Abstract
Significant vulnerabilities in traditional authentication systems have been demonstrated due to the high dependence on smartphone hardware devices to execute many different and complicated tasks. PINs, passwords, and static biometric techniques have been shown to be subjected to various serious attacks, such as environmental limitations, spoofing, and brute force attacks, and this in turn mitigates the security level of the entire system. In this study, a robust framework for smartphone authentication is presented. Touch dynamic pattern recognitions, including trajectory curvature, touch pressure, acceleration, two-dimensional spatial coordinates, and velocity, have been extracted and assessed as behavioral biometric features. The TOPSIS (Technique for Order of Preference by Similarity to Ideal Solution) methodology has also been incorporated to obtain the most affected and valuable features, which are then fed as input to three different Machine Learning (ML) algorithms: Random Forest (RF), Gradient Boosting Machines (GBM), and K-Nearest Neighbors (KNN). Our analysis, supported by experimental results, ensure that the RF model outperforms the two other ML algorithms by getting F1-Score, accuracy, recall, and precision of 95.1%, 95.2%, 95.5%, and 94.8%, respectively. In order to further increase the resiliency of the proposed technique, the data perturbation approach, including temporal scaling and noise insertion, has been augmented. Also, the proposal has been shown to be resilient against both environmental variation-based attacks by achieving accuracy above 93% and spoofing attacks by obtaining a detection rate of 96%. This emphasizes that the proposed technique provides a promising solution to many authentication issues and offers a user-friendly and scalable method to improve the security of the smartphone against cybersecurity attacks.
1. Introduction
The need for resilient and secure authentication systems has been highly requested due to the continuous incremental increase in the dependency on smartphones in daily activities for professional, personal, and financial operations. It has been pointed out that even though traditional authentication approaches, such as PINs, passwords, and static biometrics, still provide a certain security level in a system, they have been shown to be subjected to many threats, including data sensitivity leakage, phishing, theft, and brute force attacks [1]. Other static biometric methods, e.g., facial recognition and fingerprint, have enhanced and increased the security of the system; however, it has been proven that they are subject to static data constraints, environmental conditions, and spoofing-based attacks [2]. To address the aforementioned shortcomings and improve usability and security, dynamic promising solutions should be adopted [3].
Behavioral biometrics have been considered one of the best prominent solutions for system authentication issues since they analyze in-depth the personal specific interaction patterns, including swipe gestures, touch pressure, and (X, Y) coordinates of spatial movements. These approaches can repeatedly provide authentication and also be adapted to dynamic user behavior compared to traditional approaches, such as static techniques. Motion data and touch dynamics have been investigated by many prior works in order to precisely recognize unique user features; however, they are not strong enough to resist real-world variations and conditions, e.g., counterfeit attempts and environmental and climate modifications [4,5]. Such problems ensure the real need for more resilient techniques.
Interestingly, in order to further refine authentication systems, the three-dimensional (3D) touch sensors have been widely leveraged in many different applications. For instance, to get unique interaction patterns for each person, contemporary techniques have been implemented using 3D touch position and pressure sensitivity, and this significantly elevates the security level and the robustness of the system [6]. Other methodologies, e.g., audio and sound sensors, have been augmented with the 3D touch sensors to be employed for mobile healthcare in order to keep the data of the patient private and secure [7]. To significantly refine the security level of a design, the biometric data, e.g., electroencephalogram (EEG) signal processing, can be combined with sensor data [8]. While these advances contribute to improved security, there is still a need to integrate touch pressure and location data into a unified framework for more robust authentication.
Previous works have not focused on integrating 3D touch pressure data with on-screen finger location data to create a unified framework using decision-making techniques, such as TOPSIS. In this work, we focus on addressing these limitations by presenting a novel smartphone authentication framework. The TOPSIS-based decision-making approach has been augmented with ML techniques to identify and rank critical and valuable features in user behavior. By leveraging only valuable features selected using the TOPSIS approach, and enhancing model resilience using ML algorithms, the proposed technique provides a secure, scalable, and user-friendly authentication system that can thwart many attacks, including cybersecurity threats. In order to refine the resiliency and robustness of the proposed technique, temporal scaling, noise insertion, and spatial perturbation approaches have been incorporated to mimic real-world user responses. This work proposes a secure and lightweight technique against serious threats and addresses current authentication dilemmas by integrating TOPSIS methodology with ML algorithms and dynamic pattern recognition.
The main contributions of this paper are:
- A smartphone authentication application was developed on the Android platform to collect data from 30 participants, each performing 10 attempts.
- A machine learning-based approach was developed for system authentication, where various machine learning algorithms were evaluated to identify the most effective model.
- The TOPSIS method was employed to select key behavioral features, improving the authentication system’s performance by focusing on the most impactful data.
- The system’s resilience was enhanced by applying data perturbation techniques, including noise injection and temporal scaling, to simulate real-world variations.
- The system was tested against four types of cybersecurity attacks—spoofing, lighting variations, orientation changes, and noise injection—to assess its robustness and security.
The key novelty of this research lies in its integrated framework that combines behavioral biometrics, multi-criteria decision-making (TOPSIS), and ensemble machine learning models (RF, GBM, and KNN) for mobile authentication. Unlike prior works that utilized either traditional classification techniques or isolated biometric traits, this study introduces an iterative feature-ranking mechanism that refines the input space using TOPSIS and feeds only the most impactful features into multiple ML models. The proposed system also enhances robustness through real-world-inspired perturbation techniques (e.g., noise injection, temporal scaling), which are often overlooked in previous research. This combination enables the development of a real-time, lightweight, and resilient authentication system that outperforms existing models, achieving an accuracy of 95.2% with enhanced spoofing resistance and environmental adaptability. The rest of the paper is organized as follows: Section 2 gives a brief overview of previous works, including behavioral biometrics for authentication systems, ML techniques in authentication systems as well as decision-making methods, and current challenges in security and usability. Section 3 presents our proposed technique in detail. The experimental results, including the decision and analysis, are given in Section 4. Our conclusion and future works are explained in Section 5.
2. Literature Review
Due to the current advancements and modern sophistication of smart devices, many researchers have implemented biometric authentication to significantly improve the system security and usability [9]. Unfortunately, timeouts and failures are two main drawbacks of conventional authentication techniques, such as pattern locks, PIN codes, basic biometric systems, and passwords. Although traditional authentications are simple, lightweight, and easy to implement, it has been demonstrated that they are subjected to brute force, password theft, and phishing assaults [3,7,10,11]. Once static credentials are compromised, an attacker can get unlimited access to break the system’s security [12]. To address such vulnerabilities, recent research has incorporated ML algorithms and sensor data along with the traditional authentication to offer more secure and resilient systems against many serious attacks [4,13].
