1. Introduction
The internet of things (IoT) has become crucial in modern infrastructure, innovating smart homes, healthcare systems, transportation networks, and urban governance. However, the explosive growth of IoT devices has introduced significant security vulnerabilities such as distributed denial of service (DDoS) attacks which is one of the most critical threats [
1,
2]. These attacks disrupt essential services and lead to severe economic losses and societal harm. Traditional, centralized security solutions, while useful in controlled environments, struggle to meet the growing demands of scalability, adaptability, and data privacy required in large, distributed networks. Consequently, a shift towards decentralized frameworks has emerged as a promising avenue for enhancing security in IoT ecosystems.
Therefore, we developed a decentralized security framework by integrating federated learning (FL) and blockchain technology to tackle the challenges of detecting and mitigating DDoS attacks. FL offers a privacy-preserving collaborative learning approach by keeping raw data localized on edge devices. This enhances user privacy by minimizing the risks associated with centralized data storage. Blockchain technology complements this framework by providing a transparent, tamper-proof log of events and distributed monitoring, ensuring data integrity and accountability [
3,
4,
5]. Software-defined networking (SDN) was also used for dynamic resource management and a rapid response to security threats, thereby addressing the shortcomings of traditional, rigid network infrastructures.
The remainder of this article is organized as follows:
Section 2 provides an overview of related work in the domains of FL, blockchain, and SDN technologies.
Section 3 introduces the proposed framework in detail, describing how the three technologies are integrated to address the challenges of DDoS attack detection and prevention.
Section 4 presents the experimental results and performance analysis, demonstrating the effectiveness of the proposed approach. Finally,
Section 5 concludes the article and discusses potential directions for future research.
2. FL: Opportunities and Challenges
2.1. Advantages of FL
2.1.1. Privacy Preservation
FL ensures that raw data remains on local devices, eliminating the need for centralized data aggregation. Model parameters, such as weights and gradients, are transmitted between devices and the central aggregator, minimizing the risks of data breaches and unauthorized access. This feature makes FL particularly suited for healthcare and IoT, where sensitive information must be protected.
2.1.2. Scalability and Flexibility
By decentralizing the training process, FL alleviates the load on central servers and the communication overhead associated with transmitting large datasets. This distributed approach enhances the system’s scalability and fault tolerance so that the network can continue operating even if individual devices fail or are compromised. In large-scale IoT deployments, such as smart cities, flexibility is critical for maintaining continuous learning and adaptive security.
2.1.3. Reduced Latency and Network Costs
FL significantly reduces network congestion by only transmitting updates of the model instead of raw data, lowering bandwidth consumption and latency. This is particularly advantageous in edge computing environments where network resources are limited.
2.2. Challenges of Federated Learning
2.2.1. Threats from Malicious Devices
Despite its decentralized nature, FL remains vulnerable to attacks from malicious devices that can inject poisoned or biased models into the learning process. These Byzantine attacks can degrade the performance of the global model, reducing its ability to accurately detect or mitigate security threats.
2.2.2. Model Pollution and Poisoning Attacks
Attackers exploit FL frameworks by embedding malicious payloads into model updates to corrupt the model’s functionality. Over time, such model poisoning weakens the global model’s performance and introduces vulnerabilities that attackers can later exploit.
2.2.3. Model Inference and Privacy Leakage Risks
Even though FL avoids sharing raw data, the model parameters exchanged during training leak sensitive information through inference attacks [
6]. For example, attackers analyze gradients to extract patterns or reconstruct portions of the original training data, compromising user privacy.
2.2.4. Heterogeneous Data and Device Resources
In IoT scenarios, participating devices often generate non-IID data (i.e., data that is not identically and independently distributed) and have varying computational capacities. This heterogeneity negatively impacts model convergence, requiring sophisticated techniques such as personalized FL or asynchronous updates to ensure robust learning.
