Systems. In Proceedings of the 2021 IFIP/IEEE International Symposium on Integrated Network Management (IM), Bordeaux, France, 18–20 May 2021; pp. 623–627. [Google Scholar]
- Lee, J.H. BIDaaS: Blockchain Based ID As a Service. IEEE Access 2018, 6, 2274–2278. [Google Scholar] [CrossRef]
- Sigwart, M.; Borkowski, M.; Peise, M.; Schulte, S.; Tai, S. Blockchain-Based Data Provenance for the internet of Things. In Proceedings of the 9th International Conference on the Internet of Things, Bilbao, Spain, 22–25 October 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- El Kafhali, S.; Chahir, C.; Hanini, M.; Salah, K. Architecture to Manage internet of Things Data Using Blockchain and Fog Computing. In Proceedings of the 4th International Conference on Big Data and Internet of Things, Tangier-Tetuan, Morocco, 23–24 October 2019; Association for Computing Machinery: New York, NY, USA, 2019. [Google Scholar] [CrossRef]
- Fan, Q.; Chen, J.; Deborah, L.J.; Luo, M. A secure and efficient authentication and data sharing scheme for internet of Things based on blockchain. J. Syst. Archit. 2021, 117, 102112. [Google Scholar] [CrossRef]
- Chi, J.; Li, Y.; Huang, J.; Liu, J.; Jin, Y.; Chen, C.; Qiu, T. A secure and efficient data sharing scheme based on blockchain in industrial internet of Things. J. Netw. Comput. Appl. 2020, 167, 102710. [Google Scholar] [CrossRef]
- Mohammed, S.; Fiaidhi, J.; Ramos, C.; Kim, T.H.; Fang, W.C.; Abdelzaher, T. Blockchain in ECommerce: A Special Issue of the ACM Transactions on internet of ThingsBlockchain in ECommerce: A Special Issue of the ACM Transactions on internet of Things. ACM Trans. Internet Technol. 2021, 21, 11–55. [Google Scholar] [CrossRef]
- Jain, R.; Dogra, A. Solar Energy Distribution Using Blockchain and IoT Integration. In Proceedings of the 2019 International Electronics Communication Conference, Okinawa, Japan, 7–9 July 2021; Association for Computing Machinery: New York, NY, USA, 2019; pp. 118–123. [Google Scholar] [CrossRef]
- Khorasany, M.; Dorri, A.; Razzaghi, R.; Jurdak, R. Lightweight blockchain framework for location-aware peer-to-peer energy trading. Int. J. Electr. Power Energy Syst. 2021, 127, 106610. [Google Scholar] [CrossRef]
- Attaran, M. Blockchain technology in healthcare: Challenges and opportunities. Int. J. Healthc. Manag. 2022, 15, 70–83. [Google Scholar] [CrossRef]
- Bataineh, M.R.; Mardini, W.; Khamayseh, Y.M.; Yassein, M.M.B. Novel and Secure Blockchain Framework for Health Applications in IoT. IEEE Access 2022, 10, 14914–14926. [Google Scholar] [CrossRef]
- Wang, L. The Challenge and Prospect of Scalability of Blockchain Technology. In Proceedings of the 2021 5th International Conference on Computer Science and Artificial Intelligence, Beijing, China, 4–6 December 2021; pp. 296–301. [Google Scholar] [CrossRef]
- Gazis, V. A Survey of Standards for Machine-to-Machine and the internet of Things. IEEE Commun. Surv. Tutor. 2017, 19, 482–511. [Google Scholar] [CrossRef]
- Bertino, E.; Sandhu, R.; Thuraisingham, B.; Ray, I.; Li, W.; Gupta, M.; Mittal, S. Security and Privacy for Emerging IoT and CPS Domains. In Proceedings of the Association for Computing Machinery (ACM), Baltimore, MD, USA, 24–27 April 2022; pp. 336–337. [Google Scholar] [CrossRef]
- Maximizing Security in Zigbee Networks. Available online: https://bit.ly/3GVr4ed (accessed on 19 December 2022).
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the ACM Conference on Computer and Communications Security, Taipei, Taiwan, 21–24 March 2006; pp. 89–98. [Google Scholar] [CrossRef]
- Goyal, G.; Lie, P.; Sural, S. Securing Smart Home IoT Systems with Attribute-Based Access Control. In Proceedings of the 2022 ACM Workshop on Secure and Trustworthy Cyber-Physical Systems, Baltimore, DC, USA, 27 April 2022; ACM: Baltimore, DC, USA, 2022; pp. 37–46. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and Secure Sharing of Personal Health Records in Cloud Computing Using Attribute-Based Encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef]
- Yan, Q.; Lou, J.; Vuran, M.C.; Irmak, S. Scalable Privacy-preserving Geo-distance Evaluation for Precision Agriculture IoT Systems. ACM Trans. Sens. Netw. 2021, 17, 1–30. [Google Scholar] [CrossRef]
- Bertino, E.; Carminati, B.; Ferrari, E.; Thuraisingham, B.; Gupta, A. Selective and Authentic Third-Party Distribution of XML Documents. IEEE Trans. Knowl. Data Eng. 2004, 16, 1263–1278. [Google Scholar] [CrossRef]
- Al-Rubaie, M.; Chang, J.M. Privacy-Preserving Machine Learning: Threats and Solutions. IEEE Secur. Priv. 2019, 17, 49–58. [Google Scholar] [CrossRef]
- Yang, Q.; Liu, Y.; Chen, T.; Tong, Y. Federated Machine Learning: Concept and Applications. ACM Trans. Intell. Syst. Technol. 2019, 10, 1–19. [Google Scholar] [CrossRef]
- Stirapongsasuti, S. Decision Making Support for Privacy Data Upload in Smart Home. In Proceedings of the Adjunct: Adjunct Proceedings of the 2019 ACM International Joint Conference on Pervasive and Ubiquitous Computing and Proceedings of the 2019 ACM International Symposium on Wearable Computers, London, UK, 9–13 September 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 214–217. [Google Scholar] [CrossRef]
- Sandhu, R.S.; Samarati, P. Access Control: Principles and Practice. IEEE Commun. Mag. 1994, 32, 40–48. [Google Scholar] [CrossRef]
- Monshizadeh, M.; Khatri, V.; Kantola, R. Detection as a service: An SDN application. In Proceedings of the International Conference on Advanced Communication Technology, ICACT, Pyeongchang, Republic of Korea, 19–22 February 2017; pp. 285–290. [Google Scholar] [CrossRef]
- Ullah, Z.; Al-Turjman, F.; Mostarda, L.; Gagliardi, R. Applications of Artificial Intelligence and Machine learning in smart cities. Comput. Commun. 2020, 154, 313–323. [Google Scholar] [CrossRef]
- Chukkapalli, S.S.L.; Mittal, S.; Gupta, M.; Abdelsalam, M.; Joshi, A.; Sandhu5, R.; Joshi, K. Ontologies and artificial intelligence systems for the cooperative smart farming ecosystem. IEEE Access 2020, 8, 164045–164064. [Google Scholar] [CrossRef]
- CIS Controls Version 8. Available online: https://bit.ly/3kDgHnK (accessed on 19 December 2022).
