Heterogeneous Network Architecture for Integration of AI and Quantum Optics by Means of Multiple-Valued Logic
Abstract
1. Introduction
1.1. Actual Problems for Communication Networks
1.2. Quantum Data Protection Methods for CN
1.3. Achievements in the Realization of AI Methods for CN
1.4. Classical Schemes for Secured Robotics
- -
- mobile agents to hosts,
- -
- the Internet (denial of service, damage, event triggered, compound, and user attacks),
- -
- altering the logging system and agent code, data, and configuration,
- -
- fake agent and fake service.
- -
- from hosts to agents,
- -
- from agents to agents,
- -
- from users to agents,
- -
- for communication among agents, including identification and authentication, unauthorized access, message injection, knowledge injection, and other malicious impacts.
1.5. MVL-Based Schemes for Secured Coding of Data
1.6. Actual Methods of Data Clustering
1.7. Fuzzy Logic and Approximate Clustering
- -
- supposes an a priori known number of clusters to be used,
- -
- is sensitive to the cluster centers’ initialization phase, and
- -
- is also sensitive to noise and outliers.
1.8. The Aim of the Presented Work
- -
- The level of security for CN should be increased further not only by the development of various QKD schemes [7,8,9], but also by AI methods of data leakage protection and by the adaptation of a one-time-pad secret coding for different levels of data processing in the agent [67,75]. As possible data leakages due to malicious staff members create threats both for traditional and quantum network subsystems, AI methods should be especially focused on the search, analysis, and recognition of random and suspicious events, which are described in the multi-parametrical space of characteristic features of objects and events. New data clustering methods are needed to be designed both for precise and approximate models, as well as for categorical and linguistic data structures. Future CN should be enhanced by various authentication and verification schemes [75,77].
- -
- Computer vision, speech, and acoustic signals processing are the critical technologies for the knowledge exchange, monitoring of the scene, and for controlling an agent′s motivation, goal setting, planning, evaluation of resources, and objects positioning. That is why such image processing methods as data aggregation, clustering, noise filtering, contour extraction, and the analysis of the knowledge structure are very actual for robotic subsystems in global CN [58].
- -
- Peer-to-peer network segments formed by intellectual agents in global CN should be supported by the design of protocols for directly targeted and problem-oriented communications between agents. The traditional address space for future networks is to be complemented by a multi-parametrical space for the targeted addressing of MASs and for multi-parametrical modeling, which is described by the special language (protocol) for direct peer-to-peer communications. Seamless computing in global CN [65] is to be provided for different hardware platforms, and the integration of robots should not create obstacles for routine Internet protocols.
- -
