Insights into Organizational Security Readiness: Lessons Learned from Cyber-Attack Case Studies
Abstract
:1. Introduction
- the evaluation of multiple real-world cyber-attacks to understand the types of attack;
- the categorization of the human factors leading up to the cyber threats;
- The characterization of cyber-attacks;
- the mitigation strategies; and
- the lessons learned for providing actionable knowledge to create more awareness for all stakeholders.
2. Motivation
3. Case Study Methodology
3.1. Understanding the Types of Attacks
3.2. Cyber-Attack Case Studies by the Industry
3.3. Categorization of the Human Aspects
3.4. Financial Impacts
3.5. Non-Financial Impacts
3.6. Number of Customers (Victims) Impacted
3.7. Cultural Factors
3.8. End-User Trust and Loyalty
3.9. Policy Issues
3.10. Training and Awareness
3.11. Technology Adoption (for Cyber-Threat Prevention)
3.12. Investment
3.13. Factors Leading to Cyber-Attacks
4. Results and Findings
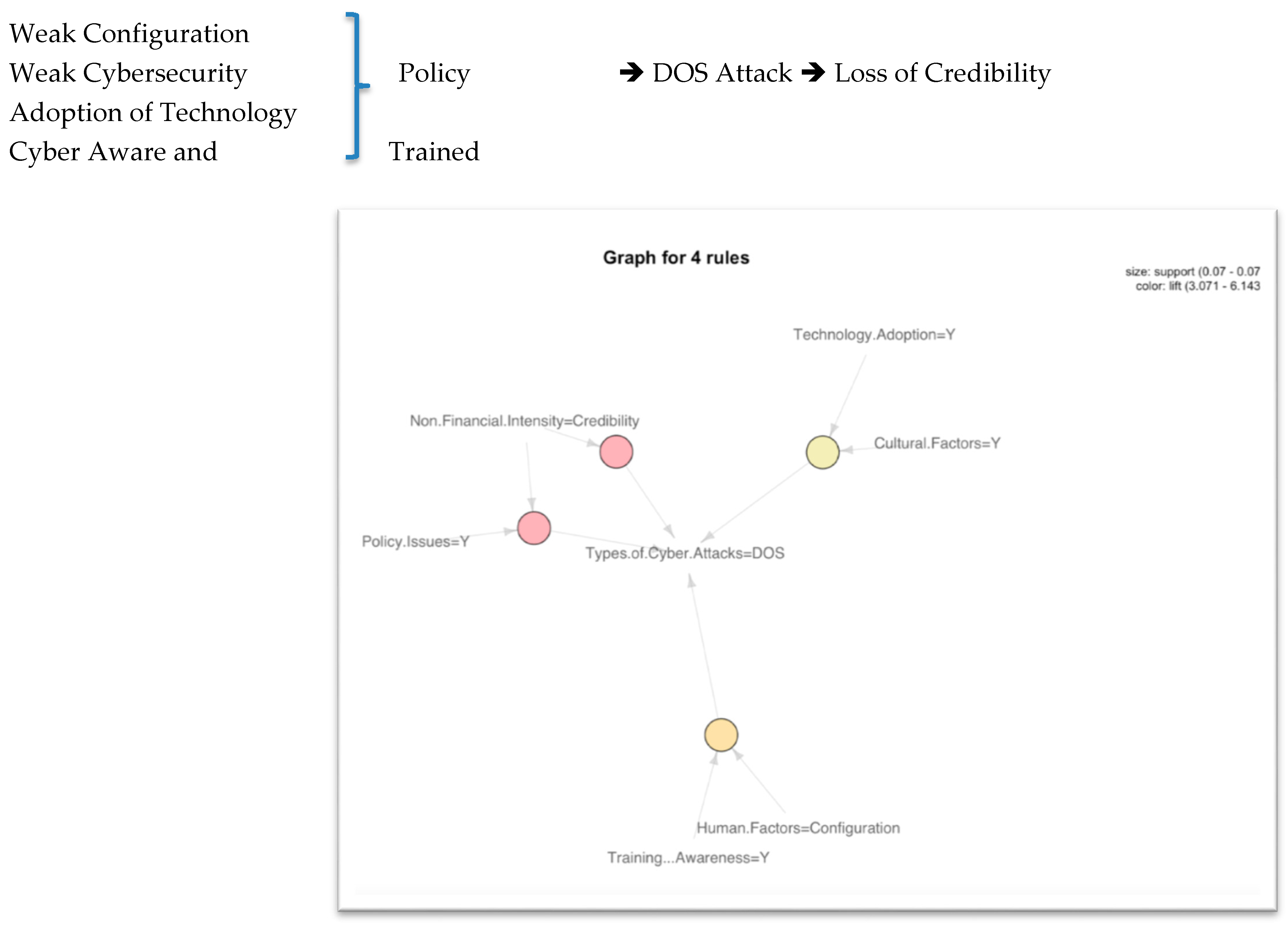
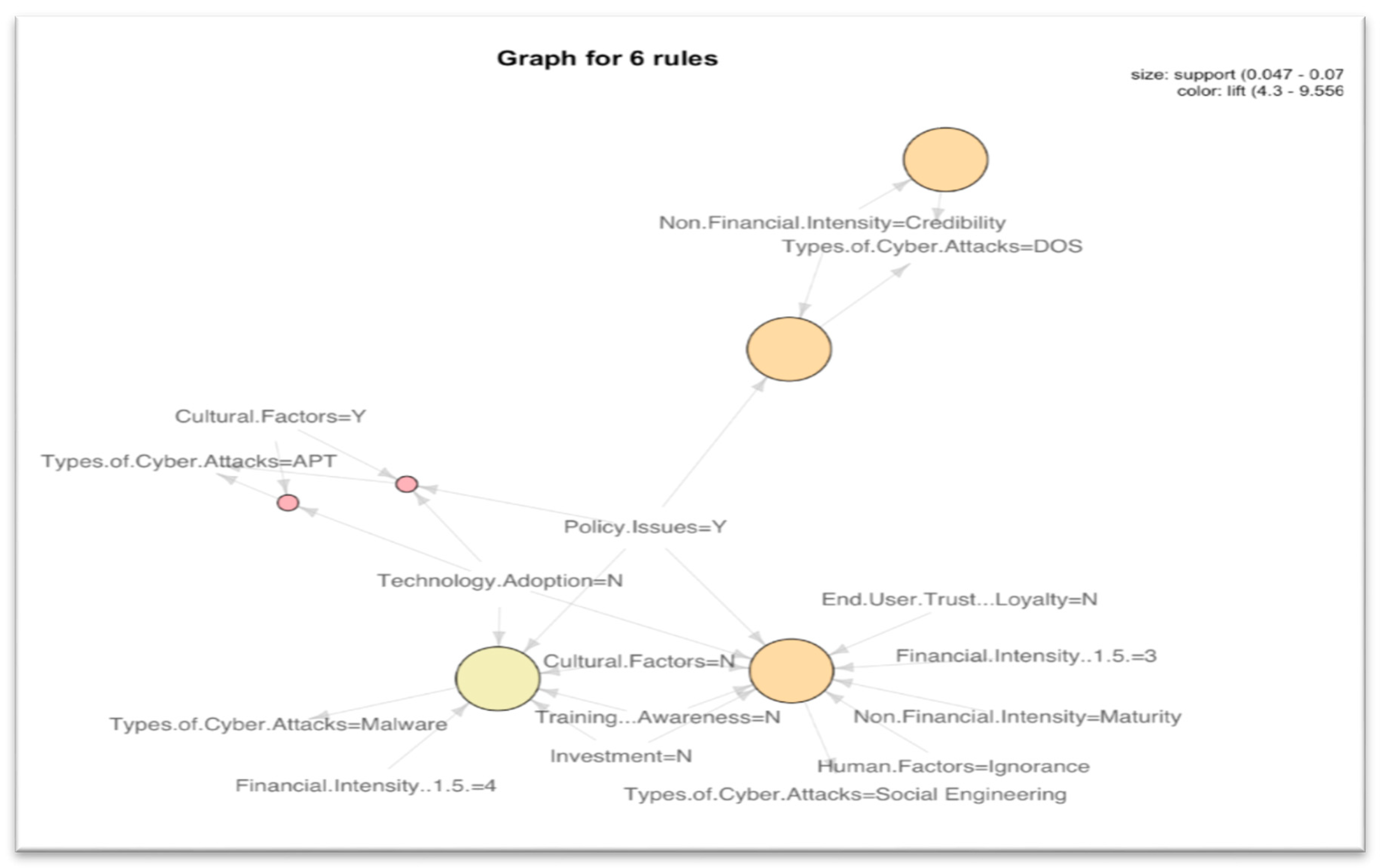
- Denial of Service (DOS) attacks [50] usually occur when an environment has a weak configuration and cybersecurity policy despite training and the related cyber awareness, as shown in Figure 4 below. Strong cybersecurity policies and strong configuration in the IT infrastructure [51] are a necessity for a secure environment because training and cyber awareness are not good enough without implementing them properly. The credibility and the reputation of the organization are impacted heavily by this kind of incident. The DOS attack [52] is related to the circular impactful attributes that imply the loss of credibility.
