AI-Driven Security for Blockchain-Based Smart Contracts: A GAN-Assisted Deep Learning Approach to Malware Detection
Abstract
1. Introduction
- To propose an AI-based security solution integrating deep learning models to detect malware that targets the execution of smart contracts.
- To introduce a GAN-algorithm-based feature selection mechanism to optimize the dataset and improve classification performance by selecting the most useful features.
- To provide a comparative evaluation of three deep learning models (ANN, CNN, and GAT) specialized for different data structures derived from malware behavior.
2. Related Works
3. Proposed Approach
- Creation: the smart contract is programmed and compiled.
- Deployment: the contract is deployed to the Ethereum blockchain, so it becomes public and immutable.
- Execution: the contract interacts with external systems and users through calling the contract’s functions.
- Completion: the contract finishes executing normally, or it reaches an end state (i.e., self-destructs or obsoletes).


3.1. Data and Pre-Processing
| Algorithm 1 Algorithm for Pre-Processing. |
|
3.1.1. Data Cleaning
3.1.2. Duplicate Removal
3.1.3. Normalization (Min–Max Scaling)
3.1.4. Standardization (Z-Score Scaling)
3.1.5. Class Balancing
3.1.6. File Transformation
3.1.7. Statistical Feature Extraction
3.1.8. Validation
