From Security Frameworks to Sustainable Municipal Cybersecurity Capabilities
Abstract
1. Introduction
2. Background and Literature
2.1. Municipal Cybersecurity
2.2. Cybersecurity Frameworks
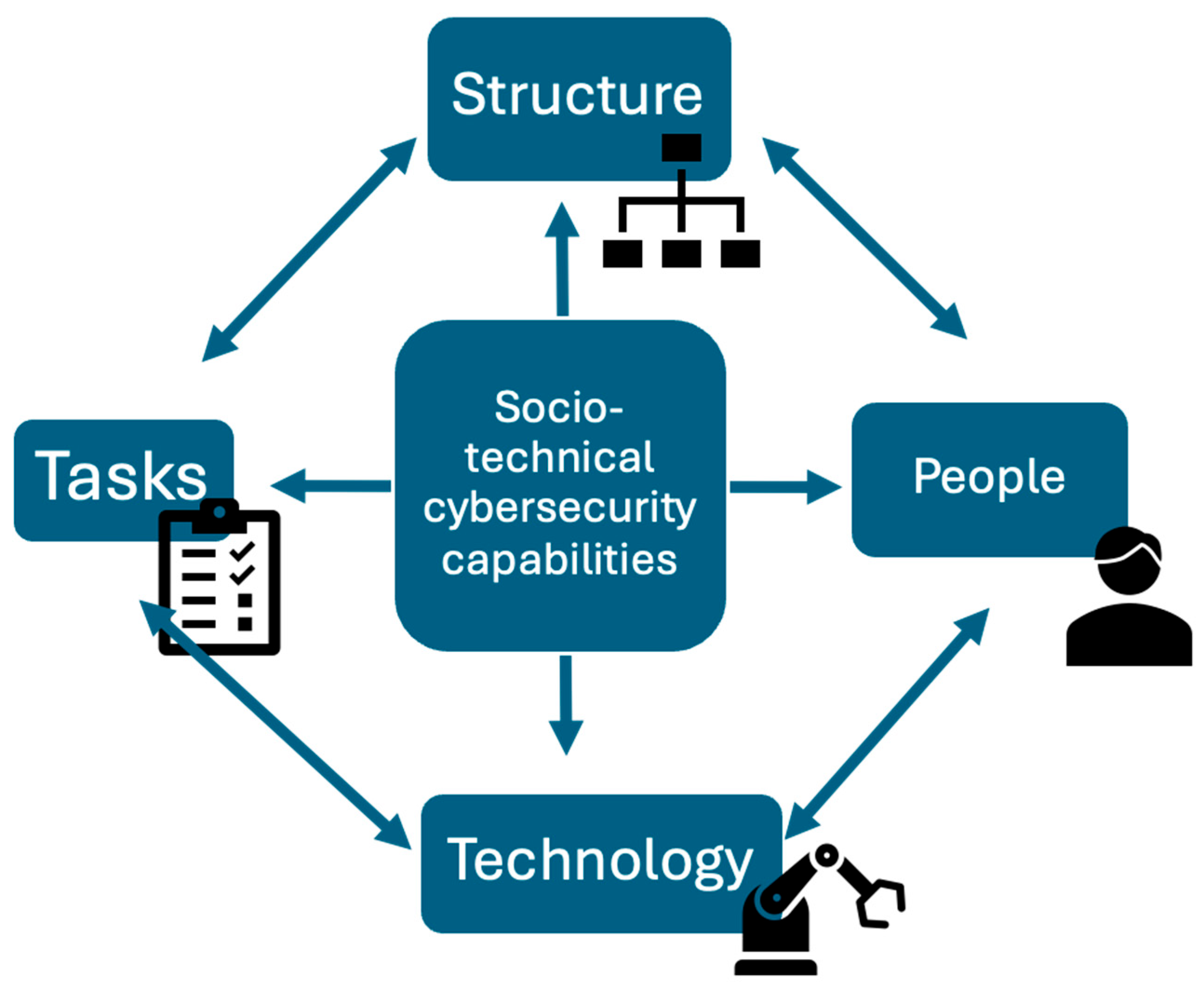
2.3. Socio-Technical Approach to Cybersecurity
- Structural issues include a lack of prioritization and sufficient resources to perform the necessary cybersecurity activities and a lack of internal coordination [31], so critical functional areas of local government, such as healthcare or water supply, are not adequately supported by vulnerability scanning or security monitoring activities;
- Issues related to people and the human aspects, such as insufficient training, either on cybersecurity issues such as threats and vulnerabilities related to all aspects of local government technology or on the tools and technologies necessary to perform cybersecurity work [32], such as vulnerability scanning, network and endpoint security, and security monitoring tools leading to lack of use or errors in detecting security issues;
- Technological issues, such as limitations in functionality and coverage, for example, for specialized security issues in local government areas such as medical technology in municipal healthcare or SCADA systems (supervisory control and data acquisition), in water supply, or the lack of integration between security technologies leading to tool overload for security analysts, or cybersecurity tooling with complicated and unsuitable user interfaces leading to lack of adoption of security technology [33];
- Doing the wrong tasks or performing them with insufficient quality can lead to vulnerabilities not being correctly removed, security alerts being wrongly prioritized, and security incidents not being investigated with sufficient rigor to identify the root causes of security incidents.