2.3. Integrating Blockchain and SDN with FL for Enhanced Security
To overcome these challenges, the developed framework leverages blockchain technology and SDN. Blockchain provides a tamper-resistant ledger to record model updates and security events [
7], enabling transparent auditing and accountability. It also mitigates the risk of model poisoning by storing hashes of valid models, ensuring that only verified updates are incorporated into the global model. SDN further enhances the framework by offering real-time network control and monitoring, enabling dynamic reconfigurations of network resources in response to detected threats. SDN controllers isolate compromised devices or reroute traffic during DDoS attacks, significantly reducing attack impact. The combination of FL, blockchain, and SDN thus provides a comprehensive security solution for IoT environments, ensuring privacy, scalability, and rapid threat mitigation.
3. Related Work
Recent advancements in applying FL to DDoS detection owe to the use of FL in various network environments as follows.
3.1. Applications of Federated Learning in DDoS Detection
In recent years, researchers have actively explored FL-based approaches for DDoS detection to address the challenges of data privacy and security. Nguyen et al [
8]. designed an FL-based defense system that enables network devices to train models locally without the need to centralize sensitive data. VY et al. applied FL to facilitate collaboration among multiple internet service providers (ISPs) for enhanced DDoS detection efficiency [
9]. Wang et al. integrated FL with convolutional neural networks (CNN) to extract features from network traffic, improving the detection of unknown attack patterns [
10].
3.2. Technical Challenges and Optimization in Distributed Learning
FL-based DDoS detection faces challenges such as limited computational resources and communication latency. Liu et al. proposed an FL framework combined with reinforcement learning to dynamically adjust communication frequency among devices, reducing latency [
11]. Zhao et al. investigated optimizing model synchronization in heterogeneous network environments to ensure efficient updates across different ISPs. Additionally [
12], Zhao et al. introduced model compression techniques to reduce model size without compromising accuracy, minimizing communication overhead between devices. By leveraging FL, network nodes collaboratively detect DDoS attacks while preserving user privacy, mitigating the risks associated with centralized systems. FL demonstrates its potential to enhance DDoS defense capabilities and provides new directions for future network security solutions [
13].
4. Materials and Methods
4.1. The Dataset
The dataset used in this study was obtained from an open-source repository that contains a wide range of DDoS attack records. It contains extensive network traffic data, including various types of DDoS attacks such as SYN flood, user datagram protocol (UDP) flood, HTTP-based attacks, and amplification attacks. The dataset included key features such as packet size, protocol type, traffic flow rate, and timestamps, making it appropriate for training machine learning models. The data was preprocessed to remove noise and normalize feature values to ensure consistency across different attack scenarios. Missing values were handled through interpolation or mean imputation techniques. In this study, the dataset was split into training and validation sets with 80% of the data used to train the models and 20% reserved for validation. This structure ensured the model’s generalization of unseen data and detected known and novel DDoS attacks.
4.2. Network Traffic Sensors
The data was collected from intrusion detection systems (IDS) and network flow monitors by capturing real-time network traffic across different protocols and network layers. These systems utilize essential traffic features, such as IP addresses, packet rates, and port numbers, and are calibrated periodically to ensure accurate data collection. This setup provides a reliable and comprehensive incoming traffic pattern to identify abnormal behavior associated with DDoS attacks.
4.3. Deep Neural Networks (DNN)
DNNs are used to model complex relationships between network traffic features and attack labels. They consist of multiple layers of neurons that enable the model to learn high-level abstractions from raw traffic data. DNNs are particularly useful in capturing non-linear patterns and distinguishing between different attack types (
Figure 1).
4.4. CNN
CNNs are applied to analyze the temporal and spatial relationships in network traffic. By using convolutional layers, CNNs detect local patterns, such as bursty traffic flows or protocol-specific anomalies which are indicative of DDoS attacks. CNNs are also robust to noise and can efficiently process large-scale traffic data.
4.5. Recurrent Neural Networks (RNN)
RNNs are used to model sequential dependencies in the network traffic data. Since DDoS attacks often involve patterns that unfold over time, RNNs are well-suited to learn these temporal relationships. The hidden state in RNNs enables the model to retain information from earlier traffic flows, making it effective for identifying ongoing attacks.
