A Blockchain-Based Decentralized Public Key Infrastructure Using the Web of Trust
Abstract
1. Introduction
- The existing system’s distribution of revocation information is characterized by time-intensive processes and sluggish verification, which can result in prolonged revocation times during breaches [7].
- The lack of transparency in the current system enables CAs to issue certificates for individual domain owners without the parent company’s knowledge [8], potentially leading to the creation of counterfeit sites.
- Introduction of a decentralized blockchain-based PKI system that ensures transparent issuance of X.509 certificates, thereby diminishing unauthorized activities.
- Integration of the WoT paradigm within the blockchain-based PKI to establish a trusted key-ring network, eliminating the need for central CAs.
- Empowerment of any ring member to serve as an auditor and initiate the revocation process upon detection of any malicious activities.
- Improvement of the algorithm and process for generating X.509 certificates to establish a robust digital certification system.
- Enhancement of the X.509v3 certificate extension field to include multiple signatures and blockchain-related information, facilitating seamless integration with existing browser certificate validation mechanisms with minor modifications.
- Facilitation of efficient computation of trust levels by incorporating the depth of the ring member nodes, which prioritizes proximity to the ring owner and maintains an optimal key-ring size.
2. Related Works
Summary of Related Works
3. Shortcomings of a Centralized PKI System
- I
- Single Point of Failure: The centralized nature of CAs presents a significant vulnerability, leading to widespread distrust, regardless of their theoretical trustworthiness. Multiple operational errors and breaches in well-known CAs have raised significant concerns [8,34], such as the 2017 Symantec incident, where over a hundred certificates were improperly issued, resulting in distrust from major platforms [5].The large number of CAs and their dependent hierarchy also pose a significant challenge, as a single compromised or rogue CA among the hundreds or thousands could lead to widespread failure, often exploited through MitM attacks [20,34]. In addition, compromised CAs can be exploited for malicious purposes, potentially undermining the entire infrastructure and compromising sensitive data; they are also able to issue a legitimate certificate for any domain [6,21,34].
- II
- Challenges in Certificate Revocation Process: Revoking specific certificates issued by a CA is essential for various reasons, such as compromised private keys, compromised CAs, change of affiliation, or certificate supersession [7,35]. The MITRE Corporation highlights the expense and time-consuming nature of a centralized PKI’s revocation information distribution, particularly in revoking certificates before expiration [1]. One common method for revoking certificates involves Certificate Revocation Lists (CRLs), managed by the CA or other trusted parties, where the issuing CA publishes revoked certificates with their serial numbers [2]. However, if the CRL becomes unreachable, clients may experience either an open or closed failure. Additionally, CAs, even in the event of a breach, may not be entirely trustworthy in containing or reporting incidents due to financial incentives and reputational concerns, often choosing not to disclose data breaches or operational errors.
- III
- Lack of Transparency: In the current system, a CA can issue a certificate for any individual domain owner. However, the parent company does not have any way of knowing whether any individual domain owner is receiving a certificate with the parent company’s domain name, potentially enabling the issuance of fake certificates for deceptive purposes [8].Currently, the only viable option is to maintain a log of all issued certificates using a log-based schema, accessible for client verification. Another potential method involves a database containing all possible CAs capable of issuing certificates for specific domains, although this approach is currently not widely adopted.
4. Background Technologies
4.1. Blockchain and Ethereum
4.2. Web of Trust
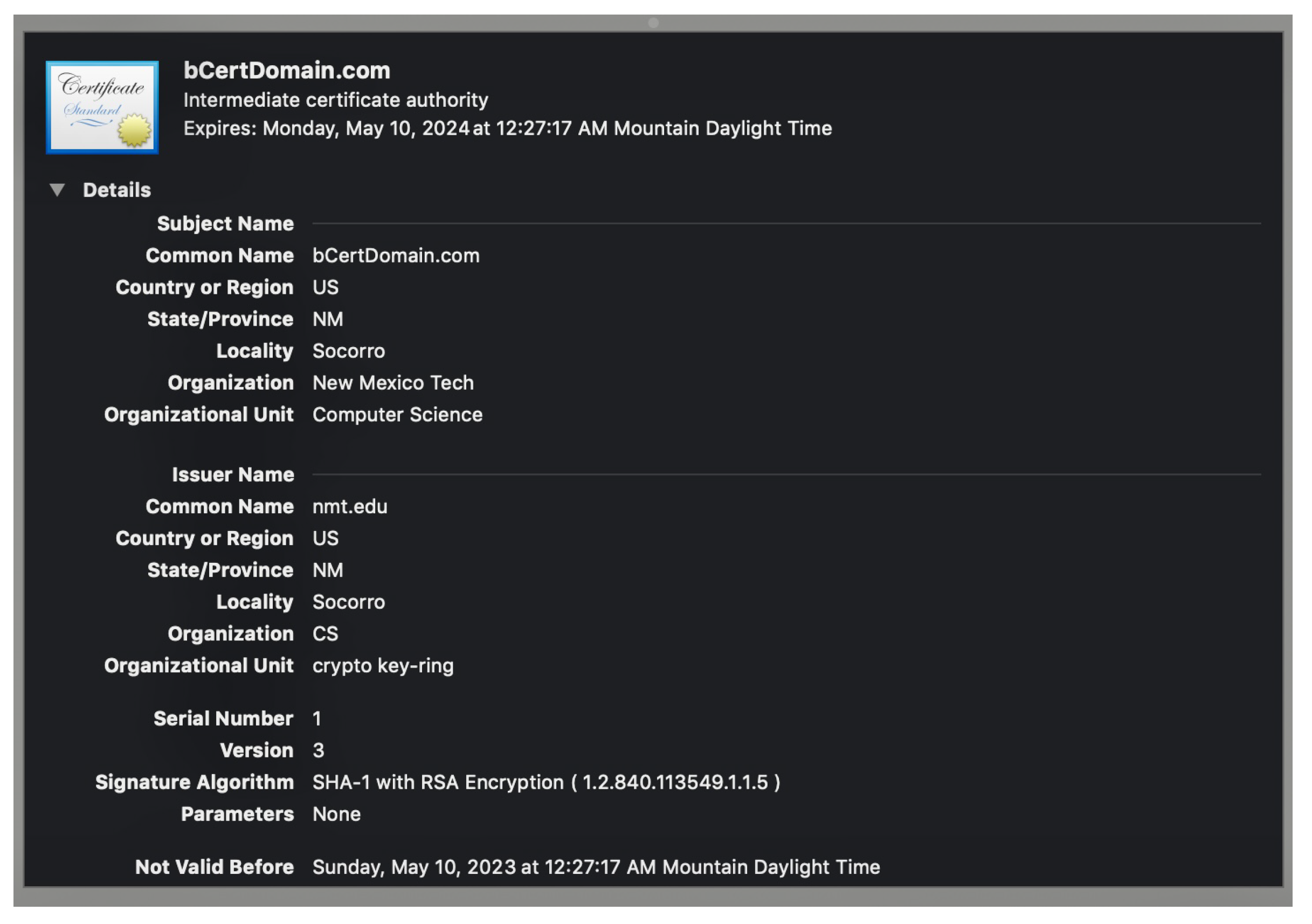
4.3. X.509 Certificate
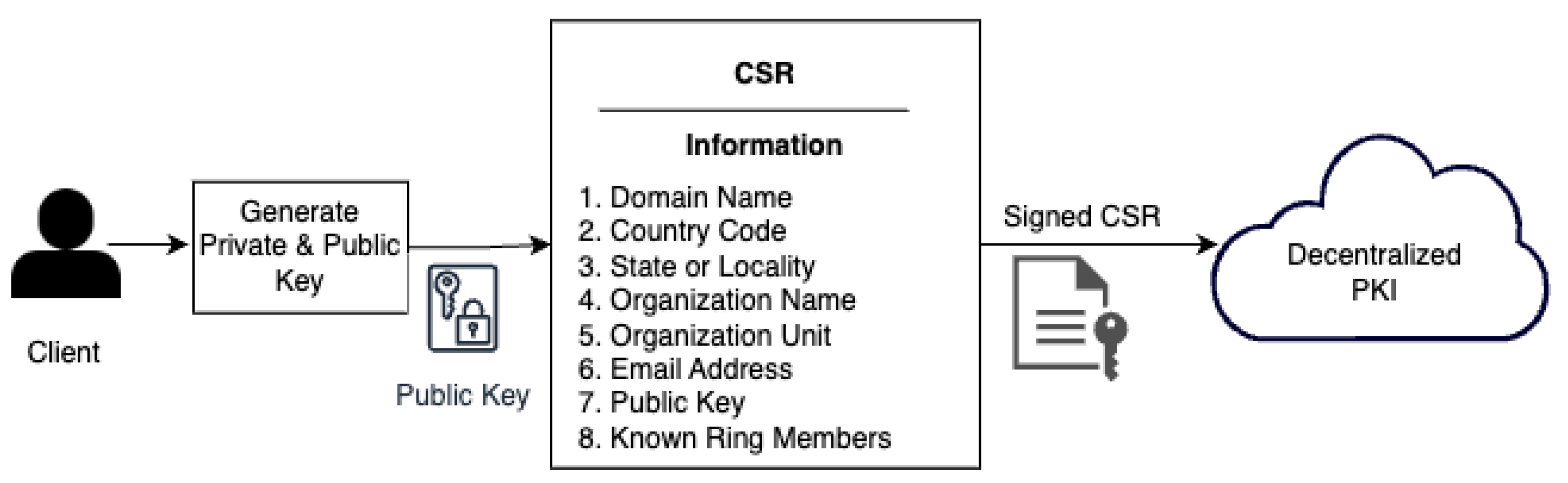
- extnID: Denoting Extension ID, which is an Object Identifier (OID) defining the extension’s definition and format.
