Towards Integration of Security and Safety Measures for Critical Infrastructures Based on Bayesian Networks and Graph Theory: A Systematic Literature Review
Abstract
1. Introduction
- (a)
- To identify records, using search queries from numerous databases, including Scopus, ACM, and the Web of Sciences, focusing on united safety and security using GT and BN models.
- (b)
- To perform a comprehensive comparative interpretation of classified approaches, regarding threat actors, performance verification mechanisms, the number of applied nodes for system development, and implementation scenarios, among others, for combining safety and security aspects using GT or BN methodologies.
- (c)
- To illustrate the research consequences of this SLR, based on pre-defined research questions (RQs).
- (d)
- To elaborate pros and cons, limitations, and future research directions of BN and GT approaches for integrating safety and security.
2. Background
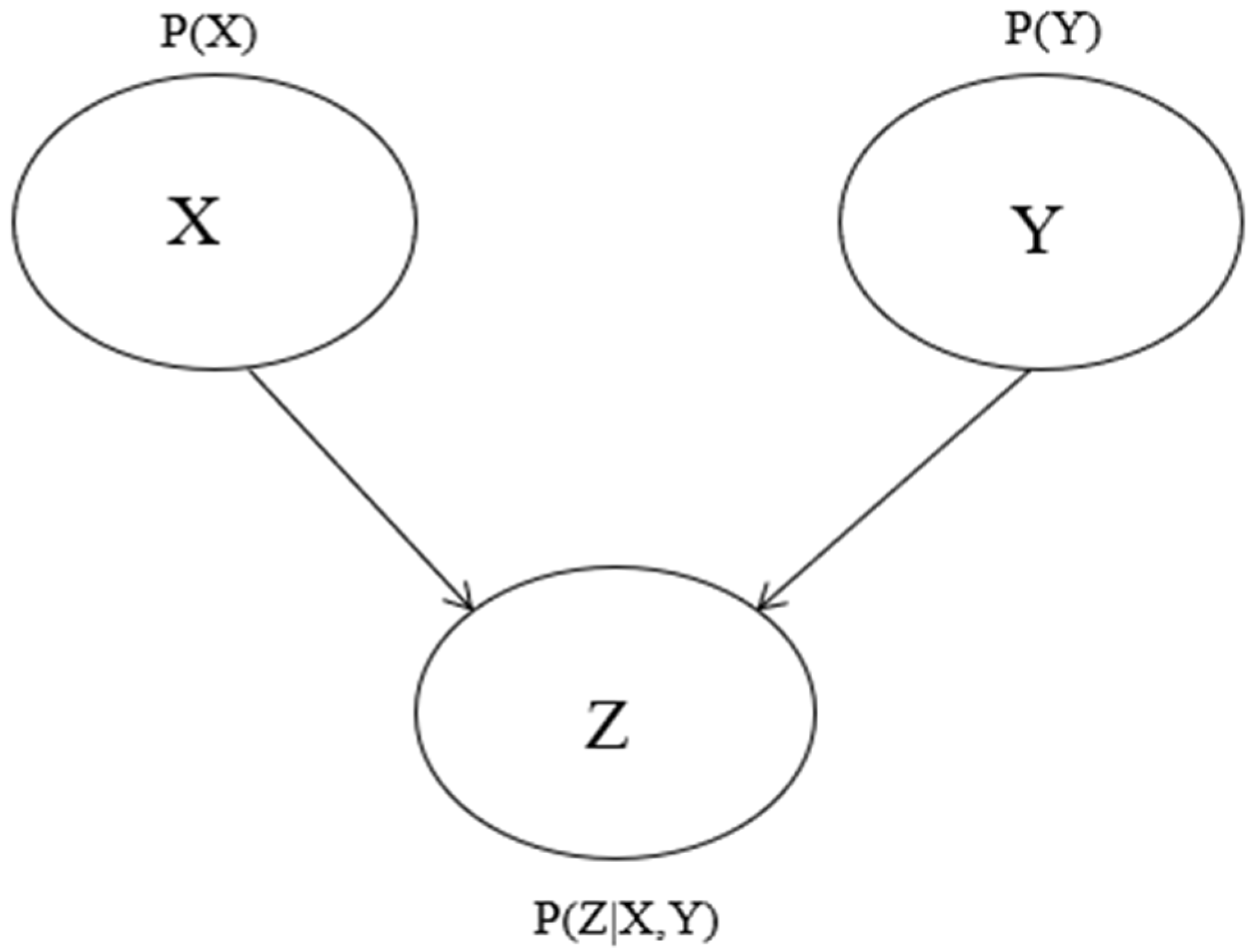
2.1. Bayesian Networks
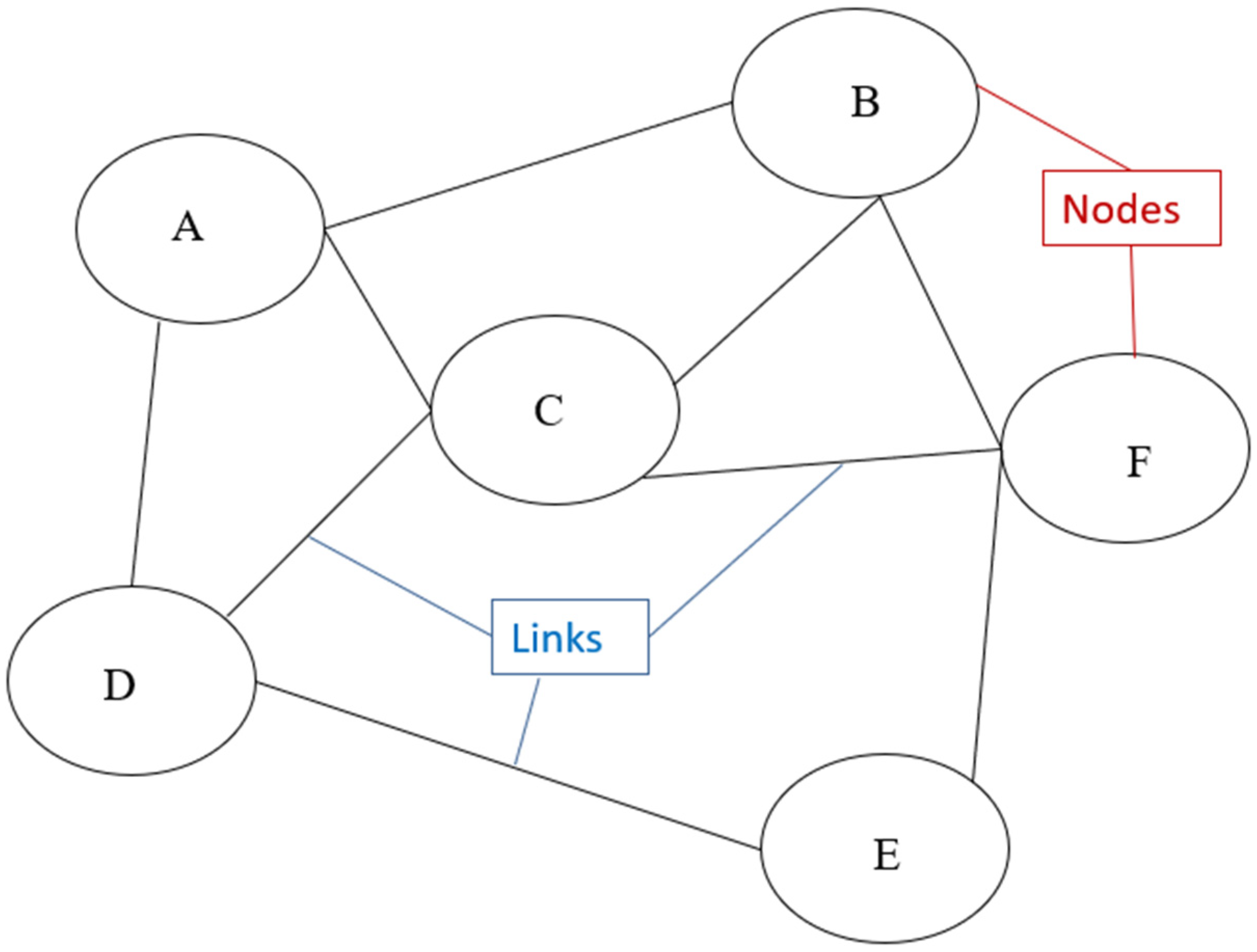
2.2. Graph Theory
3. Research Design
3.1. Search Querry Process and Research Questions
- Why is the integration of security and safety needed?
- How have BN- and GT-based methodologies been utilized for security and safety studies in CI?
- What have been the targeted application domains?
- What solutions have been developed in the identified studies?
- How is performance validated for developed techniques and algorithmic solutions?
- What are the advantages and disadvantages of existing studies?
3.2. Exclusion and Inclusion Criteria
- (a)
- Studies that are not focused on the integration of safety and security, based on Bayesian networks or graph theory (also a combination of both).
- (b)
- Studies that merely provide background about the integration of both measures.
- (c)
- Studies that do not develop or design a novel method/approach/model/tool.
- (a)
- Published in a conference or journal classified in the identified databases.
- (b)
- The records are identified from January 2011 to September 2020.
- (c)
- Developed a tool or technique for integrating safety and security measures using Bayesian Networks or Graph Theory (also a combination of both approaches).
