Information-Theoretic Security of RIS-Aided MISO System Under N-Wave with Diffuse Power Fading Model †
Abstract
1. Introduction
2. System and Channel Models
3. RIS Channel Characterization
| Algorithm 1: Unsupervised EM machine learning algorithm for fitting , , and of Nakagami-m RVs |
 |
4. RIS Secrecy Performance
4.1. Distribution of and
4.2. Secrecy Outage Probability (SOP)
4.3. Average Secrecy Rate (ASR)
4.4. Average Secrecy Loss (ASL)
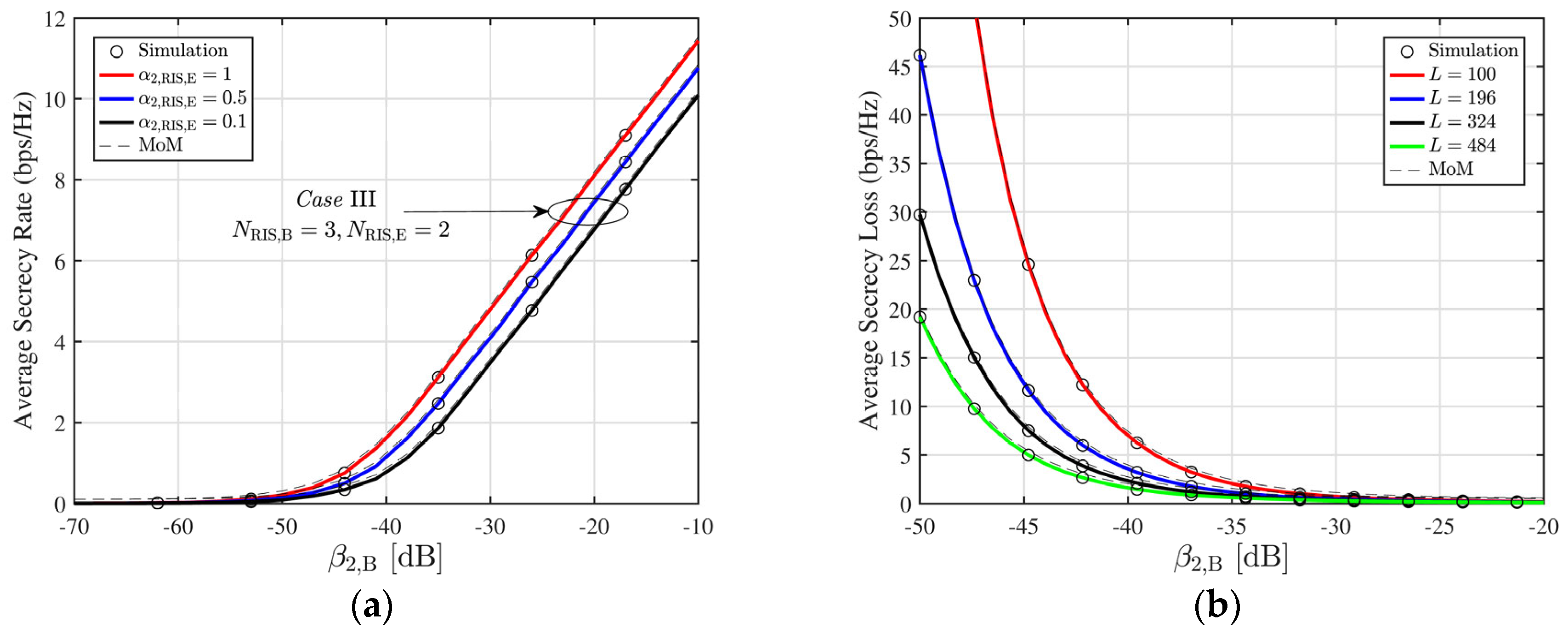
5. Numerical Results and Discussions
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhou, G.; Pan, C.; Ren, H. Secure Wireless Communication in RIS-Aided MISO System with Hardware Impairments. IEEE Wirel. Commun. Lett. 2021, 10, 1309–1313. [Google Scholar] [CrossRef]
- Yacoub, M.D. The κ-μ distribution and the η-μ distribution. IEEE Antennas Propagat. Mag. 2007, 49, 68–81. [Google Scholar] [CrossRef]
- Durgin, G.D. Theory of Stochastic Local Area Channel Modeling for Wireless Communications. Ph.D. Thesis, Virginia Polytechnic Institute and State University, Blacksburg, VA, USA, 2000. [Google Scholar]
- Chun, Y.J. A generalized fading model with multiple specular components. arXiv 2018, arXiv:1810.05258. [Google Scholar]
- Zöchmann, E.; Caban, S.; Mecklenbräuker, C.F.; Pratschner, S.; Lerch, M.; Schwarz, S.; Rupp, M. Better than Rician: Modelling millimetre wave channels as two-wave with diffuse power. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 21. [Google Scholar] [CrossRef]
- Trigui, I.; Ajib, W.; Zhu, W.-P.; Renzo, M.D. Performance Evaluation and Diversity Analysis of RIS-Assisted Communications Over Generalized Fading Channels in the Presence of Phase Noise. IEEE Open J. Commun. Soc. 2022, 3, 593–607. [Google Scholar] [CrossRef]
- Alves Junior, M.A.; Fraidenraich, G.; Ferreira, R.C.; De Figueiredo, F.A.P.; De Lima, E.R. Multiple-Antenna Weibull-Fading Wireless Communications Enhanced by Reconfigurable Intelligent Surfaces. IEEE Access 2023, 11, 107218–107236. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, J.; Lu, J.; Wang, J.; Zhang, Q.; Wang, D. Secrecy Rate Analysis for RIS-Aided Multi-User MISO System over Rician Fading Channel. J. Commun. Inf. Netw. 2023, 8, 48–56. [Google Scholar] [CrossRef]
- Shi, W.; Xu, J.; Xu, W.; Yuen, C.; Lee Swindlehurst, A.; Zhao, C. On Secrecy Performance of RIS-Assisted MISO Systems Over Rician Channels with Spatially Random Eavesdroppers. IEEE Trans. Wirel. Commun. 2024, 23, 8357–8371. [Google Scholar] [CrossRef]
- Abramowitz, M.; Stegun, I.A. Handbook of Mathematical Functions; US Department of Commerce, National Bureau of Standards: Washington, DC, USA, 1972.