- Learning methods [27], imitating the behavior of qualified men, are actual for the modeling of an agent. As of now there are no universal methods of learning that are good for all possible tasks; thus, heterogeneous models can be applied to form necessary combinations of algorithms. Methods of learning should support objects and events aggregation [35] for large databases and should provide control of possible voids and data dubbing in an agent’s knowledge base.
- -
- -
- enlarge the choice of data clustering and classification methods for various types of data,
- -
- are adapted for the integration of additional means of secret coding for agents and MAS, supplementing QKD and traditional network means of data protection,
- -
- provide new schemes for seamless computing and communication languages for global networks,
- -
- can integrate multiagent concepts, fuzzy models, and other AI methods with quantum schemes in global CN.
2. Basic Methods of Multiple-Valued Logic for Data Processing
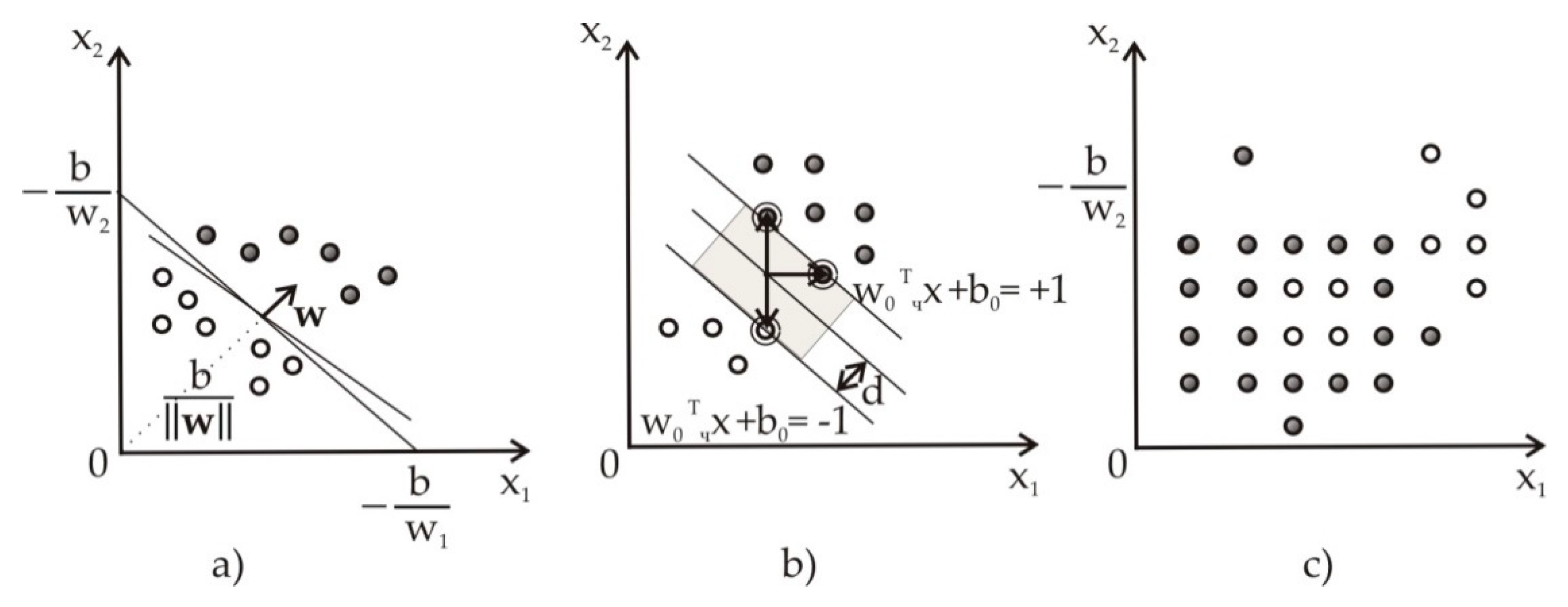
2.1. Types of Logic Models and the Specifity of Multiple-Valued Allen–Givone Algebra
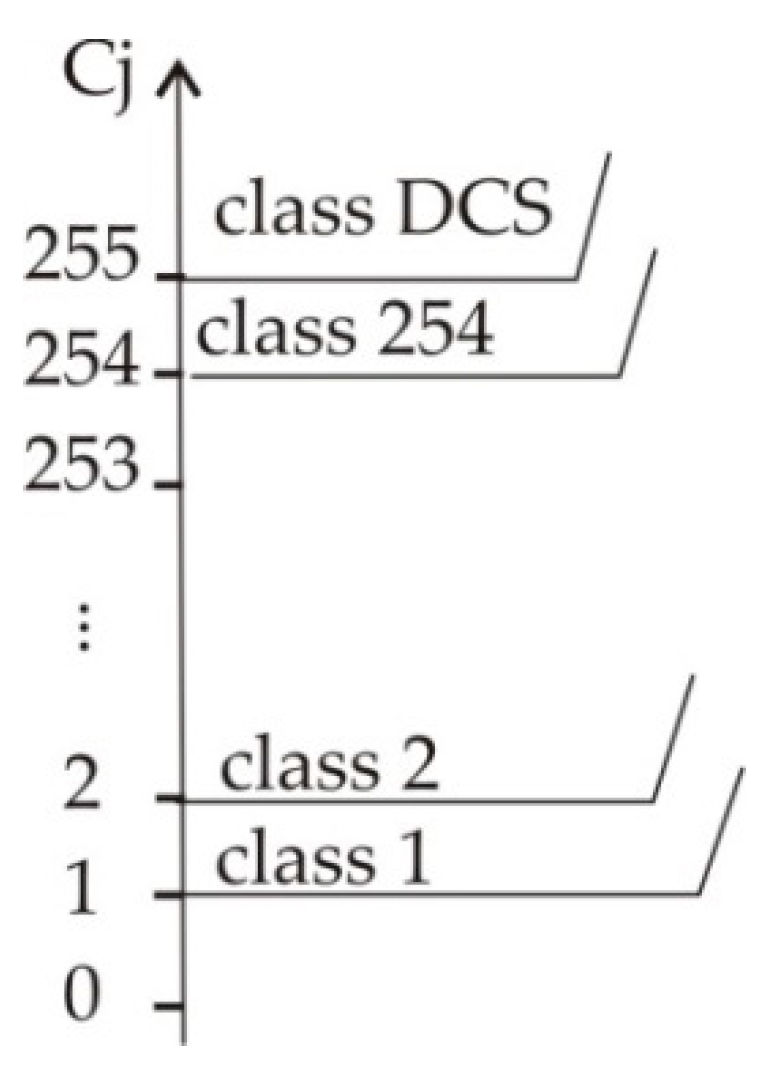
2.2. Definition of AGA and its Main Properties
- -
- are the logical constants, i.e., ∈ L = {0,1,…, k − 1}
- -
- binary operator Min() marked (*) acts on a pair of logic variables and , choosing the minimal one,
- -
- binary operator Max() marked (+) acts on a pair of logic variables and , choosing the maximal one,
- -
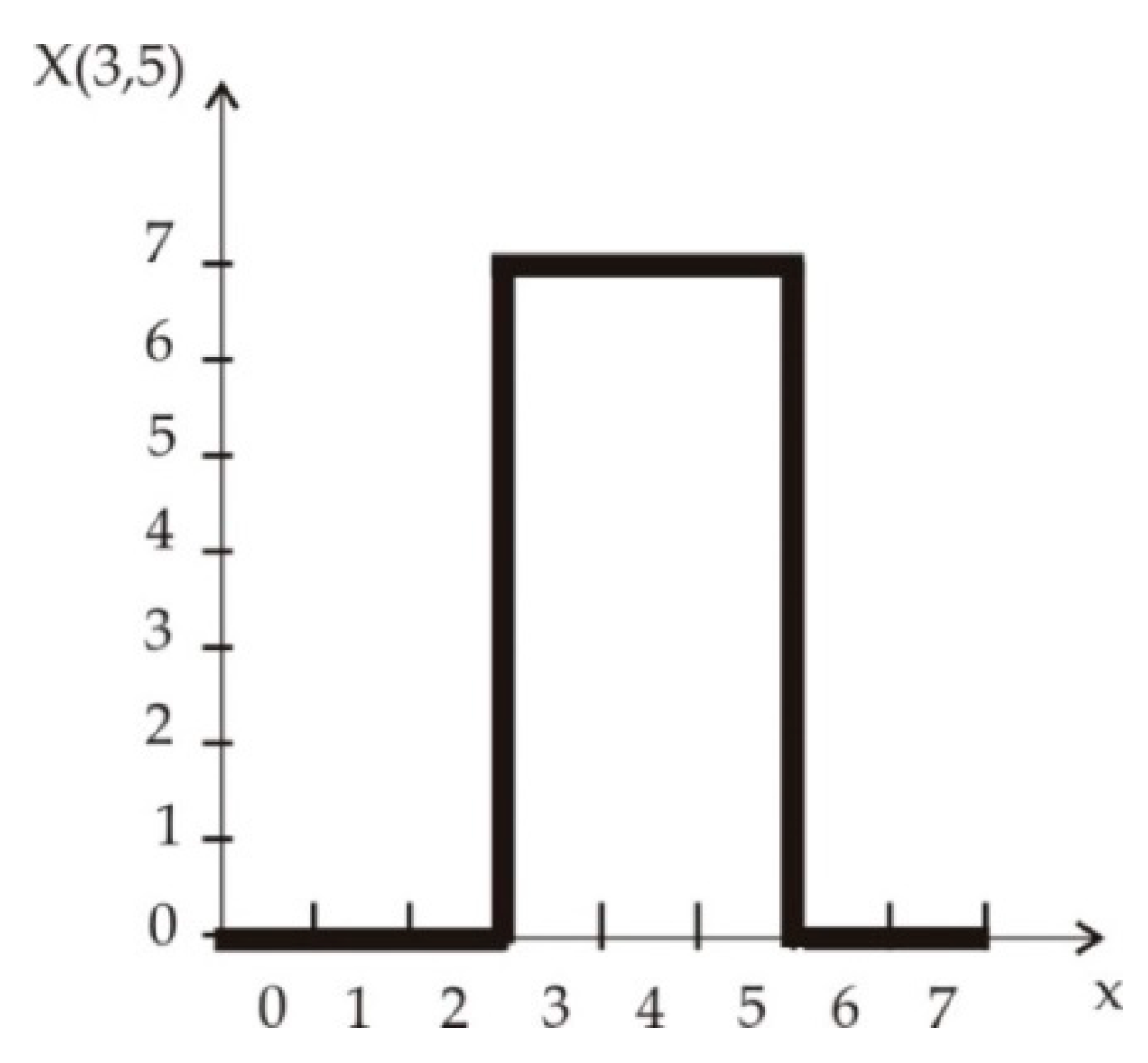
- unary operator is called Literal and acts on one logic variable , where the result is given by expression (2):where for any always and
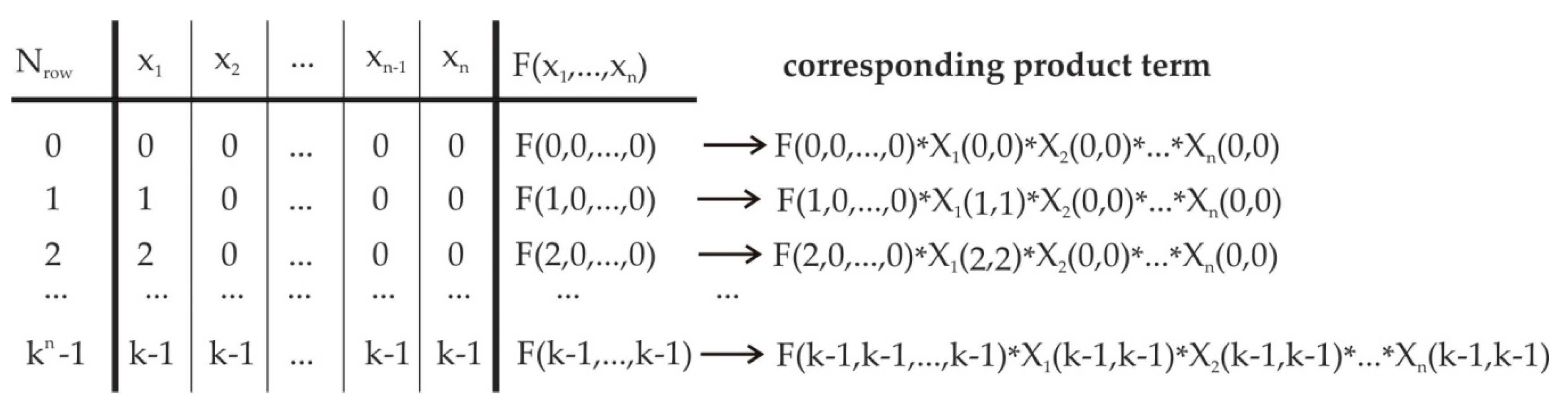
2.3. Multiparametrical Space Dimension for MVL Function
2.4. The Minimization Method for AGA Functions
- for,inequalitiesand7 are true,
- for, we have, 41 and
- for, expressions are true,.
- As in the notation, the first product term is included into the second one and can be deleted, thus it was crossed out.
- for,
- for all.
- Consensus , taken in does not exist as there are no such and , for which and rectangle markers do not intersect.
- Consensus taken in exists, as there are such and that .
- Form a numbered list of product terms for the given truth table (or the logic expression). (Note. Principally, the order does not influence the final result, but not completing the minimization procedure enlarges the computing time).
- Replace all vacuous Literals by Literals .
- Remove all subsuming product terms in the list, using expression (4) for all possible pairs of product terms.
- Add one or several DCS, substituting instead of undefined rows in the truth table, add newly formed product terms to the list, and assign consecutive numbers to product terms.
- Repeat the search for subsuming product terms, delete such terms from the list, and assign the numbers in the obtained list.
- Compute consensus by expression (5) sequentially for all input variables and product terms; if the obtained product terms do not subsume other terms, add them to the bottom of the list.
- Find all the prime implicants that do not subsume more other terms.
- Delete all literals of the form in every product term (since they are equal to k − 1 by definition).
