Secure and Privacy-Aware Blockchain Design: Requirements, Challenges and Solutions
Abstract
:1. Introduction
1.1. Paper Position
1.2. Contribution
- We provide detailed background knowledge of blockchain design, and discuss the development of blockchain implementations.
- We identify blockchain requirements in terms of privacy and security, and we present several mechanisms to meet them.
- We propose a classification of current attacks and matching countermeasures.
- We provide a critical comparative analysis of the state of the art privacy and security defense mechanisms to highlight their corresponding advantages and drawbacks.
- We present step-by-step recommendations to provide understanding of the mechanisms and we then discuss current trends based on our study and suggest future work to improve privacy and security management for blockchain.
2. Blockchain: Background Knowledge
2.1. Overview of Blockchain Technology
2.2. Structure of Blockchain
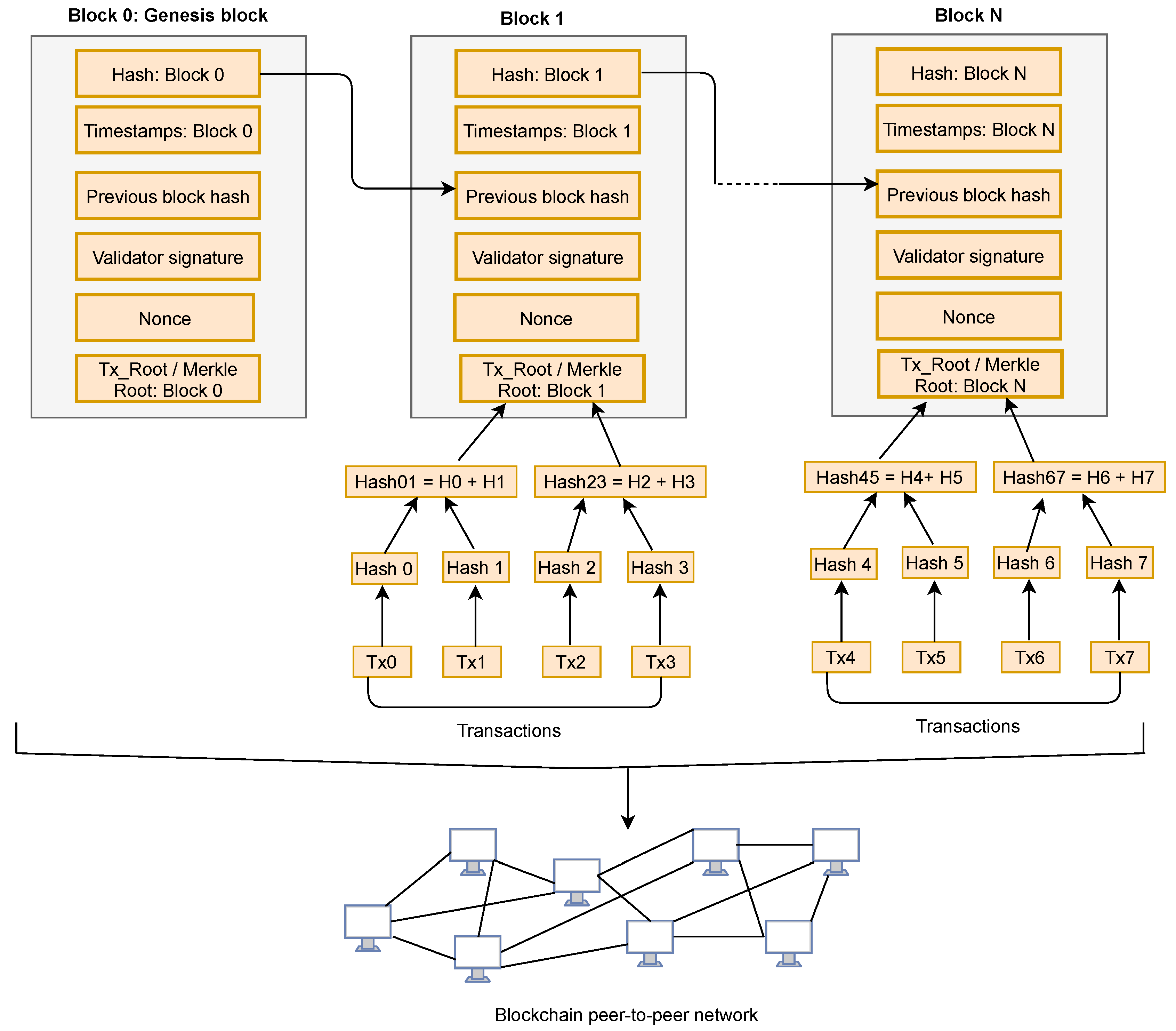
- Block: In blockchain, verified transactions are stored in a block. Any node in a blockchain system can initiate a transaction and send a copy to other available nodes on the network. When network nodes verify that all stored transactions in the block are valid, the next step is to add a block to the blockchain. Each block contains certain information such as transaction time, number of occurred transactions, etc. Each block is linked to the hash of the previous block via a hash function ( Hash functions such as MD5 and SHA-256 transform an input message into a fixed size value called a hash, making it impossible to go back to the original text, but possible to check that a copy is exact by comparing generated hashes [17]) to ensure immutability. A unique hash code is then assigned to each block which is generated by the hash function and differentiates a current block from other blocks.
- Merkle tree: It is defined as a binary search tree in which tree nodes are linked to each other using hash pointers. The blockchain transactions are arranged in a Merkle tree structure. The hashes of all nodes are combined to create the Merkle tree [18], in which each two child nodes are combined together into one node called parent node as shown in Figure 1. This process is repeated from down to top to reach the root of the tree. The root of the Merkle tree verifies all the transactions in the block. An advantage of Merkle tree is that it allows us to prove both the integrity and validity of data. If an adversary attempts to change the transaction then it is needed to change all the subsequent block hashes.
- Digital signature: It ensures the data validity by using a cryptographic algorithm. The digital signature scheme is comprised of three components. The first component is a key generation algorithm, which generates a key pair known as a private key and public key. The private key is kept secret and is used to sign a message, whereas the public key is available to the public and is used to verify the message whether the message has been signed with the corresponding private key. Second component is a signing algorithm, which uses the given private key to creates a signature on the input message. The third component is a verification algorithm, that takes three parameters as input, such as signature, a message, public key and validates the message signature by using the public key. The advantage of using a digital signature is to prevent non-repudiation so participants on the blockchain network cannot deny their own activities.
2.3. Development of Blockchain Implementations
- First generation: digital currency. The first generation of blockchain is a decentralized digital currency (e.g., bitcoin or digital coin) that allows participants to make transactions directly without the involvement of a centralized party [19]. The first blockchain generation solved major issues to create decentralized currency, this generation mainly relied on proof of work consensus algorithm. The main advantages of this generation are to provide decentralized storage, to enable nodes to share data directly, and to ensure transparency during transaction processing [20]. The main drawbacks are related to the energy consumption of consensus algorithms and the fact that proof-of-work gives rewards to the participants who already have the most computation power, which can be a security issue.
- Second generation: smart contracts. The concept of smart contract was proposed to support the self-execution of programs that execute when specific terms are met [22]. The smart contract code is stored on a public ledger and cannot be changed. The transactions that occur in a smart contract are run by the blockchain without a third party. A contract is comprised of three main parts: a unique contract address to identify them on the blockchain, private storage and amount of balance (for example, Ethereum the first implementation to provide smart contracts uses the Ether cryptocurrency). A smart contract can be written in high-level languages, for example, Ethereum uses the Solidity programming language, which can compile into low-level bytecode for the Ethereum virtual machine (EVM) code [23]. Smart contracts guarantee tamper-proof fraud prevention and reduce verification costs. It is important to highlight that some blockchain implementations do not fully, or at all, implement a smart contract. However, this second-generation still remains limited in terms of performance and scalability, as witnesses, for example, the low number to process transactions per second [21].
- Third generation: scalability. The third generation of blockchain focuses on improving the scalability identified in previous generations. Most limitations relate to mining delay, energy consumption, low number of transactions, mostly related to the use of proof of work type of consensus and application of smart contracts. We have also observed a growth in the number and variety of applications, such as e-Health [24] and supply chain management systems [25]. For example, the third generation of blockchain platforms includes Dfinity [26] and NEO [27], that aim at supporting different programming languages and the development of mobile-based applications [20].
- Consortium blockchain: is known as federated or public permission blockchain, which allows only a group of organizations to verify and add data to the blockchain. It can be an open ledger or restricted to a particular group. R3 and Corda are consortium blockchain [32].
3. Privacy and Security Requirements for Blockchain
- Transaction data protection: The transaction contents (payload) recorded on the distributed ledger (such as healthcare or business data) and the transaction itself (e.g., transaction time and amount, etc.) may need to be protected from unauthorized disclosure. Indeed, such information may be sensitive, especially for companies with public records that can be matched and that may not want to disclose their transactions on the blockchain.
- User identity protection: As mentioned above, the structure of transactions establishes a direct link to the involved users through asymmetric cryptography (if one finds out who a public key belongs to). Typically, blockchain users may want to protect the link between their identity and the transactions they perform, thus making identity protection a major issue for blockchain.
- Security properties: Typical data security properties are required: confidentiality to protect from unauthorized data access, integrity to make sure the contents are the original ones, availability as data should be accessible upon request and non-repudiation as recorded data cannot be denied. By definition, blockchain implementations must provide such properties, therefore, the challenge is to make sure that additional measures dealing with other requirements do not break any of those properties.