2.1. Behavioral Biometrics for Authentication Systems
Biometric authentication systems, including fingerprint and facial recognition, have been introduced as alternatives to address the limitations of traditional methods. These systems offer improved security and user convenience compared to passwords [14,15]. However, facial recognition systems can be spoofed using high-quality images or masks, and fingerprint sensors are susceptible to environmental factors, such as rain, dust, and physical degradation [16,17], and are vulnerable to advanced spoofing techniques [18,19]. The aforementioned challenges emphasize the need for resilient, dynamic, and adaptive authentication methods capable of addressing both security and usability issues. In [20], the authors combined fingerprint, facial recognition, and iris scanning as alternatives to traditional methods. Although the proposal utilized physiological characteristics for user verification and provides enhanced security, it is subjected to environmental factors, such as humidity, lighting conditions, and device orientation [21]. Furthermore, biometric data is susceptible to spoofing, where adversaries can mimic user credentials [19,22]. This elevates the need for behavior-based authentication approaches.
Behavioral biometrics rely on user interaction patterns, such as swipe dynamics, typing speed, and touch pressure, to enable continuous authentication. Unlike static physiological biometrics, behavioral methods are dynamic and adaptive to changes in user behavior over time, and this, in turn, provides resilience against spoofing attempts and adversarial attacks [6]. Many studies have shown the impact of behavioral biometrics on the performance of smartphone authentication. Smith et al. have employed swipe trajectories and pressure levels in order to differentiate impostors from genuine persons [23]. In [24], Wang et al. presented the touch dynamics during password input, and the results indicated that the proposed technique could highly elevate the overall performance of the authentication systems. Compared to traditional biometrics, behavioral biometrics are non-intrusive, have flexible authentication, and are difficult to duplicate. Such techniques render researchers to focus further on individuals with more features, e.g., keystroke patterns, gait, and touch dynamics [20,25]. It has been proven that touch patterns can effectively distinguish between authentic users and impostors, and this improves system security [26,27,28]. Unfortunately, behavioral biometrics are not robust in real-world conditions, such as international spoofing attempts and different environmental circumstances. Such drawbacks can be mitigated by augmenting behavioral biometrics with decision-making and ML algorithms.
2.2. ML Techniques in Authentication Systems and Decision-Making Methods
ML algorithms, such as Support Vector Machines (SVM), Decision Trees, and Neural Networks have provided promising solutions for improving the system performance and identifying user-specific patterns [29]. Other ML algorithms, such as Random Forest (RF) and Gradient Boosting Machine (GBM) based multi-classifiers, further improve both the generalization and the performance by decreasing overfitting [30]. ML techniques have shown exceptional performance in processing complicated behavioral data, and this allows to effectively classify user interactions. For example, both RF and SVM algorithms have been leveraged to analyze touch dynamics data and achieved high accuracy for user authentication [31,32,33]. Pryor et al. merged RF and SVM classifiers to process touch behavior datasets and obtained accuracy exceeding 85% [31]. However, in real-time performance for a flawless user experience, the computational complexity of such a technique with a high protection level still poses a challenge [33]. To clearly position the proposed method in relation to existing work, Table A1 summarizes a set of recent behavioral biometric authentication approaches. The comparison includes dataset type, applied algorithms, reported accuracy, benefits, and limitations. This enables a direct contrast of our method’s novelty and performance.
As shown in Table A1, while several previous works explored mobile behavioral biometrics, few integrated multi-criteria decision-making into the feature engineering pipeline. Our proposed method demonstrates competitive accuracy while also addressing interpretability, perturbation resilience, and feasibility for real-time use, filling a key gap identified in prior literature. To further reduce the computational penalty and complexity in real-time performance, ML models can be incorporated with decision-making techniques, such as TOPSIS, to select only valuable features [34,35]. The hybrid ML and decision-making frameworks can help address existing issues in authentication systems. The TOPSIS and Analytic Hierarchy Process (AHP) techniques are examples of Multi-Criteria Decision-Making (MCDM) approaches that can be employed to prioritize and rank input features in many different applications. Specifically, TOPSIS identifies the highest impact parameters on a system to provide best possible solutions [34,35], and this can help to successfully rank features in many ML models [34]. However, integrating TOPSIS and ML with behavioral biometrics for smartphone authentication is still unrevealed in the cybersecurity field. Recent deep learning approaches, particularly those leveraging convolutional and recurrent neural networks (CNNs and RNNs), have demonstrated notable success in behavioral biometrics. Wu et al. (2020) [36] proposed a hybrid framework that enhances fingerprint authentication by integrating behavioral traits to defeat puppet attacks. Their method utilizes deep learning to extract subtle user-specific behaviors in combination with liveness detection. While such deep learning models offer high accuracy, they often require large datasets and high computational resources, which limits their feasibility for real-time mobile authentication scenarios. In contrast, our proposed framework adopts a lightweight architecture combining TOPSIS-based feature selection with classical ensemble models (RF, GBM, and KNN), ensuring interpretability and efficiency while maintaining high accuracy in touch-based behavioral authentication.
2.3. Security and Usability Challenges in System Authentication
It is not easy to balance between security and usability in authentication systems. Increasing the security level of a design often leads to an increase in the system complexity that could negatively affect the user experience [37,38]. For instance, while strong authentication systems employing multi-factor approaches provide strong resistance against both spoofing and adversarial attacks, they induce user frustration due to the increase in time complexity or repeated queries for user verification [19]. Similarly, when environmental factors, e.g., lighting or humidity, disrupt sensor detection sensitivity, highly sensitive biometric systems may not function properly, leading to the production of a wrong output [39,40,41].
It is worth noting that repeatedly tracking the biometric features of users and precisely extracting valuable features, such as touch pressure, swipe dynamics, and trajectory patterns, significantly increase the system’s robustness [42,43]. However, the computations of real-time processing will be highly increased, and this renders the system unsuitable for seamless use. Interestingly, decision-making techniques, e.g., TOPSIS, can be utilized to select only valuable features, and this, in turn, ensures that the system remains user-friendly and secure and decreases the computational system penalty [44,45]. Although the use of TOPSIS introduces an additional decision-making step, it serves as a valuable dimensionality reduction technique that simplifies the learning process. By selecting only the most relevant features, TOPSIS contributes to reduced computational load and enhances real-time performance, making the system suitable for practical deployment on resource-constrained devices such as smartphones.
The goal of this work is to develop a lightweight and robust authentication framework that is dynamically adapted to the user environments and conditions in real-world applications [38]. Even though significant progress has been achieved in the field of biometric authentication, current existing techniques are still subjected to cybersecurity attacks and are not robust to real-world conditions. To address the aforementioned shortcomings, in this paper, different ML algorithms are integrated with TOPSIS and behavioral biometrics to get a secure, resilient, and lightweight prominent solution for smartphone authentication.
3. Methodology
In this section, we present the proposed touch-based authentication framework, as illustrated in Figure 1. The process begins by collecting data from thirty participants, each using the 3D touch screen on a Samsung Galaxy A72 smartphone with ten attempts. This data is gathered and recorded through a custom-developed application named the Authentication Application (AA), which was implemented on the Android platform. The AA captures sensitive data, including touch pressure, X and Y coordinates, velocity, acceleration, and trajectory curvature, as entered by the participants. This data is stored in a file named “dataset collection”.
