1. Introduction
Recent advances towards the realization of practical quantum computers with a large number of qbits, and hence the looming threat of fast implementations of Shor’s and Grover’s quantum algorithms, have spurned the research and security communities into looking for secure replacements to parts of the modern computer security infrastructure which rely on soon to be vulnerable mathematical problems (prime factorization and discrete logarithms). Two main avenues have been identified to prevent this issue, namely Post-Quantum Cryptography (PQC), and Quantum-secured Communications via Quantum Key Distribution (QKD); each presents advantages and disadvantages.
Briefly, PQC comprises new mathematical techniques to replace the vulnerable ones, which are believed to be secure even against a quantum computer. While it promises to be a practical drop-in replacement for outgoing crypto, there is, unfortunately, no guarantee that its mathematical underpinnings are indeed secure.
In contrast, QKD is an unwieldy physical solution to the problem of sharing random bit strings (i.e., secret keys). It comprises a set of protocols and devices (some, notably, already commercially available, e.g., [
1]) that exploit the weird properties of quantum mechanics to achieve the exchange of a random bit stream between two communicating parties, with an arbitrarily low upper bound on the probability that an adversary silently eavesdropped the communication, making it an ideal choice to generate key material for cryptography (especially session keys), which can then be used with symmetric ciphers, which are known to be relatively unaffected by quantum computing, or even One-Time Pads (OTPs) for short, provably secure communications. The key advantage of QKD over PQC is that it can be mathematically proven to be secure, even independently of the security of the QKD devices (via Measurement Device Independent QKD, or MDI-QKD [
2]). On the other hand, this reliance on physical properties, and hence specialized hardware with many limitations despite significant advances [
3], makes QKD impractical in the vast majority of use cases.
In this paper we focus on QKD, imagining how to use it to securely encrypt the data crossing large core transport optical networks, the kind of networks that cross countries, continents and oceans to interconnect the world. While metro-sized experimental QKD networks already exist [
4], the reach limitations of current QKD devices have so far discouraged the adoption of such technology for nation- and continent-wide networks. To cross such distances with high capacity, high reliability and low latency, there is only one economically viable technology: optical communications in fibers. And while we realize that in-network encryption is no guarantee of end-to-end privacy of security, the ease with which traffic can be spoofed from a fiber, even from underwater cables, has led operators to begin to consider how to secure their networks (to protect control traffic vital to their functioning, if nothing else). With the speed of modern transceivers exceeding 400 Gb/s per connection, and that of QKD in the order of Mb/s, a direct application of information-theoretically secure OTPs is clearly out of the question, unless used only to secure the small subset of control traffic. Outside of that, QKD could be used for continuous key regeneration, which for AES-256 operating in hardware at line rate may or may not be a concern even at these high data transmission rates, or it could even be a new value-added service for telecom operators, replacing human secure couriers with faster delivery and better guarantees of key secrecy [
5].
As mentioned, QKD has several limitations, chief among which are relatively low key generation rates (in the order of 1 Mb/s for distances <100 Km), and short reach (100–150 Km, twice that with schemes where the measuring device is in the middle like MDI-QKD), owing to relatively weak laser pulses, fiber losses and environmental noise. To overcome the latter limitation, which is vital to successfully deploy this technology in geographically wide networks, two possible solutions have been identified: satellite QKD, where the atmosphere-less space between satellites offers a much better propagation medium than terrestrial fibers, but which suffers from significant issues in ground-to-satellite links (e.g., loss-of-signal during bad weather [
6]), and the use of repeaters to regenerate the quantum signal. Regarding the latter, one possibility touted in research papers is to use Quantum Repeaters [
7], which would guarantee the security of the key material even as it passes through intermediate sites. Unfortunately, no such device has, so far, been demonstrated to work in field conditions.