- Avoiding TTP: The centralized ledgers of current transaction systems (e.g., banks) are subject to the single-point of failure vulnerability, so they can be more easily compromised than decentralized solutions. As Blockchain helps to eliminate TTPs, additional solutions that answer privacy and security problems should avoid relying on TTPs as well. Unfortunately, it is still common practice to rely on TTPs [36].
- Blockchain support: While our research approaches blockchain from a theoretical perspective, it is important to look at existing blockchain implementations that show the feasibility of those theoretical advances. Therefore, we show in Table 1 how the studied privacy and security mechanisms are supported with blockchain implementations.
| Mechanism | Requirements | ||||
|---|---|---|---|---|---|
| Identity Protection | Transaction Data Protection | Security Properties | Avoiding TTP | Blockchain Support | |
| Ring Signatures | Yes [4,37,38] | Yes [39] | Confidentiality [4,37,38] | No [37] Yes [4,38] | Monero BC [39] |
| Zero-Knowledge proof | Yes [3,5] | Yes [5] | Integrity [40]; Authentication [3] | No [3,40] | Bitcoin and Ethereum [5] |
| Mix Network | No | Yes [41] | Integrity; Authentication [1,41] | Yes [1] | Bitcoin [1] |
| Onion and Tor Routing | Yes [42,43,44] | Yes [43,44] | Integrity [42,44] | No | Loki Blockchain [42] |
| K-anonymity | Yes [45] | No [46] | Integrity [47] | Yes [45] | N/A |
| L-diversity | Yes [48] | No [49] | Confidentiality [50,51] | Yes [48] | N/A |
| T-closeness | Yes [52] | Yes [52] | N/A | Yes [52] | N/A |
| Identity-based Encryption | Yes [53,54,55] | Yes [53,54] | Integrity [55] | Yes [53,55] | Bitcoin and Namecoin [55] |
| Attribute-based Encryption | No | Yes [56,57] | Confidentiality [56] | Yes Multiple parties to generate public/private keys [56] | Private [56] |
| Symmetric key Cryptography (DES, AES, Blowfish, RC5 etc) | Yes [58] | Yes [58,59] | Integrity [58] Confidentiality Non-repudiation [59] | No | Bitcoin [58,59] |
| Asymmetric key Cryptography (Elgamal, RSA, DSA, Elliptic curve, etc.) | Yes [60] | Yes [60,61] | Authentication [60,61]; Confidentiality [61] | Server to manage user identity and password [61] | Permissioned BC [61] |
| Homomorphic Encryption | No | Yes [62,63] | Confidentiality [62,63] | Yes [63] | Bitcoin [62] |
| Hash Function (MD5, SHA-1) | Yes [64] | Yes [64] | Integrity; Confidentiality [64] | No | Bitcoin [64] |
4. Attacks and Countermeasures
- Network attacks, and therefore network security, have been historically existing since the beginning of distributed computing. Network security is typically defined as a subcategory of security [74], and as such network security attacks and countermeasures apply to blockchain implementations as well. Typical countermeasures include designing secure protocols, applying symmetric/asymmetric encryption, filtering and monitoring networks.
- Blockchain attacks specifically exploit weaknesses in the blockchain operation to be successful. Typical countermeasures involve integrating secure protocols and algorithms into the blockchain operation and extending the original blockchain design.
- Privacy attacks exploit available privacy-sensitive data to disclose additional information. Typical countermeasures rely on generating fake transactions (e.g., mixins in Monero) and use statistical models to disable data exploitation.
4.1. Network Attacks and Countermeasures
- IP spoofing attack: In which an attacker uses (or spoofs) someone else’s identity and communicates with this identity to get benefits from it [75].
- Countermeasures: Typically, it is possible to prevent such attacks by filtering network traffic in order to stop the delivery of spoofing packets. In [76], routing-based mechanisms are discussed to deal with IP spoofing attacks. These solutions are implemented by routers or end-hosts.
- Message modification attack: A malicious user modifies the contents of a message being transmitted [75].
- Countermeasures: To deal with message modification attack, using a hash function is a typical solution [77].
- Message forgery attack: The goal of this attack is to create false information on the network. Sending a spam email by using the identity (e.g., name or email address) of another entity is an example of this attack [75].
- Countermeasures: Cryptographic mechanisms such as asymmetric key cryptography can be used to mitigate a message forgery attack. Sender and receiver have their own public and private key pair to encrypt and decrypt the message [78]. It ensures that the receiver receives the original message and proves the identity of the sender.
- (Distributed) Denial-of-Service (DoS) attack: The adversary sends enough traffic so that the target is unable to process it and remains unavailable to legit users. Distributed denial-of-service (DDoS) is a distributed version of the DoS attack, where multiple nodes are orchestrated to attack the target simultaneously [6].
- Countermeasures: In [79], the authors discuss some prevention techniques against DDoS attack. It includes an intrusion prevention mechanism to disable unused network services which are not needed, install security patches to the host machine to prevent vulnerabilities in the system, use firewalls, and dynamically switch the IP address of the active server within a pool of other servers.
- Man-in-the-middle (MITM) attack: An attacker intercepts communication and acts on behalf of one end to collect valuable data [80].
- Countermeasures: One proposed solution to avoid man-in-the-middle attacks is to monitor the network using an intrusion detection system. It observes the behavior of an attacker and gives an alert if an attacker tries to take control of network traffic [81].
- Time delay attack: The goal of this attack is to slow down the network traffic. An attacker tries to control the network traffic, which leads to the delay in the transmission of message [82]. Delay attack can be categorized in the following two attacks: BGP hijacking and Liveness attack.
- Countermeasures: To prevent time delay attack, Arman et al. [83], proposed a method to track and estimate the time delay during communication on the network. If the measured time delay is more than the allowed time delay, then the system issue an alarm signal to stable the system. It is a simple and inexpensive way to secure the system from time delay attacks.
- -
- Border gateway protocol hijacking (BGP) attack: BGP is a routing protocol of the Internet. It helps to forward IP packets to their destination. The attacker conducts BGP hijacking to control the network traffic on the blockchain, which leads to delay of network messages [84].
- -
- Countermeasures: Xing et al. [85], proposed BGPcoin based on Ethereum blockchain, a BGP framework that is generated by a smart contract in the network Ethereum. It provides a transparent allocation of sources (e.g., IP prefixes). It also checks source assignments using blockchain to enhance system security.
- -
- Liveness attack: This attack [86] causes the delay of target transaction time on blockchain. It works in three phases, such as (1) attack preparation phase, in which the attacker creates a private chain longer than the public chain, (2) in-transaction denial phase, where the attacker tries to privately keep the block that contains target transaction, (3) in-blockchain phase, where the attacker will integrate their private blocks into the public chain to slow down the growth rate of the public chain.
- -
- Countermeasures: To resolve the liveness attack Chenxing et al. [87] proposed the conflux consensus protocol that allows fast confirmation and ensures the consensus progress. It is a secure, scalable, and decentralized blockchain platform.
- Traffic analysis attack: An adversary tries to observe the communication route between the sender and receiver. The goal of this attack is to analyze the network communication and from this analysis gather useful information to execute an attack [88].
- Countermeasures: Onion routing provides a solution to traffic analysis as it allows to transfer data from a source through multiple onion routers before the data reaches its destination, thus guaranteeing anonymity. Each message has various layers of encryption, where each layer links to one onion router. It prevents the attacker to identify the endpoints of communication [89].
- Eavesdropping attack: The aim of this attack is to listen to private information over the network [90].
- Countermeasures: Cryptographic techniques such as symmetric key encryption can be used to protect confidential communication against eavesdropping attack. It limits data access only to the authorized user [91].
4.2. Blockchain Attacks and Countermeasures
- Malleability attack: It consists of changing the unique ID of a transaction before confirmation on the network, so an attacker may pretend that a transaction did not occur [92]. This attack was successfully executed on many blockchains due to the nature of the ECDSA digital signature scheme. Suppose Alice sends a payment transaction to Bob with a . Before the transaction is accepted into a block, the is changed to . Bob receives the payment regardless but now Alice not knowing about the change, cannot know if Bob received the funds. This way Bob can ask Alice to resend the funds until eventually, Alice notices. The vulnerability has gained a lot of attention once it was cited by Mt Gox exchange as a key reason for suspending withdrawals.
- Countermeasures: Malleability can rarely be exploited to the attacker’s benefit. At present, it is more of a theoretical problem than a real one as the attacker stands very little to gain. The threat is addressed on the application layer with wallet software not trusting zero-confirmation transactions by either displaying them as pending or not at all. Additionally, changing a transaction ID is not trivial especially now that users’ digital signatures are properly checked by clients in most protocols [93]. However, with the influx of new blockchain implementation it is important to be aware of the potential threat.
- Nothing at Stake Problem: Proof of stake-based blockchains require staked nodes to attest, validate, and verify blocks. Attestations are used to decide, which of the two conflicting blocks is accepted. Proof of stake nodes can collude to vote on conflicting chains. Once their private chain gains more attestations for a series of blocks, they can attempt to convince the rest of the network to fork, and accept their version of the chain. In a proof of stake setting, this is referred to as voting on conflicting blocks. These issues stem from the so-called Nothing-at-Stake problem [15]. A node that receives two conflicting blocks must vote and decide which one to accept. It is always in the node’s best interest to vote for both blocks to earn the reward for contributing to the consensus, whichever block is accepted.
