A Systematic Review of Cybersecurity Risks in Higher Education
Abstract
1. Introduction
- What are the key information assets and the associated Key Performance Indicators in HE?
- Which are the most frequent threat events in HE?
- Who are the common threat agents?
- What are the most common vulnerabilities?
- Which are the most common risks?
- Section 2 presents the study context and provides the reader with the background knowledge, properties of the HEI, and previous work within the field.
- Section 3 describes the Comprehensive Literature Review Model approach of this paper.
- Section 4 provides a summary of the included and reviewed literature.
- Section 5 presents the literature review results on the information assets and key performance indicators and answers RQ 1.
- Section 6 presents the results from the literature review on cyber threats events and answers RQ 2.
- Section 7 presents the results from the literature review on threat agents and answers RQ 3.
- Section 8 presents the results from the literature review on vulnerability and answers RQ 4.
- Section 9 presents an analysis of HEI’s cybersecurity risks together with a discussion of consequences as an answer to RQ 5.
- Section 10 discusses the research questions, implications, and potential future work.
- Section 11 concludes the work.
2. Background and Previous Work
2.1. Terms and Definitions
2.2. What Separates HE from Classic Industry?
2.3. Previous Work on Information Security in HE
3. Method
3.1. Exploration Phase
3.1.1. Search Terms and Strategy
- For researching assets: Information assets or KPI and higher education or university or academia or education sector
- For researching threats: Cyber or Information and Threats or Threat intelligence and higher education or university or academia or education sector and breach
- For researching vulnerabilities: Vulnerabilities or Vulnerability and higher education or university or academia or education sector
- For researching risk: Cyber or Cyber attacks or Information and Security risk or risk and higher education or university or academia or education sector
3.1.2. Inclusion and Exclusion Criteria
- Academic studies that describe information security risk assessment or management in HE.
- Academic studies of either assets, KPI, threats, vulnerabilities, or risk in HE.
- White papers, technical reports, thesis, or websites dedicated to either topic. For these sources:
- Literature not written in either English or Norwegian
- Studies published in the year 2000 or older.
- We have restricted the inclusion of reports from security vendors to those either containing empirical data sorted on HE or containing expert insights.
- We have not included news reports and articles.
3.2. Interpretation Phase
3.3. Communication Phase
4. Description of Included Literature
4.1. Included Academic Literature
4.2. MODES
5. Assets in HE
5.1. Research Information and Data
5.2. Student and Employee Personal Identifiable Information (PII)
5.3. Student Records
5.4. Learning, Teaching, and Exam Information
5.5. Financial Management Data
5.6. Infrastructure, Computing Power and Resources
5.7. User and Administrator Accounts
