Bridging Cybersecurity Practice and Law: A Hands-On, Scenario-Based Curriculum Using the NICE Framework to Foster Skill Development †
Abstract
1. Introduction
- 1.
- Where do SMBs stand with respect to cybersecurity? This question allows us to collect and synthesize existing data to identify the gap between the current SMB workforce and best practices.
- 2.
- What are the most frequent and impactful attacks faced by SMBs? This allows us to center the scope of our research on providing the most robust skillset to SMBs. This is carried out to maximize the area of coverage with as small of a workforce as possible due to the limited nature of an SMB. Our research found that the most frequent attacks are phishing/social engineering, malware/ransomware, and web-based attacks (Section 4.1). Our work on identifying the attack vectors most frequently faced by SMBs was previously published in [6].
- 3.
- How can the workforce be equipped with the necessary knowledge and skills to apply the best practices? This helps us incorporate the NICE Framework [7] as a bridge between the workforce and the best practices by mapping the tasks, knowledge, skills, and abilities (TKSA) to the most frequent attacks. However, the NICE Framework lists a total of 634 knowledges, 377 skills, 1006 tasks, and 177 abilities, making it costly for SMB owners to investigate and implement. Our research yielded a total of 88 technical TKSA and 54 non-technical TKSA that are required to defend against the three previously mentioned attack types (Section 4.2 and Section 4.3). This is 6.47% of the total TKSAs present in the NICE Framework and is designed to be feasible for SMBs to implement, as it extracts the TKSA most relevant to defend against the attack vectors identified. Note that these findings are preliminary. Further validation with SMB practitioners in real operational contexts will be necessary to confirm its practicality and impact.
- First, the ACM cybersecurity curriculum guidelines stress that while cybersecurity is fundamentally computing-based, it inherently includes legal and policy considerations and other non-technical aspects [10]. This paper presents cybersecurity curriculum that bridges cybersecurity practice and law. Multi-disciplinary exposure helps address multifaceted cybersecurity issues and demonstrate its comprehensive view to the students. To the best of our knowledge, no textbook on security is available yet that provides an integrated view of cybersecurity. Lab manuals and the source code for the course labs are publicly available on our https://github.com/csu-techhub/scenario-security-labs (accessed on 3 October 2025).
- Second, in order to provide a comprehensive, unfragmented view, cybersecurity education within context is desirable. Scenario-based learning uses interactive classroom sessions to support active learning strategies such as problem-based or case-based learning [9,11,12,13]. It normally involves students working their way through a storyline, usually based around a complex problem, which they are required to solve. Unique to the proposed curriculum is to integrate the scenarios with hands-on experiments.
- Third, a hands-on approach of security training and education are not typically available for students. In our experience, students not only like to have hands-on experience of security issues by hacking a system, but also they learn the issues and corresponding protection much better with practical experience. To this end, it is important to design specially-crafted set of experiments with virtual machine (VM)-based platforms. NICE Challenge Project [14] and Defcon’s Capture the Flag [15] are similar examples but they focus only on technical challenges [16,17,18]. We employ Ohio Cyber Range VM environment [19], where students not only perform technical analyses and mitigations but also examine the legal implications and compliance requirements of the incidents. This integrated approach ensures thorough, hands-on skills development while simultaneously grounding students in the theoretical context of cybersecurity.
2. Preliminaries
2.1. A Note on KSA and TKSA
2.2. A Note on the NICE Framework
2.3. Ethics Statement
3. Related Work
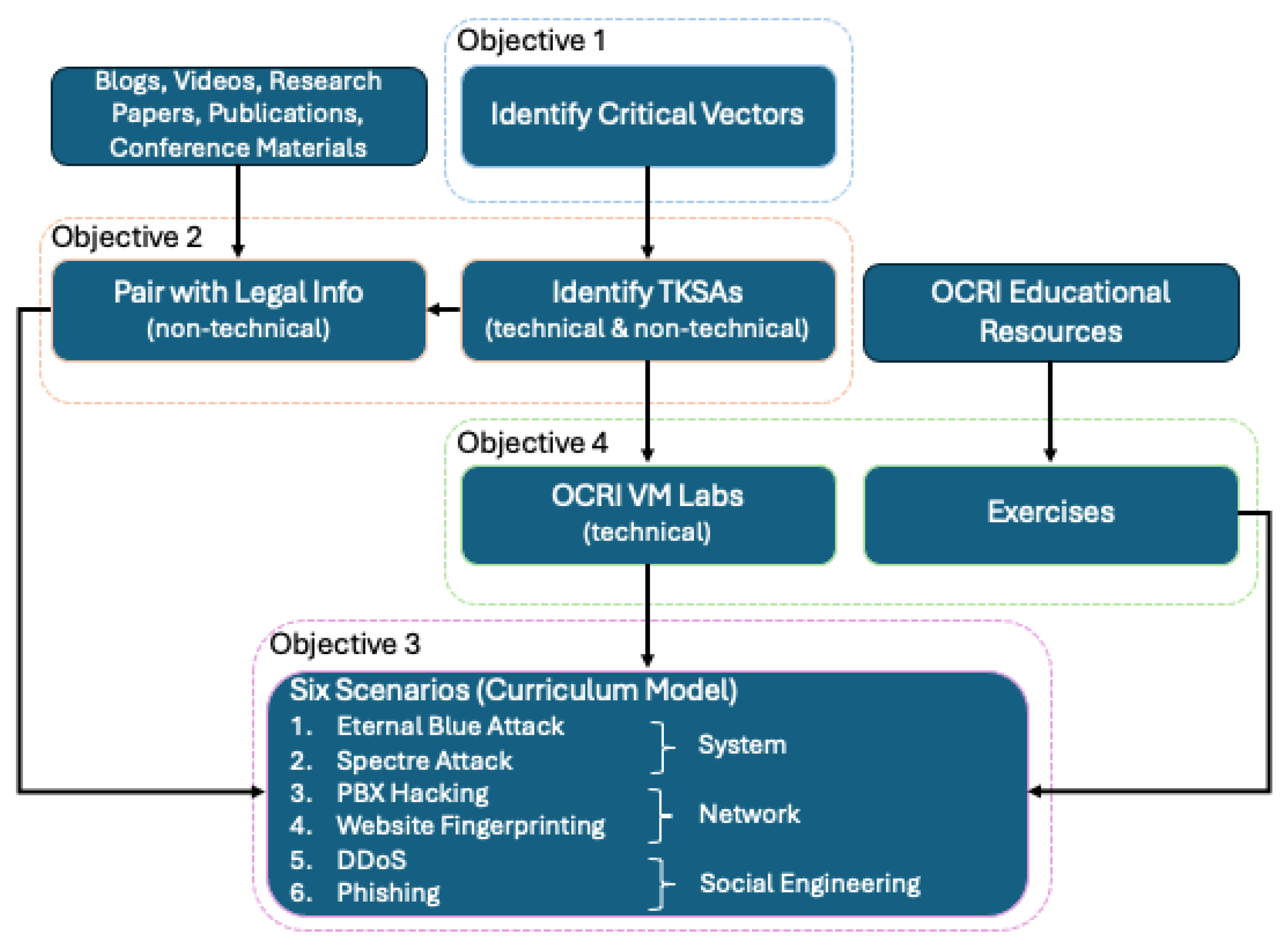
4. Proposed Work
4.1. Identifying the Most Frequent Attacks
4.2. Identifying Best Practices and Extracting Keywords
4.3. Mapping Keywords to the NICE Framework
4.3.1. Technical Model
4.3.2. Non-Technical Model
4.4. Integration of KSAs, Virtual Machine Labs, and NICE Framework
5. Scenario-Based Curriculum
- Scenario 1:
- EternalBlue—focuses on a malware attack exploiting the EternalBlue vulnerability, emphasizing patch management.
- Scenario 2:
- Spectre/Meltdown—addresses hardware-level vulnerabilities and the need for robust hardware security.
- Scenario 3:
- PBX Hacking—deals with web-based attacks on private branch exchange (PBX) systems, highlighting network security challenges.
- Scenario 4:
- Website Fingerprinting—explores attacks through website fingerprinting, stressing web traffic protection.
- Scenario 5:
- DDoS Attack—involves a distributed denial of service (DDoS) attack, focusing on network resilience.
