Energy Consumption Framework and Analysis of Post-Quantum Key-Generation on Embedded Devices
Abstract
1. Introduction
1.1. Key Generation with Hybrid Encryption
1.2. Quantum Computing Exploits
1.3. Aim of the Paper
2. Related Literature
2.1. Energy Relating to Thermodynamic Principles
2.2. Post-Quantum Cryptography (PQC)
2.2.1. In the Classical Space
2.2.2. The Rise of the ‘Quantum’ Machines
2.2.3. Standardisation and Governmental Response
2.3. Vulnerabilities Exposed by Quantum Computing
2.4. NIST Standardisation
Beyond the First Batch PQC Standards—Round 4
2.5. Energy Efficiency in PQC
3. Implementation
- Key Exchange: A crucial component of secure communication whose traditional techniques were protected by large-number factorisation and that will be rendered vulnerable to Shor’s algorithm in quantum computing. New quantum-resistant techniques are emerging.
- Energy Consumption: A comparative evaluation of the energy used during key generation methods for both traditional and post-quantum cryptography.
- Computing Platform: The Raspberry Pi 5 was selected as the test platform, ensuring the homogeneity and repeatability of the results. Its uniform and common integration into operational technology solutions and use by hobbyists make it a relevant choice.
- Software Library: Standardised libraries were employed in the solutions, recognising the implementation complexity and verification challenges of cryptographic code. Following the established best practice in cryptography, this paper utilised the tested, peer-reviewed, and performant OpenSSL library rather than developing custom implementations.
3.1. Methodology and Implementation Overview
3.2. Data Analysis
3.2.1. Calculating Energy Used
3.2.2. Result Accuracy
3.3. Selection of Parameters Tested
- Iterations: A range of experimental round sizes were implemented in the environment. These were chosen to validate the results of the tests, and the final outputs predominantly made use of ‘500,000’ key examples—with testing taking place over a period of around 24 h of operation. This iteration count was specified in the input file of the test script.
- Security Levels: A range of algorithms were chosen that covered the NIST security levels from 1 to 5, where a broad equivalence of the different algorithms under test was ensured to permit easy comparison.
- Algorithms: Three categories of algorithms were included in the testing, all were from the OpenSSL3.5 library as compiled for the Raspberry Pi device under test. The full set can be seen in Table 1.
- Elliptic Curve. Several commonly used ECC algorithms were chosen to enumerate a range of security levels. This was used to baseline the method versus other key generation categories.
- RSA. Another classic algorithm used for key generation. RSA is a more mature solution and still commonly in use. Over the years, the key sizes used have ramped upwards to maintain security as computing power has risen. Several key sizes for RSA were selected in the analysis.
- ML-KEM Post-Quantum Cryptography Technique. This is the currently available key generation technique standardised by the NIST as FIPS 203, and implemented in the April 2025 OpenSSL3.5 library release.
- The ML-DSA algorithm was also included. While this is not explicitly used as a key exchange mechanism, it does perform key generation at equivalent security levels using Lattice techniques, and was therefore a useful yardstick to ensure the broad validity of the results of the ML-KEM method while awaiting the standardisation of HQC and its implementation in OpenSSL for evaluation.
- Polling Interval: This is a parameter which was chosen as part of the experimental setup. It is the frequency at which data were recovered by the Windows collector machine from the TC66C meter, and did not impact on the key generation process. The data used for the energy calculations were a cumulative value from the TC66C, so the period chosen here only defined start and stop time granularity and the update period on the screen for the user.