2.4. Introducing Socio-Technical Cybersecurity Capabilities
3. Methodology
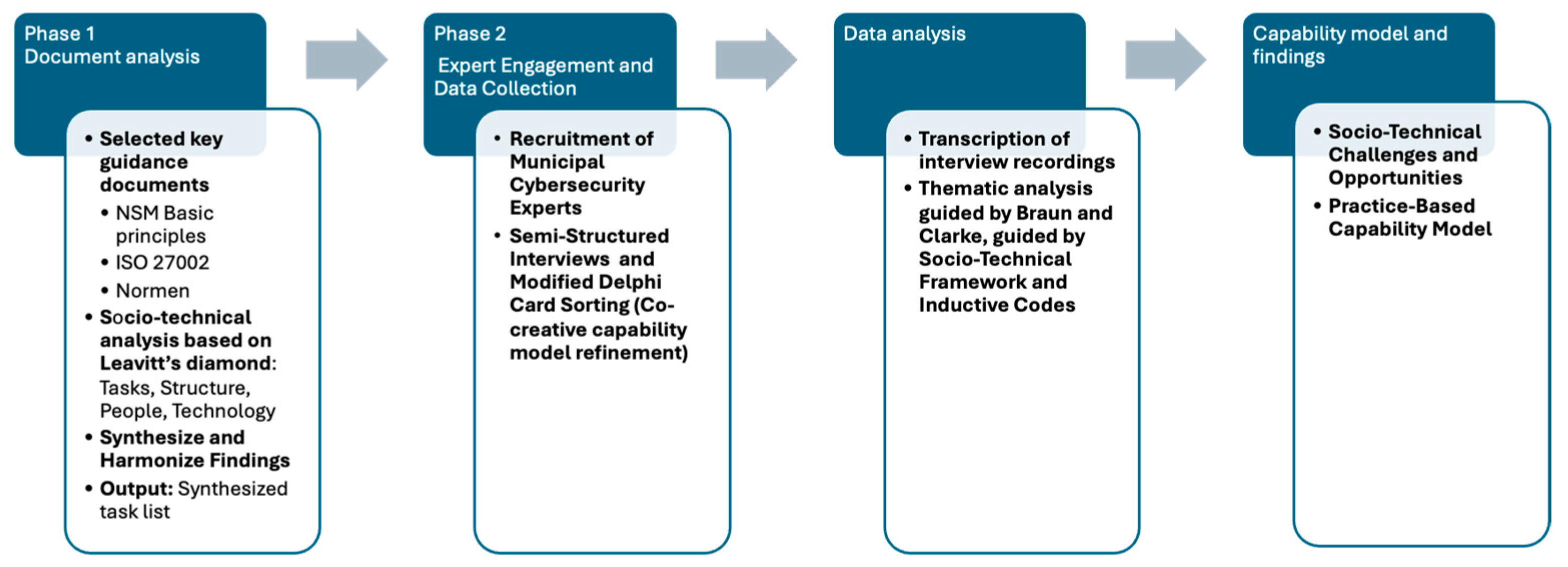
3.1. Methodological Approach—Document Analysis, Expert Interviews, and Modified Delphi-Inspired Card Sorting
3.1.1. Phase 1: Document Analysis—Establishing a Foundation of Recommended Practices
3.1.2. Phase 2: Expert Interviews Incorporating Modified Delphi Card Sorting—Co-Creating a Practice-Based Capability Model
3.2. Interactive Expert Interviews and Card-Sorting Activity: A Co-Creative Dialogue
- Warm-up: Participants performed an open sort with ~35% of the task cards (derived from the document analysis), providing their initial, unbiased (by a previous sort) categorizations. This leveraged the participant’s inherent understanding and served as an accessible entry point for familiarization with the tool;
- Iterative Model Refinement: Participants were presented with the card-sorting model sorted by previous participants, which they refined based on their experience, guided by the interview themes (structure, people, technology, tasks). Throughout, a “think-aloud” protocol [54] was used, encouraging participants to verbalize their reasoning for why cards were sorted together. The following themes were discussed:
- Structure: How are capabilities organized in practice? How do municipal structures facilitate or hinder them?
- People: What roles, skills, and knowledge are essential? What are the real-world human resource challenges?
- Technology: What technologies are used or needed, within municipal constraints? What are the practical challenges and opportunities related to technology adoption?