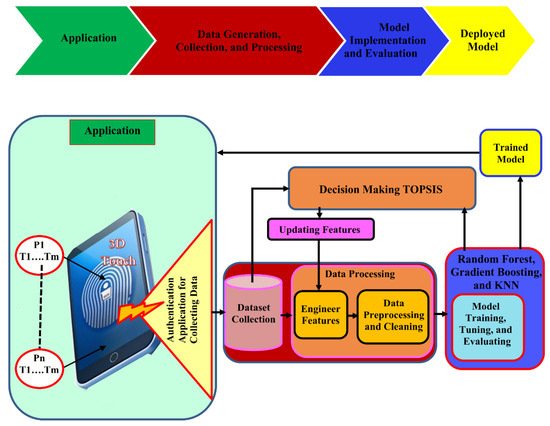
Figure 1.
The life cycle of our complete framework.
Next, the TOPSIS decision-making approach is applied to identify the most impactful features while eliminating those that have minimal effect. The dataset is then preprocessed and cleaned. Following this, three machine learning algorithms—Random Forest, Gradient Boosting, and K-Nearest Neighbors (KNN)—are implemented and trained. During the training phase, the TOPSIS approach iteratively evaluates the results from each ML model, updates the feature set, and refines the data processing based on the newly identified valuable features. Once the model is trained, it is ready for use in mobile authentication. The complete framework comprises five main processes:
3.1. Data Generation and Preprocessing
The 3D touch sensors of the Samsung Galaxy A72 device, shown in Figure 2, were experimentally utilized to collect data from touch-based behavioral biometrics. The participant group was selected to include a balanced distribution of gender (15 males and 15 females) and age range (18 to 50 years old), ensuring moderate behavioral diversity within the dataset. Ethical considerations were a fundamental aspect of this study to ensure the responsible collection and use of data. Prior to participation, all individuals provided informed consent, ensuring their awareness and voluntary involvement in the study. To protect participant privacy, all collected data was anonymized, preventing the identification of individual contributors. Every participating person gave ten different pattern recognition samples that comprised typing phrases, unlocking the device, and performing swipe gestures. Each record in the dataset was labeled based on its authentication outcome. For training purposes, valid interactions were encoded as “1” and invalid or unauthorized interactions were encoded as “0”, forming a binary classification setting. Our authentication application, implemented leveraging the Android system of Samsung Galaxy A72, received the incoming data with high resolution that are entered by the participating persons using the 3D touch screen. It is worth mentioning that the collected dataset has been encrypted to prohibit an attacker or unauthorized user from accessing it. In order to verify that this work is within the conduct research role, it follows the international organization standards in research integrity as it only deals with human participants. The main five extracted features of dynamic pattern recognition that are directly obtained from the 3D touch screen contain the following:
- Touch pressure (P): The intensity of pressure applied during interactions.
- Trajectory curvature (T): The geometric path traced by the finger’s movement.
- Velocity (V): The rate of change in position during swipe gestures.
- Spatial coordinates (X, Y): The precise position of the finger on the 3D touch screen.
- Acceleration (A): The change in velocity over time.
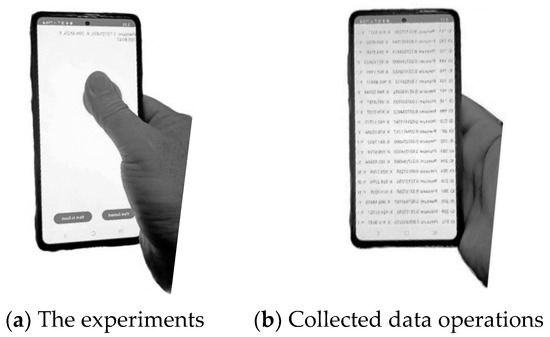
Figure 2.
Dataset generation and collection using dynamic pattern recognition.
The resulting dataset spans a broad spectrum of user behaviors and scenarios designed to enhance the robustness and adaptability of the proposed system. Noise removal, value normalization, and handling of missing data have been performed during the data preprocessing in order to ensure consistent and trustworthiness of the collected dataset. We also validated the dataset to make sure data reliability and integrity. To keep the collected data reliable and uniform, the mean for numerical features and the mode for nominal features have been leveraged. Note that, the interquartile range (IQR) approach has been used to recognize trajectory data, touch pressure, and velocity and then either exchanged with median values or eliminated for consistency purposes. Also, repeated records or entries have been recognized and then eliminated to avoid bias in the training process, and the entire features have been carefully normalized to a common scale, in order to make sure that they are matchable with each used model.
3.2. Feature Ranking and Engineering Leveraging TOPSIS Methodology
In order to rank the current entered and extracted features in terms of their effectiveness on the system performance, the TOPSIS methodology has been utilized. A similar procedure in [35,44,46] has been used to implement and run the TOPSIS methodology. First of all, the decision matrix D has been built (see Equation (1)), in which each given column corresponds to the assessment metrics, and each given row reflects the feature. The assessment metrics consist of the main measurement components, e.g., correlation, variance, and entropy. Note that the aim of leveraging the TOPSIS methodology is to recognize only the most affected features in order to refine the accuracy of the system.
Next, to ensure the features’ comparability, the D has been normalized leveraging the following formula, as seen in Equation (2):
After D is normalized, weights wj have been applied to normalized values in order to drive the weighted normalized matrix, as shown in Equation (3):
The worst and possible values for each metric are represented by negative-ideal (A−) and ideal (A+) formulas, respectively, as follows [46], in Equations (4) and (5):
J′ signifies non-beneficial criteria, while J refers to beneficial criteria.
In order to find the actual distance of each extracted feature from the negative-ideal and ideal solutions, the separation measures (S− and S+) have been performed, as follows, in Equation (6):
All given features have been ranked based on their values in Ci, in which higher values reflect high impact [47]. The relative closeness (Ci) of each feature to the ideal solution has been calculated, as follows, in Equation (7):
It is worth mentioning that the velocity, trajectory curvature, and touch pressure have been proven to represent the most valuable and effective features based on our experimental results obtained from the TOPSIS technique. Such valuable features have been demonstrated to refine the ML performance by increasing the model accuracy and mitigating the complexity of the authentication design compared to implementing the technique without incorporating the TOPSIS methodology. The choice of TOPSIS as the feature selection method was driven by its computational simplicity, ease of interpretability, and suitability for real-time mobile authentication scenarios. Unlike other MCDM methods, such as AHP and VIKOR, which may require extensive pairwise comparisons or introduce complex weighting schemes, TOPSIS provides a straightforward and scalable ranking process based on distance metrics. Additionally, while embedded feature selection methods within machine learning algorithms (e.g., L1 regularization) are widely used, they often lack cross-model transparency, making them less effective for a hybrid ensemble setup. The iterative approach adopted in this study refines the ranked feature set by incorporating feedback from the classification performance, thus enhancing both the selection quality and the final model accuracy.