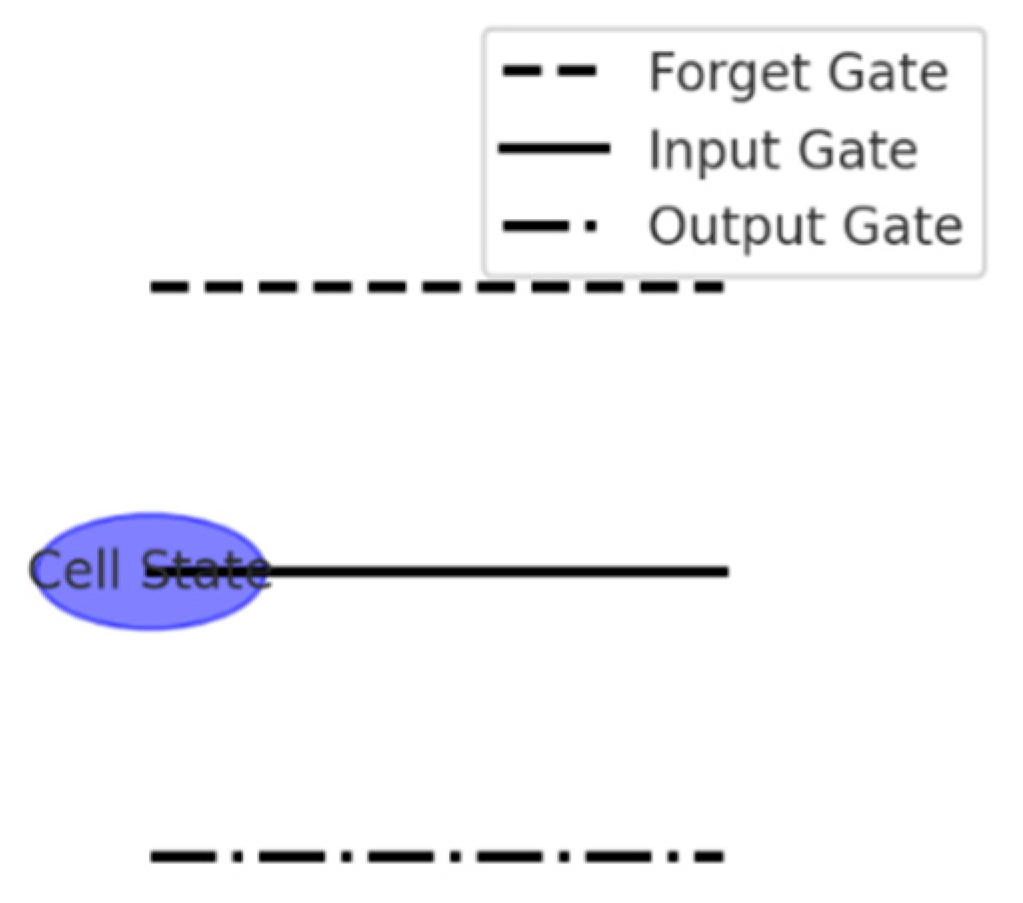
4.6. Long Short-Term Memory (LSTM) Networks
A variant of RNN, LSTM networks are utilized to overcome the vanishing gradient problem, enabling the model to learn long-term dependencies. LSTM cells maintain an internal memory, which allows the model to accurately detect attacks that exhibit patterns over extended periods (
Figure 2).
4.7. Particle Swarm Optimization (PSO)
PSO is used to optimize the hyperparameters of the DNN, CNN, and RNN models. By simulating the behavior of a swarm, the algorithm explores the search space for optimal parameter values that improve model performance. PSO ensures efficient convergence to a robust model configuration, reducing the computational cost of hyperparameter tuning (
Figure 3).
4.8. Performance Evaluation Criteria
The models are evaluated using statistical metrics, such as accuracy, precision, recall, and F1-scores. These metrics are used to assess the models’ abilities to correctly classify normal traffic and detect various DDoS attacks. The use of multiple metrics ensures an evaluation of the models across different aspects, including false positive rates and detection accuracy.