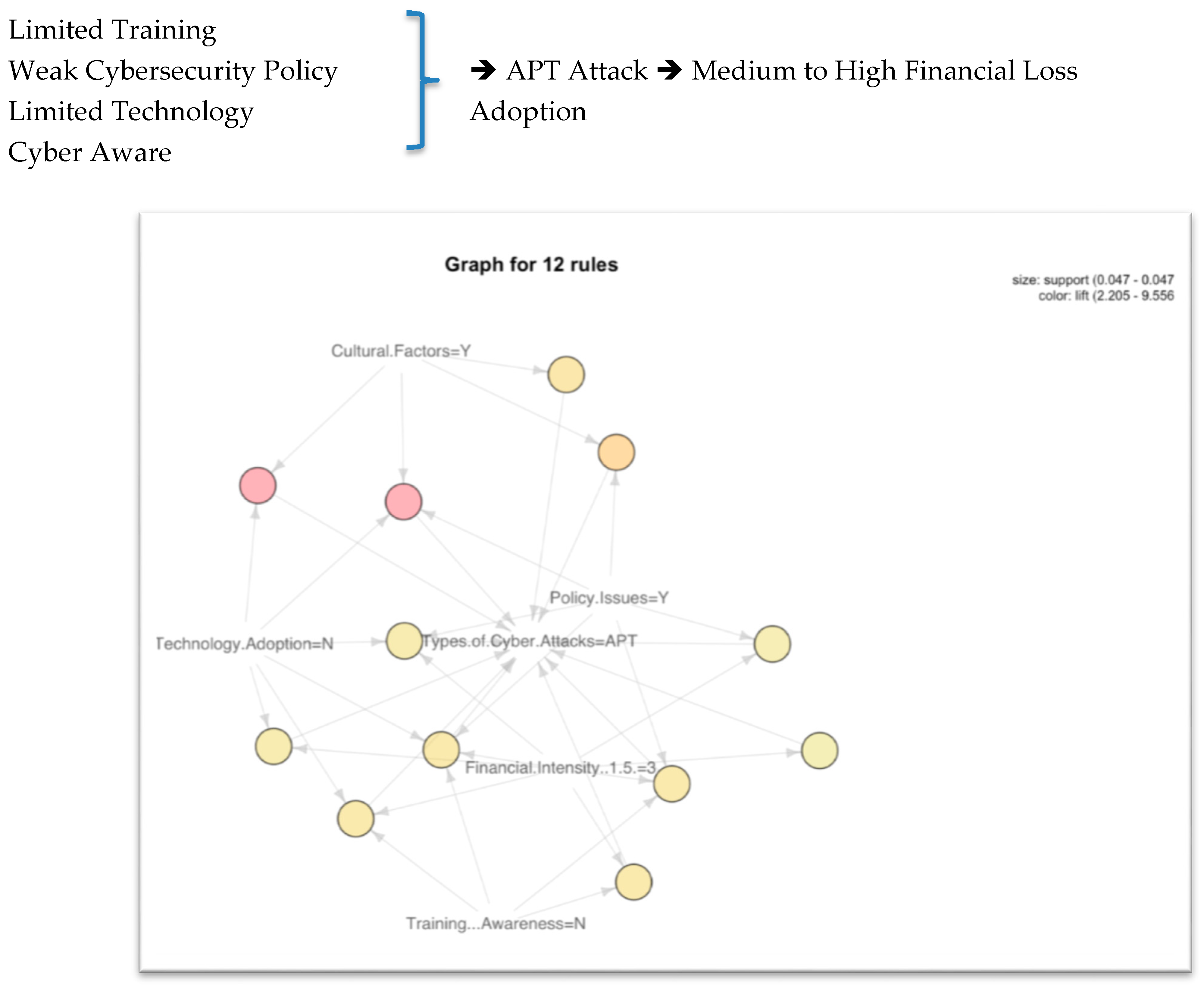
- APT: In Figure 5, we notice that APT attacks are linked to the lack of technology adoption, with not much training, as well as minimal security policy. They may cause medium to high financial loss. Cyber awareness is not enough if we do not have the proper training and technology adoption for cybersecurity.
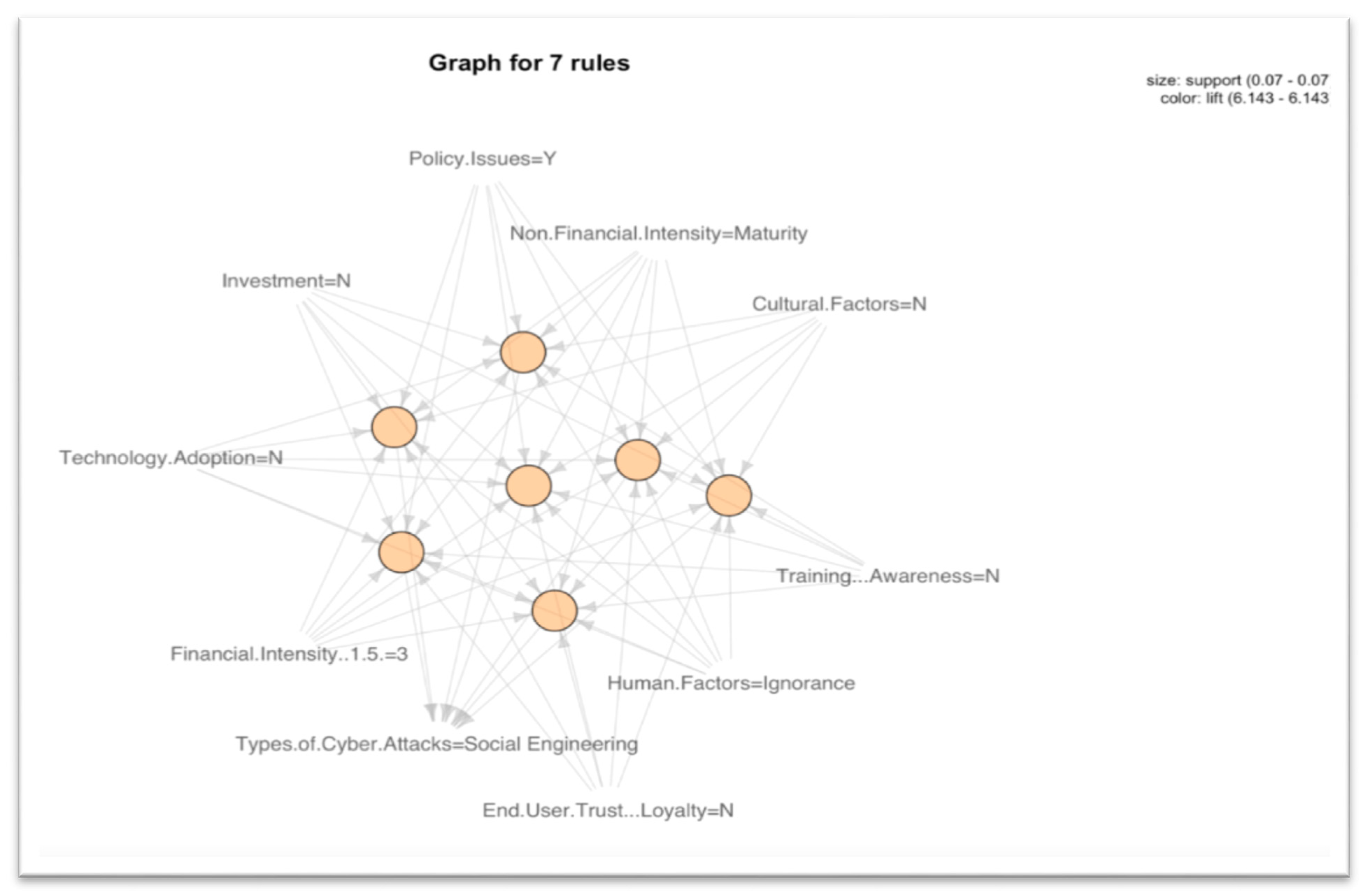
- Social Engineering: We see a lack of awareness and training with a lack of technology adoption. As a result, there is no corporate culture for security and no corporate investment for cybersecurity. The outcome from this may lead to significant financial loss. Ignorance is the main human factor for this kind of attack, as shown in Figure 6.