4. Results
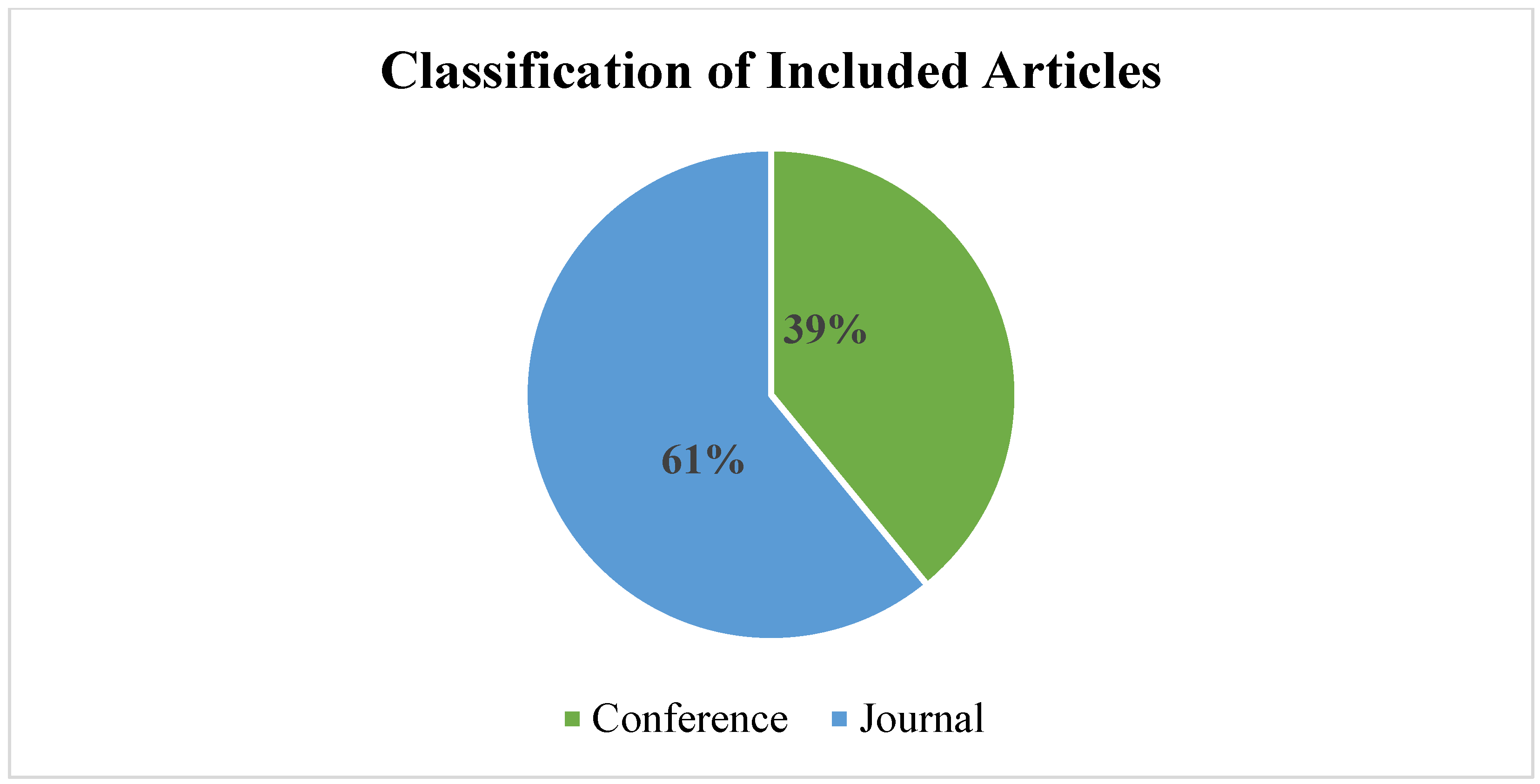
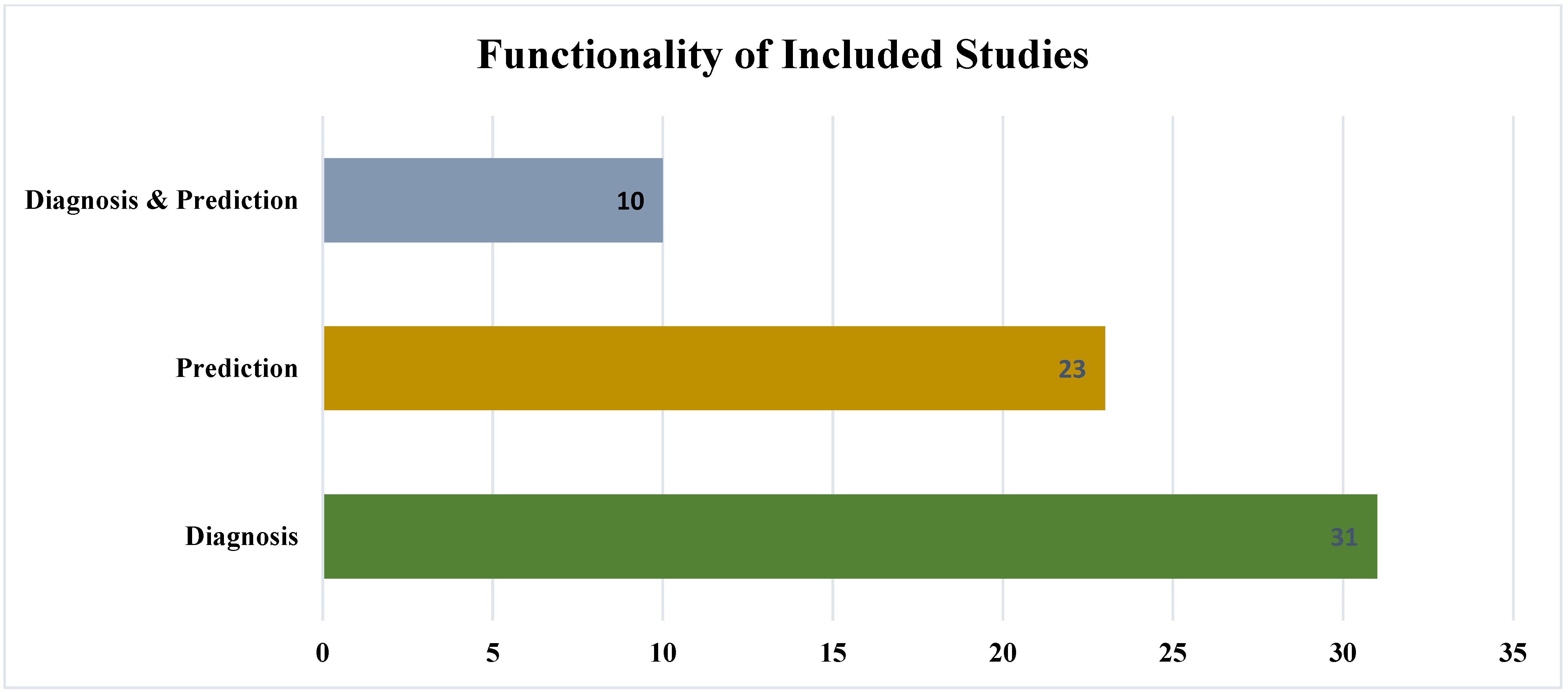
4.1. Organization and Classification of Included Studies
4.2. Included Studies Based on GT and BN for Safty and Security
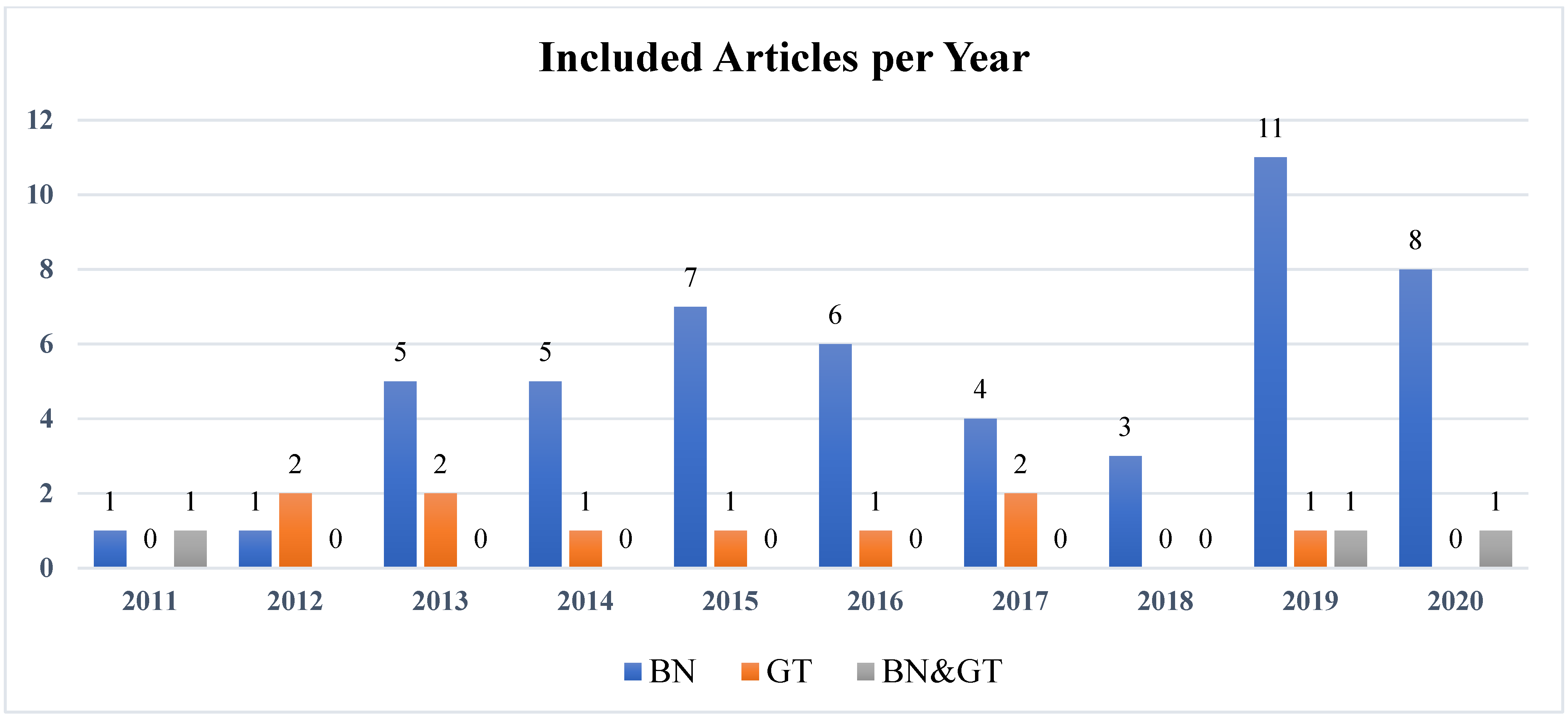
4.3. Citation Index of Included Studies
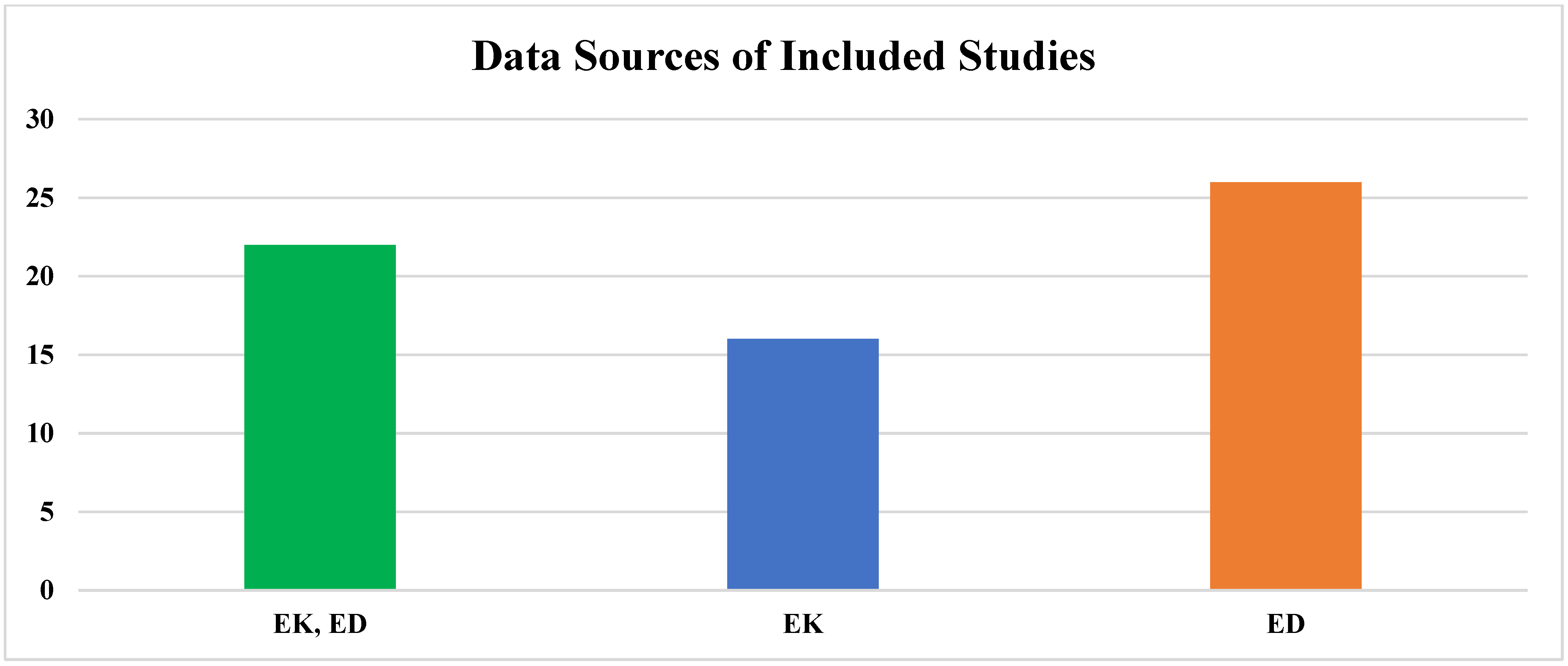
4.4. Data Sources and Number of Nodes Used to Construct BN/GT
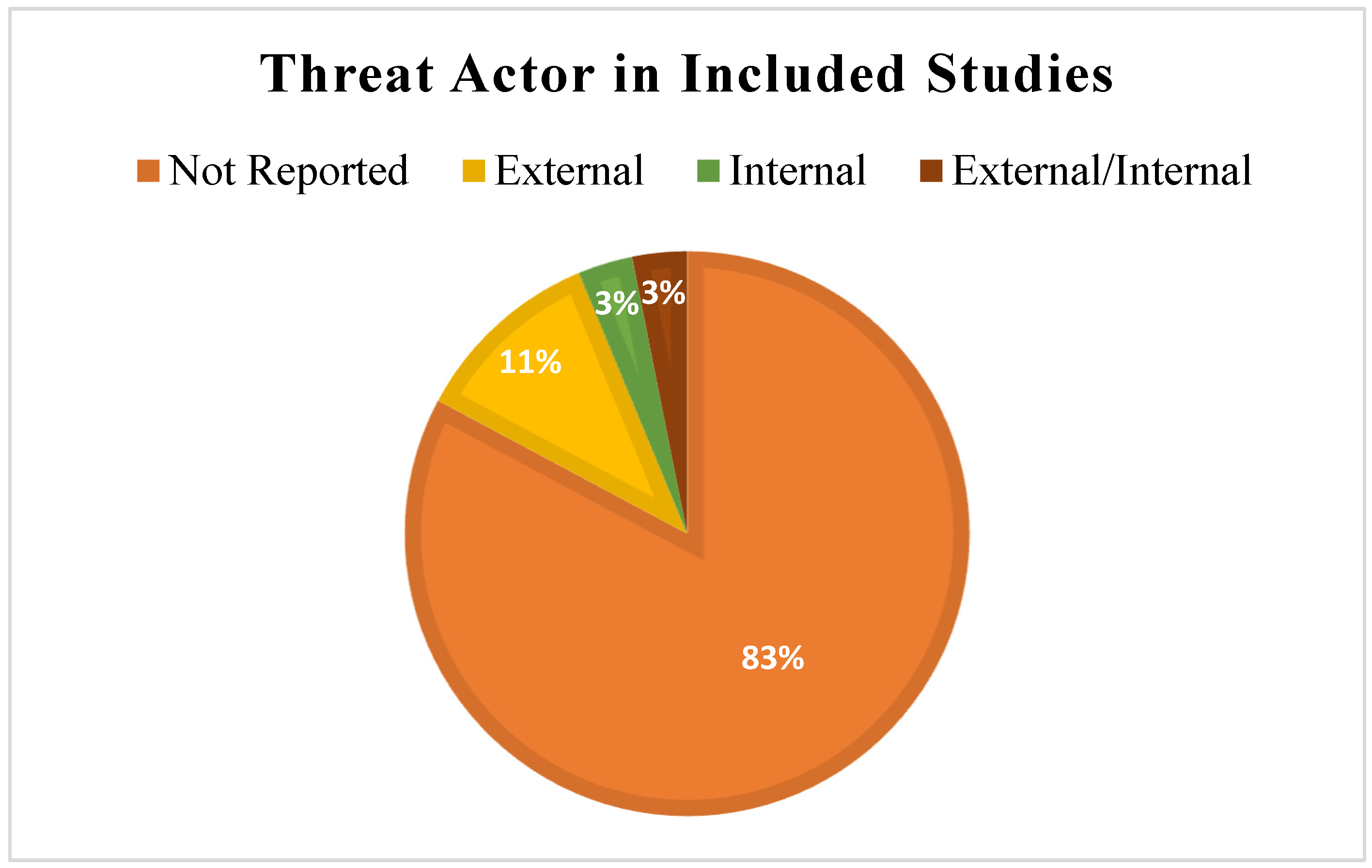
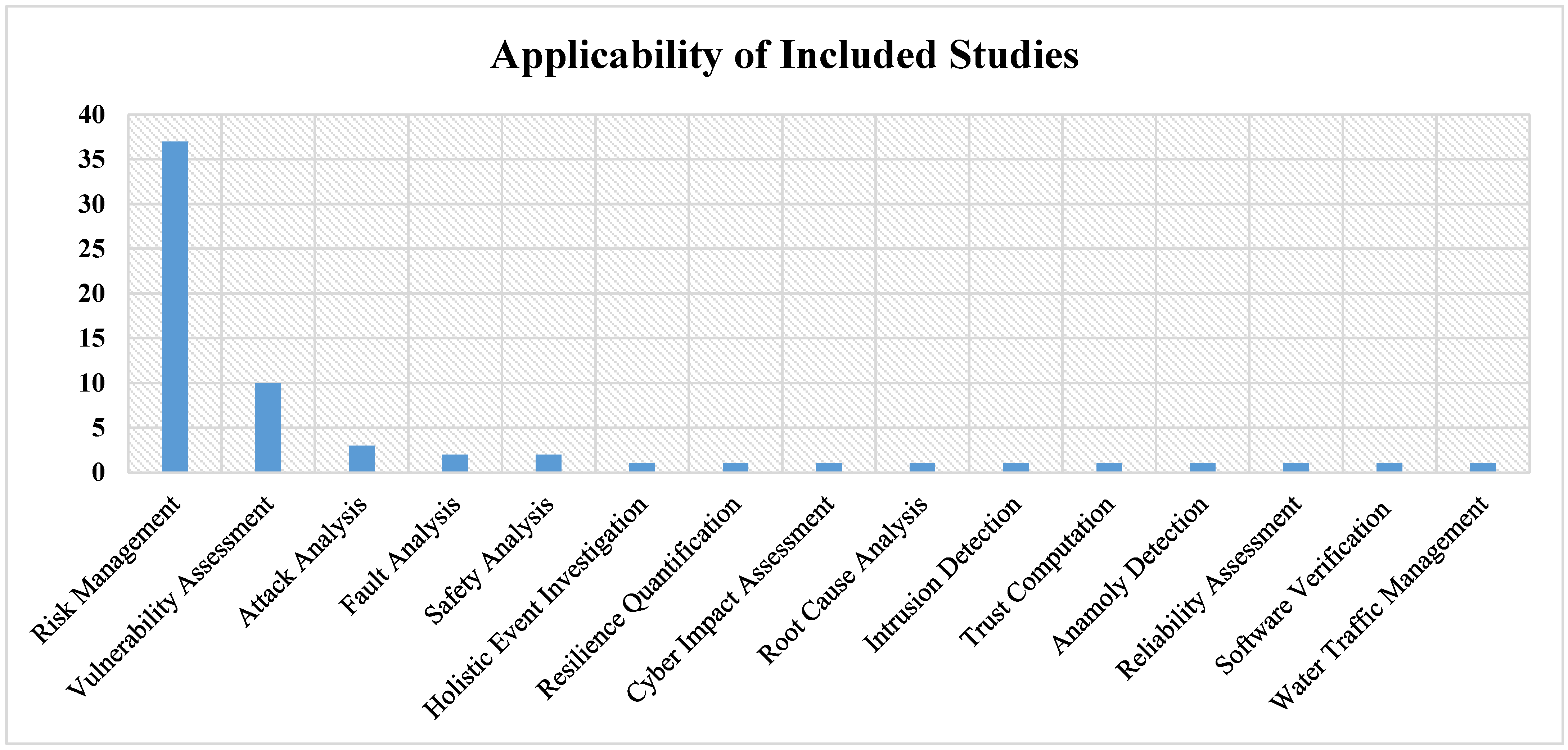
4.5. Applicability, Threat Actor, and Implementation Criteria
5. Discussion
5.1. Why Is the Integration of Security and Safety Needed?
5.2. How Have Bayesian Network- and Graph Theory-Based Methodologies Been Utilized for Security and Safety Studies in CI?
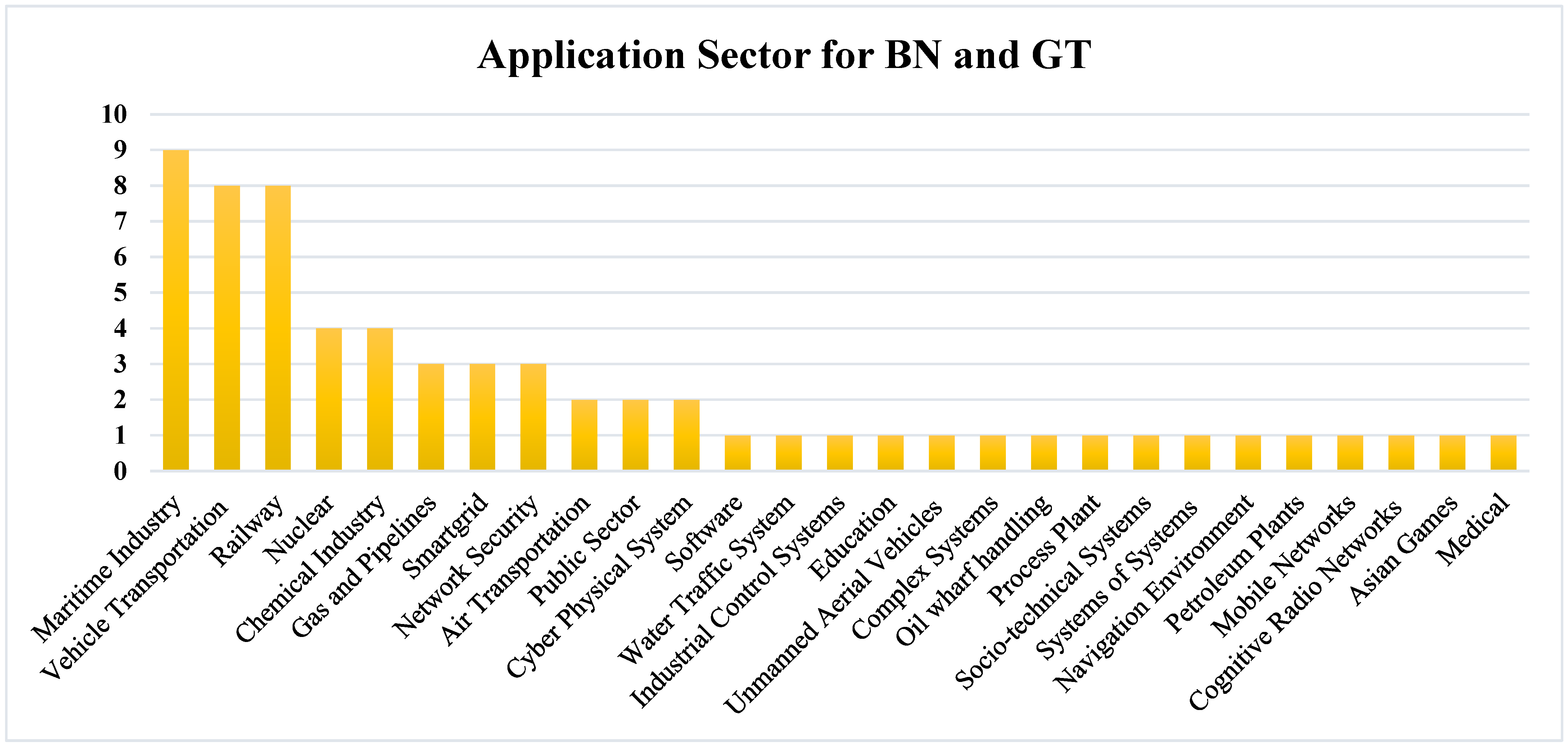
5.3. What Have Been the Targeted Application Domains?