3.2. Features Selection
| Algorithm 2 GAN-based Feature Selection. |
|
3.3. Experimentation
- The ANN model provides a free architecture to learn non-linear patterns, and ANNs are built with fully connected layers wherein every neuron connects to each neuron in nearby layers with optimal weights by applying activation functions. They are chosen for their ability to learn non-linear relationships in structured tabular data, which is essential for capturing the diverse patterns exhibited by different types of malware in our dataset. This flexibility allows ANNs to effectively distinguish between benign and malicious behaviors, even when malware variants present overlapping characteristics.
- The CNN model performs better in self-extracting features from spatial or structured data, and CNNs use convolutional filters to extract local features, automatically from structured data, such as images, progressively reducing the dimensionality of the data. They are employed for their capability to capture local spatial dependencies. CNNs are capable of automatically extracting local patterns from structured data, making them effective in detecting specific malware signatures. Their ability to reduce dimension while retaining essential information improves the detection of malicious behavior.
- The GAT model exploits graph-represented data connectivity using mechanisms to emphasize significant relations with attention processes to dynamically allocate weights to the importance of neighbors in information transfer throughout the graph. GATs are suitable for malware detection because they exploit the graph structure of malware, modeling the relationships between different signatures. Using the attention mechanism, they weigh the importance of connections to identify malicious behavior in complex structures.
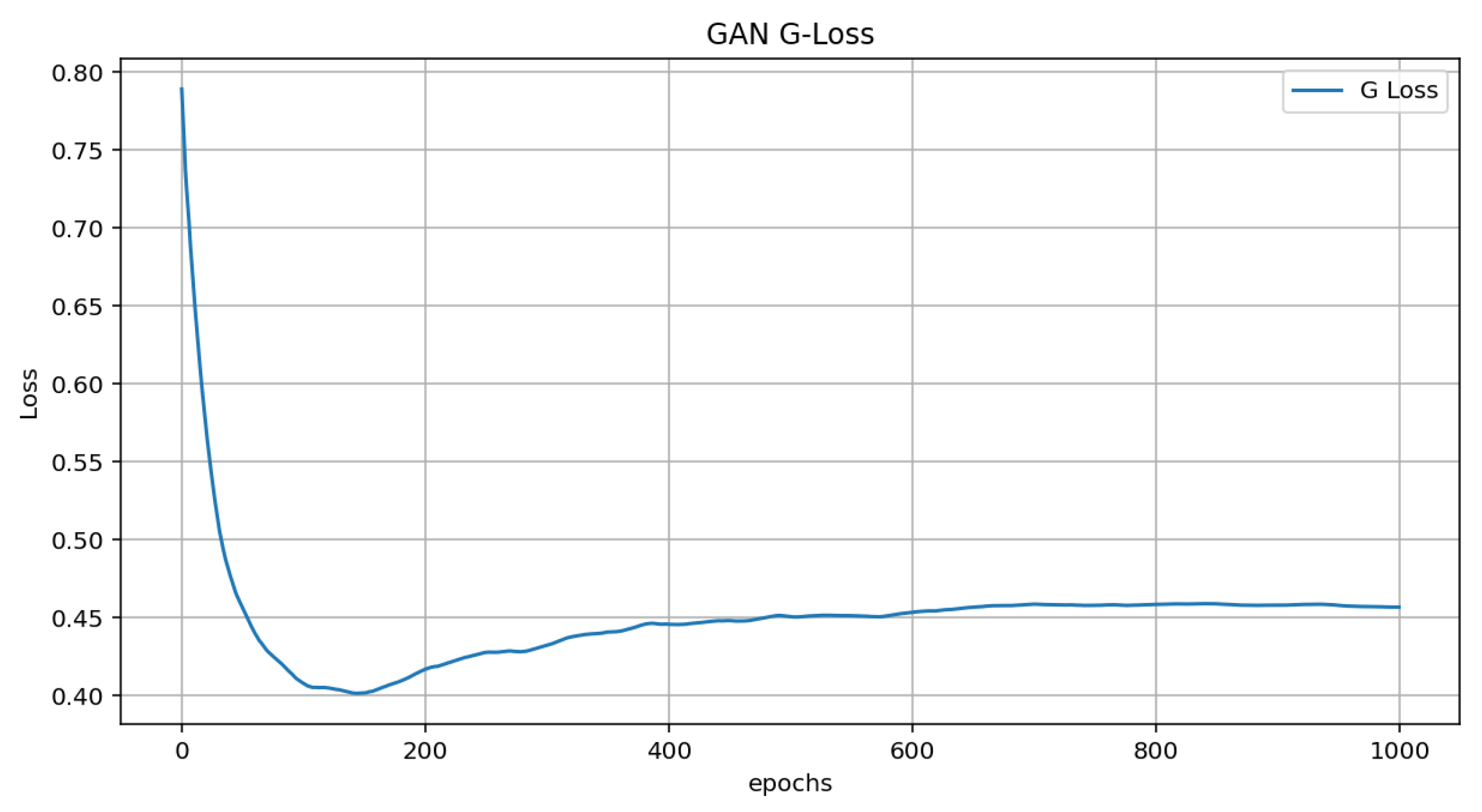
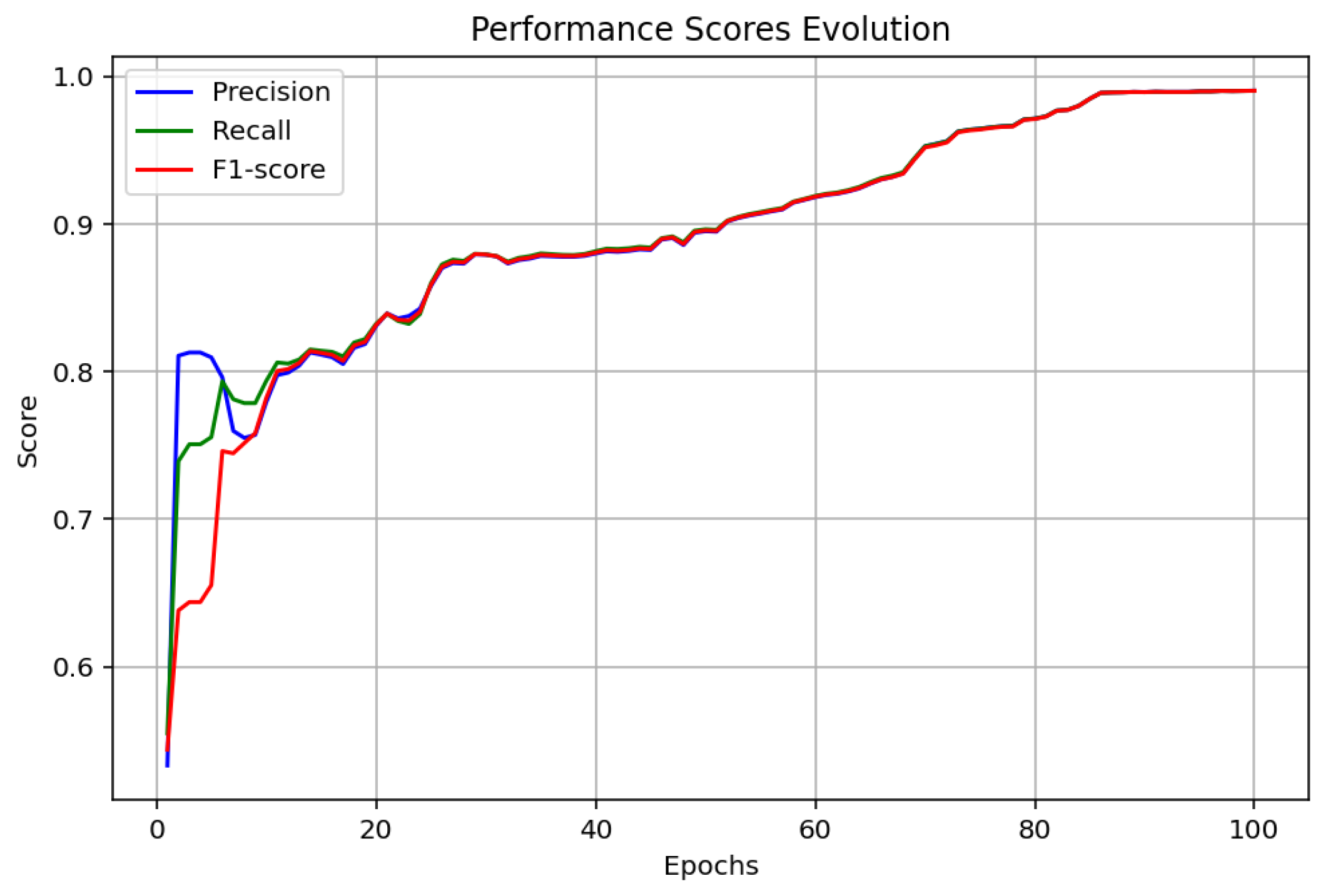
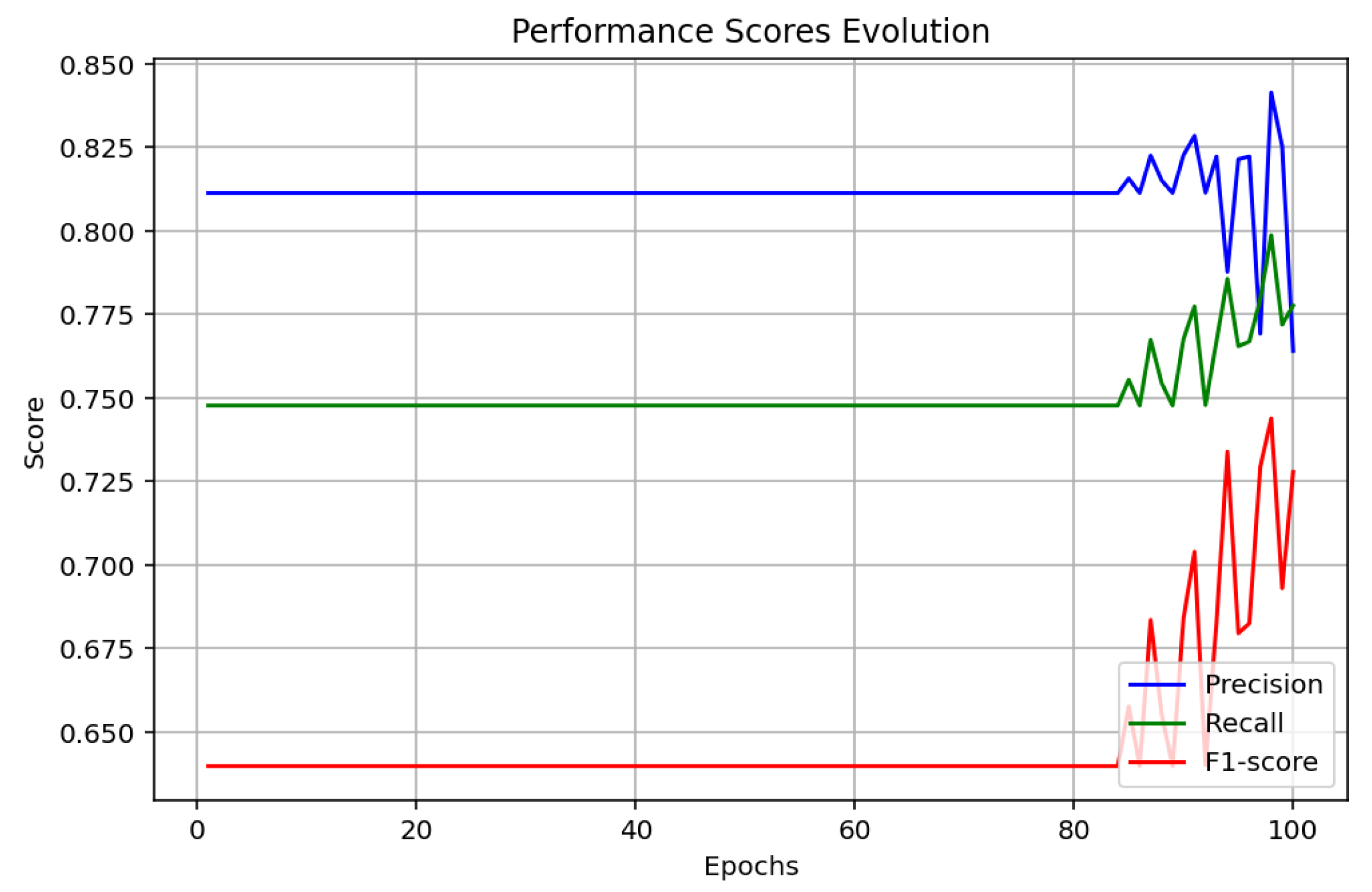
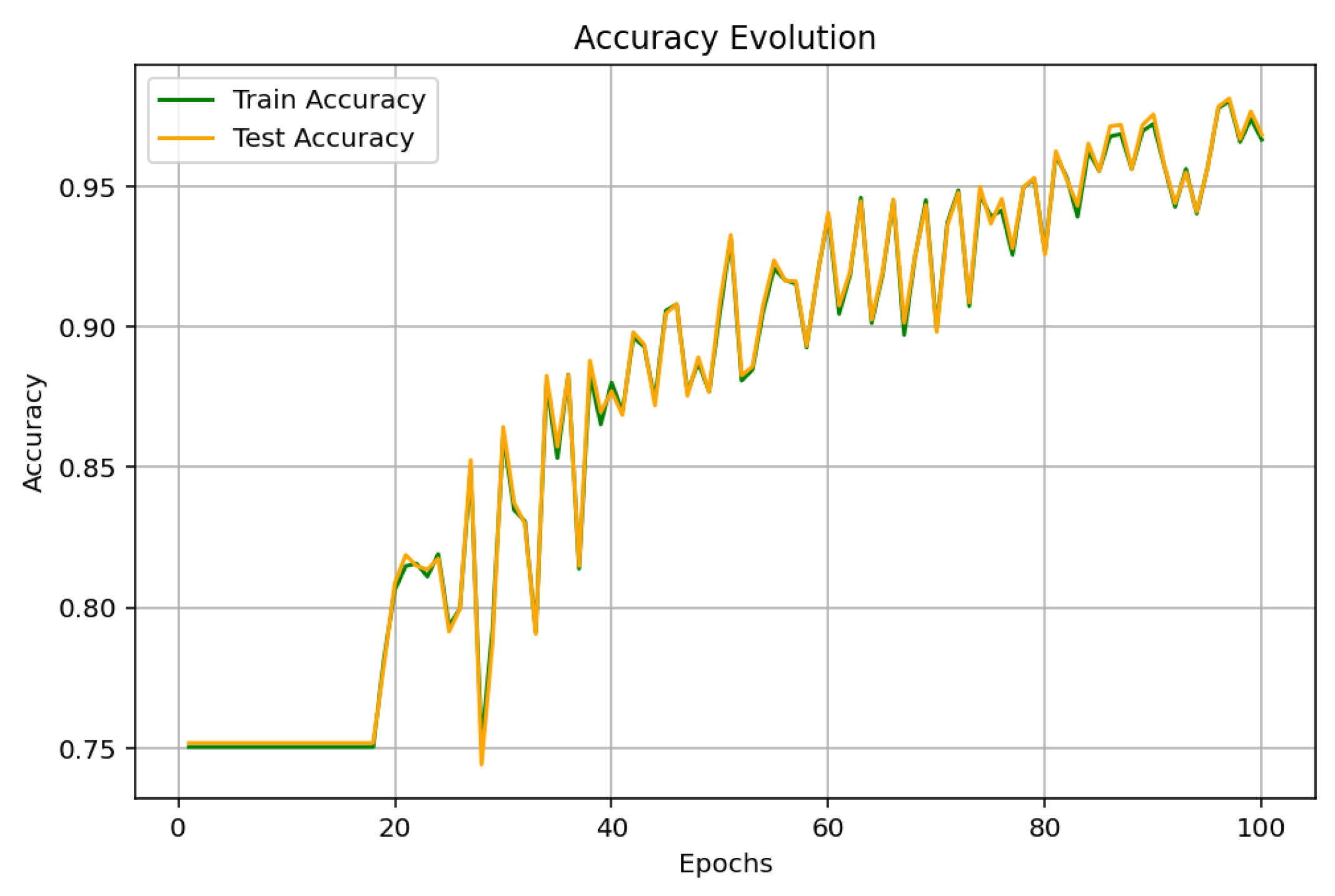
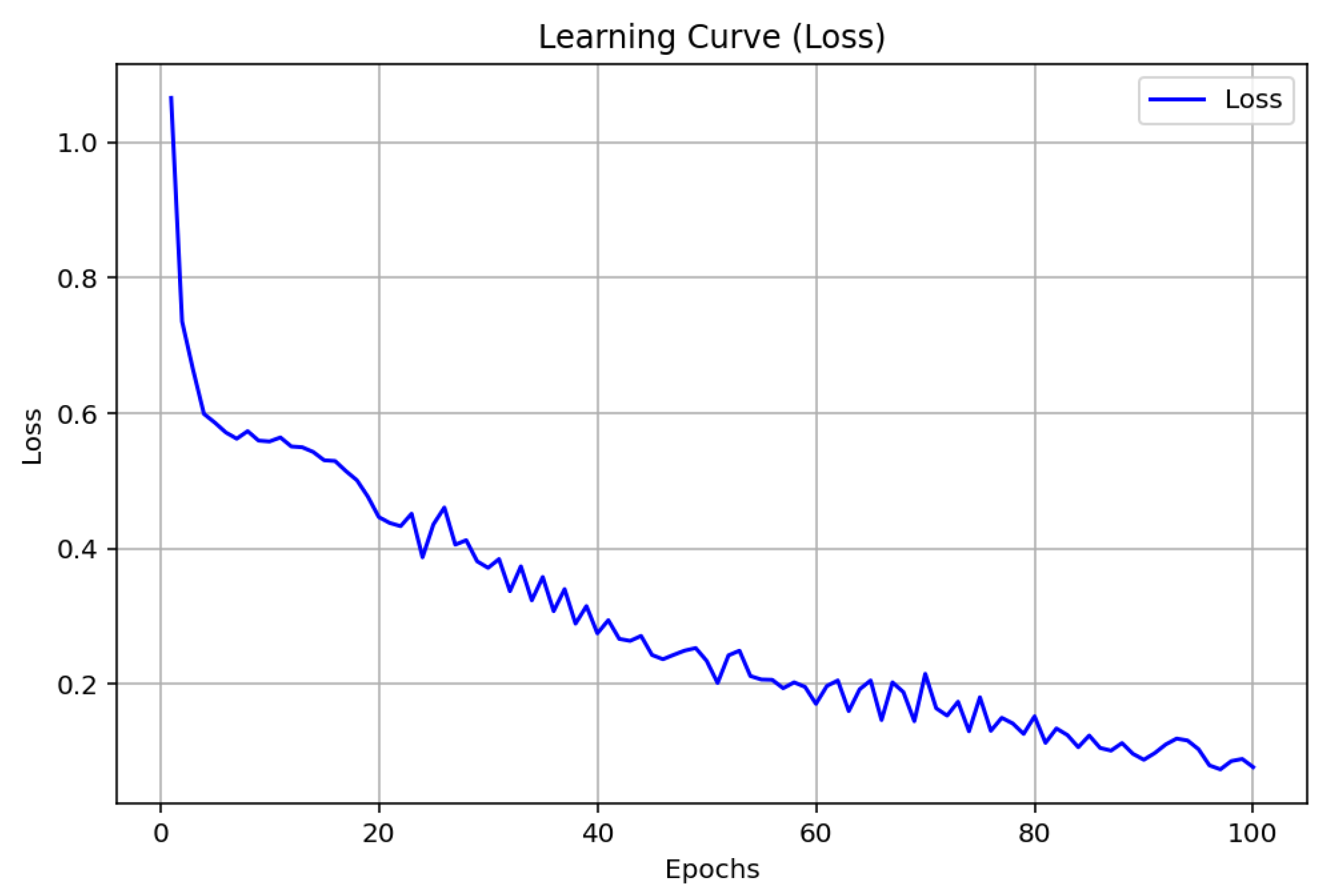
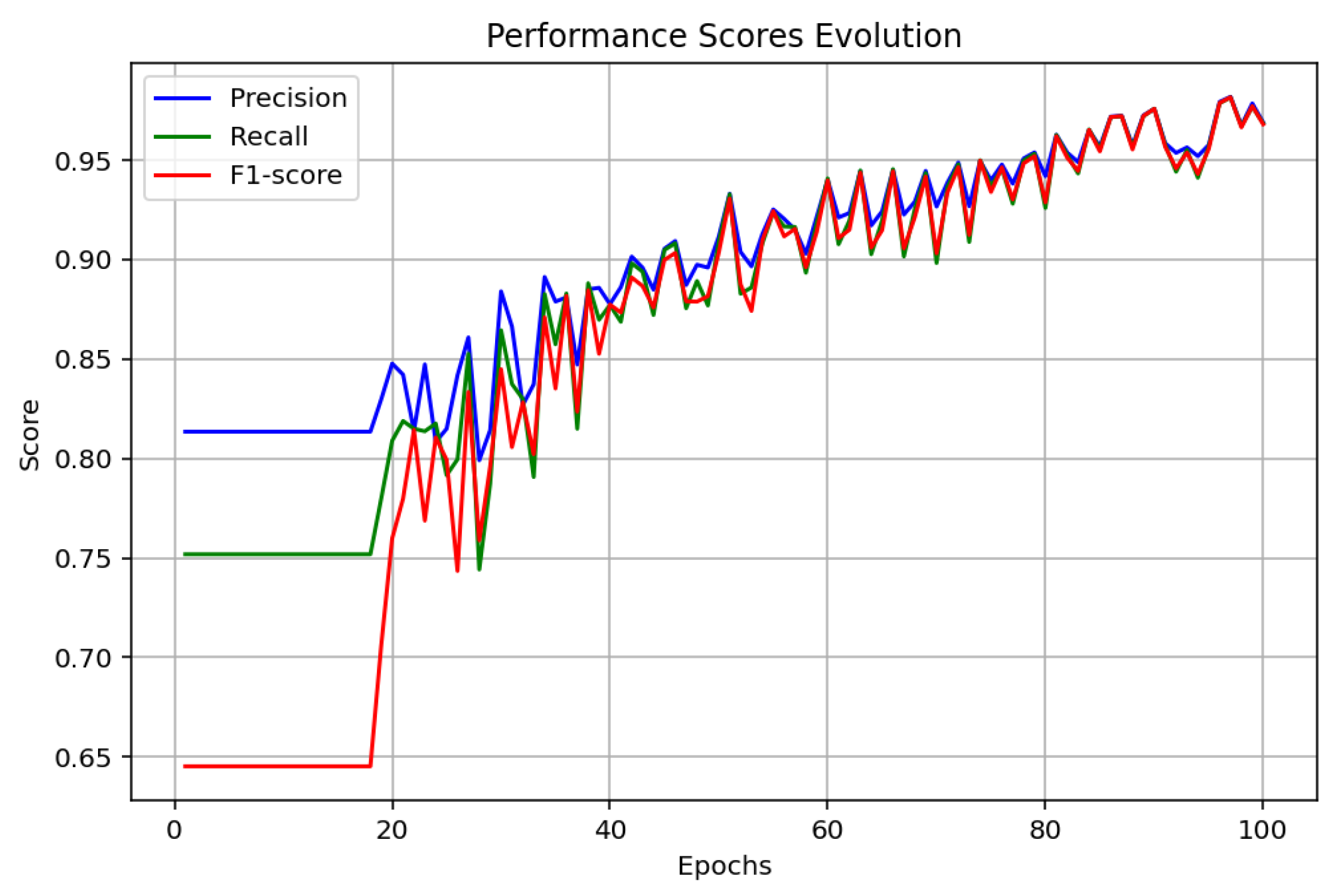
4. Simulation and Results Discussions
4.1. Analysis and Discussion
4.2. Comparison with Other Studies
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wen, Y.; Lu, F.; Liu, Y.; Huang, X. Attacks and countermeasures on blockchains: A survey from layering perspective. Comput. Netw. 2021, 191, 107978. [Google Scholar] [CrossRef]
- Bourian, I.; Sebbar, A.; Chougdali, K.; Amhoud, E.M. SSHCEth: Secure Smart Home Communications based on Ethereum Blockchain and Smart Contract. In Proceedings of the GLOBECOM 2023—2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 2674–2679. [Google Scholar] [CrossRef]