4. Methodology
4.1. Experimental Approach
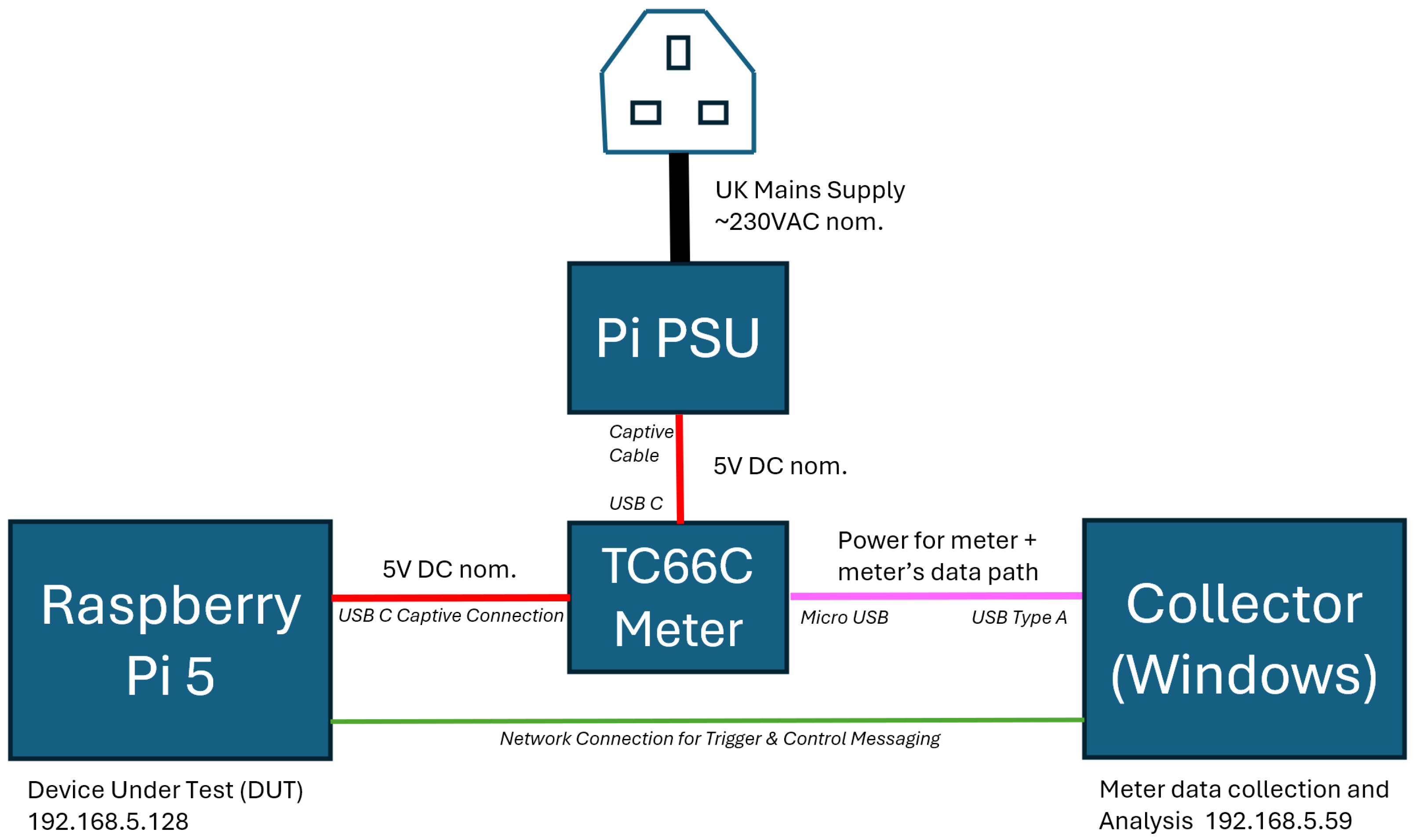
- Target System—Device Under Test—(Raspberry Pi): This single-board computer executed the software which ran the experiments whose energy consumption was being benchmarked. It also hosted a network client responsible for sending control messages to accurately start and stop the energy acquisition recording.
- Data Acquisition System (Windows Machine): This system hosted the data logging software. It was connected to the TC66C energy tester that monitored the electrical utilisation characteristics of the Raspberry Pi. This system also ran a network server to receive control messages to toggle acquisition on and off for the energy data.
- USB Tester (Ruideng TC66C): An external hardware device connected between the Raspberry Pi and its power supply. It accurately measured and reported instantaneous electrical parameters such as voltage, current, and power, and cumulative totals, including the energy consumed.
- Ethernet Network: The communication medium facilitating the exchange of control messages between the Raspberry Pi and the Windows machine. This was a dedicated network with UDP messages used, without the latency and additional energy of a TCP handshake.
4.2. Experimental Procedure
- Initialisation and Preparation (Triggered by “GETREADY” message): The Raspberry Pi, acting as the control client, sent a “GETREADY” message to the Windows data acquisition server. This message included experimental parameters (e.g., test duration, sampling frequency, experiment identifier, etc.). After receiving the “GETREADY” message, the Windows machine
- -
- Parsed the experimental parameters.
- -
- Initialised the data logging system, preparing the output file(s) with appropriate headers based on the received parameters.
- -
- Transitioned the TC66C meter to the ‘ready’ state, awaiting the “START” command.