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network: Joint Active and Passive Beamforming Design. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Durgin, G.D.; Rappaport, T.S.; De Wolf, D.A. New analytical models and probability density functions for fading in wireless communications. IEEE Trans. Commun. 2002, 50, 1005–1015. [Google Scholar] [CrossRef]
- Björnson, E.; Sanguinetti, L. Rayleigh Fading Modeling and Channel Hardening for Reconfigurable Intelligent Surfaces. IEEE Wirel. Commun. Lett. 2020, 10, 830–834. [Google Scholar] [CrossRef]
- Sánchez, J.D.V.; Urquiza-Aguiar, L.; Paredes, M.C.P.; López-Martínez, F.J. Expectation-Maximization Learning for Wireless Channel Modeling of Reconfigurable Intelligent Surfaces. IEEE Wirel. Commun. Lett. 2021, 10, 2051–2055. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.; Rodrigues, M.R.D.; McLaughlin, S.W. Wireless Information-Theoretic Security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Kong, L.; Tran, H.; Kaddoum, G. Performance analysis of physical layer security over α-μ fading channel. Electron. Lett. 2016, 52, 45–47. [Google Scholar] [CrossRef]
- Li, S.; Yang, L.; Hasna, M.O.; Alouini, M.S.; Zhang, J. Amount of Secrecy Loss: A Novel Metric for Physical Layer Security Analysis. IEEE Commun. Lett. 2020, 24, 1626–1630. [Google Scholar] [CrossRef]
- Da Costa, D.B.; Yacoub, M.D.; Filho, J. Highly Accurate Closed-Form Approximations to the Sum of α-μ Variates and Applications. IEEE Trans. Wirel. Commun. 2008, 7, 3301–3306. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vega-Sánchez, J.D.; Zambrano, A.; Mena, R.; Oscullo, J. Information-Theoretic Security of RIS-Aided MISO System Under N-Wave with Diffuse Power Fading Model. Eng. Proc. 2024, 77, 1. https://doi.org/10.3390/engproc2024077001
Vega-Sánchez JD, Zambrano A, Mena R, Oscullo J. Information-Theoretic Security of RIS-Aided MISO System Under N-Wave with Diffuse Power Fading Model. Engineering Proceedings. 2024; 77(1):1. https://doi.org/10.3390/engproc2024077001
Chicago/Turabian StyleVega-Sánchez, José David, Ana Zambrano, Ricardo Mena, and José Oscullo. 2024. "Information-Theoretic Security of RIS-Aided MISO System Under N-Wave with Diffuse Power Fading Model" Engineering Proceedings 77, no. 1: 1. https://doi.org/10.3390/engproc2024077001
APA StyleVega-Sánchez, J. D., Zambrano, A., Mena, R., & Oscullo, J. (2024). Information-Theoretic Security of RIS-Aided MISO System Under N-Wave with Diffuse Power Fading Model. Engineering Proceedings, 77(1), 1. https://doi.org/10.3390/engproc2024077001