- Imad, B.; Anass, S.; Mounir, A.; Khalid, C. Blockchain Based Smart Contract to Enhance Security in Smart City. In Proceedings of the 2024 11th International Conference on Wireless Networks and Mobile Communications (WINCOM), Leeds, UK, 23–25 July 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Raju, K.; Ramshankar, N.; Shathik, J.A.; Lavanya, R. Blockchain assisted cloud security and privacy preservation using hybridized encryption and deep learning mechanism in iot-healthcare application. J. Grid Comput. 2023, 21, 45. [Google Scholar] [CrossRef]
- El Filali, C.; Bourian, I.; Chougdali, K. Privacy-Preserving and Access Control Scheme for IoT-Based Healthcare Systems Using Ethereum Blockchain. In Proceedings of the 2024 7th International Conference on Advanced Communication Technologies and Networking (CommNet), Rabat, Morocco, 4–6 December 2024; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, Y.; Qiu, Y.; Tang, Z.; Long, S.; Zhao, L.; Tang, Z. Exploring the synergy of blockchain, IoT, and edge computing in smart traffic management across urban landscapes. J. Grid Comput. 2024, 22, 45. [Google Scholar] [CrossRef]
- Blockchain Market Size Report. 2023. Available online: https://www.marketsandmarkets.com/Market-Reports/blockchain-technology-market-90100890.html (accessed on 10 June 2025).