- Countermeasures: To mitigate this problem, proof of stake-based consensus mechanisms introduce game theoretical concepts that penalize any nodes that are discovered to vote on conflicting blocks. The state of the art protocols such as Casper [94], and GHOST [95] or recently a combination of both [96] propose modified fork-choice rules and block finalization protocols. Casper, for example, requires validators to be bonded i.e. to commit Ether to a smart contract. Validator sets continuously get randomly shuffled. Withdrawing their bond would take a long time (months). It creates a long time window within which other votes will be collected. This allows for a long enough period where the validators bond can be destroyed (called slashing in Casper) by another validator set once all votes are collected.
- Majority attack A malicious actor tries to obtain a majority representation in the network to compromise the blockchain either on the consensus level, or the network level. On the consensus level, this can lead to a double-spending attack [97] (described below). The severity of this attack largely depends on the network. In proof-of-work-based blockchain, this can lead to a double-spend using a selfish mining attack. The malicious party submits a large payment transaction, and in return receives goods or services. The transaction is confirmed on the public chain. Once the goods/services are received, the malicious party reconnects their network to the public chain, and propagates their version of the blockchain. Their version of the chain will be longer due to higher hash-rate, forcing the public chain to revert a few blocks, reverting also, the payment transaction. The extent of the thread largely depends on the underlying protocol, its consensus algorithm, and its fault tolerance.
- Countermeasures: In [97], a merged mining technique is developed to protect against majority attack, in which, two different crypto-coins are combined to be mined at the same time. This technique enhances security, because miners contribute to the hash-rate of both crypto-currencies and miners can mine multiple blocks simultaneously. However, this process is complex and merged crypto-currencies must rely on the same hashing algorithm.
- -
- Selfish mining attack: Also known as block withholding attack, occurs when attacker keeps track of their own private chain, separate from the public chain [98]. The attacker mines on the private chain and keeps private blocks, then use the majority attack. This attack is mostly applicable to Proof of Work blockchains if a malicious actor is able to sustain majority mining power for more than one block. Upon reconnecting with the public network, they would have mined more blocks, forcing the rest of the network to accept the longer chain. Transactions on the public network would hence be reversed, potentially opening the door to a double-spend attack. In proof of the stake-based consensus algorithm, this idea applies. However, the condition is different as the malicious party needs to control the majority of validator nodes. They then vote for both the blocks on the public network and the private network. However, proof of stake chains can mitigate this by finalizing blocks, and not simply following the “longest chain wins” rule of the Nakamoto consensus.
- -
- Countermeasures: To resolve selfish mining attacks Siamak et al. [99] proposed Zeroblock mechanism, in which, if a block does not generate within fixed interval time, then this block will be rejected by all other miners. However, maintaining time synchronization is not trivial. The problem becomes much harder when nodes display byzantine behavior. Blockchains with PoS consensus mechanisms rely on different fork choice rules, and block finality protocols to prevent large forks such as Casper FFG [94].
- -
- Eclipse attack: In which an adversary tries to control the incoming and outgoing connection of a node and mining power in the network. It allows an attacker to manipulate the information, and hence nodes operation and launch an attack [100]. The attacker runs a modified version of the protocol on multiple instances in an attempt to convince one or multiple nodes to connect to his malicious nodes. Once the attacked nodes only maintain connections to nodes operated by the attacker, the nodes are eclipsed from the rest of the network. The attacker can arbitrarily filter the message passing possibly even censoring transactions from eclipsed nodes. The most recent successful attack was on the Monero network [101], where the attackers ran multiple nodes by renting cloud instances. They exploited the network code that favored outgoing connections to nodes running behind the same IP address. This allowed the attacker to gain network share by eclipsing honest nodes with malicious ones. The attack ended after a few weeks with a fix of the P2P code in Monero.
- -
- Countermeasures: In paper [100], proposed solutions to mitigate eclipse attack is to use a white-list (e.g., known miners) and disable incoming connections in the network. It prevents new nodes to join the network. Another paper [102], proposed a mechanism against eclipse attack. The basic idea behind this mechanism is to bind the incoming and outgoing connections of the overlay network and allow a node to choose neighbors based on performance metrics. This countermeasure is effective because it is difficult for an attacker to control the nodes in the network.
- -
- Sybil attack: the attacker tries to control the peer network by participating with multiple identities. It tries to gain the majority of influence on the network [8]. In the context of blockchains, this attack is applicable in a proof-of-stake setting. All proof of work-based consensus protocols relies on voting schemes to decide the fork choice rule. With the majority of the consensus nodes, an attacker can win the vote for invalid blocks. However, due to staking requirements, the attack is rarely feasible. On the one hand, should such an attack be successful, all trust in the chain would be lost, and the value of the attacker’s staked coins would drop drastically. On the other hand, the investment needed to acquire such a large influence is usually too high.
- -
- Countermeasures: To prevent Sybil attack George et al. [103], proposed Xim, a two-party mixing protocol that is compatible with bitcoin and virtual crypto-currencies. It is a decentralized system that allows participants to find partners anonymously to hide coin exchange by mixing. It does not rely on TTP to choose partners for mixing, and enhances security because the malicious user cannot identify the evidence of participants that mix up.
- Double spending attack: It consists of spending digital currency more than once. This is what blockchain primarily solves, however an attacker may replicate a digital coin and use it in another transaction [92].
- Countermeasures: To prevent the double-spending attack Hyunjae et al. [104] proposed a recipient-oriented transaction method based on a private blockchain. The proposed mechanism ensures the privacy of recipients and mixes the incoming transactions to protect them from attackers. However, in public permission-less networks, double-spends are only possible by exploiting the consensus algorithm. It allows the transaction’s receiver to verify the validity of transactions before adding them to the block. The actual attack vector varies depending on the type of consensus mechanism.
- Malicious smart contract: It facilitates, for instance, leakage of privacy-sensitive information (e.g., email address into a smart contract is publicly visible) and password theft (e.g., a fair exchange between two parties can only be done after receiving a valid password) [105]. In [106], the authors explain the example of password theft. Dealing with malicious smart contracts remains an open research problem.
- Countermeasures: Slither is a fast and reliable security mechanism to detect bugs in a smart contract. The main objective of this mechanism is to understand code and detect vulnerability automatically [107]. In [108], the authors proposed the SmartCheck vulnerability analysis framework to protect the code of solidity smart contracts. It helps to identify the vulnerabilities in smart contracts and the reason of these vulnerabilities with recommendations. Ahmed et al. [34], proposed the Hawk framework, based on zero-knowledge proofs to enforce transactional privacy in a smart contract. It allows a user to write a private smart contract and does not store transactions publicly on blockchain.
- -
- Distributed autonomous organizations (DAO) attack: It occurs with the help of a malicious smart contract on Ethereum. In this way, the attacker injects some malicious functions in the smart contract, such as withdraw function, call send to Ether and steal all the Ethers from DAO [109].
- -
- Countermeasures: As DAO attack exploits calling a reentrant function in the smart contract execution, its solution consists in making sure that the code of the smart contract is not callable in such a way [110].
- -
- Wallet theft attack: Usually, the user’s private keys are generated and maintained by the user with the help of wallets. In paper [111], authors claim that ECDSA (Elliptic Curve Digital Signature Algorithm) scheme does not maintain user’s privacy because it is unable to create enough randomness during the signature process, through which an attacker can steal the user’s private key.
- -
- Countermeasures: To deal with wallet theft attack Weiqi et al. [112] proposed to use the Trust zone mechanism present on ARM processors that creates a secure execution environment (SEE) to guarantee a safe and reliable environment for the execution of sensitive processes. This is realized with non-maskable interrupts (NMI) and guarantees complete isolation from the operating system, using a secure memory zone and storage to protect user’s private key, wallet’s address, and transaction verification process.
- Blockchain Poisoning: It is an attempt to store illegal files (e.g., malware, malicious content, and privacy information, etc.) in the free space for smart contracts of blockchain. A malicious user can force blockchain nodes to download malicious files which leads to other attacks in the blockchain such as DoS (see Section 4.1). Another kind of poisoning consists of spamming many transactions and indexing the outputs so when those outputs are used as decoys on other transactions, one can consider them decoys and increase the odds of tracing the real outputs, leading to the statistical modeling attack [113].
- Countermeasures: blockchain poisoning attack can be prevented by introducing a minimal fee determined by its resemblance with existing contracts in which the minimal fee reduces if the number of similar contracts increases. The idea is to calculate the fee of all contracts which are used on blockchain and it becomes higher if there is no similar contract. In this approach, the cost to send a transaction relies on the number of similar contracts. Because the number of malicious smart contracts related to falsified transactions is small in the blockchain, then, a malicious user would need to pay a higher fee, which reduces the likelihood of such an attack to occur [113].
4.3. Privacy Attacks and Countermeasures
- Homogeneity attack and background knowledge attack: Homogeneity attack discloses privacy-sensitive information and breaks privacy when all values of a quasi-identifier attribute (e.g., zip code, date of birth, and gender) are similar in a given table [114]. Background knowledge attack occurs when an adversary has a background knowledge of a quasi-identifier to reveal the user’s sensitive attributes [67].
