Digital Forensics of Quantum Computing: The Role of Quantum Entanglement in Digital Forensics—Current Status and Future Directions
Abstract
1. Introduction
2. Traditional Digital Forensic Mechanisms
2.1. Integrity
2.2. Authenticity
2.3. Confidentiality
3. Quantum Digital Forensic Mechanisms
3.1. Integrity
3.2. Authenticity
3.3. Confidentiality
4. Entanglement Detection
- Bell’s Theorem: States that no local hidden variable theory can reproduce all the predictions of quantum mechanics, and observing a violation of the Bell inequality proves that the system is entangled.
- CHSH Inequality: A common form of Bell’s inequality that involves measuring pairs of entangled particles. If the measured correlations go beyond the classical limit, it shows entanglement.
- Scalability: Detecting entanglement becomes more challenging as the number of qubits increases because the Hilbert space grows exponentially.
- Noise and Imperfections: In real-world quantum systems, noise and imperfections can hide entanglement, making it more difficult to detect.
- Mixed States: Many quantum systems exist in mixed states rather than pure states, and detecting entanglement in such mixed states is more complex.
5. Realization in Current Experiments
6. Findings
7. Discussion
- 1-
- Integrity: Using entanglement-based quantum hash functions ensures that any unauthorized change to digital evidence will collapse the quantum state, making tampering immediately detectable. This method aims to address the collision vulnerabilities of classical hashes while offering a future-proof solution resistant to quantum attacks.
- 2-
- Authenticity: QDS, based on entangled particles and governed by the no-cloning theorem, are explored as a way to verify that forensic evidence comes from a trusted source. Unlike RSA or ECC, QDS cannot be forged or denied, strengthening its admissibility in legal cases.
- 3-
- Confidentiality: Entanglement-assisted QKD and quantum audit trails will be used to protect the transmission and storage of forensic evidence. These methods create tamper-evident custody chains, where any interception causes detectable anomalies, ensuring evidence stays private and traceable throughout its lifecycle.
8. Challenges
Influence of External Environments
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- INTERPOL. Digital Forensics.Helping Our Member Countries Make Best Use of Electronic Evidence. INTERPOL. 2025. Available online: https://www.interpol.int/en/How-we-work/Innovation/Digital-forensics (accessed on 9 March 2025).
- Shor, P.W. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 2014, 560, 7–11. [Google Scholar] [CrossRef]
- Narasimhan, P.; Ala, D. Ensuring the integrity of digital evidence: The role of the chain of custody in digital forensics. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2024, 10, 2438–2450. [Google Scholar] [CrossRef]
- Nielsen, M.A.; Chuang, I.L. Quantum Computation and Quantum Information; Cambridge University Press: Cambridge, UK, 2010. [Google Scholar] [CrossRef]
- Alagic, G.; Apon, D.; Cooper, D.; Dang, Q.; Dang, T.; Kelsey, J.; Lichtinger, J.; Liu, Y.-K.; Miller, C.; Moody, D. Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2022. [Google Scholar] [CrossRef]
- European Telecommunications Standards Institute (ETSI). Quantum-Safe Cryptography and Security. 2022. Available online: https://www.etsi.org/images/files/ETSIWhitePapers/QuantumSafeWhitepaper.pdf (accessed on 18 March 2025).
- Brijwani, G.N.; Ajmire, P.E.; Thawani, P.V. Future of quantum computing in cyber security. In Advancements in Quantum Blockchain with Real-Time Applications; IGI Global: Hershey, PA, USA, 2023; Available online: https://www.igi-global.com/chapter/future-of-quantum-computing-in-cyber-security/319874 (accessed on 9 March 2025).