In the absence of quantum repeaters, we are currently limited to ‘trusted’ repeaters, i.e., nodes (of degree two) where one QKD instance is terminated and another initiated, with classical crypto-based security in the middle. Note that having to monitor a few sites instead of hundreds of kilometers of underground fibers is already a vast security improvement over the current situation, and the nodes themselves need not expose clear-text key material if they use OTPs to simply re-encrypt an arbitrary bit string (the key) with a local key that is the XOR of the link-local QKD keys produced by its two sides [
8]. Since the key generation rate decays with distance, the next obvious question pertains to where to place how many repeaters on any particular link to achieve sufficient key generation at optimal, i.e., minimal cost. This has already been studied [
9], but due to practical constraints, such as the need for power, shelf space and physical security at repeater nodes, it also has a holistic answer: at least for existing networks, we would expect repeaters to be co-located with existing amplification stations, with the overall effectiveness of the chain being determined largely by its least efficient span (the longest, barring other sources of noise).
So we know how to organize a chain of QKD repeaters to traverse a long link. Which links in a network should we augment with such repeaters in order to connect all nodes that need secure communications? Ref. [
9] provides some answers rooted in geometric modeling for simple topologies, which however are quite hard to apply directly to real networks. Fortunately, there exists a case where the answer is indeed quite simple: if the required key rate is very low, much lower than that generated by even the least effective QKD chain in the topology, then the set of links to be augmented is simply the minimum spanning tree that connects all the required nodes on the topology graph, where the link weights represent the cost to deploy a QKD chain on those links.
If, instead, the required key rate is comparable or higher than that of the chains, i.e., multiple parallel chains might be required, the answer is slightly more complicated, as it may, in some instances, be cheaper to install fewer but more efficient chains on one link instead of more on another.
Repeater chains, however, do not prevent an attacker that manages to compromise a node from eventually reading the messages passing through it, and hence discovering the keys being passed through that node. A relatively simple way to foil this attack is to split the key over messages sent over multiple, disjoint paths, forcing an attacker to compromise at least that many nodes to recover a whole key, which is the idea we exploit in this work. A more thorough theoretical justification for this idea can be found in [
10], where multiple parallel trusted repeaters are traversed in an information-theoretic secure way by distributing the key via network coding. An additional benefit of a multi-path approach is that it also ameliorates the service disruption caused by fiber cuts, or even targeted attacks against the QKD infrastructure. QKD exchanges are delicate processes, quite vulnerable to ambient noise; therefore, an attacker can simply inject random noise in a fiber used for QKD to all but interrupt the process, which in turn forces the remote security endpoints to stretch their use of existing keys or rely on less secure classical key refresh mechanisms. With the proposed approach, the impact of such failures or attacks would be reduced at least proportionally to the number of available parallel paths.
In this paper we expand on a previous answer [
11] to the question: if we were to deploy QKD in a terrestrial core transport network tomorrow, how could we do it effectively? That is, if the threat of quantum computers and/or the emergence of some new attack on Public Key Infrastructure forced us to deploy QKD technology in the short term, how could we do it in a manner that is both economical and guarantees adequate security in the presence of (classical) repeater sites? Which links should we secure, and with how many QKD chains each? Given multiple QKD paths between nodes, which routes should every QKD session follow?
While we hope to never actually need to, to answer these questions we formulate optimization models that, given a medium-large distance fiber plant graph and a matrix of QKD traffic demands, minimize the use of costly QKD devices and compute the routes taken by the key material over the resulting QKD-enabled sub-graph such that all demands are satisfied and utilize a desired (input) number of disjoint paths. Notably, the contours of our questions prevent us to assume the existence of unproven technology: we have to rely only on the technology available today, i.e., BB84-like [
12] point to point devices and trusted (not quantum) repeaters. We present two answers to these questions, in the form of two Mixed-Integer Linear Programming (MILP) formulations. The first is an improvement over our previous solution [
11] in terms of execution time, due to using many fewer integer variables; the second new model accounts for the fact that key distribution need not follow the direction of the traffic, and, despite being significantly more complex and hence slower, can produce better (i.e., cheaper) QKD configurations which may well be significant if the cost of devices remains high.