- Tasks: Experts elaborated on their experiences, task interdependencies, and the practical scope of each capability.
3.3. Data Analysis
4. Results
4.1. Results from Card-Sorting Activity—Forming Capabilities
4.2. Quantitative Analysis
4.3. Structure
4.3.1. Formalization of Security Roles and Responsibilities
4.3.2. Organizational Structure of Cybersecurity
4.3.3. Sourcing of Cybersecurity Capabilities—Internal vs. External
4.3.4. Outsourcing and Its Limitations
4.3.5. Communication and Integration Across Functional Areas and Central IT
4.4. People
4.4.1. Cybersecurity Roles in Municipalities
4.4.2. Adaptation and Practical Realities: Role Combination and Dispersion
4.4.3. Types of Cybersecurity Knowledge
4.4.4. Strategies for Addressing the Skills Challenge
4.5. Technology
4.5.1. Evolving Municipal ICT Landscape and Cybersecurity Technology Needs
4.5.2. Challenges in Implementing Key Security Technologies
4.5.3. Continual Vulnerability Management
4.5.4. Distributed Risk Analysis Tools
4.5.5. Perspectives on Artificial Intelligence (AI) in Municipal Cybersecurity
4.6. Cooperation Strategies
5. Discussion
5.1. Misalignment and the Weakening of Municipal Cybersecurity Capabilities
5.2. The Case of System Ownership—From Role to Capability
5.3. Capability Maturity and the Path to Sustainable Municipal Cybersecurity
6. Conclusions and Further Work
6.1. Managerial and Practical Implications
6.2. Limitations of the Study
6.3. Recommendations for Future Research
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- DigDir. Arbeidet Med Informasjonssikkerhet i Fylkeskommuner og Kommuner|Digdir. Available online: https://www.digdir.no/informasjonssikkerhet/arbeidet-med-informasjonssikkerhet-i-fylkeskommuner-og-kommuner/2102 (accessed on 19 September 2024).