| 1 | 5*X1(3,3)*X2(3,3)*X3(3,3) |
| 2 | 5*X1(3,3)*X2(4,4)*X3(3,3) |
| 3 | 11* X1(1,1)*X2(1,1)*X3(3,3) |
| 4 | 11*X1(1,1)*X2(2,2)*X3(3,3) |
| 5 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 6 | 75*X1(2,2)*X2(0,0)*X3(3,3) |
| 7 | 75*X1(2,2)*X2(1,1)*X3(3,3) |
| 8 | 75*X1(2,2)*X2(2,2)*X3(3,3) |
| 9 | 75*X1(2,2)*X2(3,3)*X3(3,3). |
- consensus 1*12 does not exist,
- consensus 1*22 = 5*X1(3,3)*X2(3,3)*X3(3,3) *2 5*X1(3,3)*X2(4,4)*X3(3,3) = 5*X1(3,3)*X2(3,4)*X3(3,3), so that
| 1*22 is added as term 10 | terms 1 and 2 subsume 10 | terms 1 and 2 are deleted | |||
| 1 | 5*X1(3,3)*X2(3,3)*X3(3,3) | 1 | 1 | 11*X1(1,1)*X2(1,1)* X3(3,3) | |
| 2 | 5*X1(3,3)*X2(4,4)*X3(3,3) | 2 | 2 | 11*X1(1,1)*X2(2,2)*X3(3,3) | |
| 3 | 11*X1(1,1)*X2(1,1)*X3(3,3) | 3 | 11*X1(1,1)*X2(1,1)*X3(3,3) | 3 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 4 | 11*X1(1,1)*X2(2,2)*X3(3,3) | 4 | 11*X1(1,1)*X2(2,2)*X3(3,3) | 4 | 75*X1(2,2)*X2(0,0)*X3(3,3) |
| 5 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 5 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 5 | 75*X1(2,2)*X2(1,1)*X3(3,3) |
| 6 | 75*X1(2,2)*X2(0,0)*X3(3,3) | 6 | 75*X1(2,2)*X2(0,0)*X3(3,3) | 6 | 75*X1(2,2)*X2(2,2)*X3(3,3) |
| 7 | 75*X1(2,2)*X2(1,1)*X3(3,3) | 7 | 75*X1(2,2)*X2(1,1)*X3(3,3) | 7 | 75*X1(2,2)* X2(3,3)*X3(3,3) |
| 8 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 8 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 8 | 5*X1(3,3)* X2(3,4)*X3(3,3). |
| 9 | 75*X1(2,2)*X2(3,3)*X3(3,3) | 9 | 75*X1(2,2)*X2(3,3)*X3(3,3) | ||
| 10 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 10 | 5*X1(3,3)* X2(3,4)*X3(3,3) |
- A new search for the consensus provides:
- consensus 1*12 does not exist,
- consensus 1*22 = 11* X1 (1,1)*x2(1,1)*x3(3,3) *1 11* X1 (1,1) * x2(2,2) x3(3,3) = 11* X1 (1,1)*X2(1,2)*X3(3,3),
| 1*22 is added as term 9 | terms 1 and 2 subsume 9 | terms 1 and 2 are deleted | |||
| 1 | 11*X1(1,1) *X2(1,1)*X3(3,3) | 1 | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | |
| 2 | 11*X1(1,1)*X2(2,2)*X3(3,3) | 2 | 2 | 75*X1(2,2)*X2(0,0)*X3(3,3) | |
| 3 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 3 | 11*X1(3,3) *X2(2,2)*X3(3,3) | 3 | 75*X1(2,2)*X2(1,1)*X3 (3,3) |
| 4 | 75*X1(2,2)*X2(0,0)*X3(3,3) | 4 | 75*X1(2,2)*X2(0,0)*X3(3,3) | 4 | 75*X1(2,2)*X2(2,2)*X3(3,3) |
| 5 | 75*X1(2,2)*X2(1,1)*X3(3,3) | 5 | 75*X1(2,2)*X2(1,1)*X3(3,3) | 5 | 75*X1(2,2)*X2(3,3)*X3(3,3) |
| 6 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 6 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 6 | 5*X1(3,3)*X2(3,4)*X3(3,3) |
| 7 | 75*X1(2,2)*X2(3,3)* X2 (3,3) | 7 | 75*X1(2,2)*X2(3,3)*X3(3,3) | 7 | 11*X1(1,1)*X2(1,2)*X3 (3,3). |
| 8 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 8 | 5*X1(3,3)*X2(3,4)*X3(3,3) | ||
| 9 | 11*X1(1,1)*X2(1,2)* X3(3,3) | 9 | 11*X1(1,1)*X2(1,2)*X3 (3,3) |
- A further procedure demonstrates that term 1 has no consensuses with terms 2–7, so one should check for term 2:
- consensus 2*13 does not exist,
- consensus 2*23 = 2*23 = 75*x1(2,2)*x2(0,0) * x3(3,3) *2 75*x1(2,2)*x2(1,1) * x3(3,3) = 75*X1(2,2)*X2(0,1)*X3(3,3),
| 2*23 is added as term 8 | terms 2 and 3 subsume 8 | terms 1 and 2 are deleted | |||
| 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 2 | 75*X1(2,2)*X2(0,0)*X3(3,3) | 2 | 2 | 75*X1(2,2)*X2(2,2)*X3(3,3) | |
| 3 | 75*X1(2,2)*X2(1,1)*X3(3,3) | 3 | 3 | 75*X1(2,2)*X2(3,3)*X3(3,3) | |
| 4 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 4 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 4 | 5*X1(3,3)*X2(3,4)*X3(3,3) |
| 5 | 75*X1(2,2)*X2(3,3)*X3(3,3) | 5 | 75*X1(2,2)*X2(3,3)*X3(3,3) | 5 | 11*X1(1,1)*X2(1,2)*X3(3,3) |
| 6 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 6 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 6 | 75*X1(2,2)*X2(0,1)*X3(3,3), |
| 7 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 7 | 11*X1(1,1)*X2(1,2)*X3(3,3) | ||
| 8 | 75*X1(2,2)*X2(0,1)*X3(3,3) | 8 | 75*X1(2,2)*X2(0,1)*X3(3,3) |
| 2 *23 is added as term 7 | terms 2 and 3 subsume 7 | terms 1 and 2 are deleted | |||
| 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 2 | 75*X1(2,2)*X2(2,2)*X3(3,3) | 2 | 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) | |
| 3 | 75*X1(2,2)*X2(3,3)*X3(3,3) | 3 | 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) | |
| 4 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 4 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 4 | 75*X1(2,2)*X2(0,1)*X3(3,3) |
| 5 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 5 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 5 | 75*X1(2,2)*X2(2,3)*X3(3,3). |
| 6 | 75*X1(2,2)*X2(0,1)*X3(3,3) | 6 | 75*X1(2,2)*X2(0,1)*X3(3,3) | ||
| 7 | 75*X1 (2,2)*X2(2,3)*X3(3,3) | 7 | 75*X1(2,2)*X2(2,3)*X3 (3,3) |
| 4*25 is added as term 6 | terms 4 and 5 subsume 6 | terms 4 and 5 are deleted | |||
| 1 | 11*X1(3,3)*X2(2,2)*X3 (3,3) | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) |
| 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) |
| 4 | 75*X1(2,2)*X2 (0,1)*X3(3,3) | 4 | 4 | 75*X1(2,2)*X2(0,3)* X3(3,3) | |
| 5 | 75*X1(2,2)*X2(2,3)*X3(3,3) | 5 | |||
| 6 | 75*X1(2,2)*X2(0,3)*X3(3,3) | 6 | 75*X1(2,2)*X2(0,3)*X3(3,3) |
| 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) |
| 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) |
| 4 | 75*X1(2,2)*X2(0,3)*X3(3,3) |
| 5 | 255*X1(3,3)*X2(1,1)*X3(3,3) |
- A new search for consensus provides
- Consensus 1*25 = 11 * X1 (3,3) * X2 (2,2) * X3 (3,3) *2 255* X1 (3,3) * X2 (1,1) * X3 (3,3) = 255 * X1 (3,3) * X2 (0,3) * X3 (3,3).
| 1*25 is added as term 6 | terms 1 and 5 subsume 6 | terms 1 and 5 are deleted | |||
| 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) | 1 | 1 | 5*X1(3,3)*X2(3,4)*X3(3,3) | |
| 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) | 2 | 11*X1(1,1)*X2(1,2)*X3(3,3) |
| 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) | 3 | 75*X1(2,2)*X2(0,3)*X3(3,3) |
| 4 | 75*X1(2,2)*X2(0,3)*X3(3,3) | 4 | 75*X1(2,2)*X2(0,3)*X3(3,3) | 4 | 255*X1(3,3)*X2(0,3)*X3(3,3) |
| 5 | 255*X1(3,3)*X2(1,1)*X3(3,3) | 5 | |||
| 6 | 255*X1(3,3)*X2(0,3)*X3 (3,3) | 6 | 255*X1(3,3)*X2(0,3)*X3(3,3) |
| 1 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 2 | 5*X1(3,3)*X2(3,4)*X3(3,3) |
| 3 | 11*X1(1,1)*X2(1,2)*X3(3,3) |
| 4 | 75*X1(2,2)*X2(0,3)*X3(3,3) |
| 5 | 255*X1(3,3)*X2(1,1)*X3(3,3) |
3. Classification Schemes Based on MVL Functions
3.1. AGA Classifier and its Learning With a Teacher
3.2. Nested Structure of Classes in AGA Classifier
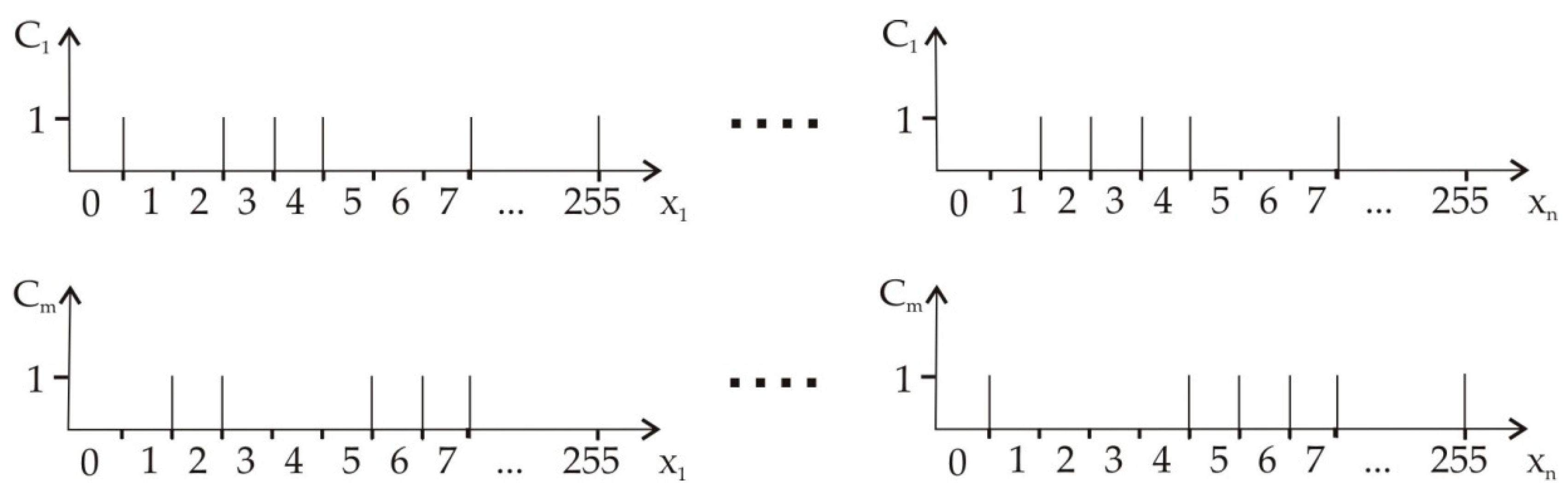
- To evaluate the maximal number of objects (tags) , i.e., to fix the necessary number of rows in the truth table.
