Evaluating Privacy Technologies in Digital Payments: A Balanced Framework
Abstract
1. Introduction
2. Methodology
2.1. Designing the Evaluation Framework
2.2. Security
2.3. Privacy-Preserving Technical Measures—Privacy Enhancement Technologies (PETs)
- Anonymity: This criterion evaluates the extent to which the proposed PETs allow users to provide proof of authorization without revealing their identities.
- Unlinkability: A significant volume of metadata—including traffic analysis, timestamps, device information, and location data—may be generated during financial transactions. The primary objective of this criterion is to prevent the correlation of multiple payments to a single user, thereby safeguarding users from behavioral profiling [17,23].
- Forward and Backward Privacy: This criterion assesses two distinct options: forward privacy [24], which safeguards past transactions if present data are compromised, and backward privacy, which secures future transactions if current information is breached.
- Future Readiness: This criterion primarily addresses resistance to emerging threats such as quantum and artificial intelligence attacks. Privacy enhancement technologies in digital payment systems must proactively incorporate safeguards to mitigate future cybercrime risks.
2.4. Auditability
2.5. GDPR Compliance
- Purpose Limitation—Article 5(1)(b) of the GDPR: This criterion stipulates that personal data must be collected for specified, explicit, and legitimate purposes, and must not be further processed in ways that are incompatible with those purposes.
- Data Minimization—Article 5(1)(c) of the GDPR: This criterion pertains to data minimization, which is a fundamental principle for personal data processing. The main objective of the article is to ensure that only the data strictly necessary to achieve the intended purpose is collected and processed.
- Storage Limitation—Article 5(1)(e) of the GDPR: This criterion addresses the storage limitation principle. In accordance with this article, data must not be retained indefinitely. Justification for retention should be based on the specific processing purpose, and data should be securely erased once it is no longer required.
- Cross-Border Data Transfers—Art. 45 GDPR: This criterion pertains to the cross-border data transfers provision. The primary focus of this article is to delineate the conditions under which personal data may be transferred to countries outside the European Union.
2.6. Operational Constraints
- Interoperability: Interoperability within digital payment systems, in relation to privacy-enhancing technologies (PETs), denotes the capacity for various implementations to operate together across diverse platforms, organizations, and jurisdictions while maintaining privacy standards.
- Scalability: This metric allows our framework to assess the capacity for processing a high volume of transactions per second. By implementing PETs, financial systems can optimize throughput while maintaining robust privacy standards.
- Resource efficiency: Resource efficiency in digital payments involves achieving an optimal balance between robust privacy and security measures and minimizing computational, communication, and energy expenditures. It is essential to evaluate privacy-enhancing technologies (PETs) based on both their effectiveness in safeguarding privacy and their practical operational efficiency.
- Offline payment: Offline central bank digital currency (CBDC) [27], along with other digital payment systems, represents a form of digital currency that facilitates transactions without requiring a network connection. This approach functions similarly to cash, enabling exchanges to occur without third-party intervention. Settlement is finalized when the device subsequently reconnects to the network. The proposed introduction of CBDC from the European Central Bank (digital euro) may make such transactions possible in practice [6]. Offline payments can be implemented using near field communication (NFC), allowing queued transactions to be processed once an internet connection is available.
2.7. Demonstrating the Evaluation Framework
- Zero-Knowledge Proofs (ZKPs): This represents sophisticated privacy-enhancing technologies that facilitate information verification without revealing the underlying data. Mechanisms utilizing ZKPs are designed to protect both integrity and confidentiality, adhering to the principle of data minimization. Confidentiality is maintained so that, even if the network is breached, the core information stays protected. Moreover, proofs are verifiable, supporting transparency while auditing. However, the computational complexity associated with their implementation poses significant challenges for integration into large-scale, real-time payment and financial systems. Additionally, we should note that despite the high score for privacy, specific implementation limitations, such as latency or processing requirements, might affect real-world adoption.
- Anonymity-enhanced signatures: This technology delivers robust privacy and security by concealing the identity of the signer. These signatures safeguard confidentiality and data integrity and are designed for seamless interoperability. Nonetheless, they demand higher computational resources, and in specific circumstances, the signer’s identity may still be determined.