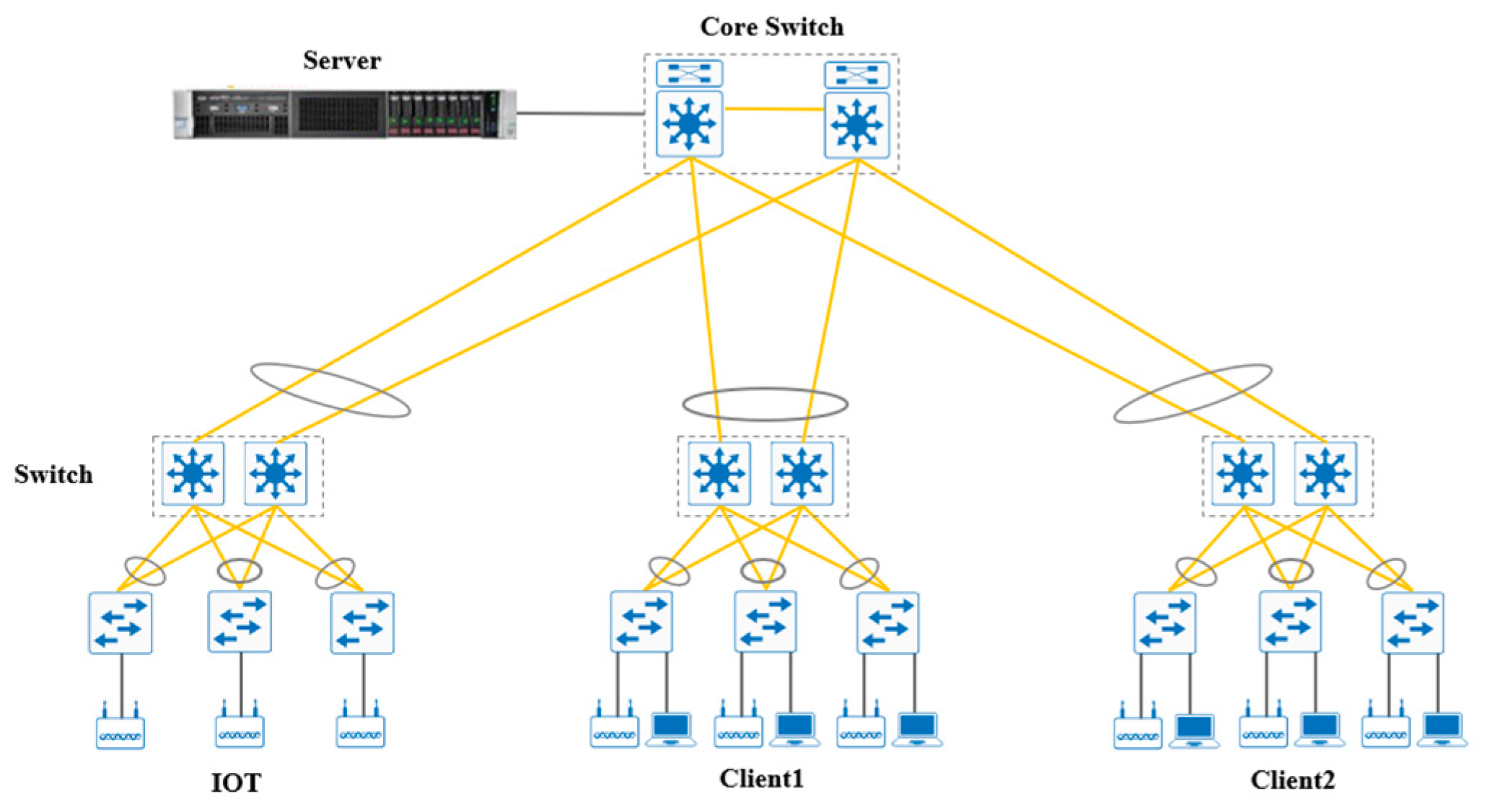
4.9. Network Architecture Diagram
The network architecture in this study is shown in
Figure 4. It supports a decentralized FL-based DDoS detection and prevention system. This framework integrates SDN and blockchain technology to enable real-time threat mitigation and ensure data integrity.