5.8. Communication Data
5.9. Examining KPIs in HEI
5.10. Critical Information Assets in Higher Education
6. Cyber Threat Events in HE
6.1. University SOC Statistics
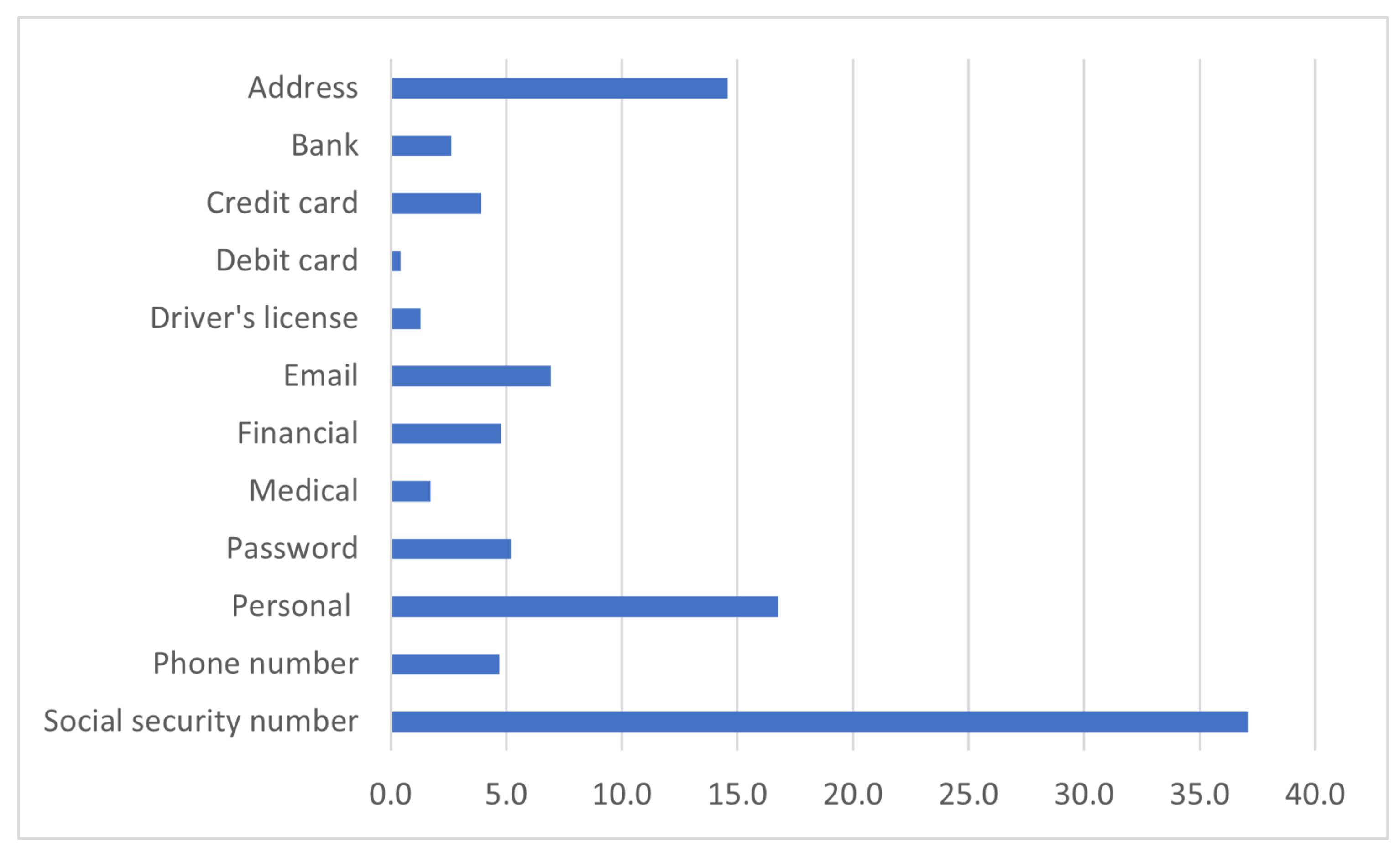
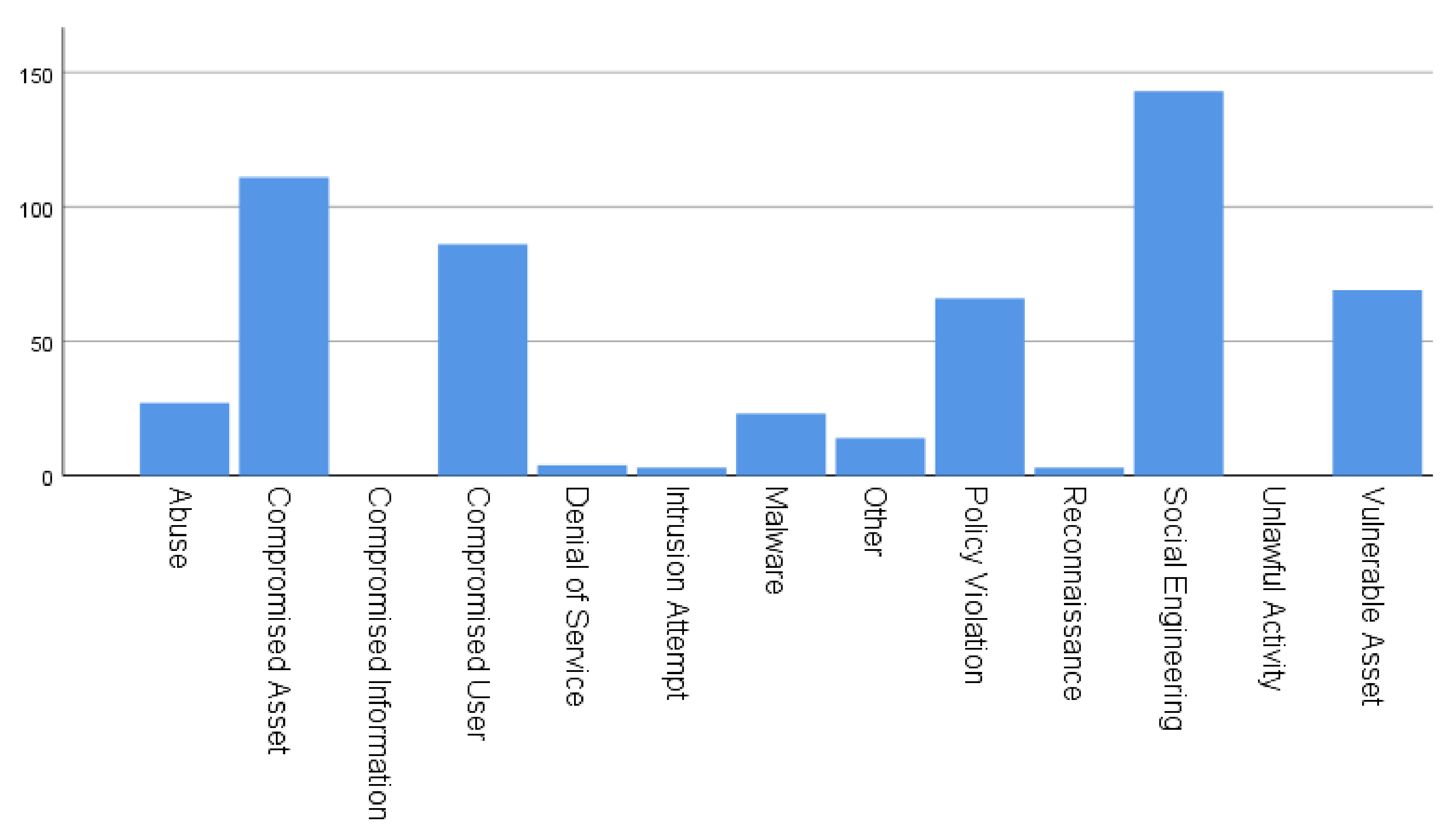
6.2. Publications on Data Breaches and Threat Events
6.3. Threat Event Summary
7. Threat Agents in HE
7.1. Who Targets HEI?
7.2. Cyber-Crime and Enterprise-Like Criminals
7.3. Nation States and Advanced Persistent Threats (APT)
7.4. Human Errors
7.5. Internal and External Opportunists
7.6. Chaotic Actors and Hacktivists
7.7. Insiders
7.8. A Summary of the Threat Agents Facing HE
8. Vulnerabilities in HE
8.1. Administrative and Cultural Vulnerabilities in HE
8.1.1. Information Security Awareness and Knowledge
8.1.2. Insufficient Information Security Management
8.1.3. Insufficient Risk Management and Communication
8.1.4. Missing Management Support, Resources, and Finance
8.1.5. Openness, Attitude and Culture
8.1.6. Password Security
8.2. Technical Vulnerabilities in HE
8.2.1. Bring Your Own Device (BYOD)
8.2.2. Data Acquisition, Storage, Processing, and Transfer
8.2.3. Missing Best Practice Technical Security Controls
8.2.4. Vulnerability Caused by Technical and Network Complexity
8.3. Physical Security in HE
8.4. Summary of the Vulnerabilities in HE
9. Analysis and Discussion of Cyber Risks and Countermeasures in HE
9.1. Risk Analysis
9.2. Data Leaks
9.3. Data Loss
9.4. Financial Fraud
9.5. Loss of Service Availability
9.6. Abuse and Misuse of University Infrastructure and Resources
9.7. Integrity Loss in Key Assets
10. Limitations and Future Work
10.1. Future Work within HE Risk Management
10.2. Critique of Incident Statistics
10.3. Scarcity of Sources
11. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| CERT | Computer Emergency Response Team |
| CLR | Comprehensive Literature Review |
| DoS | Denial of Service |
| GDPR | General Data Protection Regulation |
| HE | Higher Education |
| HEI | Higher Education Institutions |
| infosec | Information security |
| ISMS | Information security management system |
| ISRA | Information Security Risk Analysis/Assessment |
| IT | Information Technology |
| KPI | Key Performance Indicators |
| MODES | Media, Observation(s), Documentation, Expert(s), Secondary Data |
| NCSC | National Cyber Security Centre |
| PII | Personal Identifiable Information |
| PRC | Privacy Rights Center |
| SOC | Security Operations Center |
| STEM | Science, Technology, Engineering, and Mathematics |
| UNIT | The Norwegian Directorate for ICT and joint services in higher education |
| and research | |
| QUT | Queensland University of Technology |
References
- Bongiovanni, I. The least secure places in the universe? A systematic literature review on information security management in higher education. Comput. Secur. 2019, 86, 350–357. [Google Scholar] [CrossRef]
- Ncube, C.; Garrison, C. Lessons learned from university data breaches. Palmetto Bus. Econ. Rev. 2010, 13, 27–37. [Google Scholar]
- FireEye, Inc. Cyber tHreats to the Education Industry. White Paper. Library Catalog, 2016. Available online: www.fireeye.com (accessed on 28 January 2021).