- critical: A boolean indicating the importance of the extension.
- extnValue: The actual value of the extension.

5. System Overview
5.1. System Requirements
- User Validation: Ensures that only legitimate domain owners request SSL certificates by authenticating their identity to create an X.509 certificate. It is crucial for introducers to verify and confirm that only authorized domain owners are granted digital certificates.
- Decentralization: Involves multiple ring members, also referred to as introducers, to avoid a single point of failure. Allows authorized introducers to authenticate certificate information and add individual signatures, resolving dependency on the existing CA hierarchy.
- Transparency: Publicly accessible certificate creation and verification data are stored on the blockchain network. This facilitates public visibility of certificate issuances and revocations, enabling the detection of certificates that have been tampered with or compromised introducers.
- Interoperability: Requesters are provided with X.509v3 format certificates to ensure privacy, legitimacy, and secure connections during TLS handshakes. Ensuring compatibility with the existing browser verification mechanism is essential, necessitating minor adjustments.
- Revocation Efficiency: The certificate revocation process should be expedited. The system will automatically recognize and respond to revocation requests from authentic users or introducers. Additionally, it is pivotal to engage multiple introducers to thoroughly authenticate the revocation request.
5.2. System Architecture
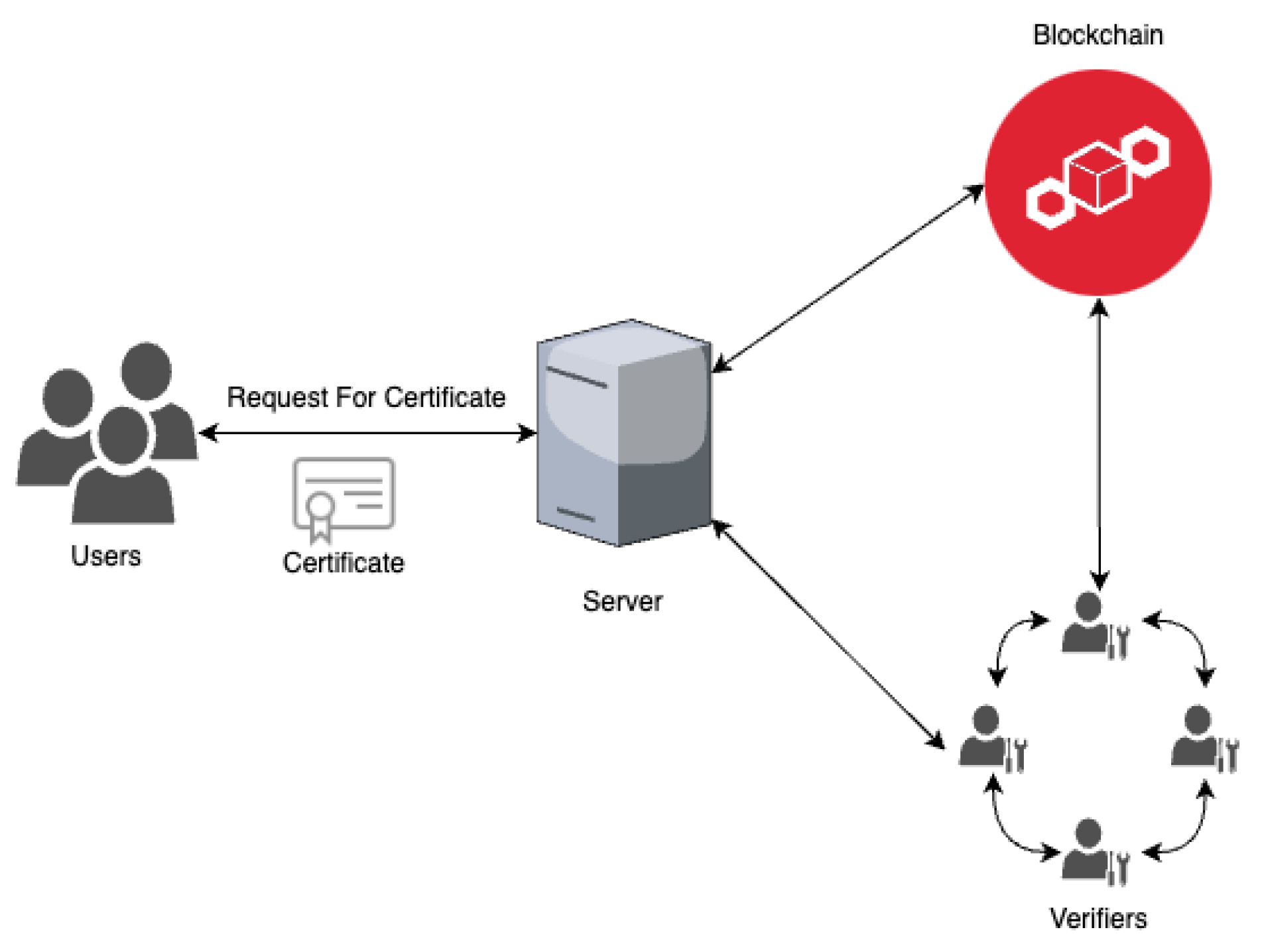
5.2.1. Certificate Issuance
5.2.2. Validation
- (A)
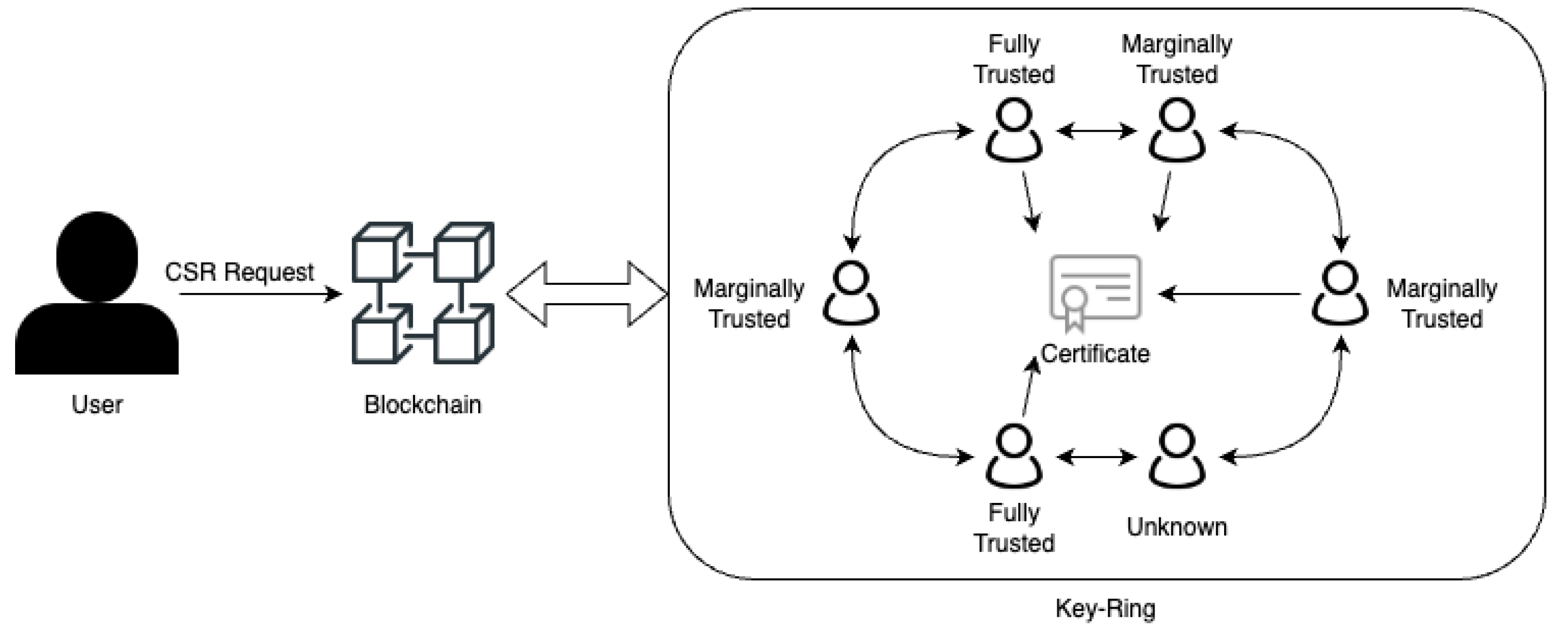
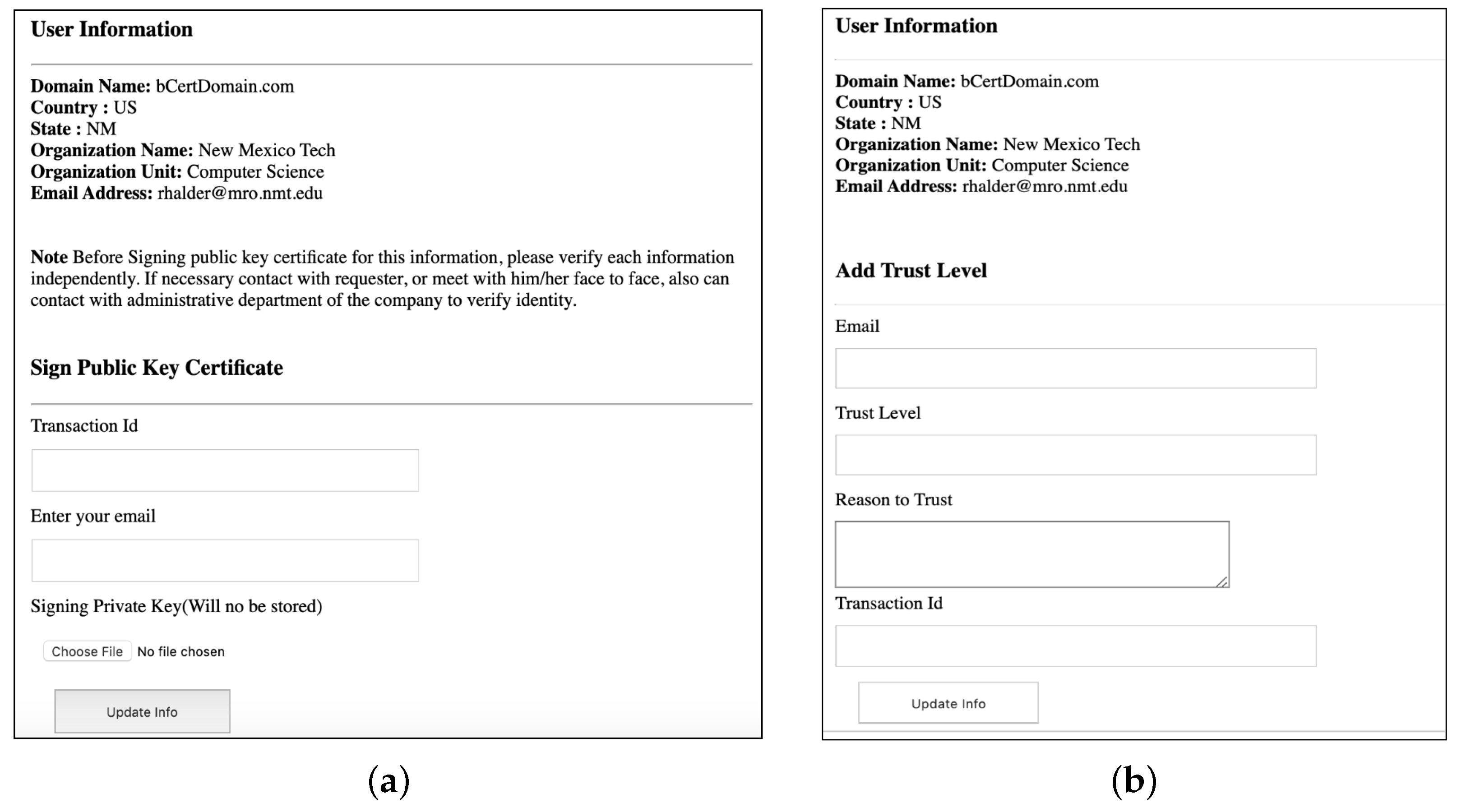