We present these formulations, and our assumptions in their design, in
Section 2, and we quantify their performance advantages compared to our previous proposal, on both random and realistic topologies, in
Section 3, before summarizing the work, its findings and potential future extensions in
Section 4.
2. MILP Formulations for QKD Subnetwork Design
In this section, we present two Mixed-Integer Linear Programming (MILP) formulations to solve the problem of finding the optimal placement of QKD devices, and the routes taken by the end-to-end QKD exchanges. Both formulations take the following items as input:
A directed graph , representing an existing or planned fiber plant.
An integer N representing the desired path multiplicity, i.e., the minimum number of parallel disjoint paths that each end-to-end QKD session must support in order to offer protection from attackers compromising some repeater nodes.
A set of directed demands , and a function (or table of weights) specifying, for each demand, the requested key bit-rate between the two terminal nodes of the demand.
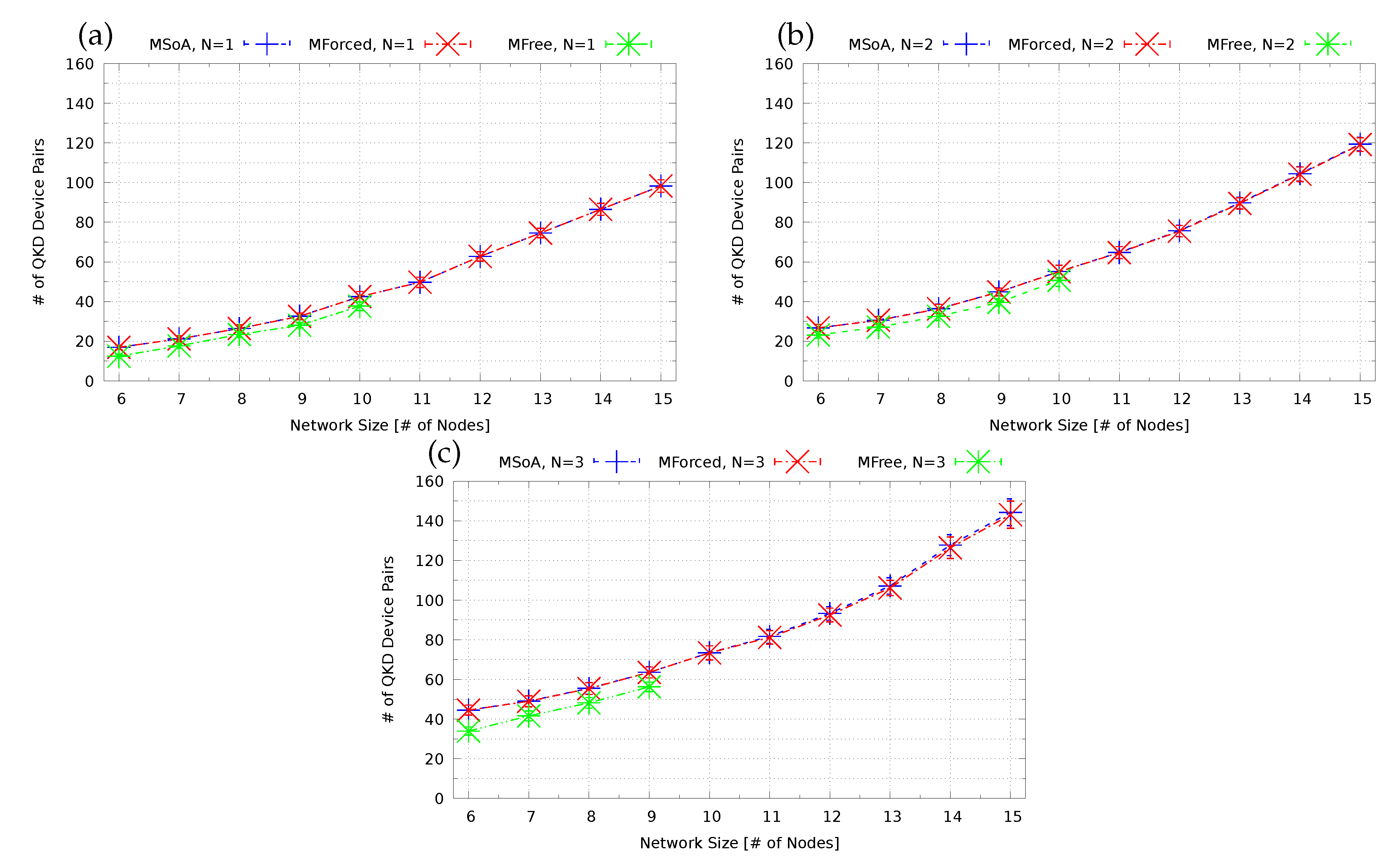
A function (or table of weights) mapping each edge to the number of devices needed to realize a QKD chain on that edge; in practice, given the current reach of QKD devices, they are likely to be co-located with optical line amplifiers serving the data fibers, which translates to somewhere in the neighborhood of 80–100 Km; we assume that the best placement of QKD repeater nodes on a link, e.g., matching the location of amplification sites, has been pre-computed, and encoded in this function.
A function (or table of weights) mapping each edge to the key bit-rate provided by a QKD chain established on that edge, pre-computed under the same distance considerations used to compute L.
We summarized this and other notations in
Table 1. Note that the
L and
Q functions encode the potentially complex inter-relation between number (i.e., cost) and placement of QKD devices on a particular link, and the corresponding key generation rate. Holistically, assuming uniform fiber quality and ambient noise, the bottleneck with respect to capacity is going to be the longest span between QKD devices. This implies that denser chains (with shorter links), while more costly, would exhibit a higher key rate. The optimal placement can be computed, if the required key rate is known, as in [