5.4. What Solutions Have Been Developed in the Identified Studies?
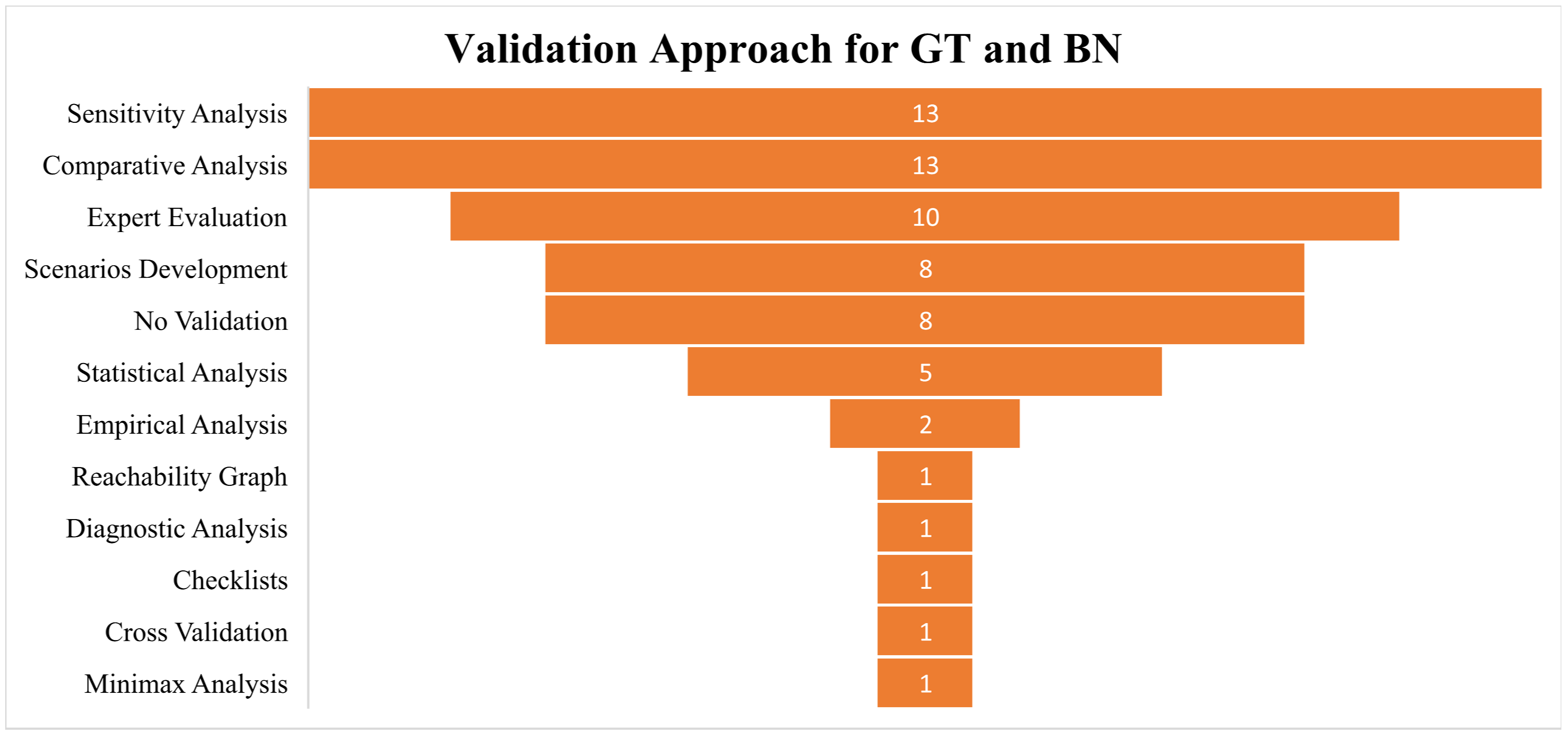
5.5. How Is Performance Validated for Developed Techniques and Algorithmic Solutions?
5.6. What Are the Advantages and Disadvantages of Existing Studies?
5.7. Limitations
- (1)
- The inclusion of articles is solely based on the English language, which indicates that notable studies of security and safety integration based on BN or GT in other languages have not been considered.
- (2)
- The results of this SLR are based on a restricted number of databases. These databases are used, due to the widespread usage for querying papers in the field of GT and BN.
- (3)
- Included studies were performed in different applications, so it might be not possible to compare each perspective.