- Scenario 6:
- Hacking Group Thallium—examines a phishing attack by the Thallium group, emphasizing defense against social engineering.
5.1. Scenarios and TKSAs
5.1.1. Leveraging Virtual Machine Labs
5.1.2. OCRI Exercises
5.1.3. Legal Considerations
5.2. Overview of Scenarios
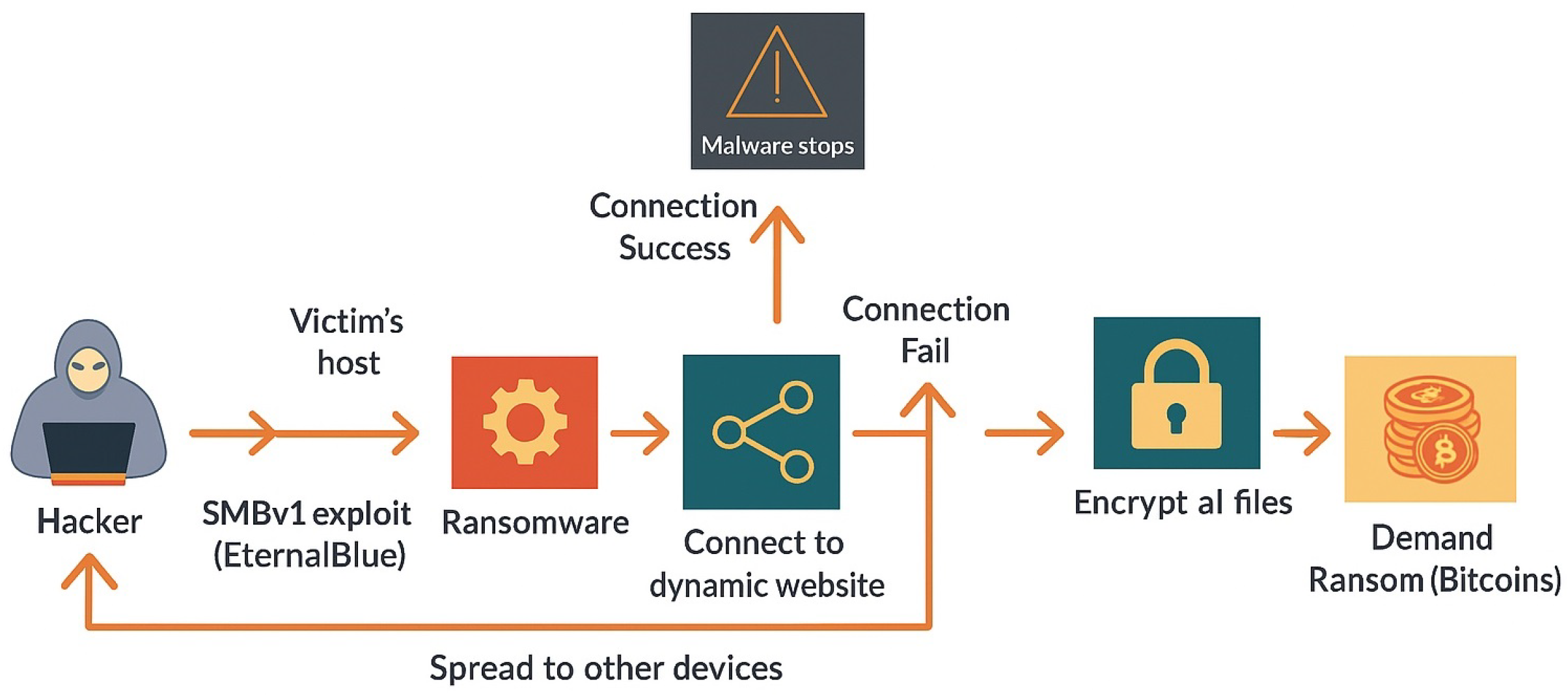
5.2.1. Scenario 1: EternalBlue
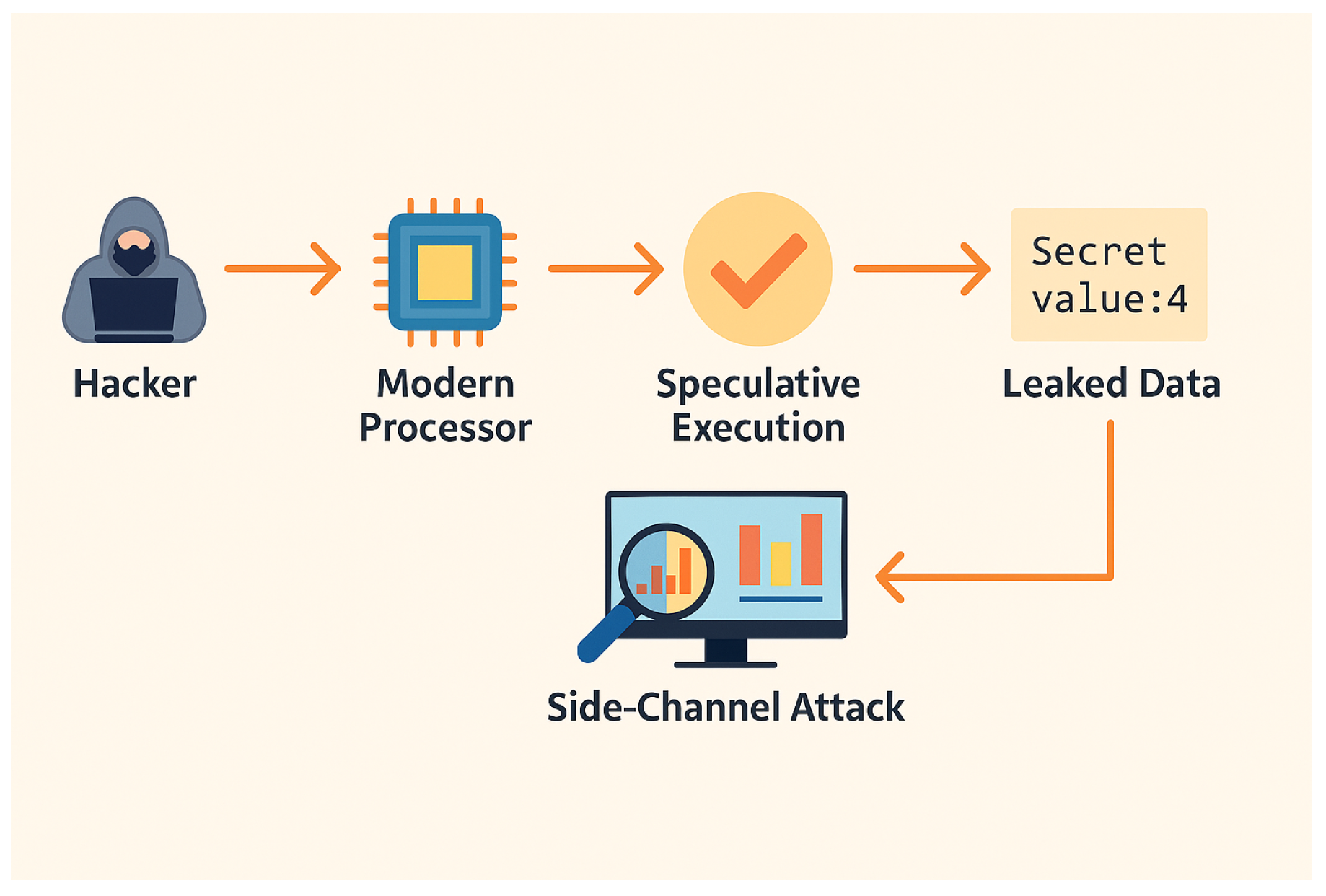
5.2.2. Scenario 2: Spectre/Meltdown
5.2.3. Scenario 3: PBX Hacking
5.2.4. Scenario 4: Website Fingerprinting
5.2.5. Scenario 5: Distributed Denial of Service Attack
5.2.6. Scenario 6: Hacking Group Thallium
6. Results and Analysis
6.1. Focus Group Interview
- 1.
- Targeted Threats: Students valued the hands-on scenarios for enhancing their cybersecurity understanding, but CS students found them easy, while law students struggled and requested clearer instructions. Balancing difficulty and guidance would improve the experience.
- 2.
- Holistic Knowledge: The non-technical material offered valuable multidisciplinary perspectives, though CS students desired more technical content, and law students found some readings repetitive. Refining content for both backgrounds could enhance learning.