- Secret Sharing/Secure Multi-Party Computation (SMPC): This measure offers robust security and privacy by distributing data among participants, ensuring that disclosure occurs only through collaborative effort. Moreover, most SMPC protocols require multiple synchronous rounds of communication to ensure correctness and prevent leakage. However, this approach is constrained by efficiency challenges and demands higher computational resources.
2.8. Comparative Analysis of the Proposed Framework
3. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kahn, C.M. Payment Systems and Privacy. Fed. Reserve Bank St. Louis Rev. 2018, 100, 337–344. [Google Scholar] [CrossRef]
- Kahn, C.M.; McAndrews, J.; Roberds, W. Money Is Privacy. Int. Econ. Rev. 2005, 46, 377–399. [Google Scholar] [CrossRef]
- Anwar, M. Quantum-Resistant Cryptography: Developing Encryption Against Quantum Attacks. Available online: https://ssrn.com/abstract=5066160 (accessed on 16 August 2018).
- NIST Releases First 3 Finalized Post-Quantum Encryption Standards. Available online: https://www.nist.gov/news-events/news/2024/08/nist-releases-first-3-finalized-post-quantum-encryption-standards (accessed on 22 October 2025).
- Available online: https://www.bis.org/publ/othp88_system_design.pdf (accessed on 22 October 2025).
- Available online: https://www.ecb.europa.eu/euro/digital_euro/html/index.en.html (accessed on 22 October 2025).
- Available online: https://www.imf.org/en/Publications/fintech-notes (accessed on 22 October 2025).
- Ahnert, T.; Hoffmann, P.; Monnet, C. Payments and privacy in the digital economy. J. Financ. Econ. 2025, 169, 104050. [Google Scholar] [CrossRef]
- The Impact of Central Bank Digital Currency on Central Bank Profitability, Risk-Taking and Capital. Available online: https://www.ecb.europa.eu/pub/pdf/scpops/ecb.op360~35915b25bd.en.pdf (accessed on 22 October 2025).
- Adwani, A. The Evolution of Digital Payments: Implications for Financial Inclusion and Risk Management. Available online: https://ssrn.com/abstract=5201787 (accessed on 22 October 2025).
- Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of Such Data and Repealing Directive 95/46/EC (General Data Protection Regulation). Available online: http://data.europa.eu/eli/reg/2016/679/oj (accessed on 26 September 2025).
- Sahi, A.M.; Khalid, H.; Abbas, A.F.; Zedan, K.; Khatib, S.F.A.; Al Amosh, H. The Research Trend of Security and Privacy in Digital Payment. Informatics 2022, 9, 32. [Google Scholar] [CrossRef]
- Borgonovo, E.; Caselli, S.; Cillo, A.; Masciandaro, D.; Rabitti, G. Money, privacy, anonymity: What do experiments tell us? J. Financ. Stab. 2021, 56, 100934. [Google Scholar] [CrossRef]
- Manigonda, S. Data Privacy and Sovereignty in Financial Technology: Governance Strategies for Global Operations. IJSAT-Int. J. Sci. Technol. 2021, 12, 2021. [Google Scholar]
- Faisal, T.; Courtois, N.; Serguieva, A. The Evolution of Embedding Metadata in Blockchain Transactions. arXiv 2018, arXiv:1806.06738. Available online: https://ieeexplore.ieee.org/abstract/document/8489377 (accessed on 22 October 2025). [CrossRef]
- Balancing Confidentiality and Auditability in a Distributed Ledger Environment, STELLA–Joint Research Project of the European Central Bank and the Bank of Japan. 2020. Available online: https://www.ecb.europa.eu/press/intro/publications/pdf/ecb.miptopical200212.en.pdf (accessed on 22 October 2025).