- Data Acquisition (Triggered by “START” message): Once the process on the Raspberry Pi was ready for benchmarking (i.e., after the CPU clock had been hard set and the fans had time to spin up and settle), and immediately prior to starting the experiment, a “START” message was sent to the Windows machine. The Windows machine then
- -
- Initiated data collection from the USB tester at the specified sample rate.
- -
- Continuously recorded the measured electrical parameters (voltage, current, power, energy, etc.) along with timestamps to the designated output file(s).
- -
- Simultaneously, a subset of the data were displayed on the Windows screen for real-time monitoring by the operating user (on the Windows machines, so not impacting the DUT).
- Termination (Triggered by “STOP” message): At completion of the benchmarking process on the Raspberry Pi, it sent a ‘STOP’ message to the Windows machine. The Windows machine next
- -
- Ceased data acquisition from the USB tester.
- -
- Closed the output file(s), ensuring all data were saved.
- -
- Cleanly terminated the data logging application and network server thread.
4.3. Software Design/Architecture
- Main Control Thread: This thread was responsible for coordinating the overall operation of the data acquisition. It also controlled the other threads and overall flow.
- Network Server Thread: This continuously listened for incoming network messages (“GETREADY”, “START”, “STOP”) from the Raspberry Pi, and was started and stopped by the main thread. After receiving a message, it parsed the command and any associated parameters, signalling to the main control thread to take appropriate action.
- Data Acquisition Thread: This thread was responsible for periodically reading data from the USB tester. It also wrote the data to the output file(s) and displayed pertinent information on the screen to give positive feedback to the user/operator as to the current operational state. This thread was started and stopped by the main thread based on the “START” and “STOP” messages received via the network from the Pi.
5. Evaluation
5.1. Energy Results—Key Generation
5.1.1. Energy Results—Commentary
5.1.2. Extrapolating Potential Energy Savings
- Web Servers (HTTPS): Assuming approximately 300 million websites active globally using certificates (an estimate in Jan 2025 based on [44]), and a conservative average certificate cycle of 3 months (LetsEncrypt uses 60 days and has over 50% of the market), this equates to roughly 1.2 billion key generations per year.
- VPN Users: With an estimated 1.5 billion VPN users globally [45], assuming each host generates a new key each year, this adds another 1.5 billion key generations annually.
- Other Applications (VPN, Email, SSH): A conservative estimate for the combined key generation for secure email, SSH, and other applications is around 10% of the web server figure, supposing approximately 120 million key generations per year.
5.2. Key Generation Time Observation
6. Conclusions
6.1. RSA’s Dead-End
6.2. Use of Elliptic Curve Cryptography
6.3. Adoption of New PQC Standards
6.4. Recommendations
6.5. Future Work
- Additional Hardware Platforms: To use and compare more than one type of hardware, for example adding Raspberry Pi 4 and another standard Intel x86/AMD64 ISA platform for comparisons. The meter used (unmodified) can capture up to 20 V with currents up to 5 A. Devices with attached batteries (e.g., laptops) are not suitable for this exercise due to the need to capture live energy utilisation directly.
- Alternative Software Libraries: To identify further suitable cryptographic libraries for comparative testing, other than OpenSSL. For example, exploring Bouncy Castle [49] and/or other potential PQC libraries as they become available. A challenge here will be ensuring comparable algorithm support and maturity across different libraries. Possible alternative sources can be found directly at asecuritysite [50], which is a cryptographic website with resources for researchers, hobbyists, and professionals in the area, including for post-quantum cryptography.
- Explore End-to-End Sessions: To expand the study to a fuller E2E lifecycle measurement across a range of scenarios:
- On-Network Key Exchange: Measure the bidirectional energy consumption of different PQC and traditional key exchange protocols including network communication.
- Data Transfer: Quantify the energy cost of encrypting and transmitting datasets of varying sizes using the negotiated symmetric keys derived from both PQC and traditional key exchange mechanisms (also considering the cost of the required hardening to AES-256 for all applications that Grover’s algorithm effectively mandates).
- Digital Signatures: Evaluate the energy efficiency of generating and verifying digital signatures using standardised PQC algorithms (e.g., ML-DSA, SLH-DSA), comparing to traditional signature schemes. Isolating the energy cost of specific operations in an end-to-end scenario will be a key challenge in this potential future work.