- 3.
- Scenario-Based Model: While the scenario approach effectively bridged theory and practice, differing difficulty levels for CS and law students indicated a need for adjustments to equally challenge all participants.
- 4.
- Practical Experience: Hands-on labs were well-received by CS students, and although law students faced challenges, they gained valuable exposure. Technical support improvements were suggested to address lab difficulties.
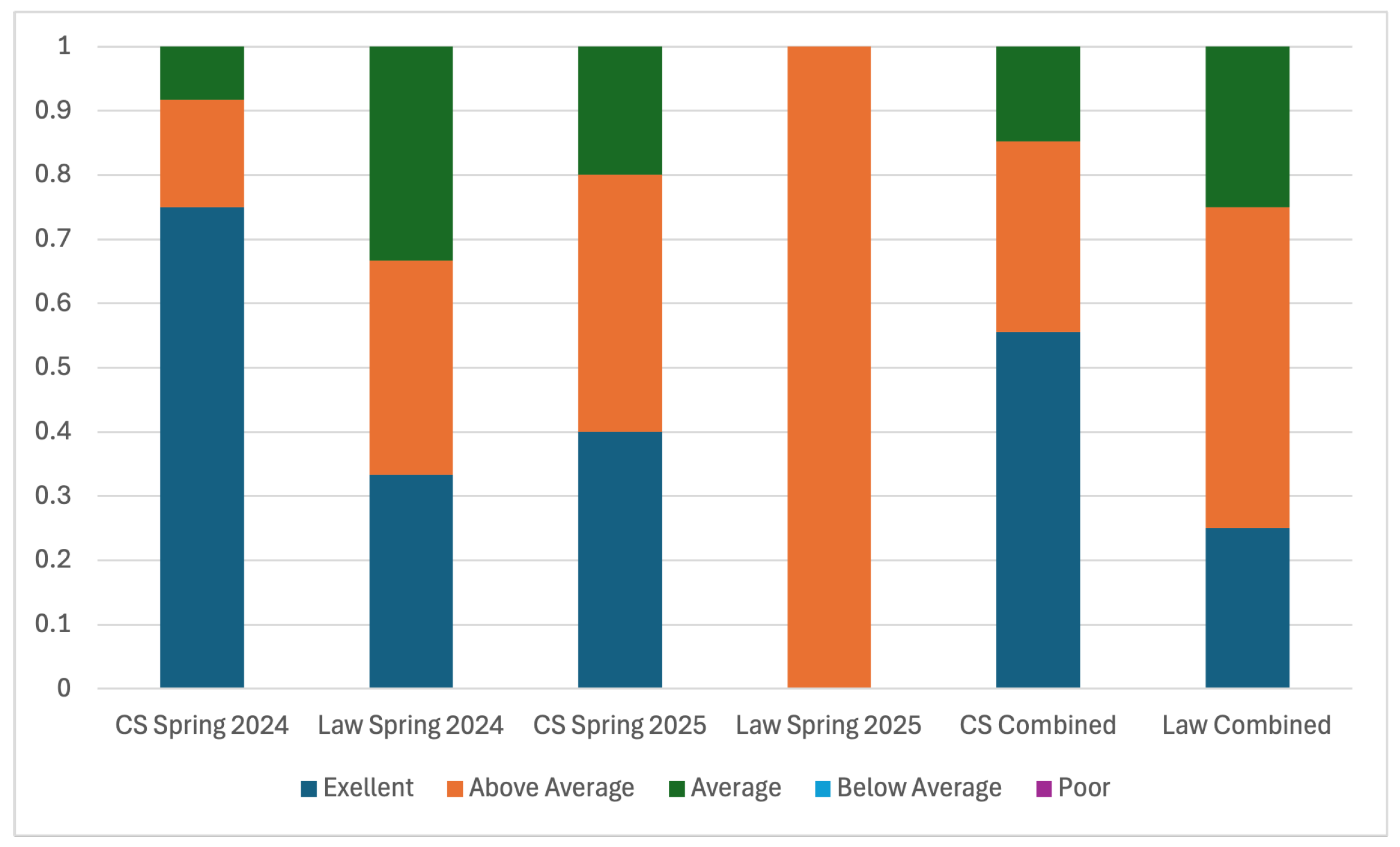
6.2. Student Survey
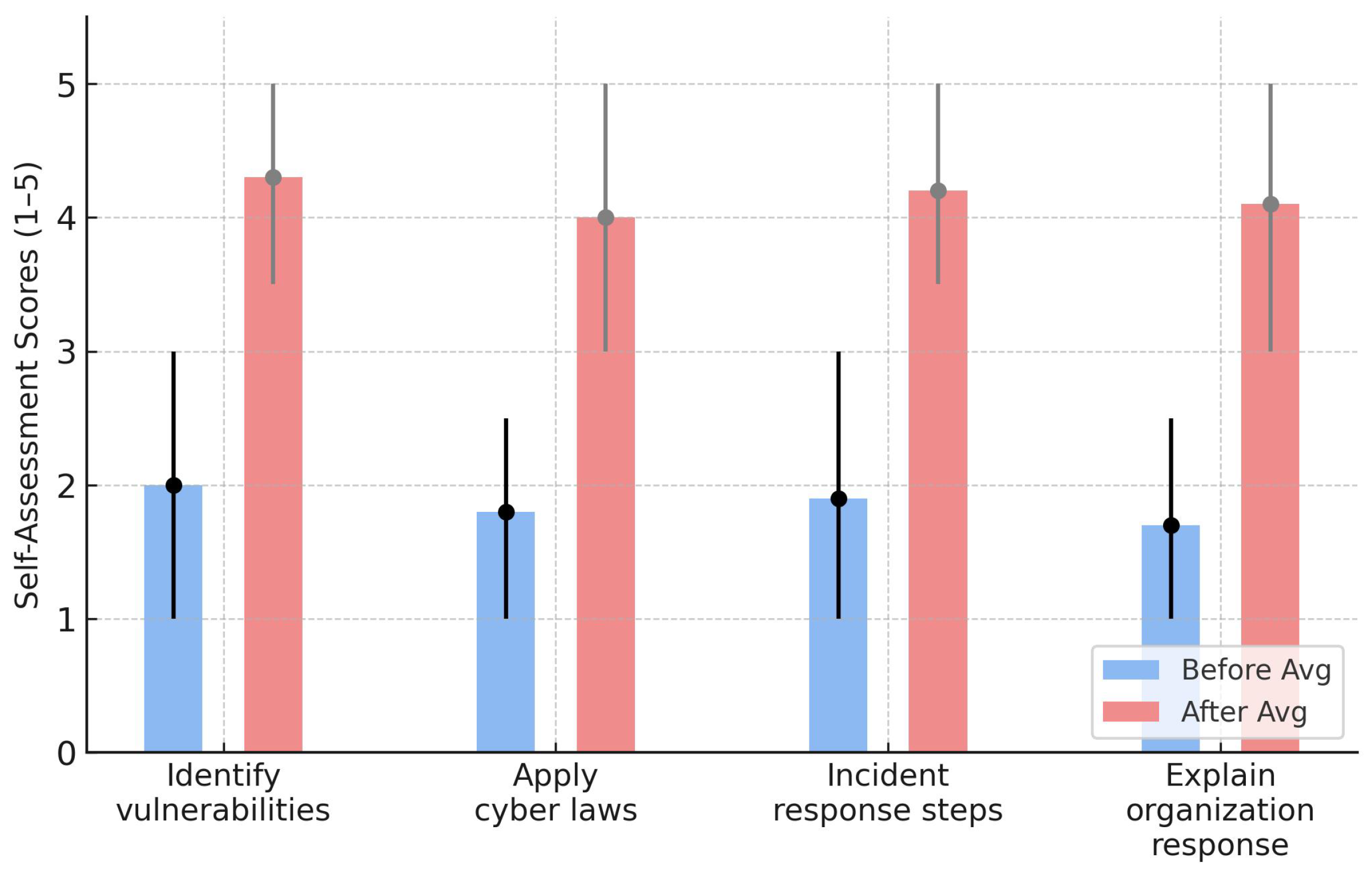
6.2.1. Self Knowledge Assessment
6.2.2. Threats Targeting SMBs
6.2.3. Technical and Legal Understanding
6.2.4. Scenario-Based Learning Model
6.2.5. Practical Experience and Skills
6.3. Students’ Course Evaluation
6.3.1. Course Evaluation from CS Students
6.3.2. Course Evaluation from Law Students
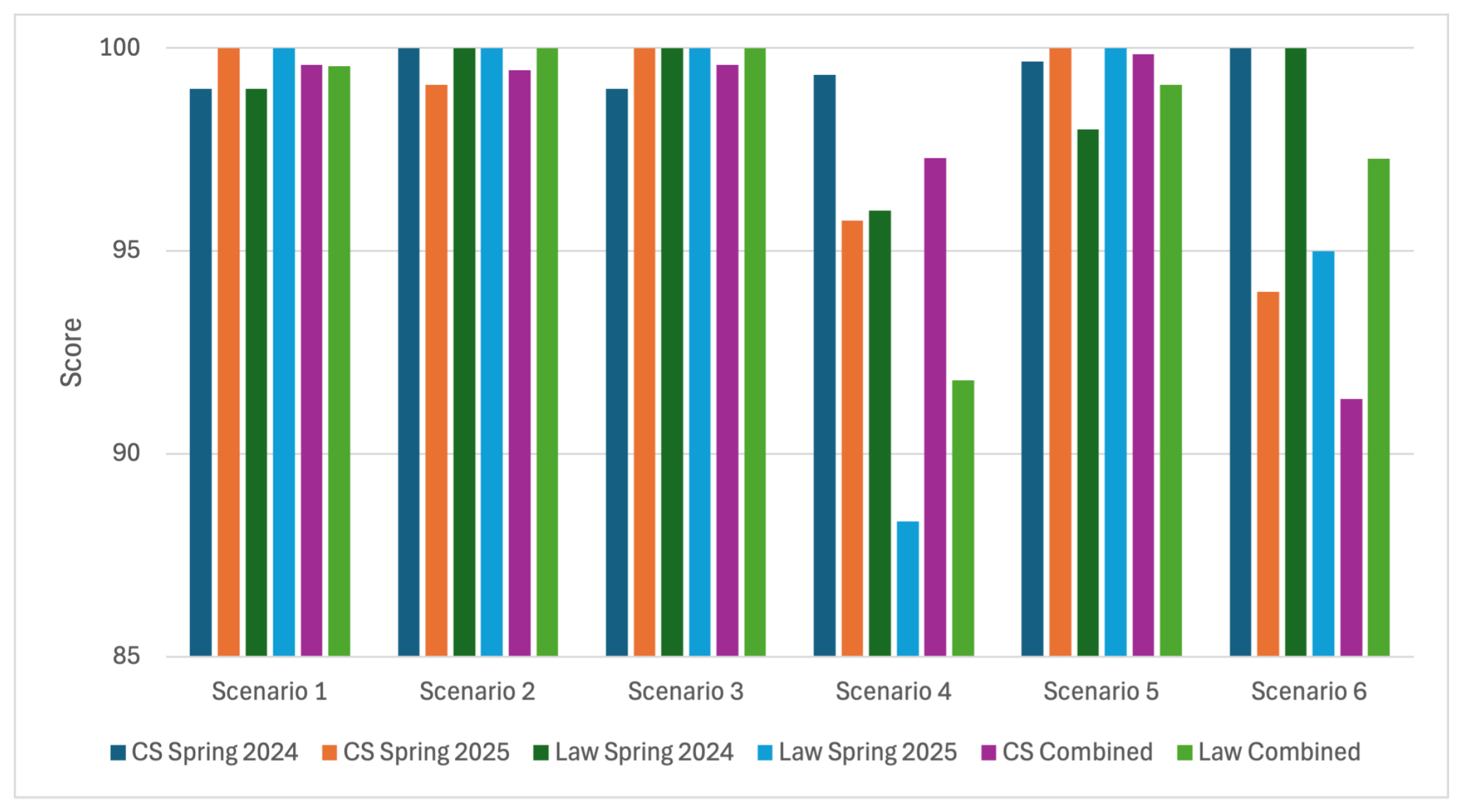
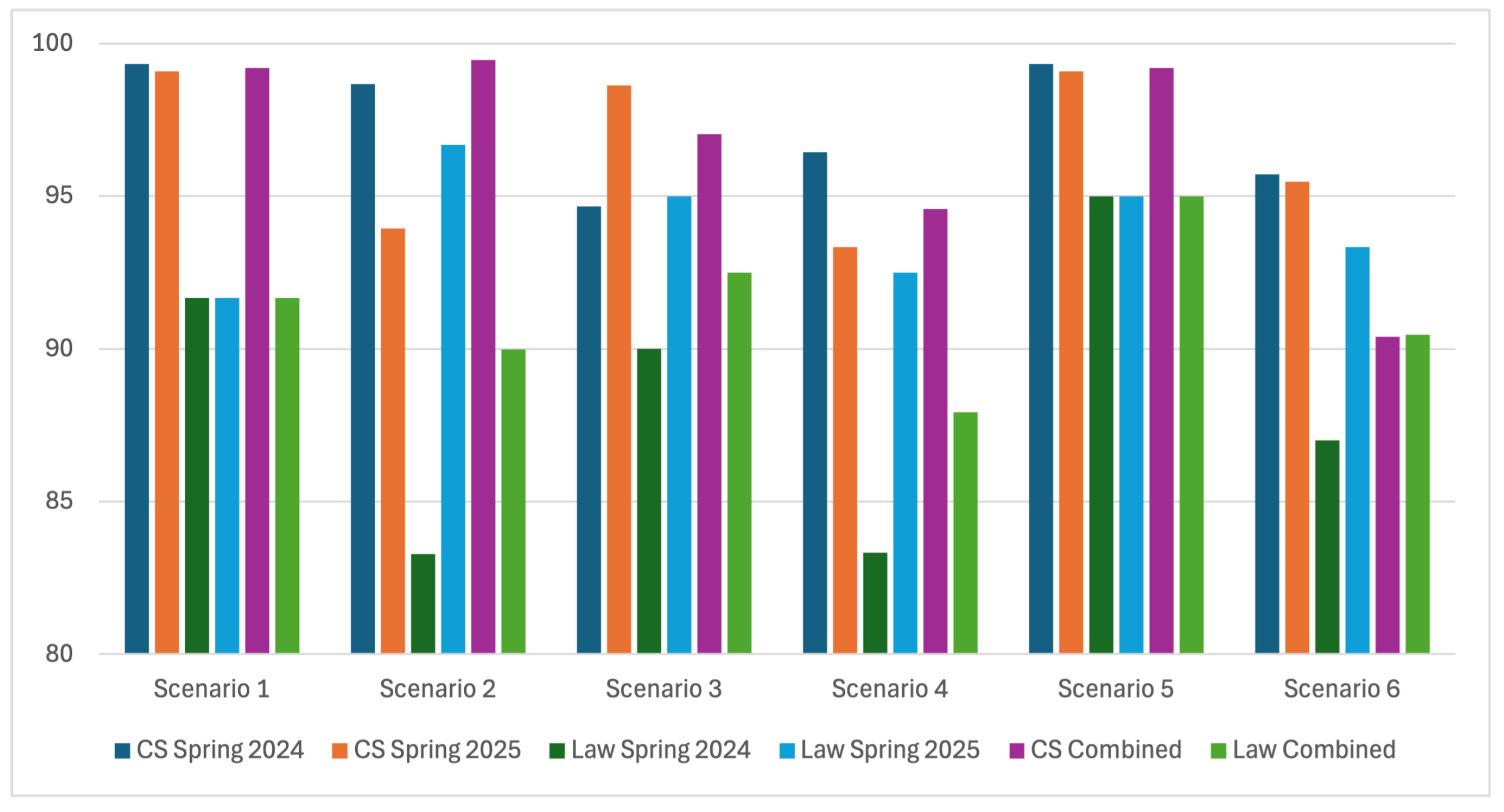
6.4. Students’ Performance
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Hiscox Group. Cyber Readiness Report 2024; Technical Report; Hiscox Group: Hamilton, Bermuda, 2024. [Google Scholar]
- Ponemon Institute; IBM Security. Cost of a Data Breach Report 2024; Technical Report; IBM: Armonk, NY, USA, 2024. [Google Scholar]
- Dojkovski, S.; Lichtenstein, S.; Warren, M.J. Fostering Information Security Culture in Small and Medium Size Enterprises: An Interpretive Study in Australia. In Proceedings of the 2007 European Conference on Information System (ECIS), St. Gallen, Switzerland, 7–9 June 2007; pp. 1560–1571. [Google Scholar]
- Paulsen, C. Cybersecuring Small Businesses. Computer 2016, 49, 92–97. [Google Scholar] [CrossRef]
- U.S. Small Business Administration, Office of Advocacy. 2024 Small Business Profile: United States; Technical Report; U.S. Small Business Administration: Washington, DC, USA, 2024.