6. Conclusions
- (a)
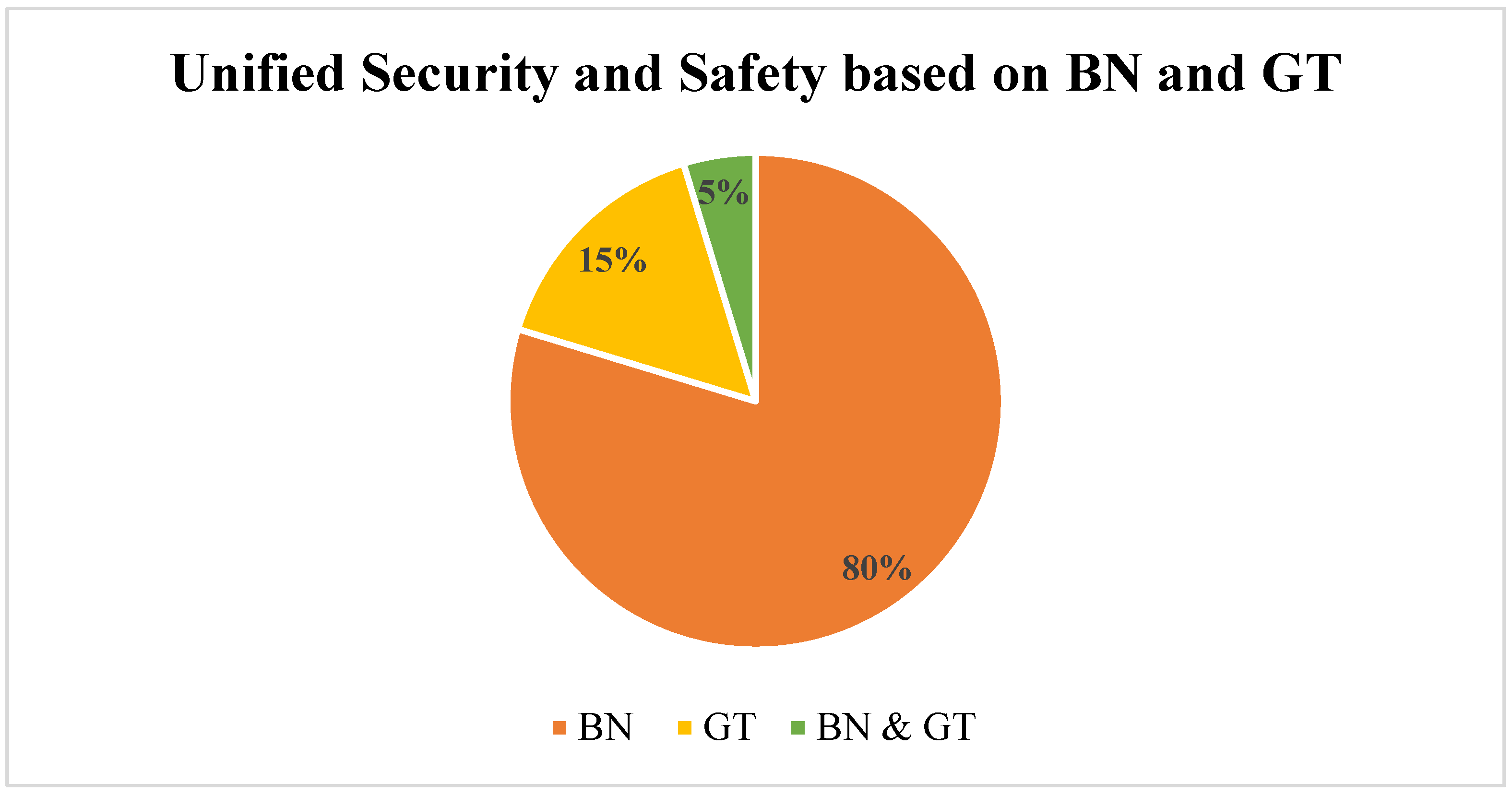
- It is observed that from the 64 included studies, 51 used BN models, 10 utilized GT models, and the remaining 3 were based on united BN and GT.
- (b)
- Most development scenarios utilized 40 nodes for performing experiments to observe unintentional failures or risks for GT and BN models.
- (c)
- It has been emphasized that approximately one-third of BN and GT models were evaluated in real-time; however, others were either based on simulation analysis or theoretical concepts.
- (d)
- There were two types of data sources (EK and ED) used for developing BN and GT models for different applications.
- (e)
- The key performance validation mechanisms for the included studies were statistical analysis, expert evaluation, and sensitivity analysis.
- (a)
- There is a need to develop a generic tool or method or standard to combine security and safety, which can be helpful for different applications, since the significance of integrating both measures was demonstrated in this SLR, and a generic approach may offer feasibility and flexibility.
- (b)
- It is observed that there are various validation methods for evaluating BN or GT. A more extended investigation is necessary to estimate the accuracy and efficiency of validation mechanisms, in order to find the optimal option.
- (c)
- Moreover, there is a need to research to acquire information about the suitable number of nodes to ensure reliable and accurate performance for ensuring safety and security based on BN or GT models.
- (d)
- Further research could improve Bayesian analysis based on the Metropolis–Hastings algorithm and Gaussian distributions [107].
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Baker, T.; Asim, M.; MacDermott, Á.; Iqbal, F.; Kamoun, F.; Shah, B.; Alfandi, O.; Hammoudeh, M. A secure fog-based platform for SCADA-based IoT critical infrastructure. Softw. Pract. Exp. 2020, 50, 503–518. [Google Scholar] [CrossRef]
- Kotenko, I.; Saenko, I.; Kushnerevich, A.; Branitskiy, A. Attack detection in IoT critical infrastructures: A machine learning and big data processing approach. In Proceedings of the 27th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Pavia, Italy, 13–15 February 2019; pp. 340–347. [Google Scholar]
- Stellios, I.; Kotzanikolaou, P.; Psarakis, M.; Alcaraz, C.; Lopez, J. A survey of iot-enabled cyberattacks: Assessing attack paths to critical infrastructures and services. IEEE Commun. Surv. Tutor. 2018, 20, 3453–3495. [Google Scholar] [CrossRef]
- Kornecki, A.J.; Liu, M. Fault Tree Analysis for Safety/Security Verification in Aviation Software. Electronics 2013, 2, 41–56. [Google Scholar] [CrossRef]
- Schmittner, C.; Ma, Z.; Schoitsch, E.; Gruber, T. A case study of fmvea and chassis as safety and security co-analysis method for automotive cyber-physical systems. In Proceedings of the 1st ACM Workshop on Cyber-Physical System Security, Singapore, 14 April 2015; pp. 69–80. [Google Scholar]
- Banerjee, A.; Venkatasubramanian, K.K.; Mukherjee, T.; Gupta, S.K.S. Ensuring safety, security, and sustainability of mission-critical cyber–physical systems. Proc. IEEE 2012, 100, 283–299. [Google Scholar] [CrossRef]
- Kornecki, A.J.; Subramanian, N.; Zalewski, J. Studying interrelationships of safety and security for software assurance in cyberphysical systems: Approach based on bayesian belief networks. In Proceedings of the 2013 Federated Conference on Computer Science and Information Systems, Krakow, Poland, 8–11 September 2013; pp. 1393–1399. [Google Scholar]
- John, A.; Yang, Z.; Riahi, R.; Wang, J. A risk assessment approach to improve the resilience of a seaport system using Bayesian networks. Ocean Eng. 2016, 111, 136–147. [Google Scholar] [CrossRef]
- Zeng, J.; Wu, S.; Chen, Y.; Zeng, R.; Wu, C. Survey of attack graph analysis methods from the perspective of data and knowledge processing. Secur. Commun. Netw. 2019, 2019, 1–17. [Google Scholar] [CrossRef]
- Sharma, R.; Kamble, S.S.; Gunasekaran, A.; Kumar, V.; Kumar, A. A systematic literature review on machine learning applications for sustainable agriculture supply chain performance. Comput. Oper. Res. 2020, 119, 104926. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Kumar, N.; Tyagi, S. Blockchain-based security attack resilience schemes for autonomous vehicles in industry 4.0: A systematic review. Comput. Electr. Eng. 2020, 86, 106717. [Google Scholar] [CrossRef]
- Chockalingam, S.; Hadžiosmanović, D.; Pieters, W.; Teixeira, A.A.; van Gelder, P. Integrated Safety and Security Risk Assessment Methods: A Survey of Key Characteristics and Applications. In Critical Information Infrastructures Security; Havarneanu, G., Setola, R., Nassopoulos, H., Wolthusen, S., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2017; Volume 10242. [Google Scholar] [CrossRef]
- Lallie, H.S.; Debattista, K.; Bal, J. A review of attack graph and attack tree visual syntax in cyber security. Comput. Sci. Rev. 2020, 35, 100219. [Google Scholar] [CrossRef]
- Fovino, L.N.; Masera, M.; De Cian, A. Integrating cyber attacks within fault trees. Reliab. Eng. Syst. Saf. 2009, 94–99, 1394–1402. [Google Scholar] [CrossRef]
- Kriaa, S.; Bouissou, M. Modeling safety and security interdependencies with bdmp (boolean logic driven markov processes). In SAFECOMP 2014; Bondavalli, A., Ceccarelli, A., Ortmeier, F., Eds.; Springer: Cham, Switzerland, 2014. [Google Scholar]
- Abdo, H.; Kaouk, M.; Flaus, J.-M.; Masse, F. A safety/security risk analysis approach of Industrial Control Systems: A cyber bowtie—Combining new version of attack tree with bowtie analysis. Comput. Secur. 2018, 72, 175–195. [Google Scholar] [CrossRef]
- Galagedarage Don, M.; Khan, F. Process Fault Prognosis Using Hidden Markov Model—Bayesian Networks Hybrid Model. Ind. Eng. Chem. Res. 2019, 58, 12041–12053. [Google Scholar] [CrossRef]
- Cooper, G.F.; Herskovits, E. A Bayesian method for the induction of probabilistic networks from data. Mach. Learn. 1992, 9, 309–347. [Google Scholar] [CrossRef]
- Afenyo, M.; Khan, F.; Veitch, B.; Yang, M. Arctic shipping accident scenario analysis using Bayesian Network approach. Ocean Eng. 2017, 133, 224–230. [Google Scholar] [CrossRef]
- Kabir, S.; Papadopoulos, Y. Applications of Bayesian networks and Petri nets in safety, reliability, and risk assessments: A review. Saf. Sci. 2019, 115, 154–175. [Google Scholar] [CrossRef]
- Bruni, R.; Melgratti, H.; Montanari, U. Bayesian network semantics for Petri nets. Theor. Comput. Sci. 2020, 807, 95–113. [Google Scholar] [CrossRef]
- Lichte, D.; Wolf, K.-D. Bayesian Network Based Analysis of Cyber Security Impact on Safety. In Proceedings of the 29th European Safety and Reliability Conference, Hannover, Germany, 22–26 September 2019; pp. 1502–1509. [Google Scholar]
- Jensen, F.V.; Nielsen, T.D. Bayesian Networks and Decision Graphs; Springer: Berlin, Germany, 2007. [Google Scholar]
- Heckerman, D.; Geiger, D.; Chickering, D.M. Learning bayesian networks: The combination of knowledge and statistical data. Mach. Learn. 1995, 20, 197–243. [Google Scholar] [CrossRef]
- Liao, W.; Ji, Q. Learning Bayesian network parameters under incomplete data with domain knowledge. Pattern Recognit. 2009, 42, 3046–3056. [Google Scholar] [CrossRef]
- Friedman, N. The bayesian structural em algorithm. In Proceedings of the Fourteenth Conference on Uncertainty in Artificial Intelligence, Madison, WI, USA, 24–26 July 1998; pp. 129–138. [Google Scholar]
- Blei, D.M.; Kucukelbir, A.; McAuliffe, J.D. Variational inference: A review for statisticians. J. Am. Stat. Assoc. 2017, 112, 859–877. [Google Scholar] [CrossRef]
- Pelikan, M.; Goldberg, D.E.; Lobo, F.G. A survey of optimization by building and using probabilistic models. Comput. Optim. Appl. 2002, 21, 5–20. [Google Scholar] [CrossRef]
- Khakzad, N.; Reniers, G. Using graph theory to analyze the vulnerability of process plants in the context of cascading effects. Reliab. Eng. Syst. Saf. 2015, 143, 63–73. [Google Scholar] [CrossRef]
- Ferrario, E.; Pedroni, N.; Zio, E. Evaluation of the robustness of critical infrastructures by Hierarchical Graph representation, clustering and Monte Carlo simulation. Reliab. Eng. Syst. Saf. 2016, 155, 78–96. [Google Scholar] [CrossRef]
- Leitold, D.; Vathy-Fogarassy, A.; Abonyi, J. Controllability and observability in complex networks—The effect of connection types. Sci. Rep. 2017, 7, 151. [Google Scholar] [CrossRef]
- Dwivedi, A.; Yu, X. A Maximum-Flow-Based Complex Network Approach for Power System Vulnerability Analysis. IEEE Trans. Ind. Inform. 2011, 9, 81–88. [Google Scholar] [CrossRef]
- Kabir, M.; Mishra, Y.; Bansal, R. Probabilistic load flow for distribution systems with uncertain PV generation. Appl. Energy 2016, 163, 343–351. [Google Scholar] [CrossRef]
- Fu, X.; Sun, H.; Guo, Q.; Pan, Z.; Zhang, X.; Zeng, S. Probabilistic power flow analysis considering the dependence between power and heat. Appl. Energy 2017, 191, 582–592. [Google Scholar] [CrossRef]
- Johansson, J.; Hassel, H. An approach for modelling interdependent infrastructures in the context of vulnerability analysis. Reliab. Eng. Syst. Saf. 2010, 95, 1335–1344. [Google Scholar] [CrossRef]
- Casoetto, B.; Flottes, E.; Ardeois, J.; Thanh, N.; Joliot, J.-B.; Nait-Abdallah, R. How to commercialize reliable capacities on a com-plex transmission network? J. Nat. Gas. Sci. Eng. 2011, 3, 657–663. [Google Scholar] [CrossRef]
- Chung, F.R.K.; Lu, L. Complex Graphs and Networks, Volume 107 of CBMS Regional Conference Series in Mathematics; American Mathematical Society: Providence, RI, USA, 2006. [Google Scholar]
- Ahmat, K. Graph Theory and Optimization Problems for Very Large Networks; City University of New York: New York, NY, USA, 2009. [Google Scholar]
- Shirinivas, S.G.; Vetrivel, S.; Elango, N.M. Applications of graph theory in computer science—An overview. Int. J. Eng. Sci. Technol. 2010, 2, 4610–4621. [Google Scholar]
- Hossain, N.U.I.; Nur, F.; Hosseini, S.; Jaradat, R.; Marufuzzaman, M.; Puryear, S.M. A Bayesian network based approach for modeling and assessing resilience: A case study of a full service deep water port. Reliab. Eng. Syst. Saf. 2019, 189, 378–396. [Google Scholar] [CrossRef]
- Silva, A.; Silva, K.; Rocha, A.; Queiroz, F. Calculating the trust of providers through the construction weighted Sec-SLA. Futur. Gener. Comput. Syst. 2019, 97, 873–886. [Google Scholar] [CrossRef]
- Lyu, X.; Ding, Y.; Yang, S.-H. Bayesian Network Based C2P Risk Assessment for Cyber-Physical Systems. IEEE Access 2020, 8, 88506–88517. [Google Scholar] [CrossRef]
- Fu, L.; Wang, X.; Liu, B.; Li, L. Investigation into the role of human and organizational factors in security work against terrorism at large-scale events. Saf. Sci. 2020, 128, 104764. [Google Scholar] [CrossRef]
- Jiang, M.; Lu, J. Maritime accident risk estimation for sea lanes based on a dynamic Bayesian network. Marit. Policy Manag. 2020, 47, 649–664. [Google Scholar] [CrossRef]
- Arief, R.; Khakzad, N.; Pieters, W. Mitigating cyberattack related domino effects in process plants via ICS seg-mentation. J. Inf. Secur. Appl. 2020, 51, 102450. [Google Scholar]
- Yang, T.-H.; Qin, J.; Li, Z.-X. Public Safety Risk Assessment of Power Investment Project Based on Fuzzy Set and DS Evidence Theory. E3S Web Conf. 2020, 143, 02009. [Google Scholar] [CrossRef]
- Zhao, M.; Ji, S.; Zhao, Q.; Chen, C.; Wei, Z.-L. Risk Influencing Factor Analysis of Urban Express Logistics for Public Safety: A Chinese Perspective. Math. Probl. Eng. 2020, 2020, 1–14. [Google Scholar] [CrossRef]
- Ma, X.; Zhou, Q.; Liu, T.; Liu, Y.; Qiao, W. Security of the Arctic route from the resilience perspective: The ideal state, influencing factors, and evaluation. Marit. Policy Manag. 2020, 1–14. [Google Scholar] [CrossRef]
- Gao, X. Study on Ideological Safety Assessment Methods for College Students in the New Era. In Proceedings of the 12th International Conference on Measuring Technology and Mechatronics Automation (ICMTMA), Phuket, Thailand, 28–29 February 2020; pp. 962–966. [Google Scholar]