- New Standards: To incorporate the evolution of the standards, for example to include HQC testing once this has been finalised by the NIST [33] into a FIPS standard and is incorporated into OpenSSL and other cryptographic libraries. Additional work to evaluate this algorithm could be carried out upon its availability, even whilst in Beta testing.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Practical Setup and Operation
Appendix A.1. Test Equipment Details
- The Raspberry Pi which performs the key generation experiments
- The Ruideng TC66C energy meter, inline with the Pi’s PSU, measuring supply parameters
- The Windows Collector Machine which powers the TC66C meter and records the DUT’s energy use data between the START and STOP command messages.
Appendix A.1.1. Raspberry Pi
- Raspberry Pi 5 Model B Rev 1.0 8 GB.
- Raspberry Pi OS Lite (Fully Patched as of 1 April 2025).
- OS ‘PRETTY-NAME’ = “Debian GNU/Linux 12 (bookworm)”.
- Added software: OpenSSL 3.5 and dependencies.
- -
- Download, unpack, local compilation is required. Add the OpenSSL3.5 binary to the path for the system. Switch default openssl version to v3.5.
- The ‘batch_experimenter.py’ & ‘experimenter.py’ files and example source files can be obtained from the project GitHub page [40].
- This software sets the Pi fan to 100% and fixes the clock frequency at the maximum to ensure these are as invariant as possible during the experiments and iterated tens of thousands of times.
Appendix A.1.2. Ruideng TC66C Meter
- Ruideng TC66C Meter.
- -
- This can also be the non-C version, as Bluetooth is not required. BT can be turned off in the interface. The data are collected by USB on the Collection PC.
- Device Switches: Power and PD toggle switches should both be OFF.
- -
- Power switch = off, indicates that the unit should be powered from the Collection PC USB connection, and not from the Pi power source.
- -
- PD switch = off, as there should be no negotiation by the meter to the Pi Power supply—these data should pass-through natively.
- The meter uses the v1.14 firmware that it was delivered with.
Appendix A.1.3. Windows Data Collection PC
- Windows PC—the experiment’s PC was running Windows 11 Professional 24H2, Build: 26100.3775. Fully Patched through 7 May 2025.
- A USB connection able to attach to the TC66C meter, using a generic Microsoft Serial USB Adaptor device driver.
- Python 3.x—the test PC used Python v3.13.3.
- Pip packages for ‘pycryptodome’ and ‘pyserial’ to communicate to the TC66C meter.
- Running the ‘responder.py’ code from the GitHub project repository.
- Trivial PC hardware requirements, but for transparency, the test Collection PC was an AMD Ryzen 9 7900X 12C 24T Processor with 96 GB DDR5 RAM and 2 TB SSD.
- Size the Collection PC according to the requirements:
- -
- The PC is running a master control thread, which spawns two additional threads for networking and polling data from the TC66C meter.
- -
- Listening and responding to Network messages for START and STOP commands. Reading a small segment of data from the USB/Serial connection periodically at less than or equal to 10 Hz. Printing a short update to the screen to keep the user updated on status. Writing out single lines of data to files at a maximum frequency of 10 Hz.
Appendix A.2. Example Experimental Run on the Framework
Appendix A.2.1. Single Run

| Line | Pi Output | Notes |
|---|---|---|
| 1 | cameron@cryp... | Experiment run with 3200 iterations of ML-KEM-1024: ‘python ./experimenter.py --algorithm ML-KEM-1024 --iterations 3200’ |
| 2 | UDP: Sent ’GET... | This notes that a ‘GETREADY’ has been sent to the Collector PC with parameters |
| 3 | Starting exp... | Notes the experiment with this ID is starting—informing user |
| 4 | Setting up e... | Notes fan and CPU are being set to static values for test |
| 5 | Start Temper... | It notes the temperature recorded by the Pi’s CPU prior to the experiment |
| 6 | UDP: Sent ’STA... | The START message is sent to the Collector so it starts recording energy information |
| 7 | STARTing exp... | Immediately afterwards it starts the experiment—3200 lots of KEM-1024 |
| 8 | Experiment f... | No output until this message after Pi experiment finishes |
| 9 | UDP: Sent ’STO... | A STOP message is set to collector to cease energy recordings |
| 10 | Time to run ... | Notes Wall-clock time for the experiment |
