Transparency with Blockchain and Physical Tracking Technologies: Enabling Traceability in Raw Material Supply Chains †
Abstract
:1. Introduction
- How can blockchain technology, combined with physical tracking technologies, support supply chain transparency?
- How can physical tracking technologies be categorized and structured in view of their applications and limitations, in order to create a simple taxonomy that can be relevant for tracking raw materials along supply chains?
2. Methodology
3. Blockchain and Tracking Technologies in the Raw Material Sector
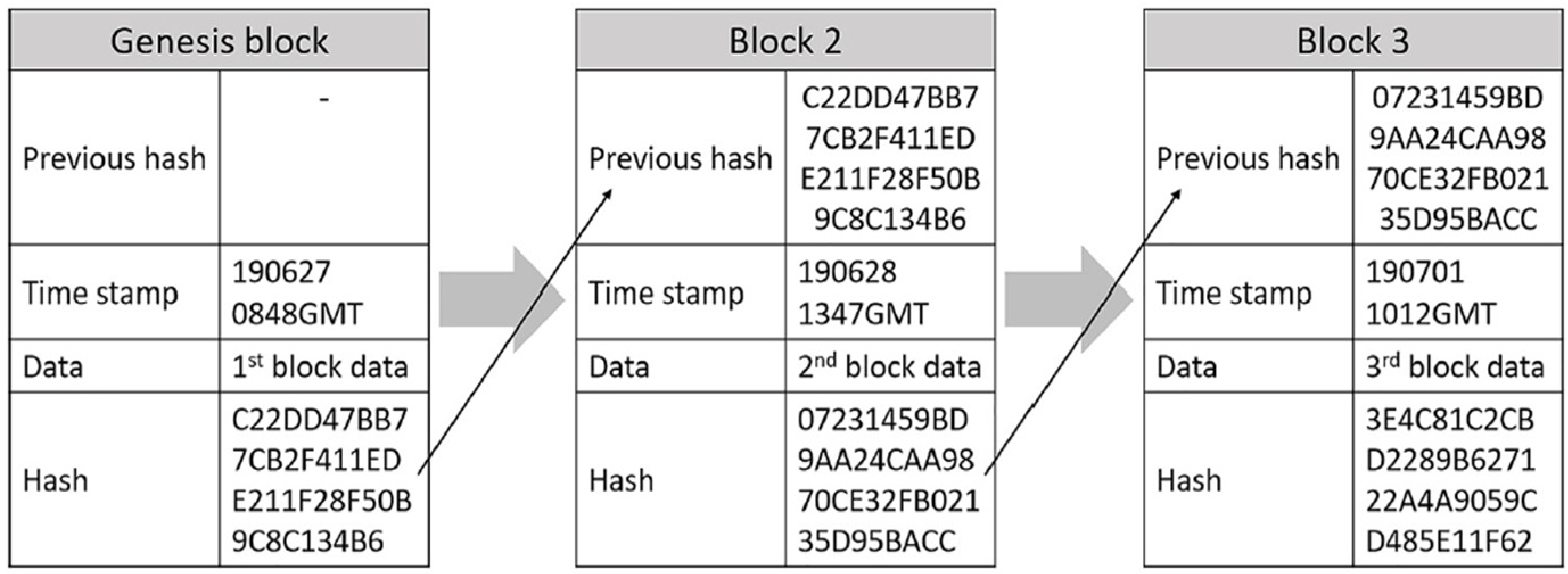
3.1. Blockchain Architectures
- The consensus protocol: for example, authorization and procedures to register and seal blocks are based on proof-of-work (PoW), proof-of-authority (PoA), proof-of-stake (PoS), proof-of-elapsed-time (PoET), or other variations or types of protocols [21]. These differing consensus protocols also determine the amount of energy a blockchain will consume in order to validate transactions.
- Node control: the governing structure to run nodes in a blockchain. For example, anyone can join to run a node in a public blockchain without further authentication, whereas in a private blockchain, every node is authenticated and its identity is known to the other nodes.
- Access control: for example, anyone may initiate or read transactions in a permissionless blockchain, whereas limitations may apply in a permissioned blockchain.