3.3. ML Models
In order to refine the performance of the user authentication technique, three different ML algorithms—Gradient Boosting Machines (GBM), Random Forest (RF), and K-Nearest Neighbors (KNN)—have been employed. Each on these three models have been trained with and without incorporating the TOPSIS methodology.
- Gradient Boosting Machines (GBM): GBM iteratively builds decision trees to minimize prediction errors, aiming to improve the model’s predictive accuracy. The prediction at each iteration is represented in Equation (8):
- 2.
- Random Forest (RF): RF constructs multiple decision trees during training and combines their outputs—through majority voting for classification or averaging for regression—with the objective of enhancing predictive performance. The prediction function is given in Equation (9) below:
- 3.
- K-Nearest Neighbors (KNN): KNN aims to classify data points by determining the majority label of their k-nearest neighbors, using a distance metric such as the Euclidean distance [50], as shown in Equation (10):
3.4. Data Perturbation Techniques
Data perturbation approaches, noise injection, temporal scaling, and spatial perturbations have been used to further refine the robustness of the proposed technique and the generalization capabilities of the ML models. The main purpose of incorporating such approaches is to imitate the real-world noise and variability in personal actions and responses by increasing the ability of the proposal to effectively deal with different conditions and circumstances.
- Spatial perturbations: In order to mimic natural hand movements, small random Perturbation has been applied to the spatial coordinates (X, Y) based on the following Equation (11):
- Noise injection: To emulate variability in real-world interactions, random noise is augmented to the extracted features, e.g., velocity and touch pressure, as shown in Equation (12):
- Temporal scaling: To emulate various interaction styles, interaction durations have been further scaled to reflect variations in user speed, as shown in Equation (13):
3.5. Assessing and Testing the Robustness of the Proposal
The collected dataset has been partitioned into 80% and 20% for training and validation, respectively, in order to assess the performance of the ML models. To reduce the risk of overfitting, data normalization was applied, and robustness was improved using perturbation-based techniques, including Gaussian noise injection, temporal scaling, and variations in user behavior. These strategies helped ensure that the proposed models remain reliable under diverse usage conditions. Although k-fold cross-validation was not applied, the applied perturbation and evaluation techniques support the reported model performance. Several testing approaches and evaluation metrics have been used to evaluate the robustness and effectiveness of the proposed technique, aiming to get a highly reliable and accurate authentication system under different circumstances and conditions:
- Recall (Sensitivity): This metric quantifies the proportion of true positives among all actual positives, ensuring genuine users are accurately recognized [8], see Equation (14):
- Precision: A critical metric for evaluating the proportion of true positives among all predicted positives, reducing false alarms, see Equation (15):
High precision minimizes false-positive rates, which is crucial to preventing unauthorized access [8].
- Accuracy: The primary metric to measure the ratio of correctly classified instances to the total number of instances, see Equation (16):
- F1-Score: A balanced measure combining precision and recall, particularly useful in scenarios with class imbalances or where addressing the trade-off between precision and recall is critical [8], Equation (17):
- Confusion Matrix (CM): In order to evaluate the system’s performance, the CM has been used, in which is can offer information about true negatives, false negatives, true positives, and false positives. This CM can provide valuable details about the model operation [54].
- Resilience testing [53]: The robustness of the proposed technique has been assessed under three different conditions. First, environmental variations are tested, including different lighting conditions (bright, dim, and dark) and humidity levels, to ensure stable feature extraction and classification accuracy. Second, variations in user behavior, such as changes in touch speed, pressure intensity, and swipe dynamics, are tested to assess the system’s ability to adapt, with performance measured by accuracy and F1-Score. Finally, the system’s performance is tested under different device orientations—portrait, landscape, and tilted—to ensure consistency across various handling scenarios.
- Spoofing Detection Rate (SDR): The effectiveness of the proposed technique can be assessed by using the SDR measurement to reveal and prevent spoofing attempts-based attacks. The mathematical equation of SDR is as in the following [22], see Equation (18):
All experiments were conducted on a machine with an Intel Core i7-12700H CPU, 16 GB RAM, running Windows 11 Pro. The implementation used Python 3.10 with Scikit-learn 1.3.2 and NumPy 1.24.
4. Experimental Results
The performance assessment of our proposed technique based on smartphone authentication is given in detail in this section, in which the TOPSIS methodology-based feature ranking has been combined with different ML algorithms. The evaluation of our proposal is mainly concentrated on the performance criteria, a comprehensive analysis of the confusion matrix to evaluate the classification accuracy, and robustness testing under real-world conditions and circumstances. The proposed framework was implemented on three main layers to correctly perform and authenticate each participating user. First of all, the touch-based dynamic pattern recognition data, including the gyroscope, 3D touch sensor, and accelerometer, were used for data collection and generation layer. This layer was leveraged to extract real-time features, such as coordinate curves for trajectories, 2D spatial coordinates, touch pressure, acceleration, and velocity. Data preparation and processing was the second layer that was used to carry out data preprocessing, including standardization, normalization, and noise mitigation or reduction. During data processing, the TOPSIS method was implemented and applied to carefully rank the extracted valuable features. The ranked valuable features were then fed as input into three different ML models—RF, KNN, and GBM—for user classification purposes. Finally, the application layer was used to classify the findings to the authenticated persons or users in order to give immediate feedback and input for denying or granting access.
The proposed framework processes the incoming dynamic touch information in real-time, in which optimized algorithms have been leveraged for low-latency performance in order to ensure a better, smooth operation. The primary sequence of the given events was as follows: the personal touch data was first entered and preprocessed; then, the ranked affected features were fed into the trained ML models; and next, the classification results of the participated persons were pulled up, and the system either refuses or allows the user to enter.
4.1. Feature Importance Analysis
The most affected and significant features for personal authentication are listed in Table 1, in which the ranking of the dynamic pattern recognition (behavioral biometrics) based on the TOPSIS methodology is presented. As illustrated in the Table, the three top-ranked values of the affected and valuable features were the touch force (pressure), abscissa (X coordinate), and duration (velocity). Note that these features have been chosen based on their highest essentiality. Then, they were fed as a primary input into each of the implemented ML models instead of considering all of the entered features by the users. This helps to further refine the performance of the system and optimize the entire framework.

Table 1.
Performance comparison of classifiers with and without TOPSIS on the same dataset.