- Casey, E. Digital Evidence and Computer Crime: Forensic Science, Computers and the Internet, 3rd ed.; Academic Press: Burlington, MA, USA, 2011; pp. 22–23. [Google Scholar]
- Thakar, A.A.; Patel, B.V.; Kumar, K. An Empirical Study Illustrating Effects on Hash Value Changes in Forensic Evidence Appreciation. Int. J. Sci. Res. 2021, 10, 1356–1358. [Google Scholar] [CrossRef]
- Schmitt, V.; Jordaan, J. Establishing the validity of MD5 and SHA-1 hashing in digital forensic practice in light of recent research demonstrating cryptographic weaknesses in these algorithms. Int. J. Comput. Appl. 2013, 68, 40–43. [Google Scholar] [CrossRef]
- Rasjid, Z.E.; Soewito, B.; Witjaksono, G.; Abdurachman, E. A review of collisions in cryptographic hash function used in digital forensic tools. Procedia Comput. Sci. 2017, 116, 381–392. [Google Scholar] [CrossRef]
- Kumar, K.; Sofat, S.; Jain, S.K.; Aggarwal, N. Significance of Hash Value Generation in Digital Forensic: A Case Study. Int. J. Eng. Res. Dev. 2012, 2, 64–70. [Google Scholar]
- SalvationDATA. MD5 and SHA1: Essential Hash Values in Digital Forensics. 2023. Available online: https://www.salvationdata.com/knowledge/hash-value/ (accessed on 26 September 2025).
- Nelson, B.; Phillips, A.; Steuart, C. Guide to Computer Forensics and Investigations, 6th ed.; Cengage Learning: Boston, MA, USA, 2018. [Google Scholar]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundation of Computer Science, Washington, DC, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Joseph, G.P.; Capra, D.; Grimm, P.W. Authenticating Digital Evidence, Fayette County Bar Association. 2017. Available online: http://www.fcba.com/wp-content/uploads/2024/06/Authenticating-Digital-Evidence.pdf (accessed on 25 April 2025).
- Lynch, C. Authenticity and Integrity in the Digital Environment: An Exploratory Analysis of the Central Role of Trust; Council on Library and Information Resources: Alexandria, VA, USA, 2000. [Google Scholar]
- Ulbricht, B.R.; Moxley, C.; Austin, M.D.; Norburg, M.D. Digital Eyewitnesses: Using New Technologies to Authenticate Evidence in Human Rights Litigation. Stanf. Law Rev. 2022, 74, 851. [Google Scholar]
- Dogra, K. Exploring the Role of Digital Signatures in Forensic Investigations, Hawk Eye Forensic. 2024. Available online: https://hawkeyeforensic.com/exploring-the-role-of-digital-signatures-in-forensic-investigations (accessed on 20 November 2024).
- Nath, S.; Summers, K.; Baek, J.; Ahn, G.-J. Digital Evidence Chain of Custody: Navigating New Realities of Digital Forensics. In Proceedings of the 2024 IEEE 6th International Conference on Trust, Privacy and Security in Intelligent Systems, and Applications, Washington, DC, USA, 28–30 October 2024; pp. 11–20. [Google Scholar]
- Banwani, D.; Kalra, Y. Maintaining and Evaluating the Integrity of Digital Evidence in Chain of Custody. Int. J. Recent Technol. Eng. 2021, 10, 90–96. [Google Scholar] [CrossRef]
- Guttman, B.; White, D.R.; Walraven, T. Digital Evidence Preservation: Considerations for Evidence Handlers; NIST Interagency Report 8387; NIST Publications: Gaithersburg, MD, USA, 2022. [Google Scholar]
- Machhi, J.; Madhavi, A.; Maurya, A.K.; Patil, S.; Lade, S. Blockchain-Based Digital Forensic Evidence Management Chain of Custody. Int. Res. J. Mod. Eng. Technol. Sci. 2023, 6, 2582–5208. [Google Scholar]
- D’Anna, T.; Puntarello, M.; Cannella, G.; Scalzo, G.; Buscemi, R.; Zerbo, S.; Argo, A. The Chain of Custody in the Era of Modern Forensics: From the Classic Procedures for Gathering Evidence to the New Challenges Related to Digital Data. Healthcare 2023, 11, 634. [Google Scholar] [CrossRef]
- Nguyen, C.; Costa, A. Digital Forensics Challenges in the Quantum Computing Era. ITSI Trans. Electr. Electron. Eng. 2022, 11, 1–7. Available online: https://journals.mriindia.com/index.php/itsiteee/article/download/153/140/1415 (accessed on 25 February 2025).