| 11 | Start Temper... | Shows start temperature of Pi |
| 12 | Stop Tempera... | Displays temperature of Pi after experiment has completed |
| 13 | Environment ... | Notes that the fan and CPU have been set back to defaults at end of experiment |
| 14 | cameron@cryp... | Command line as experiment complete. |

| Line | Coll. Output | Notes |
|---|---|---|
| 1 | PS C:Users:Ca... | Run the command to start the Collection |
| 2 | Please select... | (can force/bypass selection e.g., --com COM5) |
| 3 | 1: COM4.3:COM3.. | shows detected COM ports on the PC if not provided |
| 4 | Enter line# ... | User can select the COM line |
| 5 | No user respo... | It defaults if response times out |
| 6 | Selected COM ... | Details which port is in use |
| 7 | Please start ... | Note that Collector is ready to receive START message |
| 8 | Network Liste... | User notification that UDP will be used |
| 9 | Main thread s... | and waiting for a GETREADY from Pi |
| 12 | Listening for... | All interfaces listening on port |
| 13 | Received: ’GET... | GETREADY received from experiment and Pi |
| 14 | Experiment pa... | Prints the parameters of experiment received from Pi in packet |
| 15 | Output file o... | Specific Experiment logfile opened and ready |
| 16 | GETREADY rece... | notes that COM5 serial port will be used |
| 17 | TC66C meter i... | initialises thread for data coming in from meter on this COM |
| 18 | Received: ’STA... | Network START received on network thread |
| 19 | START signal ... | Message user to say we’re getting started |
| 20 | Data Acquisiti.. | Starts getting data from TC66C meter, counters to 0 |
| 21 | Joules thus f... | This line auto-updates - usually a few times a second, shows cumulative totals of energy and time elapsed in experiment |
| 22 | Received: ’STO... | Experiment has ended - Pi has sent STOP |
| 23 | STOP signal r... | Stop recording energy data, the totals are known now |
| 24 | Data logging ... | Experiment log file flushed and saved |
| 25 | Data Acquisit... | Close down the connection to meter as no more data to come |
| 26 | Cleanup compl... | Verifying network, meter threads and individual log file closed |
| 27 | *Total Energy... | Prints a summary of the result totals |
| 28 | *Energy Rate:... | Prints the energy rate per 1000 keys generated for experiment |
| 29 | Master:AllRes... | This is written as a one-liner to the master log AllResults.csv |
| 30 | STOP message ... | Flushing the threads - this message is last out |
| 31 | Network Liste... | No longer listening to the network, we’re done |
| 32 | PS C::Users:C... | Returns to the command line |
Appendix A.2.2. Batch Run
- EC -pkeyopt ec_paramgen_curve:secp160r1,100000
- EC -pkeyopt ec_paramgen_curve:P-521,100000
- NULL,100000
- ML-KEM-1024,100000
- RSA -pkeyopt rsa_keygen_bits:4096,200
Appendix A.2.3. Results Files
References
- FIPS 197; Advanced Encryption Standard (AES). National Institute of Standards and Technology: Gaithersburg, MD, USA, 2001. [CrossRef]
- Diffie, W.; Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar] [CrossRef]
- Boneh, D.; Shoup, V. A Graduate Course in Applied Cryptography, version 0.6; Stanford University: Stanford, CA, USA, 2023. Available online: https://toc.cryptobook.us/ (accessed on 24 April 2025).
- Barnes, R.; Bhargavan, K.; Lipp, B.; Wood, C. Hybrid Public Key Encryption. Internet Eng. Task Force (IETF) RFC 9180 2022. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Miller, V.S. Use of elliptic curves in cryptography. In Advances in Cryptology, Proceedings of the CRYPTO’ 85, Santa Barbara, CA, USA, 18–22 August 1985; Springer: Berlin/Heidelberg, Germany, 1986; pp. 417–426. [Google Scholar]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; IEEE: Piscataway, NJ, USA, 1994; pp. 124–134. [Google Scholar]
- National Institute of Standards and Technology (NIST), Computer Security Resource Center (CSRC). Post-Quantum Cryptography. Available online: https://csrc.nist.gov/projects/post-quantum-cryptography (accessed on 24 April 2025).
- The OpenSSL Project. OpenSSL Library, 2025. Released 8 April 2025. Available online: https://www.openssl.org/ (accessed on 7 May 2025).
- Buchanan, W.J. PQC Key Encapsulation Mechanism (KEM) Speed Tests. 2025. Available online: https://asecuritysite.com/pqc/pqc_kem (accessed on 7 May 2025).