- Gupta, R.; Kumari, A.; Tanwar, S. Fusion of blockchain and artificial intelligence for secure drone networking underlying 5G communications. Trans. Emerg. Telecommun. Technol. 2021, 32, e4176. [Google Scholar] [CrossRef]
- Nguyen, T.N. Smart contract: Revolutionizing transactions in the digital age. HPU2 Nat. Sci. Technol. 2024, 3, 30–38. [Google Scholar] [CrossRef]
- Kayade, P.; Pardeshi, A.; Patil, S.; Raut, P.; Shetkar, P.; Barhate, M. Decentralized Application using Blockchain. In Proceedings of the 2024 5th International Conference on Image Processing and Capsule Networks (ICIPCN), Dhulikhel, Nepal, 3–4 July 2024; pp. 906–911. [Google Scholar] [CrossRef]
- Rouhani, S.; Deters, R. Security, performance, and applications of smart contracts: A systematic survey. IEEE Access 2019, 7, 50759–50779. [Google Scholar] [CrossRef]
- Hu, B.; Zhang, Z.; Liu, J.; Liu, Y.; Yin, J.; Lu, R.; Lin, X. A comprehensive survey on smart contract construction and execution: Paradigms, tools, and systems. Patterns 2021, 2, 100179. [Google Scholar] [CrossRef] [PubMed]
- Hu, T.; Liu, X.; Chen, T.; Zhang, X.; Huang, X.; Niu, W.; Lu, J.; Zhou, K.; Liu, Y. Transaction-based classification and detection approach for Ethereum smart contract. Inf. Process. Manag. 2021, 58, 102462. [Google Scholar] [CrossRef]
- Zaidi, S.Y.A.; Shah, M.A.; Khattak, H.A.; Maple, C.; Rauf, H.T.; El-Sherbeeny, A.M.; El-Meligy, M.A. An attribute-based access control for IoT using blockchain and smart contracts. Sustainability 2021, 13, 10556. [Google Scholar] [CrossRef]