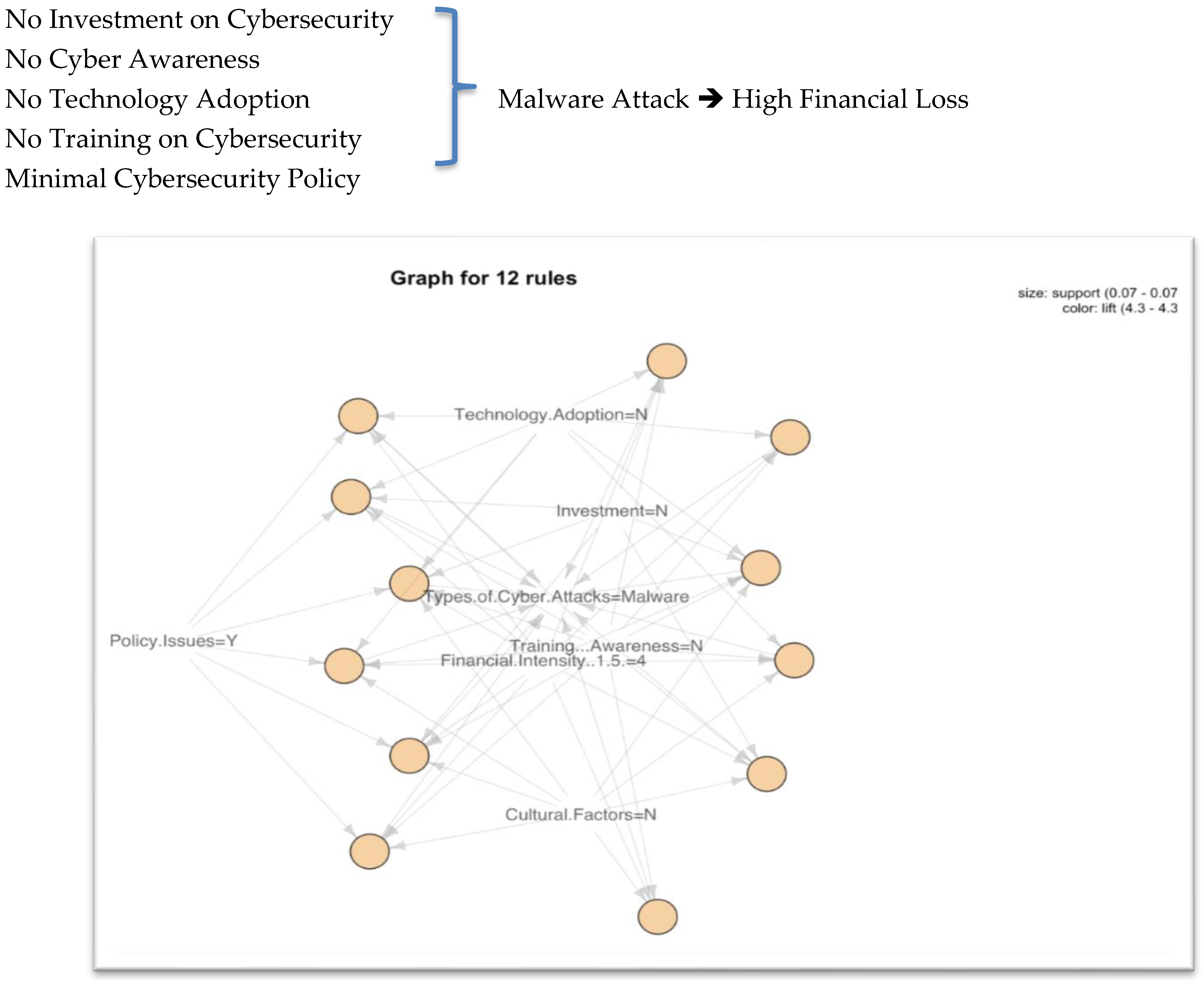
- Malware: If there is no strong cybersecurity policy, not much investment in security, and limited training and awareness on Cybersecurity, organizations may become victims of a Malware attack. The financial consequence from this attack could be very high, as depicted in Figure 7.

5. Overall Observation
- Out of the four main human factors, ignorance and negligence are the two human behaviors that appear to be linked to most of the cyber threats.
- Financial Institutes, Retail and Entertainment industries are the main targets for hackers, in addition to Technology, Health and Energy. This is especially true when financial gains are the key factor behind an attack.
- Biometric threats have serious consequences. When our biometrics are compromised, unfortunately, the mediation from these threats becomes very minimal, because we cannot change the configuration of our fingerprint.
- Cyber threats usually have high customer impacts. The financial loss can be immense, and organizational credibility is at stake.
- Insider threats are perhaps the most difficult to predict or detect. If the internal resources include an individual with bad intentions who may have significant access to the system, it becomes very difficult to protect the organizational assets.
- Having a strong cybersecurity policy is crucial to safeguard from cyber threats. We may have the most sophisticated technology, but with a weakly articulated cyber policy and less governance, an IT environment can be vulnerable to different types of cyber threats.
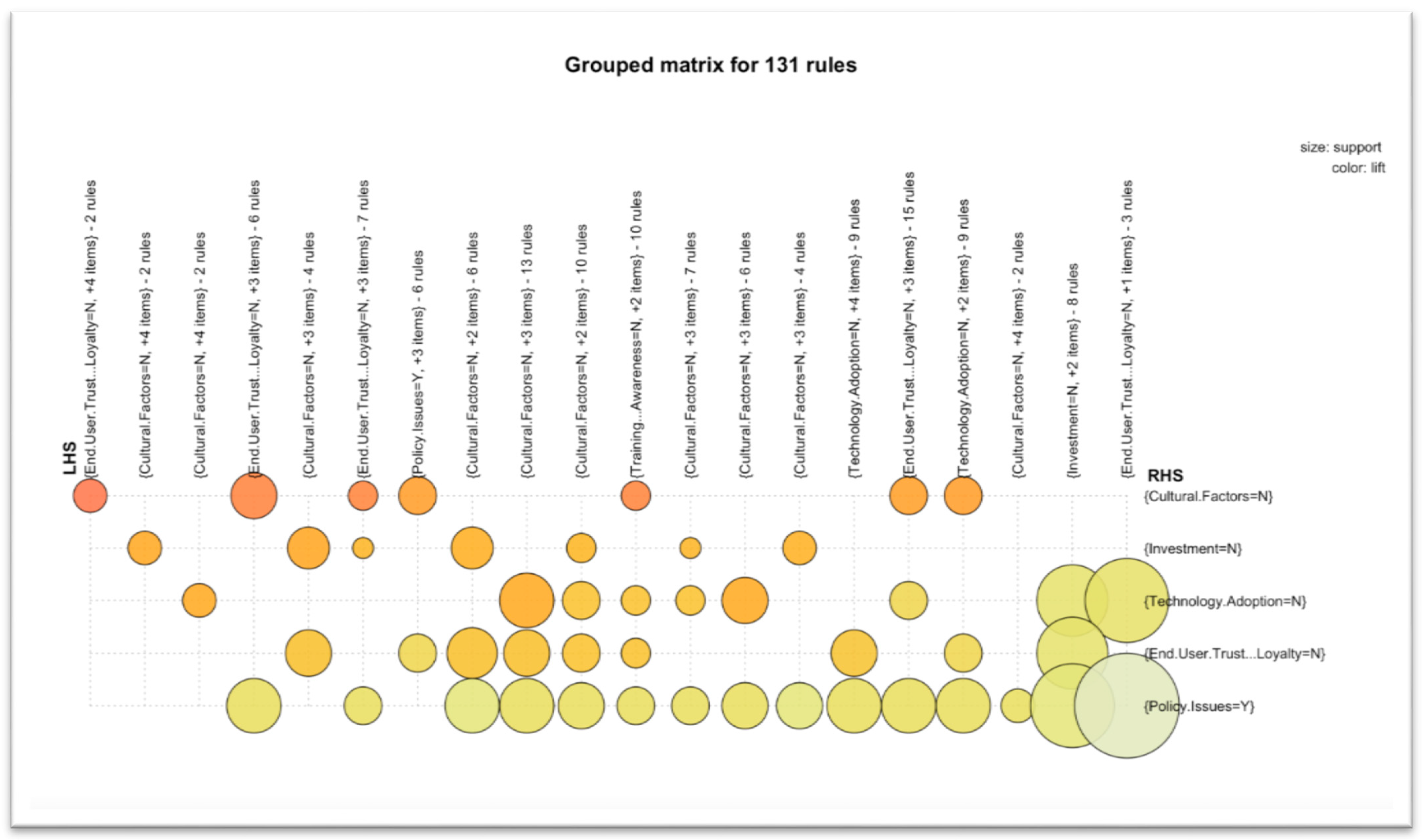
- We observed strong linkages between weak/no cyber policy and less investment on technology, no technology adoption, minimal training and education, and cyber awareness. Among these factors, technology adoption and human factors are the two dominant contributors. In other words, to make the digital assets safe, we need to invest adequately in security, train our employees, build and govern strong cybersecurity policy, and above all adopt and keep up with technology to overcome new and existing security threats. Developing and adopting a strong security policy will help increase awareness and provide opportunities for learning and establishing protocols to prevent cyber threats.