- Public Key Certificate Authenticity:In a decentralized PKI structure, there is no central authority for certification, so validated introducers act as CAs and sign certificates to ensure trustworthiness. Figure 3 demonstrates the process by which certificates can be authenticated by trusted introducers, bypassing the need for CAs. These members manually verify all information, requesting additional details or physical meetings when necessary, and document their verification methods within the signed certificates, thereby enhancing trust in user information for both the introducers and other ring members.During the process of signing a certificate, introducers are required to assess and define the level of trust for the examined certificate after verifying the CSR information. The PGP trust model relies on varying levels of trust determined by the introducers during certificate verification. We employ a similar approach to calculate the trust level of the certificate. The trust level assigned to a certificate falls into one of the following categories:
- Not trusted;
- Marginally trusted;
- Fully trusted.
Once the manual validation and signing process is completed by introducers, the system examines the number of signatures and their associated trust levels. It then employs a mathematical formula that takes into account several parameters to calculate the overall trust level. The mathematical equation used to determine the trust level of the public key certificate is as follows:In Equation (1), the following variables are defined:- L represents the certificate trust level.
- c and m represent the number of signatures from fully trusted and marginally trusted introducers, respectively.
- C and M denote the number of signatures required from fully trusted and marginally trusted introducers to validate the certificate. These values are determined by the system authority, where C ≥ 1 and M ≥ 1.
- d represents the depth from the ring owner to the current introducer. In graph terms, the depth signifies the distance from the root node to the current node. Here, calculating the depth value allows us to define the closest to the furthest introducers in the ring hierarchy based on their distance from the ring owner. A depth constraint can also be imposed to reduce the expansion of the key-ring size.