9]. For our models, which actually need to decide the key rate, we assume that practical considerations take precedence and so the QKD carrying capacity of each link can be computed in advance. The joint optimization of internal link QKD placement and network-wide QKD routes is an interesting problem left for future research on this subject.
2.1. Forced Direction MILP Model
The first formulation we discuss, an improvement over the one we presented in [
11] and which we named Forced Direction (MForced) model, contains two types of variables: (i)
, continuous variables representing the amount of the
demand passing through the edge
, and (ii)
, integer variables counting the number of parallel QKD chains deployed on edge
. The complete formulation is then given by the following problem:
The objective, expressed in (
1), is to minimize the number of parallel QKD chains traversing each edge, as that implies minimizing the capital expenditure in equipment. Each link-chain counter is weighted by the number of devices required to actually traverse that link (based on link length, reach limitation and trade-off between reach and key generation rate of QKD). Constraints (
2) and (
3) (where
) connect the two different of decision variables and linearise the ceiling relation (
12):
I.e., the number of chains on a link must have sufficient capacity to carry all the QKD traffic insisting on said link. Constraint (
4) expresses the flow conservation condition, i.e., as much non-locally-terminated QKD traffic must exit a node as it enters it. Constraints (
5) and (
6) ensure that sufficient key material exits the source node and enters the destination one to satisfy the rate required between those two nodes, respectively. Constraint (
7) limits the quantity of QKD traffic from each demand crossing each edge of the network to be at most
; this enforces the instantiation of at least
N disjoint QKD paths to serve each demand, but still allows multiple paths serving different demands to share the same QKD devices. Note that we could rewrite constraint (
7) as an equality to enforce the instantiation of exactly
N disjoint QKD paths, but this comes at the price of additional
constraints, which increase the computation time [
13]; furthermore, since we are minimizing the cost of deployed chains, in practice the computed solutions almost never contain more than the strictly required number of QKD paths (and if they did, it would be at no additional cost). Finally, constraints (
8) and (
9) prevent the instantiation of short loops around the source and destination nodes, forcing the model to actually select an entire path connecting them.