- Smart contract execution: depending on the specifications and rules of the blockchain environment to initiate automated execution procedures referred to as “smart contracts”, users may be allowed to customize transaction logics to suit their applications.
- Level of complexity [19]: Depending on the design of the consensus mechanism and other components of the blockchain environment, this can generate greater complexity compared to usual database architectures.
- Level of immutability: Depending on if and how the consensus mechanism and the further setup of the architecture restricts a change of data, the limitations to delete or modify data can be an issue with regard to legal requirements stipulated by applicable laws and regulations or by contracts. Also, it may not meet the individual user requirements or expectations [22,23].
- Level of transparency: Depending on the architecture, and in particular, in combination with the level of immutability, a high level of transparency and a limited flexibility on that level can again be an issue with regard to legal requirements stipulated by applicable laws and regulations or by contracts. Also, this missing flexibility may not meet the individual user requirements or expectations.
- Level of throughput, latency and scalability [19]: The design and the complexity of the blockchain architecture, and particularly of the consensus mechanism, can result in limitations in throughput, latency and scalability of the blockchain environment. In the context of tracking technologies, such limitations need to be considered in detail and can be a key impediment. For example, due to its latency and limited throughput, a blockchain architecture may allow others to immutably store recordings of live events, but it is not capable of displaying live events itself.
3.2. Minespider’s Blockchain
3.3. Considerations on the Value of the Data in a Blockchain Environment
4. Suggested Taxonomy: Tracking Technologies to Effectively Capture and Input Key Data on the Blockchain
- Robustness:Robustness usually needs to be considered in the context of the processing of raw materials. During their lifetime, many materials are exposed to high temperatures, pressures or other influences. For example, ores and other metals often are heated, smelted, pressed during processing. This brings up the question if the tracker in question can stand the respective transformations.
- Range:Range usually needs to be considered in the context of the implementation of the IoT environment, both in terms of the inputs the tracker can capture, as well as the access to the data it produces. For example, in some areas of operation, there may be no wired direct access to a network on which to transmit or receive data.
- Energy Requirements:Energy requirements usually need to be considered with the accessibility and lifetime of the tracker. Often the energy requirements go with the range of the tracker. Certain use cases may require flexibility, or operate in areas where access to a wired grid is not available, for example in deserts or underwater.
- Data Related Capabilities and Limitations:These usually need to be considered in terms of the kind and volume of data input and output the tracker can manage. For example, trackers like video cameras may generate large data volumes that need to be transmitted and processed.
- Other aspects for consideration such as costs and complexity to implement, legal requirements, and so forth.
5. Discussion and Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Tapscott, D. Supply Chain Revolution: How Blockchain Is Transforming the Global Flow of Assets; Barlow Book Publishing, Business & Economics: Toronto, ON, Canada, 2020; 295p. [Google Scholar]
- Rossi, M.; Mueller-Bloch, C.; Thatcher, J.B.; Beck, R. Blockchain research in information systems: Current trends and an inclusive future research agenda. J. Assoc. Inf. Syst. 2019, 20, 1388–1403. [Google Scholar] [CrossRef] [Green Version]
- Velandia, D.M.S.; Kaur, N.; Whittow, W.G.; Conway, P.P.; West, A.A. Towards industrial internet of things: Crankshaft monitoring, traceability and tracking using RFID. Robot. Comput. Integr. Manuf. 2016, 41, 66–77. [Google Scholar] [CrossRef] [Green Version]
- Dorsenmaine, B.; Kheir, N.; Wary, J.-P. Internet of Things: A Definition & Taxonomy, Conference Paper. In Proceedings of the 9th International Conference on Next Generation Mobile Applications, Services and Technologies, Cambridge, UK, 9–11 September 2015; pp. 72–77. [Google Scholar] [CrossRef]
- European Commission, Communication from the Commission to the European Parliament, the European Council, the Council, the European Economic and Social Committee and the Committee of the Regions, The European Green Deal, Register of the Commission, COM (2019) 640 Final. Available online: https://ec.europa.eu/transparency/documents-register/detail?ref=COM(2019)640&lang=en (accessed on 23 July 2021). Also See the European Green Deal Website. Available online: https://ec.europa.eu/info/strategy/priorities-2019-2024/european-green-deal_en (accessed on 23 July 2021).