Based on the values obtained from introducers and utilizing the aforementioned mathematical equation, the public key certificate is deemed fully valid if L ≥ 1, marginally valid if 0 < L < 1, and unknown if L = 0. For instance, by setting C = 1 and M = 3, indicating the requirement of at least one signature from a fully trusted introducer or at least three signatures from marginally trusted introducers, and using a depth d of 1 for all the signers, the certificate will be fully trusted; otherwise, it will be marginally or not trusted. This trust level is subsequently appended to the requester’s certificate, offering transparency for individuals from other communities to comprehend the level of trust they should place in it. - (B)
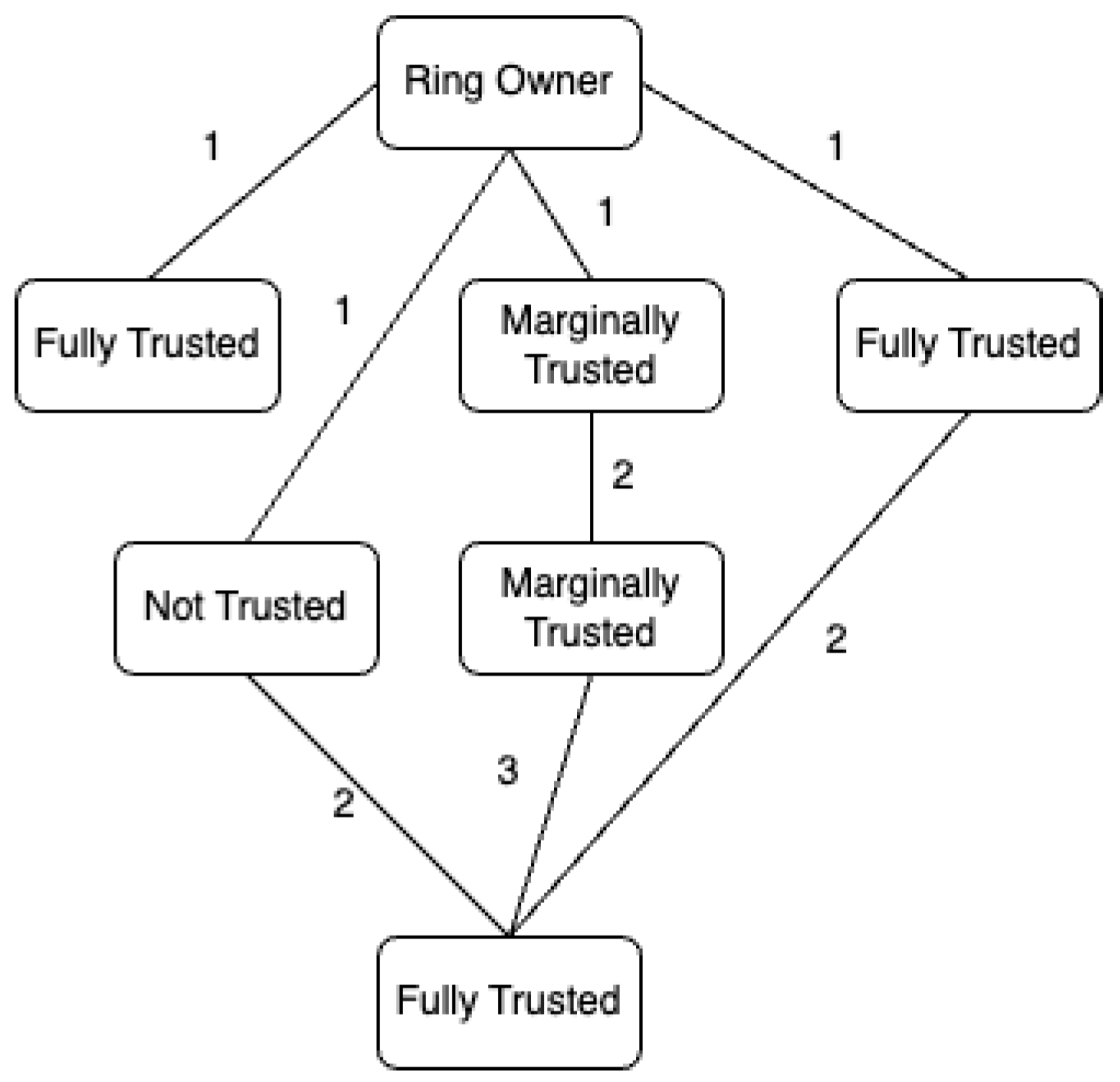
- Ring-Member Authenticity:The validation of a certificate relies on the introducer’s signature, emphasizing the importance of introducers being trusted with valid keys when establishing a key ring. In the system, existing members can verify and sign new members’ public keys to create bridges within the key-ring community. Analogous to certificate verification, a trust level is assigned during the validation process of new members.The trust level of an introducer can be categorized as fully trusted, marginally trusted, or not trusted. These trust levels are factored into the final calculation. For instance, a fully trusted introducer may assign a marginally trusted level to a new member if necessary, while a marginally trusted introducer can assign a fully trusted level during signing. Additionally, each introducer has a depth level along with their level of trust. Figure 4 shows an example of calculating the depth levels of introducers, whether they are directly or indirectly connected to the ring owner. For instance, introducers directly connected have a depth of one, while those indirectly connected have a depth greater than one, varying based on distance. Similar to the verification of public key certificates, a mathematical equation is employed to compute the trust level for the newly introduced.The equation for calculating the trust level during introducer validation is as follows:In Equation (2), the following variables are defined:
- T represents the introducer’s trust level.
- , , and denote the full, marginal, and not trusted trust levels given by fully trusted introducers. , , and are the constant weights determined by the system authority, where, > > . Similarly, , , and are the constant weights for the full, marginal, and not trusted trust levels given by marginally trusted introducers. The same goes for , , and for not trusted introducers.
- c denotes the sum of all trust level weights from the fully trusted introducers divided by their respective depth d. Similarly, m represents the sum of all trust level weights from the marginally trusted introducers divided by their respective depth d. The same goes for n not trusted introducers.
- C, M, and N denote the number of signatures required from the fully, marginally, and not trusted introducers to validate new introducers. These values are determined by the system authority where C ≥ 1, M ≥ 1, and N ≥ 1.
The introducer is classified as fully trusted if T ≥ 1, marginally trusted if 0.5 ≤ T < 1, and not trusted if T < 0.5. Upon successful validation, the new introducer will be incorporated into the key-ring network, and an announcement will be broadcast over the network to inform existing key-ring members.This section outlines various scenarios to explain the trust evaluation mechanism. For illustration purposes, in all scenarios, the weights assigned to the constants are as follows: C = 2, M = 3, and N = 4; = 4, = 3, and = 2; = 3, = 2, and = 1; and = 2, = 1, and = 0.
- Two endorsements are received from fully trusted introducers (one fully trusted, one marginally trusted).
- Three endorsements are received from marginally trusted introducers (two fully trusted, one marginally trusted).
- The trust score is T = 4.4722 and T > 1. Hence, the new participant is deemed a fully trusted introducer.
- One endorsement is received from a fully trusted source (not trusted).
- Two endorsements are received from marginally trusted sources (marginally trusted).
- Two endorsements are received from untrusted sources (marginally trusted).
- T = 0.9250 and 0.5 <= T < 1, marking the participant as marginally trusted.
- One endorsement is received from a marginally trusted source (not trusted).
- Three endorsements are received from untrusted sources (two marginally trusted, one not trusted).
- T = 0.4417 and T < 0.5. Therefore, the new participant is considered an untrusted introducer.
5.2.3. X.509 Certificate Creation
- Multiple Signatures: Accommodates signatures from multiple introducers.
- Certificate Trust Level: Contains the trust level calculated using Equation (1) during certificate validation.
- Transaction ID: This is a unique ID for blockchain transactions and is used to fetch certificate-related information from the blockchain network.
- Introducer Identifier: This identifier is used as a unique address to identify introducers in key-ring smart contracts.



5.2.4. Certificate Revocation
- Certificate Owners: They may request revocation in the event of server attacks or upon suspicion of compromised, stolen, or lost private keys.
- Authenticated Ring Members: These members possess the authority to request revocation for diverse reasons.
- Other Entities: This category encompasses users who have evidence of certificate misuse, deception, or inappropriate behavior, as well as authorized government members who can apply for certificate revocation.
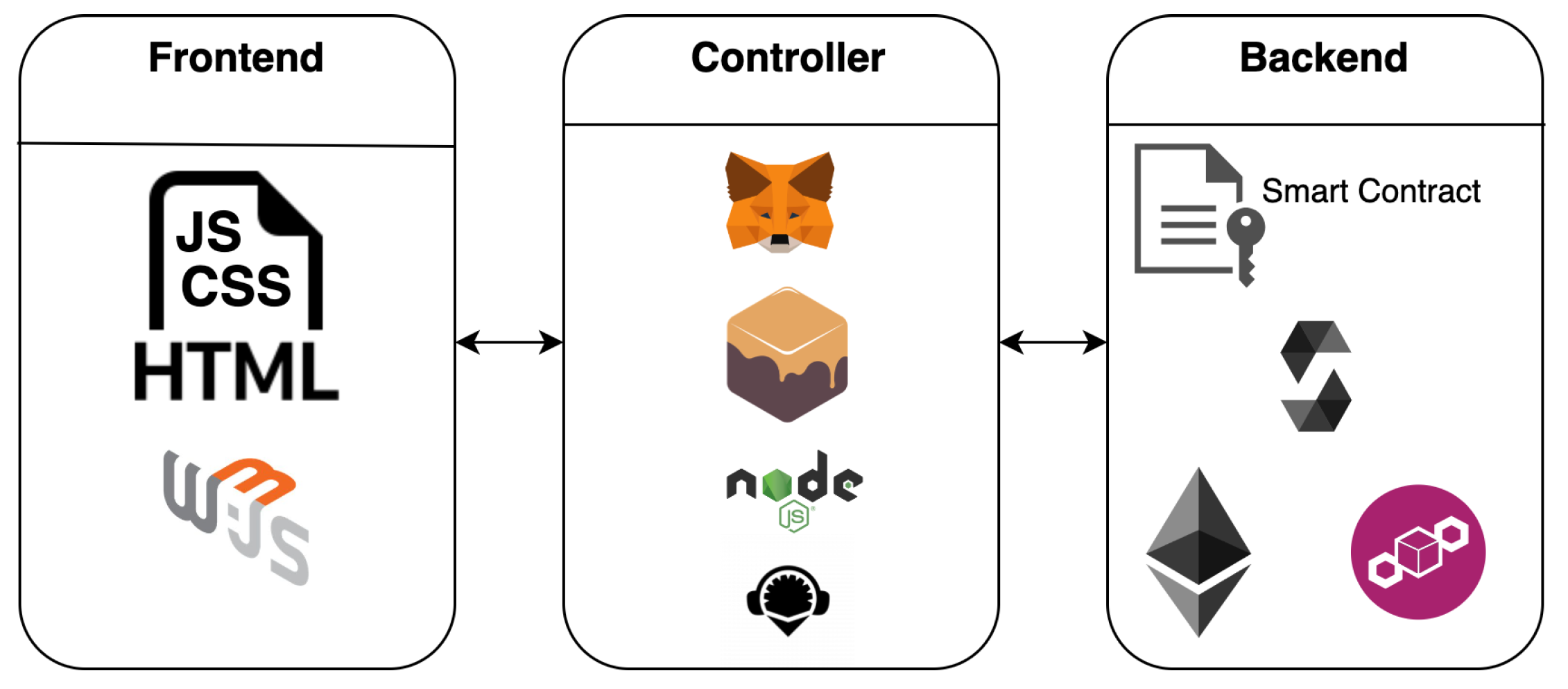
5.3. Blockchain Integration
6. Implementation
- Issue_cert: Responsible for processing CSR and revocation requests, as well as initial verification.