- Sævold, H. “Dataangrepet Mot Østre Toten: Ekstern Rapport Fant Flere Svakheter,” Digi.no. Available online: https://www.digi.no/artikler/kommune-etter-dataangrep-i-januar-noen-tjenester-er-fortsatt-nede/512959 (accessed on 17 February 2025).
- Center for Internet Security. 2022 Nationwide Cybersecurity Review Summary Report. Available online: https://www.cisecurity.org/insights/white-papers/2022-nationwide-cybersecurity-review (accessed on 20 September 2024).
- Datatilsynet. Funn Fra Tilsyn i Kommuner og Fylkeskommuner. Available online: https://www.datatilsynet.no/aktuelt/aktuelle-nyheter-2023/funn-fra-tilsyn-i-kommuner-og-fylkeskommuner/ (accessed on 7 January 2025).
- Joint Task Force Transformation Initiative. Guide for Conducting Risk Assessments; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012; Report nr. NIST SP 800-30r1. [Google Scholar]
- Hasani, T.; O’Reilly, N.; Dehghantanha, A.; Rezania, D.; Levallet, N. Evaluating the Adoption of Cybersecurity and Its Influence on Organizational Performance. SN Bus. Econ. 2023, 3, 97. [Google Scholar] [CrossRef] [PubMed]
- Jalali, M.S.; Kaiser, J.P. Cybersecurity in Hospitals: A Systematic, Organizational Perspective. J. Med. Internet Res. 2018, 20, e10059. [Google Scholar] [CrossRef]
- The Open Group. TOGAF Business Capabilities Guide V2. Available online: https://pubs.opengroup.org/togaf-standard/business-architecture/business-capabilities.html (accessed on 18 March 2024).
- Leavitt, H.J. Applied Organizational Change in Industry: Structural, Technological and Humanistic Approaches. In Handbook of Organizations (RLE: Organizations); Routledge: London, UK, 1965; ISBN 978-0-203-62913-0. [Google Scholar]
- Vestad, A.; Yang, B. Municipal Cybersecurity—A Neglected Research Area? A Survey of Current Research. In Proceedings of the International Conference on Cybersecurity, Situational Awareness and Social Media, Copenhagen, Denmark, 3–4 July 2023; Onwubiko, C., Rosati, P., Rege, A., Erola, A., Bellekens, X., Hindy, H., Jaatun, M.G., Eds.; Springer Nature: Singapore, 2023; pp. 151–165. [Google Scholar]
- Paul, C.L. A Modified Delphi Approach to a New Card Sorting Methodology. J. Usability Stud. 2008, 4, 7. [Google Scholar]
- Vestad, A. CardSort3 2025. Available online: https://github.com/arnves/CardSort3 (accessed on 17 February 2025).
- Hossain, S.T.; Yigitcanlar, T.; Nguyen, K.; Xu, Y. Local Government Cybersecurity Landscape: A Systematic Review and Conceptual Framework. Appl. Sci. 2024, 14, 5501. [Google Scholar] [CrossRef]
- Hatcher, W.; Meares, W.L.; Heslen, J. The Cybersecurity of Municipalities in the United States: An Exploratory Survey of Policies and Practices. J. Cyber Policy 2020, 5, 302–325. [Google Scholar] [CrossRef]
- Hossain, S.T.; Yigitcanlar, T.; Nguyen, K.; Xu, Y. Understanding Local Government Cybersecurity Policy: A Concept Map and Framework. Information 2024, 15, 342. [Google Scholar] [CrossRef]
- Curti, F.; Ivanov, I.; Macchiavelli, M.; Zimmermann, T. City Hall Has Been Hacked! The Financial Costs of Lax Cybersecurity. May 2023. Available online: https://ssrn.com/abstract=4465071 (accessed on 17 February 2025).