- Jiang, M.; Lu, J. The analysis of maritime piracy occurred in Southeast Asia by using Bayesian network. Transp. Res. Part E Logist. Transp. Rev. 2020, 139, 101965. [Google Scholar] [CrossRef]
- Hossain, N.U.I.; Raed, J.; Seyedmohsen, H.; Mohammad, M.; Randy, K.B. A framework for modeling and assessing system resilience using a Bayesian network: A case study of an interdependent electrical infrastructure system. Int. J. Crit. Infrastruct. Prot. 2019, 25, 62–83. [Google Scholar] [CrossRef]
- Hosseini, S.; Ivanov, D. Bayesian networks for supply chain risk, resilience and ripple effect analysis: A literature review. Expert Syst. Appl. 2020, 161, 113649. [Google Scholar] [CrossRef] [PubMed]
- Wan, Y.; Liu, C.; Qiao, W. An advanced fuzzy Bayesian-based FMEA approach for assessing maritime supply chain risks. Transp. Res. Part E Logist. Transp. Rev. 2019, 125, 222–240. [Google Scholar] [CrossRef]
- Sheehan, B.; Finbarr, M.; Martin, M.; Cian, R. Connected and autonomous vehicles: A cyber-risk classification framework. Transp. Res. Part A Policy Pract. 2019, 124, 523–536. [Google Scholar] [CrossRef]
- Barreto, A.B.; Costa, P. Cyber-ARGUS-A mission assurance framework. J. Netw. Comput. Appl. 2019, 133, 86–108. [Google Scholar] [CrossRef]
- Chockalingam, S.; Katta, V. Developing a Bayesian Network Framework for Root Cause Analysis of Observable Problems in Cyber-Physical Systems. In Proceedings of the 2019 IEEE Conference on Information and Communication Technology, Baku, Azerbaijan, 23–25 October 2019; pp. 1–6. [Google Scholar]
- Hosseini, S. Sarder Development of a Bayesian network model for optimal site selection of electric vehicle charging station. Int. J. Electr. Power Energy Syst. 2018, 105, 110–122. [Google Scholar] [CrossRef]
- Casillo, M.; Simone, C.; De Santo, M.; Pascale, F.; Santonicola, E. Embedded Intrusion Detection System for Detecting Attacks over CAN-BUS. In Proceedings of the 4th International Conference on System Reliability and Safety (ICSRS), Rome, Italy, 20–22 November 2019; pp. 136–141. [Google Scholar]
- Chen, C.; Reniers, G.; Khakzad, N. Integrating safety and security resources to protect chemical industrial parks from man-made domino effects: A dynamic graph approach. Reliab. Eng. Syst. Saf. 2019, 191, 106470. [Google Scholar] [CrossRef]
- Khakzad, N.; Reniers, G. Low-capacity utilization of process plants: A cost-robust approach to tackle man-made domino effects. Reliab. Eng. Syst. Saf. 2019, 191, 106114. [Google Scholar] [CrossRef]
- Xu, H.; Zhang, Y.; Li, H.; Skitmore, M.; Yang, J.; Yu, F. Safety risks in rail stations: An interactive approach. J. Rail Transp. Plan. Manag. 2019, 11, 100148. [Google Scholar] [CrossRef]
- Zhou, X. Security Analysis about Switching Equipment Based on Bayesian Networks. In Proceedings of the Sixth International Conference on Transportation Engineering, Chengdu, China, 20–22 September 2019; pp. 385–391. [Google Scholar]
- El Hachem, J.; Sedaghatbaf, A.; Lisova, E.; Causevic, A. Using Bayesian Networks for a Cyberattacks Propagation Analysis in Systems-of-Systems. In Proceedings of the 26th Asia-Pacific Software Engineering Conference (APSEC), Putrajaya, Malaysia, 2–5 December 2019; pp. 363–370. [Google Scholar]
- Elvin, E.; Tepe, K.; Balador, A.; Nwizege, K.S.; Jaimes, L.M. Malicious node detection in vehicular adhoc network using machine learning and deep learning. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Guo, X.; Zhang, L.; Liang, W.; Haugen, S. Risk identification of third-party damage on oil and gas pipe-lines through the Bayesian network. J. Loss Prev. Process Ind. 2018, 54, 163–178. [Google Scholar] [CrossRef]
- Zhou, Y.; Li, C.; Zhou, C.; Luo, H. Using Bayesian network for safety risk analysis of diaphragm wall deflection based on field data. Reliab. Eng. Syst. Saf. 2018, 180, 152–167. [Google Scholar] [CrossRef]
- Mukherjee, S.; Walkery, J.; Rayz, I.; Daily, J. A precedence graph-based approach to detect message injection attacks in J1939 based networks. In Proceedings of the 15th Annual Conference on Privacy, Security and Trust (PST), Calgary, AB, Canada, 28–30 August 2017; pp. 67–76. [Google Scholar]
- Su, H.; Zhang, J.; Zio, E.; Yang, N.; Li, X.; Zhang, Z. An integrated systemic method for supply reliability assessment of natural gas pipeline networks. Appl. Energy 2018, 209, 489–501. [Google Scholar] [CrossRef]
- Landucci, G.; Argenti, F.; Cozzani, V.; Reniers, G. Assessment of attack likelihood to support security risk assessment studies for chemical facilities. Process. Saf. Environ. Prot. 2017, 110, 102–114. [Google Scholar] [CrossRef]
- Hou, Z.; Zhao, P. Based on Fuzzy Bayesian Network of Oil Wharf Handling Risk Assessment. Math. Probl. Eng. 2016, 2016, 1–10. [Google Scholar] [CrossRef]
- Shin, J.; Son, H.; Heo, G. Cyber Security Risk Evaluation of a Nuclear I&C Using BN and ET. Nucl. Eng. Technol. 2017, 49, 517–524. [Google Scholar] [CrossRef]
- Donya, F.; Khakzad, N.; Reniers, G.; Cozzani, V. Security vulnerability assessment of gas pipelines using Discrete-time Bayesian network. Process Saf. Environ. Prot. 2017, 111, 714–725. [Google Scholar]
- Liang, H.; Chen, X.; Lai, X. Computer network vulnerability assessment and safety evaluation application based on Bayesian theory. Int. J. Secur. Its Appl. 2016, 10, 359–368. [Google Scholar]
- De Galizia, A.; Simon, C.; Weber, P.; Iung, B.; Duval, C.; Serdet, E. Modelling Non-Deterministic Causal Mechanisms involving Resilience in Risk Analysis. IFAC-PapersOnLine 2016, 49, 325–330. [Google Scholar] [CrossRef]
- Argenti, F.; Landucci, G.; Reniers, G. Probabilistic vulnerability assessment of chemical plants subjected to external acts of interference. Chem. Eng. Trans. 2016, 48, 691–696. [Google Scholar] [CrossRef]
- Chen, Z.; Zhang, Q.; Wu, X.; Yang, J.; Zhang, X. Safety state evaluation and risk management of navigation environment in harbour waters based on Bayesian network. In Proceedings of the 2016 IEEE International Conference on Intelligent Transportation Engineering (ICITE), Singapore, 20–22 August 2016; pp. 80–84. [Google Scholar]
- van Staalduinen, M.A.; Khan, F.; Gadag, V. SVAPP methodology: A predictive security vulnerability assessment modeling method. J. Loss Prev. Process. Ind. 2016, 43, 397–413. [Google Scholar] [CrossRef]
- Prabhakaran, R.; Krishnaprasad, R.; Nanda, M.; Jayanthi, J. System safety analysis for critical system applications using Bayesian networks. Procedia Comput. Sci. 2016, 93, 782–790. [Google Scholar] [CrossRef][Green Version]
- Chen, X. System vulnerability assessment and critical nodes identification. Expert Syst. Appl. 2016, 65, 212–220. [Google Scholar] [CrossRef]
- van Staalduinen, M.; Khan, F. A barrier based methodology to assess site security risk. In Proceedings of the SPE E&P Health, Safety, Security and Environmental Conference, Denver, CO, USA, 16–18 March 2015. [Google Scholar] [CrossRef]
- Tanguy, M.; Napoli, A. A methodology to improve the assessment of vulnerability on the maritime supply chain of energy. In Proceedings of the OCEANS 2015-MTS/IEEE Washington, Washington, DC, USA, 19–22 October 2015; pp. 1–6. [Google Scholar]
- Shin, J.; Son, H.; Heo, G. Development of a cyber security risk model using Bayesian networks. Reliab. Eng. Syst. Saf. 2015, 134, 208–217. [Google Scholar] [CrossRef]
- Gribaudo, M.; Iacono, M.; Marrone, S. Exploiting Bayesian Networks for the Analysis of Combined Attack Trees. Electron. Notes Theor. Comput. Sci. 2015, 310, 91–111. [Google Scholar] [CrossRef][Green Version]
- Peltola, M.J.; Kekolahti, P. Risk Assessment of Public Safety and Security Mobile Service. In Proceedings of the 10th International Conference on Availability, Reliability and Security, Toulouse, France, 24–27 August 2015; pp. 351–359. [Google Scholar]
- Zhou, X.; Zhang, Y. Security Analysis about a Train Control Center Based on a Bayesian Network. ICTE 2015 2015, 2525–2532. [Google Scholar] [CrossRef]
- Huo, Y.; Wang, Y.; Lin, W.; Sun, R. Three-layer Bayesian model based spectrum sensing to detect malicious attacks in cognitive radio networks. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), London, UK, 8–12 June 2015; pp. 1640–1645. [Google Scholar]
- Zhang, K.; Shi, P. Transportation Security Assessment Method for a Mountainous Freeway Using a Bayesian Network. ICTE 2015 2015, 2891–2896. [Google Scholar] [CrossRef]
- Bouejla, A.; Chaze, X.; Guarnieri, F.; Napoli, A. A Bayesian network to manage risks of maritime piracy against offshore oil fields. Saf. Sci. 2014, 68, 222–230. [Google Scholar] [CrossRef]
- Si, G.; Xu, J.; Yang, J.; Wen, S. An evaluation model for dependability of Internet-scale software on basis of Bayesian Networks and trustworthiness. J. Syst. Softw. 2014, 89, 63–75. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, Q.; Ji, W. Construction of monitoring model and algorithm design on passenger security during shipping based on improved Bayesian network. Sci. World J. 2014, 2014, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Khan, S.A.; Zafar, N.A.; Ahmad, F.; Islam, S. Extending Petri net to reduce control strategies of railway interlocking system. Appl. Math. Model. 2014, 38, 413–424. [Google Scholar] [CrossRef]
- Hang, L.; Shou-Xin, S.; Yu-Hui, Z.; Jia, X.; Qi, Y.; Qian-Hui, H. Probabilistic safety assessment for power transmission and transformation maintenance project based on fault tree analysis and Bayesian network. In Proceedings of the 2014 International Conference on Power System Technology, Chengdu, China, 20–22 October 2014; pp. 1300–1305. [Google Scholar]
- Xianfeng, Z. Research on Security Assessment and Maintenance Decision of Trains Based on Bayesian Networks. In Proceedings of the 2014 Sixth International Conference on Measuring Technology and Mechatronics Automation, Zhangjiajie, China, 10–11 January 2014; pp. 534–537. [Google Scholar]
- Tian, L.; Zhang, S. Real-Time, Multi-Factors-Coupled Early Warning Model in Water Transportation Safety. In Proceedings of the Fourth International Conference on Transportation Engineering, Chengdu, China, 19–20 October 2013; pp. 1726–1733. [Google Scholar] [CrossRef]
- Nzoukou, W.; Wang, L.; Jajodia, S.; Singhal, A. A unified framework for measuring a network’s mean time-to-compromise. In Proceedings of the 2013 IEEE 32nd International Symposium on Reliable Distributed Systems, Braga, Portugal, 30 September–3 October 2013; pp. 215–224. [Google Scholar]
- Shin, J.; Son, H.; Heo, G. Cyber Security Risk Analysis Model Composed with Activity-quality and Architecture Model. In Proceedings of the International Conference on Computer, Networks and Communication Engineering (ICCNCE 2013), Beijing, China, 23–24 May 2013. [Google Scholar] [CrossRef][Green Version]
- Dietzel, S.; Petit, J.; Heijenk, G.; Kargl, F. Graph-Based Metrics for Insider Attack Detection in VANET Multihop Data Dissemination Protocols. IEEE Trans. Veh. Technol. 2012, 62, 1505–1518. [Google Scholar] [CrossRef]
- Zhao, J.; Zheng, W. Study of fault diagnosis method based on fuzzy Bayesian network and application in CTCS-3 train control system. In Proceedings of the 2013 IEEE International Conference on Intelligent Rail Transportation, Beijing, China, 30 August–1 September 2013; pp. 249–254. [Google Scholar]
- Hird, J.; Koelle, R.; Kolev, D. Towards mathematical modelling in security risk management in system engineering. In Proceedings of the 2013 Integrated Communications, Navigation and Surveillance Conference (ICNS), Herndon, VA, USA, 22–25 April 2013; pp. 1–13. [Google Scholar]
- Eom, H.-S.; Park, G.-Y.; Jang, S.-C.; Son, H.S.; Kang, H.G. V&V-based remaining fault estimation model for safety-critical software of a nuclear power plant. Ann. Nucl. Energy 2012, 51, 38–49. [Google Scholar] [CrossRef]
- Chaze, X.; Bouejla, A.; Napoli, A.; Guarnieri, F. Integration of a bayesian network for response planning in a maritime piracy risk management system. In Proceedings of the 2012 7th International Conference on System of Systems Engineering (SoSE), Genova, Italy, 16–19 July 2012; pp. 137–142. [Google Scholar]
- Ming-Zhong, M. Network Security Analysis Based on Graph Theory Model with Neutral Network. In Future Communication, Computing, Control and Management; Springer: Berlin/Heidelberg, Germany, 2012; pp. 551–557. [Google Scholar]