- European Commission, Communication from the Commission to the European Parliament, the European Council, the Council, the European Economic and Social Committee and the Committee of the Regions, a New Circular Economy Action Plan for a Cleaner and More Competitive, COM/2020/98 Final. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?qid=1583933814386&uri=COM:2020:98:FIN (accessed on 23 July 2021). Also See the Website for the Circular Economy Action Plan, for a Cleaner and More Competitive Europe. Available online: https://ec.europa.eu/environment/strategy/circular-economy-action-plan_en (accessed on 23 July 2021).
- European Commission, Proposal for a Regulation of the European Parliament and of the Council Concerning Batteries and Waste Batteries, Repealing Directive 2006/66/EC and Amending Regulation (EU) No. 2019/1020, COM(2020) 798 Final, Recital 93. p. 41. Available online: https://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX%3A52020PC0798 (accessed on 23 July 2021).
- SAVANT. Available online: https://earthi.space/savant/ (accessed on 23 July 2021).
- Minespider, A.G. Communicate Responsibility with Product Passports. Secured on the Blockchain. Available online: https://www.minespider.com (accessed on 23 July 2021). Minespider’s projects have received funding from the European Union’s Horizon 2020 research and innovation programme under grant agreements No. 946437 and 957110 as well as from the European Institute of Innovation and Technology (EIT), a body of the European Union, under the Horizon 2020, under project agreement No. 19458-CLC-C-2020-8.
- Creswell, J.W.; Creswell, J.D. Mixed methods research: Developments, debates, and dilemmas. In Research in Organizations: Foundations and Methods of Inquiry; Publication in the Berrett-Koehler Organizational Performance Series Richard A. Swanson & Barbara L. Swanson, Series Editors; Berrett-Koehler Publishers: San Francisco, CA, USA, 2005; pp. 315–326. [Google Scholar]
- Tariq, U.; Ibrahim, A.; Ahmad, T.; Bouteraa, Y.; Elmogy, A. Blockchain in internet-of-things: A necessity framework for security, reliability, transparency, immutability and liability. IET Commun. 2019, 13, 3187–3192. [Google Scholar] [CrossRef]
- Rogerson, M.; Parry, G.C. Blockchain: Case studies in food supply chain visibility. Supply Chain Manag. Int. J. 2020, 25, 601–614. [Google Scholar] [CrossRef]
- Busse, C.; Schleper, M.C.; Weilenmann, J.; Wagner, S.M. Extending the supply chain visibility boundary: Utilizing stakeholders for identifying supply chain sustainability risks. Int. J. Phys. Distrib. Logist. Manag. 2017, 47, 18–40. [Google Scholar] [CrossRef]
- Treiblmaier, H. The impact of the blockchain on the supply chain: A theory-based research framework and a call for action. Supply Chain Manag. Int. J. 2018, 23, 545–559. [Google Scholar] [CrossRef] [Green Version]
- Cole, R.; Stevenson, M.; Aitken, J. Blockchain technology: Implications for operations and supply chain management. Supply Chain Manag. Int. J. 2019, 24, 469–483. [Google Scholar] [CrossRef]
- Saberi, S.; Kouhizadeh, M.; Sarkis, J.; Shen, L. Blockchain technology and its relationships to sustainable supply chain management. Int. J. Prod. Res. 2019, 57, 2117–2135. [Google Scholar] [CrossRef] [Green Version]
- Hilson, G.; Maconachie, R. Entrepreneurship and innovation in Africa’s artisanal and small-scale mining sector: Developments and trajectories. J. Rural. Stud. 2020, 78, 149–162. [Google Scholar] [CrossRef]
- Belotti, M.; Božić, N.; Pujolle, G.; Secci, S. A vademecum on blockchain technologies: When, which, and how. IEEE Commun. Surv. Tutor. 2019, 21, 3796–3838. [Google Scholar] [CrossRef] [Green Version]
- Dinh, T.T.A.; Liu, R.; Zhang, M.; Chen, G.; Ooi, B.C.; Wang, J. Untangling Blockchain: A Data Processing View of Blockchain Systems. IEEE Trans. Knowl. Data Eng. 2018, 30, 1366–1385. [Google Scholar] [CrossRef] [Green Version]
- Crain, T.; Gramoli, V.; Larrea, M.; Raynal, M. Blockchain consensus. In Proceedings of the ALGOTEL 2017-19èmes Rencontres Francophones sur les Aspects Algorithmiques des Télécommunications, Quiberon, France, 30 May–2 June 2017. [Google Scholar]
- Further Consensus Protocols Have Been Summarized by Saini, V., ConsensusPedia: An Encyclopedia of 30+ Consensus Algorithms. Available online: https://hackernoon.com/consensuspedia-an-encyclopedia-of-29-consensus-algorithms-e9c4b4b7d08f (accessed on 23 July 2021).