- Waltz, C.; Gasco-Hernandez, M. Understanding Cybersecurity Outsourcing Processes in Local Governments. In Proceedings of the Hawaii International Conference on System Sciences, Big Island, HA, USA, 7–10 January 2025; pp. 1874–1883. [Google Scholar] [CrossRef]
- Statistics Norway 12031: ICT Roles, by Degree of Outsourcing (Central Government, County Municipalities, Municipalities) 2012–2024 Statistikkbanken. Available online: https://www.ssb.no/en/statbank/table/12031 (accessed on 11 February 2025).
- Statistics Norway 12618: Implemented ICT Security Efforts (County Municipalities, Municipalities) 2019–2021. Statistikkbanken. Available online: https://www.ssb.no/en/statbank/table/12618 (accessed on 23 September 2024).
- Culot, G.; Nassimbeni, G.; Podrecca, M.; Sartor, M. The ISO/IEC 27001 Information Security Management Standard: Literature Review and Theory-Based Research Agenda. TQM J. 2021, 33, 76–105. [Google Scholar] [CrossRef]
- DigDir. Regelverkskrav og Anbefalinger-Internkontroll Informasjonssikkerhet|Digdir. Available online: https://www.digdir.no/informasjonssikkerhet/regelverkskrav-og-anbefalinger-internkontroll-informasjonssikkerhet/3229 (accessed on 23 September 2024).
- NSM ICT Security Principles-Nasjonal Sikkerhetsmyndighet. Available online: https://nsm.no/advice-and-guidance/publications/nsm-ict-security-principles (accessed on 23 September 2024).
- National Institute of Standards and Technology. The NIST Cybersecurity Framework (CSF) 2.0; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2024; p. NIST CSWP 29. [Google Scholar]
- Direktoratet for e-Helse Normen. Available online: https://www.ehelse.no/normen (accessed on 23 September 2024).
- Arntzen Toftegaard, Ø.A. An Effect Analysis of ISO/IEC 27001 Certification on Technical Security of Norwegian Grid Operators. In Proceedings of the 2022 IEEE International Conference on Big Data (Big Data), Osaka, Japan, 17–20 December 2022; pp. 2620–2629. [Google Scholar]
- Kamil, Y.; Lund, S.; Islam, M.S. Information Security Objectives and the Output Legitimacy of ISO/IEC 27001: Stakeholders’ Perspective on Expectations in Private Organizations in Sweden. Inf. Syst. E-Bus. Manag. 2023, 21, 699–722. [Google Scholar] [CrossRef]
- Zoto, E.; Kianpour, M.; Kowalski, S.; Lopez-Rojas, E. A Socio-Technical Systems Approach to Design and Support Systems Thinking in Cybersecurity and Risk Management Education. Complex. Syst. Inform. Model. Q. 2019, 18, 65–75. [Google Scholar] [CrossRef]
- Bostrom, R.P.; Heinen, J.S. MIS Problems and Failures: A Socio-Technical Perspective. Part I: The Causes. MIS Q. 1977, 1, 17–32. [Google Scholar] [CrossRef]
- Malatji, M.; Von Solms, S.; Marnewick, A. Socio-Technical Systems Cybersecurity Framework. Inf. Comput. Secur. 2019, 27, 233–272. [Google Scholar] [CrossRef]
- Susan, M. Tisdale Cybersecurity: Challenges From a Systems Complexity Knowledge Management and Business Intelligence Perspective. Issues Inf. Syst. 2015, 16, 191–198. [Google Scholar] [CrossRef]
- KS. Styrking av Digital Robusthet i Kommunal Sektor. Available online: https://www.ks.no/fagomrader/forskning-og-utvikling-fou/forskning-og-utvikling/digital--robusthet-i-kommunal-sektor/ (accessed on 17 February 2025).
- European Cybersecurity Skills Framework Role Profiles|ENISA. Available online: https://www.enisa.europa.eu/publications/european-cybersecurity-skills-framework-role-profiles (accessed on 5 December 2024).