- Yilmaz, R.; Yalman, Y. A Comparative Analysis of University Information Systems within the Scope of the Information Security Risks. TEM J. 2016, 5, 180–191. [Google Scholar]
- FireEye, Inc. Why Cyber Attackers Are Targeting Higher Education, and What Universities Can Do about It. White Paper. Library Catalog, 2015. Available online: www.fireeye.com (accessed on 28 January 2021).
- Unit-Department for ICT and Joint Services in Higher Education and Research. Technical Report. 2019. Available online: https://www.regjeringen.no/contentassets/f464322e9623456dabe220571dfab8f6/unit-okonomiseminar_2019.pdf (accessed on 28 January 2021).
- Adams, A.; Blanford, A. Security and Online Learning: To Protect and Prohibit. In Usability Evaluation Of Online Learning Programs; IGI Global: Hershey, PA, USA, 2003; pp. 331–359. [Google Scholar]
- Chapman, J. How Safe Is Your Data? Cyber-Security in Higher Education. HEPI Policy Note, April 2019. [Google Scholar]
- Wangen, G. Quantifying and Analyzing Information Security Risk from Incident Data; Graphical Models for Security; Albanese, M., Horne, R., Probst, C.W., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 129–154. [Google Scholar]
- NCSC. The Cyber Threat to Universities; Technical Report; UK National Cyber Security Centre: London, UK, 2019.
- ISO/IEC 27002:2013 Information Technology–Security Techniques–Information Security Risk Management; Standard; International Organization for Standardization: Geneva, Switzerland, 2018.
- Wangen, G.; Hallstensen, C.; Snekkenes, E. A framework for estimating information security risk assessment method completeness. Int. J. Inf. Secur. 2017. [Google Scholar] [CrossRef]
- ISO/IEC 27002:2013 Information Technology–Security Techniques–Code of Practice for Information Security Controls; Standard; International Organization for Standardization: Geneva, Switzerland, 2014; Available online: https://www.iso27001security.com/html/27002.html (accessed on 28 January 2021).
- Whitman, M. Management of Information Security; Cengage Learning, Inc.: Boston, MA, USA, 2018; ISBN 9780357691205. [Google Scholar]
- Ahmed, A.E.A.; Badawy, M.; Hefny, H. Exploring and Measuring the Key Performance Indicators in Higher Education Institutions. Int. J. Intell. Comput. Inf. Sci. 2018, 18, 37–47. [Google Scholar]
- Ulven, J. High level information security risk in higher education. Master’s Thesis, Norwegian University of Science and Technology, Trondheim, Norway, 2020. [Google Scholar]
- Peter, S.; Deimann, M. On the role of openness in education: A historical reconstruction. Open Prax. 2013, 5, 7–14. [Google Scholar] [CrossRef]
- Schlagwein, D.; Conboy, K.; Feller, J.; Leimeister, J.M.; Morgan, L. “Openness” with and without Information Technology: A Framework and a Brief History. 2017. Available online: https://journals.sagepub.com/doi/pdf/10.1057/s41265-017-0049-3 (accessed on 28 January 2021).
- Whitman, M.; Mattord, H. Threats to Information Protection-Industry and Academic Perspectives: An annotated bibliography. J. Cybersecur. Educ. Res. Pract. 2016, 2016, 4. [Google Scholar]
- Chen, Y.; He, W. Security risks and protection in online learning: A survey. Int. Rev. Res. Open Distrib. Learn. 2013, 14, 108–127. [Google Scholar] [CrossRef]
- Beaudin, K. The Legal Implications of Storing Student Data: Preparing for and Responding to Data Breaches. New Dir. Institutional Res. 2017, 2016, 37–48. [Google Scholar] [CrossRef]
- Beaudin, K. College and university data breaches: Regulating higher education cybersecurity under state and federal law. J. Coll. Univ. Law 2015, 41, 657–693. [Google Scholar]
- Hussain, H.S.; Din, R.; Khidzir, N.Z.; Daud, K.A.M.; Ahmad, S. Risk and Threat via Online Social Network among Academia at Higher Education. J. Physics: Conf. Ser. 2018, 1018, 012008. [Google Scholar] [CrossRef]
- Ajie, I. A Review of Trends and Issues of Cybersecurity in Academic Libraries. Libr. Philos. Pract. 2019, 1–20. Available online: https://digitalcommons.unl.edu/cgi/viewcontent.cgi?article=5803&context=libphilprac (accessed on 28 January 2021).