- Hou, P.; Shang, T.; Zhang, Y.; Tang, Y.; Liu, J. Quantum Hash Function Based on Controlled Alternate Lively Quantum Walks. Sci. Rep. 2023, 13, 5887. [Google Scholar] [CrossRef] [PubMed]
- Ziatdinov, M. From Graphs to Keyed Quantum Hash Functions. arXiv 2016, arXiv:1606.00256. [Google Scholar] [CrossRef]
- Hamlin, B.; Song, F. Quantum Security of Hash Functions and Property-Preservation of Iterated Hashing. arXiv 2019, arXiv:1902.08709. [Google Scholar] [CrossRef]
- Garcia-Escartin, J.C.; Gimeno, V.; Moyano-Fernández, J.J. Quantum Collision Finding for Homomorphic Hash Functions. arXiv 2021, arXiv:2108.00100. [Google Scholar] [CrossRef]
- Ablayev, F.; Ablayev, M. Quantum Hashing via Classical ε-Universal Hashing Constructions. arXiv 2014, arXiv:1404.1503. [Google Scholar]
- Jozsa, R.; Linden, N. On the Role of Entanglement in Quantum-Computational Speed-Up. Proc. R. Soc. A Math. Phys. Eng. Sci. 2003, 459, 2011–2032. [Google Scholar] [CrossRef]
- Clarke, P.J.; Collins, R.J.; Dunjko, V.; Andersson, E.; Jeffers, J.; Buller, G.S. Experimental demonstration of quantum digital signatures using phase-encoded coherent states of light. arXiv 2013, arXiv:1306.0879. [Google Scholar] [CrossRef]
- Gottesman, D.; Chuang, I. Quantum Digital Signatures. arXiv 2001, arXiv:quant-ph/0105032. [Google Scholar] [CrossRef]
- Lu, X.; Feng, D.-G. Quantum Digital Signature Based on Quantum One-Way Functions. arXiv 2004, arXiv:quant-ph/0403046. [Google Scholar] [CrossRef]
- Cid, M.I.G.; Martín, L.O.; Martín, D.D.; Sánchez-Ledesma, R.M.; Méndez, J.P.B.; Ayuso, V.M. A Feasible Hybrid Quantum-Assisted Digital Signature for Arbitrary Message Length. arXiv 2023, arXiv:2303.00767. [Google Scholar] [CrossRef]
- Duan, H. A Research on Quantum Digital Signatures. In Proceedings of the 5th International Conference on Computing and Data Science, Wenzhou, China, 15–17 November 2024. [Google Scholar]
- Chapman, J.C.; Alshowkan, M.; Qi, B.; Peters, N.A. Quantum digital signatures over entanglement-based deployed campus network. In Proceedings of the 2024 Conference on Lasers and Electro-Optics (CLEO: Fundamental Science 2024) (Paper FM3K.6), Charlotte, NC, USA, 5–10 May 2024; IEEE: Piscataway, NJ, USA; Optica Publishing Group: Washington, DC, USA, 2024. [Google Scholar] [CrossRef]
- Aktaş, A.; Yilmaz, I. High Dimensional Quantum Digital Signature Depending on Entanglement Swapping and Super-Dense Coding. Int. J. Inf. Secur. Sci. 2023, 12, 14–28. [Google Scholar] [CrossRef]
- Bonomi, A.H.; Mir, R.N. Forensic-Chain: Blockchain Based Digital Forensics Chain of Custody with PoC in Hyperledger Composer. Digit. Investig. 2019, 28, 44–55. [Google Scholar] [CrossRef]