- Vestad, A.; Yang, B. Adoption of Cybersecurity Innovations—A Systematic Literature Review. In Proceedings of the International Conference on Cybersecurity, Situational Awareness and Social Media, Scotland, UK, 27–28 June 2024; Onwubiko, C., Rosati, P., Rege, A., Erola, A., Bellekens, X., Hindy, H., Jaatun, M.G., Eds.; Springer Nature: Singapore, 2024; pp. 285–304. [Google Scholar]
- Devaraj, S.; Kohli, R. Performance Impacts of Information Technology: Is Actual Usage the Missing Link? Manag. Sci. 2003, 49, 273–289. [Google Scholar] [CrossRef]
- Venkatesh, V.; Bala, H. Technology Acceptance Model 3 and a Research Agenda on Interventions. Decis. Sci. 2008, 39, 273–315. [Google Scholar] [CrossRef]
- Goodhue, D.L.; Thompson, R.L. Task-Technology Fit and Individual Performance. MIS Q. 1995, 19, 213–236. [Google Scholar] [CrossRef]
- Barley, S.R. Technology as an Occasion for Structuring: Evidence from Observations of CT Scanners and the Social Order of Radiology Departments. Adm. Sci. Q. 1986, 31, 78–108. [Google Scholar] [CrossRef] [PubMed]
- The Open Group. The TOGAF® Standard. Available online: https://pubs.opengroup.org/togaf-standard/introduction/index.html (accessed on 23 September 2024).
- Kotusev, S. Enterprise Architecture and Enterprise Architecture Artifacts: Questioning the Old Concept in Light of New Findings. J. Inf. Technol. 2019, 34, 102–128. [Google Scholar] [CrossRef]
- Van Riel, J.; Poels, G. A Method for Developing Generic Capability Maps. Bus. Inf. Syst. Eng. 2023, 65, 403–424. [Google Scholar] [CrossRef]
- Tell, A.W. What Capability Is Not. In Proceedings of the Perspectives in Business Informatics Research, Lund, Sweden, 22–24 September 2014; Johansson, B., Andersson, B., Holmberg, N., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 128–142. [Google Scholar]
- Nussbaum, B.; Park, S. A Tough Decision Made Easy? Local Government Decision-Making About Contracting for Cybersecurity. In Proceedings of the 19th Annual International Conference on Digital Government Research: Governance in the Data Age, Delft, The Netherlands, 30 May–1 June 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 1–9. [Google Scholar]
- DigDir. Felles Sikkerhet i Forvaltningen|Digdir. Available online: https://www.digdir.no/informasjonssikkerhet/felles-sikkerhet-i-forvaltningen/4106 (accessed on 17 February 2025).
- Trinczek, R. How to Interview Managers? Methodical and Methodological Aspects of Expert Interviews as a Qualitative Method in Empirical Social Research. In Interviewing Experts; Bogner, A., Littig, B., Menz, W., Eds.; Palgrave Macmillan: London, UK, 2009; pp. 203–216. ISBN 978-0-230-24427-6. [Google Scholar]
- Dwyer, S.C.; Buckle, J.L. The Space Between: On Being an Insider-Outsider in Qualitative Research. Int. J. Qual. Methods 2009, 8, 54–63. [Google Scholar] [CrossRef]
- Bogner, A.; Littig, B.; Menz, W. (Eds.) Interviewing Experts; Palgrave Macmillan: London, UK, 2009; ISBN 978-1-349-30575-9. [Google Scholar]
- ISO/IEC 27002:2022. Available online: https://www.iso.org/standard/75652.html (accessed on 11 March 2025).