- Wu, C.; Xiong, J.; Xiong, H.; Zhao, Y.; Yi, W. A review on recent progress of smart contract in blockchain. IEEE Access 2022, 10, 50839–50863. [Google Scholar] [CrossRef]
- Li, D.; Wong, W.E.; Wang, X.; Pan, S.; Koh, L.S. Smart Contract Vulnerability Detection based on Static Analysis and Multi-Objective Search. arXiv 2024, arXiv:2410.00282. [Google Scholar] [CrossRef]
- Kumar, N.K.; Honnungar, N.V.; Prakash, M.S.; Lohith, J. Vulnerabilities in Smart Contracts: A Detailed Survey of Detection and Mitigation Methodologies. In Proceedings of the 2024 International Conference on Emerging Technologies in Computer Science for Interdisciplinary Applications (ICETCS), Bengaluru, India, 22–23 April 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Aldweesh, A.; Alharby, M.; Mehrnezhad, M.; Van Moorsel, A. OpBench: A CPU performance benchmark for Ethereum smart contract operation code. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 May 2019; pp. 274–281. [Google Scholar] [CrossRef]
- del Castillo, M. The DAO Attacked: Code Issue Leads to $60 Million Ether Theft. Article Online, CoinDesk. 2016. Available online: https://www.coindesk.com/markets/2016/06/17/the-dao-attacked-code-issue-leads-to-60-million-ether-theft (accessed on 10 June 2025).