- Countermeasures: K-anonymity is based on quasi-identifier attributes to hide user’s identity in a dataset [45] by providing at least k identical records in the data set for each quasi-identifier attribute. Thus, even if an attacker accesses the data set, he could not identify the real identity of a person due to a similar record in the data set. However, background knowledge attacks can still link outside information to disclose sensitive information.L-diversity extends k-anonymity to prevent homogeneity attack and background knowledge attack as it normalizes data distribution. It improves the diversity of user’s sensitive information in the data set to achieve higher privacy. It ensures data privacy without disclosure of sensitive attributes. However, it is vulnerable to skewness and similarity attacks [67].
- Skewness attack and similarity attack: Skewness attack occurs when the values in the table have a non-uniform distribution, a malicious user obtains a sensitive value based on its higher frequency distribution over a subset of the data [115]. A similarity attack happens when the values of sensitive attributes are distinct but semantically similar, and the attacker uses the meaning of data to infer missing information [49].
- Countermeasures: The t-closeness approach [49] improves privacy by integrating k-anonymity and l-diversity. It provides protection against sensitive attribute disclosure. This approach works properly if the distance between two distributions in the table should not more than the given threshold value. It does not work properly if the distribution of sensitive values in a class is not close to the distribution of sensitive values in the overall dataset.
- Statistical modeling: Such attacks are specific to blockchain implementations that use decoys to prevent transaction identification, such as Monero. Statistical modeling, coupled with a heuristic approach for decoy elimination is believed to be the attack vector CipherTrace is using to attempt to trace Monero transactions at the time of writing [116]. The accuracy of such models can be increased significantly when coupled with other privacy attacks such as blockchain poisoning.
- Countermeasures: Statistical modeling can be prevented with binned mixin sampling, which changes the current mixin sampling process. The idea is to combine outputs into groups of some fixed size in the Monero blockchain, called bins. Each input transaction is referencing an output transaction in a bin, either as a mixin or spend. It estimates the real spend-time distribution, and then sample mixins according to this distribution. It helps to prevent the traceability of transaction input and disclosure of mixin sampling distribution [117].

5. Evaluation and Discussion
5.1. Comparative Analysis
| Mechanism | Complexity | Scalable | Size Overhead | High Memory Cost | Efficiency | Computation Overhead | Communication Overhead | High Latency |
|---|---|---|---|---|---|---|---|---|
| Ring Signature | Low [4,37,38] | No | O(n) ring signature grows linear with group size [4,37,38,39] | No [4,37,38] | Yes [4,37,38] | - High [4] - O (n + 1) n is group size of ring signature [129,130] - O(n) [38] | N/A | No |
| Zero Knowledge Proof | High [118] | Yes [119] | Low [5] | Yes [5] | No [5] | Expensive [5] | N/A | Yes [5] |
| Mix Network | O(snN) s is length of plain text parallel to input [41] | Yes [1] | O(n) Input entities is linear to mix servers [41] | Yes [1] | yes [41] | O(N + n) All inputs [41] | N/A | Yes [1] |
| Tor Routing | Low [44] | No | Low [44] | No [44] | Yes [44] | Low [44] | N/A | Low [44] |
| Onion Routing | Low [42,43] | Yes [42] | High [42] | Yes [42] | Yes [42] | High [42] | Yes [42] | High [43] |
| K-anonymity | Very low [68] | Yes [120] | Low [121] | No [121] | No [122] | Low [121] | N/A | No [121] |
| L-diversity | Low [68] | Yes [123] | Low [123] | Low [122] | No [122] | Low [123] | N/A | No |
| T-closeness | Very high [68] | No [68] | Low [52] | Low [52] | Yes [52] | Low [52] | N/A | No [131] |
| Identity-based Encryption (session key, and encapsulation algorithm) | Low [53] | No | - O(n) public-key size and encryption time grows linearly [53] - n-bits messages [54] | Yes [55] | Yes [53,54] | weak [53,54] | N/A | No |
| Attribute-based Encryption (bilinear Diffie-Hellman) | High [57] | Yes [125] | Low [57] | No [57,125] | Yes [124,125] | High [125] | High [125] | No |
| Symmetric key Cryptography (DES, AES, RC5 etc) | Low [58] | Yes [59] | Low [72] | Yes [58] | Yes [58] | Low [132] | Yes [58,59] | Yes [58] |
| Asymmetric key Cryptography (Elgamal, RSA, DSA, etc.) | High [127] | Yes [61] | High [133] | High [61,128] | Yes [60,128] | High [127] | Yes [134] | No [134] |
| Homomorphic Encryption | Low [62] | No | Low [62] | No [62] | Yes [62,63] | Low [62] | Low [62] | No |
| Hash Function (MD5, SHA-1) | O(N), N is a size of data [135] | No | High [136] | Yes [136] | Yes [135] | Low [136] | N/A | No |
| Privacy and Security Mechanisms | Advantages | Limitations | Attack Risks |
|---|---|---|---|
| Ring Signature | Flexible, Efficient; Does not depend on TTP. | Computational infeasible; Could not identify actual signer of transaction. | Attribution attack. |
| Zero Knowledge Proof | Protect identity and transaction data. | Efficiency; Need high computational time; Size of proofs. | One user pretends to be another. |
| Mix Network | Efficient; Difficult for an attacker to trace communication. | Require TTP as mixing server. | Active attack; Sleeper attack. |
| Onion Routing | Enforce security on data. | High communication overhead. | Replay attack. |
| Tor Routing | Efficient; Protect user’s identity online. | Does not ensure data security; Slow network speed. | Attack on client through internet browser and external software e.g., Flash etc |
| K-Anonymity | Ensure identity privacy; Easy to understand. | It does not prevent attribute disclosure; Attacks are possible; Re-identification is possible. | Homogeneity attack; Background knowledge attack. |
| l-Diversity | Ensure privacy of user attributes. | Does not prevent data against the attacks; In-efficient; Attribute disclosure can be possible. | Skewness attack; Similarity attack. |
| T-closeness | Protect data privacy | Difficult to identify the closeness between the knowledge gained and t-value by using Earth Mover’s Distance(EMD) | Linkability risk is possible to link external data to the equivalence areas |
| Symmetric Key Cryptography | Re-identification of message is not possible; Authorized user has access to data; Fast; Easy to use. | Difficult to manage multiple keys; Require secure platform to share secret keys. | Re-identification of key from plain text; Recover plain text from cipher text. |
| Asymmetric Key Cryptography | Ensures data confidentiality. | Slow; Does not provide data integrity. | Possible to crack private keys; Brute force attack. |
| Hash Function | Flexible; Easy to use. | Not effective on small scale dataset; High computation cost; In-efficient. | Collision attack; Brute force attack. |
| Homomorphic Encryption | No one can read or modify data; Prevention of active and passive attacks. | Slow. | Heuristic attack. |
5.2. Current Recommendations and Research Directions
5.2.1. Current Recommendations
- Ring signature we consider ring signature to be efficient for identity protection, because of its lower complexity than zero-knowledge proof. However, it is not as scalable as other mechanisms. While scalability can be moderated by creating several rings with a manageable number of participants, key management remains a central problem for ring signature.
- Zero-knowledge proof has higher memory cost and complexity as compared to ring signature. It is mostly considered as a solution to identity management where identity attributes need to be proven without revealing the actual identity. In such a case, it is considered relevant to prevent identity/transaction data disclosure. Despite their higher cost, zero-knowledge-proof constructions are currently the most suitable to address both privacy, and scalability. We conclude that ZKPs can be used to provide anonymous transactions such as Monero [39]. However, they can also be used as a scaling mechanism, where transactions can be batched off-chain, and verified on-chain in blockchain platforms with Turing-complete smart contracts. Presently, the use of ZKPs is limited by the time complexity of constructing proofs, and the lack of protocols that enable trust-less setup [138] with the exception of STARKs [40].
- Mix network is efficient to randomize the order of input data and it is scalable as compared to other available solutions. However, mixed networks require TTPs to shuffle transaction data [1] which is a major drawback in our context.
- Identity-based encryption is better to prevent users’ identity disclosure because of its low complexity and computation overhead as compared to attribute-based encryption. However, it is not scalable and has a higher memory overhead than other available solutions.
- Attribute-based encryption mechanism is good to enforce confidentiality on data and fulfills transaction data protection requirements without latency. It works efficiently because it has lower data size overhead and memory cost than identity-based encryption and onion routing mechanisms.
- Symmetric key cryptography is relatively fast for large amounts of data because of its low computation overhead as compared to asymmetric key cryptography. In symmetric key cryptography, keys can be developed and exchanged between two parties through cryptographic algorithms (e.g Diffie-hellman key exchange).
- Asymmetric key cryptography is easy to use due to separate public and private keys, however, it has high computation overhead as compared to symmetric key cryptography.
- Homomorphic encryption is considered less complex and efficient due to its low memory cost as compared to ZKPs, onion routing, and symmetric key cryptography [62]. Advances in cryptography are consistently being integrated to possibly overcome security and privacy issues. Homomorphic encryption is well-positioned to address most privacy concerns. However, the lack of practical, scalable, and audited implementations is hindering integration.
- Hash function is good to fulfill identity and transaction data protection requirements without an intermediate party, because it has lower computation overhead without latency. It generates a unique signature of fixed size from variable-size data input and it is useful to assess the integrity of data during data exchange. It is very widely used for data integrity verification.