- Iqbal, W.; Abbas, H.; Daneshmand, M.; Rauf, B.; Bangash, Y.A. An In-Depth Analysis of IoT Security Requirements, Challenges, and Their Countermeasures via Software-Defined Security. IEEE Internet Things J. 2020, 7, 10250–10276. [Google Scholar] [CrossRef]
| Capability | Public BCN | Private BCN | Consortium BCN |
|---|---|---|---|
| Decentralization 1 | Yes | Yes | Yes |
| Distributed Computing | No | No | No |
| TXNs 2 Verification | Performed by all (or majority) of nodes | Random or selected node | Random or selected node |
| Network Participation | Open to any node | Approved by network manager | Approved by network manager |
| TXNs (Data) Privacy | Not protected | Not-protected | Not-protected |
| TXNs Traceability | Pseudo-anonymous | Traceable or Pseudo-anonymous | Traceable or Pseudo-anonymous |
| Data Immutability | Highly immutable | Limited | Limited |
| Fault Tolerance | Yes | Limited | Limited |
| Trustworthy Execution | Yes | No | No |
| Consensus Mechanism | PoW, PoS, etc. | PoW, PoS, etc. | PoW, PoS, etc. |
| Smart Contract | Optional (mostly supported) | Optional | Optional |
| Cost | TXNs execution fee | Free to the internal TXNs | Free to the internal TXNs |
| S.N. | Research Questions | Objectives |
|---|---|---|
| RQ.1 | What are the security assurances of an IoT? | To explore the chief security assurances pertinent to IoT systems |
| RQ.2 | What is the threat model of IoT? | To explore different events that pose threats to the security requirements. |
| RQ.3 | What are the application scenarios of an IoT in isolation to new technology such as blockchain technology? | To explore applications of IoT without considering blockchain technologies. |
| RQ.4 | What are the advantages and disadvantages that come with the integration of IoT with blockchain technology? | To discuss various integration models and their merits. |
| RQ.5 | What are the challenges for IoT and blockchain integration? | To discuss technical and non-technical problems and challenges that need to be overcome for the successful integration of IoT and blockchain technology. |
| Terminologies 1 |
|---|
| “{Internet of Things, IoT} for Blockchain {Networks, technology }” |
| “Integration of {Internet of Things, IoT} and Blockchain {Networks, technology}” |
| “Challenges of {Internet of Things, IoT} and Blockchain {Networks, technology}” |
| “Issues in {Internet of Things, IoT} and Blockchain {Networks, technology} integration” |
| “Applications of Challenges of {Internet of Things, IoT} and Blockchain {Networks, technology}” |
| “Merging Challenges of {Internet of Things, IoT} and Blockchain {Networks, technology}” |
| “Combining Challenges of {Internet of Things, IoT} and Blockchain {Networks, technology}” |
| “Combination of Challenges of {Internet of Things, IoT} and Blockchain {Networks, technology}” |
| “{Using, Use of} Blockchain network for {health, hospitals, farm, farming, poultry, fishery}” |
| “{Using, Use of} Blockchain network for {agriculture, forestry, smart city, smart driving}” |
| “{Using, Use of} Blockchain network for {parking, war, smart grid, battle}” |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Adhikari, N.; Ramkumar, M. IoT and Blockchain Integration: Applications, Opportunities, and Challenges. Network 2023, 3, 115-141. https://doi.org/10.3390/network3010006
Adhikari N, Ramkumar M. IoT and Blockchain Integration: Applications, Opportunities, and Challenges. Network. 2023; 3(1):115-141. https://doi.org/10.3390/network3010006
Chicago/Turabian StyleAdhikari, Naresh, and Mahalingam Ramkumar. 2023. "IoT and Blockchain Integration: Applications, Opportunities, and Challenges" Network 3, no. 1: 115-141. https://doi.org/10.3390/network3010006
APA StyleAdhikari, N., & Ramkumar, M. (2023). IoT and Blockchain Integration: Applications, Opportunities, and Challenges. Network, 3(1), 115-141. https://doi.org/10.3390/network3010006