6. Mitigation Strategy
7. Conclusions and Open Challenges
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Paganinip, P. FireEye Why Humans Could Be the Weakest Link in Cyber Security Chain. Security Affairs, 3 October 2012. Available online: http://securityaffairs.co/wordpress/9076/social-networks/why-humans-could-be-the-weakest-link-in-cyber-security-chain.html(accessed on 23 October 2021).
- Abraham, S.; Chengalur-Smith, I. An overview of social engineering malware: Trends, tactics, and implications. Technol. Soc. 2010, 32, 183–196. [Google Scholar] [CrossRef]
- Wheatley, M. Hidden Costs of Sony’s Data Breach Will Add up for Years, Experts Say. Silicon Angle, 20 February 2015. Available online: http://siliconangle.com/blog/2015/02/20/hidden-costs-of-sonys-data-breach-will-add-up-for-years-experts-say/(accessed on 2 March 2021).
- Smith, G. Home Depot Admits 56 million Payment Cards at Risk after Cyber Attack. The Huffington Post, 18 September 2014. Available online: http://www.huffingtonpost.com/2014/09/18/home-depot-hack_n_5845378.html(accessed on 23 May 2019).
- Stevenage, S. Human Aspects of Cybersecurity; Super Identity Project; University of Southampton: Southampton, UK, 2010. [Google Scholar]
- Haggard, S.; Lindsay, R.J. North Korea and the Sony Hack: Exporting Instability Through Cyberspace; Asia Pacific Issues, No. 117; East-West Center: Honolulu, HI, USA, 2015. [Google Scholar]
- Love, D. Why Microsoft And Sony Couldn’t Stop Lizard Squad Attack Despite Warnings. International Business Times, 30 December 2014. Available online: http://www.ibtimes.com/why-microsoft-sony-couldnt-stop-lizard-squad-attack-despite-warnings-1769174(accessed on 9 January 2020).
- Sicard, S. North Korean Cyber Attack on Sony Poses Tough Security Questions. Natl. Def. 2015, 99, 24–25. [Google Scholar]
- Al-Mahmood, Z.S. Hackers Lurked in Bangladesh Central Bank’s Servers for Weeks. 22 March 2016. The Wall Streel Journal. Economy. Available online: http://www.wsj.com/articles/hackers-in-bangladesh-bank-account-heist-part-of-larger-breach-1458582678 (accessed on 16 January 2019).
- Cheney, S.J. Heartland Payment Systems: Lessons Learned from a Data Breach; Discussion Paper—Payment Cards Center; Federal Reserve Bank of Philadelphia: Philadelphia, PA, USA, 2010. [Google Scholar]
- Cassano-Piché, A.; Vicente, K.J.; Jamieson, G.A. A Sociotechnical Systems Analysis of the Bse Epidemic in the Uk Through Case Study. Proc. Hum. Fact. Ergon. Soc. Annu. Meet. 2006, 50, 386–390. [Google Scholar] [CrossRef] [Green Version]
- Zetter, K. A Cyberattack Has Caused Confirmed Physical Damage for the Second Time Ever. Security, 8 January 2015. Available online: https://www.wired.com/2015/01/german-steel-mill-hack-destruction/(accessed on 21 April 2018).
- Cyber Security Crimes. Types of Cyber Attacks. Available online: www.cybersecuritycrimes.com/types-of-cyber-attacks/ (accessed on 20 February 2017).
- Joubert, V. Five Years after Estonia’s Cyber Attacks: Lessons Learned for NATO? Research Paper; Research Division, NATO Defense College: Rome, Italy, 2012; p. 76. [Google Scholar]
- Nyblom, P.; Wangen, G.; Kianpour, M.; Østby, G. The Root Causes of Compromised Accounts at the University. In Proceedings of the 6th International Conference on Information Systems Security and Privacy, Valletta, Malta, 25–27 February 2020. [Google Scholar]
- Abubakar, A.; Zadeh, P.B.; Janicke, H.; Howley, R. Root cause analysis (rca) as a preliminary tool into the investigation of identity theft. In Proceedings of the Cyber Security and Protection Of Digital Services (Cyber Security), 2016 International Conference, London, UK, 13–14 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–5. [Google Scholar]
- Collmann, J.; Cooper, T. Breaching the security of the Kaiser permanente internet patient portal: The organizational foundations of information security. J. Am. Med. Inf. Assoc. 2007, 14, 239–243. [Google Scholar] [CrossRef] [PubMed]
- Wen, S.F.; Kowalski, S. A Case Study: Heartbleed Vulnerability Management and Swedish Municipalities. Human Aspects of Information Security, Privacy and Trust. In Proceedings of the International Conference on Human Aspects of Information Security, Privacy, and Trust, Vancouver, BC, Canada, 9–14 July 2017; Springer: Cham, Switzerland, 2017; pp. 414–431. [Google Scholar]
- Teradata. Big Data Analytics in Cyber Defense; Ponemon Institute Research Report; Ponemon Institute LLC: Traverse City, MI, USA, 2013. [Google Scholar]
- Allen, M. Social Engineering: A Means to Violate a Computer System; The SANS Institute: Bethesda, MD, USA, 2006. [Google Scholar]
- Al-Shurman, M.; Yoo, S.M.; Park, S. Black Hole Attack in Mobile Ad Hoc Networks. In Proceedings of the ACMSE’04, Huntsville, AL, USA, 2–3 April 2014. [Google Scholar]
- Derbyshire, R.; Green, B.; Prince, D.; Mauthe, A.; Hutchison, D. An Analysis of Cyber Security Attack Taxonomies. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), London, UK, 23–27 April 2018; pp. 153–161. [Google Scholar] [CrossRef]
- Kee, J.; Deterding, B. Social Engineering: Manipulating the Source; SANS Institute InfoSec Reading Room; The SANS Institute: Bethesda, MD, USA, 2008. [Google Scholar]
- Honan, B. Ubiquity Networks Victim of $39 Million Social Engineering Attack. August 2015. CSO from IDG. Available online: http://www.csoonline.com/article/2961066/supply-chain-security/ubiquiti-networks-victim-of-39-million-social-engineering-attack.html (accessed on 19 February 2021).
- Brower, J. Which Disney Princess are YOU? 2010: (Web 2.0) Social Engineering in Social Networks; The SANS Institute: Bethesda, MD, USA, 2010. [Google Scholar]
- Manjak, M. Social Engineering Your Employees to Information Security; SANS Institute InfoSec Reading Room, The SANS Institute: Bethesda, MD, USA, 2006. [Google Scholar]
- King, R. Cyberattackers Target 19,000 French Websites in Wake of Charlie Hebdo. The Wall Street Journal, 15 January 2015. Available online: http://blogs.wsj.com/cio/2015/01/15/cyberattackers-target-19000-french-websites-in-wake-of-charlie-hebdo/(accessed on 23 October 2021).
- Jakobsson, M. The Human Factor in Phishing; School of Informatics, Indiana University at Bloomington: Bloomington, IN, USA, 2007; Available online: https://www.usenix.org/legacy/event/sec07/tech/jakobsson.pdf (accessed on 21 December 2020).
- McMillan, R. Was this the email that took down RSA? A Spear Phishing Email That Has Surfaced in a Security Database Looks Like It may Have Been the One to Hit RSA. IDG News Service, 26 August 2011. Available online: http://www.networkworld.com/article/2180520/malware-cybercrime/was-this-the-email-that-took-down-rsa-.html(accessed on 23 October 2021).
- Anderson, M. How Not to Be Sony Pictures. IEEE Spectrum, 11 December 2014. Available online: http://spectrum.ieee.org/riskfactor/telecom/security/how-not-to-be-sony-pictures(accessed on 29 July 2018).