- Bursuc, S.; Horne, R.; Mauw, S.; Yurkov, S. Provably Unlinkable Smart Card-based Payments. In Proceedings of the 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 26–30 November 2023; Available online: https://doi.org/10.1145/3576915.3623109 (accessed on 22 October 2025). [CrossRef]
- Rajendran, B.; Pandey, A.K.; Bindhumadhava, B.S. Secure and privacy preserving digital payment. In Proceedings of the 2017 IEEE SmartWorld, Ubiquitous Intelligence & Computing, Advanced & Trusted Computed, Scalable Computing & Communications, Cloud & Big Data Computing, Internet of People and Smart City Innovation (SmartWorld/SCALCOM/UIC/ATC/CBDCom/IOP/SCI), San Francisco, CA, USA, 4–8 August 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Schiansky, P.; Kalb, J.; Sztatecsny, E.; Roehsner, M.C.; Guggemos, T.; Trenti, A.; Bozzio, M.; Walther, P. Demonstration of quantum-digital payments. Nat. Commun. 2024, 14, 3849. [Google Scholar] [CrossRef] [PubMed]
- Privacy and Confidentiality Options for Central Bank Digital Currency, Digital Currency Governance Consortium, World Economic Forum. 2021. Available online: https://www3.weforum.org/docs/WEF_Privacy_and_Confidentiality_Options_for_CBDCs_2021.pdf (accessed on 22 October 2025).
- Karasek-Wojciechowicz, I. Reconciliation of anti-money laundering instruments and European data protection requirements in permissionless blockchain spaces. J. Cybersecur. 2021, 7, tyab004. [Google Scholar] [CrossRef]
- Available online: https://digitaldollarproject.org/wp-content/uploads/2021/10/DDP-Privacy-Principles-10.25.21_Final.pdf (accessed on 22 October 2025).
- Gross, J.; Sedlmeir, J.; Babel, M.; Bechtel, A.; Schellinger, B. Designing a Central Bank Digital Currency with Support for Cash-Like Privacy. Available online: https://ssrn.com/abstract=3891121 or http://dx.doi.org/10.2139/ssrn.3891121 (accessed on 22 October 2025). [CrossRef]
- Available online: https://www.imf.org/en/Publications/WP/Issues/2025/03/28/Privacy-Technologies-The-Digital-Economy-565415 (accessed on 22 October 2025).
- Das, G.; Ali, Y.A.; Singh, B.; Nag, K. Digital Forensics in E-Commerce: Investigating Online Payment Fraud and Data Breaches. Int. J. Innov. Sci. Eng. Manag. 2025, 4, 262–268. [Google Scholar] [CrossRef]
- Nardelli, M.; De Sclavis, F.; Iezzi, M. Hitchhiker’s Guide to Privacy-Preserving Cryptocurrencies: A Survey on Anonymity, Confidentiality, and Auditability. arXiv 2025, arXiv:2505.21008v1,2025. Available online: https://arxiv.org/abs/2505.21008 (accessed on 22 October 2025).
- Peng, T.; Gong, B.; Tu, S.; Namoun, A.; Alshmrany, S.; Waqas, M.; Alasmary, H.; Chen, S. Forward: Backward Private Searchable Encryption for Cloud-Assisted Industrial IoT. Sensors 2024, 24, 7597. [Google Scholar] [CrossRef] [PubMed]
- Lavin, R.; Liu, X.; Mohanty, H.; Norman, L.; Zaarour, G.; Krishnamachari, B. A Survey on the Applications of Zero-Knowledge Proofs. arXiv 2024, arXiv:2408.00243v1. Available online: https://arxiv.org/abs/2408.00243 (accessed on 22 October 2025).
- Central Bank Digital Currencies: Foundational Principles and Core Features. Available online: https://www.bis.org/publ/othp33.pdf (accessed on 22 October 2025).
- Introducing a Framework for Measuring the Quantitative Benefits of Privacy-Enhancing Technologies, Federal Reserve Bank of Cleveland Working Paper Series, August 2024. Available online: https://www.ingentaconnect.com/content/hsp/jpss/2024/00000018/00000004/art00007 (accessed on 22 October 2025).