- Kunde, E.; Kaulartz, M.; Naceur, M.R.B.; Liban, S.; Kunz, M.; Skwarek, V.; Adam, K.; Weiß, R.; Liesenjohann, M. Blockchain und Datenschutz, Bitkom Faktenpapier. 2017, pp. 1–39. Available online: https://www.bitkom.org/sites/default/files/file/import/180502-Faktenpapier-Blockchain-und-Datenschutz.pdf (accessed on 23 July 2021).
- Rasinki, A. Blockchain-Technologie: Analyse Ausgewählter Anwendungsfälle und Bewertung Rechtlicher Aspekte. Schriftenreihe Analysen und Berichte zum Wirtschafts- und Steuerrecht. Master’s Thesis, Universität Ulm, Ulm, Germany, 2017; pp. 1–160. [Google Scholar]
- Go Ethererum. Available online: https://geth.ethereum.org (accessed on 23 July 2021).
- Nazir, S.; Fairhurst, G.; Verdicchio, F. WiSE—A satellite-based system for remote monitoring. Int. J. Satell. Commun. Monit. 2017, 35, 201–214. [Google Scholar] [CrossRef] [Green Version]
- Chang, P.Y.; Hwang, M.S.; Yang, C.C. A blockchain-based traceable certification system. In Proceedings of the International Conference on Security with Intelligent Computing and Big-data Services, Hubei, China, 5–6 August 2017; pp. 363–369. [Google Scholar] [CrossRef]
- Knapp, A.C. Karle Fellowship Final Report: Development of a Chemical Blockchain with Biased Detection of Matched Taggants; Naval Research Lab: Washington, DC, USA, 2020; Available online: https://apps.dtic.mil/sti/pdfs/AD1111566.pdf (accessed on 23 July 2021).
- Duong, B.; Liu, H.; Li, C.; Deng, W.; Ma, L.; Ming, S. Printed Multilayer Microtaggants with Phase Change Nanoparticles for Enhanced Labeling Security. Appl. Mater. Interfaces 2014, 6, 8909–8912. [Google Scholar] [CrossRef] [PubMed]
- Pujolle, G. Les Réseaux: Edition 2018–2020, L’ère des Réseaux Cloud et de la 5G Editions; Eyrolles: Paris, France, 2018. [Google Scholar]
- Sakai, H.; Castañeda, V.A. RFID Tracking Implementation for Supplier Chain Management at Toyota USA: Proposal of Development of Advanced TPS for Global Production Strategy, Scholink. Sustain. Environ. 2021, 6, 15–26. [Google Scholar] [CrossRef]
- Pour, F.S.A.; Gheorghe, A. A Sand Resource Governance Framework That Employs Satellite Imagery and Blockchain Technology. In Space Infrastructures: From Risk to Resilience Governance; NATO Science for Peace and Security Series, D: Information and Communication Security; IOS Press: Amsterdam, The Netherlands, 2020; Volume 57, pp. 215–222. [Google Scholar] [CrossRef]
- Moran, D.; Giljum, S.; Kanemoto, K.; Goda, J. From Satellite to Supply Chain: New Approaches Connect Earth Observation to Economic Decisions. One Earth Comment. 2020, 3, 5–8. [Google Scholar] [CrossRef]
- Russel, S.; Norvig, P. Artificial Intelligence: A Modern Approach, 4th ed.; Pearson: London, UK, 2020. [Google Scholar]
| Typical Use Cases | Video monitoring is a very common way to track activities on properties or in facilities. In the mining industry, it can be used to track movements of loads and machinery, as well as other operations and their environmental impacts. It can be used in open pits and other large environments on the ground, but also in underwater operations. It is typically used to monitor the exploitation and delivery of large volumes like bulk material. It is used in fixed installations as well as in combination with movable technology, such as drones, planes or satellites (see also Table 5 below). Video monitoring can also be combined with an automated evaluation of the image material to trigger further events [8,24]. For example, in ports the incoming deliveries of containers can be tracked per video monitoring while image and text capture software can identify container-related data. |
| Robustness | Video technology can be quite robust and used even in harsh environments. Although, like most technical equipment, if there is no protective encapsulation, there can be limitations to withstand excessive temperatures, dust, humidity, vibrations or other impacts. |
| Range | Video technology can be used to monitor objects in and from various ranges. Often it is used to monitor the direct vicinity, e.g., by fixed installed cameras, but, as mentioned above, wide distances can be covered. This then usually depends on supportive technology to bridge the distances, such as cellular or satellite technology to transmit the image material (see the respective chapters below). |
| Energy Requirements | The energy requirements for video monitoring can depend on multiple aspects, in particular the volumes and distances that need to be covered. Where wired power is not possible or practical, battery or solar powered installations and appropriate consumption management may be used. |