- Wang, S.; Hong, L.; Chen, X. Vulnerability analysis of interdependent infrastructure systems: A methodological framework. Phys. A Stat. Mech. Appl. 2012, 391, 3323–3335. [Google Scholar] [CrossRef]
- Lu, S.; Wu, D.; Lu, S.; Zhang, H. A Bayesian network model for the Asian Games fire risk assessment. In Proceedings of the International Conference on Information Systems for Crisis Response and Management (ISCRAM), Harbin, China, 19–22 October 2011; pp. 350–355. [Google Scholar]
- Cavalheiro, A.C.; Fo, D.J.S.; Andrade, A.; Cardoso, J.R.; Horikawa, O.; Bock, E.; Fonseca, J. Specification of Supervisory Control Systems for Ventricular Assist Devices. Artif. Organs 2011, 35, 465–470. [Google Scholar] [CrossRef] [PubMed]
- Chockalingam, S.; Pieters, W.; Teixeira, A.; van Gelder, P. Bayesian network models in cyber security: A systematic review. In Secure IT Systems; Springer: Cham, Switzerland, 2017; pp. 105–122. [Google Scholar]
- Contreras-Reyes, J.E.; Quintero, F.O.L.; Wiff, R. Bayesian modeling of individual growth variability using back-calculation: Application to pink cusk-eel (Genypterus blacodes) off Chile. Ecol. Model. 2018, 385, 145–153. [Google Scholar] [CrossRef]

| S.No. | Study | Year | References | Category |
|---|---|---|---|---|
| 1 | Xiaorong et al. [42] | 2020 | 32 | Journal |
| 2 | Lipeng et al. [43] | 2020 | 63 | Journal |
| 3 | Meizhi et al. [44] | 2020 | 44 | Journal |
| 4 | Raditya et al. [45] | 2020 | 40 | Journal |
| 5 | Tai-hua et al. [46] | 2020 | 4 | Conference |
| 6 | Mingjing et al. [47] | 2020 | 42 | Journal |
| 7 | Xiaoxue et al. [48] | 2020 | 38 | Journal |
| 8 | Xin et al. [49] | 2020 | 10 | Conference |
| 9 | Meizhi et al. [50] | 2020 | 40 | Journal |
| 10 | Niamat et al. [51] | 2019 | 78 | Journal |
| 11 | Chengpeng et al. [52] | 2019 | 46 | Journal |
| 12 | Yi et al. [53] | 2019 | 7 | Conference |
| 13 | Barry et al. [54] | 2019 | 48 | Journal |
| 14 | Alexandre et al. [55] | 2019 | 98 | Journal |
| 15 | Sabarathinam et al. [56] | 2019 | 17 | Conference |
| 16 | Seyedmohsen et al. [57] | 2019 | 33 | Journal |
| 17 | Mario et al. [58] | 2019 | 20 | Conference |
| 18 | Chao et al. [59] | 2019 | 61 | Journal |
| 19 | Nima et al. [60] | 2019 | 27 | Journal |
| 20 | Hui et al. [61] | 2019 | 39 | Journal |
| 21 | Xiqiang et al. [62] | 2019 | 6 | Journal |
| 22 | Jamal et al. [63] | 2019 | 30 | Conference |
| 23 | Elvin et al. [64] | 2018 | 27 | Conference |
| 24 | Xiaoyan et al. [65] | 2018 | 31 | Journal |
| 25 | Ying et al. [66] | 2018 | 71 | Journal |
| 26 | Subhojeet et al. [67] | 2017 | 30 | Conference |
| 27 | Huai et al. [68] | 2017 | 64 | Journal |
| 28 | Gabriele et al. [69] | 2017 | 41 | Journal |
| 29 | Zhiqiang et al. [70] | 2017 | 22 | Journal |
| 30 | Jinsoo et al. [71] | 2017 | 23 | Journal |
| 31 | Donya et al. [72] | 2017 | 42 | Journal |
| 32 | Xianyou et al. [73] | 2016 | 15 | Journal |
| 33 | Galizia et al. [74] | 2016 | 13 | Conference |
| 34 | Francesca et al. [75] | 2016 | 21 | Journal |
| 35 | Zhao et al. [76] | 2016 | 8 | Conference |
| 36 | Mark et al. [77] | 2016 | 14 | Journal |
| 37 | Remya et al. [78] | 2016 | 14 | Conference |
| 38 | Xin Chen [79] | 2016 | 25 | Journal |
| 39 | Mark et al. [80] | 2015 | 9 | Conference |
| 40 | Martin et al. [81] | 2015 | 15 | Conference |
| 41 | Jinsoo et al. [82] | 2015 | 29 | Journal |
| 42 | Marco et al. [83] | 2015 | 28 | Journal |
| 43 | Matti et al. [84] | 2015 | 21 | Conference |
| 44 | Xiqiang et al. [85] | 2015 | 6 | Conference |
| 45 | Yongjia et al. [86] | 2015 | 16 | Conference |
| 46 | Kairan et al. [87] | 2015 | 9 | Conference |
| 47 | Amal et al. [88] | 2014 | 19 | Journal |
| 48 | Guannan et al. [89] | 2014 | 36 | Journal |
| 49 | Jiali et al. [90] | 2014 | 17 | Journal |
| 50 | Sher et al. [91] | 2014 | 39 | Journal |
| 51 | LONG et al. [92] | 2014 | 20 | Conference |
| 52 | Zeng Xianfeng [93] | 2014 | 4 | Conference |
| 53 | TIAN et al. [94] | 2013 | 5 | Conference |
| 54 | William et al. [95] | 2013 | 34 | Conference |
| 55 | Jinsoo et al. [96] | 2013 | 23 | Journal |
| 56 | Stefan et al. [97] | 2013 | 15 | Journal |
| 57 | Jingjing et al. [98] | 2013 | 15 | Conference |
| 58 | John et al. [99] | 2013 | 15 | Conference |
| 59 | Heung et al. [100] | 2013 | 21 | Journal |
| 60 | Chaze et al. [101] | 2012 | 16 | Conference |
| 61 | Mo Ming [102] | 2012 | 4 | Journal |
| 62 | Shuliang et al. [103] | 2012 | 68 | Journal |
| 63 | Song et al. [104] | 2011 | 23 | Conference |
| 64 | André et al. [105] | 2011 | 16 | Journal |
| Study | Application Sector | Technique | Description |
|---|---|---|---|
| Xiaorong et al. [42] | Cyber–Physical Systems (CPS) | BN | The advanced, BN-based method is proposed to offer a combined solution to the cyber-to-physical (C2P) risk evaluation for CPS. Additionally, for verifying the developed model, two scenarios are constructed. |
| Lipeng et al. [43] | Public Sector | BN | A systematic causation model for evaluating the main reasons for the failure of security in the 2022 Olympics. |
| Meizhi et al. [44] | Maritime Industry | BN | A BN-based model is proposed for the dynamic emergency risk estimation. |
| Raditya et al. [45] | Industrial Control Systems (ICS) | BN and GT | A decision-making methodology for analyzing risk is proposed to examine and estimate in ICS. |
| Tai-hua et al. [46] | Public Sector | BN | To develop public safety and safety evaluation approach using fuzzy logic and BN methods. |
| Mingjing et al. [47] | Vehicle Transportation | BN | Development of BN enabled model to analyze the risk aspects of urban transportation. |
| Xiaoxue et al. [48] | Maritime Industry | BN | A framework is developed for maritime to offer a balance between resilience and vulnerability. |
| Xin et al. [49] | Education | BN | An ideological security evaluation approach is developed to examine the risk factors for college students. |
| Meizhi et al. [50] | Maritime Industry | BN | To develop and validate the developed model for pirate attack mitigation by recognizing the most significant risk factors. |
| Niamat et al. [51] | Smart grid | BN | This research quantifies the resilience of electrical systems to address risks, based on BN model power. |
| Chengpeng et al. [52] | Maritime Industry | BN | To evaluate the risk assessment using fuzzy rule and BN model in maritime supply chains. |
| Yi et al. [53] | Maritime Industry | BN | To evaluate the possibility of several risks associated with shipping in navigation environments. |
| Barry et al. [54] | Vehicle Transportation | BN | A proactive cyber-risk classification model is proposed, based on BN in transportation. |
| Alexandre et al. [55] | Air Transportation | BN | This research presented a framework using BN for the command-and-control support systems of air transportation. |
| Sabarathinam et al. [56] | CPS | BN | A framework is developed for the decision-maker to determine the root cause of problems in CPSs. |
| Seyedmohsen et al. [57] | Vehicle Transportation | BN | Development of model, which includes both qualitative and quantifiable measures for vehicular electrical systems. |
| Mario et al. [58] | Vehicle Transportation | BN | A system is proposed for the recognition of threats in automotive-enabled applications. |
| Chao et al. [59] | Chemical Industry | GT | Integrating security and safety resources to protect the chemical industry. |
| Nima et al. [60] | Process Plants | BN and GT | A low-capacity approach is proposed for process plants, as a temporary mode of eliminating vulnerabilities. |
| Hui et al. [61] | Railways | BN | A risk analysis method is proposed for managing operative risks in the railway. |
| Xiqiang et al. [62] | Railways | BN | A model is developed to predict and diagnose risks for urban railway. |
| Jamal et al. [63] | Systems of Systems (SoS) | BN | Development of an approach to determine cyber-attacks propagation in SoS. |
| Elvin et al. [64] | Vehicle Transportation | BN | To develop a framework for trust model using ML and DL for vehicle transportation. |
| Xiaoyan et al. [65] | Oil and Gas Sector | BN | This research identifies risk in the oil and gas sector by proposing a graphic model and BN approach. |
| Ying et al. [66] | Railways | BN | A risk identification method based on BN for metro construction is developed. |
| Subhojeet et al. [67] | Vehicle Transportation | GT | A graph enabled based risks recognition approach in vehicle-vehicle communication. |
| Huai et al. [68] | Gas Pipelines | GT | Development of a method to examine the reliability in gas pipeline systems. |
| Gabriele et al. [69] | Chemical Industry | BN | A probabilistic risk assessment method is developed based on BN to monitor threats in the chemical industry. |
| Zhiqiang et al. [70] | Oil wharf Handling | BN | To develop a risk analysis model based on a static incident approach. |
| Jinsoo et al. [71] | Nuclear | BN | A methodology is proposed for diagnostic outcomes from BN model for risk assessment. |
| Donya et al. [72] | Gas and Pipelines | BN | A novel methodology is proposed for vulnerability calculation of gas pipelines. |
| Xianyou et al. [73] | Networks Security | BN | Development of vulnerability analysis method that may eliminate the cyber-attacks. |
| Galizia et al. [74] | Socio-Technical Systems | BN | This study aims to examine what factors could influence sociotechnical systems. |
| Francesca et al. [75] | Chemical Industry | BN | The developed approach addresses the vulnerability evaluation using BN model. |
| Zhao et al. [76] | Navigation Environment | BN | Establishment of an index system by integrating BN with fuzzy theory to offer safety evaluation. |
| Mark et al. [77] | Chemical Industry | BN | Development of vulnerability analysis approach methodology for monitoring intentional attacks. |
| Remya et al. [78] | Unmanned Aerial Vehicles (UAV) | BN | A technique to solve issues related to software risks and failures are developed by using BayesiaLab. |
| Xin Chen [79] | Complex Systems | GT | A polynomial-time system is proposed to recognize critical nodes for ensuring security in complex systems, such as the power and energy sectors. |
| Mark et al. [80] | Petroleum Plants | BN | Development of extended risk analysis methods at various stages of plants to ensure unauthorized access. |
| Martin et al. [81] | Maritime Industry | GT | This study develops an approach for validating the vulnerability in the maritime sector. |
| Jinsoo et al. [82] | Nuclear | BN | To develop a model for evaluating security for the nuclear domain in a unified way. |
| Marco et al. [83] | Railways | BN | Development of methodology for transferring attacks trees into BNs. |
| Matti et al. [84] | Mobile Networks | BN | Establishment of probabilistic risk evaluation approach for risk assessment and sensitivity analysis. |
| Xiqiang et al. [85] | Railways | BN | To develop BN enabled model for train control center that can be quantifiable for safety analysis in railway. |
| Yongjia et al. [86] | Cognitive Radio Networks (CRNs) | BN | Establishing an innovative system to diagnose and protect from malicious attacks. |
| Kairan et al. [87] | Vehicle Transportation | BN | Development of transportation security evaluation method to estimate a real-world mountainous expressway. |
| Amal et al. [88] | Maritime Industry | BN | A novel solution related to offshore piracy is proposed to characterize threats and probable targets. |
| Guannan et al. [89] | Software | BN | An estimation model is proposed for internet-based software applications. |
| Jiali et al. [90] | Maritime Industry | BN | To develop a fuzzy enabled BN system in shipping to evaluate the security of passengers. |
| Sher et al. [91] | Railways | GT | Incorporation of mobile agent notions with Petri nets offers one-dimensional control, which raises the safety of the train system. |
| LONG et al. [92] | Smart Grid | BN | An integrated method of FTA and BN is developed for analyzing risks in power systems. |
| Zeng Xianfeng [93] | Railways | BN | To develop a security evaluation method using BN model to improve train equipment and repair and maintenance work reliability. |