4.2. Performance Evaluation
The performance assessment of the three implemented ML models—KNN, RF, and GBM—with and without incorporating TOPSIS methodology-based feature ranking is elucidated in Table 2. Based on the experimental results, it is pointed out that the KNN model performed well on small datasets; however, it encountered a problem with scalability when the data size was significantly elevated. The GBM model accomplished high accuracy due to its iterative boosting process, yet it needed longer training time. RF model offered a good solution balance between computational efficiency and accuracy, and this renders the system more appropriate for real-time applications and processing systems. Note that the RF model produced the highest accuracy compared to the two other models, KNN and GBM. Also, it was pointed out that classification accuracy was refined when TOPSIS-methodology-based feature chosen ranking was augmented, and this further emphasized that the feature selection approach was valuable. A good balance between computational efficiency and performance could be obtained based on this comparative assessment leveraging the most suitable model for authentication system purposes. To further clarify the efficiency of this trade-off, it was observed that the application of TOPSIS improved training efficiency by reducing the input feature set, which, in turn, lowered the overall computational complexity during model training. This supports the use of feature ranking in real-time mobile authentication, where reducing computational latency is a critical requirement. Although TOPSIS introduces an additional preprocessing step, it helps reduce the input dimensionality by eliminating less relevant features before classification. This dimensionality reduction led to faster training and inference processes, as the classifiers operated on fewer inputs. While no exhaustive benchmarking was conducted, the observed improvement in training efficiency and resource usage supports the suitability of this method for real-time mobile environments.

Table 2.
Performance metrics of the proposed models.
The comparative results shown in Table 2 reflect the influence of applying TOPSIS-based feature ranking before classification. All three classifiers demonstrated improved performance metrics when trained on the reduced feature set selected by TOPSIS. This suggests that TOPSIS effectively filtered out less informative or redundant features, leading to sharper class boundaries and reduced model variance. While a formal decision-boundary visualization is beyond the current scope, the observed increase in precision and F1-Score indicates enhanced separability between genuine and impostor interactions.
4.3. Confusion Matrix Results
In order to verify both areas and strengths of our proposal, the confusion matrix (CM) has been leveraged to further show whether our design is able to successfully classify personal interactions based on the selected features. Figure 3 illustrates CM outcomes for the classification performance of our proposed technique based on the RF model for the smartphone authentication system.
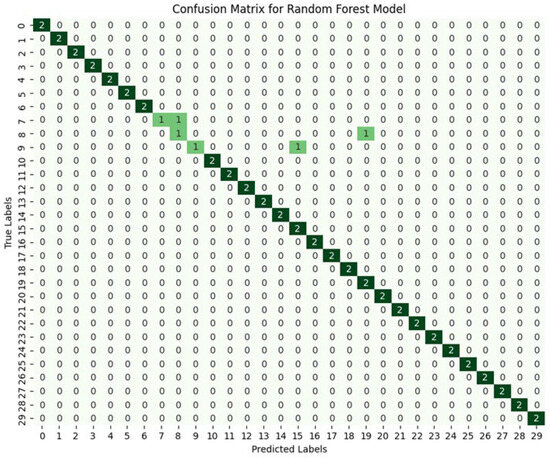
Figure 3.
The Confusion Matrix (CM) outcomes of our proposal.
Firstly, the matrix illustrates diagonal clarity, where the majority of predictions are correctly classified. For example, most of the users have been successfully classified based on prediction accuracy, and this shows the great performance of our proposal. The given simulation results indicate that our proposed technique is able to correctly recognize between user touch dynamic patterns based on valuable selected features, including spatial coordinates (X, Y), interaction duration or velocity, and touch pressure intensity.
However, with some minor emerged errors, the matrix also reveals misclassification cases, represented by off-diagonal values, and this could be due to overlapping behavioral patterns among participated users, leading to the possibility of overlapping among classes. For example, one sample from each of the users 6, 7, and 8 have been misclassified as users 8, 19, and 15, respectively, due to some overlapping in dynamic pattern recognition, e.g., similar swipe trajectories and/or similar touch pressure levels among some participated users. Note that some minor deviations in performance may lead to missing data in some experiments when taking into consideration the differences in some samples among the participating users.
Even though some numbers have not been classified correctly, the correct classifications shown on the main diagonal of the CM elucidates the significant effectiveness of the TOPSIS methodology-based feature extraction. Also, the high correct predictions in the matrix diagonal imply that the selected features, e.g., spatial X coordinates, trajectory curvature, and touch pressure intensity, are the most promising ones. By incorporating only valuable features and optimizing the hyperparameters of the model, the proposed technique can offer an excellent balance among different classes, and this, in turn, could lead to mitigate the wrong classification and obtain better performance.
4.4. Evaluating the Strength of Our Proposal
In order to examine the resiliency of the proposal-based RF model under various real-world circumstances, four different cybersecurity attacks have been incorporated, as elucidated in Table 3. The reason behind selecting the RF model for the testing is that the FR model provides better accuracy compared to the two other models, as shown previously in Table 2. The proposed technique showed excellent resiliency against spoofing attempts-based attacks in which the spoofing detection rate reached 96%, and this emphasized that the proposed techniques can successfully prohibit adversarial access-based attacks. Moreover, even when random noise has been inserted into the primary input dataset, the framework is illustrated to be strong against such noise insertion data-based attacks via accomplishing 90.8% accuracy. The proposal can also prevent environmental variations or conditions, including device orientation adjustments and lighting changes, by achieving 93.2% and 92.3% accuracies, respectively. Given the aforementioned experimental results, the proposal is shown to be resilient against different conditions and circumstances, and this makes it appropriate for real-world processing systems and applications.

Table 3.
Testing the resiliency of the proposed technique-based RF model against four serious cybersecurity threats.
4.5. Discussion Summary
It has been proven that the TOPSIS methodology can effectively be leveraged to select the most affected features, and this, in turn, increases the security level of the authentication system. The three extracted features, velocity, X coordinate, and touch pressure, have been recognized to be the most affected and valuable features and can significantly elevate the classification accuracy. As previously explained via the experimental findings, the hybrid ML models and these affected features have refined the performance of the system significantly. It has been pointed out that when the RF combined with the TOPSIS methodology-based feature was chosen, it can accomplish the highest accuracy compared to the two other algorithms. Under different environmental circumstances and conditions, e.g., device orientation and modifications in lighting density, our proposed technique has been carefully evaluated in terms of resiliency and robustness with minimal performance penalty and high detection rates in spoofing attempt-based attacks. Moreover, the proposal keeps achieving a high level of accuracy, underscoring the combined strength of the chosen features and robustness’s model in refining both accuracy and reliability in real-world applications and real system processing even when noise was inserted into the original dataset. Although the applied perturbation methods proved useful in enhancing model robustness, it is acknowledged that their parameters were heuristically defined. The absence of a detailed sensitivity analysis may limit the understanding of how perturbation intensity or scaling affects classification accuracy and stability. Future work will address this gap by systematically evaluating a range of perturbation settings and quantifying their impact on model performance.