- Diaz, A.; Sherman, A.T.; Joshi, A. Phishing in an Academic Community: A Study of User Susceptibility and Behavior. arXiv 2018, arXiv:1811.06078. [Google Scholar] [CrossRef]
- Cuchta, T.; Blackwood, B.; Devine, T.R.; Niichel, R.J.; Daniels, K.M.; Lutjens, C.H.; Maibach, S.; Stephenson, R.J. Human Risk Factors in Cybersecurity. In Proceedings of the 20th Annual SIG Conference on Information Technology Education, Tacoma, WA, USA, 3–5 October 2019; pp. 87–92. [Google Scholar]
- Dadkhah, M.; Borchardt, G.; Maliszewski, T. Fraud in Academic Publishing: Researchers Under Cyber-Attacks. Am. J. Med. 2017, 130, 27–30. [Google Scholar] [CrossRef] [PubMed][Green Version]
- Teixeira da Silva, J.; Alkhatib, A.; Tsigaris, P. Spam emails in academia: Issues and costs. Scientometrics 2020, 122, 1171–1181. [Google Scholar] [CrossRef]
- Wangen, G.; Hellesen, N.; Torres, H.; Brækken, E. An empirical study of root-cause analysis in information security management. In Proceedings of the SECURWARE 2017-The Eleventh International Conference on Emerging Security Information, Systems and Technologies. International Academy, Research and Industry Association (IARIA), Rome, Italy, 10–14 September 2017. [Google Scholar]
- Kashiwazaki, H. Personal Information Leak in a University, and Its Cleanup. In Proceedings of the 2018 ACM SIGUCCS Annual Conference; Association for Computing Machinery: New York, NY, USA, 2018; pp. 43–50. [Google Scholar] [CrossRef]
- Liu, C.W.; Huang, P.; Lucas, H.C. Centralized IT Decision Making and Cybersecurity Breaches: Evidence from U.S. Higher Education Institutions. SSRN Scholarly Paper ID 2850178; Social Science Research Network: Rochester, NY, USA, 2019. [Google Scholar]
- Liu, C.W.; Huang, P.; Lucas, H. IT Centralization, Security Outsourcing, and Cybersecurity Breaches: Evidence from the US Higher Education 2017. Available online: http://penghuang.com/WordPress/wp-content/uploads/2021/01/IT-Centralization-Security-Outsourcing-and-Cybersecurity-Breach.pdf (accessed on 28 January 2021).
- Dar, W.M. Cyber Security Challenges on Academic Institutions and Need For Security Framework Towards Institutional Sustainability Growth and Development. i-Manag. J. Inf. Technol. 2015, 5, 1. [Google Scholar]
- Luker, M.A.; Petersen, R.J. Computer and Network Security in Higher Education; Jossey-Bass: San Francisco, CA, USA, 2003. [Google Scholar]
- Custer, W.L. Information security issues in higher education and institutional research. New Dir. Institutional Res. 2010, 2010, 23–49. [Google Scholar] [CrossRef]
- Onwuegbuzie, A.J.; Frels, R. Seven Steps to a Comprehensive Literature Review: A Multimodal and Cultural Approach; Sage: Thousand Oaks, CA, USA, 2016; pp. 48–64. [Google Scholar]
- Bishop, M. Academia and Education in Information Security Four Years Later. Available online: http://citeseerx.ist.psu.edu/viewdoc/download;jsessionid=E3FBD07A58F3919A670717FF93B9F419?doi=10.1.1.9.5820&rep=rep1&type=pdf (accessed on 28 January 2021).
- Orozova, D.; Kaloyanova, K.; Todorova, M. Introducing Information Security Concepts and Standards in Higher Education. TEM J. 2019, 8, 1017–1024. [Google Scholar]
- Johal, J.; Ward, R.; Gielecki, J.; Walocha, J.; Natsis, K.; Tubbs, R.; Loukas, M. Beware of the Predatory Science Journal: A Potential Threat to the Integrity of Medical Research. Clin. Anat. 2017, 30. [Google Scholar] [CrossRef]
- Ballard, P.J. Measuring Performance Excellence: Key Performance Indicators for Institutions Accepted into the Academic Quality Improvement Program (AQIP). PhD Thesis, Western Michigan University, Kalamazoo, MI, USA, 2013. [Google Scholar]
- Asif, M.; Searcy, C. A composite index for measuring performance in higher education institutions. Int. J. Qual. Reliab. Manag. 2014. Available online: https://www.emerald.com/insight/content/doi/10.1108/IJQRM-02-2013-0023/full/html?fullSc=1&fullSc=1 (accessed on 28 January 2021).
- Pinheiro, J. Review of cyber threats on Educational Institutions. In Proceedings of the Digital Privacy and Security Conference 2020, Porto, Portugal, 15 January 2020; p. 43. [Google Scholar]
- Al-Janabi, S.; AlShourbaji, I. A Study of Cyber Security Awareness in Educational Environment in the Middle East. J. Inf. Knowl. Manag. 2016, 15, 1650007. [Google Scholar] [CrossRef]
- Metalidou, E.; Marinagi, C.; Trivellas, P.; Eberhagen, N.; Giannakopoulos, G.; Skourlas, C. Human factor and information security in higher education. J. Syst. Inf. Technol. 2014, 16, 210–221. [Google Scholar] [CrossRef]
- Nyblom, P.; Wangen, G.B.; Kianpour, M.; Østby, G. The Root Causes of Compromised Accounts at the University. In Proceedings of the 6th International Conference on Information Systems Security and Privacy; SciTePress: Setubal, Portugal, 2020; pp. 540–551. [Google Scholar] [CrossRef]
- Rezgui, Y.; Marks, A. Information security awareness in higher education: An exploratory study. Comput. Secur. 2008, 27, 241–253. [Google Scholar] [CrossRef]
- Ismail, W.; Widyarto, S. A Formulation and development process of information security policy in higher education. In Proceedings of the 1st International Conference on Engineering Technology and Applied Sciences, Afyonkarahisar, Turkey, 21–22 April 2016. [Google Scholar]
- Noghondar, E.R.; Marfurt, K.; Haemmerli, B. The Human Aspect in Data Leakage Prevention in Academia. In ISSE 2012 Securing Electronic Business Processes: Highlights of the Information Security Solutions Europe 2012 Conference; Reimer, H., Pohlmann, N., Schneider, W., Eds.; Springer Fachmedien Wiesbaden: Wiesbaden, Germany, 2012; pp. 137–146. [Google Scholar] [CrossRef]
- Kim, E. Information Security Awareness Status of Business College: Undergraduate Students. Inf. Secur. J. A Glob. Perspect. 2013, 22, 171–179. [Google Scholar] [CrossRef]
- Singar, A.V.; Akhilesh, K. Role of Cyber-security in Higher Education. In Smart Technologies; Springer: Berlin/Heidelberg, Germany, 2020; pp. 249–264. [Google Scholar]
- Kwaa-Aidoo, E.K.; Agbeko, M. An Analysis of Information System Security of a Ghanaian University. Int. J. Inf. Secur. Sci. 2018, 7, 90–99. [Google Scholar]
- Itradat, A.; Sultan, S.; Al-Junaidi, M.; Qaffaf, R.; Mashal, F.; Daas, F. Developing an ISO27001 Information Security Management System for an Educational Institute: Hashemite University as a Case Study. Jordan J. Mech. Ind. Eng. 2014, 8, 102–118. [Google Scholar]
- Mello, S. Data Breaches in Higher Education Institutions. In Honors Theses and Capstones; University of New Hampshire: Durham, NH, USA, 2018. [Google Scholar]
- Fawcett, D. Information Asset Register. 2020. Available online: https://www.qut.edu.au/about/governance-and-policy/information-asset-register (accessed on 1 October 2020).