5. Network Architecture Description
5.1. Server Endpoint
The server is responsible for the aggregation and update of global models. Each client, such as IoT devices and network nodes, sends the trained model’s parameters to the server which performs weighted averaging to update the global model. The updated model is then distributed back to the clients for the next training iteration.
5.2. Core Switches
Located at the core of the network, the core switches manage traffic from multiple clients and ensure efficient data transmission. With redundant designs and multi-path connections, the switches guarantee high availability and fault tolerance, preventing disruptions caused by single-point failures.
5.3. Network Switches
This layer handles traffic distribution between servers, core switches, and various sub-networks or clients. These switches support SDN control and real-time resource allocation adjustments to quickly respond to network conditions during an attack.
5.4. IoT Sensors and Terminal Devices
The architecture incorporates multiple IoT sensors and client devices responsible for monitoring network traffic and collecting data. These devices perform local model training to collaboratively detect attacks. The locally trained models are periodically uploaded to the server for aggregation within the federated learning process.
5.5. Client Network Nodes (Client 1 and 2)
Each client node consists of multiple devices or sub-networks including laptops, desktops, or wireless routers. During a DDoS attack, these client nodes dynamically adjust their traffic paths through SDN controllers to mitigate the impact of the attack.
5.6. SDN Control and Blockchain Validation
All network events and model updates are recorded in a blockchain ledger to ensure data immutability and enable transparent auditing. The SDN controllers provide dynamic reconfigurations of network paths, allowing for the isolation of suspicious devices and optimal resource utilization. The advantages of such architecture are outlined in the following subsections (
Section 5.6.1,
Section 5.6.2 and
Section 5.6.3):
5.6.1. Decentralized Learning
Each node participates in local model training, reducing the computational burden on the centralized server.
5.6.2. Dynamic Resource Management
SDN technology enables real-time traffic control and resource allocation adjustments.
5.6.3. High Security
Blockchain technology ensures the integrity and transparency of data and events. This network architecture demonstrates how a decentralized FL system operates in an IoT environment, ensuring privacy, security, and scalability. The design showcases excellent real-time response capabilities for DDoS attack mitigation, laying a solid foundation for future smart city and large-scale IoT applications.
5.7. DDoS Dataset
This section outlines the dataset used for evaluating the proposed FL-based DDoS detection framework. The dataset, referred to as the SDN–DDoS traffic dataset, provides information on DDoS attack patterns in an SDN environment. The data collected is essential for training, validating, and benchmarking the models used in this study.
The dataset contains several thousand records representing different network conditions, including both normal traffic and various types of DDoS attacks. Each record includes the following attributes that are crucial for identifying DDoS attacks:
Timestamp: The exact time when the traffic was recorded.
Source and Destination IP: Identifies the sender and receiver of the packets.
Packet Size: Describes the size of each transmitted packet.
Protocol Type: Indicates the protocol used (e.g., TCP, UDP, and ICMP).
Flow Rate: Measures the rate of packets or data flowing through the network.
Label: Specifies whether the traffic is normal or an attack (e.g., SYN Flood and UDP Flood).
The key attributes used to identify DDoS attacks in the SDN–DDoS traffic dataset are summarized in
Table 1.
The dataset was pre-processed to remove missing or noisy data to ensure consistency across different attack scenarios. The dataset was split into 80 and 20% for training and validation, maintaining a balance between normal and malicious traffic. This dataset is used for training machine learning models and real-time DDoS detection. The combination of multiple attributes allows for the development of robust models to distinguish between benign and malicious traffic. By leveraging FL, the model improves continuously while preserving the privacy of the participating nodes.
5.8. Diagram
Figure 5 illustrates a system that uses FL and the FLOWER framework to analyze data connection logs and enhance the security functions of the firewall.
5.8.1. Data Transmission and Log Collection
Data flows between the ISP and the internal network. The firewall monitors incoming and outgoing data connections, intercepting and collecting data connection logs for further analysis by the server.