- To evaluate the maximal number of classes to be used, thus choosing the necessary number of truth levels .
- To write the list of all characteristic features for classification , thus choosing the number of input variables .
- To fill the rows of the table by sets .
- To fill the column for by responding tags of classes , using any correct methods for their estimates.
- To compose the expression нaбop for every row .
- To unite all sets of minterms by the operator MAXIMUM (+) into the general expression of the function
- To hold a consensus minimization procedure according to Section 2, in order to reduce the computing time.
- To choose the platform and adapt the software for emulation of the minimized MVL function by the classifier device.
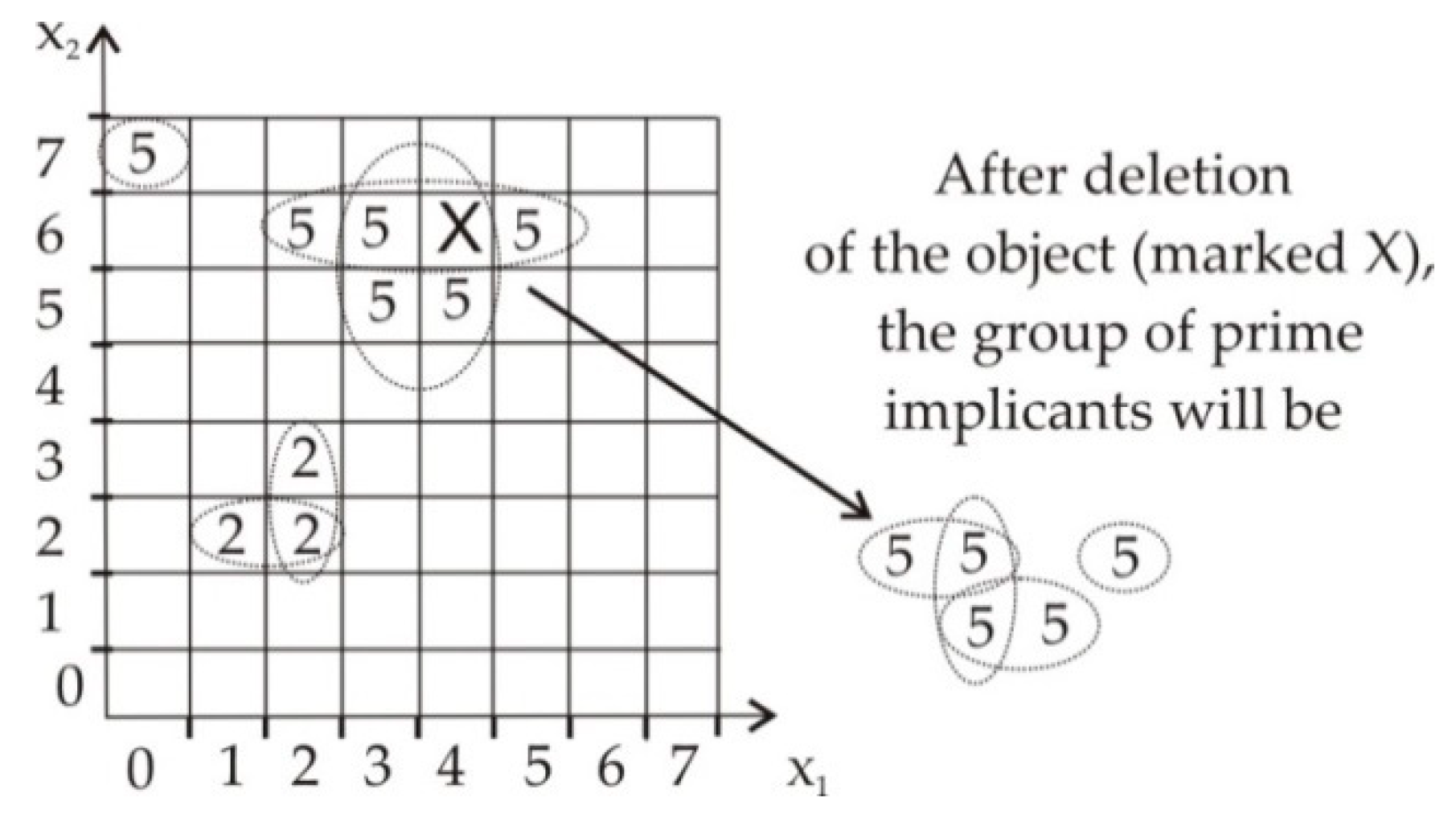
3.3. Description of Objects in the AGA Model
- Add the product term (x1,x1)...(xn,xn) to the earlier obtained list of product terms.Note.Position in the list can be chosen intentionally in order to fasten the search of aggregated groups of terms.
- If the added cell has neighboring cells with nonzero logic constants , run the minimization procedure defined in Section 2.3.
- Find the aggregated group of all V cells, neighboring to the cell (x1, ..., xn) and surrounded by DCSs. The set of constants used in the aggregated group is marked as , j = 1,..,m.
- Restore the set of product terms for individual cells in the aggregated group, according to Steps 3–5:
- Assign j = 1.
- For every input variable in the jth product term form the set of all possible Literals, as shown below:
- Compose all possible combinations of product terms, containing the constant and all possible combinations of Literals , obtained at Step 4:
- Repeat Steps 4 and 5 for all other j.
- Run the minimization procedure.
3.4. The General Scheme to Analyze the MVL Classifier
- Form the numbered (in arbitrary order) list of all product terms:
- Define the set of arrays for and .
- Assign
- Assign
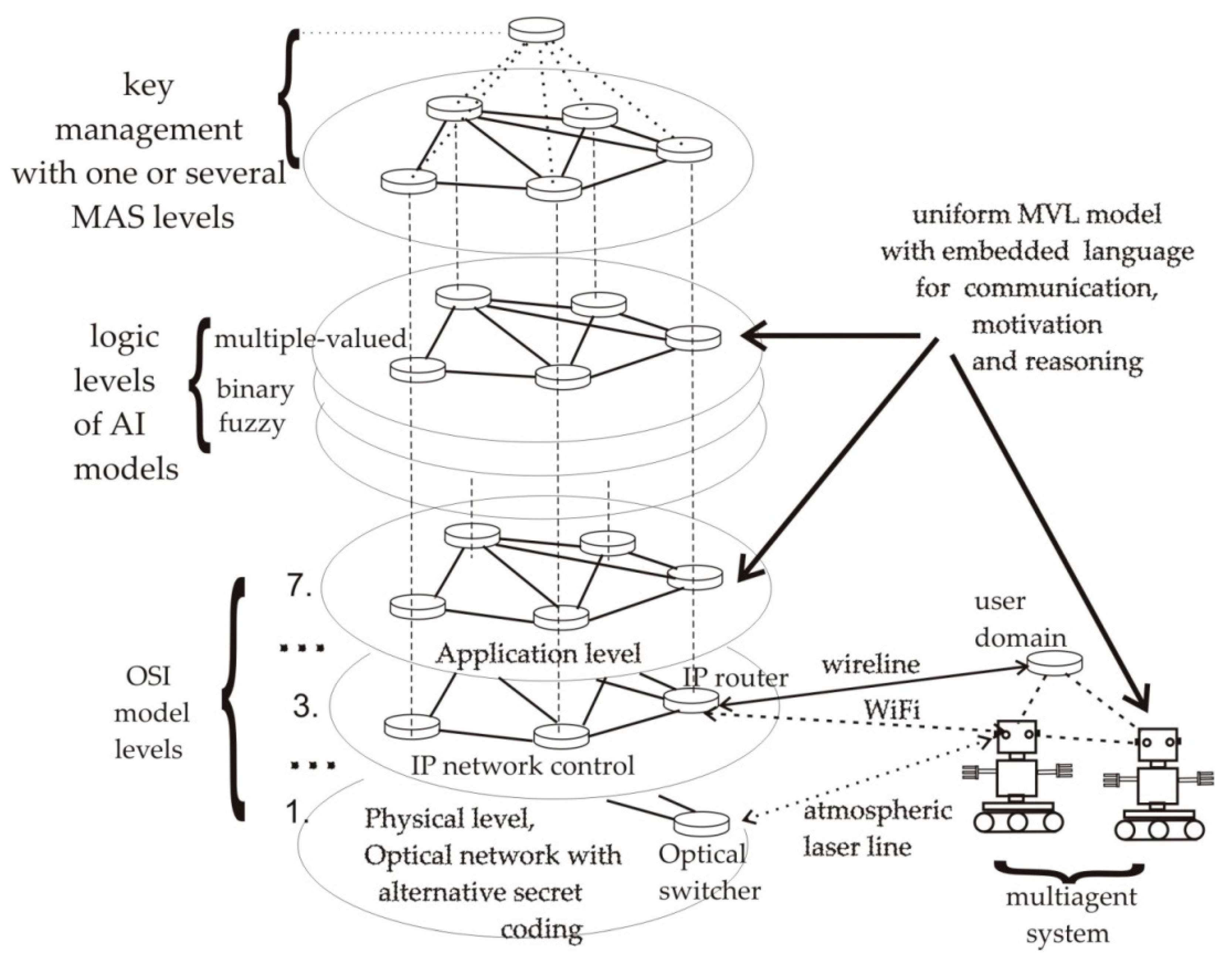
3.5. Heterogenious Architecture for the Integration of MAS
3.6. The Structure of Knowledge and the Agent′s Model, Necessary for Processing by AGA Methods
4. Discussion of Possible Further Steps for Application of MVL Models
4.1. High Information Capacity MVL Model of a Language for Robotic Communications
4.2. MVL Emulation of Classification Models
- -
- the presence of voids in the truth table between adjacent blocks of rows in the truth table, if these blocks refer to different groups of data and there are gaps in the domain of the function,
- -
- the overlap of blocks of rows in the truth table, if these blocks were obtained for partially matching training sequences or respond to different models.