- Certificate: Generates X.509 certificates and oversees the signing process.
- Verification: Manages verification processes with introducers and aids in building the key ring.
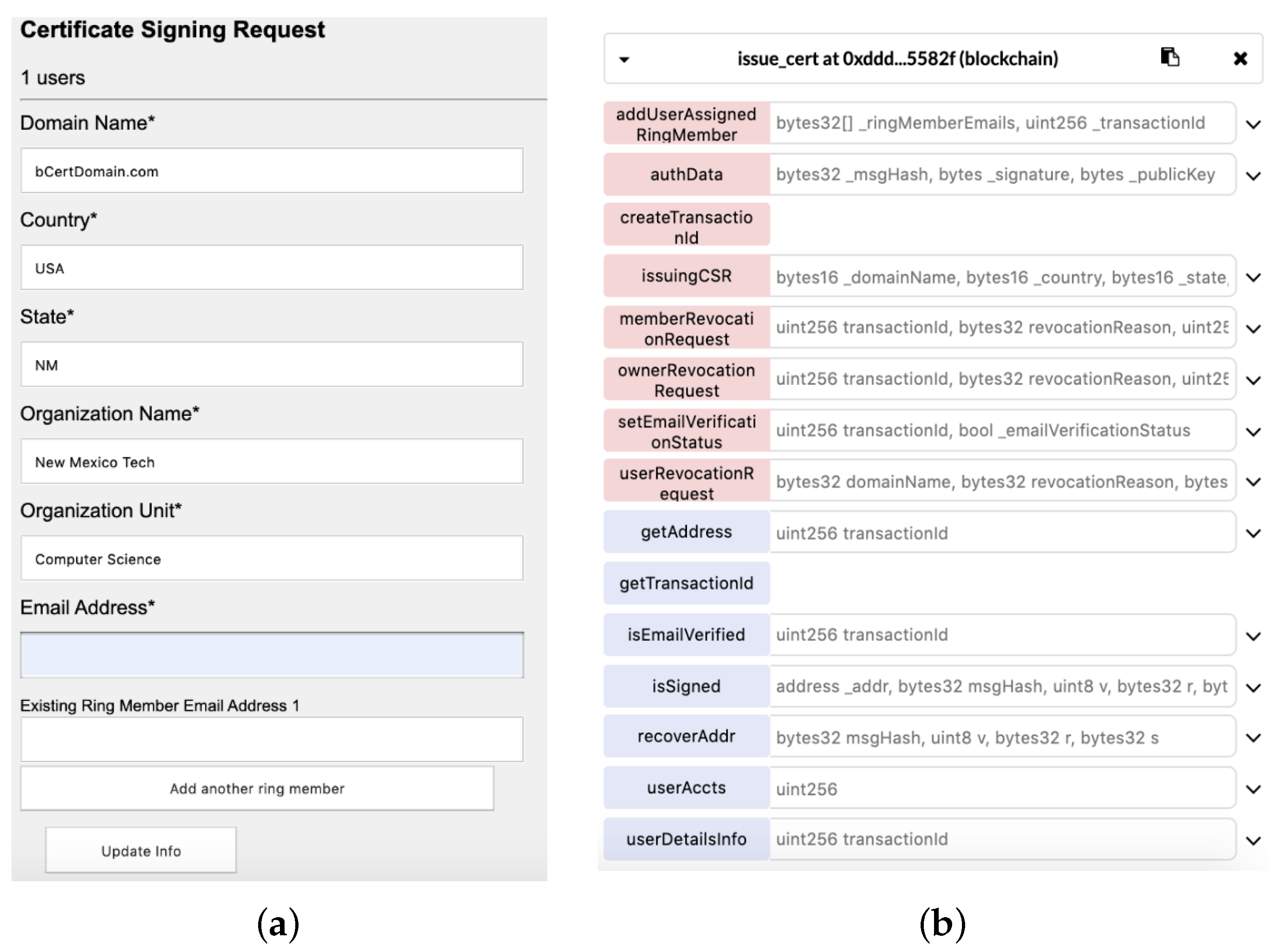
6.1. Certificate Signing Request
6.2. Backend Controller
6.3. Smart Contracts
6.3.1. Issue_cert Smart Contract
6.3.2. Certificate Smart Contract
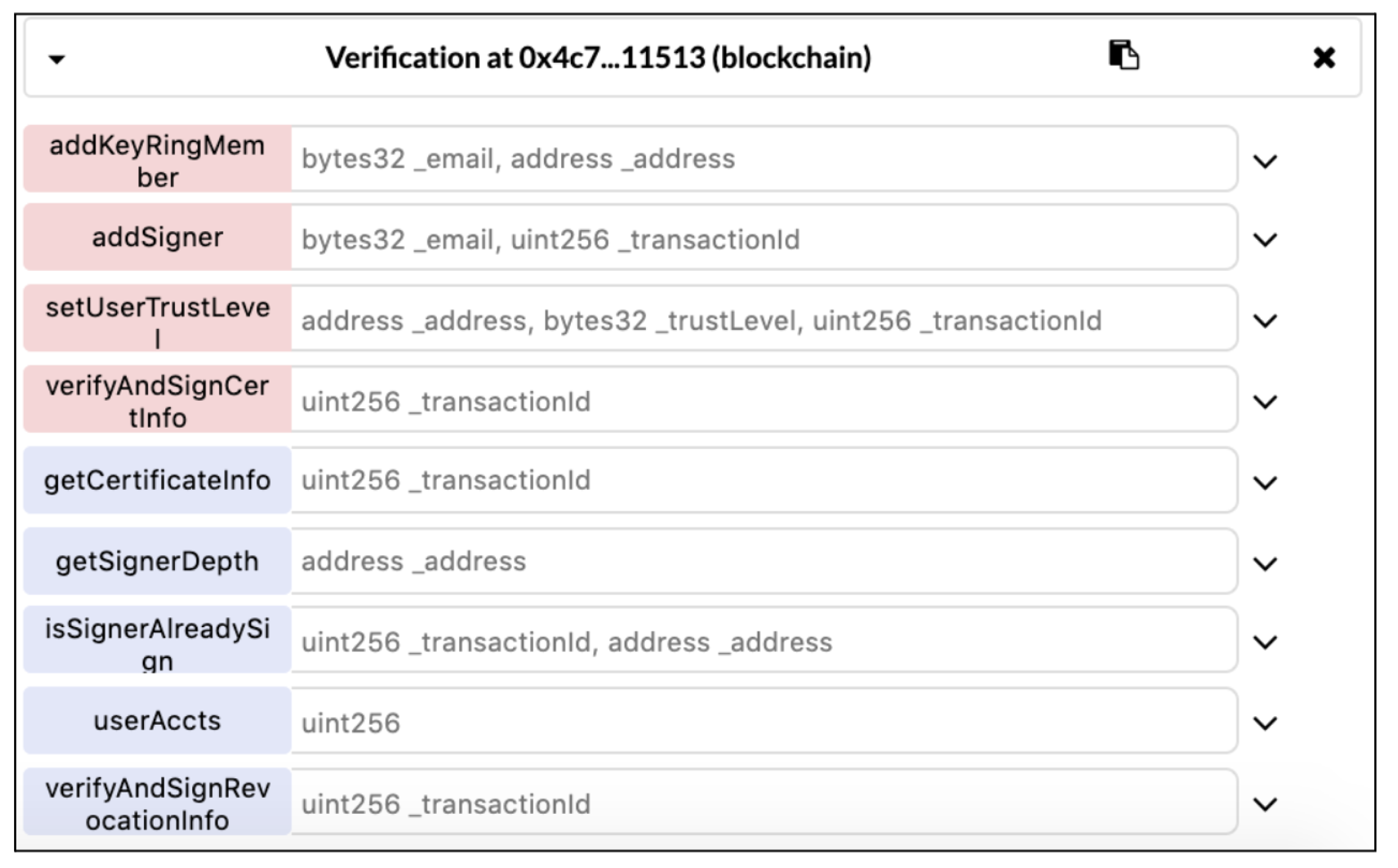
6.3.3. Verification Smart Contract
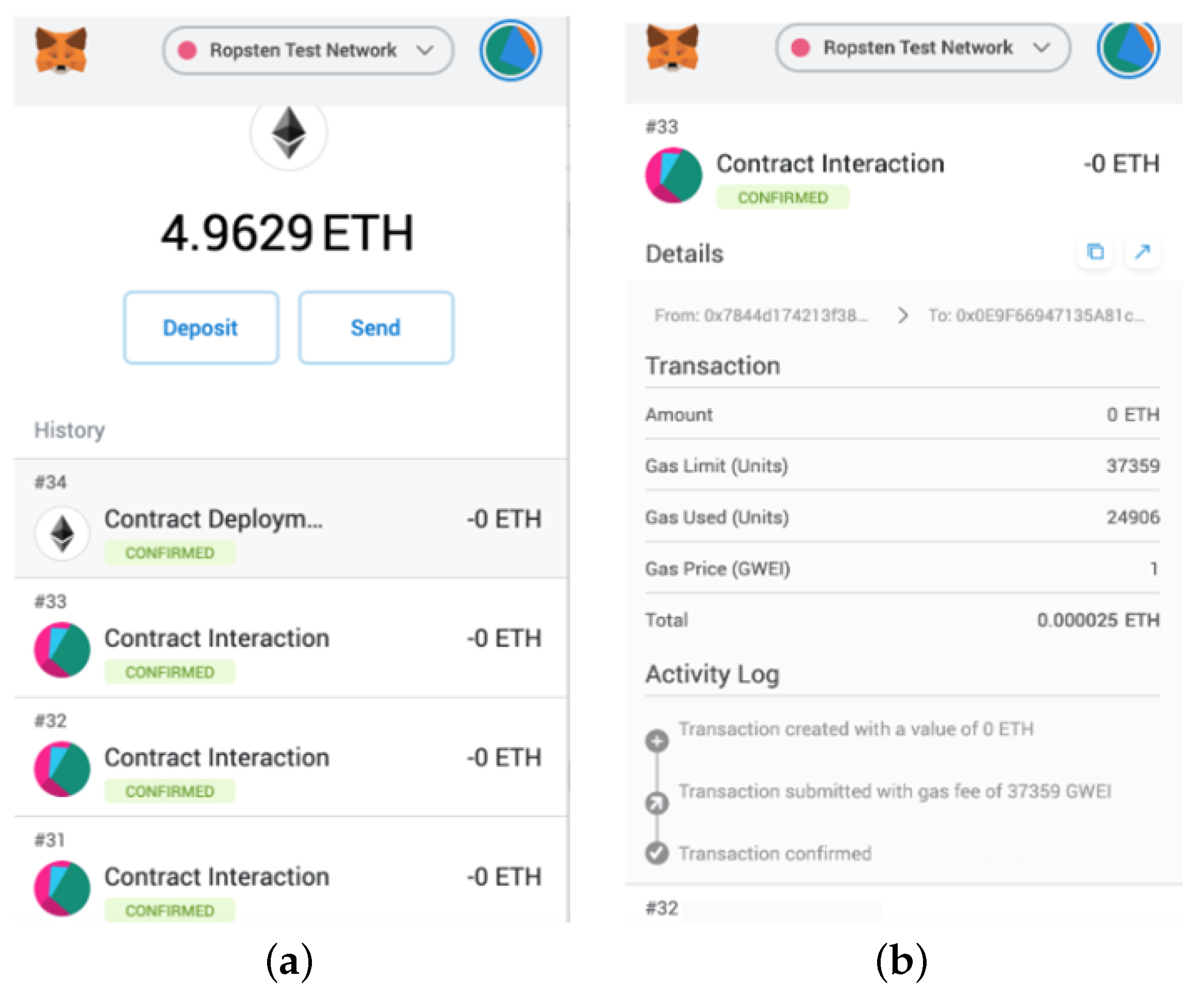
6.4. System Test
7. System Evaluation and Limitations
7.1. Security Evaluation
- Earlier research was primarily aimed at detecting attacks and fast certificate revocation, with less emphasis on detailed prevention strategies. Our research, however, prioritizes preventing malicious certification through an advanced verification system and a decentralized trust network. Public blockchains utilize cryptography to prevent unauthorized access, complemented by an initial authentication system designed for the same purpose. Furthermore, our verification system, upheld by members of a trusted key ring, ensures that certificates are not issued to malicious users.
- In our system, each certification and revocation action is meticulously recorded on the blockchain network, establishing a transparent and immutable public audit trail. This property provides a robust mechanism for tracking and identifying compromised certifications. As a result, the system is capable of executing faster revocations.
- The decentralized and tamper-resistant characteristics of blockchain significantly hinder attackers’ ability to intercept and alter data exchanged between parties. Furthermore, numerous members are involved in creating and revocation of certificates, making MitM attacks nearly impossible.
- The inclusion of multiple signatures in the X.509v3 to issue a certificate significantly reduces the risk of CA compromise and the problem of a single point of failure.
7.2. Cost Analysis
- Simplicity and Efficiency: By maintaining simple contract designs and employing Solidity’s features, such as utilizing bytes over strings, preferring delegatecall where possible, and using bit operations, we aim to minimize gas costs.
- Cost Calculation:
- -
- Low-Cost Operations: Common tasks like request creation, signature additions, and revocations incur moderate costs.
- -
- Free Operations: Operations that do not modify blockchain data, such as CSR processing and data reading, are free.
- -
- High-Cost Write Operations: Functions that update blockchain data, especially storing CSR hashes and certificate metadata, are gas-intensive.
7.3. Standardization and Interoperability
- Permission Type: Choosing between a permissionless or permissioned blockchain.