- Khan, A.A.; Shaikh, A.A.; Laghari, A.A. IoT with Multimedia Investigation: A Secure Process of Digital Forensics Chain-of-Custody Using Blockchain Hyperledger Sawtooth. Arab. J. Sci. Eng. 2022, 48, 10173–10188. [Google Scholar] [CrossRef]
- Bonomi, S.; Casini, M.; Ciccotelli, C. B-CoC: A Blockchain-Based Chain of Custody for Evidences Management in Digital Forensics. arXiv 2018, arXiv:1807.10359. [Google Scholar]
- Li, M.; Lal, C.; Conti, M.; Hu, D. LEChain: A blockchain-based lawful evidence management scheme for digital forensics. Futur. Gener. Comput. Syst. 2021, 115, 406–420. [Google Scholar] [CrossRef]
- Ali, M.; Ismail, A.; Elgohary, H.; Darwish, S.; Mesbah, S. A Procedure for Tracing Chain of Custody in Digital Image Forensics: A Paradigm Based on Grey Hash and Blockchain. Symmetry 2022, 14, 334. [Google Scholar] [CrossRef]
- Ahammed, F.; Kadir, M.I. Entanglement and Teleportation in Quantum Key Distribution for Secure Wireless Systems. IET Quantum Commun. 2024, 5, 64–73. [Google Scholar] [CrossRef]
- Tagliavacche, N.; Borghi, M.; Guarda, G.; Ribezzo, D.; Liscidini, M.; Bacco, D.; Galli, M.; Bajoni, D. Frequency-bin entanglement-based quantum key distribution. NPJ Quantum Inf. 2025, 11, 60. [Google Scholar] [CrossRef]
- Shang, T.; Du, G.; Liu, J.-W. Opportunistic Quantum Network coding based on quantum teleportation. Quantum Inf. Process. 2015, 15, 1743–1763. [Google Scholar] [CrossRef]
- Curty, M.; Lewenstein, M.; Lütkenhaus, N. Entanglement as a precondition for secure quantum key distribution. Phys. Rev. Lett. 2004, 92, 217903. [Google Scholar] [CrossRef]
- K, B.; Siddhu, V.; Jagannathan, K. Classical Bandit Algorithms for Entanglement Detection in Parameterized Qubit States. arXiv 2024, arXiv:2406.19738. [Google Scholar] [CrossRef]
- Zhahir, A.A.; Mohd, S.M.; Shuhud, M.I.M.; Idrus, B.; Zainuddin, H.; Jan, N.M.; Wahiddin, M.R. Entanglement Detection: A Scoping Review. J. Adv. Res. Appl. Sci. Eng. Technol. 2024, 42, 209–220. Available online: https://semarakilmu.com.my/journals/index.php/applied_sciences_eng_tech/article/view/4184/4392 (accessed on 9 March 2025). [CrossRef]
- Chen, S. Hiding Secrets Using Quantum Entanglement. Physics 2022, 15, 116. Available online: https://physics.aps.org/articles/v15/116 (accessed on 9 March 2025). [CrossRef]
- Wang, K.; Song, Z.; Zhao, X.; Wang, Z.; Wang, X. Detecting and quantifying entanglement on near-term quantum devices. NPJ Quantum Inf. 2022, 8, 52. Available online: https://www.nature.com/articles/s41534-022-00556-w (accessed on 9 March 2025). [CrossRef]
- Tóth, G.; Gühne, O. Detection of Multipartite Entanglement with Two-Body Correlations. arXiv 2003, arXiv:quant-ph/0302028. [Google Scholar] [CrossRef]