| TIAN et al. [94] | Water Traffic System | BN | This research develops a system that can monitor the safety issues associated with water traffic to realize the initial warning efficiently. |
| William et al. [95] | Networks Security | BN | An incorporated framework is developed to monitor for computing a mean time to compromise the system by the known-unknown vulnerability. |
| Jinsoo et al. [96] | Nuclear | BN | To establish a risk investigation approach for instrumentation and control (I and C) for identifying mitigating vulnerabilities. |
| Stefan et al. [97] | Vehicle Transportation | GT | Three graph-based protocols were developed, by means of wide-ranging simulations, to detect insider threats. |
| Jingjing et al. [98] | Railways | BN | To propose an approach to meet the necessities of accuracy in high safety for the train control system for a fault diagnosis system. |
| John et al. [99] | Air Transportation | GT | Development of method using game theory and GT concepts and graph theory for security risk mitigation. |
| Heung et al. [100] | Nuclear | BN | This study analytically modeled management approach, which offers the progress of safety-critical software. |
| Chaze et al. [101] | Maritime Industry | BN | This study presents the architecture based on incorporated BNs for its feedback planning. |
| Mo Ming [102] | Network Security | GT | An integrated GT approach is developed to have a safety evaluation in the network security domain. |
| Shuliang et al. [103] | Smart Grid | GT | A framework is proposed to investigate the susceptibilities in interdependent systems. |
| Song et al. [104] | Asian Games | BN | The proposed BN model accomplishes fire risk evaluation along with conducting fast disaster condition valuation. |
| André et al. [105] | Medical | BN and GT | This study presents an application for risk mitigation in ventricular-enabled devices. |
| Study | Citations | Data Source | Nodes | Applicability |
|---|---|---|---|---|
| Xiaorong et al. [42] | 2 | EK, ED | 9 | Risk Management |
| Lipeng et al. [43] | 2 | EK, ED | 31 | Holistic Event Investigation |
| Meizhi et al. [44] | 2 | EK, ED | 15 | Risk Management |
| Raditya et al. [45] | 1 | ED | 8 | Risk Management |
| Tai-hua et al. [46] | 0 | EK | Risk Management | |
| Mingjing et al. [47] | 1 | EK, ED | 11 | Risk Management |
| Xiaoxue et al. [48] | 0 | EK | 16 | Vulnerability Assessment |
| Xin et al. [49] | 0 | ED | Risk Management | |
| Meizhi et al. [50] | 1 | EK, ED | 14 | Risk Management |
| Niamat et al. [51] | 30 | EK, ED | 5 | Resilience Quantification |
| Chengpeng et al. [52] | 32 | EK, ED | 11 | Risk Management |
| Yi et al. [53] | 1 | EK, ED | 24 | Risk Management |
| Barry et al. [54] | 48 | EK, ED | 51 | Risk Management |
| Alexandre et al. [55] | 4 | ED | 13 | Cyber Impact Assessment |
| Sabarathinam et al. [56] | 0 | EK, ED | 8 | Root Cause Analysis |
| Seyedmohsen et al. [57] | 37 | EK, ED | 6 | Risk Management |
| Mario et al. [58] | 7 | ED | 5 | Intrusion Detection |
| Chao et al. [59] | 30 | ED | 4 | Risk Management |
| Nima et al. [60] | 8 | ED | 6 | Vulnerability Assessment |
| Hui et al. [61] | 4 | ED | 24 | Risk Management |
| Xiqiang et al. [62] | 0 | EK, ED | 19 | Risk Management |
| Jamal et al. [63] | 0 | EK | 8 | Risk Management |
| Elvin et al. [64] | 10 | ED | Trust Computation | |
| Xiaoyan et al. [65] | 25 | ED | 40 | Risk Management |
| Ying et al. [66] | 16 | EK, ED | 31 | Risk Management |
| Subhojeet et al. [67] | 7 | ED | 6 | Anomaly Detection |
| Huai et al. [68] | 60 | EK, ED | 53 | Reliability Assessment |
| Gabriele et al. [69] | 16 | EK | 8 | Risk Management |
| Zhiqiang et al. [70] | 4 | ED | 47 | Risk Management |
| Jinsoo et al. [71] | 27 | ED | 13 | Risk Management |
| Donya et al. [72] | 17 | EK | 30 | Vulnerability Assessment |
| Xianyou et al. [73] | 3 | ED | 20 | Vulnerability Assessment |
| Galizia et al. [74] | 4 | EK | 12 | Risk Management |
| Francesca et al. [75] | 12 | EK, ED | 8 | Vulnerability Assessment |
| Zhao et al. [76] | 0 | EK | 24 | Risk Management |
| Mark et al. [77] | 9 | EK, ED | 8 | Vulnerability Assessment |
| Remya et al. [78] | 2 | EK, ED | 6 | Safety Assessment |
| Xin Chen [79] | 6 | EK | 60 | Vulnerability Assessment |
| Mark et al. [80] | 4 | EK, ED | 17 | Risk Management |
| Martin et al. [81] | 1 | ED | 3 | Vulnerability Assessment |
| Jinsoo et al. [82] | 76 | ED | 64 | Vulnerability Assessment |
| Marco et al. [83] | 22 | EK | 10 | Risk Management |
| Matti et al. [84] | 1 | EK | 5 | Risk Management |
| Xiqiang et al. [85] | 3 | EK | 47 | Risk Management |
| Yongjia et al. [86] | 7 | ED | 4 | Attacks Analysis |
| Kairan et al. [87] | 4 | EK | 36 | Risk Management |
| Amal et al. [88] | 60 | EK | 20 | Risk Management |
| Guannan et al. [89] | 1 | ED | 20 | Risk Management |
| Jiali et al. [90] | 0 | EK, ED | 58 | Risk Management |
| Sher et al. [91] | 17 | ED | 14 | Software Verification |
| LONG et al. [92] | 2 | EK | 4 | Risk Management |
| Zeng Xianfeng [93] | 0 | ED | 22 | Safety Assessment |
| TIAN et al. [94] | 1 | ED | 12 | Water Traffic Management |
| William et al. [95] | 33 | ED | 20 | Risk Management |
| Jinsoo et al. [96] | 17 | ED | 16 | Risk Management |
| Stefan et al. [97] | 49 | ED | 8 | Attack Analysis |
| Jingjing et al. [98] | 10 | EK, ED | 7 | Fault Analysis |
| John et al. [99] | 3 | EK | 16 | Risk Management |
| Heung et al. [100] | 32 | EK, ED | 8 | Fault Analysis |
| Chaze et al. [101] | 11 | EK | 4 | Risk Management |
| Mo Ming [102] | 0 | ED | 6 | Attack Analysis |
| Shuliang et al. [103] | 139 | ED | 182 | Vulnerability Assessment |
| Song et al. [104] | 1 | EK, ED | 45 | Risk Management |
| André et al. [105] | 15 | ED | 4 | Risk Management |
| Study | Implementation Criteria | Threat Actor |
|---|---|---|
| Xiaorong et al. [42] | Simulation | Not Specified |
| Lipeng et al. [43] | Simulation | Outsider |
| Meizhi et al. [44] | Simulation | Not Specified |
| Raditya et al. [45] | Real-time | Insider |
| Tai-hua et al. [46] | Real-time | Outsider |
| Mingjing et al. [47] | Simulation | Not Specified |
| Xiaoxue et al. [48] | Real-time | Not Specified |
| Xin et al. [49] | Real-time | Not Specified |
| Meizhi et al. [50] | Preliminary | Not Specified |
| Niamat et al. [51] | Preliminary | Outsider, Insider |
| Chengpeng et al. [52] | Real-time | Not Specified |
| Yi et al. [53] | Simulation | Not Specified |
| Barry et al. [54] | Preliminary | Not Specified |
| Alexandre et al. [55] | Simulation | Outsider |
| Sabarathinam et al. [56] | Simulation | Not Specified |
| Seyedmohsen et al. [57] | Simulation | Not Specified |
| Mario et al. [58] | Simulation | Not Specified |
| Chao et al. [59] | Preliminary | Not Specified |
| Nima et al. [60] | Real-time | Outsider |
| Hui et al. [61] | Real-time | Outsider |
| Xiqiang et al. [62] | Real-time | Not Specified |
| Jamal et al. [63] | Simulation | Not Specified |
| Elvin et al. [64] | Preliminary | Not Specified |
| Xiaoyan et al. [65] | Real-time | Not Specified |
| Ying et al. [66] | Real-time | Outsider |
| Subhojeet et al. [67] | Simulation | Not Specified |
| Huai et al. [68] | Simulation | Not Specified |
| Gabriele et al. [69] | Preliminary | Not Specified |
| Zhiqiang et al. [70] | Simulation | Not Specified |
| Jinsoo et al. [71] | Real-time | Insider |
| Donya et al. [72] | Preliminary | Not Specified |
| Xianyou et al. [73] | Preliminary | Not Specified |
| Galizia et al. [74] | Simulation | Not Specified |
| Francesca et al. [75] | Simulation | Outsider |
| Zhao et al. [76] | Real-time | Not Specified |
| Mark et al. [77] | Real-time | Outsider, Insider |
| Remya et al. [78] | Simulation | Not Specified |
| Xin Chen [79] | Simulation | Not Specified |
| Mark et al. [80] | Preliminary | Not Specified |
| Martin et al. [81] | Preliminary | Not Specified |
| Jinsoo et al. [82] | Real-time | Not Specified |
| Marco et al. [83] | Simulation | Not Specified |
| Matti et al. [84] | Simulation | Not Specified |
| Xiqiang et al. [85] | Real-time | Not Specified |
| Yongjia et al. [86] | Preliminary | Not Specified |
| Kairan et al. [87] | Preliminary | Not Specified |
| Amal et al. [88] | Preliminary | Not Specified |
| Guannan et al. [89] | Simulation | Not Specified |
| Jiali et al. [90] | Real-time | Not Specified |
| Sher et al. [91] | Real-time | Not Specified |
| LONG et al. [92] | Simulation | Not Specified |
| Zeng Xianfeng [93] | Simulation | Not Specified |
| TIAN et al. [94] | Real-time | Not Specified |
| William et al. [95] | Simulation | Not Specified |
| Jinsoo et al. [96] | Simulation | Not Specified |
| Stefan et al. [97] | Simulation | Insider |
| Jingjing et al. [98] | Simulation | Not Specified |
| John et al. [99] | Preliminary | Not Specified |
| Heung et al. [100] | Preliminary | Not Specified |
| Chaze et al. [101] | Simulation | Not Specified |
| Mo Ming [102] | Real-time | Not Specified |
| Shuliang et al. [103] | Simulation | Not Specified |
| Song et al. [104] | Simulation | Not Specified |
| André et al. [105] | Real-time | Not Specified |
| Study | Research Outcome | Study | Research Outcome |
|---|---|---|---|
| Xiaorong et al. [42] | Risk Assessment Model | Galizia et al. [74] | Risk Analysis Framework |
| Lipeng et al. [43] | Systematic Causation Model | Francesca et al. [75] | Vulnerability Assessment Method |
| Meizhi et al. [44] | Dynamic Bayesian Network Model | Zhao et al. [76] | Safety State Assessment Model |
| Raditya et al. [45] | Risk Oriented Decision-Making Method | Mark et al. [77] | Vulnerability Assessment |
| Tai-hua et al. [46] | Risk Assessment Model | Remya et al. [78] | System Safety Approach |
| Mingjing et al. [47] | Interpretative Structural Model | Xin Chen [79] | Polynomial-Time Algorithm |
| Xiaoxue et al. [48] | An Integrated Security and Safety Framework | Mark et al. [80] | Extended Risk Evaluation Model |
| Xin et al. [49] | Ideological Security Assessment Method | Martin et al. [81] | Spatial Agent Enabled Model |
| Meizhi et al. [50] | Analytical Model | Jinsoo et al. [82] | Security Risk Model |
| Niamat et al. [51] | Resilience Framework | Marco et al. [83] | Transformational Approach |
| Chengpeng et al. [52] | Risk Assessment Model | Matti et al. [84] | Risk Assessment Method |
| Yi et al. [53] | Risk Probability Evaluation Model | Xiqiang et al. [85] | BN-Based Structure Learning Algorithm |
| Barry et al. [54] | Cyber Risk Classification Model | Yongjia et al. [86] | Three-Layer Bayesian Model |
| Alexandre et al. [55] | Cyber Impact Evaluation Framework | Kairan et al. [87] | Security Assessment Model |
| Sabarathinam et al. [56] | A Root Cause Evaluation Framework | Amal et al. [88] | Offshore Piracy Solution |
| Seyedmohsen et al. [57] | Decision-Making Tool | Guannan et al. [89] | Dependability Evaluation Model |
| Mario et al. [58] | Intrusion Recognition System | Jiali et al. [90] | Fuzzy-Based BN Model |
| Chao et al. [59] | Vulnerability Assessment Graph Model | Sher et al. [91] | Mobile Petri Net Model |
| Nima et al. [60] | Cost Robust Approach for Domino Effects | LONG et al. [92] | Combined BN an FTA Model |
| Hui et al. [61] | Risk Interaction Analysis Method | Zeng Xianfeng [93] | BN enabled Model |
| Xiqiang et al. [62] | Risk Management Model | TIAN et al. [94] | Multi-layer System |
| Jamal et al. [63] | Model-Driven Assessment Approach | William et al. [95] | Unified Framework |
| Elvin et al. [64] | Malicious Node Detection Approach | Jinsoo et al. [96] | Security Risk Model |
| Xiaoyan et al. [65] | Risk Identification Model | Stefan et al. [97] | Attack Detection Method |
| Ying et al. [66] | Risk Analysis Method | Jingjing et al. [98] | Fault Diagnosis Method |
| Subhojeet et al. [67] | Graph-based Anomaly Detection Technique | John et al. [99] | Security Risk Assessment Method |
| Huai et al. [68] | GT-BNbased Method | Heung et al. [100] | Fault Estimation Method |
| Gabriele et al. [69] | A Probabilistic Risk Evaluation Approach | Chaze et al. [101] | Risk Management System |
| Zhiqiang et al. [70] | Risk Assessment Model | Mo Ming [102] | New GT Method |