| Payer/Payee identity | Official documents or digital records that are verifiable and linked to a counterparty, often required by regulations, such as name, address, digital ID |
| Payer/Payee Pseudonyms | Information that allows the counterparty to participate in a transaction without being verified, such as phone numbers or token addresses, such as account number, phone number, or alias. |
| Transaction data | The essential information necessary to complete a transaction typically includes the transaction amount and date. |
| Additional Data from the Payer | Data generated for payer notification that exceeds the requirements of the transaction, such as free text, payment reference, invoice number, and payment purpose. |
| Additional Data from the Payee | Supplementary information that is not essential for the transaction may include details such as location, merchant name, or other data intended to facilitate easier access. |
| Types of Cyber Threats | Information at Risk |
|---|---|
| Data Leakage | The primary consequences of data leakage include:
|
| Misuse of Information | If data are used without the owner’s consent, or if the owner is not properly informed about its intended scope, issues may arise (primarily for advertising purposes). |
| Information System Breach | A cyberattack resulting in an information breach within a digital system can have severe consequences not only for the specific affected system but also for the broader economy. It is essential that every digital payment platform be capable of detecting and responding effectively to all forms of cyber threats, including hacking and malware. |
| Data Protection in Cross-Border Transactions | International transactions are required to comply with all applicable regulations. In situations where regulatory standards differ between countries, a higher standard of control should be applied to ensure data protection. |
| Dimensions | Maximum Score | Scoring Range | Sub-Scoring |
|---|---|---|---|
| Security (P1) | 20 | 5–20 |
|
| GDPR Compliance (P2) | 20 | 0–20 |
|
| Auditability (P3) | 20 | 0–20 |
|
| Privacy-Preserving Technical Measures (P4) | 20 | 0–20 | Allocate five points for each criterion that is fulfilled (see Table 4).
|
| Operational Constraints (P5) | 20 | 0–20 | Allocate five points for each criterion that is fulfilled (see Table 4).
|
| Criterion | 0 Points | 1–2 Points | 3 Points | 4 Points | 5 Points |
|---|---|---|---|---|---|
| Interoperability | Closed system; no compatibility | Limited interoperability, requires adapters | Supports standards but with restrictions | Broad interoperability across platforms | Fully interoperable, seamless integration |
| Scalability | The architecture supports only a fixed or very small number of users/transactions. | The system is effective for small-scale operations; however, as it scales, it experiences considerable latency and communication bottlenecks. | System can handle moderate transaction volumes or limited concurrent users. | Designed to deliver reliable performance even during periods of heavy transaction volume. | Supports millions of users and transactions in real time with low latency, demonstrating proven scalability. |
| Resources Efficiency | Extremely resource | High demand | Moderate efficiency, acceptable | Balanced performance and sustainability | Highly efficient, lightweight, eco-friendly |
| Offline Payment | No offline support | Offline in very constrained cases | Partial offline, needs resync | Robust offline for most scenarios | Fully functional offline, secure reconciliation |
| Anonymity | All transactions are fully identifiable. | Basic pseudonymization or identifier masking is used, but transactions remain easily linkable to a specific user through metadata | Some privacy protections are in place, but the system remains vulnerable to linkage attacks | Identities and transaction metadata are well protected through advanced cryptographic or network-level techniques | Transaction architecture ensures that no personally identifiable information (PII) is collected, processed, or inferable—untraceable transactions |
| Unlikability | Transactions easily linkable | Partial unlikability, metadata leaks | Moderate unlikability | Strong unlikability, resists profiling | Complete unlikability, uncorrelatable transactions |
| Forward & Backward Privacy | Compromise exposes all past/future data | Limited protection, large exposure | Reasonable secrecy, some leaks | Strong, minimal exposure upon compromise | Robust, no past/future compromise possible |
| Future Readiness | Outdated, non-adaptable | Limited adaptability, risks obsolescence | Some forward-looking but needs upgrades | Flexible, aligns with emerging standards | Fully future-proof, modular, post-quantum, adaptable |