- Raghavan, A.V.; Yu, C. Task, Knowledge, Skill, and Ability: Equipping the Small-Medium Businesses Cybersecurity Workforce. In Proceedings of the 2024 ASEE Annual Conference & Exposition, American Society for Engineering Education, Portland, OR, USA, 3 June 2024. [Google Scholar]
- Newhouse, W.D.; Keith, S.; Scribner, B.; Witte, G.A. National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework; Special Publication NIST SP 800-181; National Institute of Standards and Technology (NIST): Gaithersburg, MA, USA, 2017. [CrossRef]
- Brilingaitė, A.; Bukauskas, L.; Juozapavičius, A. A framework for competence development and assessment in hybrid cybersecurity exercises. Comput. Secur. 2020, 88, 101607. [Google Scholar] [CrossRef]
- Ghosh, T.; Francia, G. Assessing Competencies Using Scenario-Based Learning in Cybersecurity. J. Cybersecur. Priv. 2021, 1, 539–552. [Google Scholar] [CrossRef]
- Joint Task Force on Cybersecurity Education. Cybersecurity 2017 Version 1.0: Curriculum Guidelines for Post-Secondary Degree Programs in Cybersecurity; Technical Report; Association for Computing Machinery (ACM): New York, NY, USA; IEEE Computer Society (IEEE-CS): Piscataway, NJ, USA; Association for Information Systems SIGSEC: Atlanta, GA, USA, 2017. [Google Scholar]
- Shivapurkar, M.; Bhatia, S.; Ahmed, I. Problem-Based Learning for Cybersecurity Education. J. Colloq. Inf. Syst. Secur. Educ. 2020, 7, 6. [Google Scholar]
- Clark, R. Accelerating Expertise with Scenario-Based Learning; Learning Blueprint/American Society for Training and Development: Merrifield, VA, USA, 2009. [Google Scholar]
- Savery, J.R. Overview of Problem-Based Learning: Definitions and Distinctions. Interdiscip. J.-Probl.-Based Learn. 2006, 9, 5–15. [Google Scholar] [CrossRef]
- NICE Challenge Project. 2014. Available online: https://www.nice-challenge.com/ (accessed on 4 October 2025).
- Cowan, C.; Arnold, S.; Beattie, S.; Wright, C.; Viega, J. Defcon Capture the Flag: Defending Vulnerable Code from Intense Attack. In Proceedings of the DARPA Information Survivability Conference and Exposition (DISCEX III), Washington, DC, USA, 22–24 April 2003; pp. 120–124. [Google Scholar] [CrossRef]
- Cheung, R.S.; Cohen, J.P.; Lo, H.Z.; Elia, F. Challenge-Based Learning in Cybersecurity Education. In Proceedings of the 2011 International Conference on Security & Management (SAM 2011), Las Vegas, NV, USA, 18–21 July 2011; Volume 1. [Google Scholar]
- Wagner, P.J.; Wudi, J.M. Designing and Implementing a Cyberwar Laboratory Exercise for a Computer Security Course. In Proceedings of the 35th SIGCSE Technical Symposium on Computer Science Education, SIGCSE ’04, Norfolk, VA, USA, 3–7 March 2003; Association for Computing Machinery: New York, NY, USA, 2004; pp. 402–406. [Google Scholar] [CrossRef]
- Doupe, A.; Egele, M.; Caillat, B.; Stringhini, G.; Yakin, G.; Zand, A.; Cavedon, L.; Vigna, G. Hit’em Where It Hurts: A Live Security Exercise on Cyber Situational Awareness. In Proceedings of the 27th Annual Computer Security Applications Conference ACSAC ’11, New York, NY, USA, 5–9 December 2011; pp. 51–61. [Google Scholar] [CrossRef]
- Ohio Cyber Range Institute. Available online: https://www.ohiocyberrangeinstitute.org (accessed on 4 October 2025).
- NIST. National Initiative for Cybersecurity Education (NICE)—The National Cybersecurity Workforce Framework; NIST: Gaithersburg, MA, USA, 2017.
- National Institute of Standards and Technology. Workforce Framework for Cybersecurity (NICE Framework); Technical Report NIST SP 800-181r1; Revision 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. ISO: Geneva, Switzerland, 2022.
- Barrett, M. Framework for Improving Critical Infrastructure Cybersecurity Version 1.1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [CrossRef]
- Freund, J.; Jones, J. Measuring and Managing Information Risk: A FAIR Approach; Butterworth-Heinemann: Oxford, UK, 2014. [Google Scholar]
- Chidukwani, A.; Zander, S.; Koutsakis, P. A Survey on the Cyber Security of Small-to-Medium Businesses: Challenges, Research Focus and Recommendations. IEEE Access 2022, 10, 85701–85719. [Google Scholar] [CrossRef]
- Osborn, E.; Simpson, A. Risk and the Small-Scale Cyber Security Decision Making Dialogue—A UK Case Study. Comput. J. 2017, 61, 472–495. [Google Scholar] [CrossRef]
- Organisation for Economic Co-Operation and Development (OECD). OECD Glossary of Statistical Terms–Small and Medium-Sized Enterprises (SMEs) Definition; OECD: Washington, DC, USA, 2008. [Google Scholar]
- Petersen, R.; Santos, D.; Wetzel, K.A.; Smith, M.C.; Witte, G. Workforce Framework for Cybersecurity (NICE Framework); Technical Report; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2020.
- Kim, K.; Smith, J.; Yang, T.A.; Kim, D.J. An Exploratory Analysis on Cybersecurity Ecosystem Utilizing the NICE Framework. In Proceedings of the 2018 National Cyber Summit (NCS), Huntsville, AL, USA, 5–7 June 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Bada, M.; Nurse, J.R.C. Developing cybersecurity education and awareness programmes for small- and medium-sized enterprises (SMEs). Inf. Comput. Secur. 2019, 27, 393–410. [Google Scholar] [CrossRef]
- Tobey, D.; Watkins, A.; O’Brien, C. Applying Competency-Based Learning Methodologies to Cybersecurity Education and Training: Creating a Job-Ready Cybersecurity Workforce. Infragard J. 2018, 1, 1–14. [Google Scholar]
- Wetzel, K. NICE Framework Competencies: Assessing Learners for Cybersecurity Work; Technical Report; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2021.
- Verizon. 2022 Data Breach Investigations Report; Technical Report; Verizon: New York, NY, USA, 2022. [Google Scholar]
- Ponemon Institute. 2019 Global State of Cybersecurity in Small and Medium-Sized Businesses; Technical Report; Ponemon Institute: Traverse City, MI, USA, 2019. [Google Scholar]
- CISA. CISA INSIGHTS; CISA: Washington, DC, USA, 2019.
- Hiscox Group. Cyber Readiness Report 2022; Technical Report; Hiscox Group: Pembroke, Bermuda, 2022. [Google Scholar]
- ENISA. Cybersecurity for SMEs—Challenges and Recommendations; Technical Report; ENISA: Heraklion, Greece, 2021.
- ENISA. ENISA Threat Landscape 2020—Web-Based Attacks; Technical Report; ENISA: Heraklion, Greece, 2022.
- ENISA. ENISA Threat Landscape 2020—List of Top 15 Threats; Technical Report; European Union Agency for Cybersecurity (ENISA): Heraklion, Greece, 2020.
- Campos, R.; Mangaravite, V.; Pasquali, A.; Jorge, A.; Nunes, C.; Jatowt, A. YAKE! Keyword extraction from single documents using multiple local features. Inf. Sci. 2020, 509, 257–289. [Google Scholar] [CrossRef]
- CISA. Capacity Enhancement Guide: Counter-Phishing Recommendations for Non-Federal Organizations; CISA: Washington, DC, USA, 2021.