- Ola, F.R.; Lasse, S.; Sebastian, B.W.; Arne, M.L. Trusselprofilering og Etterretning i åpne kilder. Bachelor’s Thesis, NTNU Open Gjøvik, Trondheim, Sweden, 2018. [Google Scholar]
- Group, C. 2018 Cyberthreat Defense Report. White Paper. Library Catalog, 2018. Available online: https://cyber-edge.com/wp-content/uploads/2018/03/CyberEdge-2018-CDR.pdf (accessed on 28 January 2021).
- Group, C. 2019 Cyberthreat Defense Report. White Paper. Library Catalog, 2019. Available online: https://www.imperva.com/resources/reports/CyberEdge-2019-CDR-Report-v1.1.pdf (accessed on 28 January 2021).
- Wangen, G.; Brodin, E.Ø.; Skari, B.H.; Berglind, C. Unrecorded Security Incidents at NTNU 2018 (Mørketallsundersøkelsen ved NTNU 2018). Bachelor’s Thesis, NTNU Open Gjøvik, Trondheim, Sweden, 2019. [Google Scholar]
- Ellestad, J.N.; Lilja, M.L.; Gustad, A.G.; Skuggerud, E.S. Sikkerhetskultur ved NTNU. Bachelor’s Thesis, NTNU Open Gjøvik, Trondheim, Sweden, 2019. [Google Scholar]
- Grama, J. Just in Time Research: Data Breaches in Higher Education. EDUCAUSE 2014. Available online: https://library.educause.edu/~/media/files/library/2014/5/ecp1402-pdf.pdf (accessed on 28 January 2021).
- Verizon. 2017 Data Breach Investigations Report. White Paper. Library Catalog, 2017. Available online: https://www.ictsecuritymagazine.com/wp-content/uploads/2017-Data-Breach-Investigations-Report.pdf (accessed on 28 January 2021).
- Verizon. 2018 Data Breach Investigations Report. White Paper; 2018; Library Catalog. Available online: https://admin.govexec.com/media/vz_assets/2018_dbir_public_sector_final.pdf (accessed on 28 January 2021).
- Verizon. 2019 Data Breach Investigations Report. White Paper. Library Catalog, 2019. Available online: https://www.key4biz.it/wp-content/uploads/2019/05/2019-data-breach-investigations-report.pdf (accessed on 28 January 2021).
- Verizon. 2020 Data Breach Investigations Report. White Paper. Library Catalog, 2020. Available online: https://itb.dk/wp-content/uploads/2020/07/verizon-data-breach-investigations-report-2020.pdf (accessed on 28 January 2021).
- Hackmageddon. 2018: A Year of Cyber Attacks. Library Catalog, 2019. Available online: www.hackmageddon.com (accessed on 28 January 2021).
- Hackmageddon. 2019 Cyber Attacks Statistics. Library Catalog, 2020. Available online: www.hackmageddon.com (accessed on 28 January 2021).
- James, J.G.; Dominic, A.; Paluzzi, S.A.K. Pass or Fail? Data Privacy and Cybersecurity Risks in Higher Education; White Paper; McDonald Hopkins: Chicago, IL, USA, 2016. [Google Scholar]
- Wangen, G. The Role of Malware in Reported Cyber Espionage: A Review of the Impact and Mechanism. Information 2015, 6, 183–211. [Google Scholar] [CrossRef]
- Potter, B. Practical Threat Modeling. Login 2016, 41, 59–63. Available online: https://www.usenix.org/system/files/login/articles/login_fall16_11_potter.pdf (accessed on 28 January 2021).
- Norwegian Police Security Services (PST). Annual Threat Assessment 2020. White Paper. Library Catalog, 2020. Available online: www.pst.no (accessed on 28 January 2021).
- Compton, Y.R. Obstacles With Data Security: Strategies From Carolina Universities. Ph.D. Thesis, Walden University, Minneapolis, MA, USA, 2020. [Google Scholar]
- Maia, D.V.A. Cyberattacks across academic organisations: Analysis of attacks and guidelines to improve defence. In Proceedings of the 11th International Conference on System Safety and Cyber-Security (SSCS 2016), London, UK, 11–13 October 2016. [Google Scholar] [CrossRef]
| Exploration Phase |
| Step 1: Exploring beliefs and topics Step 2: Initiating the search Step 3: Storing and organizing information Step 4: Selecting/Deselecting information Step 5: Expanding the search to include one or more MODES (Media, Observation(s), Documentation, Expert(s), Secondary Data) |
| Interpretation Phase |
| Step 6: Analyzing and synthesizing information |
| Communication Phase |
| Step 7: Presenting the CLR report |
| Source | Reference | Publication | Topics | Country | Year |
|---|---|---|---|---|---|
| Academic | Ballard [40] | Ph.D. Thesis | Asset/KPI | USA | 2013 |
| Literature | Asif & Searcy [41] | Journal article | Asset/KPI | Saudi-Arabia & Canada | 2013 |
| Ncube & Garrison [2] | Journal article | Threat | USA | 2010 | |
| Pinheiro [42] | Conference article | Threat | Portugal | 2020 | |
| Al-Janabi & AlShourbaji [43] | Journal article | Vulnerability | Middle east | 2016 | |
| Metalidou et al. [44] | Journal article | Vulnerability | Greece | 2014 | |
| Nyblom et al. [45] | Conference article | Vulnerability | Norway | 2020 | |
| Yilmaz & Yalman [4] | Journal article | Vulnerability | Turkey | 2016 | |
| Rezgui & Marks [46] | Journal article | Vulnerability | UAE | 2008 | |
| Ismail & Widyarto [47] | Conference article | Vulnerability | Malaysia | 2016 | |
| Noghondar et al. [48] | Conference article | Vulnerability | Norway & Switzerland | 2012 | |
| Kim [49] | Journal Article | Vulnerability | USA | 2013 | |
| Wangen [9] | Conference article | Risk | Norway | 2019 | |
| Singar & Akhilesh [50] | Book chapter | Risk | India | 2020 | |
| Kwaa-Aido & Agbeko [51] | Journal article | Risk | Ghana | 2018 | |