| Privacy Enhancement Technology | ||||
|---|---|---|---|---|
| Criteria | ZKPs | Anonymity-Enhanced Signatures | Secret Sharing/Secure Multi-Party Computation (SMPC) | |
| Security | System-specific assessment is required | |||
| GDPR Compliance | Purpose Limitation | System-specific assessment is required | ||
| Data Minimization | ||||
| Storage Limitation | ||||
| Cross-Border Transfers | ||||
| Auditability | 15 Provides strong auditability through verifiable proofs that confirm correctness without revealing the underlying process | 10 Provides authenticity and non-repudiation, but anonymity restricts later verification and accountability | 10 Allows correctness checks in distributed environments, but auditing remains difficult because the data are fragmented | |
| Privacy Preserving Technical Measures | Anonymity | 4 Enables anonymous validation without revealing identity | 3 Small groups may still pose some linkability risk | 3 Protects data content but not user identity, anonymity is secondary |
| Unlinkability | 4 Proper implementation prevents multiple proofs from being linked to a single user | 5 Demonstrates a high degree of unlinkability, individual signatures cannot be correlated with any specific signer | 3 if an individual participates multiple times, their activity could potentially be linked through correlation attacks | |
| Forward/Backward Privacy | 3 While not guaranteed by every protocol, evolving proofs or temporary keys can make this possible | 4 Frequently ensures key evolution and protects interactions before and after | 3 Session-based protection lacks inherent forward and backward secrecy | |
| Future Readiness | 5 Highly adaptable, with active integration in blockchain and post-quantum systems | 3 Mature but less flexible for evolving technological frameworks | 4 Useful for distributed models, though scalability and communication remain challenges | |
| Operational Constraints | Interoperability | 4 Demonstrates effective integration with various infrastructures, including digital identification | 3 Primarily operates within particular systems that rely on signatures | 3 Needs tailored coordination methods and parties working in sync |
| Scalability | 3 Emerging technologies are progressing, yet they continue to demand substantial computing power | 4 Scales efficiently for large user sets with minimal performance overhead | 2 Limited scalability due to heavy communication and computation demands | |
| Resource Efficiency | 3 Moderately demanding; proof generation and verification remain costly | 4 Lightweight and computationally efficient | 2 Resource-intensive due to multi-round encrypted computation requirements | |
| Offline Payment | 4 Supports offline validation (e.g., in privacy-preserving digital cash) via pre-generated proofs | 4 Suitable for offline transactions through pre-computed signatures | 2 Requires active participation, hindering offline use | |
| Final Score | 45 | 40 | 32 | |
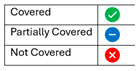 | Evaluation Criteria | BIS: Enhancing Technologies for Digital Payments: Mapping the Landscape | IMF Privacy Technologies & The Digital Economy | Proposed Framework |
|---|---|---|---|---|
| Security | Security |  |  |  |
| GDPR Compliance | Purpose Limitation |  |  |  |
| Data Minimization |  |  |  | |
| Storage Limitation |  |  |  | |
| Cross-Border Transfers |  |  |  | |
| AUDIT | Auditability |  |  |  |
| Technical metrics of Privacy | Anonymity |  |  |  |
| Unlinkability |  |  |  | |
| Forward/Backward Privacy |  |  |  | |
| Future Readiness |  |  |  | |
| Operational Constraints | Interoperability |  |  |  |
| Scalability |  |  |  | |
| Resource Efficiency |  |  |  | |
| Offline Payment |  |  |  | |
| Scoring System |  |  |  |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fragkiadakis, I.; Gritzalis, S.; Lambrinoudakis, C. Evaluating Privacy Technologies in Digital Payments: A Balanced Framework. J. Cybersecur. Priv. 2025, 5, 107. https://doi.org/10.3390/jcp5040107
Fragkiadakis I, Gritzalis S, Lambrinoudakis C. Evaluating Privacy Technologies in Digital Payments: A Balanced Framework. Journal of Cybersecurity and Privacy. 2025; 5(4):107. https://doi.org/10.3390/jcp5040107
Chicago/Turabian StyleFragkiadakis, Ioannis, Stefanos Gritzalis, and Costas Lambrinoudakis. 2025. "Evaluating Privacy Technologies in Digital Payments: A Balanced Framework" Journal of Cybersecurity and Privacy 5, no. 4: 107. https://doi.org/10.3390/jcp5040107
APA StyleFragkiadakis, I., Gritzalis, S., & Lambrinoudakis, C. (2025). Evaluating Privacy Technologies in Digital Payments: A Balanced Framework. Journal of Cybersecurity and Privacy, 5(4), 107. https://doi.org/10.3390/jcp5040107