- CISA. Capacity Enhancement Guide: Counter-Phishing Recommendations for Federal Organizations; CISA: Washington, DC, USA, 2021.
- Cybersecurity and Infrastructure Security Agency (CISA). Website Security; CISA: Washington, DC, USA, 2021.
- Australian Cyber Security Centre (ACSC). Ransomware Prevention Guide; Technical Report; Australian Cyber Security Centre: Canberra, Australia, 2022.
- National Cyber Security Centre (NCSC). Mitigating Malware and Ransomware Attacks; National Cyber Security Centre (NCSC): London, UK, 2021.
- Souppaya, M.; Scarfone, K. Guide to Malware Incident Prevention and Handling for Desktops and Laptops; Technical Report; National Institute of Standards and Technology (NIST): Gaithersburg, MD, USA, 2013.
- European Union Agency for Cybersecurity (ENISA). ENISA Threat Landscape 2020—Web-Based Attacks; Technical Report; European Union Agency for Cybersecurity: Heraklion, Greece, 2020.
- Federal Trade Commission (FTC). Cybersecurity for Small Business: Phishing; Technical Report; Federal Trade Commission: Washington, DC, USA, 2018. [Google Scholar]
- Cybersecurity and Infrastructure Security Agency (CISA). Guidance for Managed Service Providers and Small- and Mid-Sized Businesses; Technical Report; Cybersecurity and Infrastructure Security Agency: Washington, DC, USA, 2021.
- Chen, C. Science Mapping: A Systematic Review of the Literature. J. Data Inf. Sci. 2017, 2, 1–40. [Google Scholar] [CrossRef]
- Yoon, B.; Lee, S.; Lee, G. Development and application of a keyword-based knowledge map for effective R&D planning. Scientometrics 2010, 85, 803–820. [Google Scholar] [CrossRef]
- Fakhar Manesh, M.; Pellegrini, M.M.; Marzi, G.; Dabic, M. Knowledge Management in the Fourth Industrial Revolution: Mapping the Literature and Scoping Future Avenues. IEEE Trans. Eng. Manag. 2021, 68, 289–300. [Google Scholar] [CrossRef]
- Sun, C.; Hu, L.; Li, S.; Li, T.; Li, H.; Chi, L. A Review of Unsupervised Keyphrase Extraction Methods Using Within-Collection Resources. Symmetry 2020, 12, 1864. [Google Scholar] [CrossRef]
- Levenshtein, V.I. Binary codes capable of correcting deletions, insertions, and reversals. Sov. Phys.-Dokl. 1965, 10, 8. [Google Scholar]
- Winkler, W.E. String Comparator Metrics and Enhanced Decision Rules in the Fellegi-Sunter Model of Record Linkage; Technical Report; Educational Resources Information Center (ERIC): Washington, DC, USA, 1990. [Google Scholar]
- Hamming, R.W. Error detecting and error correcting codes. Bell Syst. Tech. J. 1950, 29, 147–160. [Google Scholar] [CrossRef]
- Prasetya, D.D.; Wibawa, A.P.; Hirashima, T. The performance of text similarity algorithms. Int. J. Adv. Intell. Inform. 2018, 4, 63–69. [Google Scholar] [CrossRef]
- National Initiative for Cybersecurity Careers and Studies (NICCS). NICE Framework Keyword Search. Available online: https://niccs.cisa.gov/tools/nice-framework (accessed on 4 October 2025).
- Bada, M.; Sasse, A.M.; Nurse, J.R.C. Cyber Security Awareness Campaigns: Why do they fail to change behaviour? arXiv 2019, arXiv:1901.02672. [Google Scholar] [CrossRef]
- Shojaifar, A.; Fricker, S.A.; Gwerder, M. Automating the Communication of Cybersecurity Knowledge: Multi-case Study. In Proceedings of the Information Security Education. Information Security in Action, Maribor, Slovenia, 21–23 September 2020; Springer International Publishing: Cham, Switzerland, 2020; pp. 110–124. [Google Scholar]
- Schaffer, S.; Chen, X. Cross-Disciplinary Team Learning: Assessment Guidelines. In Proceedings of the EPICS Annual Conference on Service-Learning in Engineering and Computing, Austin, TX, USA, 3–4 August 2009. [Google Scholar]
- Global Investigations Review. The Guide to Cybersecurity Investigations, 2nd ed.; Global Investigations Review: London, UK, 2021; Available online: https://globalinvestigationsreview.com/guide/the-guide-cyber-investigations-archived/first-edition/article/the-cyber-threat-landscape (accessed on 4 October 2025).
- Chesney, R. Cybersecurity Law, Policy, and Institutions (Version 3.1); Technical Report; SSRN: Rochester, NY, USA, 2021. [Google Scholar]
- Darknet Diaries. Russia vs. Ukraine: The Biggest Cyber Attack Ever. Darknet Diaries Ep. 54: NotPetya. Available online: https://www.youtube.com/watch?v=N20q-ZMop0w (accessed on 4 October 2025).
- The Sedona Conference. Incident Response Guide. 2020. Available online: https://www.thesedonaconference.org/sites/default/files/publications/IncidentResponseGuide.pdf (accessed on 4 October 2025).
- WannaCry: The World’s Largest Ransomware Attack. Video, YouTube. 2021. Available online: https://www.youtube.com/watch?v=PKHH_gvJ_hA (accessed on 4 October 2025).
- WannaCry Ransomware CyberAttack Raises Legal Issues. The National Law Review, 22 May 2017. Available online: https://natlawreview.com/article/wannacry-ransomware-cyberattack-raises-legal-issues (accessed on 4 October 2025).
- Schmitt, M.; Fahey, S. WannaCry and the International Law of Cyberspace. Just Security, 22 December 2017. Available online: https://www.justsecurity.org/50038/wannacry-international-law-cyberspace/ (accessed on 4 October 2025).
- Hooked By Phisherman: Quarterbacking Breach Response with Law Enforcement. Presentation at RSA Conference. 2021. Available online: https://www.rsaconference.com/library/Presentation/USA/2021/hooked-by-phisherman-quarterbacking-breach-response-with-law-enforcement (accessed on 4 October 2025).
- Global Investigations Review. The Guide to Cybersecurity Investigations, 3rd ed.; Global Investigations Review: London, UK, 2023; Available online: https://globalinvestigationsreview.com/guide/the-guide-cyber-investigations/third-edition (accessed on 4 October 2025).
- BakerHostetler. U.S. Data Breach Notification Law Interactive Map. Available online: https://www.bakerlaw.com/us-data-breach-interactive-map/ (accessed on 4 October 2025).
- Kroah-Hartman, G. Keynote: Spectre, Meltdown, & Linux. Video, The Linux Foundation/YouTube. 2018. Available online: https://www.youtube.com/watch?v=lQZzm9z8g_U (accessed on 4 October 2025).
- Simpson, A.P.; Solomon, A.H. Complying with Breach Notification Obligations in a Global Setting: A Legal Perspective. In The Guide to Cyber Investigations, 3rd ed.; Global Investigations Review: London, UK, 2019; pp. 45–54. [Google Scholar]
- Celerium. The Complete Guide to Understanding Cybersecurity Frameworks. Available online: https://www.celerium.com/cybersecurity-frameworks-a-comprehensive-guide (accessed on 4 October 2025).
- Thomson Reuters. Performing Data Security Risk Assessments Checklist. Practical Law/Thomson Reuters. 2018. Available online: https://mena.thomsonreuters.com/content/dam/ewp-m/documents/mena/en/pdf/other/data-security-risk-assessments-checklist-thomson-reuters.pdf (accessed on 4 October 2025).
- Basu, A.; Grover, G. Scenario 24: Internet Blockage; International Cyber Law Toolkit, NATO Cooperative Cyber Defence Centre of Excellence; NATO Cooperative Cyber Defence Centre of Excellence: Tallinn, Estonia, 2021. [Google Scholar]
- RSA Conference. Cyber and Modern Conflict: The Changing Face of Modern Warfare. Session Presented at RSA Conference. 7 June 2022. Available online: https://www.rsaconference.com (accessed on 4 October 2025).
- Kushner, D. The Hacker Who Cared Too Much. Rolling Stone, 29 June 2017. Available online: https://www.rollingstone.com/culture/culture-features/the-hacker-who-cared-too-much-196425/ (accessed on 4 October 2025).