- Tasopoulos, G.; Dimopoulos, C.; Fournaris, A.P.; Zhao, R.K.; Sakzad, A.; Steinfeld, R. Energy Consumption Evaluation of Post-Quantum TLS 1.3 for Resource-Constrained Embedded Devices. In Proceedings of the 20th ACM International Conference on Computing Frontiers, CF ’23, Bologna, Italy, 9–11 May 2023; pp. 366–374. [Google Scholar] [CrossRef]
- Raspberry Pi Holdings plc. Annual Report and Accounts 2024. 17 April 2025. Available online: https://investors.raspberrypi.com/reports/7/document (accessed on 4 July 2025).
- Landauer, R. Irreversibility and Heat Generation in the Computing Process. IBM J. Res. Dev. 1961, 5, 183–191. [Google Scholar] [CrossRef]
- Bérut, A.; Arakelyan, A.; Petrosyan, A.; Ciliberto, S.; Dillenschneider, R.; Lutz, E. Experimental verification of Landauer’s principle linking information and thermodynamics. Nature 2012, 483, 187–189. [Google Scholar] [CrossRef] [PubMed]
- Bennett, C.H. The thermodynamics of computation—A review. Int. J. Theor. Phys. 1982, 21, 905–940. [Google Scholar] [CrossRef]
- Aydeger, A.; Zeydan, E.; Yadav, A.K.; Hemachandra, K.T.; Liyanage, M. Towards a Quantum-Resilient Future: Strategies for Transitioning to Post-Quantum Cryptography. In Proceedings of the 2024 15th International Conference on Network of the Future (NoF), Castelldefels, Spain, 2–4 October 2024; pp. 195–203. [Google Scholar] [CrossRef]
- FIPS 46; Data Encryption Standard. National Bureau of Standards: Gaithersburg, MD, USA, 1977.
- Karn, P.; Metzger, P. The ESP Triple DES Transform. Internet Eng. Task Force (IETF) RFC 1851 1995. [Google Scholar] [CrossRef]
- Schaller, R. Moore’s law: Past, present and future. IEEE Spectr. 1997, 34, 52–59. [Google Scholar] [CrossRef]
- Mansfield, E.; Barnes, B.; Kline, R.; Vladar, A.; Obeng, Y.; Davydov, A. International Roadmap for Devices and Systems (IRDS™) 2023 Edition; Technical Report; IEEE: Piscataway, NJ, USA, 2023; Available online: https://irds.ieee.org/editions/2023/20-roadmap-2023-edition/122-irds%E2%84%A2-2023-editorial (accessed on 24 April 2025).
- Australian Cyber Security Centre (ACSC). Guidelines for Cryptography. 2025. Available online: https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/ism/cybersecurity-guidelines/guidelines-cryptography (accessed on 24 April 2025).
- National Cyber Security Centre (NCSC). Timelines for Migration to Post-Quantum Cryptography. 2025. Available online: https://www.ncsc.gov.uk/guidance/timelines-for-migration-to-post-quantum-cryptography (accessed on 24 April 2025).
- NIST IR 8547; Threshold Timelines and Recommendations for the Transition to Post-Quantum Cryptography Standards. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. [CrossRef]
- Cybersecurity Agencies of 18 EU Member States. Securing Tomorrow, Today: Transitioning to Post-Quantum Cryptography. 2024. Available online: https://www.bsi.bund.de/SharedDocs/Downloads/EN/BSI/Crypto/PQC-joint-statement.pdf?__blob=publicationFile&v=3 (accessed on 24 April 2025).
- European Commission. Recommendation on a Coordinated Implementation Roadmap for the Transition to Post-Quantum Cryptography. 2024. Available online: https://digital-strategy.ec.europa.eu/en/library/recommendation-coordinated-implementation-roadmap-transition-post-quantum-cryptography (accessed on 24 April 2025).
- Weinstein, Y.; Rodenburg, B. Quantum Computing: Quantifying Current State to Assess Cybersecurity Threats; Project Report PR-24-3812; The MITRE Corporation: Bedford, MA, USA, 2025; Available online: https://www.mitre.org/sites/default/files/2025-01/PR-24-3812-Quantum-Computing-Quantifying-Current-State-Assess-Cybersecurity-Threats.pdf (accessed on 8 May 2025).