- Steffen, M.; Ansmann, M.; Bialczak, R.C.; Katz, N.; Lucero, E.; McDermott, R.; Neeley, M.; Weig, E.M.; Cleland, A.N.; Martinis, J.M. Measurement of the Entanglement of Two Superconducting Qubits via State Tomography. Science 2006, 313, 1423–1425. Available online: https://www.science.org/doi/10.1126/science.1130886 (accessed on 9 March 2025). [CrossRef]
- Tabia, G.N.M.; Chen, K.-S.; Hsieh, C.-Y.; Yin, Y.-C.; Liang, Y.-C. Entanglement transitivity problems. NPJ Quantum Inf. 2022, 8, 98. Available online: https://www.nature.com/articles/s41534-022-00616-1 (accessed on 9 March 2025). [CrossRef]
- Hiesmayr, B.C. Free versus bound entanglement, a NP-hard problem tackled by machine learning. Sci. Rep. 2021, 11, 19739. Available online: https://www.ncbi.nlm.nih.gov/pmc/articles/PMC8492810/ (accessed on 9 March 2025). [CrossRef]
- Arbel, E.; Israel, N.; Belgorodsky, M.; Shafrir, Y.; Maslennikov, A.; Gandelman, S.P.; Rozenman, G.G. Optical Emulation of Quantum State Tomography and Bell Test—A Novel Undergraduate Experiment. Results Opt. 2025, 21, 100847. [Google Scholar] [CrossRef]
- César-Cuello, J.; Carnoto, I.; García-Muñoz, L.E.; Carpintero, G. Towards a lithium niobate photonic integrated circuit for Quantum Sensing Applications. Photonics 2024, 11, 239. [Google Scholar] [CrossRef]
- Azuma, K.; Tamaki, K.; Lo, H.-K. All-photonic quantum repeaters. Nat. Commun. 2015, 6, 1–7. [Google Scholar] [CrossRef]
- Dunjko, V.; Wallden, P.; Andersson, E. Quantum Digital Signatures without Quantum Memory. Phys. Rev. Lett. 2014, 112, 040502. [Google Scholar] [CrossRef]
- Wallden, P.; Dunjko, V.; Kent, A.; Andersson, E. Quantum digital signatures with quantum-key-distribution components. Phys. Rev. A 2015, 91, 042304. [Google Scholar] [CrossRef]
- Gisin, N.; Thew, R. Quantum communication. Nat. Photonics 2007, 1, 165–171. [Google Scholar] [CrossRef]
- Wang, J.-Y.; Yang, B.; Liao, S.-K.; Zhang, L.; Shen, Q.; Hu, X.-F.; Wu, J.-C.; Yang, S.-J.; Jiang, H.; Tang, Y.-L.; et al. Direct and full-scale experimental verifications towards ground–satellite quantum key distribution. Nat. Photonics 2013, 7, 387–393. [Google Scholar] [CrossRef]
- Lydersen, L.; Wiechers, C.; Wittmann, C.; Elser, D.; Skaar, J.; Makarov, V. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat. Photonics 2010, 4, 686–689. [Google Scholar] [CrossRef]
- Dieks, D. Communication by EPR devices. Phys. Lett. A 1982, 92, 271–272. [Google Scholar] [CrossRef]
- Deutsch, D. Quantum theory, the Church–Turing principle and the universal quantum computer. Proc. R. Soc. London Ser. A Math. Phys. Sci. 1985, 400, 97–117. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Smirne, A.; Egloff, D.; Diaz, M.G.; Plenio, M.B.; Huelga, S.F. Coherence and non-Markovianity in open quantum systems. Phys. Rev. A 2018, 98, 023856. [Google Scholar] [CrossRef]
- Rivas, Á.; Huelga, S.F.; Plenio, M.B. Entanglement and non-Markovianity of quantum evolutions. Phys. Rev. Lett. 2009, 103, 210401. [Google Scholar] [CrossRef]