| Data Related Capabilities and Limitations | Large volumes of data can be generated during the capture and further processing of video footage. This in particular can be the case with live monitoring of events. However, as mentioned above, due to latency and capacity limitations of blockchain architectures (in particular due to time needed to achieve consensus for validating data on a blockchain) such limitations may conflict with the requirements for live monitoring. |
| Other Aspects | Video monitoring technology usually can be provided at reasonable costs. However, in cases where personal data, such as biometric information and other sensitive data is involved, legal limitations or obligations such as the General Data Protection Regulation (GDPR) need to be considered. In particular, legal requirements to modify or delete data may be an issue if the blockchain environment would not allow it to meet such requirements. |
| Typical Use Cases | A barcode is a machine-readable optical label that contains information about the item to which it is attached or assigned to. A QR code is a matrix type of barcode. The use of bar and QR codes is mostly associated with fast moving consumer goods for supermarket check-out, but is also widely used in the early stages of the supply chain. Within the mining industry, barcodes and QR codes can, for instance, be attached to bags of ore, ingots, and even containers to identify specific lots and verify provenance [25]. Moreover, unlike RFID labels for example, bar- and QR codes can be generated and distributed electronically, e.g., via e-mail or mobile phone. |
| Robustness | Barcode and QR codes usually are quite robust. For example, certain materials may allow that the bar or QR code is directly laser-printed on the material. Thus the robustness often correlates with the material of choice. This also means that a smelting procedure can interrupt the tracking of objects that are labeled with a laser-printed barcode or QR code. |
| Range | The range of a barcode or QR code is limited to its visibility, unless it is transmitted by supportive means. It requires a scanner or other reader to read the code and translate it into data for further processing. |
| Energy Requirements | Besides the energy needed to print and read the code, there are usually no further energy requirements. |
| Data Related Capabilities and Limitations | The data capacity of the barcode or QR code may be limited, depending on the type of code and the standard(s) applicable to it, for example in terms of data type, version and correction level. But usually it is used just to link to the relevant information via an URL. Problems can relate to difficulties reading a barcode or QR code, for example due to errors in code printing, surface contamination, water, humidity, varying lighting levels [3]. |
| Other Aspects | Barcode and QR code solutions both can be relatively low cost and low tech, which can make them very practical concerning most use cases for raw materials tracing and sourcing scenarios. However, to provide visibility and compatibility with the applicable standards, barcodes and QR codes require a minimum space to be printed on. This can exclude them from being printed directly on bulk material or material of smaller size. A solution to this may again be bags or other containers. |
| Typical Use Cases | Taggants are chemical or physical markers that are added to materials, which enables them to be tested for authenticity. In this way, they also mitigate risks for counterfeiting and forgery in products. There are several types of taggants/physical markers, and are generally microscopic particles. They are added to the materials in small quantities and are easy to detect with a “reader” mechanism. Markers can combine visible or concealed security features and have several form factors, such as DNA encoded information, or micro-dust made out of ceramics or diamonds that can withstand harsh processing treatments within the supply chain. Similarly to the unique fingerprints of humans, taggants can go beyond the level of barcodes since they can provide objects with an identity that cannot be tampered with [26]. A multilayer taggant system has been described based on phase change nanoparticles of metals and eutectic alloys, which can be added in matrix materials and printed on objects to form microscale features containing fluorescence and thermal signatures [27]. The fluorescence additive could be used for initial screening. Micro features could add an extra layer of protection, and phase change nanoparticles could be used for high capacity serialization or forensic investigation [27]. |