- Blockchain Type: Evaluating the benefits of different blockchain implementations, like Ethereum or custom blockchains.
- Trust Model Type: Deciding between a hierarchical PKI or a WoT model.
- Certificate Format: Ensuring that formats like X.509 or custom formats support interoperability.
- Revocation: Incorporating certificate revocation as a critical security feature.
- Implementable: Demonstrating feasibility through proof-of-concept implementations.
- Complexity and Cost: Assessing and managing system complexity and operational costs.
- Updateable Key: Providing support for key updates for long-term sustainability.
- We adopted a permissionless blockchain for certificate transparency and suitability for large-scale applications.
- We chose Ethereum smart contracts for their decentralized infrastructure, facilitating the storage of certificate metadata to solve block traversal problems.
- We adopted a WoT trust model to eliminate centralized CAs and ensure a distributed verification system.
- We integrated multi-signature capabilities into the X.509v3 extension field, requiring minimal browser adjustments.
- We proposed a theoretical approach for expediting the revocation process.
- We provided a detailed system architecture with implementation specifics as a proof of concept. The system also supports the updateable key feature.
7.4. Scalability Evaluation
8. Discussion
- Trust Model: Evaluates the trust relationship for deciding certificate legitimacy.
- Certificate Format: Specifies the proposed certificate format, like X.509 or PGP.
- Auto-Scalable: Indicates whether the system features auto-scalability for large networks.
- Certificate Transparency: Reflects the visibility of issued certificates.
- Browser Side Unchanged: Describes the minimal modifications required for browsers and servers to align with the proposed schema.
- Decentralized Trust: Involves distributed trust calculation across multiple servers.
- Advanced Verification: Utilizes strong authentication methods for precise identity verification.
- Prohibits Malicious Certification: Offers enhanced security and a robust verification system.
- No Centralized CA: Operates without a centralized certificate authority.
- Monitors CA Activity: Allows domains or external systems to oversee all CA operations.
9. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Berkovits, S.; Chokhani, S.; Furlong, J.A.; Geiter, J.A.; Guild, J.C. Public Key Infrastructure Study; Final Report; National Institute of Standards and Technology: Gaithersburg, MD, USA, 1994. [Google Scholar]
- Boeyen, S.; Santesson, S.; Polk, T.; Housley, R.; Farrell, S.; Cooper, D. RFC 5280; Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. Internet Engineering Task Force, May 2008. Available online: https://doi.org/10.17487/RFC5280 (accessed on 29 March 2024).