- Calia, M.P.F. Chang’s Says Data Breach Affected 33 Locations. The Wall Street Journal, 4 August 2014; Tech 1-3. Available online: http://www.wsj.com/articles/p-f-changs-says-data-breach-affected-33-locations-1407159131(accessed on 23 October 2021).
- Schwartz, J.M. Epsilon Fell to Spear-Phishing Attack. Information Week. 2011. Available online: http://www.darkreading.com/attacks-and-breaches/epsilon-fell-to-spear-phishing-attack/d/d-id/1097119? (accessed on 20 March 2019).
- Clayton, M. Exclusive: New Thesis on How Stuxnet Infiltrated Iran Nuclear Facility. 25 February 2014. The Christian Science Monitor. Available online: http://www.csmonitor.com/World/Security-Watch/2014/0225/Exclusive-New-thesis-on-how-Stuxnet-infiltrated-Iran-nuclear-facility (accessed on 23 October 2021).
- Villeneuve, N.; Bennett, J. Detecting APT Activity with Network Traffic Analysis; Trend Micro Incorporated. Research Paper; Trend Micro: Tokyo, Japan, 2012. [Google Scholar]
- Beckerman, J. International Dairy Queen Confirms Data Breach. The Wall Street Journal, 9 October 2014; 7–9. Available online: http://www.wsj.com/articles/international-dairy-queen-confirms-data-breach-1412891919(accessed on 12 June 2019).
- Reuters. Cyber attack could cost Sony studio as much as $100 million. Technology News, 10 December 2014. [Google Scholar]
- Pfleeger, L.S.; Caputo, D.D. Leveraging Behavioral Science to Mitigate Cyber Security Risk. Comput. Secur. 2012, 31. [Google Scholar] [CrossRef]
- Robinson, W.S. Corporate Espionage 201; Version 1.0; SANS Institute InfoSec Reading Room, The SANS Institute: Bethesda, MD, USA, 2007. [Google Scholar]
- Mclean, R. Hospital Pays Bitcoin Ransom after Malware Attack. 2016. CNN Money, New York. Available online: http://money.cnn.com/2016/02/17/technology/hospital-bitcoin-ransom/ (accessed on 23 October 2021).
- Kalige, E.; Burkey, D. A Case Study of Eurograbber: How 36 million Euros was Stolen via Malware. Versafe 2012, 35, 35–36. [Google Scholar]
- Filkins, B. The SANS 2013 Help Desk Security and Privacy Survey; The SANS Institute: Bethesda, MD, USA, 2013. [Google Scholar]
- Hartmann, K.; Steup, C. The Vulnerability of UAVs to Cyber Attacks—An Approach to the Risk Assessment. In Proceedings of the 2013 5th International Conference on Cyber Conflict, Tallinn, Estonia, 4–7 June 2013; NATO CCD COE Publications: Tallinn, Estonia, 2013. [Google Scholar]
- Welch, C. Over 150 Million Breached Records from Adobe Hack Have Surfaced Online. The Verge, 7 November 2013. Available online: http://www.theverge.com/2013/11/7/5078560/over-150-million-breached-records-from-adobe-hack-surface-online(accessed on 1 February 2020).
- Østby, G.; Berg, L.; Kianpour, M.; Katt, B.; Kowalski, S.J. A Socio-Technical Framework to Improve cyber security training: A Work in Progress. CEUR Workshop Proceed. 2019, 1–3. [Google Scholar]
- Kowalski, S.J. The SBC Model as a Conceptual Framework for Reporting IT Crimes. In Proceedings of the IFIP TC9/WG9. 6 Working Conference on Security and Control of Information Technology in Society on Board M/S Illich and Ashore, St. Petersburg, Russia, 12–17 August 1993. [Google Scholar]
- Williams, R. Jennifer Lawrence hack: ICloud security explained. The Telegraph, 1 September 2014. Available online: http://www.telegraph.co.uk/technology/internet-security/11067563/Jennifer-Lawrence-hack-iCloud-security-explained.html(accessed on 17 November 2020).
- Geraci, R. CEOs and Cyber Defense: The New Reality. Bloomberg Business Week, 2–5 November 2015. [Google Scholar]
- Brumfield, B. Study: Hack Attack Aimed at ISIS’ Opposition. 19 December 2014. CNN. Innovations. Available online: http://www.cnn.com/2014/12/19/world/meast/isis-opponents-malware-attack/ (accessed on 23 October 2021).
- Colwill, C. Human factors in information security: The insider threat—Who can you trust these days? Inf. Secur. Tech. Rep. 2010, 14, 1–11. [Google Scholar] [CrossRef]
- Kessler, C.G. Defenses Against Distributed Denial of Service Attacks. In Computer Security Handbook, 4th ed.; Wiley & Sons: Hoboken, NJ, USA, 2000; Available online: http://www.garykessler.net/library/ddos.html (accessed on 7 July 2018).
- Zetter, K. Logic Bomb Set Off South Korea Cyberattack. Cybersecurity Hacks and Cracks, 21 March 2013. Available online: https://www.wired.com/2013/03/logic-bomb-south-korea-attack/(accessed on 25 August 2020).
- Marsan, D.C. 5 things Estonia did right in battling hacktivism: Being open, asking for help keys to snuffing out cyberattacks. Network World, 22 August 2007. Available online: http://www.networkworld.com/article/2294176/lan-wan/5-things-estonia-did-right-in-battling-hacktivism.html(accessed on 23 October 2021).
- Kowalski, S. Do Computer Security Models Model Computer Crime: A Study of Swedish Computer Crime Cases. In Proceedings of the 5th Canadian Computer Security Symposium, Ottawa, ON, Canada, 12–14 May 1993. [Google Scholar]
- Avecto Article. One Big Thing You Can Do to Mitigate Cyber Attacks. 2014. Available online: https://cdn2.hubspot.net/hub/333464/file-603003268-pdf/Avecto/Avecto-Article-Cyber-Security.pdf (accessed on 16 March 2020).
- Bhattacharyya, A.; Banerjee, A.; Bose, D. Different Types of Attacks in Mobile ADHOC Network: Prevention and Mitigation Techniques; Department of Computer Science & Engineering, Institute of Engineering & Management; Saltlake Publisher: Salt Lake City, UT, USA, 2011. [Google Scholar]
- Kraemer, S.; Carayon, P.; Clem, J. Human and organizational factors in computer and information security: Pathways to vulnerabilities. Comput. Secur. 2009, 28, 1–12. [Google Scholar] [CrossRef]
- Chen, W.D. Man Charged with Sabotage of Computers. The NY Times, 18 February 1988; pp. 1–2. Available online: http://www.nytimes.com/1998/02/18/nyregion/man-charged-with-sabotage-of-computers.html(accessed on 23 October 2021).
- Barrett, N. Penetration testing and social engineering: Hacking the weakest link. Inf. Secur. Tech. Rep. 2003, 4, 8. [Google Scholar]
- Orosz, M. Addressing Human Behavior in Cyber Security; USC Information Sciences Institute: Arlington, VA, USA, 2010. [Google Scholar]
- Waxer, C. The Top 5 Internal Security Threats. 2007. IT Security. Available online: http://www.itsecurity.com/features/the-top-5-internal-security-threats-041207/ (accessed on 16 March 2020).