5. Conclusions
Supplementary Materials
Funding
Conflicts of Interest
References
- Gros, D. Study “Global Trends to 2035. Economy and Society”. European Parliamentary Research Service Global Trends Unit PE 627. 126 November 2018; pp. 54–59. Available online: https://www.europarl.europa.eu/RegData/etudes/STUD/2018/627126/EPRS_STU(2018)627126_EN.pdf (accessed on 31 January 2020).
- Linton, P.; Schuchhard, P. Report to the Project “The Digital World in 2025. Indicators for European Action.” European Internet Foundation. September 2009; pp. 5–30. Available online: http://www.EIFonline.org (accessed on 31 January 2020).
- Report Global Strategic Trends. In The Future Starts Today, 6th ed.; Ministry of Defence, 2018; pp. 90–92. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/771309/Global_Strategic_Trends_-_The_Future_Starts_Today.pdf (accessed on 31 January 2020).
- Abdrachmanova, G.I.; Bondarenko, N.V.; Vishnevsky, K.O.; Gohberg, L.M.; Kevesh, M.A.; Kovaleva, G.G.; Kotzhemir, M.N.; Miltshina, J.V.; Mjazina, E.J.; Tokareva, M.S.; et al. Trends in the Development of the Internet in Russia. Analyt. Rep. by NRU HSE ISSEK. Institute for Statistical Studies and Economics of Knowledge, Russia. 2018, pp. 19–144. Available online: https://issek.hse.ru/data/2018/04/19/1150466651/Tendencii_razvitiya_interneta_v_Rossii.pdf (accessed on 31 January 2020).
- Laudicina, P.; Peterson, E.R.; McCaffrey, C.R. Five Significant Trends will Dramatically Shape the Global Outlook and Operating Environment through 2023. In Global Trends 2018–2023. Global Business Policy Council (GBPC). Competition, Disruption, and Deception. 2018. Trend #4. 2018. Available online: https://www.atkearney.com/web/global-business-policy-council/global-trends/2018-2023 (accessed on 31 January 2020).
- 2018 Annual Activity Report of the Commission’s Directorate-General for Communications Networks, Content and Technology (DG CONNECT). DG Communications Networks, Content and Technology. Ref. Ares (2019) 2265421 –29 March 2019. pp. 4–12. Available online: https://ec.europa.eu/info/sites/info/files/connect_2018_aar_final.pdf/ (accessed on 31 January 2020).
- Agrell, E.; Karlsson, M.; Chraplyvy, A.R.; Richardson, D.J.; Krummrich, P.M.; Winzer, P.; Roberts, K.; Fischer, J.K.; Savory, S.J.; Eggleton, B.J.; et al. Roadmap of optical communications. N. J. Opt. 2016, 18, 063002. [Google Scholar] [CrossRef]
- Jain, N.; Stiller, B.; Khan, I.; Elser, D.; Marquardt, C.; Leuchs, G. Attacks on practical quantum key distribution systems (and how to prevent them). Contemp. Phys. 2016, 57, 366–387. [Google Scholar] [CrossRef]
- Bykovsky, A., Yu.; Kompanets, I.N. Quantum cryptography and combined schemes of quantum cryptography communication networks. Quantum Electron. 2018, 48, 777–801. [Google Scholar] [CrossRef]
- Available online: http://www.ethw.org (accessed on 31 January 2020).
- Shallit, J. A Very Brief History of Computer Science. Available online: https://cs.uwaterloo.ca/~shallit/Courses/134/history.html (accessed on 31 January 2020).
- Konolige, K.; Fox, D.; Ortiz, C.; Agno, A.; Eriksen, M.; Limketkail, B.; Ko, J.; Morisett, B.; Schultz, D.; Stewart, B.; et al. Centibots: Very Large Scale Distributed Robotic Team. In Experimental Robotics IX: The 9th International Symposium on Experimental Robotics; Marcelo, H., Ang, M.H., Khatib, O., Eds.; Springer-Verlag: Berlin, Germany, 2006; pp. 131–140. [Google Scholar]
- Braunl, T. Embedded Robotics: Mobile Robot Design and Applications with Embedded Systems, 3rd ed.; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Turcu, Cr.; Turcu, Co.; Gaitan, V. Integrating robots into the Internet of Things. Int. J. Circuits Syst. Signal Proc. 2012, 6, 430–437. [Google Scholar]
- Matin, M.A.; Islam, M.M. Overview of Wireless Sensor Network, Wireless Sensor Networks-Technology and Protocols, Mohammad, A. Matin, IntechOpen. pp. 3–24. Available online: https://www.intechopen.com/books/wireless-sensor-networks-technology-and-protocols/overview-of-wireless-sensor-network (accessed on 6 September 2012). [CrossRef]
- Xu, W.; Yang, Z.; Wang, X. A Technical and Business Perspective on Wireless Sensor Network for Manufacturing Execution System. Math. Probl. Eng. 2015, 2015, 15. [Google Scholar] [CrossRef]
- Qureshi, U.M.; Zuneera, A.; Shaikh, F.K.; Bohra, N.; Memon, A.A. Project Oriented Problem Based Learning: A WirelessSensor Network Perspective. In Wireless Personal Communications; Springer Science + Business Media: New York, NY, USA, 2014; p. 14. Available online: https://www.academia.edu/11482307/Project_Oriented_Problem_Based_Learning_A_Wireless_Sensor_Network_Perspective (accessed on 31 January 2020).
- Derakhshan, F.; Yousefi, S. A review on the applications of multiagent systems in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2019, 15, 1–19. [Google Scholar] [CrossRef]
- Soldani, D.; Manzalini, A. On the 5G Operating System for a True Digital Society. IEEE Veh. Technol. Mag. 2015, 10, 32–42. [Google Scholar] [CrossRef]
- Available online: https://searchnetworking.techtarget.com/definition/6G (accessed on 31 January 2020).
- Vincent, B.; China Said It’s Developing 6G. China Said It’s Developing 6G. What Does That Mean? Available online: https://www.nextgov.com/emerging-tech/2019/11/china-said-its-developing-6g-what-does-mean/161225/ (accessed on 11 November 2019).