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Bernstein, D.J.; Heninger, N.; Lou, P.; Valenta, L. Post-quantum RSA. In Post-Quantum Cryptography, Proceedings of the 8th International Workshop, PQCrypto 2017, Utrecht, The Netherlands, 26–28 June 2017; Lange, T., Takagi, T., Eds.; Springer: Cham, Switzerland, 2017; pp. 311–329. [Google Scholar]
- NIST IR 8547; NIST SP 800-197 (Initial Preliminary Draft) PRE-DRAFT Call for Comments: NIST Proposes to Standardize a Wider Variant of AES. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. Available online: https://csrc.nist.gov/pubs/sp/800/197/iprd (accessed on 24 April 2025).
- NIST Releases First 3 Finalized Post-Quantum Encryption Standards. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. Standards: FIPS 203, FIPS 204 and FIPS 205. Available online: https://www.nist.gov/news-events/news/2024/08/nist-releases-first-3-finalized-post-quantum-encryption-standards (accessed on 24 April 2025).
- FIPS 203; Module-Lattice-Based Key-Encap-sulation Mechanism Standard. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. [CrossRef]
- Status Report on the Fourth Round of the NIST Post-Quantum Cryptography Standardization Process; Technical Report NISTIR 8545; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2025. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2025/NIST.IR.8545.pdf (accessed on 24 April 2025).
- FIPS 204; Stateless Hash-Based Digital Signature Standard. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024. [CrossRef]
- FIPS 205; SPHINCS+ Signature Scheme. National Institute of Standards and Technology: Gaithersburg, MD, USA, 2023. [CrossRef]
- Paquin, C.; Stebila, D.; Tamvada, G. Benchmarking post-quantum cryptography in TLS. In Proceedings of the Post-Quantum Cryptography: 11th International Conference, PQ-Crypto 2020, Paris, France, 15–17 April 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 72–91. [Google Scholar] [CrossRef]
- Barton, J.; Buchanan, W.J.; Pitropakis, N.; Sayeed, D.S.; Abramson, W. Post Quantum Cryptography Analysis of TLS Tunneling on a Constrained Device. In Proceedings of the International Conference on Information Systems Security and Privacy, Prague, Czech Republic, 23–25 February 2019. [Google Scholar]
- Schöffel, M.; Lauer, F.; Rheinländer, C.C.; Wehn, N. On the energy costs of post-quantum KEMs in TLS-based low-power secure IoT. In Proceedings of the International Conference on Internet-of-Things Design and Implementation, Nashville, TN, USA, 18–21 May 2021; pp. 158–168. [Google Scholar]
- Roma, C.A.; Tai, C.E.A.; Hasan, M.A. Energy efficiency analysis of post-quantum cryptographic algorithms. IEEE Access 2021, 9, 71295–71317. [Google Scholar] [CrossRef]
- Patterson, J.C. Cameron Patterson (Paper GitHub Respository)—Source Code, Source Data and Results. 2025. Available online: https://github.com/billbuchanan/energy_pqc (accessed on 5 May 2025).
- TheHWCave. TheHWcave/TC66 (GitHub Respository)—Library for Data Collection from TC66(C) Energy Monitor. 2021. Available online: https://github.com/TheHWcave (accessed on 5 May 2025).
- TheHWcave. TheHWcave—YouTube Channel. 2025. Available online: https://www.youtube.com/@TheHWcave (accessed on 5 May 2025).
- Barker, E.; Roginsky, A.; Vassilev, S. Recommendation for Key Management: Part 1—General; Special Publication 800-57 Part 1 Revision 5; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2020. [Google Scholar]
- Dragon, S. 12 SSL Stats You Should Know in 2025. Available online: https://ssldragon.com/blog/ssl-stats/ (accessed on 6 May 2025).
- Howarth, J. 30+ VPN Statistics, Trends & Facts (2024–2027). Available online: https://explodingtopics.com/blog/vpn-stats (accessed on 2 July 2025).
- Department for Energy Security and Net Zero. Quarterly Energy Prices. Available online: https://www.gov.uk/government/collections/quarterly-energy-prices (accessed on 6 May 2025).
- Amdahl, G.M. Validity of the Single Processor Approach to Achieving Large Scale Computing Capabilities. In Proceedings of the AFIPS Spring Joint Computer Conference, AFIPS ’67, Atlantic City, NJ, USA, 18–20 April 1967; pp. 483–485. [Google Scholar] [CrossRef]
- Centreon. Best Practices to Ensure IT and OT Uptime. Centreon Blog. 2024. Available online: https://www.centreon.com/post-type/best-practices/ (accessed on 6 May 2025).
- Legion of the Bouncy Castle. Bouncy Castle: Open-source Cryptographic APIs for Java and C#. Available online: https://www.bouncycastle.org/ (accessed on 6 May 2025).