- SecureWorks Dell. Advanced Threat Protection with Dell SecureWorks Security Services; Dell SecureWorks: Atlanta, GA, USA, 2012. [Google Scholar]
- Krombholz, K.; Hobel, H.; Huber, M.; Weippl, E. Social Engineering Attacks on the Knowledge Worker. In Proceedings of the 6th International Conference on Security of Information and Networks, Aksaray, Turkey, 26–28 November 2013. [Google Scholar]
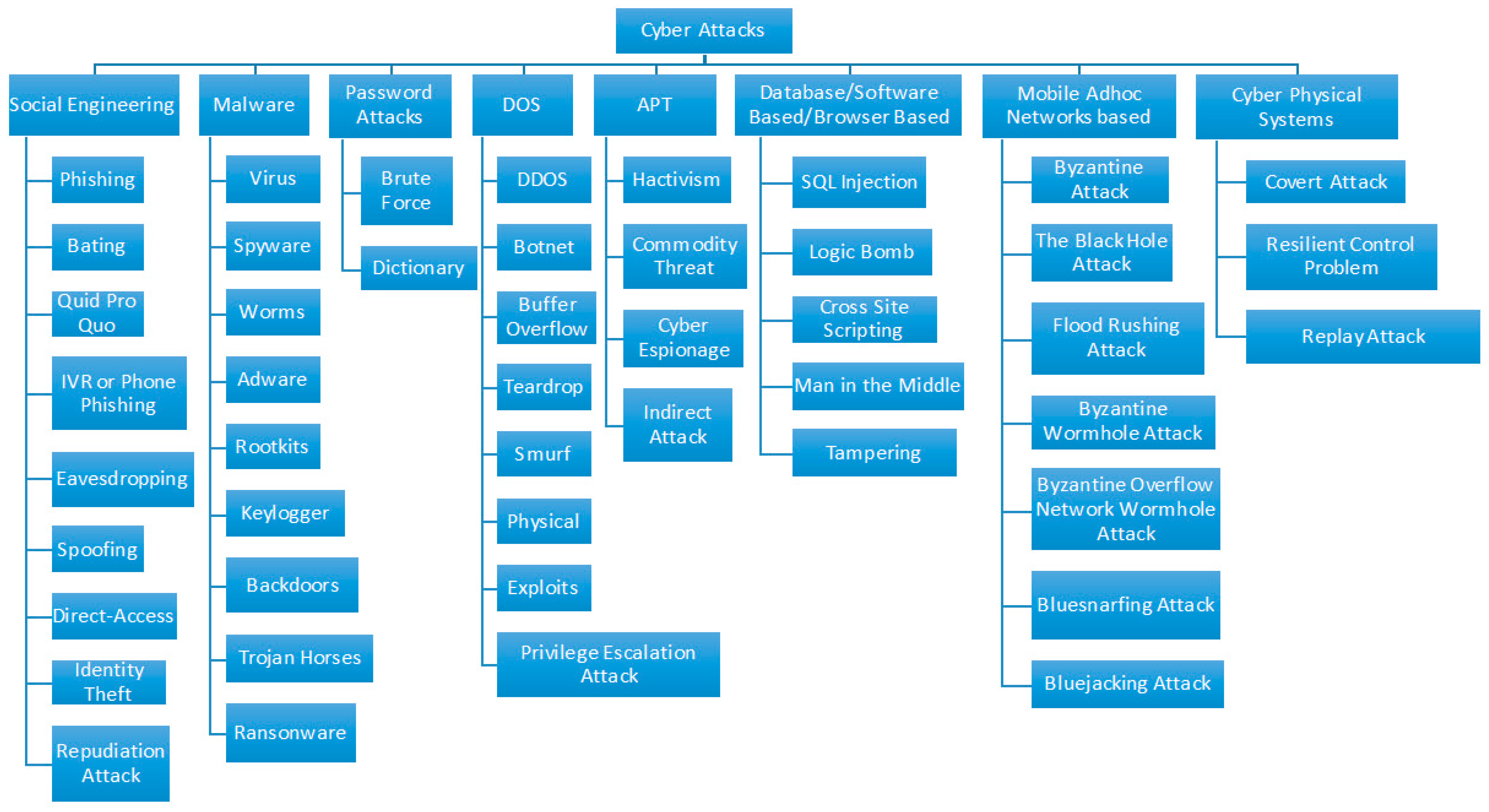
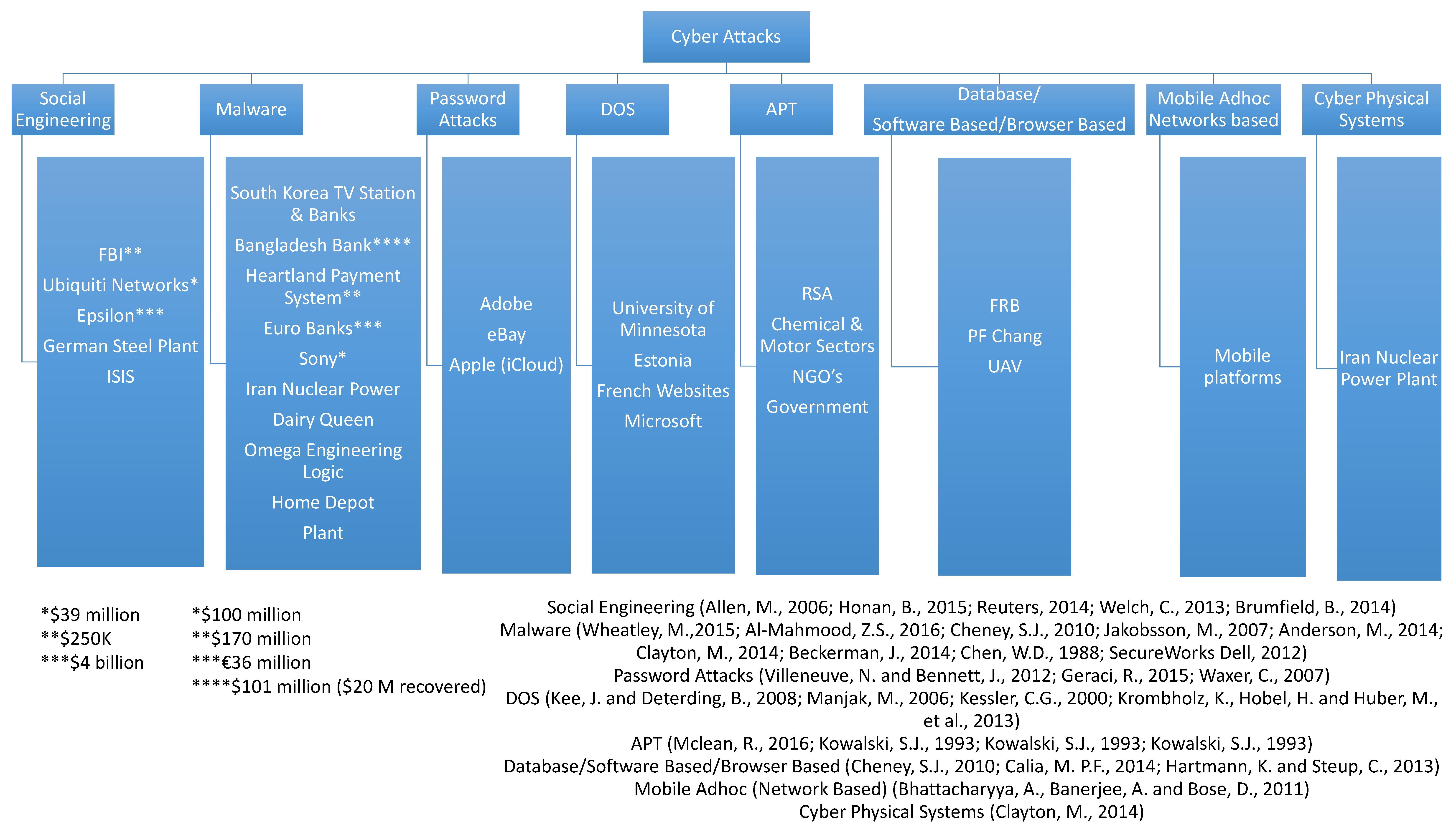
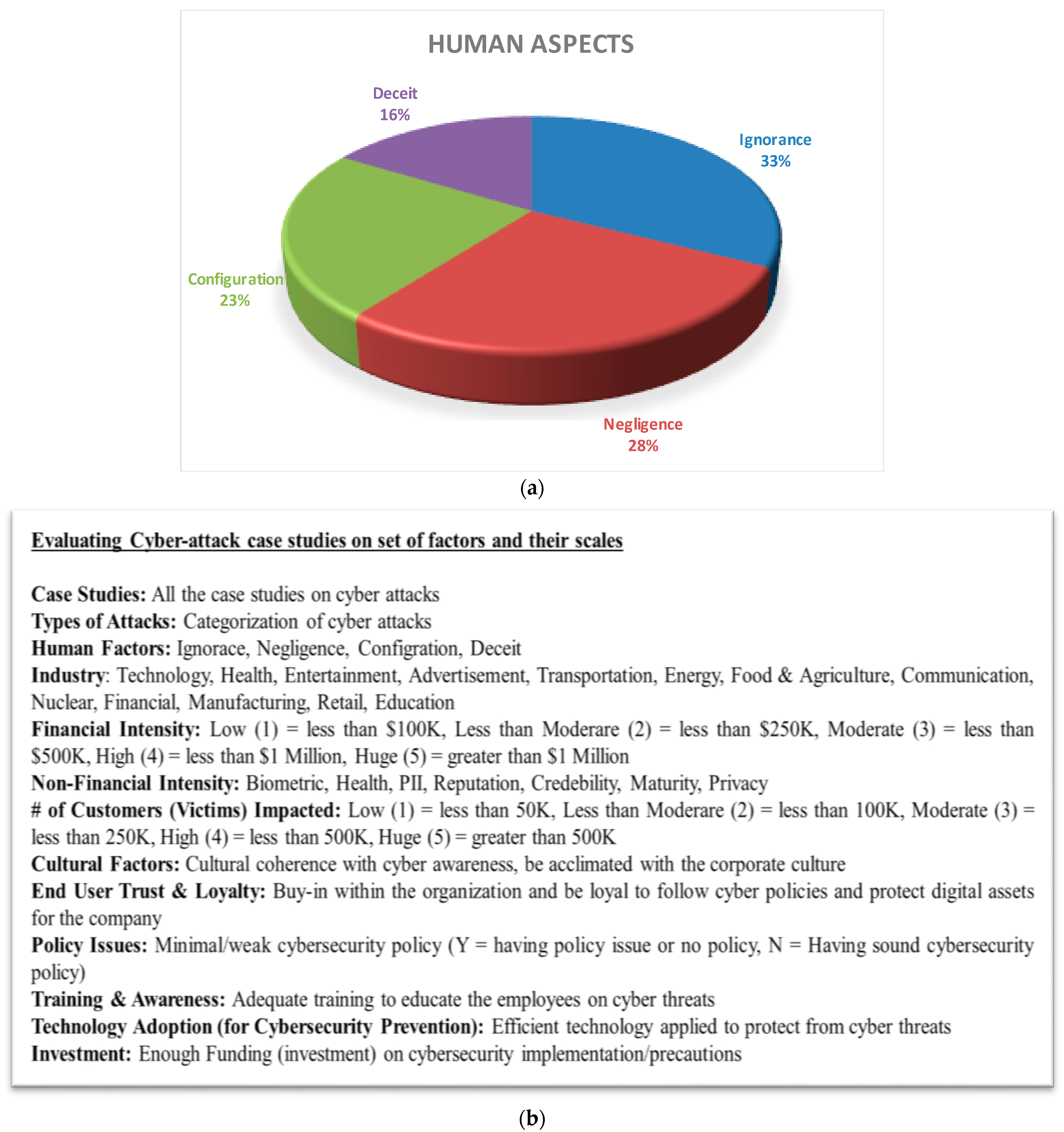
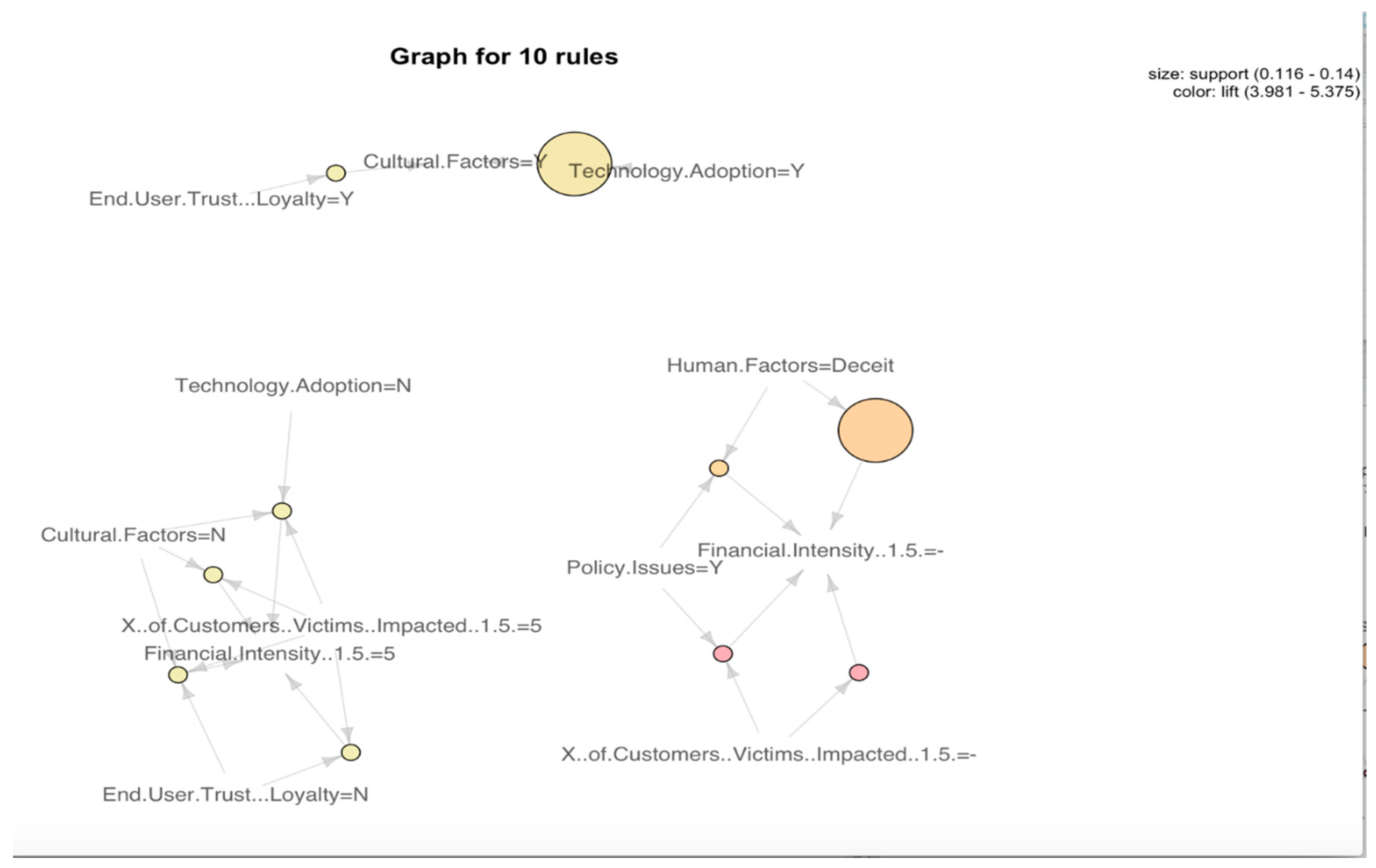
| Physical Intrusion (Security Violation) | Cyber Intrusion (Security Violation) |
|---|---|
| Reason—Greed, Activism, Political, Hurt | Reason—Greed, Activism, Political, Hurt |
| Outcome to victims—Destruction, Financial Loss | Outcome to victims—Destruction, Financial Loss |
| Outcome to attacker—Gain, fulfilling a political or personal agenda | Outcome to attacker—Gain, fulfilling a political or personal agenda |
| Physical | Virtual |
| Attacker—sense of power | Attacker—sense of power, accomplishing a political agenda |
| Likelihood of getting caught is higher | Likelihood of getting caught is lower |
| Mostly Visible | Not always visible—APT (takes long time) |
| Visible breakage | Likely Invisible breakage |
| Protection is by physical security (guard, lock) | Protection is by cyber security (Firewall, password protection) |
| Case Studies | Types of Cyber Attacks | Human Factors | Industry | Financial Intensity (1–5) | Non-Financial Intensity | # of Customers Impacted (1–5) | Cultural Factors | End User Trust & Loyalty | Policy Issues | Training & Awareness | Technology Adoption | Investment |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Stuxnet Cyber Warfare | Malware (Worm) | Ignorance | Nuclear | 5 | Reputation | 4 | Y | N | Y | N | N | Y |
| RSA APT Attack | APT | Ignorance | Technology | 3 | Credibility | 5 | Y | Y | Y | N | N | Y |
| eBay Account Hack | Password Attacks | Ignorance | Technology | 3 | Reputation | 4 | N | N | Y | N | N | N |
| German Steel Plant Attack | Social Engineering | Ignorance | Manufacturing | 3 | Maturity | 3 | N | N | Y | N | N | N |
| Social Engineering Malware Attack (ISIS) | Social Engineering/Malware | Ignorance | Advertisement | 2 | Maturity | 3 | N | N | Y | N | N | N |
| Heartland Payment System Data Breach 2008 | SQL Injection Attack | Ignorance | Financial | 5 | Credibility | 5 | Y | Y | N | N | Y | Y |
| Home Depot Data Access Attack | malware (Worm) | Ignorance | Retail | 5 | Reputation | 5 | N | N | Y | N | N | N |
| UAV (Unmanned Aerial/Air Vehicles) Feed Interception. | Cyber-Physical Attack | Ignorance | Communication | 5 | Maturity | 5 | N | N | Y | N | N | N |
| Trojan Attack | Malware (Worm) | Ignorance | Financial | 4 | Maturity | 4 | N | N | Y | N | N | N |
| South Korea Financial & TV Station cyber-attack—Summer of 2013 | Social Engineering/Malware | Ignorance | Entertainment/Financial | 3 | Reputation | 4 | N | N | Y | N | N | N |
| Botnet Attack | DOS | Ignorance | Technology | 2 | Maturity | 3 | N | N | Y | N | N | N |
| Francophoned | Social Engineering | Ignorance | Financial | 3 | Maturity | 3 | N | N | Y | N | N | N |
| Interactive voice response (IVR) or Phone Phishing | Social Engineering | Ignorance | Financial | 3 | Maturity | 4 | N | N | Y | N | N | N |