5.8.2. FL Analysis Using FLOWER Framework
The collected data connection logs are transmitted from the firewall to the server. The server collaborates with multiple clients through FL models to analyze the data. FLOWER framework supports a multi-client environment, allowing each client to perform local computations of weights and send the results back to the server for aggregation. The server and clients exchange weights bidirectionally to continuously optimize the model.
5.8.3. Returning Analysis Results
After the analysis is completed, the server sends the results back to the firewall. The firewall applies blocking strategies based on the analysis results to intercept potential threats or suspicious connections.
FL protects client data privacy by ensuring that large amounts of sensitive data are not transmitted to the server, reducing the risk of data breaches. The analyzed data is automatically sent back to the firewall, enabling it to block abnormal behaviors or attacks in real time. This architecture is applied in IoT networks, enterprise security systems, or any network environment requiring real-time protection.
The developed system demonstrates how the FLOWER framework for FL analyzes data connection logs and how the analysis results can be utilized by the firewall to achieve real-time security protection.
6. Developed System
We developed an FL approach, using the Flower framework, to efficiently detect and analyze DDOS attacks through decentralized firewalls. The system leverages multiple firewall nodes that collect packet data in a distributed manner. FL optimizes the detection capabilities without sharing raw data and maintains data privacy. Each firewall node acts as a learning agent, continuously improving its attack detection rules in response to evolving patterns.
Each firewall node trains a local model on collected packet data to identify potential DDOS attack features. After training, nodes send their model weights (not raw data) to the central server, ensuring privacy and compliance. The central server aggregates local models using weighted averaging (1), which can be expressed as follows:
where
is the updated global model weight,
is the weight of the
node’s model at iteration
is the data size of that node, and
N is the total number of nodes.
The aggregated global model is sent back to the nodes for further training, continuously improving detection performance across iterations.
6.1. PSO-Based Optimization in FL
The developed system integrates PSO to accelerate the search for attack sources. Each firewall node, treated as a particle in the PSO algorithm, explores potential attack patterns in network traffic. The velocity and position of each node are updated using the following equations.
6.1.1. Velocity Update
The velocity update can be expressed as follows:
: Velocity of the particle at iteration.
: Position of the particle.
: Personal best position of the particle.
: Global best position found by the swarm.
: Random variables, are hyperparameters.
6.1.2. Position Update
This iterative update mechanism enables nodes to converge toward optimal attack patterns and enhances detection accuracy, which is express able as the following:
6.2. CNN–LSTM for DDOS Detection in Network Traffic
We designed a lightweight CNN–LSTM model to analyze the temporal characteristics of network traffic. The CNN extracts short-term patterns from packet sequences, while the LSTM identifies long-term anomalies. The model’s loss function is the mean squared error (MSE) which is used to measure the deviation between predicted and actual values, which can be expressed as the following:
where
is the actual value,
is the predicted value, and
n is the number of samples.
6.3. Results
In the experiment, multiple firewall nodes were used to perform FL on simulated DDOS attack traffic. The effectiveness of our CNN–LSTM model was evaluated and compared with other models under different network loads, using accuracy and recall. Accuracy was used to measure the percentage of correctly identified DDOS attacks while recall was used to assess the model’s ability to detect all attack events, expressible as the following:
where TP is the number of true positives and FN is the number of false negatives.
7. Conclusions and Future Work
We investigated how FL with the FLOWER framework effectively detects DDOS attacks in a decentralized environment while maintaining data privacy. By integrating PSO with the CNN–LSTM model, the system shows high accuracy and efficiency in detecting network anomalies. It is necessary to reduce communication overhead by developing advanced model compression techniques to minimize bandwidth usage. Implementing dynamic resource allocation is also required to handle varying network demands. To enhance real-time detection, more lightweight models need to be added to manage high-frequency traffic efficiently.
Author Contributions
Conceptualization, M.-H.H.; methodology, M.-H.H.; experiment program design, M.-H.H.; data collection, C.-C.L.; statistical analysis, C.-C.L.; writing—original draft preparation, C.-C.L. All authors have read and agreed to the published version of the manuscript.