- Meuser, M.; Nagel, U. The Expert Interview and Changes in Knowledge Production. In Interviewing Experts; Bogner, A., Littig, B., Menz, W., Eds.; Palgrave Macmillan: London, UK, 2009; pp. 17–42. ISBN 978-0-230-24427-6. [Google Scholar]
- Lobinger, K.; Brantner, C. Picture-Sorting Techniques. Card Sorting and Q-Sort as Alternative and Complementary Approaches in Visual Social Research. In The Sage Handbook of Visual Research Methods; Sage: Newcastle upon Tyne, UK, 2020; pp. 309–321. ISBN 978-1-4739-7800-3. [Google Scholar]
- Navas de Maya, B.; Khalid, H.; Kurt, R.E. Application of Card-Sorting Approach to Classify Human Factors of Past Maritime Accidents. Marit. Policy Manag. 2021, 48, 75–90. [Google Scholar] [CrossRef]
- Jeong, R.; Chiasson, S. “Lime”, “Open Lock”, and “Blocked”: Children’s Perception of Colors, Symbols, and Words in Cybersecurity Warnings. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 1–13. [Google Scholar]
- Garcia-Granados, F.B.; Bahsi, H. Cybersecurity Knowledge Requirements for Strategic Level Decision Makers. In Proceedings of the International Conference on Cyber Warfare and Security, Online, 20–21 October 2020; Academic Conferences International Limited: Oxfordshire, UK, 2020. [Google Scholar]
- Cole, M.F.; Britton, C.O.; Roberts, D.; Rubin, P.; Shin, H.D.; Watson, Y.R.; Harrison, C. A Card-Sorting Tool to Measure Expert versus Novice Thinking in Scientific Research. Life Sci. Educ. 2023, 22, ar38. [Google Scholar] [CrossRef]
- Conrad, L.Y.; Tucker, V.M. Making It Tangible: Hybrid Card Sorting within Qualitative Interviews. J. Doc. 2019, 75, 397–416. [Google Scholar] [CrossRef]
- Braun, V.; Clarke, V.; Terry, G. Thematic Analysis. In Handbook of Research Methods in Health Social Sciences; Springer: Berlin/Heidelberg, Germany, 2014; pp. 95–113. ISBN 978-1-137-29104-2. [Google Scholar]
- Paul, C. Analyzing Card-Sorting Data Using Graph Visualization. J. Usability Stud. 2014, 9, 87–104. [Google Scholar]
- Rose, S.; Borchert, O.; Mitchell, S.; Connelly, S. Zero Trust Architecture; National Institute of Standards and Technology: Gaithersburg, ML, USA, 2020. [Google Scholar]
- DigDir. Rolle: Systemeier|Digdir. Available online: https://www.digdir.no/informasjonssikkerhet/rolle-systemeier/2111 (accessed on 16 February 2025).
- Skjelvik, A.; Vestad, A. Digital Safety Alarms—Exploring the Understandings of the Cybersecurity Practice in Norwegian Municipalities. In Proceedings of the 2023 European Interdisciplinary Cybersecurity Conference, Stavanger, Norway, 14–15 June 2023; Association for Computing Machinery: New York, NY, USA, 2023; pp. 129–133. [Google Scholar]
- Prislan, K.; Mihelič, A.; Bernik, I. A Real-World Information Security Performance Assessment Using a Multidimensional Socio-Technical Approach. PLoS ONE 2020, 15, e0238739. [Google Scholar] [CrossRef] [PubMed]
- Brezavšček, A.; Baggia, A. Recent Trends in Information and Cyber Security Maturity Assessment: A Systematic Literature Review. Systems 2025, 13, 52. [Google Scholar] [CrossRef]
- Heidt, M.; Gerlach, J.P.; Buxmann, P. Investigating the Security Divide between SME and Large Companies: How SME Characteristics Influence Organizational IT Security Investments. Inf. Syst. Front. 2019, 21, 1285–1305. [Google Scholar] [CrossRef]
- Chidukwani, A.; Zander, S.; Koutsakis, P. A Survey on the Cyber Security of Small-to-Medium Businesses: Challenges, Research Focus and Recommendations. IEEE Access 2022, 10, 85701–85719. [Google Scholar] [CrossRef]