- Schatten, M.; Tomičić, I.; Durić, B.O. A review on application domains of large–scale multiagent systems. In Proceedings of the Central European Conference on Information and Intelligent Sytems, 28th CECIS, Varaždin, Croatia, 27–29 September 2017; pp. 201–205. [Google Scholar]
- Nebot, E. Robotics: From automation to intelligent systems. Engineering 2018, 4, 446–448. [Google Scholar] [CrossRef]
- Zhang, T.; Li, Q.; Zhang, C.-S.; Liang, H.-W.; Li, P.; Wang, T.-M.; Li, S.; Zhu, Y.-L., Wu. Current trends in the development of intelligent unmanned autonomous systems. Front. Inform. Technol. Electron. Eng. 2017, 18, 68–85. [Google Scholar] [CrossRef]
- Hu, Y.; Gong, J.; Jiang, Y.; Liu, L.; Xiong, G.; Chen, H. Hybrid Map-Based Navigation Method for Unmanned GroundVehicle in Urban Scenario. Remote Sens. 2013, 5, 3662–3680. [Google Scholar] [CrossRef]
- ITU-T FG-NET-2030. White Paper Network 2030-A Blueprint of Technology, Applications and Market Drivers towards the Year 2030 and Beyond; ITU-T; ITU: Lisbon, Portugal, May 2019. [Google Scholar]
- Russell, S.; Norvig, P. Artificial Intelligence: A Modern Approach; Prentice Hall: Englewood Cliffs, NJ, USA, 1995. [Google Scholar]
- Cao, X.; Yang, P.; Alzenad, M.; Xi, X.; Wu, D.; Yanikomeroglu, H. Airborne Communication Networks: A Survey. IEEE J. Sel. Areas Commun. 2018, 36, 1907–1926. [Google Scholar] [CrossRef]
- Moafipoor, S.; Bock, L.; Fayman, J.A. Relative Navigation System for Manned and Unmanned Vehicles. In Proceedings of the 25th International Technical Meeting of the Satellite Division of the Institute of Navigation, ION GNSS 2012, Nashville, TN, USA, 17–21 September 2012; pp. 3512–3522. [Google Scholar]
- Faisal, A.; Yigitcanlar, T.; Kamruzzaman, M.; Currie, G. Understanding autonomous vehicles: A systematic literature review on capability, impact, planning and policy. J. Trans. Land Use 2019, 12, 45–72. [Google Scholar] [CrossRef]
- Buehler, M.; Iagnemma, K.; Singh, S. (Eds.) The 2005 DARPA Grand Challenge: The Great Robot Race; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar] [CrossRef]
- Ashraf, S.; Aggarwal, P.; Shahrukh, A.; Damachrala, P. A low-cost solution for unmanned aerial vehicle navigation in a global positioning system–denied environment. Int. J. Distrib. Sens. Netw. 2018, 14, 1–17. [Google Scholar] [CrossRef]
- He, N.; Zhang, D.Z.; Ki, Q. Agent based hierarchical production planning and scheduling in make-to-order manufacturing systems. Int. J. Prod. Econ. 2014, 149, 117–130. [Google Scholar] [CrossRef]
- Andreadis, G.; Klazoglou, P.; Niotaki, K.; Bouzakis, K.-D. Classification and review of muilti-agent systems in the manufacturing section. Procedia Eng. 2014, 69, 282–290. [Google Scholar] [CrossRef]
- Tudor, V.; Gulisano, V.; Almgren, M.; Papatriantafilou, M. BES: Differentially private event aggregation for large scale IOT-based. Future Gener. Comput. Syst. 2018, 1–17. [Google Scholar] [CrossRef]
- Manzalini, A. Complex deep learning with quantum optics. Quantum Rep. 2019, 1, 107–118. [Google Scholar] [CrossRef]
- Nguyen, T.T.; Nguyen, N.D.; Nahavandi, S. Deep reinforcement learning for Multi-agent systems: A review of challenges, solutions and applications. arXiv 2018, arXiv:1812.11794v2. [Google Scholar]
- Oroojlooy, A.; Hajinezhad, D. A review of cooperative multi-agent deep reinforcement learning. arXiv 2019, arXiv:1908.03963v2. [Google Scholar]
- Sandholm, T. Perspectives of multiagent learning. Artif. Intell. 2007, 171, 382–391. [Google Scholar] [CrossRef]
- Bouchon-Meunier, B.; Yager, R.R.; Zadeh, L. (Eds.) Uncertainty in Intelligent and Information Systems; Advances in Fuzzy Systems—Applications and Theory; World Scientific: Singapore, 2000; Volume 20, p. 304. [Google Scholar] [CrossRef]
- Ross, T.J. Fuzzy Logic with Engineering Applications; John Wiley: Hoboken, NJ, USA, 2016. [Google Scholar] [CrossRef]
- Sinčák, P.; Vaščák, J.; Hirota, K. (Eds.) Machine Intelligence: Quo Vadis? Advances in Fuzzy Systems—Applications and Theory: Volume 21; World Scientific Publishing Co Pte Ltd.: Singapore, 2004. [Google Scholar]
- Abraham, A. Adaptation of Fuzzy Inference System Using Neural Learning, Fuzzy System Engineering: Theory and Practice; Studies in Fuzziness and Soft Computing; Nedjah, N., Ed.; Springer Verlag: Berlin, Germany, 2005; pp. 53–83. [Google Scholar]
- Black, P.E.; Kuhn, D.R.; Williams, C. Quantum computing and communication. J. Adv. Comput. 2002, 56, 189–241. [Google Scholar]
- Wu, W.; Liu, M.; Liu, Q.; Shen, W.A. Quantum multi-agent based neural network model for failure prediction. J. Syst. Sci. Syst. Eng. 2016, 25, 210–228. [Google Scholar] [CrossRef]
- Tacchino, F.; Macchiavello, C.; Gerace, D.; Bajoni, D. An artificial neuron implemented on an actual quantum processor. npj Quantum Inf. 2019, 5, 8. [Google Scholar] [CrossRef]
- Nauerth, S.; Moll, F.; Rau, M.; Fuchs, C.; Horwath, J.; Frick, S.; Weinfurter, H. Air-to-ground quantum communication. Nat. Photonics Lett. 2013, 7, 382–386. Available online: http://www.nature.com/nphoton/journal/v7/n5/full/nphoton.2013.46.html (accessed on 31 January 2020). [CrossRef]
- Bedington, R.; Arrazola, J.M.; Ling, A. Progress in satellite quantum key distribution. npj Quantum Inf. 2017, 3, 30. Available online: https://www.nature.com/articles/s41534-017-0031-5 (accessed on 31 January 2020). [CrossRef]
- Godouvitis, S.; Mueller, H.; Premnadh, S.; Seitz, A.; Bruegge, B. Seamless computing in industrial systems using container orchestration. Future Gener. Comput. Syst. 2018, 1–13. [Google Scholar] [CrossRef]
- Kitayama, K.-I.; Sasaki, M.; Araki, S.; Tsubokawa, M.; Tomita, A.; Inoue, K.; Harasawa, K.; Nagasako, Y.; Takada, A. Security in Photonic Networks: Threats and Security Enhancement. J. Lightwave Technol. 2011, 29, 3210–3221. Available online: https://www.researchgate.net/publication/224255782 (accessed on 31 January 2020). [CrossRef]
- Kuznetsov, A.V. The short review of multi-agent models. UBS 2018, 71, 6–44. [Google Scholar]
- Bojadziev, G.; Bojadziev, M. Fuzzy Logic for Business, Finance, and Management, 2nd ed.; Advances in Fuzzy Systems—Applications and Theory; World Scientific Publishing Co Pte Ltd.: Singapore, 2007; p. 252. [Google Scholar]
- Tarasov, V.B. From Multiagent Systems to Intellectual Organizations: Philosophy, Psychology, Informatics; URSS: Moscow, Russia, 2002. [Google Scholar]
- Alberts, D.S.; Garstka, J.; Stein, F.P. Network Centric Warfare: Developing and Leveraging Information Superiority (pdf), 2nd ed.; CCR Press: Boca Raton, FL, USA, 2017; p. 287. ISBN 1-57906-019-6. [Google Scholar]
- Seeja, G.; Arockia, S.; Berlin, H. A Survey on Swarm Robotic Modeling, Analysis and Hardware Architecture. Procedia Comput. Sci. 2018, 133, 478–485. [Google Scholar]
- Ullmann, M.и. Secure Vehicle-to Infrastructure Communication: Secure Roadside Stations, Key Management, and Crypto Agilty. Int. J. Adv. Secur. 2016, 9, 35–43. [Google Scholar]
- Shapiro, L.G.; Stockman, G.C. Computer Vision, 1st ed.; Prentice Hall PTR: Upper Saddle River, NJ, USA, 2001. [Google Scholar]
- The Visual Studio Integrated Development environment is a creative launching pad that you can use to edit, debug, and build code, and then publish an app. Microsoft Visual Studio. Available online: https://docs.microsoft.com/en-us/visualstudio/porting/port-migrate-and-upgrade-visual-studio-projects?view=vs- (accessed on 12 December 2019).
- Dertouzos, M.L. Threshold Logic: A Synthesis Approach; MIT Press: Cambridge, MA, USA, 1965. [Google Scholar]
- Arrathoon, R. (Ed.) Optical Computing. Digital and Symbolic; Marcel Dekker: New York, NY, USA, 1989. [Google Scholar]
- Rashvand, H.F.; Salah, K.; Calero, J.M.A.; Harn, L. Distributed security for multi-agent systems-review and applications. IET Inf. Secur. 2010, 4, 188–201. [Google Scholar] [CrossRef]
- Karygiannis, T.; Jansen, W. Mobile Agent Security. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=151186 (accessed on 31 January 2020).
- Hedin, Y.; Moradian, E. Security in multi-agent systems. Proc. Comput. Sci. 2015, 60, 1604–1612. [Google Scholar] [CrossRef]
- Cohen, R.; Schaekermann, M.; Liu, S.; Cormier, M. Trusted AI and the Contribution of Trust Modeling in Multiagent Systems. In Proceedings of the 18th International Conference on Autonomous Agents and Multiagent Systems (AAMAS 2019), Montreal, QC, Canada, 13–17 May 2019; pp. 1644–1648. [Google Scholar]
- NesC: A Programming Language for Deeply Networked Systems. UC Berkeley WEBS Project. Available online: http://nescc.sourceforge.net/ (accessed on 31 January 2020).
- Franklin, M.J.; Hellerstein, J.M.; Hong, W. TinyDB: An Acquisitional Query Processing System for Sensor Networks. Available online: http://telegraph.cs.berkeley.edu/tinydb/overview.html (accessed on 31 January 2020).