- Gupta, V.; Gupta, S. Securing the wireless internet. IEEE Commun. Mag. 2001, 39, 68–74. [Google Scholar] [CrossRef]
- International Telecommunication Union. ITU-T Recommendation X. 509| ISO/IEC 9594-8: “Information Technology-Open Systems Interconnection-The Directory: Public-Key and Attribute Certificate Frameworks”; Tecnical Report; ITU: Geneva, Switzerland, 2012. [Google Scholar]
- Ayer, A. Misissued/Suspicious Symantec Certificates. 2017. Available online: https://www.mail-archive.com/dev-security-policy@lists.mozilla.org/msg05455.html (accessed on 29 March 2024).
- Arthur, C. DigiNotar SSL Certificate Hack Amounts to Cyberwar, Says Expert. 2011. Available online: https://www.theguardian.com/technology/2011/sep/05/diginotar-certificate-hack-cyberwar (accessed on 29 March 2024).
- Liu, Y.; Tome, W.; Zhang, L.; Choffnes, D.; Levin, D.; Maggs, B.; Mislove, A.; Schulman, A.; Wilson, C. An end-to-end measurement of certificate revocation in the web’s PKI. In Proceedings of the 2015 Internet Measurement Conference, Tokyo, Japan, 28–30 October 2015; pp. 183–196. [Google Scholar]
- Berkowsky, J.A.; Hayajneh, T. Security issues with certificate authorities. In Proceedings of the 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 19–21 October 2017; pp. 449–455. [Google Scholar]
- Laurie, B.; Langley, A.; Kasper, E. RFC 6962; Certificate Transparency; Internet Engineering Task Force: Fremont, CA, USA, 2013. [Google Scholar] [CrossRef]
- Matsumoto, S.; Szalachowski, P.; Perrig, A. Deployment Challenges in Log-Based PKI Enhancements. In Proceedings of the EuroSec ’15: Eighth European Workshop on System Security, Bordeaux, France, 21 April 2015. [Google Scholar] [CrossRef]
- Housley, R.; Ford, W.; Polk, W.; Solo, D. RFC 2459; Internet X. 509 Public Key Infrastructure Certificate and CRL Profile; Internet Engineering Task Force: Fremont, CA, USA, 1999. [Google Scholar] [CrossRef]
- Millen, J.K.; Wright, R.N. Certificate revocation the responsible way. In Proceedings of the Proceedings Computer Security, Dependability, and Assurance: From Needs to Solutions (Cat. No. 98EX358), York, UK; Williamsburg, VA, USA, 7–9 July 1998; pp. 196–203. [Google Scholar]
- Kubilay, M.Y.; Kiraz, M.S.; Mantar, H.A. CertLedger: A new PKI model with Certificate Transparency based on blockchain. Comput. Secur. 2019, 85, 333–352. [Google Scholar] [CrossRef]
- Boyen, X.; Herath, U.; McKague, M.; Stebila, D. Associative blockchain for decentralized PKI transparency. Cryptography 2021, 5, 14. [Google Scholar] [CrossRef]
- Hwang, G.H.; Chang, T.K.; Chiang, H.W. A semidecentralized PKI system based on public blockchains with automatic indemnification mechanism. Secur. Commun. Netw. 2021, 2021, 1–15. [Google Scholar] [CrossRef]
- Khieu, B.; Moh, M. CBPKI: Cloud blockchain-based public key infrastructure. In Proceedings of the 2019 ACM Southeast Conference, Kennesaw, GA, USA, 18–20 April 2019; pp. 58–63. [Google Scholar]
- Chen, J.; Yao, S.; Yuan, Q.; He, K.; Ji, S.; Du, R. Certchain: Public and efficient certificate audit based on blockchain for tls connections. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications, Honolulu, HI, USA, 16–19 April 2018; pp. 2060–2068. [Google Scholar]
- Fromknecht, C.; Velicanu, D.; Yakoubov, S. Certcoin: A Namecoin Based Decentralized Authentication System; Massachusetts Institute of Technology: Cambridge, MA, USA, 2014; Volume 6, pp. 46–56. [Google Scholar]
- Qin, B.; Huang, J.; Wang, Q.; Luo, X.; Liang, B.; Shi, W. Cecoin: A decentralized PKI mitigating MitM attacks. Future Gener. Comput. Syst. 2020, 107, 805–815. [Google Scholar] [CrossRef]
- Schwittmann, L.; Wander, M.; Weis, T. Domain Impersonation is Feasible: A Study of CA Domain Validation Vulnerabilities. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; pp. 544–559. [Google Scholar]
- Incidents Involving the CA WoSign, in June 2015. Available online: https://wiki.mozilla.org/CA/WoSign_Issues (accessed on 29 March 2024).
- Haenni, R.; Jonczy, J. A new approach to PGP’s web of trust. In Proceedings of the EEMA’07, European e-Identity Conference, Paris, France, 12–13 June 2007. [Google Scholar]
- Wang, X.; Bai, Y.; Hu, L. Certification with multiple signatures. In Proceedings of the 4th Annual ACM Conference on Research in Information Technology, Chicago, IL, USA, 30 September–3 October 2015; pp. 13–18. [Google Scholar]
- Buterin, V.; Wood, G. Ethereum white paper. GitHub Repos. 2013, 1, 22–23. [Google Scholar]
- Zhai, Z.; Shen, S.; Mao, Y. BPKI: A secure and scalable blockchain-based public key infrastructure system for web services. J. Inf. Secur. Appl. 2022, 68, 103226. [Google Scholar] [CrossRef]
- Ryan, M.D. Enhanced certificate transparency and end-to-end encrypted mail. In Proceedings of the 21st Annual Network and Distributed System Security Symposium, NDSS 2014, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Basin, D.; Cremers, C.; Kim, T.H.J.; Perrig, A.; Sasse, R.; Szalachowski, P. ARPKI: Attack resilient public-key infrastructure. In Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 382–393. [Google Scholar]
- Toorani, M.; Gehrmann, C. A decentralized dynamic PKI based on blockchain. In Proceedings of the 36th Annual ACM Symposium on Applied Computing, Virtual, 22–26 March 2021; pp. 1646–1655. [Google Scholar]
- Yakubov, A.; Shbair, W.; State, R. BlockPGP: A blockchain-based framework for PGP key servers. In Proceedings of the 2018 Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018; pp. 316–322. [Google Scholar]
- Al-Bassam, M. SCPKI: A smart contract-based PKI and identity system. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, Abu Dhabi, United Arab Emirates, 2 April 2017; pp. 35–40. [Google Scholar]
- Liang, W.; You, L.; Hu, G. LRS_PKI: A novel blockchain-based PKI framework using linkable ring signatures. Comput. Netw. 2023, 237, 110043. [Google Scholar] [CrossRef]
- Dua, A.; Barpanda, S.S.; Kumar, N.; Tanwar, S. Trustful: A decentralized public key infrastructure and identity management system. In Proceedings of the 2020 IEEE Globecom Workshops (GC Wkshps), Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Kakei, S.; Shiraishi, Y.; Mohri, M.; Nakamura, T.; Hashimoto, M.; Saito, S. Cross-certification towards distributed authentication infrastructure: A case of hyperledger fabric. IEEE Access 2020, 8, 135742–135757. [Google Scholar] [CrossRef]
- Roberts, P. Phony SSL Certificates issued for Google, Yahoo, Skype, Others. 2011. Available online: https://threatpost.com/phony-ssl-certificates-issued-google-yahoo-skype-others-032311/75061/ (accessed on 29 March 2024).
- Naor, M.; Nissim, K. Certificate revocation and certificate update. IEEE J. Sel. Areas Commun. 2000, 18, 561–570. [Google Scholar] [CrossRef]
- Zimmermann, P.R. The Official PGP User’s Guide; MIT Press: Cambridge, MA, USA, 1995. [Google Scholar]
- Michael Satran, M.J.X. 509 Public Key Certificates. 2018. Available online: https://docs.microsoft.com/en-us/windows/win32/seccertenroll/about-x-509-public-key-certificates (accessed on 29 March 2024).