| Robustness | Chemical taggants, biological taggants, DNA taggants and isotope ratios may be too sensitive to the environment, may degrade over time, and may only function over a limited period of time [27]. They often may not stand smelting processes of raw materials. However, as mentioned, some markers or taggants, such as micro-dust made out of ceramics or diamonds, can withstand harsh processing treatments. Also, a durable colored polymer sandwich can be capable of surviving detonation events of explosives. The color sequence of the requisite layers can determine the origin and ownership of the materials [26]. |
| Range | Depending on the type of marker or taggant and the detection method, the ranges and performances can vary. |
| Energy Requirements | Besides the energy needed to generate and detect the marker or taggant, there are usually no further energy requirements. |
| Data Related Capabilities and Limitations | Often the data related capabilities of markers and taggants may be limited. DNA, as the building block of the genetic code, has the advantages of almost unlimited coding capacity for unique identifications and relatively cheap synthesis for taggants. However, the verification of DNA requires labour intensive sequencing of the DNA taggant [26]. Spectroscopic tagging can allow for high-throughput through verifying measurements via spectrophotometry [26]. |
| Other Aspects | Although the technology on which markers are based is mature, their use in raw materials supply chains for traceability and transparency purposes is still in the early stages and may be relatively costly. To enhance the security level of labeling, multilayer taggants that contain fluorescent, microscopic features and numeric code sequence may be used [27]. These solutions may be complemented with biochemical fingerprinting solutions to cross-check authenticity. |
| Typical Use Cases | A vast array of radio frequency-based technologies enable tracing of materials both on production sites, such as mines, as well as throughout global supply chains [28]. RFID tags combined with sensors are widely used to measure everything from location to temperature conditions for tracked goods [29], [12]. One can distinguish between tracking technologies that are designed for short range applications such as NFC (Near Field Communications) to large networks using low power such as Sigfox or LoRa (Low Range). The emerging 5G networks can create an additional layer for tracking use cases as they were designed to further enhance the IoT with larger data volume capacities and autonomous vehicle applications. |
| Robustness | The robustness of the power networks depends on the type of network and the devices involved. Some may be encapsulated to withstand harsh environments, but usually there are limits to be considered. For example, RFID tags or other senders usually will not withstand a smelting process. |
| Range | The various technologies often differ significantly in their range and performance. Unlike a barcode, a sender may not always be required to be within the line of sight of the reader, so it may be embedded in the tracked object. For example, an RFID device inside a box or other container may be readable from outside without a need to open the box or container. However, there may be performance variations, too [3]. NFC communication usually has a range of a few cm only, whereas Sigfox or LoRa can enable long-range transmissions with low power consumption to bridge the gap to more energy intensive long range networks, such as 5G, 4G etc. |
| Energy Requirements | Passive devices, such as some types of RFID, can be powered by energy from the reader’s interrogating radio waves. Active devices require their own source of power, for example a battery. This is why active devices usually can be read at a greater range. |
| Data Related Capabilities and Limitations | Depending on the technology used, devices can be read only or include a fixed or programmable logic for processing and transmitting and/or receiving data. In cases where the technology responds strictly sequentially (like with some types of RFID devices), managing bulks of items may be an issue, because the time needed for bulk reading can grow linearly with the number of devices to be read. Depending on the granularity of the tracking and the content that is tracked, data protection requirements need to be considered, too. For example, tracking of movements of goods per RFID, NFC, GSM or other technology may also allow direct conclusions to be drawn about the movement or performance of persons involved with the handling of the tracked goods. Moreover, depending on the type of technology, eavesdropping may be an issue. For example standard plain NFC may not be protected against eavesdropping and data modifications. |