| Cross-Site Request Forgery (CSRF) | Browser Based Attack | Ignorance | Advertisement | 2 | Reputation | 3 | N | N | Y | N | N | N |
| Sony—the wiper malware attack in 2014 | Malware (Worm) | Negligence | Entertainment | 5 | Reputation | 5 | N | N | N | Y | N | Y |
| P.F. Chang’s Sales Machine Hacked | Malware | Negligence | Food | 4 | Maturity | 4 | N | N | Y | N | N | N |
| Epsilon data breach attack | Malware | Negligence | Financial | 5 | Reputation | 5 | N | N | Y | N | N | N |
| Omega Engineering Logic Bomb | Software Based Attack | Negligence | Technology | 5 | Credibility | 4 | N | N | Y | N | N | N |
| Living social hack and password hack 2013 | Password Attacks/SQL Injection | Negligence | Communication | 4 | PII | 5 | N | N | Y | N | N | N |
| Stuxnet attack through USB | APT | Negligence | Communication | 3 | Maturity | 3 | N | N | Y | N | N | N |
| Hacktivism–Estonia | DOS | Negligence | Financial/Education | 4 | Reputation | 4 | Y | N | Y | N | Y | N |
| Capture password by brute force | Password Attacks | Negligence | Retail | 3 | Maturity | 3 | N | N | Y | N | N | N |
| TJX Cyber attack: WEP (Wired Equivalent Privacy) attack. | Malware | Negligence | Retail | 5 | PII | 5 | N | N | Y | N | N | N |
| SQL Injection Attack at the Federal Reserve Bank. | Database Attack | Negligence | Financial | 5 | PII | 4 | N | N | Y | Y | N | Y |
| Man in the middle attack | Software/Browser Based Attack | Negligence | Retail | 4 | Maturity | 4 | N | N | Y | N | N | N |
| Tailgating | Social Engineering | Negligence | Retail | 3 | Maturity | 3 | N | N | Y | N | N | N |
| Evernote DDOS Attack | DOS | Configuration | Retail | 4 | Credibility | 3 | N | N | Y | Y | N | N |
| Adobe password breach 2013 | Password Attacks | Configuration | Technology | 4 | Reputation | 4 | Y | N | Y | Y | Y | N |
| Dairy Queen International Data Breach | Malware | Configuration | Food & Agriculture | 4 | PII | 4 | N | N | Y | N | N | N |
| Microsoft DOS Attack | DOS | Configuration | Technology | 3 | Reputation | 5 | Y | Y | N | Y | Y | Y |
| Cyber espionage - Titan Rain Attack | APT | Configuration | Entertainment | 4 | Reputation | 4 | Y | N | Y | Y | N | N |
| Flame Malware Attack | Malware | Configuration | Energy | 4 | Privacy | 3 | N | Y | Y | N | N | N |
| Smurf Attack | DOS | Configuration | Education | 3 | Credibility | 3 | Y | Y | Y | Y | Y | N |
| Logic Bomb Attack in South Korea Banks and broadcasting organizations | Database Attack | Configuration | Financial / Entertainment | 3 | Reputation | 3 | N | N | Y | N | N | N |
| Kerberos Replay Attack | Password Attacks | Configuration | Communication | - | Maturity | - | N | N | Y | - | N | N |
| Cross Site Scripting (XSS) | Browser Based Attack | Configuration | Entertainment | - | Reputation | - | N | N | Y | N | N | N |
| iCloud Account Hack –Password Attack | Social Engineering / Password Attack | Deceit | Technology | - | Reputation | 5 | Y | Y | N | Y | Y | Y |
| DOS Attack and DDOS Attack | DOS | Deceit | Entertainment | - | Reputation | 4 | N | N | Y | N | N | N |
| DDOS–NTP | DOS | Deceit | Retail | - | Credibility | - | N | N | Y | N | N | - |
| Bating | Social Engineering | Deceit | Transportation | 3 | Privacy | 2 | N | N | Y | - | N | N |
| Pretexting | Social Engineering | Deceit | Financial | - | PII | - | N | N | Y | N | Y | Y |
| Quid Pro Quo | Social Engineering | Deceit | Communication | - | Privacy | - | - | - | Y | - | N | N |