- Buchanan, W.J. Security and So Many Things. 2025. Available online: https://asecuritysite.com/ (accessed on 26 April 2025).





| NIST Sec Level | Protocol | Category | Equiv. Bit Size |
|---|---|---|---|
| Level 1 | RSA-1024 | Classic Technology | 80 |
| Level 2 | EC secp160r1 | Elliptic Curve Cryptography | 80 |
| RSA-1536 | Classic Technology | ∼96 | |
| Level 3 | EC secp224r1 | Elliptic Curve Cryptography | 112 |
| RSA-2048 | Classic Technology | 112 | |
| EC P-256 (secp256r1, FIPS 186-4) | Elliptic Curve Cryptography | 128 | |
| ML-DSA-44 | Post-quantum Technology | ∼128 | |
| ML-KEM-512 (Kyber-512, FIPS 203) | Post-quantum Technology | ∼128 | |
| Level 4 | RSA-3072 | Classic Technology | 128 |
| EC P-384 (secp384r1, FIPS 186-4) | Elliptic Curve Cryptography | 192 | |
| ML-DSA-65 | Post-quantum Technology | ∼192 | |
| ML-KEM-768 (Kyber-768, FIPS 203) | Post-quantum Technology | ∼192 | |
| Level 5 | RSA-4096 | Classic Technology | ∼140 |
| EC P-521 (secp521r1, FIPS 186-4) | Elliptic Curve Cryptography | 256 | |
| ML-DSA-87 | Post-quantum Technology | ∼256 | |
| ML-KEM-1024 (Kyber-1024, FIPS 203) | Post-quantum Technology | ∼256 |
| NIST ‘Sec’ Level | Protocol | Category | J/1000 Keygens |
|---|---|---|---|
| Level 1 | RSA-1024 | Classic Technology | 218.64 |
| Level 2 | EC secp160r1 | Elliptic Curve Cryptography | 8.69 |
| RSA-1536 | Classic Technology | 828.84 | |
| Level 3 | EC secp224r1 | Elliptic Curve Cryptography | 10.16 |
| EC P-256 (secp256r1, FIPS 186-4) | Elliptic Curve Cryptography | 7.33 | |
| ML-DSA-44 | Post-quantum Technology | 8.36 | |
| ML-KEM-512 (Kyber-512, FIPS 203) | Post-quantum Technology | 7.61 | |
| RSA-2048 | Classic Technology | 1093.08 | |
| Level 4 | EC P-384 (secp384r1, FIPS 186-4) | Elliptic Curve Cryptography | 17.05 |
| ML-DSA-65 | Post-quantum Technology | 8.97 | |
| ML-KEM-768 (Kyber-768, FIPS 203) | Post-quantum Technology | 7.76 | |
| RSA-3072 | Classic Technology | 4014.84 | |
| Level 5 | EC P-521 (secp521r1, FIPS 186-4) | Elliptic Curve Cryptography | 33.76 |
| ML-DSA-87 | Post-quantum Technology | 9.82 | |
| ML-KEM-1024 (Kyber-1024, FIPS 203) | Post-quantum Technology | 7.89 | |
| RSA-4096 | Classic Technology | 11,952.0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Patterson, J.C.; Buchanan, W.J.; Turino, C. Energy Consumption Framework and Analysis of Post-Quantum Key-Generation on Embedded Devices. J. Cybersecur. Priv. 2025, 5, 42. https://doi.org/10.3390/jcp5030042
Patterson JC, Buchanan WJ, Turino C. Energy Consumption Framework and Analysis of Post-Quantum Key-Generation on Embedded Devices. Journal of Cybersecurity and Privacy. 2025; 5(3):42. https://doi.org/10.3390/jcp5030042
Chicago/Turabian StylePatterson, J. Cameron, William J. Buchanan, and Callum Turino. 2025. "Energy Consumption Framework and Analysis of Post-Quantum Key-Generation on Embedded Devices" Journal of Cybersecurity and Privacy 5, no. 3: 42. https://doi.org/10.3390/jcp5030042
APA StylePatterson, J. C., Buchanan, W. J., & Turino, C. (2025). Energy Consumption Framework and Analysis of Post-Quantum Key-Generation on Embedded Devices. Journal of Cybersecurity and Privacy, 5(3), 42. https://doi.org/10.3390/jcp5030042