| Other Aspects | A variety of standards have been developed for various use cases to provide compatibility and safety. Although implementing and using these networks for tracking objectives can be costly, some of their features such as roaming across borders are key benefits when tracking global supply chain journeys. Moreover, the low latency rates of 5G are expected to enable new business models to emerge for the IoT ecosystem with potential new tracking applications. |
| Typical Use Cases | Small satellites in low orbits allow mobile means of transportation such as trucks, airplanes, and ships to continuously stay in contact throughout their journeys, by providing updates on location, as well as external conditions. One of the most used satellite systems for shipment tracking is “AIS” (automatic identification system). This automatic tracking system uses transceivers on ships for vessel traffic services. Its main goal was initially to avoid accident collisions and aid ship navigation. However very rapidly the potential for using the AIS satellites for fleet and cargo tracking seemed apparent. Furthermore satellite imaging can provide almost real time information about events happening in the field, especially in areas that are geographically remote such as open air mines [30,31,32]. As already mentioned in the introduction, video monitoring data from several different Earth observation satellites, is used to show and analyse smelter activity levels and to detect periods of shutdown or inactivity [8]. Also drones can complement these real time observations and insights with additional aerial imaging. |
| Robustness | Usually the robustness of the satellite is no issue. However, the data connection to the satellite may be subject to limitations. |
| Range | Obviously, communication with a satellite can cover long distances. The resolution can be relatively high. However, clouds and other weather conditions, volcanic eruptions or other incidents may have an impact on imagery, spectrography or other procedures and the respective quality of the data. |
| Energy Requirements | The satellites can be powered by built-in photovoltaic modules. |
| Data Related Capabilities and Limitations | In terms of imagery, there is a classification of five types of resolution: spatial (image size representing a size of surface), spectral (wavelength interval and number of intervals), temporal (time of image collection periods for a surface location), radiometric (levels of brightness and bit-depths of sensors) and geometric (capability to effectively image a portion of surface in a pixel). Because of relatively high resolutions, satellites can generate huge volumes of data. Depending on the technology and the altitude of the satellites, resolutions can vary. It can take an effort to process and create useful data from the raw data. Privacy regulations may also need to be considered. As mentioned, the quality of the data may be impacted by weather conditions, volcanic eruptions, or other incidents. By combining satellite imagery with vector or raster data from geographic information systems, the imagery can be spatially rectified to gain compatibility with further data sources. |
| Other Aspects | Smaller low-orbit satellites can be more cost-effective and are transforming the field of supply chain visibility and transparency. Recent advances in satellite imaging, data processing, and machine learning are opening new doors to monitor activities within supply chains in almost real time as well as rendering the cost of accessing geospatial data more affordable. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bacchetta, A.v.B.; Krümpel, V.; Cullen, E. Transparency with Blockchain and Physical Tracking Technologies: Enabling Traceability in Raw Material Supply Chains. Mater. Proc. 2021, 5, 1. https://doi.org/10.3390/materproc2021005001
Bacchetta AvB, Krümpel V, Cullen E. Transparency with Blockchain and Physical Tracking Technologies: Enabling Traceability in Raw Material Supply Chains. Materials Proceedings. 2021; 5(1):1. https://doi.org/10.3390/materproc2021005001
Chicago/Turabian StyleBacchetta, Angela v. Beckh, Volker Krümpel, and Ella Cullen. 2021. "Transparency with Blockchain and Physical Tracking Technologies: Enabling Traceability in Raw Material Supply Chains" Materials Proceedings 5, no. 1: 1. https://doi.org/10.3390/materproc2021005001
APA StyleBacchetta, A. v. B., Krümpel, V., & Cullen, E. (2021). Transparency with Blockchain and Physical Tracking Technologies: Enabling Traceability in Raw Material Supply Chains. Materials Proceedings, 5(1), 1. https://doi.org/10.3390/materproc2021005001