- Piilo, J.; Harkonen, K.; Maniscalco, S.; Suominen, K. Non-Markovian quantum jumps. Phys. Rev. A 2010, 81, 042103. [Google Scholar] [CrossRef] [PubMed]

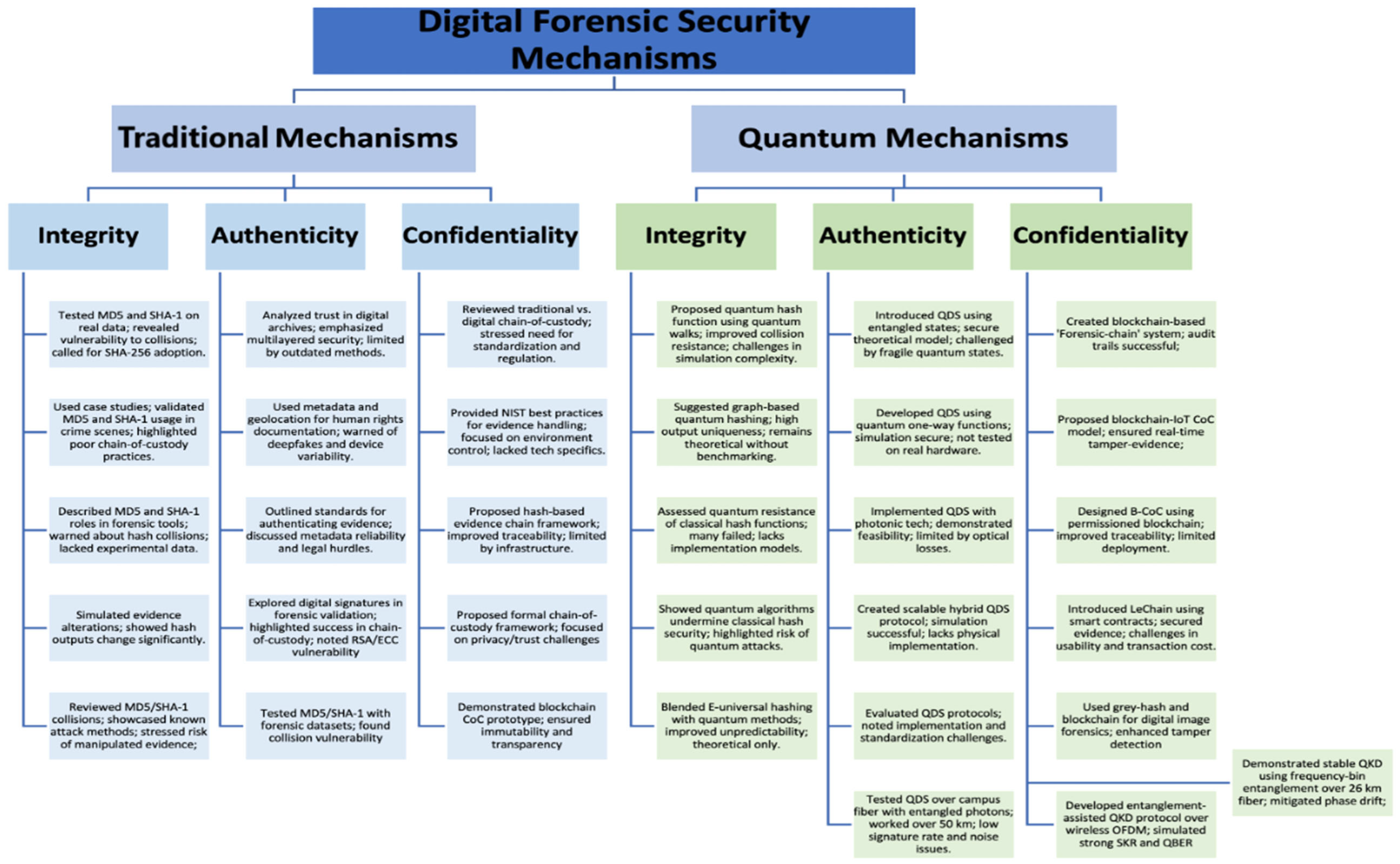
| Aspect | Traditional Digital Forensics | Quantum Digital Forensics |
|---|---|---|
| Integrity | Uses cryptographic hash functions (MD5, SHA-1, SHA-256); vulnerable to hash collisions and tampering; needs transition to secure algorithms. | Employs quantum hash functions leveraging entanglement and superposition; high resistance to tampering; current methods are theoretical or simulated. |
| Authenticity | Relies on digital signatures (RSA, ECC); vulnerable to quantum attacks (e.g., Shors algorithm); needs quantum-resistant methods. | Uses Quantum Digital Signatures (QDS) with entangled particles; ensures unforgeability and non-repudiation; limited by hardware and implementation complexity. |
| Confidentiality | Achieved through AES encryption and secure containers; susceptible to future quantum decryption; lacks blockchain integration. | Uses Quantum Key Distribution (QKD), quantum watermarking, and quantum audit trails; ensures secure key exchange and tamper-evident tracking; challenges in implementation, synchronization, and infrastructure. |
| Traditional Digital Forensic Mechanisms | Quantum Digital Forensic Mechanisms | ||||
|---|---|---|---|---|---|
| Key Aspect | Author | Contribution Summary | Key Aspect | Author | Contribution Summary |
| Integrity | V. Schmitt and J. Jordaan [11] | Tested MD5 and SHA-1 on real data; revealed vulnerability to collisions; called for SHA-256 adoption. | Integrity | P. Hou et al. [27] | Proposed quantum hash function using quantum walks; improved collision resistance; challenges in simulation complexity. |
| K. Kumar and S. Singh [13] | Used case studies; validated MD5 and SHA-1 usage in crime scenes; highlighted poor chain-of-custody practices. | Ziatdinov, M. [28] | Suggested graph-based quantum hashing; high output uniqueness; remains theoretical without benchmarking. | ||
| SalvationDATA [14] | Described MD5 and SHA-1 roles in forensic tools; warned about hash collisions; lacked experimental data. | B. Hamlin & F. Song [29] | Assessed quantum resistance of classical hash functions; many failed; lacks implementation models. | ||
| A. Thakar et al. [10] | Simulated evidence alterations; showed hash outputs change significantly; emphasized usefulness for investigator training; lacked discussion of stronger hash alternatives. | J. C. Garcia-Escartin et al. [30] | Showed quantum algorithms undermine classical hash security; highlighted risk of quantum attacks. | ||