5.2.2. Research Directions
- Key management: As it is the case with ring signature, most solutions today rely on asymmetric cryptography. Therefore, a pair of public/private is required for each involved actor. Key management is an issue that needs to be mitigated as a large-scale adoption of developed solutions would need to handle very large numbers of key pairs, including the important constraint that the private key must not be disclosed.
- Energy consumption of consensus protocols: Blockchain consensus protocols consume a lot of computing resources, especially the ones based on proof-of-work, which leads to low-system throughput and high system latency. Designing a better consensus mechanism to improve system throughput is challenging due to the algorithmic complexity involved.
- Security and consensus protocols: As detailed in Section 4 a good part of security issues related to consensus protocols, such as proof of work, proof of stake, and delegated proof of stake. While consensus mechanisms also have their own challenges in terms of computational cost, they are also central from a security perspective. One possible option in this direction is to constrain the longest chain rule to alleviate majority attacks, which remains an open problem [97].
- Privacy: On most public blockchains, transaction data is verified and stored on every node due to its decentralized nature and security concerns. It increases the chances of misuses of the user identities and transaction data. As stated in [34], blockchain does not guarantee transaction and user’s identity privacy since all data on the blockchain is publicly available. A lot of work as been ongoing to integrate solutions for privacy protection into the blockchain, a good example of implementation being Monero. Further work is required to protect anonymity at the level of transaction contents, blockchain, history of added blocks, and even blockchain access, so that data read and write accesses becomes totally protected from monitoring attacks. It is noticeable that this problem spreads across the OSI model layers, as identifiers also relate to the network and data link layers (IP and MAC addresses), therefore a well-designed solution should make sure that all layers are covered. The ability to perform computation on encrypted data will arguably have enormous implications on privacy, security, and scalability. Therefore, future research on homomorphic encryption should be aimed not only at mathematical constructions but also audited implementations. The ability to verify, and process transactions without revealing the data will be the key enabler technology for the future development of DLT.
- Storage cost: Due to the decentralized nature of blockchain, data is copied on every node in the network. Therefore, it imposes a huge cost due to the ever-increasing size of the chain. Building storage-wise lightweight blockchain solutions still remains an open challenge. One direction to explore in this domain is the study of multiple subsets with data intersections, where replication would occur on relevant data subsets while maintaining the security properties that make the blockchain interesting. Local network structures could serve as filters in such setup, guaranteeing that majority attacks could not occur within one particular network by preventing external participants to contribute. At the higher level, a decentralized marketplace of micro-currencies would guarantee global communication, maybe using a central blockchain as we know them now to store the history of the different subsets.
- Blockchain vulnerabilities: Consensus mechanisms are arguably the biggest security risk. Different consensus mechanisms are available, each with different properties and trade-offs between scalability, security, and decentralization. Secure mechanisms like proof of work have issues with scalability, whereas scalable consensus mechanisms like proof of stake, have issues with security and decentralization [139]. Efficient mechanisms yet require guaranteeing the privacy of transactions and protect against attacks such as double-spending.
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zheng, Z.; Xie, S.; Dai, H.; Chen, X.; Wang, H. An overview of blockchain technology: Architecture, consensus, and future trends. In Proceedings of the 2017 IEEE International Congress on Big Data (BigData Congress), Honolulu, HI, USA, 25–30 June 2017; pp. 557–564. [Google Scholar]
- Bonneau, J.; Narayanan, A.; Miller, A.; Clark, J.; Kroll, J.A.; Felten, E.W. Mixcoin: Anonymity for bitcoin with accountable mixes. In Proceedings of the International Conference on Financial Cryptography and Data Security, Christ Church, Barbados, 3–7 March 2014; pp. 486–504. [Google Scholar]
- Lu, L.; Han, J.; Hu, L.; Huai, J.; Liu, Y.; Ni, L.M. Pseudo trust: Zero-knowledge based authentication in anonymous peer-to-peer protocols. In Proceedings of the 2007 IEEE International Parallel and Distributed Processing Symposium, Long Beach, CA, USA, 26–30 March 2007; pp. 1–10. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Tauman, Y. How to leak a secret. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Gold Coast, Australia, 9–13 December 2001; pp. 552–565. [Google Scholar]
- Bernabe, J.B.; Canovas, J.L.; Hernandez-Ramos, J.L.; Moreno, R.T.; Skarmeta, A. Privacy-preserving solutions for Blockchain: Review and challenges. IEEE Access 2019, 7, 164908–164940. [Google Scholar] [CrossRef]
- Conti, M.; Kumar, E.S.; Lal, C.; Ruj, S. A survey on security and privacy issues of bitcoin. IEEE Commun. Surv. Tutor. 2018, 20, 3416–3452. [Google Scholar] [CrossRef] [Green Version]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2019. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 March 2021).
- Feng, Q.; He, D.; Zeadally, S.; Khan, M.K.; Kumar, N. A survey on privacy protection in blockchain system. J. Netw. Comput. Appl. 2019, 126, 45–58. [Google Scholar] [CrossRef]
- Zhang, R.; Xue, R.; Liu, L. Security and privacy on blockchain. ACM Comput. Surv. (CSUR) 2019, 52, 1–34. [Google Scholar] [CrossRef] [Green Version]
- Halpin, H.; Piekarska, M. Introduction to Security and Privacy on the Blockchain. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 1–3. [Google Scholar]
- Chen, H.; Pendleton, M.; Njilla, L.; Xu, S. A survey on ethereum systems security: Vulnerabilities, attacks and defenses. arXiv 2019, arXiv:1908.04507. [Google Scholar]
- Joshi, A.P.; Han, M.; Wang, Y. A survey on security and privacy issues of blockchain technology. Math. Found. Comput. 2018, 1, 121–147. [Google Scholar] [CrossRef] [Green Version]
- Narayanan, A.; Bonneau, J.; Felten, E.; Miller, A.; Goldfeder, S. Bitcoin and Cryptocurrency Technologies: A Comprehensive Introduction; Princeton University Press: Princeton, NJ, USA, 2016. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Li, W.; Andreina, S.; Bohli, J.M.; Karame, G. Securing proof-of-stake blockchain protocols. In Data Privacy Management, Cryptocurrencies and Blockchain Technology; Springer: Cham, Switzerland, 2017; pp. 297–315. [Google Scholar]
- King, S.; Nadal, S. Ppcoin: Peer-to-peer crypto-currency with proof-of-stake. Self-Publ. Pap. 2012, 19, 1. [Google Scholar]
- Sobti, R.; Geetha, G. Cryptographic hash functions: A review. Int. J. Comput. Sci. Issues 2012, 9, 461. [Google Scholar]
- Merkle, R.C. Protocols for public key cryptosystems. In Proceedings of the 1980 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 14–16 April 1980; p. 122. [Google Scholar]
- Burgess, K.; Colangelo, J. The Promise of Bitcoin and the Blockchain; Consumers’ Research: Oxford, UK, 2015. [Google Scholar]
- Yang, W.; Garg, S.; Raza, A.; Herbert, D.; Kang, B. Blockchain: Trends and future. In Pacific Rim Knowledge Acquisition Workshop; Springer: Cham, Switzerland, 2018; pp. 201–210. [Google Scholar]
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 71. [Google Scholar]
- Szabo, N. The Idea of Smart Contracts; Satoshi Nakamoto Institute: Nashville, TN, USA, 1997; Volume 6. [Google Scholar]
- Brent, L.; Jurisevic, A.; Kong, M.; Liu, E.; Gauthier, F.; Gramoli, V.; Holz, R.; Scholz, B. Vandal: A scalable security analysis framework for smart contracts. arXiv 2018, arXiv:1809.03981. [Google Scholar]
- Ekblaw, A.; Azaria, A.; Halamka, J.D.; Lippman, A. A Case Study for Blockchain in Healthcare: “MedRec” prototype for electronic health records and medical research data. In Proceedings of the IEEE Open & Big Data Conference, Washington, DC, USA, 5–8 December 2016; Volume 13, p. 13. [Google Scholar]
- Underwood, S. Blockchain beyond bitcoin. Commun. ACM 2016, 59, 15–17. [Google Scholar] [CrossRef]
- Hanke, T.; Movahedi, M.; Williams, D. Dfinity technology overview series, consensus system. arXiv 2018, arXiv:1805.04548. [Google Scholar]
- Eisses, J.; Verspeek, L.; Dawe, C.; Dijkstra, S. Effect Network: Decentralized Network for Artificial Intelligence. 2018. Available online: http://effect.ai/download/effectwhitepaper.pdf (accessed on 9 March 2021).
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Xu, L.; Shah, N.; Chen, L.; Diallo, N.; Gao, Z.; Lu, Y.; Shi, W. Enabling the sharing economy: Privacy respecting contract based on public blockchain. In Proceedings of the ACM Workshop on Blockchain, Cryptocurrencies and Contracts, Abu Dhabi, United Arab Emirates, 2–6 April 2017; pp. 15–21. [Google Scholar]
- Kumari, K.A.; Padmashani, R.; Varsha, R.; Upadhayay, V. Securing Internet of Medical Things (IoMT) using private blockchain network. In Principles of Internet of Things (IoT) Ecosystem: Insight Paradigm; Springer: Cham, Switzerland, 2020; pp. 305–326. [Google Scholar]
- Dinh, T.T.A.; Wang, J.; Chen, G.; Liu, R.; Ooi, B.C.; Tan, K.L. Blockbench: A framework for analyzing private blockchains. In Proceedings of the 2017 ACM International Conference on Management of Data, Chicago, IL, USA, 14–19 May 2017; pp. 1085–1100. [Google Scholar]
- Polge, J.; Robert, J.; Le Traon, Y. Permissioned blockchain frameworks in the industry: A comparison. ICT Express 2020. [Google Scholar] [CrossRef]
- Henry, R.; Herzberg, A.; Kate, A. Blockchain access privacy: Challenges and directions. IEEE Secur. Priv. 2018, 16, 38–45. [Google Scholar] [CrossRef]
- Kosba, A.; Miller, A.; Shi, E.; Wen, Z.; Papamanthou, C. Hawk: The blockchain model of cryptography and privacy-preserving smart contracts. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 839–858. [Google Scholar]
- Barcelo, J. User Privacy in the Public Bitcoin Blockchain. Available online: http://www.dtic.upf.edu/jbarcelo/papers/20140704User.2014PrivacyinthePublicBitcoinBlockchain/paper.pdf (accessed on 9 May 2016).