- Sanchez-Zurdo, J.; San-Martín, J. A Country Risk Assessment from the Perspective of Cybersecurity in Local Entities. Appl. Sci. 2024, 14, 12036. [Google Scholar] [CrossRef]
- Henderson, K. Flexible Sketches and Inflexible Data Bases: Visual Communication, Conscription Devices, and Boundary Objects in Design Engineering. Sci. Technol. Hum. Values 1991, 16, 448–473. [Google Scholar] [CrossRef]
- Teece, D.J. Explicating Dynamic Capabilities: The Nature and Microfoundations of (Sustainable) Enterprise Performance. Strateg. Manag. J. 2007, 28, 1319–1350. [Google Scholar] [CrossRef]
- Hettinger, L.J.; Kirlik, A.; Goh, Y.M.; Buckle, P. Modelling and Simulation of Complex Sociotechnical Systems: Envisioning and Analysing Work Environments. Ergonomics 2015, 58, 600–614. [Google Scholar] [CrossRef] [PubMed]
- Vestad, A.; Yang, B. A survey of agent-based modeling for cybersecurity. In Human Factors in Cybersecurity, Proceedings of the AHFE (2024) International Conference, Nice, France, 24–27 July 2024; AHFE Open Access; Moallem, A., Ed.; AHFE International: New York, NY, USA, 2024; Volume 127. [Google Scholar] [CrossRef]




| Cybersecurity Capability | ECSF Roles |
|---|---|
| Secure operations | Cybersecurity Implementer |
| Governance, risk, and compliance | Chief Information Security Officer (CISO), Cybersecurity Architect, Cyber Legal, Policy, and Compliance Officer, Cybersecurity Auditor, Cybersecurity Educator, Cybersecurity Risk Manager, |
| Monitoring and incident management | Cyber Incident Responder, Cyber Threat Intelligence Specialist, Digital Forensics Investigator |
| System ownership | No related ECSF role identified |
| Secure development | No related role ECSF role identified |
| Security testing | Penetration Tester |
| Not directly relevant | Cybersecurity Researcher |
| Formal | Informal |
|---|---|
| IKSs, interkommunale selskaper (inter-municipal enterprises), or formalized inter-municipal cooperations May provide whole or parts of several cybersecurity capabilities, and general ICT operations services and infrastructure. | Membership organizations, particularly Foreningen Kommunal Informasjonssikkerhet -KiNS, Forum for personvernombud Mainly individual-level membership organizations for security and privacy. |
| Utilization of shared services from KS or government (DigDir) Provides specific shared services, such as ID-Porten for authentication of citizens, electronic signature, citizen communication, etc. Municipalities are to a large extent free to choose to implement these or other services. | CTF competitions Participation in CTF competitions, mainly individual-level participation. |
| Helse- og KommuneCERT | |
| Managed security service providers Providing outsourced SOC services. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vestad, A.; Yang, B. From Security Frameworks to Sustainable Municipal Cybersecurity Capabilities. J. Cybersecur. Priv. 2025, 5, 19. https://doi.org/10.3390/jcp5020019
Vestad A, Yang B. From Security Frameworks to Sustainable Municipal Cybersecurity Capabilities. Journal of Cybersecurity and Privacy. 2025; 5(2):19. https://doi.org/10.3390/jcp5020019
Chicago/Turabian StyleVestad, Arnstein, and Bian Yang. 2025. "From Security Frameworks to Sustainable Municipal Cybersecurity Capabilities" Journal of Cybersecurity and Privacy 5, no. 2: 19. https://doi.org/10.3390/jcp5020019
APA StyleVestad, A., & Yang, B. (2025). From Security Frameworks to Sustainable Municipal Cybersecurity Capabilities. Journal of Cybersecurity and Privacy, 5(2), 19. https://doi.org/10.3390/jcp5020019