| Itradat et al. [52] | Journal article | Risk | Kingdom of Jordan | 2014 | |
| Mello [53] | Ph.D. Thesis | Risk | USA | 2018 | |
| MODES | Fawcett. QUT [54] | Website | Asset | Australia | 2020 |
| FireEye Inc. [3] | White paper | Threat | USA | 2016 | |
| Ringdalen et al. [55] | Bachelors thesis | Threat | Norway | 2018 | |
| CyberEdge group [56,57] | White paper | Vulnerability | International | 2018-19 | |
| Wangen et al. [58] | Technical report | Vulnerability | Norway | 2019 | |
| Ellestad et al. [59] | Bachelors thesis | Vulnerability | Norway | 2019 | |
| FireEye Inc. [5] | White paper | Risk | USA | 2015 | |
| Chapman [8] | Policy Note | Risk | UK | 2019 | |
| NCSC [10] | Technical report | Risk | UK | 2019 | |
| Grama [60] | White paper | Risk | USA | 2014 | |
| UNIT [6] | Technical report | Risk | Norway | 2019 | |
| Verizon [61,62,63,64] | Technical report | Risk | USA | 2017-20 | |
| Hackmageddon [65,66] | Website | Risk | International | 2018-19 | |
| Giszczak et al. [67] | White paper | Risk | USA | 2016 |
| Category | Information Assets from Queensland University of Technology |
|---|---|
| Student information | - Personal/sensitive information (e.g., name, e-mail, address) |
| - Admission details | |
| - Class registration information | |
| - Student financial information | |
| - Student results (e.g., exam results) | |
| - Records of student support services | |
| - Student communications platforms | |
| - Study records of course completion and achievements | |
| Learning and teaching | - Curriculum information |
| information | - Information associated with curriculum |
| - Online learning information | |
| - Course information | |
| - Exam information | |
| - Library learning resources | |
| - Meta data about resources | |
| Research information | - Research management data (e.g., resources, |
| business and industry engagement) | |
| - Research results and publications | |
| - Contract management | |
| - Intellectual property (patent) | |
| - Funding information | |
| Facilities management | - Campus infrastructure information |
| information | - Security infrastructure |
| Financial management | - General corporate finance information |
| information | - Management information regarding budget, costing, pricing and report |
| Governance, strategy and | - Committees management data |
| policy information | - Meetings schedules |
| - Legislative documents | |
| - Audit and risk management | |
| - Strategy documents | |
| IT support information | - Communication and collaboration |
| information | |
| - Infrastructure information | |
| - Identity and access information (e.g., username and password) | |
| - Technology procurement information | |
| - Technology support information | |
| Human resources information | - Staff and employee records |
| - Recruitment information | |
| - Records of Health, Safety & Environment | |
| Alumni information | - Records of personal detail |
| - International partner agreement information | |
| - Partnership | |
| Market and Media | - Websites |
| - Market management information | |
| - Intranet | |
| - Social media information |
| KPI | Critical Information Assets | Reference |
|---|---|---|
| Enrollment & Graduation | Student PII and records | [5,6,9,10,40,41,42,50,51,53,54,67] |
| Learning and teaching information | [40,41,50,54] | |
| Financial management information | [5,6,9,40,41,42,50,53,54,67] | |
| Stakeholder satisfaction | Sensitive Research information/data and IP | [5,9,10,40,41,42,50,51,54,67] |
| Government and Third-party data | [5,67] | |
| Employee & HR | Employee & Student PII | [5,9,10,40,41,42,50,51,54,67] |
| Administration details | [40,41,50,51,54,67] | |
| User and administrator accounts | [6,8,9,45,53,58,65,66] | |
| IT Supporting services | Bandwidth and Internet Connection | [6,9,10,51] |
| Computing power and resources | [6,9,10,52] | |
| Communication systems and data | [6,10,52,53] |
| KPI Category in HE | Score by % |
|---|---|
| Graduation measures | 100 |
| Stakeholder satisfaction | 100 |
| Employee & HR | 97 |
| Enrollment | 94 |
| Retention | 94 |
| Financial | 88 |
| Student success | 88 |
| Student engagement | 85 |
| Strategic planning | 82 |
| Admission | 76 |
| Academic Processes | KPI |
|---|---|
| Research performance indicators | Number of research publications |
| Number of research projects | |
| Number of patents | |
| Number of monographs | |
| Number of spin-offs from main research stream | |
| Number of patents addressing local needs | |
| % of faculty winning academic grants | |
| Number of technology projects | |
| Number of research projects addressing local needs | |
| % of faculty attending conferences and seminars | |
| Research impact | |
| Teaching performance indicators | Students and other stakeholder satisfaction |
| Employer satisfaction with graduates skills | |
| Number of students completing the program | |
| Student progression rate | |
| Dropout rate (Number of dropouts/No. of students enrolled) | |
| Median score of students | |
| % of students with a particular GPA | |
| Course rating – median evaluation of the course by students | |
| Graduates employment rate | |