| F. Ablayev & M. Ablayev [31] | Blended E-universal hashing with quantum methods; improved unpredictability; theoretical only. | ||||
| Rasjid Z.E. et al. [12] | Reviewed MD5/SHA-1 collisions; showcased known attack methods; stressed risk of manipulated evidence; lacked experimental validation; urged updates in forensic standards. | R. Jozsa and N. Linden [32] | Explored entanglement’s role in computational speed-up; found entanglement essential in pure-state algorithms; limited to theoretical models and pure states. | ||
| Authenticity | D. Gottesman & I. Chuang [34] | Introduced QDS using entangled states; secure theoretical model; challenged by fragile quantum states. | |||
| Authenticity | C. Lynch [18] | Analyzed trust in digital archives; emphasized multilayered security; limited by outdated methods. | X. Lu & D.-G. Feng [35] | Developed QDS using quantum one-way functions; simulation secure; not tested on real hardware. | |
| Ulbricht et al. [19] | Used metadata and geolocation for human rights documentation; warned of deep fakes and device variability. | P. J. Clarke et al. [33] | Implemented QDS with photonic tech; demonstrated feasibility; limited by toptical losses. | ||
| P. Grimm and G. P. Joseph [17] | Outlined standards for authenticating evidence; discussed metadata reliability and legal hurdles. | M. I. Garcia Cid et al. [36] | Created scalable hybrid QDS protocol; simulation successful; lacks physical implementation. | ||
| Dogra, K. [20] | Explored digital signatures in forensic validation; highlighted success in chain-of-custody; noted RSA/ECC vulnerability; promoted quantum-resistant protocols; limited by cryptographic dependency. | H. Duan [37] | Evaluated QDS protocols; noted implementation and standardization challenges. | ||
| J. C. Chapman et al. [38] | Tested QDS over campus fiber with entangled photons; worked over 50 km; low signature rate and noise issues. | ||||
| A.Aktaş & I. Yılmaz [39] | Proposed high-dimensional QDS using entanglement swapping and super-dense coding; improved security; remains theoretical without implementation. | ||||
| V. Schmitt and J. Jordaan [11] | Tested MD5/SHA-1 with forensic datasets; found collision vulnerability; warned about outdated tool use; called for updates; did not include SHA-256. | Confidentiality | A. H. Lone & R. N. Mir [40] | Created blockchain-based ‘Forensic-chain’ system; audit trails successful; challenged by training and legal fit. | |
| A. A. Khan et al. [41] | Proposed blockchain-IoT CoC model; ensured real-time tamper-evidence; issues with multimedia and privacy. | ||||
| Confidentiality | T. D’Anna et al. [25] | Reviewed traditional vs. digital chain-of-custody; stressed need for standardization and regulation. | S. Bonomi et al. [42] | Designed B-CoC using permissioned blockchain; improved traceability; limited deployment. | |