- Singh, R.; Tanwar, S.; Sharma, T.P. Utilization of blockchain for mitigating the distributed denial of service attacks. Secur. Priv. 2020, 3, e96. [Google Scholar] [CrossRef]
- Soud, M.; Qasse, I.; Liebel, G.; Hamdaqa, M. Automesc: Automatic framework for mining and classifying ethereum smart contract vulnerabilities and their fixes. In Proceedings of the 2023 49th Euromicro Conference on Software Engineering and Advanced Applications (SEAA), Durres, Albania, 6–8 September 2023; pp. 410–417. [Google Scholar] [CrossRef]
- Kumar, A.S.L.; Mishra, S. Ransomware Criminal Smart Contract. In Proceedings of the 2024 IEEE International Conference on Blockchain (Blockchain), Copenhagen, Denmark, 19–22 August 2024; pp. 219–226. [Google Scholar] [CrossRef]
- Güler, O. A Model Design Using Blockchain and Smart Contracts Against Cyberattacks in Smart Home Systems. Acta Infologica 2024, 8, 11–22. [Google Scholar] [CrossRef]
- Khoa, T.V.; Son, D.H.; Nguyen, C.H.; Hoang, D.T.; Nguyen, D.N.; Trung, N.L.; Quynh, T.T.T.; Hoang, T.M.; Ha, N.V.; Dutkiewicz, E. Securing Blockchain Systems: A Novel Collaborative Learning Framework to Detect Attacks in Transactions and Smart Contracts. arXiv 2024, arXiv:2308.15804. [Google Scholar] [CrossRef]
- DeCusatis, C.; Gormanly, B.; Iacino, J.; Percelay, R.; Pingue, A.; Valdez, J. Cybersecurity Test Bed for Smart Contracts. Cryptography 2023, 7, 15. [Google Scholar] [CrossRef]
- Alkhalifah, A.; Ng, A.; Watters, P.A.; Kayes, A. A mechanism to detect and prevent Ethereum blockchain smart contract reentrancy attacks. Front. Comput. Sci. 2021, 3, 598780. [Google Scholar] [CrossRef]
- Motaghi, Z.; Yazdani, N.; Bahrak, B. A Framework for Collaborative Attack based on Criminal Smart Contract. arXiv 2020, arXiv:2010.12280. [Google Scholar] [CrossRef]
- Li, Z.; Wang, Y.; Wen, S.; Ding, Y. Evil chaincode: Apt attacks based on smart contract. In Proceedings of the International Conference on Frontiers in Cyber Security, Tianjin, China, 15–17 November 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 178–196. [Google Scholar] [CrossRef]
- Sebastian-Cardenas, D.J.; Gourisetti, S.N.G.; Saha, S.S.; Khan, K.; Tillman, L.C.; Cali, U.; Hughes, T. Cybersecurity and privacy aspects of smart contracts in the energy domain. In Proceedings of the 2022 IEEE 1st Global Emerging Technology Blockchain Forum: Blockchain & Beyond (iGETblockchain), Irvine, CA, USA, 7–11 November 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Swaminathan, K.; Saravanan, S. A Criminal Smart Contract for Distributed Denial of Service Attacks. In Proceedings of the 2021 6th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 8–10 July 2021; pp. 853–862. [Google Scholar] [CrossRef]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Pathak, J.P.; Singh, K.; Roy, S. Role of Artificial Intelligence and Blockchain on Cyber Security. Adv. Bus. Inf. Syst. Anal. 2024. [Google Scholar] [CrossRef]
- Alevizos, L. Automated cybersecurity compliance and threat response using AI, blockchain and smart contracts. Int. J. Inf. Technol. 2024, 17, 767–781. [Google Scholar] [CrossRef]
- Adeniyi, A.E.; Jimoh, R.G.; Awotunde, J.B.; Aworinde, H.O.; Falola, P.B.; Ninan, D.O. Blockchain for Secured Cybersecurity in Emerging Healthcare Systems; IET: London, UK, 2024; pp. 335–361. [Google Scholar]
- ThamaraiSelvi, K.; Pushpalatha, A.; Chidambarathanu, K.; Wankhede, J.P.; Alagumuthukrishnan, S.; Sarveshwaran, V. SecureChainAI: Integrating Blockchain and Artificial Intelligence for Enhanced Security in IoT Environments. In Proceedings of the 2024 5th International Conference on Smart Electronics and Communication (ICOSEC), Trichy, India, 18–20 September 2024; pp. 781–789. [Google Scholar] [CrossRef]
- Ainur, J.; Gulzhan, M.; Amandos, T.; Venera, R.; Bulat, S.; Zauresh, Y.; Aizhan, S. The impact of blockchain and artificial intelligence technologies in network security for e-voting. Int. J. Electr. Comput. Eng. (IJECE) 2024, 14, 6723–6733. [Google Scholar] [CrossRef]
- Saleh, A.M.S. Blockchain for secure and decentralized artificial intelligence in cybersecurity: A comprehensive review. Blockchain Res. Appl. 2024, 5, 100193. [Google Scholar] [CrossRef]