| Service performance indicators | Number of academic programs designed |
| (university, profession, and | Participation in curriculum development |
| community) | Participation in academic committees |
| Students counseling | |
| Community service | |
| Financial performance | Revenues |
| Income generated from research projects | |
| Income generated from consultancies | |
| Income generated from spin-offs/patents | |
| Sponsorship’s/endowments | |
| Income generated from tuition | |
| Expenses | |
| Total teaching and research cost | |
| % of budget allocated to the research |
| Type | 2005 | 2006 | 2007 | 2008 | 2009 | TOTAL |
|---|---|---|---|---|---|---|
| Stolen | 9 | 15 | 16 | 21 | 12 | 73 |
| Hacker | 38 | 20 | 16 | 14 | 22 | 110 |
| Insider | 1 | 1 | 0 | 3 | 1 | 6 |
| Exposed | 5 | 13 | 25 | 28 | 12 | 83 |
| Missing | 1 | 5 | 6 | 6 | 0 | 18 |
| Total | 54 | 54 | 63 | 72 | 47 | 290 |
| Incident | Description | Grama [60] | Mello [53] |
|---|---|---|---|
| Payment Card Fraud (CARD) | Fraud involving debit and credit cards that is not accomplished via hacking | 0% | 0% |
| Unintended disclosure (DISC) | Sensitive information posted publicly on a website, mishandled, or sent to the wrong party via e-mail or other. | 30% | 29% |
| Hacking or malware (HACK) | Electronic entry by an outside party; data loss via malware and spyware. | 36% | 39% |
| Insider (INSD) | Intentional breach of information by someone with legitimate access (e.g., an employee or contractor) | 3% | 3% |
| Physical loss (PHYS) | Lost, discarded, or stolen non electronic records, such as paper documents. | 5% | 5% |
| Portable device (PORT) | Lost, discarded, or stolen portable devices (e.g., laptop, PDA, smartphone, portable memory device, CD) | 17% | 16% |
| Stationary device (STAT) | Lost, discarded, or stolen stationary electronic device such as a computer or server not designed for mobility. | 7% | 6% |
| Unknown or other (UNKN) | Breaches that do not fit into the above categories or where a root cause has not been determined. | 1% | 1% |
| Threat Events (Action) | 2017 | 2018 | 2019 | 2020 | Sum |
|---|---|---|---|---|---|
| Error | 19 | 16 | 37 | 66 | 138 |
| Hacking | 43 | 46 | 42 | 85 | 216 |
| Malware | 26 | 14 | 16 | 39 | 95 |
| Misuse | 5 | 3 | 9 | 7 | 24 |
| Physical | 2 | 8 | 1 | 7 | 18 |
| Social | 32 | 41 | 38 | 61 | 172 |
| Total number of breaches | 127 | 128 | 143 | 265 | 663 |
| Attacks (Threat Events) | 2018 | 2019 |
|---|---|---|
| Malware/PoS Malware | 16 | 71 |
| Account Hijacking | 30 | 26 |
| Unknown | 20 | 20 |
| Targeted Attacks | 4 | 4 |
| Vulnerability | 1 | 2 |
| Brute-Force | 0 | 2 |
| DDoS | 2 | 0 |
| Defacement | 0 | 1 |
| Malicious Script Injection | 0 | 1 |
| Malicious Spam | 0 | 1 |
| SQLi | 1 | 0 |
| Total | 74 | 128 |
| Source | Wangen [9] | Chapman [8] | UNIT [6] | Ncube [2] | Mello [53] | Verizon [61,62,63,64] | Hackmag. [65,66] |
|---|---|---|---|---|---|---|---|
| Coll. Year | 2017 | 2018 | 2018 | 2005–2009 | 2005–2014 | 2017–2020 | 2018–2019 |
| 1 | Soc.Eng. (26%) | Malware | Vuln. assets (70%) | Hacker (38%) | HACK (39%) | Hacking (33%) | Malware (43%) |
| 2 | Comp. asset (20%) | Copyright | Comp. asset (10%) | Exposed (28%) | DISC (29%) | Social (26%) | Account Hij. (27%) |
| 3 | Comp. user (16%) | Compromise | Scanning (10%) | Stolen (25%) | PORT (16%) | Error (21%) | Unknown (19%) |
| 4 | Vuln. asset (12%) | DoS | Comp. system | Missing (6%) | STAT (5%) | Malware (14%) | Targeted Att. (4%) |
| 5 | Copyright (12%) | Unauth. use | DDOS | Insider (2%) | PHYS (5%) | Misuse (4%) | Vulnerability (2%) |
| 6 | Abuse (5%) | Scanning | Spam | INSD (3%) | Physical (3%) | Brute-Force (1%) | |
| 7 | Malware(4%) | Phishing | Query | UNKN (1%) | DDoS (1%) | ||
| 8 | Other (5%) | Other | Other | CARD (0%) | Other (2%) | ||
| n | 550 | ∼6100 | 965 | 290 | 604 | 663 | 202 |
| Threat Agents (Motivation) | 2018 | 2019 |
|---|---|---|
| Cyber Crime | 70 | 122 |
| Cyber Espionage | 3 | 5 |
| Hacktivists | 1 | 1 |
| Total | 74 | 128 |
| Threat | Motivation | Intention | Threat events | Citations |
|---|---|---|---|---|
| Cyber-crime | Financial | Unauthorized access, Deny Access Infrastructure hijack | Malware, Hacking, Social engineering, Abuse, Botnets, Stolen Credentials. Fraud | [2,5,8,9,10,55,61,62,63,64,65,66] |
| State sponsored espionage | Intelligence, Political | Unauthorized access, Data gathering | Sophisticated attacks: Social engineering, Tailored malware, Persistent access, credential harvesting | [5,6,8,9,10,55,58,61,62,63,64,65,66]. |
| Human errors | Carelessness | N/A | Data loss, Data leakage | [2,58,60,61,62,63,64] |
| Opportunists | Self-assertion, Fun | Exploitation, Infrastructure hijack | Hacking, Copyright violations, DDoS | [8,9,55,58] |
| Chaotic actors Hacktivists | Ideology, Political | Damage reputation, Sabotage | DDoS, Spear-phish, Website hacking | [5,55,61,62,63,64,65,66] |
| Insider | Grudge | Sabotage | Rights abuse, Physical destruction, Data leakage, Denial of Service | [2,8,55,60,61,62,63,64] |
| Classification | Description | Citations |
|---|---|---|
| Administrative | Insufficient Security Awareness and knowledge | [4,6,8,9,10,43,44,45,46,50,52,58,61,62,63,64] |