Even though the proposed framework has shown many advancements, it also has some limitations. For example, environmental conditions and highly dependency on variations in device orientation and lighting density can slightly impact on collected and generated datasets. Although the dataset consisted of 30 participants, this sample size is considered relatively small and may not fully capture the diversity of behavioral biometric patterns observed in real-world settings. To enhance generalizability, future work will involve expanding the dataset by including a broader range of participants from different groups and evaluating the system across multiple smartphone platforms. However, it should be noted that the evaluation was conducted using a single smartphone model (Samsung Galaxy A72), which may limit the generalizability of the results across different hardware platforms. To address this limitation, future work will include validating the proposed framework on multiple smartphone devices with diverse hardware and sensor configurations to better assess its practical applicability under real-world conditions. Finally, significant additional resources might be requested in some of the designed and implemented ML algorithms, e.g., GBM, and this, in turn, potentially impacts both the computational penalty and the real-time performance.
5. Conclusions and Future Work
A smartphone framework-based authentication technique has been designed and implemented, leveraging the TOPSIS technique-based extracted feature ranking, dynamic pattern recognition (behavioral biometrics), and different ML models. It has been proven that when RF is incorporated, the proposed technique performs better than the other two ML algorithms, with a reported accuracy of 95.2%. The system is also resilient against serious cybersecurity attacks, achieving over 93% accuracy against environmental changes and 96% detection rates against spoofing attacks. By considering only critical features, such as touch pressure, velocity, and trajectory curvature, the framework balances security and usability, enabling real-time adaptability for end users. The proposed technique provides a lightweight, robust, secure, and scalable authentication solution when the TOPSIS decision-making technique and ML algorithms are integrated into the design. Despite promising results, this work has limitations, including the use of a small dataset and the lack of testing against extreme environmental factors. In future work, we plan to expand our datasets further by considering multi-modal biometrics, such as facial recognition and fingerprints, and leveraging deep learning algorithms, such as CNN, DNN, and RNNs, to enhance performance in real-world applications and improve energy efficiency.
Author Contributions
Conceptualization, M.L.S.; methodology, M.L.S., Q.A. and M.M.H.; software, M.M.H. and N.S.A.; validation, M.L.S., A.A.Y. and R.A.A.; formal analysis, S.H.T. and S.K.A.; investigation, M.L.S. and Q.A.; resources, M.F. and A.H.K.; data curation, S.L.Q. and N.S.A.; writing—original draft preparation, M.L.S.; writing—review and editing, Q.A., M.M.H. and N.S.A.; visualization, R.A.A. and S.H.T.; supervision, M.L.S.; project administration, M.L.S. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
The data is unavailable due to privacy or ethical restrictions.
Acknowledgments
We thank the participants who contributed their touch dynamics data to this study.
Conflicts of Interest
The authors declare no conflicts of interest.
Appendix A

Table A1.
Comparative summary of recent behavioral biometric authentication methods on mobile devices.
Table A1.
Comparative summary of recent behavioral biometric authentication methods on mobile devices.
| Study | Dataset Type | Algorithm Used | Accuracy | Advantages | Limitations |
|---|---|---|---|---|---|
| Wang et al. (2020) [55] | HMOG + BioIdent | RF, SVM, KNN | 82% | Multi-sensor fusion, practical for mobile | Moderate accuracy, dataset limitations |
| Fereidooni et al. (2023) [56] | Motion Sensors Only | Siamese Network (Few-Shot) | 97% | Continual auth., scalable framework | Needs specific motion events |
| Dave et al. (2022) [57] | Mixed Behavioral Dataset | Deep Metric Learning | >95% | On-device training, spoof-resistant | Complex deployment |
| Proposed Work | Touch + TOPSIS Features | RF + GBM + KNN | 95.2% | Dynamic feature ranking, robust, real-time | Limited dataset size (future work) |
References
- Shaheed, K.; Szczuko, P.; Kumar, M.; Qureshi, I.; Abbas, Q.; Ullah, I. Deep learning techniques for biometric security: A systematic review of presentation attack detection systems. Eng. Appl. Artif. Intell. 2024, 129, 107569. [Google Scholar] [CrossRef]
- Shuwandy, M.L.; Zaidan, B.B.; Zaidan, A.A. Novel Authentication of Blowing Voiceless Password for Android Smartphones Using a Microphone Sensor; Multimedia Tools and Applications; Springer: Berlin/Heidelberg, Germany, 2022. [Google Scholar]
- Ryu, R.; Yeom, S.; Herbert, D.; Dermoudy, J. The design and evaluation of adaptive biometric authentication systems: Current status, challenges and future direction. ICT Express 2023, 9, 1183–1197. [Google Scholar] [CrossRef]
- Shuwandy, M.L.; Zaidan, B.B.; Zaidan, A.A.; Albahri, A.S. Sensor-Based mHealth Authentication for Real-Time Remote Healthcare Monitoring System: A Multilayer Systematic Review. J. Med. Syst. 2019, 43, 2019. [Google Scholar] [CrossRef] [PubMed]
- Zurita, B.; Bosque, S.; Fuertes, W.; Macas, M. Social Engineering Shoulder Surfing Attacks (SSAs): A Literature Review. Lessons, Challenges, and Future Directions. In Advanced Research in Technologies, Information, Innovation and Sustainability; Guarda, T., Portela, F., Diaz-Nafria, J.M., Eds.; Springer Nature: Cham, Switzerland, 2024; pp. 220–233. [Google Scholar]
- Shuwandy, M.L.; Aljubory, H.A.; Hammash, N.M.; Salih, M.M.; Altaha, M.A.; Alqaisy, Z.T. BAWS3TS: Browsing Authentication Web-Based Smartphone Using 3D Touchscreen Sensor. In Proceedings of the 2022 IEEE 18th International Colloquium on Signal Processing and Applications, CSPA 2022, Selangor, Malaysia, 12 May 2022; pp. 425–430. [Google Scholar] [CrossRef]