| B. Guttman et al. [23] | Provided NIST best practices for evidence handling; focused on environment control; lacked tech specifics. | M. Li et al. [43] | Introduced LeChain using smart contracts; secured evidence; challenges in usability and transaction cost. | ||
| D. Banwani and Y. Kalra [22] | Proposed hash-based evidence chain framework; improved traceability; limited by infrastructure. | M. Ali et al. [44] | Used grey-hash and blockchain for digital image forensics; enhanced tamper detection; computationally intensive. | ||
| S. Nath et al. [21] | Proposed formal chain-of-custody framework; focused on privacy/trust challenges; emphasized policy adaptability; limited by complexity in heterogeneous systems. | Ahammed and Kadir [45] | Developed entanglement-assisted QKD protocol over wireless OFDM; simulated strong SKR and QBER; limited by decoherence, memory, and hardware feasibility. | ||
| Borghi et al. [46] | Demonstrated stable QKD using frequency-bin entanglement over 26 km fiber; mitigated phase drift; constrained by complexity and photon source limitations. | ||||
| J. Machhi et al. [24] | Demonstrated blockchain CoC prototype; ensured immutability and transparency; noted tool integration issues and latency; limited by cost and adoption barriers. | Shang, T. et al. [47] | Suggested intercept-resistant MEQKD; modeled errors from eavesdropping; showed robustness in theory; limited by reliance on ideal quantum hardware. | ||
| Curty, M. et al. [48] | Proved entanglement is necessary for secure QKD; used entanglement witnesses in 4- and 6-state protocols; theoretical only, lacking noise validation. | ||||
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alhazmi, S.; Elleithy, K.; Elleithy, A. Digital Forensics of Quantum Computing: The Role of Quantum Entanglement in Digital Forensics—Current Status and Future Directions. Quantum Rep. 2025, 7, 44. https://doi.org/10.3390/quantum7040044
Alhazmi S, Elleithy K, Elleithy A. Digital Forensics of Quantum Computing: The Role of Quantum Entanglement in Digital Forensics—Current Status and Future Directions. Quantum Reports. 2025; 7(4):44. https://doi.org/10.3390/quantum7040044
Chicago/Turabian StyleAlhazmi, Shatha, Khaled Elleithy, and Abdelrahman Elleithy. 2025. "Digital Forensics of Quantum Computing: The Role of Quantum Entanglement in Digital Forensics—Current Status and Future Directions" Quantum Reports 7, no. 4: 44. https://doi.org/10.3390/quantum7040044
APA StyleAlhazmi, S., Elleithy, K., & Elleithy, A. (2025). Digital Forensics of Quantum Computing: The Role of Quantum Entanglement in Digital Forensics—Current Status and Future Directions. Quantum Reports, 7(4), 44. https://doi.org/10.3390/quantum7040044