The size of the resulting problem instances is dominated by the number of
variables, which is upper-bounded by
, and the number of constraints that is
. These sizes are large but still manageable for design problems (which afford significant running time), especially with modern, efficient solvers like Gurobi [
14], which we used to obtain our results.
Note that, once a solution is found, it is trivial to extract the routes followed by each demand sub-path by examining the values of the corresponding variables.
Compared to our previous model in [
11], this one is similar (and indeed computes the same optimal solutions) but forgoes the need for a large number of binary variables, which ought to result in non-trivial execution speed gains.
2.2. Free Direction MILP Model
A careful observer may have noticed that the MILP problem formulated above considers demands to be directed, i.e., key material generated to protect traffic from s to d is completely unrelated to that generated for the protection of traffic from d to s. Clearly, this is not really the case in real networks, although the two directions may exhibit large differences in traffic load, and hence required key rate. For our purposes, this limitation entails that, in the MForced model, we need to set up two separate directed paths between each couple of communicating nodes (as communication is in general bidirectional, if asymmetric). But, based on the observation above, we only need one QKD path between each two nodes, in whatever direction, to establish secret key material between them. This could lead to better utilization of QKD devices, and hence cheaper deployments.
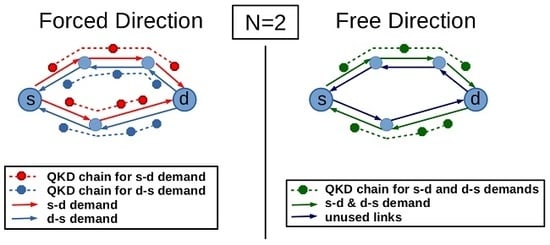
The idea is graphically represented in
Figure 1, showing the difference between how MForced and a model exploiting this observation would behave on a simple example. For a required QKD path multiplicity
and two demands, one from
s to
d and the other from
d to
s, MForced establishes two QKD chains per direction for a total of four (12 QKD devices), while the other model could make do with just two (only six devices), running the deployed QKD devices hotter.
This observation led us to develop the Free Direction (MFree) model, which, in addition to those already in MForced, relies on a third type of variable: binary variables