- Darknet Diaries. Ep. 14: OpJustina. YouTube Video. 2021. Available online: https://www.youtube.com/watch?v=0qvBYj7F3jo&list=PLtN43kak3fFEEDNo0ks9QVKYfQpT2yUEo&index=14 (accessed on 4 October 2025).
- Computer Fraud and Abuse Act (CFAA). YouTube Video. 2020. Available online: https://www.youtube.com/watch?v=cPr6hZfoBfQ (accessed on 4 October 2025).
- Burt, T. Microsoft Takes Court Action Against Fourth Nation-State Cybercrime Group. Microsoft (On the Issues Blog). 30 December 2019. Available online: https://blogs.microsoft.com/on-the-issues/2019/12/30/microsoft-court-action-against-nation-state-cybercrime/ (accessed on 4 October 2025).
- Microsoft Corporation. Complaint for Civil Action No. 1:19-cv-01582 (LO/JFA). United States District Court for the Eastern District of Virginia, Alexandria Division, 2019. Available online: https://noticeofpleadings.com/thallium/files/FINAL%20COMPLAINT.pdf (accessed on 27 July 2025).
- The CyberWire. Taking Down Thallium. YouTube Video. 2020. Available online: https://www.youtube.com/watch?v=jGC-UwKVkYc (accessed on 4 October 2025).
- Lubin, A.; Marinotti, E. Why Current Botnet Takedown Jurisprudence Should Not Be Replicated. Lawfare. 2024. Available online: https://www.lawfaremedia.org/article/why-current-botnet-takedown-jurisprudence-should-not-be-replicated (accessed on 4 October 2025).
- Microsoft. Microsoft Security Bulletin, (n.d.). Available online: https://learn.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17-010 (accessed on 4 October 2025).
- U.S. Congress. Health Insurance Portability and Accountability Act of 1996; Enacted by the 104th U.S. Congress on August 21, 1996; U.S. Congress: Washington, DC, USA, 1996. [Google Scholar]
- Meltdown and Spectre, (n.d.). Available online: https://meltdownattack.com/ (accessed on 4 October 2025).
- Powell, B.A.; Mercer, S.T. (Eds.) The Guide to Cyber Investigations, 3rd ed.; Global Investigations Review: London, UK, 2023. [Google Scholar]
- McInnes, N.; Wills, G. The VoIP PBX Honeypot Advance Persistent Threat Analysis. In Proceedings of the 6th International Conference on Internet of Things, Big Data and Security, Online, 23–25 April 2021; pp. 70–80. [Google Scholar] [CrossRef]
- Khan, S.; Sadiq, N. Design and configuration of VoIP based PBX using asterisk server and OPNET platform. In Proceedings of the 2017 International Electrical Engineering Congress (iEECON), Pattaya, Thailand, 8–10 March 2017; pp. 1–4. [Google Scholar] [CrossRef]
- U.S. Congress. Computer Fraud and Abuse Act, 1986; 18 U.S. Code § 1030; U.S. Congress: Washington, DC, USA, 1986. [Google Scholar]
- U.S. Congress. 18 U.S. Code § 1343—Fraud by Wire, Radio, or Television, 1952; United States Code, Title 18, Section 1343; U.S. Congress: Washington, DC, USA, 1952. [Google Scholar]
- U.S. Congress. 18 U.S. Code § 1028—Fraud and Related Activity in Connection with Identification Documents, Authentication Features, and Information, 1982; United States Code, Title 18, Section 1028; U.S. Congress: Washington, DC, USA, 1982. [Google Scholar]
- Cherubin, G.; Jansen, R.; Troncoso, C. Online Website Fingerprinting: Evaluating Website Fingerprinting Attacks on Tor in the Real World. In Proceedings of the 31st USENIX Security Symposium (USENIX Security 22), Boston, MA, USA, 10–12 August 2022; pp. 753–770. [Google Scholar]
- The Tcpdump Group. tcpdump—A Powerful Command-Line Packet Analyzer; The Tcpdump Group. 2024. Available online: https://www.tcpdump.org/ (accessed on 4 October 2025).
- Kumarasamy, S.; Ramasamy, A. Distributed Denial of Service (DDOS) Attacks Detection Mechanism. Int. J. Comput. Sci. Eng. Inf. Technol. 2012, 5, 39–49. [Google Scholar] [CrossRef]
- htr tech. Zphisher: Automated Phishing Tool with 30+ Templates; HTR Tech: Calgary, AB, Canada, 2025. [Google Scholar]
- ngrok, Inc. ngrok—Secure Introspectable Tunnels to Localhost; ngrok, Inc.: San Francisco, CA, USA, 2025. [Google Scholar]







| Publisher | Document |
|---|---|
| Verizon | Data Breach Investigation Report (DBIR) 2022 [33] |
| Ponemon Institute | Ponemon Institute 2019 Global State of Cybersecurity in Small to Medium-sized Businesses [34] |
| CISA | CISA Insights [35] |
| Hiscox Group | Hiscox Cyber Readiness Report 2022 [36] |
| ENISA | Cybersecurity for SMEs—Challenges and Recommendations [37] |
| ENISA Threat Landscape: List of top 15 threats [38] |
| Publisher | Document | Attack Vector |
|---|---|---|
| CISA | Capacity Enhancement Guide: Counter-phishing recommendations for Non-Federal Organizations [41] | PSE MR WB |
| Capacity Enhancement Guide: Counter-phishing recommendations for Federal Organizations [42] | ||
| CISA Website Security [43] | ||
| CISA Ransomware Guide [35] | ||
| ACSC | ACSC Ransomware Prevention and Protection Guide [44] | MR |
| NCSC | NCSC Mitigating Malware and Ransomware Attacks [45] | MR |
| NIST | NIST SP 800-83r1: Guide to Malware | MR |
| Incident Prevention and Handling for Desktops and Laptops [46] | ||
| ENISA | ENISA Threat Landscape 2020—Web-based Attacks [47] | WB |
| FTC | Cybersecurity for Small Businesses: Phishing [48] | PSE |
| CISA | CISA Insights: Mitigations and hardening guidance from MSPs and Small and Mid-Sized Businesses [49] | MR |
| Keyword | Score (S) | After De-Duplication |
|---|---|---|
| Secure Gateway Capabilities | 0.0023 | |
| Stop Phishing Emails | 0.0090 | Removed |
| Secure email gateways | 0.0102 | |
| Gateway Capabilities | 0.0132 | Removed |
| Secure Gateway | 0.0345 | Removed |
| Gateways | 0.1013 | |
| Email filter solution | 0.1434 | |
| Signatures and blocklists | 0.1481 | Removed |
| Host Level Protections | 0.1710 |
| TKSA Number | TKSA Description | PSE | MR | WB |
|---|---|---|---|---|
| K0001 | Knowledge of computer networking concepts and protocols, and network security methodologies. | * | ||
| K0002 | Knowledge of risk management processes (e.g., methods for assessing and mitigating risk). | * | * | * |
| K0004 | Knowledge of cybersecurity and privacy principles. | * | * | * |
| K0005 | Knowledge of cyber threats and vulnerabilities. | * | * | * |
| K0007 | Knowledge of authentication, authorization, and access control methods. | * | * | * |
| K0013 | Knowledge of cyber defense and vulnerability assessment tools and their capabilities. | * | * | * |
| K0033 | Knowledge of host/network access control mechanisms (e.g., access control list, capabilities lists). | * | ||
| K0038 | Knowledge of cybersecurity and privacy principles used to manage risks related to the use, processing, storage, and transmission of information or data. | * |
| TKSA Number | TKSA Description | PSE | MR | WB |
|---|---|---|---|---|
| K0003 | Knowledge of laws, regulations, policies, and ethics as they relate to cybersecurity and privacy. | * | * | * |
| K0006 | Knowledge of specific operational impacts of cybersecurity lapses. | * | * | * |
| K0066 | Knowledge of Privacy Impact Assessments. | * | * | * |
| K0098 | Knowledge of the cyber defense Service Provider reporting structure and processes within one’s own organization. | * | * | * |
| K0101 | Knowledge of the organization’s enterprise information technology (IT) goals and objectives. | * | * | * |
| K0107 | Knowledge of Insider Threat investigations, reporting, investigative tools and laws/regulations. | * | * | * |