| Jinsoo et al. [71] | A Cyber Security Risk Model | Shuliang et al. [103] | Vulnerability Analysis Framework |
| Donya et al. [72] | Security Vulnerability Valuation Method | Song et al. [104] | BN-Enabled Model |
| Xianyou et al. [73] | Network Security Model | André et al. [105] | Risk Mitigation Approach |
| Study | Pros | Cons |
|---|---|---|
| Xiaorong et al. [42] | Offers a feasible solution for risk assessment in CPS, the feasibility is verified based on two event scenarios. | Lacks in presenting the finished model of the research. |
| Lipeng et al. [43] | The key benefit of the proposed model is that its applicability is checked in multiple scenarios. | The process consumes a lot of time, thus restricting the model’s application up to few only. |
| Meizhi et al. [44] | Utilization of vast dataset. | The use case areas are fixed. |
| Raditya et al. [45] | This study is useful in offering real-time risk management options to mitigate cyber threats. | This study has not provided conclusive data, as it was an early study. |
| Tai-hua et al. [46] | Potential to be applied for Chinese enterprises in presenting efficient anomaly prevention and response policies. | It is specified for Chinese enterprises for a Chinese problem. Readjustment is needed if used in other places. |
| Mingjing et al. [47] | Efficient in enhancing security in urban express logistics and avoiding safety hazards. | Merely a prototype is proposed. |
| Xiaoxue et al. [48] | The authors recommended low vulnerable and improved resilient perspective for the northern sea route. | Resilience level needs improvement. |
| Xin et al. [49] | Improves evaluation accuracy and reduces estimation error for the educational sector. | It has a limited use case to demonstrate its developed method. |
| Meizhi et al. [50] | Various significant influencing factors for maritime piracy are identified, and the applicability is authenticated using sensitivity analysis. | Feasibility issues, due to limited data. |
| Niamat et al. [51] | The capability of framework to be applied for different sectors. | This study does not offer decision-theoretic troubleshooting. Moreover, the framework is still preliminary. |
| Chengpeng et al. [52] | Offers efficient and flexible risk management for real circumstances. | It is limited up to only operational aspects. In contrast, complete analysis is not focused on this tool. |
| Yi et al. [53] | More accuracy in the navigation risk of ships in the bridge area in distinct conditions. | This research is validated based on a specific use case. |
| Barry et al. [54] | High prediction accuracy (nearly 100%) of the qualitative and quantitative risk factors. | It is used for specific sectors only. |
| Alexandre et al. [55] | Efficient in demonstrating cyber impacts in whole systems based on invaders and defenders’ plans, without knowing the hard-to-assess attacker’s activities. | Limited scenarios and tested situations. |
| Sabarathinam et al. [56] | To assist in determining the root cause of risks within the systems. | The results are based on simulations. |
| Seyedmohsen et al. [57] | Both qualitative and quantitative factors are used with rigorous testing. | Perhaps overspecialized. Only to be used in its sector. |
| Mario et al. [58] | The accuracy of the developed model is reasonably optimal. | Lacking in measuring efficiency in real-time scenarios. |
| Chao et al. [59] | Ability to decrease the risk of intended attacks by continuous monitoring | Allocation optimization is not considered. |
| Nima et al. [60] | A cost-efficient solution for vulnerability assessment. | Limited to restricted sectors. |
| Hui et al. [61] | Offers practical recommendations for establishing countermeasures in diminishing risk events in railway. | A risk mitigation strategy is not presented. |
| Xiqiang et al. [62] | Efficient in diagnosing of main factors, which may put threats to rail transport. | Threat actors are not specified. |
| Jamal et al. [63] | High efficiency in autonomous quarry mitigation associated with signal interference. | Cannot protect from all high impact attacks. |
| Elvin et al. [64] | Improved malicious detection in vehicular networks, due to inclusion of perception and reasoning in the decision building process. | Results are still preliminary. |
| Xiaoyan et al. [65] | Continuous evaluation of possible incident frequencies and outcomes by providing unique risk awareness. | Conditional probability tables are not presented. |
| Ying et al. [66] | The casual diagnostic analysis in complex and uncertain environments. More accurate than fault tree analysis. | Complex data collection process, an automatic technology for collecting required information, is not considered. |
| Subhojeet et al. [67] | Capability to recognize malicious threats and differentiate them from safety-critical activities. | The developed model is still preliminary. |
| Huai et al. [68] | Failure analysis from different prospects, such as topology, functional restriction, environmental, and dynamic. | There needs an improvement for analyzing network measurements and results of unit failures. |
| Gabriele et al. [69] | Accurate quantitative estimation of attack success probability and for the classification of the more hazardous escalation situations. | Lacks in performing a quantitative evaluation of the credibility of attack success. |
| Zhiqiang et al. [70] | An efficient quantitative risk assessment for finding security weaknesses. | The results need to be verified based on real-time scenarios. |
| Jinsoo et al. [71] | A generic approach toward monitoring and mitigating security and safety risks. | This study is conducted for a specific sector. |
| Donya et al. [72] | This study efficiently resolves uncertainties in the failure probability of elements and the temporal classification of occurrences. | The developed model is still preliminary. |
| Xianyou et al. [73] | Using multiple BN models to accurately assess vulnerabilities. | The developed model is still preliminary. |
| Galizia et al. [74] | New recommendations for resilience in socio-technical systems. | Lacks in presenting real-time analysis. |
| Francesca et al. [75] | A systematic procedure for vulnerability assessment against outside threats. | Insider threats are not considered in this study. |
| Zhao et al. [76] | An experiential analysis that effectively exhibits the safety status for the navigation environment. | Threats are not specified. |
| Mark et al. [77] | Increase awareness in vulnerability management for the chemical industry. | This study is conducted for a specific sector. |
| Remya et al. [78] | Robustly monitoring of unmodeled and unexpected failures. | This study does not robustly manage unexpected and unmodeled failures. |
| Xin Chen [79] | Efficiently evaluate vulnerabilities and crucial devices of the system. | The simulation results still need to be modified. |
| Mark et al. [80] | Efforts in delivering awareness to society for the development of databases about associated security failures. | The developed methodology is still preliminary. |
| Martin et al. [81] | The accuracy of the developed model is reasonably well in comparing existing approaches. | The developed model is still preliminary. |
| Jinsoo et al. [82] | An efficient mitigation measures for real-time analysis of risks in the nuclear sector. | The proposed research affects BN accuracy. |
| Marco et al. [83] | Results verified for combined attacks with mutual and non-trivial influences. | Limited to only one case study. |
| Matti et al. [84] | This research is helpful in documenting the expert knowledge. | Real-time traffic monitoring control has not been performed. |
| Xiqiang et al. [85] | Applicability in emergency cases with high accuracy. | Specific for the case study. Challenging implementing in other fields. |
| Yongjia et al. [86] | Having low-SNR and better availability. | The results are only preliminary. Testing on the different scenarios is needed. |
| Kairan et al. [87] | A security assessment is verified using a use case study. | The results are only preliminary. |
| Amal et al. [88] | BN implementation improves the Sargos system with is inherent abilities. | A specific approach is developed for the maritime industry; a lot of modifications are needed for use in other sectors. |
| Guannan et al. [89] | A dynamic and optimal risk assessment for the software industry. | The simulation results still need to be modified. |
| Jiali et al. [90] | Increases accuracy for risk assessment in the maritime industry. | Lacks in empirical data for circumstantial results. |
| Sher et al. [91] | Offers support mobility, protection, and concurrency for software verification. | Threat actors are not specified. |
| LONG et al. [92] | Offer recommendations for the designing and implementing of the energy sector to decrease the potential risks. | Specific use cases are hard to emulate outside of the sector or system. |
| Zeng Xianfeng [93] | Presented reliable dataset for research purposes in the railway sector. | Lack of practicality in railways. |
| TIAN et al. [94] | More robust solution for the water traffic system. | The human factor is not considered in real-time monitoring and is lacking for managing adequate personnel. |
| William et al. [95] | Applicable for both known and unknown vulnerabilities. | Limited applicability domains. |
| Jinsoo et al. [96] | This study assists in identifying fundamental factors that may pose cybersecurity hazards. | The simulation results still need to be modified. |
| Stefan et al. [97] | Reduces communication redundancies and enables data uniformity inspection in transportation. | Limited usability. |
| Jingjing et al. [98] | Improved accuracy and effective use of train control system. | Merely a preliminary analysis for the high-speed railway. |
| John et al. [99] | Feasibility and compatibility for protecting air transportation. | The results are only preliminary. |
| Heung et al. [100] | Systematic evaluation of the anticipated faults in the system. | There is not sufficient data of safety-critical software, assembled for real-time systems. |
| Chaze et al. [101] | To efficiently recognize and respond to risks in maritime piracy. | There is a need for an ontology for proper usability. |
| Mo Ming [102] | Correctly demonstrate the network safety situation and improve the safety of the system. | Heavily integrated with its system; therefore, difficult to use outside of network security analysis. |
| Shuliang et al. [103] | Efficiency in analyzing vulnerabilities in smart grid. | The developed model is more methodological than practical. |
| Song et al. [104] | The developed BN model plays a significant role in reducing fire risks. | The testing is not entirely performed before winter games. |
| André et al. [105] | Providing a better quality of life and more prolonged survival of patients. | The threat actors are not specified. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pirbhulal, S.; Gkioulos, V.; Katsikas, S. Towards Integration of Security and Safety Measures for Critical Infrastructures Based on Bayesian Networks and Graph Theory: A Systematic Literature Review. Signals 2021, 2, 771-802. https://doi.org/10.3390/signals2040045
Pirbhulal S, Gkioulos V, Katsikas S. Towards Integration of Security and Safety Measures for Critical Infrastructures Based on Bayesian Networks and Graph Theory: A Systematic Literature Review. Signals. 2021; 2(4):771-802. https://doi.org/10.3390/signals2040045
Chicago/Turabian StylePirbhulal, Sandeep, Vasileios Gkioulos, and Sokratis Katsikas. 2021. "Towards Integration of Security and Safety Measures for Critical Infrastructures Based on Bayesian Networks and Graph Theory: A Systematic Literature Review" Signals 2, no. 4: 771-802. https://doi.org/10.3390/signals2040045
APA StylePirbhulal, S., Gkioulos, V., & Katsikas, S. (2021). Towards Integration of Security and Safety Measures for Critical Infrastructures Based on Bayesian Networks and Graph Theory: A Systematic Literature Review. Signals, 2(4), 771-802. https://doi.org/10.3390/signals2040045