- Shuwandy, M.L.; Zaidan, B.; Zaidan, A.; Albahri, A.; Alamoodi, A.; Albahri, O.; Alazab, M. mHealth authentication approach based 3D touchscreen and microphone sensors for real-time remote healthcare monitoring system: Comprehensive review, open issues and methodological aspects. Comput. Sci. Rev. 2020, 38, 100300. [Google Scholar] [CrossRef]
- Younis, A.Y.; Shuwandy, M.L. Biometric Authentication Utilizing EEG Based-on a Smartphone’s 3D Touchscreen Sensor. In Proceedings of the 2023 IEEE 14th Control and System Graduate Research Colloquium (ICSGRC), Shah Alam, Malaysia, 5 August 2023; IEEE: Pistacaway, NJ, USA, 2023; pp. 169–174. [Google Scholar]
- Bhagavatula, R.; Ur, B.; Iacovino, K.; Kywe, S.M.; Cranor, L.F.; Savvides, M. Biometric authentication on iphone and android: Usability, perceptions, and influences on adoption. In Proceedings of the USEC ’15: Workshop on Usable Security, San Diego, CA, USA, 8 February 2015. [Google Scholar]
- Constantinides, A.; Belk, M.; Fidas, C.; Beumers, R.; Vidal, D.; Huang, W.; Bowles, J.; Webber, T.; Silvina, A.; Pitsillides, A. Security and usability of a personalized user authentication paradigm: Insights from a longitudinal study with three healthcare organizations. ACM Trans. Comput. Healthc. 2023, 4, 1–40. [Google Scholar] [CrossRef]
- Saadi, Z.M.; Sadiq, A.T.; Akif, O.Z.; Farhan, A.K. A Survey: Security Vulnerabilities and Protective Strategies for Graphical Passwords. Electronics 2024, 13, 3042. [Google Scholar] [CrossRef]
- Aslan, Ö.; Aktuğ, S.S.; Ozkan-Okay, M.; Yilmaz, A.A.; Akin, E. A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions. Electronics 2023, 12, 1333. [Google Scholar] [CrossRef]
- Shuwandy, M.L.; Jouda, A.; Ahmed, M.; Salih, M.M.; Al-Qaysi, Z.; Alamoodi, A.; Garfan, S.; Albahri, O.; Zaidan, B.; Albahri, A. Sensor-Based Authentication in Smartphone: A Systematic Review. J. Eng. Res. 2024, in press. [Google Scholar] [CrossRef]
- Sathya, K.; Esther, J.; Kavitha, S.; Kamalakumari, J. Facetpass-Intelligent Facial Recognition Authentication System Security and Usability. In Proceedings of the 2024 2nd International Conference on Artificial Intelligence and Machine Learning Applications Theme: Healthcare and Internet of Things (AIMLA), Toronto, ON, Canada, 19–20 August 2025; IEEE: Pistacaway, NJ, USA, 2024; pp. 1–6. [Google Scholar]
- Harikrishnan, D.; Kumar, N.S.; Joseph, S.; Nair, K.K. Towards a fast and secure fingerprint authentication system based on a novel encoding scheme. Int. J. Electr. Eng. Educ. 2024, 61, 100–112. [Google Scholar] [CrossRef]
- Wone, A.; Di Manno, J.; Charrier, C.; Rosenberger, C. Impact of environmental conditions on fingerprint systems performance. In Proceedings of the 2021 18th International Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 13–15 December 2021; IEEE: Pistacaway, NJ, USA, 2021; pp. 1–5. [Google Scholar]
- Liu, S.; Yang, B.; Yuen, P.C.; Zhao, G. A 3D mask face anti-spoofing database with real world variations. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition Workshops, Las Vegas, NV, USA, 26 June–1 July 2016; pp. 100–106. [Google Scholar]
- Ametefe, D.S.; Sarnin, S.S.; Ali, D.M.; Muhamad, W.N.W.; Ametefe, G.D.; John, D.; Aliu, A.A. Enhancing Fingerprint Authentication: A Systematic Review of Liveness Detection Methods Against Presentation Attacks. J. Inst. Eng. Ser. B 2024, 105, 1451–1467. [Google Scholar] [CrossRef]
- Toli, C.-A.; Preneel, B. Provoking security: Spoofing attacks against crypto-biometric systems. In Proceedings of the 2015 World Congress on Internet Security (WorldCIS), Dublin, Ireland, 19–21 October 2015; pp. 67–72. [Google Scholar] [CrossRef]
- Sharif, M.I.; Mehmood, M.; Sharif, M.I.; Uddin, M.P. Human gait recognition using deep learning: A comprehensive review. arXiv 2023, arXiv:2309.10144. [Google Scholar]
- Alrawili, R.; AlQahtani, A.A.S.; Khan, M.K. Comprehensive survey: Biometric user authentication application, evaluation, and discussion. Comput. Electr. Eng. 2024, 119, 109485. [Google Scholar] [CrossRef]
- Menotti, D.; Chiachia, G.; Pinto, A.; Schwartz, W.R.; Pedrini, H.; Falcao, A.X.; Rocha, A. Deep representations for iris, face, and fingerprint spoofing detection. IEEE Trans. Inf. Forensics Secur. 2015, 10, 864–879. [Google Scholar] [CrossRef]
- Aviv, A.J.; Gibson, K.; Mossop, E.; Blaze, M.; Smith, J.M. Smudge Attacks on Smartphone Touch Screens. In Proceedings of the 4th USENIX workshop on offensive technologies (WOOT 10), Washington, DC, USA, 9 August 2010. [Google Scholar]
- Wang, K.; Zhou, L.; Zhang, D. Biometrics-Based Mobile User Authentication for the Elderly: Accessibility, Performance, and Method Design. Int. J. Hum. Comput. Interact. 2024, 40, 2153–2167. [Google Scholar] [CrossRef]
- Yampolskiy, R.V.; Govindaraju, V. Behavioural biometrics: A survey and classification. Int. J. Biom. 2008, 1, 81–113. [Google Scholar] [CrossRef]
- Pelto, B.; Vanamala, M.; Dave, R. Your identity is your behavior-continuous user authentication based on machine learning and touch dynamics. In Proceedings of the 2023 3rd International Conference on Electrical, Computer, Communications and Mechatronics Engineering (ICECCME), Online, 20–21 July 2023; IEEE: Pistacaway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Aaby, P.; Giuffrida, M.V.; Buchanan, W.J.; Tan, Z. An omnidirectional approach to touch-based continuous authentication. Comput. Secur. 2023, 128, 103146. [Google Scholar] [CrossRef]
- do Nascimento, P.G.; Witiak, P.; MacCallum, T.; Winterfeldt, Z.; Dave, R. Your device may know you better than you know yourself--continuous authentication on novel dataset using machine learning. arXiv 2024, arXiv:2403.03832. [Google Scholar] [CrossRef]
- Khalil, A.E.K.; Perez-Diaz, J.A.; Cantoral-Ceballos, J.A.; Antelis, J.M. Unlocking Security for Comprehensive Electroencephalogram-Based User Authentication Systems. Sensors 2024, 24, 7919. [Google Scholar] [CrossRef]
- Upadhyay, D.; Manero, J.; Zaman, M.; Sampalli, S. Gradient boosting feature selection with machine learning classifiers for intrusion detection on power grids. IEEE Trans. Netw. Serv. Manag. 2020, 18, 1104–1116. [Google Scholar] [CrossRef]
- Pryor, L.; Mallet, J.; Dave, R.; Seliya, N.; Vanamala, M.; Boone, E.S. Evaluation of a User Authentication Schema Using Behavioral Biometrics and Machine Learning. arXiv 2022, arXiv:2205.08371. [Google Scholar] [CrossRef]