encoding the direction in which the QKD session is ‘flowing’ (practically, in which of the fiber plant’s fiber, which is generally directed, the QKD photons are traveling). Furthermore, this model has an additional pre-processing step that sums the directed demands in
D for each node couple. The whole model is represented by the following problem (constraints in bold are new):
The objective, expressed in (
13), is identical to that of the MForced formulation, as are constraints (
14)–(
16) and (
19). The significant differences are encoded in constraints (
17) and (
18), which now ensure that there is sufficient key material entering or exiting the terminal nodes of each demand (without caring for which direction it is traveling in, or whether it is split among both), and in constraints (
20) and (
21), which perform a similar function to constraints (
8) and (
9) in MForced, by linearising the relation (
25):
In words, the sum of key material traveling, in either direction, through the neighbours of the source node of a demand must be sufficient to satisfy said demand. In conjunction with constraint (
16), this extends to all non-terminal nodes of a demand. This trick allows us to more efficiently use the QKD devices we choose to deploy, as it removes the constraint of directionality, leading to a lower number of required QKD devices, as evidenced in
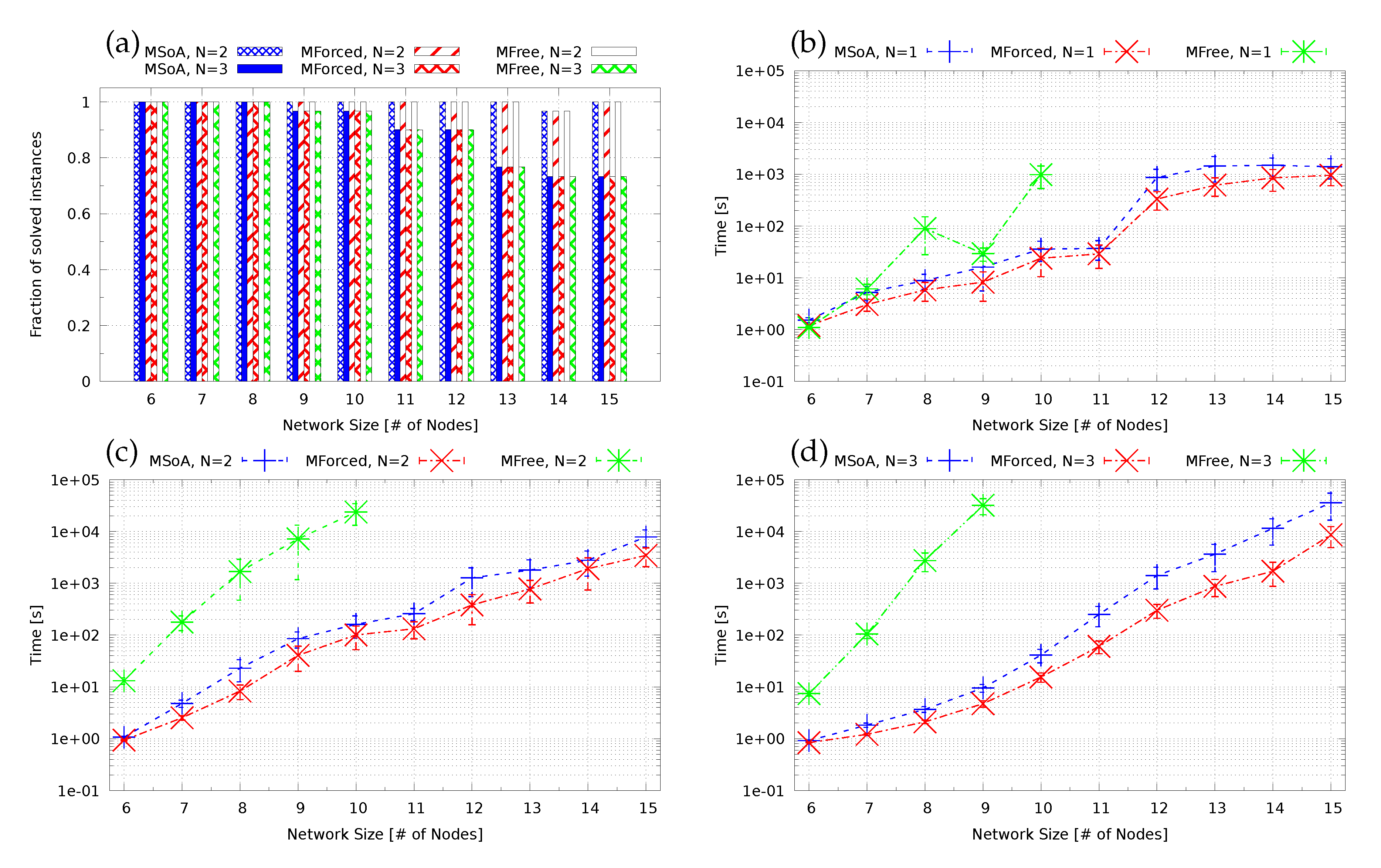
Section 3.
M needs to be a large enough number for the relationships to hold, in this case
.
As before, also in this formulation the problem size is dominated by the number of
variables,
, and the number of constraints that is
. Time-wise, however, solving this model requires dealing with a large (
) number of binary variables
, whose value strongly impacts the feasible assignments to the remaining families of variables. As solving integer (or binary) linear problems is much less efficient that solving continuous ones [
15], this has a large impact on computation time, as also shown in
Section 3. Nonetheless, the advantages in terms of the number of required (expensive, in the order of tens of thousands of Euros) QKD devices can more than justify the investment of additional design (computational) resources.