- Antipov, A.L.; Bykovsky, A.Y.; Vasiliev, N.A.; Egorov, A.A. Multiple-valued logic-protected coding for an optical non-quantum communication line. J. Russ. Laser Res. 2006, 27, 492–505. [Google Scholar] [CrossRef]
- Antipov, A.L.; Bykovsky, A.Y.; Vasiliev, N.A.; Egorov, A.A. Protected Query Coding in Multi-Agent Optoelectronic System. Opt. Mem. Neur. Netw. 2007, 16, 211–220. [Google Scholar] [CrossRef]
- Ma, X.; Yuan, X.; Cao, Z.; Qi, B.; Zhang, Z. Quantum random number generation. npj Quantum Inf. 2016, 2, 1–9. [Google Scholar] [CrossRef]
- Abellán, C.; Amaya, W.; Mitrani, D.; Pruneri, V.; Mitchell, M. Generation of fresh and pure random numbers for loophole-free bell tests. Phys. Rev. Lett. 2015, 115, 250403. [Google Scholar] [CrossRef]
- Allen, C.M.; Givone, D.D. The Allen-Givone Implementation Oriented Algebra. In Computer Science and Multiple-Valued Logic: Theory and Applications; Rine, D.C., Ed.; North Holland: Amsterdam, The Netherlands, 1984; pp. 262–283. [Google Scholar]
- Shimbirev, P.N. Hybrid Continious Logic Devices; Energoatomizdat: Moscow, Russia, 1990. [Google Scholar]
- Beeler, M.; Gosper, R.W.; Schroeppel, R. HAKMEM, Memo 239, Artificial Intelligence Laboratory; Massachusetts Institute of Technology: Cambridge, MA, USA, 1972. [Google Scholar]
- Padmanabhan, T. Inflation from quantum gravity. Phys. Letts. 1984, A104, 196–199. [Google Scholar] [CrossRef]
- Bykovsky, A.Y. A Multiple-Valued Logic for Implementing a Random Oracle and the Position-Based Cryptography. J. Russ. Laser Res. 2019, 40, 173–183. Available online: http://link.springer.com/article/10.1007/s10946-019-09785-5 (accessed on 31 January 2020). [CrossRef]
- Bykovsky, A.Y.; Egorov, A.A.; Rager, B.Y. Multiple-Valued Logic Protected Coding for Optoelectronic Systems Distant Control via The Global Network. Pac. Sci. Rev. 2011, N3, 140–150. [Google Scholar]
- Broadbent, A.; Schaffner, C. Quantum cryptography beyond quantum key distribution. Des. Codes Cryptogr. 2016, 78, 351–382. [Google Scholar] [CrossRef]
- Unruh, D. Quantum Position Verification in the Random Oracle Model. In Advances in Cryptology–CRYPTO 2014; Garay, J.A., Gennaro, R., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014. [Google Scholar] [CrossRef]
- Antipov, A.L.; Bykovsky, A.Y.; Egorov, A.A. Data Protection Ordering/Disordering of a Fuzzy Logic Model in a Robotic Agent via the Optical Data Transfer Line. J. Russ. Laser Res. 2008, 29, 324–335. [Google Scholar] [CrossRef]
- Bykovsky, A.Y. Digital maps modeling method based on discrete multiple-valued logic. Bull. Lebedev Phys. Inst. 2013, 11, 9–18. [Google Scholar]
- Negoita, C.V. (Ed.) Cybernetics and Applied Systems; Marcel Decker: New York, NY, USA, 1992. [Google Scholar]
- Bykovsky, A.Y.; Rager, B.Y. Heterogeneous logic models for optoelectronic data processing in multi-agent systems. In Proceedings of the XIIth All-Russian Conference on the Control Problems VSPU-2014, Moscow, Russia, 16–19 June 2014; pp. 3917–3928. [Google Scholar]
- Cristianini, N.; Shawe-Taylor, J. An Introduction to Support Vector Machines and Other Kernel-based Learning Methods; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar] [CrossRef]
- Bishop, C.M. Pattern Recognition and Machine Learning; Springer: New York, NY, USA, 2006. [Google Scholar]
- Shenoi, B.A. Introduction to Digital Signal Processing and Filter Design; John Wiley and Sons: New York, NY, USA, 2006; p. 120. [Google Scholar]
- Data clustering. Algorithms and Applications; Aggarwal, C.C., Reddy, C.K., Eds.; CRC Press, Taylor & Francis Group: Boca Raton, FL, USA, 2014. [Google Scholar]
- Ibe, O.C. Fundamentals of Data Communication Networks; John Wiley & Sons, Inc.: New York, NY, USA, 2018. [Google Scholar] [CrossRef]
- Xu, R.; Wunsch, D.C. Clustering algorithms in Biomedical Research: A Review. IEEE Rev. Biomed. Eng. 2010, 3, 120–154. [Google Scholar] [CrossRef] [PubMed]
- Xu, D.; Tian, Y. A Comprehensive Survey of Clustering Algorithms. Ann. Data Sci. 2015, 2, 165–193. [Google Scholar] [CrossRef]
- Ahmad, A.; Khan, S.S. Survey of State-of-the-Art Mixed Data Clustering Algorithms. IEEE Access 2019, 7, 31883–31902. [Google Scholar] [CrossRef]
- Zadeh, L.A. The concept of a linguistic variable and its application to approximate reasoning. Inf. Sci. 1975, 8, 199–249. [Google Scholar] [CrossRef]
- Horn, D.; Gottlieb, A. Algorithm for data clustering in pattern recognition problems based on quantum mechanics. Phys. Rev. Lett. 2001, 88, 4. [Google Scholar] [CrossRef]
- Horn, D.; Gottlieb, A. The method of quantum clustering. In Advances in neural information processing systems 14. Proceedings of the conference Neural Information Processing Systems 2001, Vancouver, BC, Canada, 3–8 December 2001; MIT Press: Cambridge, MA, USA, 2002; pp. 769–776. [Google Scholar]
- Weinstein, M.; Horn, D. Dynamic quantum clustering: a method for visual exploration of structures in data. Phys. Rev. E 2009, 80, 066117. [Google Scholar] [CrossRef]
- Habibb, C.; Makhoula, A.; Darazib, R.; Couturiera, R. Health risk assessment and decision-making for patient monitoring and decision-support using wireless body sensor networks. Inf. Fusion 2019, 47, 10–22. [Google Scholar] [CrossRef]
- Gustafson, E.E.; Kessel, W.C. Fuzzy Clustering with a Fuzzy Covariance Matrix. In Proceedings of the IEEE Conference on Decision and Control, San Diego, CA, USA, 10–12 January 1979; pp. 761–766. [Google Scholar]
- Iwakoshi, Y.; Furuhashi, T.; Uchikawa, Y. A fuzzy classifier system for evolutionary learning of robor behaviors. Appl. Math. Comput. 1998, 91, 73–81. [Google Scholar]
- Pham, T.D.; Yan, H. Color image segmentation using fuzzy integral and mountain clustering. Fuzzy Sets Syst. 1999, 107, 121–130. [Google Scholar] [CrossRef]
- Valente de Oliveira, J.; Pedrycz, W. (Eds.) Advances in Fuzzy Clustering and Its Applications; John Wiley& sons, Ltd.: New York, NY, USA, 2001. [Google Scholar]
- Jiamin Li, J.; Lewis, H.W. Fuzzy Clustering Algorithms—Review of the Applications. In Proceedings of the 2016 IEEE International Conference on Smart Cloud, New York, NY, USA, 18–20 November 2016; pp. 282–288. [Google Scholar] [CrossRef]
- Gosain, A.; Dahiya, S. Performance analysis of Various Fuzzy Clustering Algorithms: A Review. Proc. Comp. Sci. 2016, 79, 100–111. [Google Scholar] [CrossRef]
- Yang, H.; Yao, Q.; Yu, A.; Lee, Y.; Zhang, J. Resource Assignment Based on Dynamic Fuzzy. Clustering in Elastic Optical Networks with Multi-Core Fibers. IEEE Trans. Commun. 2019, 67, 3457–3469. [Google Scholar] [CrossRef]
- Alomoush, W.; Alrosan, A. Review: Metaheuristic Search-Based Fuzzy Clustering Algorithms. Available online: https://arxiv.org/abs/1802.08729 (accessed on 31 January 2020).
- Rodriguez, M.Z.; Comin, C.H.; Casanova, D.; Bruno, O.M.; Amancio, D.R.; Ba, F.; Costa, L.; Rodrigues, F.A. Clustering algorithms: A comparative Approach. PLoS ONE 2019, 14, e0210236. [Google Scholar] [CrossRef]
- Kozen, D. On Kleene Algebras and Closed Semirings; Mathematical foundations of computer science. In Proceedings of the 15th, Int. Symposium on Math. Foundations of Comp. Science MFCS’90, Banská Bystrica, Czech Republic, 27–31 August 1990; Rovan, B., Ed.; Springer-Verlag: Berlin, Germany, 1990; pp. 26–47. [Google Scholar]
- Antipov, A.L.; Bykovsky, A.Y.; Egorov, A.A.; Kompanets, I.N. Procedure of autentification of robotic agents, based on multiple-valued and fuzzy logic. Radiotechnika 2008, N8, 97–104. [Google Scholar]
- Bykovsky, A.Y.; Sherbakov, A.A. The multi-criteria optimization for the formation of the multiple-valued logic model of a robotic agent. J. Phys. Conf. Ser. 2016, 737, 1–9. [Google Scholar] [CrossRef]
- Bykovsky, A.Y. Discrete k-valued logic for multi-parametrical modeling of a robotic agent. Phys. Procedia 2015, 73, 257–263. [Google Scholar] [CrossRef]
- Hughes, R.J.; Nordholt, J.E.; McCabe, K.P.; Newell, R.; Peterson, C.G.; Somma, R.D. Network-Centric Quantum Communications with Application to Critical Infrastructure Protection. In Proceedings of the 3rd International Conference Quantum Cryptography, Waterloo, Canada, 5–9 August 2013; LA-UR-13-22718. Available online: http://2013.qcrypt.net/program/#invited (accessed on 31 January 2020).
- Hughes, R.J.; Chapuran, T.E.; Dallmann, N.; Hiskett, P.A.; McCabe, K.P.; Montano, P.M.; Nordholt, J.E.; Peterson, C.G.; Runser, R.J.; Sedillo, R.; et al. A Quantum Key Distribution System for Optical Fiber Networks. Available online: https://www.spiedigitallibrary.org/conference-proceedings-of-spie/5893/589301/A-quantum-key-distribution-system-for-optical-fiber-networks/10.1117/12.615594.short?SSO=1 (accessed on 31 January 2020).