- Ammous, S. Blockchain Technology: What Is It Good for? 2016. Available online: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2832751 (accessed on 9 March 2021).
- Chow, S.S.; Yiu, S.M.; Hui, L.C. Efficient identity based ring signature. In International Conference on Applied Cryptography and Network Security; Springer: Berlin/Heidelberg, Germany, 2005; pp. 499–512. [Google Scholar]
- Tsang, P.P.; Au, M.H.; Liu, J.K.; Susilo, W.; Wong, D.S. A suite of non-pairing id-based threshold ring signature schemes with different levels of anonymity. In International Conference on Provable Security; Springer: Berlin/Heidelberg, Germany, 2010; pp. 166–183. [Google Scholar]
- Noether, S. Ring SIgnature Confidential Transactions for Monero. IACR Cryptol. ePrint Arch. 2015, 2015, 1098. [Google Scholar]
- Ben-Sasson, E.; Bentov, I.; Horesh, Y.; Riabzev, M. Scalable, transparent, and post-quantum secure computational integrity. IACR Cryptol. ePrint Arch. 2018, 2018, 46. [Google Scholar]
- Jakobsson, M.; Juels, A. An optimally robust hybrid mix network. In Proceedings of the Twentieth Annual ACM Symposium on Principles of Distributed Computing, Newport, RI, USA, 26–29 August 2001; pp. 284–292. [Google Scholar]
- Jefferys, K.; Shishmarev, M.; Harman, S. Session: A Model for End-To-End Encrypted Conversations with Minimal Metadata Leakage. arXiv 2020, arXiv:2002.04609. [Google Scholar]
- Swan, K. Onion Routing and Tor. Geo. Law Tech. Rev. 2016, 1, 110–118. [Google Scholar]
- Dingledine, R.; Mathewson, N.; Syverson, P. Tor: The Second-Generation Onion Router; Technical Report; Naval Research Lab.: Washington, DC, USA, 2004. [Google Scholar]
- Sharma, K.; Jayashankar, A.; Banu, K.S.; Tripathy, B. Data Anonymization Through Slicing Based on Graph-Based Vertical Partitioning. In Proceedings of the 3rd International Conference on Advanced Computing, Networking and Informatics; Springer: New Delhi, India, 2016; pp. 569–576. [Google Scholar]
- Domingo-Ferrer, J.; Torra, V. A critique of k-anonymity and some of its enhancements. In Proceedings of the 2008 Third International Conference on Availability, Reliability and Security, Barcelona, Spain, 4–7 March 2008; pp. 990–993. [Google Scholar]
- Aggarwal, G.; Feder, T.; Kenthapadi, K.; Motwani, R.; Panigrahy, R.; Thomas, D.; Zhu, A. Approximation algorithms for k-anonymity. In Proceedings of the International Conference on Database Theory (ICDT 2005), Edinburgh, UK, 5–7 January 2005. [Google Scholar]
- Yao, L.; Chen, Z.; Hu, H.; Wu, G.; Wu, B. Sensitive attribute privacy preservation of trajectory data publishing based on l-diversity. Distrib. Parallel Databases 2020, 1–27. [Google Scholar] [CrossRef]
- Li, N.; Li, T.; Venkatasubramanian, S. t-closeness: Privacy beyond k-anonymity and l-diversity. In Proceedings of the 2007 IEEE 23rd International Conference on Data Engineering, Istanbul, Turkey, 15–20 April 2007; pp. 106–115. [Google Scholar]
- Machanavajjhala, A.; Kifer, D.; Gehrke, J.; Venkitasubramaniam, M. l-diversity: Privacy beyond k-anonymity. ACM Trans. Knowl. Discov. Data 2007, 1, 3-es. [Google Scholar] [CrossRef]
- Kern, M. Anonymity: A formalization of privacy-l-diversity. In Proceedings of the Zum Seminar Future Internet (FI), Innovative Internet Technologien und Mobilkommunikation (IITM) und Autonomous Communication Networks (ACN), Munich, Germany, 13 April 2013; Volume 49. [Google Scholar]
- Wang, M.; Jiang, Z.; Zhang, Y.; Yang, H. T-closeness slicing: A new privacy-preserving approach for transactional data publishing. INFORMS J. Comput. 2018, 30, 438–453. [Google Scholar] [CrossRef]
- Boyen, X.; Mei, Q.; Waters, B. Direct chosen ciphertext security from identity-based techniques. In Proceedings of the 12th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 7–11 November 2005; pp. 320–329. [Google Scholar]
- Waters, B. Efficient identity-based encryption without random oracles. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2005; pp. 114–127. [Google Scholar]
- Fotiou, N.; Polyzos, G.C. Decentralized name-based security for content distribution using blockchains. In Proceedings of the 2016 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), San Francisco, CA, USA, 10–14 April 2016; pp. 415–420. [Google Scholar]
- Guo, R.; Shi, H.; Zhao, Q.; Zheng, D. Secure attribute-based signature scheme with multiple authorities for blockchain in electronic health records systems. IEEE Access 2018, 6, 11676–11686. [Google Scholar] [CrossRef]
- Rahulamathavan, Y.; Phan, R.C.W.; Rajarajan, M.; Misra, S.; Kondoz, A. Privacy-preserving blockchain based IoT ecosystem using attribute-based encryption. In Proceedings of the 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bhubaneswar, India, 17–20 December 2017; pp. 1–6. [Google Scholar]
- Panwar, G.; Misra, S.; Vishwanathan, R. Blanc: Blockchain-based anonymous and decentralized credit networks. In Proceedings of the Ninth ACM Conference on Data and Application Security and Privacy, Richardson, TX, USA, 25–27 March 2019; pp. 339–350. [Google Scholar]
- Vasantha, R.; Prasad, R.S.; Guntur, A. Secured email data based on blowfish with blockchain technology. Sci. Technol. Dev. 2019, 8, 456–464. [Google Scholar]
- Zhang, Z.; Qi, Q.; Kumar, N.; Chilamkurti, N.; Jeong, H.Y. A secure authentication scheme with anonymity for session initiation protocol using elliptic curve cryptography. Multimed. Tools Appl. 2015, 74, 3477–3488. [Google Scholar] [CrossRef]
- Shah, S. Use of Blockchain as a Software Component to Send Messages Anonymously for a Data Trading Platform; Archemy: New Egypt, NJ, USA, 2017. [Google Scholar]
- Wang, Q.; Qin, B.; Hu, J.; Xiao, F. Preserving transaction privacy in bitcoin. Future Gener. Comput. Syst. 2017, 107, 793–804. [Google Scholar] [CrossRef]
- Fun, T.S.; Samsudin, A. A survey of homomorphic encryption for outsourced big data computation. KSII Trans. Internet Inf. Syst. 2016, 10, 3826–3851. [Google Scholar]
- AlTawy, R.; ElSheikh, M.; Youssef, A.M.; Gong, G. Lelantos: A blockchain-based anonymous physical delivery system. In Proceedings of the 2017 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 15–1509. [Google Scholar]
- Gamage, C.; Gras, B.; Crispo, B.; Tanenbaum, A.S. An identity-based ring signature scheme with enhanced privacy. In Proceedings of the 2006 Securecomm and Workshops, Baltimore, MD, USA, 28 August–1 September 2006; pp. 1–5. [Google Scholar]
- Maxwell, G. CoinJoin: Bitcoin Privacy for the Real World. Bitcoin Forum. 2013. Available online: https://bitcointalk.org/index (accessed on 9 March 2021).