Funding
National Science and Technology Council, (NSTC-112/113-2634-F-150-001-MBK; 113-2218-E-150-003).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The datasets generated and/or analyzed during the current study are not publicly available due to privacy concerns, proprietary reasons but are available from the corresponding author on reasonable request.
Acknowledgments
This research was supported by the National Science and Technology Council.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Bonawitz, K.; Eicher, H.; Grieskamp, W.; Huba, D.; Ingerman, A.; Ivanov, V.; Kiddon, C.; Konecny, J.; Mazzocchi, S.; Mcmahan, B.; et al. Towards Federated Learning at Scale: System Design. Available online: https://proceedings.mlsys.org/paper_files/paper/2019/hash/7b770da633baf74895be22a8807f1a8f-Abstract.html (accessed on 8 May 2024).
- Chhikara, P.; Tekchandani, R.; Kumar, N.; Guizani, M.; Hassan, M.M. Federated Learning and Autonomous UAVs for Hazardous Zone Detection and AQI Prediction in IoT Environment. IEEE Internet Things J. 2021, 8, 15456–15467. [Google Scholar] [CrossRef]
- Liu, Y.; Nie, J.; Li, X.; Ahmed, S.H.; Lim, W.Y.B.; Miao, C. Federated Learning in the Sky: Aerial-Ground Air Quality Sensing Framework With UAV Swarms. IEEE Internet Things J. 2020, 8, 9827–9837. [Google Scholar] [CrossRef]
- Buterin, V. Ethereum Whitepaper. 2. Buterin, V. Ethereum Whitepaper. Available online: https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf (accessed on 20 November 2024).
- Majeed, U.; Khan, L.U.; Hassan, S.S.; Han, Z.; Hong, C.S. FL-Incentivizer: FL-NFT and FL-Tokens for Federated Learning Model Trading and Training. IEEE Access. 2023, 11, 4381–4399. [Google Scholar] [CrossRef]
- Kreutz, D.; Ramos, F.M.V.; Verissimo, P.E.; Rothenberg, C.E.; Azodolmolky, S.; Uhlig, S. Software-Defined Networking: A Comprehensive Survey. Proc. IEEE 2015, 103, 14–76. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Marchal, S.; Miettinen, M.; Fereidooni, H.; Asokan, N.; Sadeghi, A.-R. DÏoT: A federated self-learning anomaly detection system for IoT. In Proceedings of the 39th International conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019. [Google Scholar]
- VY, N.C.; Quyen, N.H.; Duy, N.H.; Pham, V.-H. Federated learning-based intrusion detection in the context of IIoT networks: Poisoning attack and defense. In Proceedings of the Network and System Security: 15th International Conference, NSS 2021, Tianjin, China, 23 October 2021; pp. 131–147. [Google Scholar]
- Wang, Y.; Su, Z.; Luan, T.H.; Li, R.; Zhang, K. Federated Learning With Fair Incentives and Robust Aggregation for UAV-Aided Crowdsensing. IEEE Trans. Netw. Sci. Eng. 2021, 9, 3179–3196. [Google Scholar] [CrossRef]
- Liu, S.; Yang, S.; Zhang, H.; Wu, W. A federated learning and deep reinforcement learning-based method with two types of agents for computation offload. Sensors 2023, 23, 2243. [Google Scholar] [CrossRef] [PubMed]
- Zhao, H.; Ji, F.; Li, Q.; Guan, Q.; Wang, S.; Wen, M. Federated Meta-Learning Enhanced Acoustic Radio Cooperative Framework for Ocean of Things. IEEE J. Sel. Top. Signal Process. 2022, 16, 474–486. [Google Scholar] [CrossRef]
- Latif, N.; Ma, W.; Ahmad, H.B. Advancements in securing federated learning with IDS: A comprehensive review of neural networks and feature engineering techniques for malicious client detection. Artif Intell Rev. 2025, 58. [Google Scholar] [CrossRef]
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).