| K0123 | Knowledge of legal governance related to admissibility (e.g. Rules of Evidence). | * | * | * |
| K0126 | Knowledge of Supply Chain Risk Management Practices (NIST SP 800-161) | * |
| Week | Topic | Lab | Readings | Videos/ Assignment/ Quiz |
|---|---|---|---|---|
| 1 | Introduction |
|
| |
| 2 | Ransomware Investigations | EternalBlue |
|
|
| 3 | Ransomware Investigations | EternalBlue |
|
|
| 4 | Data Breach Notification Laws | Meltdown/ Spectre |
|
|
| 5 | Data Breach Notification Laws | Meltdown/ Spectre |
|
|
| 6 | Cybersecurity Risk Assessments | PBX Hacking |
|
|
| 7 | Cybersecurity Risk Assessments | PBX Hacking |
|
|
| 8 | International Law Issues | Website Fingerprinting |
|
|
| 9 | Spring Break | |||
| 10 | International Law Issues | Website Fingerprinting |
|
|
| 11 | Criminal Law | #OPJustina: DDoS |
|
|
| 12 | Criminal Law | #OPJustina: DDoS |
|
|
| 13 | Nation-State Cybercrime | Thallium |
|
|
| 14 | Nation-State Cybercrime | Thallium |
|
|
| Attack Vector | Scenarios | Non-Technical TKSAs |
|---|---|---|
| MR | Scenario 1 Scenario 2 | K0003, K0006, K0098, K0101, K0123, K0150, K0264, K0287, K0315, K0351, K0429, K0504, K0511, K0524, K0585, A0009, A0033, A0046, A0110, A0113, A0115, A0146 |
| WB | Scenario 3 Scenario 4 | K0003, K0006, K0098, K0101, K0123, K0150, K0264, K0287, K0315, K0351, K0429, K0504, K0511, K0524, K0585, A0033, A0046, A0110, A0113, A0115, A0146 |
| PSE | Scenario 5 Scenario 6 | K0003, K0006, K0098, K0101, K0123, K0150, K0264, K0287, K0315, K0351, K0429, K0504, K0511, K0524, K0585, S0085, S0213, S0219, S0232, S0361, T0099, T0280, A0033, A0046, A0110, A0113, A0115, A0146 |
| Attack Vector | Scenarios | Technical TKSAs |
|---|---|---|
| MR | Scenario 1 Scenario 2 | K0002, K0004, K0005, K0007, K0013, K0038, K0046, K0049, K0070, K0073, K0074, K0104, K0135, K0176, K0188, K0189, K0205, K0210, K0260, K0261, K0274, K0368, K0392, K0480, K0516, K0536, K0624, K0626, K0627, S0001, S0022, S0076, S0084, S0121, S0192, S0264, S0298, T0056, T0161, T0181, T0271, T0438, T0553, T0751, A0010, A0062 |
| WB | Scenario 3 Scenario 4 | K0001, K0002, K0004, K0005, K0013, K0033, K0046, K0049, K0056, K0058, K0062, K0070, K0100, K0104, K0131, K0176, K0189, K0202, K0332, K0392, K0427, K0452, S0001, S0004, S0022, S0046, S0076, S0084, S0121, S0192, S0258, S0264, T0023, T0161, T0271, T0438, T0553, A0176 |
| PSE | Scenario 5 Scenario 6 | K0002, K0004, K0005, K0007, K0013, K0046, K0049, K0104, K0131, K0202, K0205, K0210, K0260, K0274, K0336, K0368, K0392, K0452, S0022, S0076, S0084, S0121, S0192, T0056, T0271, T0438, T0553, A0063, A0119, A0123, A0176 |
| Scenarios | Scenario Description (Part 1) | Topics Illustrated (Part 2) |
|---|---|---|
| #1 EternalBlue (Week 2–3) | Ransomware attack exploited the vulnerabilities in Windows OS, affecting online services of numerous cities including Baltimore (2019). Earlier, NSA discovered the vulnerabilities but did not report to Microsoft. Experiment with the VirtualBox environment. | Non-technical topics: Data breach notification laws; identifying technical “triggers” for reporting; role of law enforcement; data privacy laws. Technical topics: Basic security concepts (confidentiality, integrity, and availability); Encryption; Malware (Virus, Trojan); Hardening OS. |
| #2 Meltdown/Spectre (Week 4–5) | In 2015, Google’s Project Zero team discovered a hardware vulnerability, affecting a wide range of systems running iOS, Linux, macOS, and Windows. Software workaround has been assessed as slowing computers between 5∼30%, although companies responsible for software correction of the exploit are reporting minimal impact from general benchmark testing. | Non-technical topics: Legal responsibility/liability for hardware vulnerabilities; legal analysis of when to disclose vulnerabilities. Technical topics: Hardware security (hardware trojan, reverse engineering, side channel attacks); IoT security. |
| #3 PBX Hacking (Week 6–7) | A cyber-criminal, who is on the Interpol and the FBI’s most wanted list, was arrested (2015). He let other people’s phones dialed pay-per-minute numbers that they owned, making money. Experiment with FreePBX system inside VirtualBox. | Non-technical topics: Challenges in addressing low-level cybercrime; limits of law enforcement. Technical topics: Access control (firewalls, ports, authentication, etc.), Voice over IP (VoIP). |
| #4 Website Fingerprinting Attack (Week 8–9) | Internet censorship is on the rise. It allows a state agency to block the information flow to and from a black-listed websites. Experiment to show the distinguishable traffic pattern when visiting websites. | Non-technical topics: Internet censorship laws; legal and ethical issues in compliance. Technical topics: Computer network protocols including HTTP; VPN; Anonymous networks (Tor); Machine learning/AI. |
| #5 #OpJustina: DDoS Attack (Week 10–11) | DDoS attack on Boston Children’s Hospital (2013) disrupting the hospital’s day-to-day operations. Attacker gains control of a network of online machines and directs them to send requests to the target. Experiment within the Ohio Cyber Range virtual machine (VM). | Non-technical topics: Computer Fraud and Abuse Act; legal reform to address cybercrime. Technical topics: Network security concepts; Anomaly detection. |
| #6 Hacking Group Thallium (Week 12–13) | The US District Court for the Eastern District of Virginia unsealed documents related to a lawsuit filed by Microsoft against the cybercrime group Thallium (2019). It used malware to compromise systems and steal data, then create fake email addresses to launch phishing attacks to individual employees of the organization. | Non-technical topics: Cybercrime laws; practical and legal challenges in attribution; laws and procedures for shutting down servers used for cybercrime. Technical topics: Ethical hacking; Phishing attacks; Identity theft; Social engineering. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
McGuan, C.; Vijaya Raghavan, A.; Mandapati, K.M.; Yu, C.; Ray, B.E.; Jackson, D.K.; Kumar, S. Bridging Cybersecurity Practice and Law: A Hands-On, Scenario-Based Curriculum Using the NICE Framework to Foster Skill Development. J. Cybersecur. Priv. 2025, 5, 106. https://doi.org/10.3390/jcp5040106
McGuan C, Vijaya Raghavan A, Mandapati KM, Yu C, Ray BE, Jackson DK, Kumar S. Bridging Cybersecurity Practice and Law: A Hands-On, Scenario-Based Curriculum Using the NICE Framework to Foster Skill Development. Journal of Cybersecurity and Privacy. 2025; 5(4):106. https://doi.org/10.3390/jcp5040106
Chicago/Turabian StyleMcGuan, Colman, Aadithyan Vijaya Raghavan, Komala M. Mandapati, Chansu Yu, Brian E. Ray, Debbie K. Jackson, and Sathish Kumar. 2025. "Bridging Cybersecurity Practice and Law: A Hands-On, Scenario-Based Curriculum Using the NICE Framework to Foster Skill Development" Journal of Cybersecurity and Privacy 5, no. 4: 106. https://doi.org/10.3390/jcp5040106
APA StyleMcGuan, C., Vijaya Raghavan, A., Mandapati, K. M., Yu, C., Ray, B. E., Jackson, D. K., & Kumar, S. (2025). Bridging Cybersecurity Practice and Law: A Hands-On, Scenario-Based Curriculum Using the NICE Framework to Foster Skill Development. Journal of Cybersecurity and Privacy, 5(4), 106. https://doi.org/10.3390/jcp5040106