- Kiran, P.; Kavya, N. A survey on methods, attacks and metric for privacy preserving data publishing. Int. J. Comput. Appl. 2012, 53, 20–28. [Google Scholar]
- Sriramoju, S.B. Analysis and Comparison of Anonymous Techniques for Privacy Preserving in Big Data. Int. J. Adv. Res. Comput. Commun. Eng. 2017, 6, 64–67. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2001; pp. 213–229. [Google Scholar]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Paris, France, 9–11 April 1984; pp. 47–53. [Google Scholar]
- Nie, T.; Song, C.; Zhi, X. Performance evaluation of DES and Blowfish algorithms. In Proceedings of the 2010 International Conference on Biomedical Engineering and Computer Science, Wuhan, China, 23–25 April 2010; pp. 1–4. [Google Scholar]
- Jeeva, A.; Palanisamy, D.V.; Kanagaram, K. Comparative analysis of performance efficiency and security measures of some encryption algorithms. Int. J. Eng. Res. Appl. 2012, 2, 3033–3037. [Google Scholar]
- Yakoubov, S.; Gadepally, V.; Schear, N.; Shen, E.; Yerukhimovich, A. A survey of cryptographic approaches to securing big-data analytics in the cloud. In Proceedings of the 2014 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 9–11 September 2014; pp. 1–6. [Google Scholar]
- Marin, G.A. Network security basics. IEEE Secur. Priv. 2005, 3, 68–72. [Google Scholar] [CrossRef]
- Jawandhiya, P.M.; Ghonge, D.; Ali, M.; Deshpande, J. A survey of mobile ad hoc network attacks. Int. J. Eng. Sci. Technol. 2010, 2, 4063–4071. [Google Scholar] [CrossRef]
- Ehrenkranz, T.; Li, J. On the state of IP spoofing defense. ACM Trans. Internet Technol. 2009, 9, 1–29. [Google Scholar] [CrossRef] [Green Version]
- Tsudik, G. Message Authentication with One-Way Hash Functions. SIGCOMM Comput. Commun. Rev. 1992, 22, 29–38. [Google Scholar] [CrossRef]
- Chandra, S.; Paira, S.; Alam, S.S.; Sanyal, G. A comparative survey of symmetric and asymmetric key cryptography. In Proceedings of the 2014 International Conference on Electronics, Communication and Computational Engineering (ICECCE), Hosur, India, 17–18 November 2014; pp. 83–93. [Google Scholar]
- Yarımtepe, O.; Dalkılıç, G.; Özcanhan, M.H. Distributed Denial of Service Prevention Techniques. In Proceedings of the 3rd International Symposium on Digital Forensics and Security, Ankara, Turkey, 11–12 May 2015; pp. 24–28. [Google Scholar]
- Ekparinya, P.; Gramoli, V.; Jourjon, G. Impact of man-in-the-middle attacks on ethereum. In Proceedings of the 2018 IEEE 37th Symposium on Reliable Distributed Systems (SRDS), Salvador, Brazil, 2–5 October 2018; pp. 11–20. [Google Scholar]
- Aliyu, F.; Sheltami, T.; Shakshuki, E.M. A detection and prevention technique for man in the middle attack in fog computing. Procedia Comput. Sci. 2018, 141, 24–31. [Google Scholar] [CrossRef]
- Lou, X.; Huu, C.T.; Tan, R.; Yau, D.K.; Kalbarczyk, Z.T. Assessing and Mitigating Impact of Time Delay Attack against Cyber-Physical Systems. Available online: http://publish.illinois.edu/cps-security/files/2018/05/delay.pdf (accessed on 14 September 2020).
- Sargolzaei, A.; Yen, K.K.; Abdelghani, M.N.; Mehbodniya, A.; Sargolzaei, S. A novel technique for detection of time delay switch attack on load frequency control. Intell. Control. Autom. 2015, 6, 205. [Google Scholar] [CrossRef]
- Apostolaki, M.; Zohar, A.; Vanbever, L. Hijacking bitcoin: Routing attacks on cryptocurrencies. In Proceedings of the 2017 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2017; pp. 375–392. [Google Scholar]
- Xing, Q.; Wang, B.; Wang, X. Bgpcoin: Blockchain-based internet number resource authority and bgp security solution. Symmetry 2018, 10, 408. [Google Scholar] [CrossRef] [Green Version]
- Kiayias, A.; Panagiotakos, G. On trees, chains and fast transactions in the blockchain. In International Conference on Cryptology and Information Security in Latin America; Springer: Cham, Switzerland, 2017; pp. 327–351. [Google Scholar]
- Li, C.; Li, P.; Zhou, D.; Yang, Z.; Wu, M.; Yang, G.; Xu, W.; Long, F.; Yao, A.C.C. A Decentralized Blockchain with High Throughput and Fast Confirmation. In Proceedings of the 2020 USENIX Annual Technical Conference (USENIX ATC 20), Boston, MA, USA, 15–17 July 2020; pp. 515–528. [Google Scholar]
- Serjantov, A.; Sewell, P. Passive attack analysis for connection-based anonymity systems. In European Symposium on Research in Computer Security; Springer: Berlin/Heidelberg, Germany, 2003; pp. 116–131. [Google Scholar]
- Hiller, J.; Pennekamp, J.; Dahlmanns, M.; Henze, M.; Panchenko, A.; Wehrle, K. Tailoring onion routing to the Internet of Things: Security and privacy in untrusted environments. In Proceedings of the 2019 IEEE 27th International Conference on Network Protocols (ICNP), Chicago, IL, USA, 8–10 October 2019; pp. 1–12. [Google Scholar]
- Pawar, M.V.; Anuradha, J. Network security and types of attacks in network. Procedia Comput. Sci. 2015, 48, 503–506. [Google Scholar] [CrossRef]
- Sinha, P.; Jha, V.; Rai, A.K.; Bhushan, B. Security vulnerabilities, attacks and countermeasures in wireless sensor networks at various layers of OSI reference model: A survey. In Proceedings of the 2017 International Conference on Signal Processing and Communication (ICSPC), Coimbatore, India, 28–29 July 2017; pp. 288–293. [Google Scholar]
- Decker, C.; Wattenhofer, R. Bitcoin transaction malleability and MtGox. In European Symposium on Research in Computer Security; Springer: Cham, Switzerland, 2014; pp. 313–326. [Google Scholar]
- Rajput, U.; Abbas, F.; Oh, H. A solution towards eliminating transaction malleability in bitcoin. J. Inf. Process. Syst. 2018, 14, 837–850. [Google Scholar]
- Buterin, V.; Griffith, V. Casper the friendly finality gadget. arXiv 2017, arXiv:1710.09437. [Google Scholar]
- Sompolinsky, Y.; Zohar, A. Secure high-rate transaction processing in bitcoin. In Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 507–527. [Google Scholar]
- Buterin, V.; Hernandez, D.; Kamphefner, T.; Pham, K.; Qiao, Z.; Ryan, D.; Sin, J.; Wang, Y.; Zhang, Y.X. Combining GHOST and Casper. arXiv 2020, arXiv:2003.03052. [Google Scholar]
- Sayeed, S.; Marco-Gisbert, H. Assessing blockchain consensus and security mechanisms against the 51% attack. Appl. Sci. 2019, 9, 1788. [Google Scholar] [CrossRef] [Green Version]
- Eyal, I.; Sirer, E.G. Majority is not enough: Bitcoin mining is vulnerable. In Conference on Financial Cryptography and Data Security; Springer: Berlin/Heidelberg, Germany, 2014; pp. 436–454. [Google Scholar]
- Solat, S.; Potop-Butucaru, M. Brief announcement: Zeroblock: Timestamp-free prevention of block-withholding attack in bitcoin. In International Symposium on Stabilization, Safety, and Security of Distributed Systems; Springer: Cham, Switerland, 2017; pp. 356–360. [Google Scholar]
- Heilman, E.; Kendler, A.; Zohar, A.; Goldberg, S. Eclipse attacks on bitcoin’s peer-to-peer network. In Proceedings of the 24th {USENIX} Security Symposium ({USENIX} Security 15), Washington, DC, USA, 12–14 August 2015; pp. 129–144. [Google Scholar]
- Simmons, S. A Brief Breakdown of Monero’s Ongoing Network Attacks. 2021. Available online: https://sethsimmons.me/posts/moneros-ongoing-network-attack/ (accessed on 26 February 2021).
- Singh, A.; Castro, M.; Druschel, P.; Rowstron, A. Defending against eclipse attacks on overlay networks. In Proceedings of the 11th Workshop on ACM SIGOPS European Workshop, Leuven, Belgium, 19–22 September 2004; p. 21-es. [Google Scholar]
- Bissias, G.; Ozisik, A.P.; Levine, B.N.; Liberatore, M. Sybil-resistant mixing for bitcoin. In Proceedings of the 13th Workshop on Privacy in the Electronic Society, Scottsdale, AZ, USA, 3 November 2014; pp. 149–158. [Google Scholar]
- Lee, H.; Shin, M.; Kim, K.S.; Kang, Y.; Kim, J. Recipient-oriented transaction for preventing double spending attacks in private blockchain. In Proceedings of the 2018 15th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Hong Kong, China, 11–13 June 2018; pp. 1–2. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef] [Green Version]
- Juels, A.; Kosba, A.; Shi, E. The ring of gyges: Investigating the future of criminal smart contracts. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 283–295. [Google Scholar]
- Feist, J.; Grieco, G.; Groce, A. Slither: A static analysis framework for smart contracts. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27 May 2019; pp. 8–15. [Google Scholar]
- Tikhomirov, S.; Voskresenskaya, E.; Ivanitskiy, I.; Takhaviev, R.; Marchenko, E.; Alexandrov, Y. Smartcheck: Static analysis of ethereum smart contracts. In Proceedings of the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain, Gothenburg, Sweden, 27 May–3 June 2018; pp. 9–16. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In International Conference on Principles of Security and Trust; Springer: Berlin/Heidelberg, Germany, 2017; pp. 164–186. [Google Scholar]
- Sayeed, S.; Marco-Gisbert, H.; Caira, T. Smart contract: Attacks and protections. IEEE Access 2020, 8, 24416–24427. [Google Scholar] [CrossRef]
- Mayer, H. ECDSA security in bitcoin and ethereum: A research survey. CoinFaabrik 2016, 28, 126. [Google Scholar]
- Dai, W.; Deng, J.; Wang, Q.; Cui, C.; Zou, D.; Jin, H. SBLWT: A secure blockchain lightweight wallet based on trustzone. IEEE Access 2018, 6, 40638–40648. [Google Scholar] [CrossRef]
- Laurent, M.; Giannetsos, T. (Eds.) Information Security Theory and Practice; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12024. [Google Scholar] [CrossRef] [Green Version]
- Xiao, Z.; Xu, J.; Meng, X. p-sensitivity: A semantic privacy-protection model for location-based services. In Proceedings of the 2008 Ninth International Conference on Mobile Data Management Workshops (MDMW), Beijing, China, 27–30 April 2008; pp. 47–54. [Google Scholar]
- Sowmyarani, C.; Srinivasan, G.; Sukanya, K. A New Privacy Preserving Measure: p-Sensitive, t-Closeness. In International Conference on Advances in Computing; Springer: New Delhi, India, 2013; pp. 57–62. [Google Scholar]
- Kumar, A.; Fischer, C.; Tople, S.; Saxena, P. A traceability analysis of monero’s blockchain. In Proceedings of the European Symposium on Research in Computer Security, Oslo, Norway, 11–15 September 2017; pp. 153–173. [Google Scholar]
- Möser, M.; Soska, K.; Heilman, E.; Lee, K.; Heffan, H.; Srivastava, S.; Hogan, K.; Hennessey, J.; Miller, A.; Narayanan, A.; et al. An empirical analysis of traceability in the monero blockchain. Proc. Priv. Enhanc. Technol. 2018, 2018, 143–163. [Google Scholar] [CrossRef] [Green Version]
- Prabhakaran, M.; Sahai, A. Concurrent Zero Knowledge Proofs with Logarithmic Roundcomplexity. 2004. Available online: http://eprint.iacr.org/2002/055.pdf (accessed on 9 March 2021).