- Gupta, C.; Johri, I.; Srinivasan, K.; Hu, Y.-C.; Qaisar, S.M.; Huang, K.-Y. A systematic review on machine learning and deep learning models for electronic information security in mobile networks. Sensors 2022, 22, 2017. [Google Scholar] [CrossRef] [PubMed]
- Disha, R.A.; Waheed, S. Performance analysis of machine learning models for intrusion detection system using Gini Impurity-based Weighted Random Forest (GIWRF) feature selection technique. Cybersecurity 2022, 5, 1. [Google Scholar] [CrossRef]
- Abushark, Y.B.; Khan, A.I.; Alsolami, F.J.; Almalawi, A.; Alam, M.; Agrawal, A.; Kumar, R.; Khan, R.A. Usability evaluation through fuzzy AHP-TOPSIS approach: Security requirement perspective. Comput. Mater. Contin. 2021, 68, 1203–1218. [Google Scholar] [CrossRef]
- Alhakami, W. Evaluating modern intrusion detection methods in the face of Gen V multi-vector attacks with fuzzy AHP-TOPSIS. PLoS ONE 2024, 19, e0302559. [Google Scholar] [CrossRef]
- Wu, C.; He, K.; Chen, J.; Zhao, Z.; Du, R. Liveness is not enough: Enhancing fingerprint authentication with behavioral biometrics to defeat puppet attacks. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020; pp. 2219–2236. [Google Scholar]
- Braz, C.; Robert, J.-M. Security and usability: The case of the user authentication methods. In Proceedings of the 18th Conference on l’Interaction Homme-Machine, Montreal, QC, Canada, 18–21 April 2006; pp. 199–203. [Google Scholar]
- Agboola, T.O.; Adegede, J.; Jacob, J.G. Balancing Usability and Security in Secure System Design: A Comprehensive Study on Principles, Implementation, and Impact on Usability. Int. J. Comput. Sci. Res. 2024, 8, 2995–3009. [Google Scholar] [CrossRef]
- Zhang, J.; Beresford, A.R.; Sheret, I. SensorID: Sensor calibration fingerprinting for smartphones. In Proceedings of the IEEE Symposium on Security and Privacy, San Francisco, CA, USA, 19–23 May 2019; pp. 638–655. [Google Scholar] [CrossRef]
- Shen, C.; Chen, Y.; Guan, X. Performance evaluation of implicit smartphones authentication via sensor-behavior analysis. Inf. Sci. 2018, 430–431, 538–553. [Google Scholar] [CrossRef]
- Basar, O.E.; Alptekin, G.; Volaka, H.C.; Isbilen, M.; Incel, O.D. Resource usage analysis of a mobile banking application using sensor-and-touchscreen-based continuous authentication. Procedia Comput. Sci. 2019, 155, 185–192. [Google Scholar] [CrossRef]
- Teh, P.S.; Zhang, N.; Teoh, A.B.J.; Chen, K. A survey on touch dynamics authentication in mobile devices. Comput. Secur. 2016, 59, 210–235. [Google Scholar] [CrossRef]
- Zhang, L.; Jiang, Y.; Ma, Y.; Mao, S.; Huang, W.; Yu, Z.; Zheng, X.; Shu, L.; Fan, X.; Xu, G.; et al. Toward Robust and Effective Behavior Based User Authentication with off-the-shelf Wi-Fi. IEEE Trans. Inf. Forensics Secur. 2024, 19, 8731–8746. [Google Scholar] [CrossRef]
- Radulescu, C.Z.; Radulescu, M. A Hybrid Group Multi-Criteria Approach Based on SAW, TOPSIS, VIKOR, and COPRAS Methods for Complex IoT Selection Problems. Electronics 2024, 13, 789. [Google Scholar] [CrossRef]
- Haque, A.K.M.B.; Bhushan, B.; Dhiman, G. Conceptualizing smart city applications: Requirements, architecture, security issues, and emerging trends. Expert Syst. 2022, 39, e12753. [Google Scholar] [CrossRef]
- Kumar, R.; Khan, A.I.; Abushark, Y.B.; Alam, M.M.; Agrawal, A.; Khan, R.A. An integrated approach of fuzzy logic, AHP and TOPSIS for estimating usable-security of web applications. IEEE Access 2020, 8, 50944–50957. [Google Scholar] [CrossRef]
- Al-Zahrani, F.A. Evaluating the usable-security of healthcare software through unified technique of fuzzy logic, ANP and TOPSIS. IEEE Access 2020, 8, 109905–109916. [Google Scholar] [CrossRef]
- Lu, H.; Karimireddy, S.P.; Ponomareva, N.; Mirrokni, V. Accelerating gradient boosting machines. In Proceedings of the International Conference on Artificial Intelligence and Statistics, PMLR, Online, 26–28 August 2020; pp. 516–526. [Google Scholar]
- Raja, D.J.S.; Sriranjani, R.; Arulmozhi, P.; Hemavathi, N. Unified Random Forest and Hybrid Bat Optimization based Man-in-the-Middle Attack Detection in Advanced Metering Infrastructure. IEEE Trans. Instrum. Meas. 2024, 73, 2523812. [Google Scholar] [CrossRef]
- Wang, R.; Tao, D. DTW-KNN Implementation for Touch-based Authentication System. In Proceedings of the 5th International Conference on Big Data Computing and Communications, BIGCOM 2019, Qingdao, China, 9–11 August 2019; pp. 318–322. [Google Scholar] [CrossRef]
- Li, Y.; Hu, H.; Zhou, G. Using Data Augmentation in Continuous Authentication on Smartphones. IEEE Internet Things J. 2019, 6, 628–640. [Google Scholar] [CrossRef]
- Mikołajczyk, A.; Grochowski, M. Data augmentation for improving deep learning in image classification problem. In Proceedings of the 2018 International Interdisciplinary PhD Workshop (IIPhDW), Swinoujscie, Poland, 9–12 May 2018; IEEE: Pistacaway, NJ, USA; pp. 117–122. [Google Scholar]
- Yang, H.; Chen, L.; Bian, K.; Tian, Y.; Ye, F.; Yan, W.; Zhao, T.; Li, X. TapLock: Exploit finger tap events for enhancing attack resilience of smartphone passwords. IEEE Int. Conf. Commun. 2015, 2015, 7139–7144. [Google Scholar] [CrossRef]
- Mijwil, M.M.; Aljanabi, M. A comparative analysis of machine learning algorithms for classification of diabetes utilizing confusion matrix analysis. Baghdad Sci. J. 2023, 20, 10.21123. [Google Scholar] [CrossRef]
- Wang, C.; Xiao, Y.; Gao, X.; Li, L.; Wang, J. A framework for behavioral biometric authentication using deep metric learning on mobile devices. IEEE Trans. Mobile Comput. 2021, 22, 19–36. [Google Scholar] [CrossRef]
- Fereidooni, H.; König, J.; Rieger, P.; Chilese, M.; Gökbakan, B.; Finke, M.; Dmitrienko, A.; Sadeghi, A.R. Authentisense: A scalable behavioral biometrics authentication scheme using few-shot learning for mobile platforms. arXiv 2023, arXiv:2302.02740. [Google Scholar]
- Mallet, M.; Pryor, L.; Dave, R.; Seliya, N.; Vanamala, M.; Sowells-Boone, E. Hold on and swipe: A touch-movement based continuous authentication schema based on machine learning. In Proceedings of the 2022 Asia Conference on Algorithms, Computing and Machine Learning (CACML), Hangzhou, China, 25–27 March 2022; pp. 442–447. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).