- Housley, R.; Polk, T.; III, L.E.B. RFC 3279; Algorithms and Identifiers for the Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile; Internet Engineering Task Force: Fremont, CA, USA, 2002. [Google Scholar] [CrossRef]
- Housley, R.; Schaad, J.; Kaliski, B. RFC 4055; Additional Algorithms and Identifiers for RSA Cryptography for use in the Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile; Internet Engineering Task Force: Fremont, CA, USA, 2005. [Google Scholar] [CrossRef]
- Shefanovski, D.; Leontiev, S. RFC 4491; Using the GOST R 34.10-94, GOST R 34.10-2001, and GOST R 34.11-94 Algorithms with the Internet X.509 Public Key Infrastructure Certificate and CRL Profile; Internet Engineering Task Force: Fremont, CA, USA, 2006. [Google Scholar] [CrossRef]
- Legg, D.S. RFC 4913; Abstract Syntax Notation X (ASN.X) Representation of Encoding Instructions for the Generic String Encoding Rules (GSER); Internet Engineering Task Force: Fremont, CA, USA, 2007. [Google Scholar] [CrossRef][Green Version]
- Santesson, S.; Myers, M.; Ankney, R.; Malpani, A.; Galperin, S.; Adams, C. RFC 2560; X. 509 Internet Public Key Infrastructure Online Certificate Status Protocol-OCSP; Internet Engineering Task Force: Fremont, CA, USA, 1999. [Google Scholar] [CrossRef]
- AlSobeh, A.M.; Magableh, A.A. BlockASP: A Framework for AOP-based Model Checking Blockchain System. IEEE Access 2023, 11, 115062–115075. [Google Scholar] [CrossRef]
- Haugum, T.; Hoff, B.; Alsadi, M.; Li, J. Security and privacy challenges in blockchain interoperability-A multivocal literature review. In Proceedings of the 26th International Conference on Evaluation and Assessment in Software Engineering, Gothenburg, Sweden, 13–15 June 2022; pp. 347–356. [Google Scholar]
- Lesavre, L.; Varin, P.; Mell, P.; Davidson, M.; Shook, J. A taxonomic approach to understanding emerging blockchain identity management systems. arXiv 2019, arXiv:1908.00929. [Google Scholar]
- Longchamp, Y.; Deshpande, S.; Mehra, U.; The Blockchain Trilemma. SEBA Swiss, October 2020. Available online: https://theblockchaintest.com/uploads/resources/SEBA%20-%20The%20Blockchain%20Trilema%20-%202020%20-%20Oct.pdf (accessed on 29 March 2024).
- Luo, X.; Xu, Z.; Xue, K.; Jiang, Q.; Li, R.; Wei, D. ScalaCert: Scalability-Oriented PKI with Redactable Consortium Blockchain Enabled “On-Cert” Certificate Revocation. In Proceedings of the 2022 IEEE 42nd International Conference on Distributed Computing Systems (ICDCS), Bologna, Italy, 10–13 July 2022; pp. 1236–1246. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Cortes-Goicoechea, M.; Franceschini, L.; Bautista-Gomez, L. Resource analysis of Ethereum 2.0 clients. In Proceedings of the 2021 3rd Conference on Blockchain Research & Applications for Innovative Networks and Services (BRAINS), Paris, France, 27–30 September 2021; pp. 1–8. [Google Scholar]


| Schema | Features | Benefits | Drawbacks |
|---|---|---|---|
| Yakubov et al. [29] | A smart contract-based hybrid X.509v3 certificate that incorporates blockchain metadata. |
|
|
| CertLedger [13] | Certificate transparency and records all issued certificates and revocation status. |
|
|
| Hwang et al. [15] | Leverages TP-Merkle tree data structure for transparency and a fully automated compensation system. Partially addresses scalability issues. |
|
|
| CBPKI [16] | Incorporates blockchain and cloud technologies. Decoupling data from the certificate authority |
|
|
| CertChain [17] | Establishes CertOper for storing certificates and enabling forward traceability. Segregates revocation history. |
|
|
| CertCoin [18] | Manages a public record of domains and associated public keys utilizing Bitcoin, distributed hash tables, and a Merkle accumulator as a CRL. |
|
|
| CeCoin [19] | Blockchain and web-of-trust-based PKI influenced by Bitcoin. Miners replace CAs. |
|
|
| DBPKI [28] | A dynamic PKI based on blockchain and the WoT. Any system entity can serve as an auditor and handle revocation tasks. |
|
|
| SCPKI [30] | Utilizes Ethereum smart contracts to detect malicious certificates and the WoT for verification. Saves certificate data in the InterPlanetary File System (IPFS). |
|
|
| META_PKI [33] | A cross-certification approach employing a smart contract on Hyperledger Fabric. It offers distributed authentication by using multiple service providers. |
|
|
| Proposed system | WoT model and blockchain-based PKI. Incorporates trusted key rings and an advanced verification system. Offers faster revocation. |
|
|
| Accomplishment | Approach | Existing Problem Addressed |
|---|---|---|
| Decentralized PKI | Create a blockchain-based decentralized PKI, utilizing a distributed trust model for enhanced security in the certification process | Centralized PKI limitations |
| Build distributed trust model | Employ a web of trust model to build a key ring with trusted members to work as CAs | Single point of failure |
| Introduce multiple introducers | Empower multiple authorized introducers to verify and sign X.509 certificates | Single point of failure, MitM attacks |
| Prioritized trusted introducers | Incorporating the concept of introducer depth helps limit the key ring’s size and gives precedence to the introducer in closer proximity to the ring owner | |
| Minimal modifications on the browser side | Instead of changing the existing certificate format, we leverage the extension field in X.509v3 to incorporate additional signatures | |
| Information publicly visible | The nature of blockchain’s distributed and append-only data entry helps to keep the certificate information in the public ledger | Lack of transparency |
| Faster revocation | Data transparency facilitates the detection of misbehaving CAs and the decentralized verification process and expedites the revocation of certificates | Convoluted revocation procedures |
| Data integrity | Blockchain’s immutability ensures the integrity of stored data, making it tamper-proof | Data forgery attack |
| Refine certification algorithm | Provide an enhanced algorithm and procedure to support multiple signatures in X.509v3 | |
| System implementation architecture | Provide complete implementation architecture with workflow and necessary technologies |
| Schema | Trust Model | Certificate Format | Auto-Scalable | Certificate Transparency | Browser Side Unchanged | Decentralized Trust | Advanced Verification | Prohibits Malicious Certification | No Centralized CA | Monitors CA Activity |
|---|---|---|---|---|---|---|---|---|---|---|
| Yakubov et al. [29] | Hierarchical | Hybrid X.509 | × | × | × | PY | × | × | × | PY |
| CertLedger [13] | Hierarchical | X.509 | × | ✓ | × | PY | × | × | × | ✓ |
| Hwang et al. [15] | Hierarchical | X.509 | × | ✓ | × | PY | × | × | × | ✓ |
| CBPKI [16] | Hierarchical | X.509 | ✓ | ✓ | × | PY | × | × | PY | N/A |
| CertChain [17] | Hierarchical | Custom | × | ✓ | × | PY | × | × | × | ✓ |
| CertCoin [18] | WoT | Custom | × | ✓ | × | ✓ | × | PY | ✓ | ✓ |
| CeCoin [19] | WoT | Custom | × | ✓ | × | ✓ | × | PY | ✓ | ✓ |
| DBPKI [28] | WoT | Custom | × | ✓ | × | ✓ | × | PY | ✓ | ✓ |
| SCPKI [30] | WoT | Custom | × | ✓ | × | ✓ | × | PY | ✓ | × |
| Meta-PKI [33] | Hierarchical | Custom | × | ✓ | × | PY | ✓ | × | PY | ✓ |
| Proposed system | WoT | X.509v3 | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Halder, R.; Das Roy, D.; Shin, D. A Blockchain-Based Decentralized Public Key Infrastructure Using the Web of Trust. J. Cybersecur. Priv. 2024, 4, 196-222. https://doi.org/10.3390/jcp4020010
Halder R, Das Roy D, Shin D. A Blockchain-Based Decentralized Public Key Infrastructure Using the Web of Trust. Journal of Cybersecurity and Privacy. 2024; 4(2):196-222. https://doi.org/10.3390/jcp4020010
Chicago/Turabian StyleHalder, Ratna, Dipanjan Das Roy, and Dongwan Shin. 2024. "A Blockchain-Based Decentralized Public Key Infrastructure Using the Web of Trust" Journal of Cybersecurity and Privacy 4, no. 2: 196-222. https://doi.org/10.3390/jcp4020010
APA StyleHalder, R., Das Roy, D., & Shin, D. (2024). A Blockchain-Based Decentralized Public Key Infrastructure Using the Web of Trust. Journal of Cybersecurity and Privacy, 4(2), 196-222. https://doi.org/10.3390/jcp4020010