- Available online: https://www.samsongroup.com/document/l155en.pdf (accessed on 31 January 2020).
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the 28th Annual ACM Symposium on the Theory of Computing, Philadelphia, PA, USA, 21–24 May 1996; pp. 212–220. [Google Scholar]






| Industrial and intrafacility networks for control and management (1890s–1900s) | Network of traffic lights (1914) | Radioloca- tion network (1940s) | Satellite communi- cations (1958) | Mobile telephones (1973) | Fiber optics (1975–1980) |
| Internet (1983) | Project of distributed quantum computing (1990s) | Project of network- centric system (1999) | Project of photonic network (2000) | Multiagent system of robots (2000s) | Quantum key distribu- tion (2005) |
| Computing | Defense | Computer Security | Social Security | Finance and Commerce | Search and Storage of Data |
| Cloud, Supercomputer, Cryptocurrency mining, Quantum computer | Global systems for control, detection, and monitoring, Robotics swarms | Data leakage protection, Computer monitoring of staff activity, Quantum key distribution | Face control, Biometrics, Search of illegal cargo | Accounting, Billing, Document exchange, Advertising, Marketing E-commerce, | Data and knowledge search, Expert systems, Machine text and speech translation |
| Medicine | Computer Vision | Sensor Networks | Industrial Robotics | Navigation and Space Positioning | Unmanned Vehicles and Logistics |
| 3D tomo- graphy, Distant consulting, Health control and surgery, Robotic nursing | Image and scene processing for defense, transport, and industry | Objects detection, Positioning control | Control of semi- and fully unmanned systems | Optimal routing, Multiagent mapping, | Optimal logistics, Unmanned traffic control, Automatic repair and service |
| Education | Mass Communications | Mass Media | Entertainment and Travel Industry | Social Activity and Networks | Household |
| E-Libraries, Data search, Educational films andsimulators entry | Mobile and stationary telephone, Skype, Internet | Delivery of news and targeted packets | Search of network content, Hotel and ticket reservation | Polling, Computer voting, Social projects | IoT, Food ordering Automatic repair services |
| N | K | Nrows = kn | Nlog.functions = |
|---|---|---|---|
| 50 | 2 | ≈1.13 × 1015 | ≈1.27·× 1030 |
| 50 | 256 | ≈2.58·10120 | ≈2.96·× 1030825 |
| 50 | 65536 | ≈6.67·× 10240 | >1015770928 |
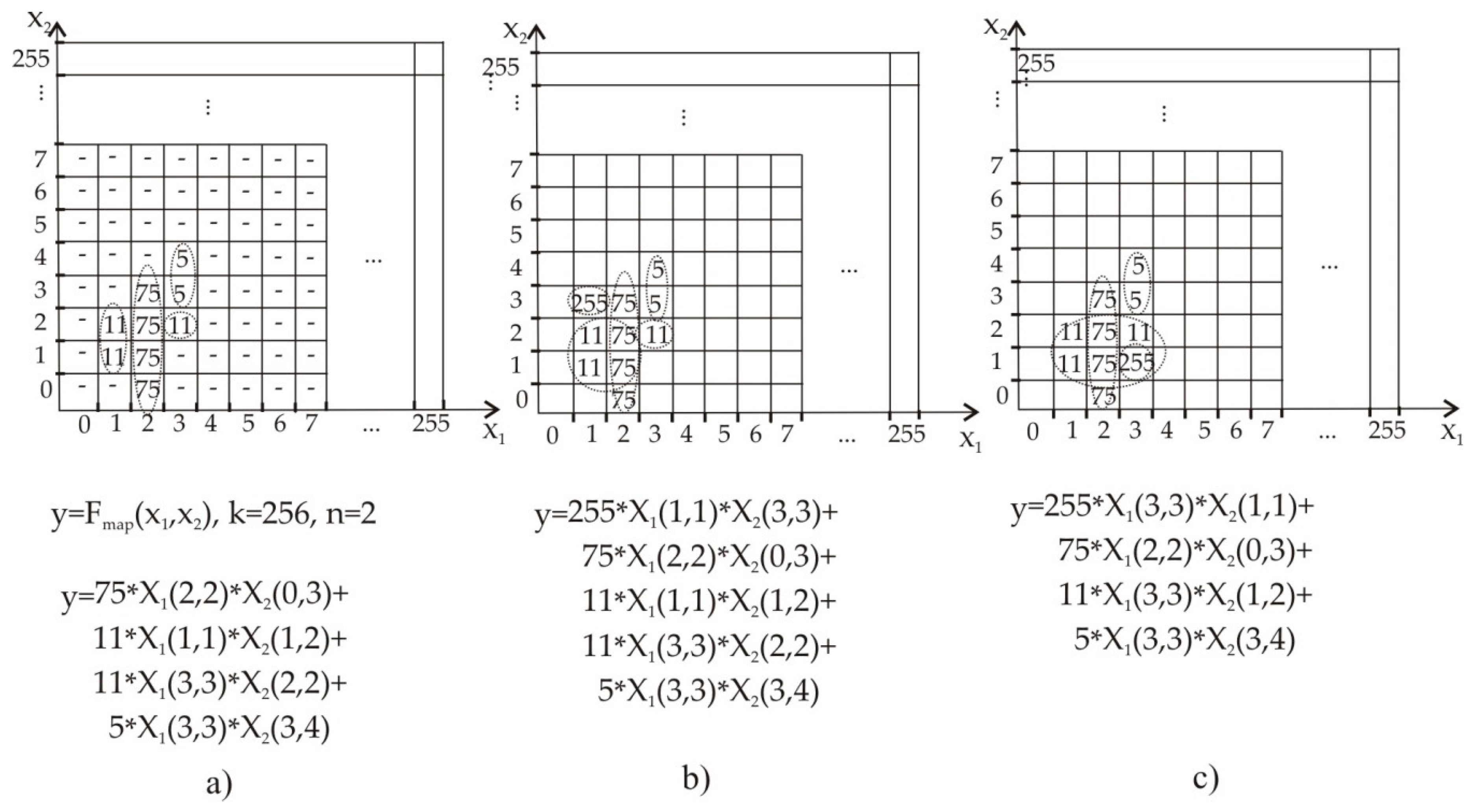
| N | X1 | X2 | X3 | F(x1,x2,x3) | Responding Product Terms |
|---|---|---|---|---|---|
| 1 | 2 | 0 | 3 | 75 | 75*X1(2,2)* X2(0,0)* X3(3,3) |
| 2 | 1 | 1 | 3 | 11 | 11*X1(1,1)*X2(1,1)* X3(3,3) |
| 3 | 2 | 1 | 3 | 75 | 75*X1(2,2)* X2(1,1)*X3(3,3) |
| 4 | 1 | 2 | 3 | 11 | 11*X1(1,1)*X2(2,2)*X3(3,3) |
| 5 | 2 | 2 | 3 | 75 | 75*X1(2,2)*X2(2,2)*X3(3,3) |
| 6 | 3 | 2 | 3 | 11 | 11*X1(3,3)*X2(2,2)*X3(3,3) |
| 7 | 2 | 3 | 3 | 75 | 75*X1(2,2)*X2(3,3)*X3(3,3) |
| 8 | 3 | 3 | 3 | 5 | 5*X1(3,3)*X2(3,3)*X3(3,3) |
| 9 | 3 | 4 | 3 | 5 | 5* X1(3,3)*X2(4,4)*X3(3,3) |
| Levels of OSI Model | Standard OSI Model, (Key Words), [86,111] | Network-centric QKD Project, [109] | Photonics Networks QKD Project [50] |
|---|---|---|---|
| 9. | - | - | Key management center |
| 8. | - | - | Multiagent system for joint key management |
| 7. | Application (access to network services, HTTP, FTP, POP3, etc.) | Trusted authority (“Trent”) was realized by the server | + |
| 6. | Presentation and secret coding (ASCII, EBCDIC) | + | + |
| 5. | Session (communication session control) | + | + |
| 4. | Transport (reliability of a link, segment, datagram, TCP, UDP) | + | + |
| 3. | Network (packet, routing and logical addressing, IPv4-6, IPSec) | + | + |
| 2. | Data link (bits, frames, physical addressing, Ethernet, network card, IEEE 802.22) | + | + |
| 1. | Physical (bits, cable, twisted pair, fiber optics, RF channel, USB ports,) | traditional means and QKD fiber lines | traditional means and QKD fiber lines and optical cross connects, directly plugged to switchers of IP routers |
© 2020 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bykovsky, A.Y. Heterogeneous Network Architecture for Integration of AI and Quantum Optics by Means of Multiple-Valued Logic. Quantum Rep. 2020, 2, 126-165. https://doi.org/10.3390/quantum2010010
Bykovsky AY. Heterogeneous Network Architecture for Integration of AI and Quantum Optics by Means of Multiple-Valued Logic. Quantum Reports. 2020; 2(1):126-165. https://doi.org/10.3390/quantum2010010
Chicago/Turabian StyleBykovsky, Alexey Yu. 2020. "Heterogeneous Network Architecture for Integration of AI and Quantum Optics by Means of Multiple-Valued Logic" Quantum Reports 2, no. 1: 126-165. https://doi.org/10.3390/quantum2010010
APA StyleBykovsky, A. Y. (2020). Heterogeneous Network Architecture for Integration of AI and Quantum Optics by Means of Multiple-Valued Logic. Quantum Reports, 2(1), 126-165. https://doi.org/10.3390/quantum2010010