| Sybil Attack | Mobile Ad hoc Network Based | Deceit | Retail | - | PII | 4 | N | N | Y | N | N | N |
| Index | Association Rule | Confidence | Lift |
|---|---|---|---|
| 1 | Investment=N ==> Policy Issues=Y | 1.00 | 1.10 |
| 2 | End User Trust & Loyalty=N Investment=N ==> Policy Issues=Y | 1.00 | 1.10 |
| 3 | Technology Adoption=N Investment=N ==> Policy Issues=Y | 1.00 | 1.10 |
| 4 | End User Trust & Loyalty=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 5 | Technology Adoption=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 6 | Cultural Factors=N ==> End User Trust & Loyalty=N | 0.97 | 1.16 |
| 7 | Cultural Factors=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 8 | Cultural Factors=N ==> Technology Adoption=N | 0.97 | 1.16 |
| 9 | End User Trust & Loyalty=N Technology Adoption=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 10 | Training & Awareness=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 11 | Cultural Factors=N Policy Issues=Y ==> End User Trust & Loyalty=N | 0.97 | 1.16 |
| 12 | Cultural Factors=N End User Trust & Loyalty=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 13 | Cultural Factors=N Technology Adoption=N ==> End User Trust & Loyalty=N | 0.97 | 1.16 |
| 14 | Cultural Factors=N End User Trust & Loyalty=N ==> Technology Adoption=N | 0.97 | 1.16 |
| 15 | Cultural Factors=N Technology Adoption=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 16 | Cultural Factors=N Policy Issues=Y ==> Technology Adoption=N | 0.97 | 1.16 |
| 17 | Cultural Factors=N Policy Issues=Y Technology Adoption=N ==> End User Trust & Loyalty=N | 0.97 | 1.16 |
| 18 | Cultural Factors=N End User Trust & Loyalty=N Technology Adoption=N ==> Policy Issues=Y | 0.97 | 1.07 |
| 19 | Cultural Factors=N End User Trust & Loyalty=N Policy Issues=Y ==> Technology Adoption=N | 0.97 | 1.16 |
| 20 | Cultural Factors=N ==> End User Trust & Loyalty=N Policy Issues=Y | 0.94 | 1.15 |
| 21 | End User Trust & Loyalty=N Technology Adoption=N ==> Cultural Factors=N | 0.94 | 1.22 |
| 22 | Cultural Factors=N ==> End User Trust & Loyalty=N Technology Adoption=N | 0.94 | 1.22 |
| 23 | Cultural Factors=N ==> Policy Issues=Y Technology Adoption=N | 0.94 | 1.15 |
| 24 | End User Trust & Loyalty=N Policy Issues=Y Technology Adoption=N ==> Cultural Factors=N | 0.94 | 1.22 |
| 25 | Cultural Factors=N Technology Adoption=N ==> End User Trust & Loyalty=N Policy Issues=Y | 0.94 | 1.15 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Quader, F.; Janeja, V.P. Insights into Organizational Security Readiness: Lessons Learned from Cyber-Attack Case Studies. J. Cybersecur. Priv. 2021, 1, 638-659. https://doi.org/10.3390/jcp1040032
Quader F, Janeja VP. Insights into Organizational Security Readiness: Lessons Learned from Cyber-Attack Case Studies. Journal of Cybersecurity and Privacy. 2021; 1(4):638-659. https://doi.org/10.3390/jcp1040032
Chicago/Turabian StyleQuader, Faisal, and Vandana P. Janeja. 2021. "Insights into Organizational Security Readiness: Lessons Learned from Cyber-Attack Case Studies" Journal of Cybersecurity and Privacy 1, no. 4: 638-659. https://doi.org/10.3390/jcp1040032
APA StyleQuader, F., & Janeja, V. P. (2021). Insights into Organizational Security Readiness: Lessons Learned from Cyber-Attack Case Studies. Journal of Cybersecurity and Privacy, 1(4), 638-659. https://doi.org/10.3390/jcp1040032