- Lu, L.; Han, J.; Liu, Y.; Hu, L.; Huai, J.P.; Ni, L.; Ma, J. Pseudo trust: Zero-knowledge authentication in anonymous P2Ps. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 1325–1337. [Google Scholar] [CrossRef] [Green Version]
- Byun, J.W.; Kamra, A.; Bertino, E.; Li, N. Efficient k-anonymization using clustering techniques. In International Conference on Database Systems for Advanced Applications; Springer: Berlin/Heidelberg, Germany, 2007; pp. 188–200. [Google Scholar]
- Meyerson, A.; Williams, R. On the complexity of optimal k-anonymity. In Proceedings of the Twenty-Third ACM SIGMOD-SIGACT-SIGART Symposium on Principles of Database Systems, Paris, France, 14–16 June 2004; pp. 223–228. [Google Scholar]
- Ghinita, G.; Karras, P.; Kalnis, P.; Mamoulis, N. Fast data anonymization with low information loss. In Proceedings of the 33rd International Conference on Very Large Data Bases, Vienna, Austria, 23–27 September 2007; pp. 758–769. [Google Scholar]
- Mehta, B.B.; Rao, U.P. Improved l-Diversity: Scalable Anonymization Approach for Privacy Preserving Big Data Publishing. J. King Saud Univ. Comput. Inf. Sci. 2019. [Google Scholar] [CrossRef]
- Chase, M.; Chow, S.S. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009; pp. 121–130. [Google Scholar]
- Edemacu, K.; Park, H.K.; Jang, B.; Kim, J.W. Privacy Provision in Collaborative Ehealth With Attribute-Based Encryption: Survey, Challenges and Future Directions. IEEE Access 2019, 7, 89614–89636. [Google Scholar] [CrossRef]
- Farah, S.; Javed, Y.; Shamim, A.; Nawaz, T. An experimental study on performance evaluation of asymmetric encryption algorithms. In Proceedings of the 3rd European Conference of Computer Science on Recent Advances in Information Science (EECS-12), Paris, France, 2–4 December 2012; pp. 121–124. [Google Scholar]
- Levi, A.; Savas, E. Performance evaluation of public-key cryptosystem operations in WTLS protocol. In Proceedings of the Eighth IEEE Symposium on Computers and Communications (ISCC 2003), Kemer-Antalya, Turkey, 3 July 2003; pp. 1245–1250. [Google Scholar]
- Maqsood, F.; Ahmed, M.; Ali, M.M.; Shah, M.A. Cryptography: A comparative analysis for modern techniques. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 442–448. [Google Scholar] [CrossRef]
- Awasthi, A.K.; Lal, S. ID-based ring signature and proxy ring signature schemes from bilinear pairings. arXiv 2005, arXiv:cs/0504097. [Google Scholar]
- Boneh, D.; Gentry, C.; Lynn, B.; Shacham, H. Aggregate and verifiably encrypted signatures from bilinear maps. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2003; pp. 416–432. [Google Scholar]
- Jurczyk, P.; Xiong, L. Distributed anonymization: Achieving privacy for both data subjects and data providers. In IFIP Annual Conference on Data and Applications Security and Privacy; Springer: Berlin/Heidelberg, Germany, 2009; pp. 191–207. [Google Scholar]
- Kawle, P.; Hiwase, A.; Bagde, G.; Tekam, E.; Kalbande, R. Modified advanced encryption standard. Int. J. Soft Comput. Eng. 2014, 4, 21–23. [Google Scholar]
- Padmavathi, B.; Kumari, S.R. A survey on performance analysis of DES, AES and RSA algorithm along with LSB substitution. Int. J. Sci. Res. 2013, 170–174. [Google Scholar]
- Mansour, A.; Malik, K.M.; Kaso, N. AMOUN: Asymmetric lightweight cryptographic scheme for wireless group communication. arXiv 2020, arXiv:2002.06713. [Google Scholar]
- Amin, M.; Faragallah, O.S.; Abd El-Latif, A.A. Chaos-based hash function (CBHF) for cryptographic applications. Chaos Solitons Fractals 2009, 42, 767–772. [Google Scholar] [CrossRef]
- Nakajima, J.; Matsui, M. Performance analysis and parallel implementation of dedicated hash functions. In Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2002; pp. 165–180. [Google Scholar]
- Gahi, Y.; Guennoun, M.; El-Khatib, K. A secure database system using homomorphic encryption schemes. arXiv 2015, arXiv:1512.03498. [Google Scholar]
- Gennaro, R.; Micciancio, D.; Rabin, T. An efficient non-interactive statistical zero-knowledge proof system for quasi-safe prime products. In Proceedings of the 5th ACM Conference on Computer and Communication Security (CCS’98), San Francisco, CA, USA, 3–5 November 1998; ACM Press: San Francisco, CA, USA, 1998; pp. 67–72. [Google Scholar]
- Brown-Cohen, J.; Narayanan, A.; Psomas, A.; Weinberg, S.M. Formal barriers to longest-chain proof-of-stake protocols. In Proceedings of the 2019 ACM Conference on Economics and Computation, Phoenix, AZ, USA, 24–28 June 2019; pp. 459–473. [Google Scholar]
Short Biography of Authors
 | Sidra Aslam received her Master degree in Computer Science from the COMSATS University Islamabad, Pakistan in January 2017. During this period, she worked on research projects and published research papers in scholarly journals and conference proceedings. In 2015, she received the best research paper award at the National Software Engineering Conference (NSEC), IEEE in Pakistan. She is currently an Assistant Researcher at the InnoRenew CoE, a teaching assistant and a Ph.D. student at the Faculty of Mathematics, Natural Sciences and Information Technologies, University of Primorska, Slovenia. Her current research interests include information security and privacy, blockchain, and semantic web technologies. |
 | Aleksandar Tošić received his Masters in Computer Science from the University of Primorska in 2016. He is currently a teaching assistant and Phd student at University of Primorska, and a research assistant at InnoRenew CoE. His main areas of research are related to distributed, and decentralised network protocols, and distributed ledger technology. |
 | Dr. Michael Mrissa received his PhD in computer science from the University of Lyon, France, in 2007. His main areas of research are related to distributed systems and include service-oriented computing, semantic web, privacy, web of things. He has authored 80+ peer-reviewed publications in international conferences and journals, and he has been involved in several European, French and Slovenian research projects. He is currently researcher in the ICT research group of the InnoRenew CoE. He also holds a full professor position at the Faculty of Mathematics, Natural sciences and Information Technologies of the University of Primorska. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aslam, S.; Tošić, A.; Mrissa, M. Secure and Privacy-Aware Blockchain Design: Requirements, Challenges and Solutions. J. Cybersecur. Priv. 2021, 1, 164-194. https://doi.org/10.3390/jcp1010009
Aslam S, Tošić A, Mrissa M. Secure and Privacy-Aware Blockchain Design: Requirements, Challenges and Solutions. Journal of Cybersecurity and Privacy. 2021; 1(1):164-194. https://doi.org/10.3390/jcp1010009
Chicago/Turabian StyleAslam, Sidra, Aleksandar Tošić, and Michael Mrissa. 2021. "Secure and Privacy-Aware Blockchain Design: Requirements, Challenges and Solutions" Journal of Cybersecurity and Privacy 1, no. 1: 164-194. https://doi.org/10.3390/jcp1010009
APA StyleAslam, S., Tošić, A., & Mrissa, M. (2021). Secure and Privacy-Aware Blockchain Design: Requirements, Challenges and Solutions. Journal of Cybersecurity and Privacy, 1(1), 164-194. https://doi.org/10.3390/jcp1010009