| Insufficient information security management | [1,4,6,8,9,52,58] | |
| Insufficient risk management and communication | [4,5,6,45,52] | |
| Missing management support, resources, and finance | [5,42,47,56,57] | |
| Openness, Attitude and culture | [5,10,45,55] | |
| Password Security | [4,9,10,45,50,58,61,62,63,64] | |
| Technical | Bring your own device (BYOD) | [5,50] |
| Data acquisition, storage, processing, and transfer | [4,5,6,58] | |
| Missing best practice security controls | [4,5,6,9,52,61,62,63,64] | |
| Vulnerability caused by technical and network complexity | [5,6,8,9,10,42,61,62,63,64] | |
| Physical | Physical security in HE | [5,58] |
| Threat Event/Incident | Description | Freq. | % |
|---|---|---|---|
| Intrusion, malware, and compromise | Electronic entry by an outside party; data loss via malware, spyware, and hacking. Also includes compromised asset. | 864 | 29.0 |
| Vulnerable assets and scanning | Organizational property that is vulnerable to external and internal attacks, or adversaries scanning for vulnerabilities. | 852 | 28.6 |
| Social Engineering and targeted attacks | Frauds primarily attempted through phishing scams, targeted attacks, and intrusion attempts towards the organization. | 324 | 10.9 |
| Unintended disclosure and error | Sensitive information posted publicly on a website, mishandled, or sent to the wrong party via e-mail, fax, or mail. | 311 | 10.4 |
| Device or document loss or theft | Lost, discarded, or stolen devices (e.g., laptop, PDA, PC, smartphone, portable memory device, CD, hard drive) or stolen non-electronic records such as paper documents. | 187 | 6.2 |
| Unknown or other | Breaches that do not fit into the other categories or where a root cause has not been determined. | 165 | 5.5 |
| Account hijack/Compromised user | A compromised user is when the username and password of an account get compromised. | 142 | 4.8 |
| Abuse and misuse | Law or policy violations through abuse and misuse of Infrastructure for copyright infringement, illegal hosting, cryptomining, etc. | 117 | 3.9 |
| Insider attacks | Intentional breach of information by someone with legitimate access. | 17 | 0.6 |
| DoS/DDoS | Denial of service (DoS) occurs when a service or asset becomes unavailable. | 6 | 0.2 |
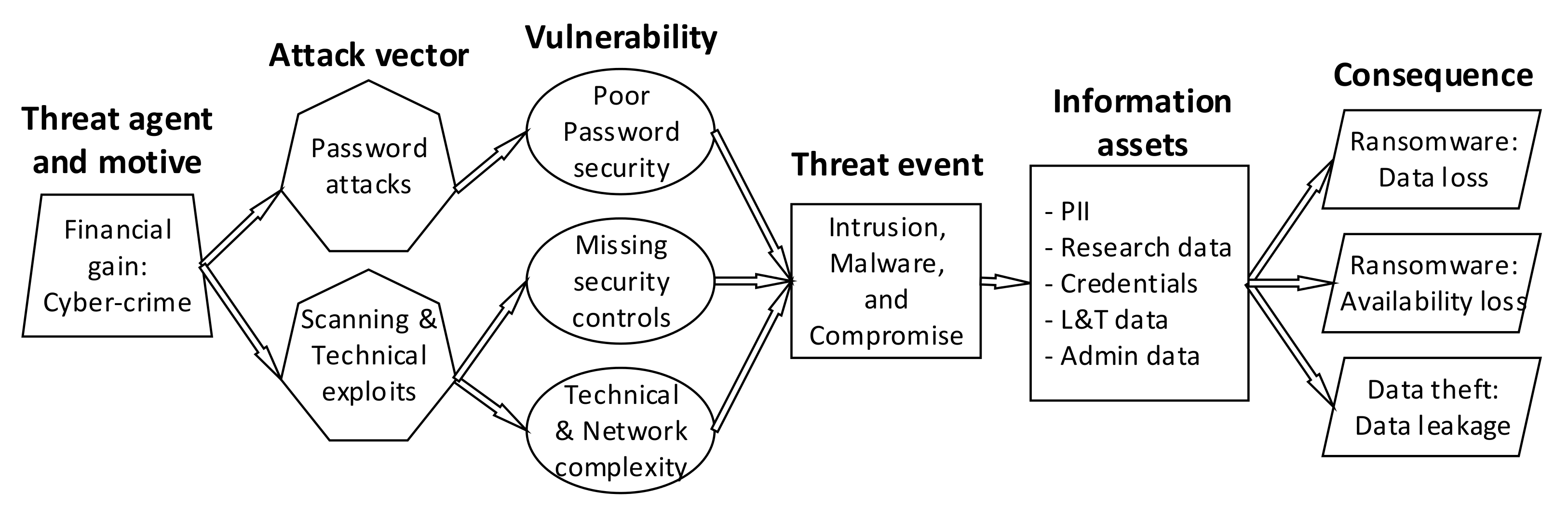
| Threat Event/Incident | Vulnerability | Threat | Asset | Consequence |
|---|---|---|---|---|
| Intrusion, malware, and compromise | Missing security Controls Security awareness Security culture Password security BYOD Missing security controls Complexity | Cyber-crime State sponsored esp. | Info assets. for example: PII Research data Credentials Financial data IT supporting ser.: Bandwidth Comp. resources Comm. systems | Data loss Data leakage Availability |
| Vulnerable assets and scanning | Missing resources and finance Missing security controls Complexity | Cyber-crime State sponsored esp. Opportunists | IT supporting ser.: Bandwidth Comp. resources Comm. systems | Abuse/Misuse Availability loss |
| Social Engineering and targeted attacks | Security awareness Security Culture Missing security controls | Cyber-crime State sponsored esp. | Info assets, for example: PII Research data Credentials Financial data | Fraud Data leakage |
| Unintended disclosure and error | Security awareness Insufficient security management Security culture Data acquisition, storage, processing, transfer | Human errors | Info assets | Data leakage Integrity loss Availability loss |
| Device or document loss or theft | Insufficient security management Physical security in HE | Human errors Criminals Opportunists | Physical devices Physical Documents | Hardware loss Data loss |
| Account hijack Compromised user | Security awareness Password security | Cyber-crime State sponsored esp. | Credentials | Data leakage Data loss Abuse/Misuse |
| Abuse and misuse | Insufficient security management Security culture Missing security controls | Opportunists Insiders | IT resources, for example: Bandwidth Comp. power Hosting Subscriptions | Abuse/Misuse Availability loss |
| Insider attacks | Insufficient security management Missing security controls | Insiders | Info assets IT resources | Data leakage Data loss Integrity loss Availability loss |
| DoS/DDoS | Insufficient security management Missing resources and finance Missing security controls Complexity | Cyber-crime Opportunists Hacktivists | IT resources | Availability loss |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ulven, J.B.; Wangen, G. A Systematic Review of Cybersecurity Risks in Higher Education. Future Internet 2021, 13, 39. https://doi.org/10.3390/fi13020039
Ulven JB, Wangen G. A Systematic Review of Cybersecurity Risks in Higher Education. Future Internet. 2021; 13(2):39. https://doi.org/10.3390/fi13020039
Chicago/Turabian StyleUlven, Joachim Bjørge, and Gaute Wangen. 2021. "A Systematic Review of Cybersecurity Risks in Higher Education" Future Internet 13, no. 2: 39. https://doi.org/10.3390/fi13020039
APA StyleUlven, J. B., & Wangen, G. (2021). A Systematic Review of Cybersecurity Risks in Higher Education. Future Internet, 13(2), 39. https://doi.org/10.3390/fi13020039