- Ahakonye, L.A.C.; Nwakanma, C.I.; Kim, D.S. Tides of Blockchain in IoT Cybersecurity. Sensors 2024, 24, 3111. [Google Scholar] [CrossRef] [PubMed]
- Karnwal, V.; Chaurasia, A.; Agarwal, D. Blockchain Security and Privacy using Machine Learning and Internet of Things-A Review. In Proceedings of the 2024 First International Conference on Pioneering Developments in Computer Science & Digital Technologies (IC2SDT), Delhi, India, 2–4 August 2024; pp. 19–22. [Google Scholar] [CrossRef]
- Ramos, S.; Ellul, J. Blockchain for Artificial Intelligence (AI): Enhancing compliance with the EU AI Act through distributed ledger technology. A cybersecurity perspective. Int. Cybersecur. Law Rev. 2024, 5, 1–20. [Google Scholar] [CrossRef]
- Venkatasubramanian, M.; Lashkari, A.H.; Hakak, S. Federated Learning Assisted IoT Malware Detection Using Static Analysis. In Proceedings of the 2022 12th International Conference on Communication and Network security, Beijing, China, 1–3 December 2022; pp. 191–198. [Google Scholar] [CrossRef]
- Abirind, K.; Vijai, K.; Nandakumar, R. Malware Detection: A Comparison of Different Machine Learning and Deep Learning Networks. In Proceedings of the 2024 15th International Conference on Computing Communication and Networking Technologies (ICCCNT), Kamand, India, 24–28 June 2024; pp. 1–6. [Google Scholar] [CrossRef]






| Ref. | Attack | Vulnerability | Target | Method Used |
|---|---|---|---|---|
| [22] | Ransomware via SC | SC Automation | Data | Criminal SCs |
| [23] | Cyberattacks | Insufficient Security | Smart Home | SC |
| [24] | Transaction attacks | SC | Transactions | Collaborative learning |
| [25] | Social engineering attacks | Unsecure code | SC | Test bed |
| [26] | Reentrancy attacks | Reentrancy vulnerabilities | Ethereum SC | Detection mechanism |
| [27] | Criminal SCs | SC Exploitation | SC | Criminal SCs |
| [28] | APT | Open system | Blockchain | Data theft |
| [29] | SC for energy | Attack vectors | SC | Best practices |
| [30] | DDoS | Open system | Resources | DDoS |
| [31] | Exploitation | Security patches | SC | Classification and analysis |
| Technology | Description |
|---|---|
 | An open-source platform used to develop and manage data science and scientific computing libraries required for deep learning and data processing tasks. |
 | An open-source development environment used for writing, testing, and debugging Python v3.13.2 code, bundled with Anaconda. |
 | The main programming language used to implement deep learning models, GAN-based feature selection, and experiment pipelines. |
| Metrics | ANN | CNN | GAT |
|---|---|---|---|
| Accuracy | 97.60% | 80% | 96.84% |
| Precision, recall, and F1-score | High value after 20 epochs | High value after 80 epochs | High value after 20 epochs |
| References | Objective | Accuracy Score |
|---|---|---|
| [41] | Propose a Federated Learning-based approach that employs a random forest model for detecting IoT malware samples. | 95% |
| [42] | Evaluate the effectiveness of deep learning models for malware detection. | 96.6% |
| Our work | Combined blockchain and deep learning architecture to improve security in smart systems. | 97.6% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bourian, I.; Hassine, L.; Chougdali, K. AI-Driven Security for Blockchain-Based Smart Contracts: A GAN-Assisted Deep Learning Approach to Malware Detection. J. Cybersecur. Priv. 2025, 5, 53. https://doi.org/10.3390/jcp5030053
Bourian I, Hassine L, Chougdali K. AI-Driven Security for Blockchain-Based Smart Contracts: A GAN-Assisted Deep Learning Approach to Malware Detection. Journal of Cybersecurity and Privacy. 2025; 5(3):53. https://doi.org/10.3390/jcp5030053
Chicago/Turabian StyleBourian, Imad, Lahcen Hassine, and Khalid Chougdali. 2025. "AI-Driven Security for Blockchain-Based Smart Contracts: A GAN-Assisted Deep Learning Approach to Malware Detection" Journal of Cybersecurity and Privacy 5, no. 3: 53. https://doi.org/10.3390/jcp5030053
APA StyleBourian, I., Hassine, L., & Chougdali, K. (2025). AI-Driven Security for Blockchain-Based Smart Contracts: A GAN-Assisted Deep Learning Approach to Malware Detection. Journal of Cybersecurity and Privacy, 5(3), 53. https://doi.org/10.3390/jcp5030053





